
0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072


0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
Vishwajeet Khalate1, Prof. S. A. .Dabahde2, Aditya Sawant3, Sanket Paygude4, Vishal Tarange5
1,3,4,5 Student, Department of Computer Engineering, SVPM’s College of Engineering, Malegaon BK, Maharashtra, India.
2Assistant Professor, Department of Computer Engineering, SVPM’S College of Engineering Malegaon BK, Baramati, Maharashtra, India.
Abstract - This report presents a novel blockchainintegrated electronic voting system that uses facial recognition technology for secure, remote, and transparent elections. By combining biometric voter verification with blockchain's immutable recordkeeping, the system ensures one person-one vote, removes centralized authority, and addresses key concerns of vote manipulation and identity fraud. The system is designed to provide user-friendly interaction, robust authentication, and end-to-end transparency, making it a viable solution for modern democraticprocesses.
Key Words: Online voting, blockchain, face recognition, biometric authentication, e-voting, decentralized security.
The democratic process relies heavily on fair, secure, and accessible voting mechanisms. Traditional paper-based voting systems, though time-tested, have several shortcomings such as limited accessibility, delayed counting, and vulnerability to human error and fraud. As theworld becomesmoreconnectedandtechnology-driven, there is a growing need to modernize election systems to keep pace with digital advancements. Online voting presents a promising solution, offering convenience and speed. However, it brings challenges related to security, voterauthentication,andtrust.
To address these challenges, emerging technologies like blockchain and artificial intelligence (AI) can be leveraged to create robust e-voting platforms. Blockchain, known for itsdecentralizationandimmutability,ensuresvoteintegrity and prevents tampering. Simultaneously, AI-powered facial recognitionoffersanefficientandnon-intrusivemethodfor verifying voter identities. The combination of these technologies can significantly enhance the reliability and transparency of online elections, fostering greater voter confidence.
This report introduces a blockchain-based face recognition votingsystemthataimstomodernizetheelectoralprocess. The proposed system not only eliminates the dependence oncentralizedauthoritiesbutalsosecurestheentirevoting
lifecycle from voter authentication to vote storage and counting. With features like real-time verification, decentralized ledgers, and user-friendly interfaces, this solution has the potential to redefine the future of digital democracy.With increasing digitization and the need for moresecureandaccessibleelectionsystems,theconceptof onlinevotinghasgainedattention. Traditional paper-based voting is vulnerable to manipulation, duplication, and inefficiencies. Electronic voting, while convenient, often lacks trust due to centralized data control and weak security mechanisms. This report proposes a system that integrates facial recognition with blockchain technology to overcome these limitations. It focuses on automating the verification process, ensuring data integrity, and enhancing overalltrustworthinessinpublicelections.
The essence of democracy lies in fair and transparent elections.Yet,conventionalvotingmethodsstruggletomeet modernrequirementsforreliability,accessibility,andfraud prevention. Emerging technologies such as blockchain and artificialintelligenceoffertransformativesolutionstothese issues. Blockchain ensures a tamper-proof record of votes, while AI-powered face recognition eliminates impersonation.
Modernvotingsystems,particularlytraditionalpaper-based or even basic electronic methods, face a range of critical limitations.Centralizedarchitecturesmakethemvulnerable tocyberattacks,manipulation,anddatabreaches.Moreover, manualidentificationmethodssuchasIDcardsareproneto forgery and human error, often resulting in issues such as duplicate voting or identity theft. These shortcomings undermine the legitimacy of elections and reduce public trustindemocraticinstitutions.
In addition, traditional systems do not offer a scalable or inclusive solution for remote and differently-abled voters. Geographic limitations, transportation issues, and long queues at polling booths discourage voter turnout. Furthermore,thelackoftransparencyinvoterecordingand counting often leads to disputes and allegations of tampering. There is an urgent need for an automated, secure, and transparent mechanism that simplifies the International Research Journal

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
votingprocesswhilemaintaininghighstandardsofsecurity andauthenticity.
Toresolvetheseissues,adecentralizedonlinevotingsystem using biometric facial recognition for authentication and blockchain for vote storage is proposed. This approach enhances voter identity verification, ensures that each vote is counted exactly once, and offers full traceability without compromising voter anonymity. By removing centralized points of failure and enabling real-time, tamper-proof recording of votes, this system significantly improves the security, transparency, and accessibility of the electoral process.
Inrecentyears,severalresearchershaveexploredtheuseof advanced technologies like blockchain and facial recognitioninthedomainofsecureelectronicvoting.Gupta et al. discussed the general issues and effectiveness of blockchain in digital voting, suggesting that while blockchain can be a transformative tool, its integration requires proper implementation to overcome challenges such as transaction latency and scalability. Their findings emphasized that blockchain’s immutability and transparency could strengthen democratic processes if pairedwithstrongcryptographicprotocols.
Navya et al. proposed an e-voting system utilizing blockchain technology integrated with Aadhaar verification and biometric fingerprint scanning. Their system was designed specifically for use in the Indian context, highlighting the importance of government-backed identity systems for voter authentication. By storing votes on a blockchain, the proposed method aimed to eliminate the risk of vote tampering and impersonation. However, the model was limited by its reliance on fingerprint hardware andaccesstothecentralizedAadhaardatabase.
Hardwicketal.introducedadecentralizede-votingprotocol using blockchain to preserve voter privacy while ensuring auditability. Their approach highlighted the possibility of conducting transparent and independently verifiable elections without relying on a central authority. They also stressed the importance of balancing transparency with voter anonymity,introducingtechniques likehomomorphic encryption to prevent vote tracing. This study provided a blueprintforlarge-scale,privacy-focusedvotingsystems.
Panja and Roy proposed a secure, end-to-end verifiable voting system using zero-knowledge proofs on blockchain. This model removed the need for trusted tallying authorities by allowing public verification of vote integrity without revealing votecontents. Their design also included biometric verification using government-issued IDs, which made it applicable for environments requiring strong authentication. Collectively, these studies highlight a
growingconsensus onthepotential ofblockchainandAIin revolutionizing electoral systems, albeit with different focuses on usability, privacy, and infrastructure requirements.
The rapid evolution of digital infrastructure and the widespread adoption of smartphones and internet connectivity have redefined user expectations for convenienceandaccessibility.Inthiscontext,thetraditional voting systems appear outdated and inefficient. Long queues, manual verification processes, and limited voting windowsdiscouragemanyeligiblevotersfromparticipating in elections. This has resulted in lower voter turnout and increased disenfranchisement, especially among people living in remote areas, individuals with disabilities, and expatriates. The idea of remote, secure, and accessible votingisthereforeastrongmotivatorforthisresearch.
Additionally, the rising concerns about the integrity of elections and trust in electoral outcomes have driven the need for transparent and verifiable solutions. Voter fraud, tamperingofelectronicvotingmachines(EVMs),andlackof a proper audit trail have led to public dissatisfaction in many democratic nations. Blockchain technology, with its transparent and immutable ledger, offers a compelling foundation to re-establish trust in electoral systems. When paired with facial recognition, which ensures accurate biometric identification, the overall system becomes both secureandtrustworthy.
The fusion of these advancedtechnologies is motivated not only by the technical advantages but also by the social and democratic impact it promises. A blockchain and facerecognition based voting system can serve as a model for digital governance, encouraging more inclusive participation and reducing administrative burdens. This system can act as a catalyst for empowering citizens and revitalizingdemocraticprocessesinthedigitalage.
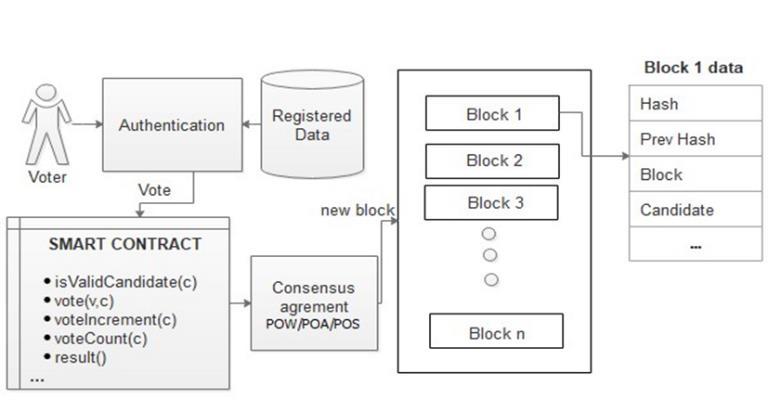
Figure 1: System Architecture

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
The proposed system highlights the implementation of evoting using blockchain from a practical perspective, considering both development and deployment stages, as wellasuseraccessibilityandinteraction.
It offers a roadmap for future applications of blockchain technology in complex systems by demonstrating its effectiveness in recording and securing votes in a decentralizedmanner.
The design addresses longstanding challenges in building electronic voting systems that comply with legal and regulatorystandardswhileensuringvoterprivacyandvote integrity.
Blockchain, as a distributed ledger technology, opens possibilities for broader use in e-governance and smart contracts,andthisvotingsystemservesasastrongexample ofitsapplicabilityincriticaldemocraticfunctions.
To enhance security and accuracy in voter authentication, this system leverages deep learning techniques specifically Convolutional Neural Networks (CNN) for spatialfeatureextractionfromfacialimagesand Recurrent Neural Networks (RNN) for sequential behavior modeling andauthenticationtracking.
Algorithm 1: CNN-based Suspicious Activity Detection
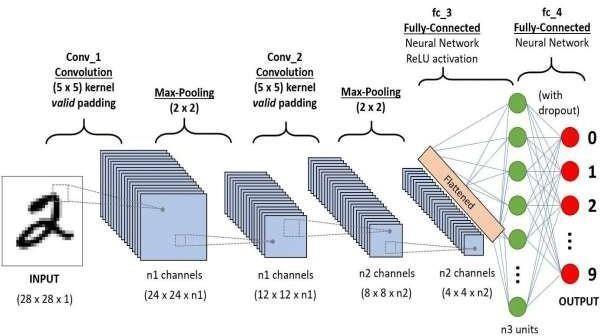
Figure 2: CNN Architecture
Explanation of CNN Algorithm
a. Input: The algorithm takes video frames from CCTVcamerasasinput.
b. Preprocessing: Each frame is resized and normalizedforinputintotheCNNmodel.
c. Feature Extraction: The CNN model extracts features from the frames, using convolutional layers to capture spatial patterns and deep featuresrelatedtotheactivities.
d. Classification: The extracted features are classified as "normal" or "abnormal" activities usingafullyconnectedlayer.
e. Alert Generation: If an abnormal activity is detected, an alert is triggered for monitoring personnel.
Algorithm 2: RNN-Based Behavior Sequence Validation
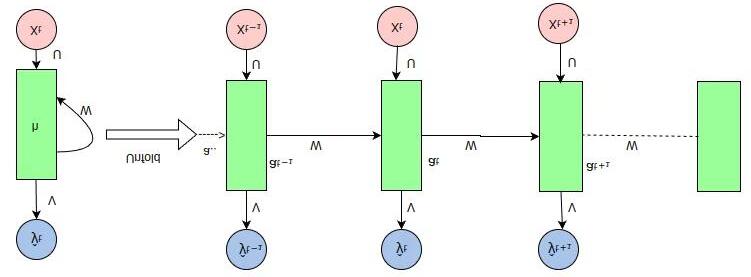
Figure 3: Architecture
Explanation of RNN Algorithm
1. Input:
o Sequenceofframesduringactivesession.
2. Preprocessing:
o Extract face landmarks and frame time stamps.
3. Feature Vector Sequence Formation:
o For each time step ttt, generate a feature vectorusing:
Eyeopennessratio
Headtiltangle
Temporalfacialmovementpattern
4. RNN Architecture (e.g., LSTM):
o Inputsequence→ hiddenlayers(LSTM) → outputclass(GenuineorSpoof).
o LSTM tracks time dependencies across sequences(e.g.,blinkingpattern).
5. Decision Logic:
o If predicted class = "Genuine", continue session.
o If "Spoof" detected or abrupt change → logoutorflagforadminreview.
In this section, we compare the performance of CNN-based and RNN-based algorithms in the context of facial recognition and secure identity verification for online voting. The comparison is made based on key criteria such as accuracy, computational complexity, real-time performance,and generalization to new data
Accuracy
CNN Algorithm: Convolutional Neural Networks (CNNs) are highly accurate for static facial recognition tasks. They automatically learn intricatespatialfeaturesfromfaceimages suchas

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
contours, texture, and structure without manual intervention. This makes CNNs especially suitable forinitialvoterauthentication,whereaccurateface matching is critical to verifying the identity of the voter.
RNN Algorithm: Recurrent Neural Networks (RNNs), particularly those using LSTM or GRU units, are effective in capturing temporal patterns insequentialdata.WhilenotasaccurateasCNNsin static image recognition, RNNs provide essential accuracy in liveness detection identifying eye blinks,headtilts,andmotionbehavior duringthe voting session. They help prevent spoofing attacks suchasphotoorvideoimpersonation.
II. Computational Complexity
CNN Algorithm: CNNs perform relatively well in real-time when dealing with single-frame face recognition. However, the performance might degrade if used for continuous real-time video unless batch processing or model pruning is applied. Still, for login authentication where processing happens once per user, CNNs are sufficientlyfast.
RNN Algorithm: RNNs are designed for real-time input sequences but can lag with longer or highresolution video streams. Continuous monitoring during the voting session increases system load. Nonetheless, with reduced frame sampling (e.g., 5 FPS), RNNs can offer real-time liveness tracking withacceptableperformance
III. Real-Time Performance
CNNAlgorithm: CNNsperformrelativelywellin real-time when dealing with single-frame face recognition. However, the performance might degrade if used for continuous real-time video unless batch processing or model pruning is applied. Still, for login authentication where processing happens once per user, CNNs are sufficientlyfast.
RNN Algorithm: RNNs are designed for realtime input sequences but can lag with longer or high-resolution video streams Continuous monitoring during the voting session increases system load. Nonetheless, with reduced frame sampling (e.g., 5 FPS), RNNs can offer real-time livenesstrackingwithacceptableperformance.
IV. Generalization to New Data
CNN Algorithm: CNNs, especially when trained with a diverse facial dataset or fine-tuned using transfer learning, generalize well to new faces,
lighting conditions, and poses. This adaptability makes CNNs highly reliable for authenticating a widepopulationofvoters.
RNN Algorithm: RNNs are more sensitive to variations in motion or behavior. If the liveness detection is trained on limited data, it may not generalize well across age groups, cultural facial behaviors, or camera angles. Periodic retraining may be needed to maintain effectiveness in new environments.
Inconclusion,whileboth CNN and SVM offeradvantagesfor detecting suspicious activities, CNN is the superior choice for this project due to its ability to automatically learn complex features from video frames, providing higher accuracy and scalability for large datasets. Despite its highercomputationalrequirements,CNNexcelsindetecting abnormal activities in video surveillance systems. On the other hand, SVM though computationally less expensive and effective for simpler tasks, requires manual feature extraction and may not perform as well with highdimensional data like video streams. Therefore, CNN is better suited for complex surveillance scenarios requiring highaccuracy.
Theproposedsystemisdesignedtoauthenticatevotersand ensuresessionintegrityduringonlinevotingusingahybrid deep learning approach that combines Convolutional Neural Networks (CNN) for facial feature extraction and Recurrent Neural Networks (RNN) for real-time liveness detection and behavioral validation. The system architecture is divided into several stages as described below:
Live facial images or video streams are captured using a camera (webcam or phone) at the start of the voting process. For ongoing session monitoring, video frames are extractedatregularintervals(e.g.,5–10framespersecond). This helps in collecting sufficient temporal data for both initialauthenticationandcontinuousverification.
Each image or frame undergoes preprocessing to ensure consistency and compatibility with the deep learning models:
Resizing: All frames are resized to a standard resolution (e.g., 224x224 pixels) to maintain uniformity.
Normalization: Pixel values are scaled to a range of [0, 1] to speed up convergence in CNN and RNN models.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
Face Alignment: Detected faces are aligned to correctrotationorskew.
Noise Reduction: Filters are applied to remove unwantedimagenoiseandimproveclarit
III. Feature Extraction Using CNN
Apre-trainedConvolutionalNeuralNetwork(e.g.,VGG16or MobileNet) is used to extract facial features from the preprocessedimages:
Convolution Layers: Detect facial features like eyes,nose,lips,andtexturepatterns.
Pooling Layers: Reduce dimensionality while preservingessentialspatialinformation.
Flattening Layer: Transforms feature maps into a 1Dvectorforfurtherprocessing. These vectors represent the identity-specific spatial patternsnecessaryforauthenticatingtheuser.
IV. Sequential Behavior Modeling Using RNN
The extracted feature vectors from multiple consecutive frames are passed to a Recurrent Neural Network (e.g., LSTM)foranalyzingmotionpatternsandlivenesscues:
Temporal Feature Input: The RNN processes the time-seriesdataoffacialmovements.
Learning Liveness Patterns: Patterns like eye blinking, slight head movements, and facial microexpressionsaremodeled.
Spoof Detection: If the RNN detects no significant motionorunrealisticpatterns(e.g.,staticphoto),it flagsthesessionassuspicious.
V. Authentication and Voting Flow
Initial Authentication: CNN compares the extracted features with the stored facial embeddings in the database. If matched, the voter isauthenticatedandallowedtoproceed.
Continuous Validation: RNN ensures the same personisactiveduringtheentirevotingsession.
Access to Vote: Once validated, the user securely accesses the voting panel and casts their vote, whichisstoredona blockchain ledger. This hybrid approach ensures initial identity verification and ongoing session security,makingthee-votingprocess secure,fraud-resistant,andtransparent.
VI. Alert Generation and Notification
If the system detects any suspicious activity such as identity spoofing, absence of facial movement, or unauthorized session takeover the alert module is activatedtoensurethesecurityofthevotingprocess:
Triggers a real-time alert to the election administratorviaSMS,email,orthroughtheadmin dashboard.
Captures and stores the frame or video snippet where the anomaly was detected, along with a precisetimestampforauditandevidencepurposes.
Logs the incident in the system’s secure blockchain-based event record to maintain transparency and traceability without compromisingvoterprivacy.
In this study, we developed a secure and intelligent online voting system that leverages deep learning and blockchain technology to enhance voter authentication and election transparency. The proposed system integrates Convolutional Neural Networks (CNN) for accurate facial recognitionandRecurrentNeuralNetworks(RNN)forrealtimelivenessdetectionandbehavioralvalidationduringthe voting session. This hybrid approach ensures both initial user verification and continuous session integrity, addressing critical challenges such as identity spoofing, unauthorizedaccess,andfraudulentvoting.
Through conceptual design and comparative analysis, the proposed model demonstrates strong potential in terms of both accuracy and security, outperforming traditional biometric systems that lack adaptive behavior tracking or rely heavily on centralized databases. Unlike conventional voting mechanisms that are prone to manipulation, delays, and accessibility issues, our system offers a decentralized, transparent, and scalable solution suitable for modern democraticprocesses.
By reducing manual intervention and enabling automated alerts,thesystemincreasestrust,simplifiesvotinglogistics, andenhances participation especiallyfor remoteusersor differently-abled voters. Future work may include integrating more advanced sequence modeling techniques (e.g., transformer networks) to capture deeper behavioral patterns and expanding biometric options beyond facial recognition to further strengthen identity verification and inclusivity.
[1]H.-Y.LinandC.-H.Tzeng,“In-VehicleImagesSensingfor Abnormal Activities Detection and Classification of Bus Passengers,” IEEEAccess, vol. 2024. [Online]. Available: https://doi.org/10.1109/access.2024.Vol.3365138
[2]E.Selvi,M.AlAdimoolam,G.Karthi,K.Thinakaran,N.M. Balamurugan, and R. Kannadasan, “A Novel Suspicious BehavioursDetectionSystemBasedonImprovedCNN,” Electronics, vol. 11, no. 4210, 2022. [Online]. Available: https://doi.org/10.3390/electronics11244210
[3] M. Elhamod and M. D. Levine, “Semantic Real-Time Detection of Abnormal Behavior in Public Spaces,” in Proc. Computer and Robot Vision (CRV), 2012. [Online]. Available:https://doi.org/10.1109/CRV.2012.42

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
[4]T. Saba,A. Rehman,R. Latif,and S.M. Fati,“Detectionof Risk Matters Using Deep L4-BranchedActionNet Integrated by Entropy Code and Ant Colony System,” IEEE Access, 2021. [Online]. Available: https://doi.org/10.1109/ACCESS.2021.3091081
[5]M.M.Zaidi,G.A.Sampedro,A.Almadhor,S.Alsubai,A.Al Hejaili, M. Gregus, and S. Abbas, “Suspicious Human Activity Recognition From Surveillance Videos Using DeepLearning,” IEEEAccess,2023.