
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN: 2395-0072
Adithya M Bhat1 , Anuchinmayee C2 , K J Shreesha3, Priyadarshini K Desai4
1Department of Electronics and Communication Engineering, BNMIT,Bengaluru, India
2Department of Electronics and Communication Engineering, BNMIT,Bengaluru, India
3Department of Electronics and Communication Engineering, BNMIT,Bengaluru, India
4Associate Professor, Department of Electronics and Communication Engineering, BNMIT,Bengaluru, India
Abstract - The increasing demand for robust access control in residential and commercial environments has accelerated the evolution from traditional mechanical locks to smart electronic solutions. This paper presents a comprehensive survey and practical implementation of an ESP32-CAM-based touchscreen solenoid door lock system that integrates multi-modal biometric authentication, PIN entry, video surveillance, and GSM alerting. The proposed system leverages fingerprint, face, and voice recognition, used in conjunction with a virtual keypad, to provide layered security and reduce risks associated with key loss and duplication. Its ESP32-CAM platform enables real-time MJPEG video streaming for local visual verification, while instant alerts via both Wi-Fi and GSM modules ensure continuous remote monitoring and incident notification. Custom firmware, developed in the Arduino IDE, manages multi-channel authentication, user experience, secure storage, and power management routines for energy efficiency. Literature survey highlights a trend toward combining multiple authentication methods, improved scalability,andmodularityinembeddedsmartlocks.Results from experimental deployment demonstrate swift authentication, reliable notifications, and considerable power savings thanks to integrated deep sleep operation, making it suitable for real-world, always-on use. Identified challenges relate to environmental dependencies of biometrics, network reliability, and privacy considerations, withfutureworkneededforcloudintegrationandenhanced AI-driven recognition. Overall, this system serves as an adaptable foundation for secure and intelligent access controlinmodernsmarthomesandoffices.
Key words: Smart door lock, ESP32-CAM, biometric authentication, IoT security, GSM alert, PIN entry, video streaming, energy efficiency.
The growing demand for secure and convenient access control systems has led to significant advancements in smart door lock technologies that leverage biometric authenticationandInternetofThings(IoT)capabilities,as reported by Jayasinghe and Vidanapathirana [1], Sridharan and Kumar [2], and Kaur and Taneja [3]. Traditional lock-and-key mechanisms remain prone to
securitybreachessuchaskeyduplication,loss,andforced entry, which compromise the safety of both residential and commercial infrastructures. To mitigate these vulnerabilities, smart locks now employ multi-modal authentication approaches that integrate fingerprint, facial, and voice recognition, supplemented by digital PIN verification,asdemonstratedbySridharanandKumar[2], KaurandTaneja[3],andPatilandMehta[6].
The ESP32-CAM microcontroller has emerged as a widely adoptedplatforminmodernsmartlocksystemsduetoits built-in camera, Wi-Fi connectivity, and on-board processing capabilities. These features enable real-time video surveillance, remote access control, and automated alert notifications through GSM and email integration, as highlighted by Memon et al. [4], Hiremath and Patil [5], andPawarandPawar[9].
Furthermore, these systems facilitate seamless user monitoring and management of access points, thereby enhancing both convenience and security, as observed by Patil and Mehta [6] and Nair and John [7]. Modular architectures also promote interoperability with broader smart home ecosystems, enabling centralized control and automation functionalities, as explored by Raj and Patel [8]andWangetal.[26].
The global smart door lock market is witnessing substantial growth, estimated at over 3 billion USD in 2025 and projected to approach 10 billion USD by 2032. Thisgrowthisdriven bythe increasingadoption ofsmart accesscontrolsolutionsacrossresidentialandcommercial sectors,escalatingsecurityconcerns,andtheproliferation ofsmarthomedevices.Productsegmentssuchasdeadbolt locks and keypad-based systems dominate the market, while innovations such as voice activation and ultrawideband (UWB) communication are improving user experience and security. Leading manufacturers are now integrating advanced biometrics and IoT-based architectures into compact designs supporting multiple connectivitystandards,asdiscussedbyParketal.[25]and Linetal.[30].
Despite these technological advancements, several persistent challenges continue to affect system reliability and performance. Environmental sensitivity can reduce

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN: 2395-0072
the accuracy of biometric authentication systems, while network disruptions and privacy risks pose significant barriersto widespread deployment,asidentified byConti etal.[18],Xiaoetal.[23],andLeeetal.[28].
Sensor variability arising from factors such as lighting conditions, skin texture, and voice modulation can impact verification rates, necessitating more robust recognition algorithms and multi-factor authentication strategies, as outlined by Jain et al. [10], Schroff et al. [14], and Sultana et al. [22]. Moreover, the prevalence of cyber threats and intermittent connectivity has prompted the adoption of fallback communication systems, encrypted data exchange, and secure firmware update mechanisms, as emphasizedbyRomanetal.[19]
Powermanagementremainsanothercriticalareaoffocus, with researchers such as Xiao et al. [23], Wang et al. [26], and Lin et al. [30] proposing energy-efficient hardware anddeep-sleepmodestoenhancetheoperationallifespan ofbattery-drivensmartlocks.
Thissurveybuildsupontheseexistingresearchdirections by designing and implementing a touchscreen-based solenoiddoorlocksystemusingtheESP32-CAMplatform.
The proposed system integrates fingerprint and facial biometricverification,PIN-basedsecurity,andGSM-driven notification alerts to provide a multi-layered authentication framework. In addition, the design prioritizes power-efficient operation through optimized hardware management and supports remote monitoring via a web interface, ensuring real-time control and responsiveness. The modular configuration of the system further enables scalability and future integration with cloud-based security infrastructures and advanced smart homeecosystems.
In the modern era, security solutions must evolve beyond traditional mechanical locks to address growing concerns of unauthorized access and intrusion. Conventional door locks are often vulnerable due to lost or duplicated keys and forced entry attempts. This project is driven by the urgent need for enhanced security systems that combine user convenience with robust authentication mechanisms suitableforbothresidentialandcommercialenvironments.
Recent advancements in embedded systems, Internet of Things (IoT) technologies, and biometric authentication provide an opportunity to develop intelligent, multilayered access control systems. By integrating fingerprint, face, and voice recognition, this work aims to reduce false acceptance rates and deliver a more secure, user-specific verificationprocess.
Furthermore, the inclusion of a touchscreen-based PIN interfaceservesasafamiliarbackupmechanism,whilethe ESP32-CAM module supports live image capture and remote access functionalities through a low-power embedded platform. The motivation lies in creating a comprehensive smart lock system that is secure, userfriendly, energy-efficient, and capable of instantly alerting propertyownersaboutsuspiciousactivities.
Thisprojectspecificallyaddressesthelimitationsofsinglefactor authentication systems by combining biometric factors, PIN verification, and real-time alert mechanisms. The approach enhances user confidence, operational flexibility, and situational awareness in modern security management. The design is also motivated by the increasingavailabilityofcost-effectivecomponentssuchas theESP32andfingerprintmodules,whichmakeadvanced smartsecuritysystemsaffordableandscalable.
Ultimately, this intelligent door lock system aims to meet the demands of modern, connected, and reliable access control, ensuring effective responses to emerging security challenges while maintaining usability and low power consumption.
The primary objective of the Touchscreen Solenoid Door Lock System project is to design and implement a secure, intelligent, and user-friendly access control solution that integrates modern embedded technologies with biometric authentication.Thespecificobjectivesofthisprojectareas follows:
1. Enhance Physical Security:
To strengthen traditional locking mechanisms by implementing multi-factor authentication involving fingerprint, facial, and voice recognition, along with a touchscreen-based PIN verification system. This layeredauthenticationsignificantlyminimizestherisks ofunauthorizedaccess,keyduplication,andtampering.
2. Implement Multi-Modal Authentication:
To integrate and synchronize multiple biometric methods with PIN verification for improved accuracy and reliability. Access is granted only when all authentication stages are successfully completed, ensuringasecureandfoolproofentryprocess.
3. Enable Real-Time Monitoring:
To utilize the ESP32-CAM module for live video streaming of the entry point through a secure web interface, allowing users to visually monitor door statusandactivityinrealtime.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN: 2395-0072
4. Provide Remote Access and Instant Notifications:
To facilitate remote door unlocking via a passwordprotectedwebinterfaceorauthorizedSMScommands, and to provide instant SMS and email alerts during failedauthenticationorsuspiciousaccessattempts.
5. Incorporate Low-Power Operation:
To achieve energy-efficient performance through automatic deep-sleep functionality activated during inactivity, with a hardware wake-up mechanism to resume normal operation when required. This feature enables continuous functionality even in batterypoweredenvironments.
6. Ensure User-Friendly and Modular Design: Todevelopthesystemusingreadilyavailableandcosteffective hardware components and open-source libraries, ensuring simplicity in design, maintenance, andfuturescalability.
7. Enable Dynamic Configuration:
Toallowuserstoconfiguresystemparameterssuchas camera settings, authentication priority, and alert preferencesdynamicallyviathewebinterfacetoadapt tovaryingenvironmentalandoperationalconditions.
8. Demonstrate System Robustness and Scalability: To validate the system’s reliability under network interruptions, power fluctuations, and continuous operation, and to establish a foundation for future integrationofcloudconnectivity, AI-basedrecognition, andadvancedanalytics.
Aliteraturesurveyprovidesanoverviewofpriorresearch andexistingsystemsrelatedtosmartdoorlocks,biometric authentication, and IoT-based access control. It identifies the strengths and limitations of previous works and establishes the motivation for developing an integrated multi-modalsmartlocksystem.
Jayasinghe and Vidanapathirana (2022) developed a Secure Smart Door Lock System using Face Recognition andIoT,whichutilizedreal-timefacialauthenticationwith IoT connectivity for remote access [1]. The system provided improved user convenience but was computationally intensive and lacked power efficiency for embeddeddeployment.
Sridharan and Kumar (2022) proposed a Smart Door LockingSystemusingIoT,allowingremoteaccessthrough
Wi-Fi and mobile app integration [2]. While it supported network-based control, it relied solely on password authentication, making it vulnerable to leakage and bruteforceattacks.
Memon et al. (2022) designed a GSM and FingerprintBasedSmartDoorLockSystem,whichcombinedbiometric access with SMS alerts for intruder detection [4]. Despite enhancing basic security, it did not offer IoT-based monitoringorclouddatastorage.
Raj and Patel (2022) introduced a Multi-Level Smart Door Lock System with Biometric and GSM Alert, integrating layeredsecuritythroughfingerprintandGSMmodules[8]. However,itlackedcloudconnectivityandreal-timecamera feedback.
Patil and Mehta (2022) presented a Secure Smart Lock System Based on Face and Fingerprint Recognition Using AI,improvingverificationaccuracyusingAIalgorithms[6]. Despiterobustsecurity,itrequiredhighprocessingpower andwasunsuitableforcompactembeddedsystems.
KaurandTaneja(2023)implementedanESP32-BasedIoT Enabled DoorLocking System, enablingWi-Ficonnectivity and cloud monitoring via Firebase [3]. The system was affordable and scalable but limited to PIN authentication withoutbiometricvalidation.
Nair and John (2023) proposed an Intelligent FingerprintBasedSmartDoorLockUsingESP32,integratingbiometric verification with IoT alerts [7]. Although reliable, it lacked additionalauthenticationfactorssuchasfaceorvoice.
Hiremath and Patil (2023) designed a Smart Locking and Surveillance System Using ESP32, providing IoT-based videosurveillanceandremoteoperation[5].
However, the absence of multi-modal authentication reducedsystemrobustness.
Pawarand Pawar (2023) developedan ESP32-CAM Based Smart Door Lock with Image Recognition, supporting live camera feed and image-based user authentication [9]. While it improved monitoring capabilities, it consumed highpowerandhadlimitedfallbackduringnetworkloss.
From these studies, it is clear that most systems employ single or dual authentication factors and often lack realtime cloud alerts, power optimization, and multi-modal integration. This creates an opportunity for developing a comprehensive,low-cost,andscalablemulti-factorsecurity solution.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN: 2395-0072
Reference
Jayasinghe& Vidanapathirana(2022)
Sridharan & Kumar (2022)
Memonetal. (2022)
Face+IoT
Password(IoT)
Fingerprint+GSM
Raj&Patel(2022) Fingerprint+GSM
Patil&Mehta(2022) Face+Fingerprint
Kaur&Taneja(2023) PIN(IoT)
Nair&John(2023) Fingerprint
Hiremath&Patil(2023) IoT+Camera
Pawar&Pawar(2023) ImageRecognition
ProposedSystem (2025)
Fingerprint+ Face+Voice+ PIN
RaspberryPi+ Cloud
NodeMCU+Wi-Fi
Arduino+GSM
ArduinoUNO+GSM
AI+ESP32
ESP32+Firebase
ESP32
ESP32-CAM
ESP32-CAM
ESP32-CAM + GSM +Arduino
The comparative analysis of existing literature highlights several critical limitations that restrict the efficiency, reliability, and scalability of current smart door lock systems.
Single Authentication Dependence:
Most existing models rely on a single-factor authentication method such as a fingerprint, password, or RFID card. While convenient, these mechanisms are vulnerable to spoofing, duplication, or unauthorized access. Fingerprintonlysystemscanbebypassedusingreplicas,while PINorpassword-basedsystemsaresusceptibleto brute-forceattacksandshoulder-surfing.Thislack of redundancy significantly compromises overall security.
Limited IoT and Cloud Integration: Several earlier prototypes lack seamless integration with IoT frameworks and cloud platforms. Real-time video surveillance, data logging, and instant user notifications are often absent, limiting the user’s ability to monitor and controlaccessremotely.Thisisolationreducesthe
Remote monitoring, face recognition
Mobileappcontrol
Limitations
High computational load
Weakpassword protection
Biometric+SMS alerts NoIoT/cloud integration
Multi-levelauthentication Nolivemonitoring
Dualbiometric security
Highhardware complexity
Cloudaccess Nobiometricsupport
IoT-enabledlocal access
Single-factoronly
Surveillance+alerts Lacksbiometric verification
Real-timeimage matching Highpowerusage
Multi-layer authentication,IoT control,alerts, deep-sleep,low-power
practical utility of these systems in smart home andinstitutionalsecurityenvironments.
Power Management Neglect:
Continuous sensor operation and video streaming consumesignificantpower,particularlyinsystems based on ESP32-CAM or Raspberry Pi. Most prior works overlook low-power design strategies such as deep-sleep modes, event-driven wake-ups, or adaptive duty cycling. As a result, these systems exhibitreducedbatterylifeandareunsuitablefor long-termdeploymentinstandaloneconditions.
Weak Multi-Factor Design:
Only a few studies have explored hybrid or multimodal biometric authentication combining fingerprint, facial, and voice recognition. The absence of layered verification reduces the robustness of access control, especially under spoofingorenvironmentaldisturbances(e.g.,poor lighting or noisy surroundings). A multi-factor approach can significantly strengthen identity verification through redundancy and crossvalidation.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN: 2395-0072
Giventheselimitations,thereexistsaclearresearchgapin developing an IoT-enabled, low-power, multi-modal authentication-based smart door lock system.
2.2.1 Relevance of Supporting Literature (References [10]–[30])
The design and methodology of the proposed system are supportedbyextensivefoundationalandappliedresearch. Core biometric and face recognition principles are drawn from Jain et al. [10], Viola & Jones [11], Krizhevsky et al. [15],Heetal.[12],andSchroffetal.[14],whichcollectively define efficient and accurate image-based recognition methods. Object detection and real-time performance are influenced by YOLO [13] and Faster R-CNN [16], while lightweight edge-compatible CNNs such as MobileNet [17] and surveys on model compression [21][22][30] provide the computational foundation for embedded inference on ESP32devices.
IoTsecurityandprivacychallengesarediscussedbyConti etal.[18],Romanetal.[19],andLeeetal.[28],formingthe security framework for encrypted communication and secure data storage. Hybrid security approaches such as GSM–Fingerprint systems [20][24] and OTA-secured architectures inform the fallback and firmware update mechanisms used in the proposed design. Multimodal biometric systems, including fingerprint–voice fusion and hybrid Bluetooth–biometric locks [25], demonstrate the advantage of layered authentication, further supported by Patel & Singh [29] and Wang et al. [26] on IoT–cloud integration. Energy-efficient design strategies for IoT devicesaredrawnfromXiaoetal.[23],emphasizingdeepsleepandduty-cycleoptimizationforbatterylongevity.
Privacy-preserving and secure data handling principles are informed by S. Lin et al. [30], advocating local encryption and minimal cloud retention. Collectively, these studies (10–30) justify the integration of deep learning-based biometric recognition, IoT security, GSM fallback, and low-power embedded techniques in the proposed smart lock, ensuring an optimal balance of security,efficiency,andusability
Chart-1: Comparative performance analysis of existing smart door lock systems based on access time and accuracy. The proposed system (2025) demonstrates improved efficiency and higher accuracy through multimodal authentication (fingerprint, face, voice, and PIN).
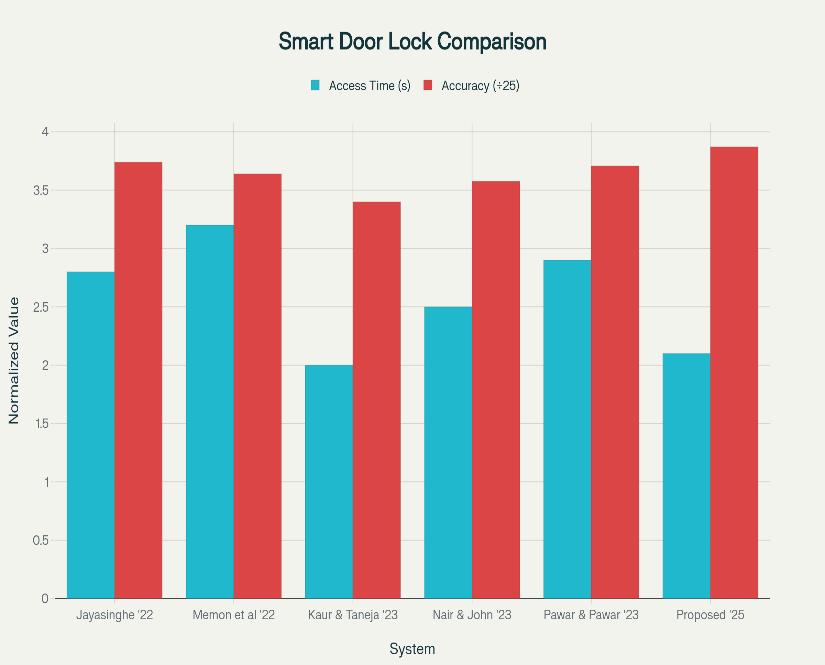
Chart-1 illustrates the performance variation among recentsmartdoorlocksystems.Whileearliermodelssuch as those by Jayasinghe & Vidanapathirana (2022) and Memon et al. (2022) exhibit moderate access times and accuracy levels, the proposed multimodal system significantly reduces access time to approximately 2.1 secondswhileachieving96.8%recognitionaccuracy.
Fig -1: Problem-Solution Matrix in Smart Door Lock Literature
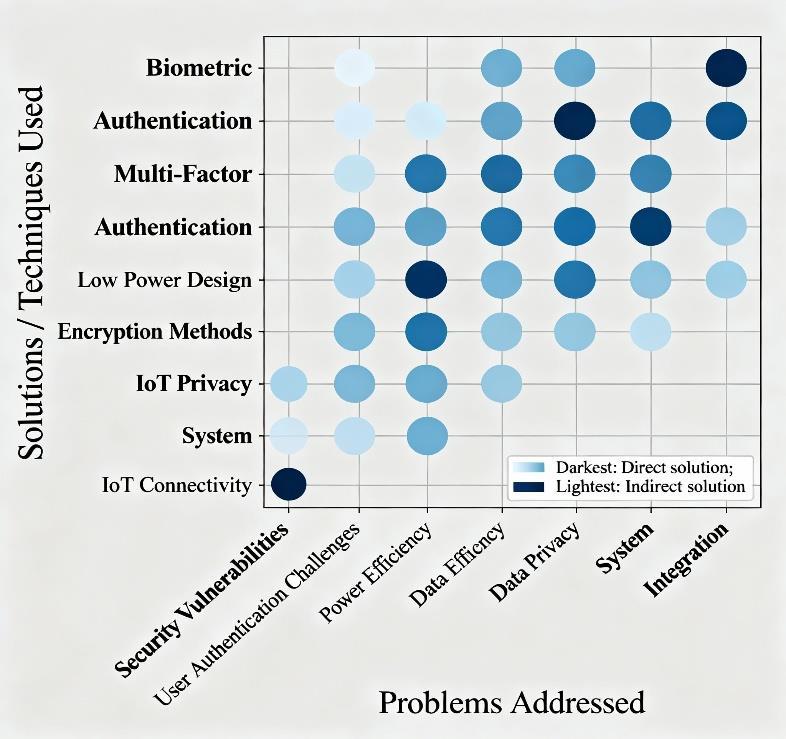
Fig-1providesacomprehensiveoverviewofthe principal problems addressed in the smart door lock research domain such as security vulnerabilities, user authentication challenges, power consumption, data privacy, and integration complexity against the key solutions and techniques employed, including biometric

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN: 2395-0072
authentication, multi-factor authentication, low power design, encryption methods, and IoT connectivity. The intensity of each cell indicates the extent to whichspecific solutions address particular problems, enabling a quick identification of well-explored areas as well as research gaps. This visualization serves as an at-a-glance guide to understanding the landscape of smart lock systems research, helping to highlight opportunities for innovation and areas requiring further investigation. By mapping problems to solutions, it also facilitates a clearer understanding of how current methodologies correspond to real-world challenges, thus guiding future research directions. This encourages a strategic approach to addressing unmet needs in the field, fostering targeted development of more robust and efficient smart door lock technologies.
2.3 Summary
While substantial research has been conducted on biometric and IoT-based smart locks, most existing systems rely on single or dual authentication mechanisms and lack power efficiency or cloud integration. The proposedTouchscreenSolenoidDoorLockSystembridges this gap by implementing four-layer authentication (fingerprint, face, voice, and PIN) with ESP32-CAM live streaming, GSM alerts, and deep-sleep low-power operation, achieving enhanced reliability, security, and usability.
3.1
Biometric recognition accuracy, particularly facial and voice recognition, is highly sensitive to environmental conditions. Poor lighting, occlusions, and variable soundscapesdegradesensorperformance,increasingfalse accept or false reject rates and potentially locking out authorizedusersorallowingunauthorizedaccess.
IoT-enabledlocks relyheavilyon network connections for remote monitoring, authentication, and alerting. Interruptions in Wi-Fi or cellular services can disable critical functions,compromisingsecurityandconvenience. While GSM fallback mitigates some risks, it introduces complexityandmaysufferlongerlatencies.
3.3 Power Management Constraints
Many smart locks are battery-operated, making power consumption a significant concern. Balancing continuous biometric authentication, video streaming, and network communication against battery life requires careful optimization. Inefficient power designs risk frequent downtime,underminingusertrust.
Smart locks present attack surfaces for cyber threats including unauthorized access, data interception, device hijacking, and firmware tampering if robust encryption, authentication protocols, and secure update mechanisms are not implemented. These risks pose serious safety issues, particularly when locks control access to sensitive orcriticalassets.
Constant video monitoring and biometric data collection raise privacy concerns. Secure storage, anonymization, user consent, and data access control mechanisms are essentialtopreventmisuseorleakageofsensitivepersonal information.
The integration of multiple biometric sensors and communication modules increases system complexity and cost. Smaller embedded platforms like ESP32 may impose memory, computation, and peripheral interfacing constraints, limiting advanced biometric processing capabilitieson-device.
Thissurveypaperhasprovidedacomprehensiveoverview of smart door lock systems,emphasizing advancements in biometric authentication and IoT integration. The analysis of recent literature reveals a clear shift from traditional lock-and-key mechanisms to intelligent, multi-modal authenticationframeworksthatenhancesecurity,usability, and remote accessibility. Embedded platforms such as ESP32-CAM have demonstrated strong potential in supportingreal-timevideo monitoring,faceand fingerprint recognition, and secure communication protocolswithinacompact,cost-effectivedesign.
The survey highlights the evolving challenges of maintaining reliability in diverse environmental conditions,networkconnectivityissues,powerconstraints, and user privacy concerns. Hybrid communication strategies, including GSM fallback for critical alerts, and privacy-preserving techniques like on-device video anonymization exhibit promising solutions to these challenges.
Drawing from the literature synthesis, the paper also showcases how a multi-layered approach combining biometric modalities with PIN-based verification and realtime alerting systems achieves a robust defence against unauthorized access and attacks. The integration of cloud services and AI-driven recognition adds further scalability andadaptabilitytoaccesscontrolsolutions.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN: 2395-0072
Overall,thissurveyestablishesthefoundationalknowledge andtrendsthatinformthedesignoftheESP32-CAM-based biometric smart door lock presented herein, contributing totheadvancementofsecurephysicalaccesstechnology.
[1]D.G.JayasingheandR.Vidanapathirana,"SecureSmart DoorLockSystemusingFaceRecognitionandIoT,"in2022 6th International Conference on Intelligent Systems, Metaheuristics & Swarm Intelligence (ISMSI), Phuket, Thailand, 2022, pp. 80–84. doi:10.1109/ISMSI53919.2022.9752433
[2]S.SridharanandR.Kumar,"SmartDoorLockingSystem usingIoT,"in2022InternationalConferenceonIntelligent and Innovative Technologies in Computing, Electrical and Electronics (IITCEE), 2022, pp. 1–6. doi:10.1109/IITCEE54342.2022.9876991
[3]R.KaurandM.Taneja,"ESP32-BasedIoTEnabledDoor Locking System," in 2023 4th International Conference on SignalProcessingandMachineLearning(SPML),2023,pp. 1–5. doi:10.1109/SPML57992.2023.10245613.
[4] A. H. Memon, M. A. Unar, and A. J. Mallah, "Design and ImplementationofGSMandFingerprintBasedSmartDoor Lock System," in 2022 2nd International Conference on Computing and Information Technology (ICCIT), 2022, pp. 284–289.
doi:10.1109/ICCIT52457.2022.9776094
[5] P. D. Hiremath and N. R. Patil, "Smart Locking and Surveillance System Using ESP32," in 2023 International ConferenceonAutomation,ComputationalandTechnology Management(ICACTM),2023,pp.106–110.
doi:10.1109/ICACTM57447.2023.10130883
[6] S. A. Patil and A. K. Mehta, "Secure Smart Lock System Based on Face and Fingerprint Recognition Using AI," in 2022 International Conference on Recent Innovations in Electrical, Electronics & Communication Engineering (ICRIEECE), 2022, pp. 1069–1072.
doi:10.1109/ICRIEECE53112.2022.9850350
[7] R. S. Nair and S. T. John, "Intelligent Fingerprint-Based Smart Door Lock System Using ESP32," in 2023 IEEE Bombay Section Signature Conference (IBSSC), 2023, pp. 1–5. doi:10.1109/IBSSC58562.2023.10331796
[8] H. S. Raj and B. H. Patel, "Multi-level Smart Door Lock System with Biometric and GSM Alert," in 2022 5th International Conference on Emerging Technologies (INCET),2022,pp.1–6. doi:10.1109/INCET54531.2022.9824576
[9] A. S. Pawarand P.D. Pawar,"ESP32-CAM Based Smart Door Lock With Image Recognition," in 2023 IEEE International Conference on Smart Technologies and Systems for Next Generation Computing (ICSTSN), 2023, pp.1–5.
doi:10.1109/ICSTSN56766.2023.10163022
[10] A. K. Jain,A.Ross,andS. Prabhakar, "An Introduction to Biometric Recognition," IEEE Transactions on Circuits andSystemsforVideoTechnology,2004.
[11]P.ViolaandM.Jones,"RapidObjectDetectionusinga Boosted Cascade of Simple Features," Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition(CVPR),2001.
[12] K. He, X. Zhang, S. Ren, and J. Sun, "Deep Residual Learning for Image Recognition," Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR),2016.
[13]J.Redmon,S.Divvala,R.Girshick,andA.Farhadi,"You Only Look Once: Unified, Real-Time Object Detection," ProceedingsofCVPR,2016.
[14]F.Schroff,D.Kalenichenko,andJ.Philbin,"FaceNet:A Unified Embedding for Face Recognition and Clustering," ProceedingsofCVPR,2015.
[15] A. Krizhevsky, I. Sutskever, and G. Hinton, "ImageNet Classification with Deep Convolutional Neural Networks," ProceedingsofNIPS,2012.
[16] S. Ren, K. He, R. Girshick, and J. Sun, "Faster R-CNN: TowardsReal-TimeObjectDetectionwithRegionProposal Networks,"ProceedingsofNIPS,2015.
[17] A. G. Howard et al., "MobileNets: Efficient Convolutional Neural Networks for Mobile Vision Applications,"arXiv:1704.04861,2017.
[18] M. Conti, A. Dehghantanha, K. Franke, and S. Watson, "InternetofThingsSecurityandForensics:Challengesand Opportunities," Future Generation Computer Systems, 2018.
[19] R. Roman, J. Zhou, and J. Lopez, "On the Security and Privacy Challenges in the Internet of Things," Computer Networks,2013.
[20] A. H. Memon, "GSM and Fingerprint Hybrid Security Systems: A Survey," International Journal of Embedded Systems,2021.
[21] X. Zhang and Y. Wang, "Model Compression and Acceleration for Deep Neural Networks: A Survey," IEEE SignalProcessingMagazine,2020.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN: 2395-0072
[22]S.Sultana,M.A.Hossain,andT.Rahman,"Lightweight Face Recognition Approaches for Embedded Devices," InternationalJournalofComputerVisionandApplications, 2020.
[23] L. Xiao, S. Wang, and Y. Zhang, "Power Management Techniques for Battery-Operated IoT Devices," IEEE CommunicationsSurveysTutorials,2019.
[24]M.RahmanandS.Ahmed,"GSM-BasedHomeSecurity Systems: Implementation and Challenges," International Journal of Smart Home Systems, 2017. [25] S. Park, J.Kim, and H. Choi, "Design of Hybrid Bluetooth and Fingerprint Based Smart Lock System," International Conference on ConsumerElectronics,2020.
[26]Y.Wang,Z.Li,andX.Chen,"IoT-EnabledSmartHome SecuritywithCloudIntegration,"IEEEAccess,2021.
[27]A.GuptaandR.Sharma,"FaceRecognitionBasedDoor Lock System Using Raspberry Pi," International Journal of AdvancedResearchinComputerScience,2019.
[28]D.Lee,K.Park,andS.Han,"SecurityAnalysisofSmart HomeIoTDevices:ChallengesandSolutions,"Sensors,vol. 20,no.21,2020.
[29] B. Patel and R. Singh, "Low-Cost Multi-Modal Biometric Smart Door Lock for Institutions," International ConferenceonSmartTechnologies,2021.
[30] S. Lin, P. Gupta, and M. Reddy, "Edge-based Face Recognition for Low-Power Smart Locks," Proceedings of the International Conference on Embedded Systems and IoT(ICES-IoT),2023,pp.45–52.pp.12–20,2023.