
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
Minakshi Rana, Jaspreet Dhiman
Assistant Professor, Department of Computer Applications, Chandigarh Group of Colleges Landran, Mohali, India Assistant Professor, Department of Computer Applications, Chandigarh Group of Colleges Landran, Mohali, India
Abstract - Social media networking has greatly impacted social, cultural, and economic dynamics during the last ten years, becoming an essential part of life on a global scale. Worldwide Internet users as of March 2019 were 4,168,461,500, or 50.08% of the global population, according to internetlivestats.com. According to Statist, 2.22 billion people used social media in the world in 2021, accounting for 53%ofall social media users. Estimates suggest that by 2024, this figure will rise to 4.9 billion.
Users froma varietyofbackgrounds aredrawntothesesocial networking sites, and the data they produce is kept on cloud storage. But there are a lot of difficulties because of the explosionintheamount, speed, diversity,andaccuracyofdata in social media networking, especially when it comes to privacy and security issues. Simultaneously, it presents an opportunity to combat and investigate cybercrime when approached with intelligence and sophistication. Law enforcement agencies are actively engaged in preventing cybercrime by monitoring internet communications. This paper delves into recommendations and techniques aimed at thepreventionofcybercrime withinthecontextoftheevolving landscape of social media networking.
Key Words: Cybersecurity, Social Media Crime, Cyberstalking, Phishing Attacks, Digital Forensics, Online CriminalInvestigationetc.
Socialmediahasundergoneatransformativeimpactonthe cultural,economic,andsocialfabricofsociety,evolvinginto an indispensable aspect of individuals' lives. Serving as a multimedia content-sharing platform, encompassing text, audio, video, images, graphs, and animations, social media facilitatesinteractionthroughwebsitesorapplications.The contents shared constitute cloud-based big data, characterized by volume, diversity, speed, accuracy, unpredictability,quality,discovery,and
Asofyear2023,globalinternetusersreachedastaggering 5.2 billion, marking a 65% penetration of the world population [2]. Social media networking users, totaling billion worldwide in (60% global penetration), are anticipatedtoreach4.9billionby2024[3].Thisdiverseuser basespansvariousagegroups,cultures,religions,andsocial
attitudes, utilizing a multitude of devices to access social mediaplatforms.
Given the widespread appeal of these networking sites, individualsfromallwalksoflifearedrawntoconnectwith friendsand family, share daily experiences,and forge new connections. The allure of these social networking sites extends across different demographic segments, with user data beingstored in the cloud [4]. Thecontemporaryshift towardonlinelivinghassignificantlyalteredperspectiveson privacy and security, posing new challenges in the digital realm.
Modern problems are closely associated with the growing dimensions of data in social media networking, which are marked by an increase in quantity, speed, diversity, and accuracy. Concerns have been raised by this increase, particularly in the areas of security and privacy. Simultaneously,astutelyharnessed,itservesasapotenttool for crime prevention and investigation. The present age is synonymouswithinformationubiquity,manifestedthrough diversecommunicationchannelssuchasTwitter,Facebook, blogs,imageandvideosharing,andmobilemessaging.
The rapid interconnectivity facilitated by social media has exposed vulnerabilities, giving rise to cybercrime and traditional criminal activities online. Criminals exploit the perceived 'safe havens' afforded by the digital realm, capitalizingontheunawarenessofthecommunityengaging in electronic communications [6].Social media,actingasa dual-edged sword, not only facilitates community communication but also serves as a medium for criminal activitiesduetoitsreal-timeresponsiveness.
In the pursuit of a peaceful community and world, the prevalenceofcrimecannotbeignored.Ascrimeevolvesfrom traditional to electronic forms, social media becomes a dynamic arena where both criminal activities and law enforcement effortsunfold.Criminals exploitthe real-time nature of social media for planning and executing crimes, whilelawenforcementagenciesdeploythesameplatforms forcontrol,prevention,protection,andinvestigation.
Thispaperisstructuredasfollows:Section2delvesintothe ralatedworkmaterialoftheresearch;Section3exploresin depthstudyofcybercrimes;Section4providesasummaryof

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
research findings, concluding with discussions on future researchareas.
Cybercrimeisagrowingproblemthat'stoughtocatchand stoponceithappens,leavinglastingeffectsonvictims.The increase in cybercrime is linked to the widespread use of socialmedia,onlineshopping,andinternetbanking,where personalandfinancialinformationisoftenatrisk.Theriseof internet technology and its widespread availability bring aboutsecurityissues,leadingtocyber-attacksandhackers.
Tostaysafefromcybercrime,it'scrucial tounderstandits different forms and illegal activities online. Whether it's happening nationally or internationally, cybercrime has significantnegativeimpactsonsociety.Thisresearchfocuses onexploringvariouscybercrimemethodsandthetypesof illegalactivitiestakingplaceontheinternet.Wepayspecial attention to the role of social media in contributing to cybercrimesduetooveruseandalackofawareness.
Astheincidenceofcrimecontinuestorise,detectingcriminal activities on the internet has become increasingly challenging. Cybercrime is a term broadly employed to describe illicitactivities wherein computers and computer networks play pivotal roles as tools, targets, or sites of criminal operations. This includes a wide range ofactions, suchasdenial-of-serviceassaultsandelectronichacking.The phrase also refers to more conventional crimes in which networksorcomputersareusedtosupportillicitactivities. Cybercrimemanifestsasunauthorizedaccesstosystemdata, datamanipulation,destruction,andthetheftofintellectual property.
With the escalating frequency of criminal incidents, the associated crime-related data is expanding, making the analysis of crime information progressively intricate. The manualcollectionofcrimenewsisbothtime-consumingand exasperating.Anautomatedsystembecomesimperativeto streamline the process of gathering crime-related informationinatimelyandefficientmanner
To evaluate social media users' awareness of cybercrime.
To identify ideal strategies to prevent cybercrime throughsocialmedia.
Inordertoextractandvalidatepertinentdataoncybercrime prevention and detection solutions as well as intelligent cybersecuritymodels,asecondaryexploratoryapproachwas used.Thetargetdatainclusioncriterionwaspredicatedon onlinecontentonsubjectsassociatedwiththestatedtitles. For all search operations, the researchers used Mozilla FirefoxandGoogleChrome
Table -1: Impact of cybercrime on Social Media platforms
been duplicatedormisusedthrough
Thecyberworldfacesnumerousthreatsduetovarioustypes of cybercrimes. Commonly employed methods to deceive individuals include Cyber-Stalking, Cyber Assassination, Bluffing,andothers.Itisessentialtofamiliarizeoneselfwith thesecrimestonavigatethecyberworldsafely.
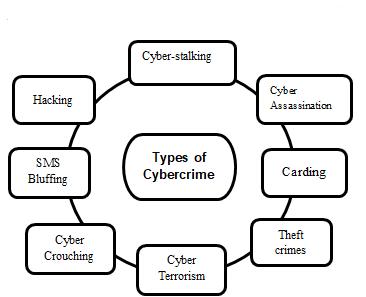
Fig.1showscategorizationofCyberCrime
a) Cyberstalking isacriminaloffensethatinvolvesan offender harassing a victim using electronic messaging platforms, including chat rooms, websites,andemail[2].Theanonymityofferedby

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
theInternetisusedbythecyberstalkertopursue theirvictimwhileavoidingdetection.
b) Cyber assassination is an act of assassination or character defamation carried out through digital media, usually including the Internet. It is not a separate criminal offense, misconduct, or tort. Although the punishments for "Cyber Assassination" vary from nation to nation, they usuallyfollowthebasicprinciplesspecifiedinthe EU'sandtheUN'sDeclarationsofHumanprinciples.
c) Hacking istheprocessofgettingunauthorizedor authorized access to a computer and using it to view, copy, or create data without intending to destroyitordoanyothermaliciousdamagetothe machine. Anyone who acquires unauthorized or permittedaccesstoacomputerwithoutintending tocauseharmisconsideredahacker.
d) SMS Bluffing makes use of the short messaging servicethatisavailableonmostmobilephonesand PDAs.Itentailschangingthesender'slookbyusing alphanumeric characters in place of the sender's originalmobilenumber(SenderID).Bluffingcanbe used for both legal and illegal purposes, such as impersonating a different person, business, or product, or mentioning the company name or productinthecommunication.
e) Carding is a type of credit card scam where a pilferedcreditcardisutilizedtomakechargeson pre-paid cards [3]. In the context of carding, individualstypicallyholdingthestolencardengage in purchasing store-branded gift cards. These gift cardscansubsequentlybesoldtoothersorusedto acquireotheritemsthatareconvertibleintocash. Thoseperpetratingcreditcardfraudinthismanner arecommonlyreferredtoascarders.
f) Cyber Crouching istheregistration,sale,oruseof a domain name on the internet with the goal of deliberately making money off the goodwill attached to another person's trademark. These onlinescammersmaythenoffertosellthedomain tothepersonorbusinessthatownsthetrademark foralargesum.
g) Theft crimes haveemergedasthemostprevalent formofcybercrime,withCredit/DebitCardFraud being the predominant type occurring frequently nowadays. This form of fraud transpires when unauthorized individuals deceitfully use a debit/credit card to acquire money or assets. Credit/debit card numbers can be compromised
through identity theft schemes or through vulnerabilitiesincertainwebsites
h) Cyber Terrorism deemedoneofthemostperilous manifestations of cybercrime, involves the utilizationoftheinternettoorchestrateviolentacts, encompassingdeliberateandextensivedisruptive activities [4]. Cyber terrorism is characterized by theintentionaldeploymentofdisruptiveactivities. Presently, this threat has expanded to include terrorist organizations engaging in cyber brain warfare,utilizingadvancedcomputingtechnologies to influence the human brain for their own objectives.
Asubstantialnumberofindividualsutilizesocialnetworking sitesthroughtheirmobilephones,laptops,orotherdevices, expressingtheirskillsandexperiencesbyuploadingvideos, photos, or written content. While these platforms simplify connectingwithfriendsthroughasimpleclick,manyusers remainunawareofthepotentialdrawbacksassociatedwith sharingextensivepersonalinformation.Socialmediagiants likeFacebook,WhatsApp,andInstagramserveasplatforms where user information, including location and personal profiles,canbeeasilyaccessed.
Despitetheconveniencetheseplatformsoffer,asignificant portionofusers,particularlyteenagersinIndia,maynotfully grasptheinherentrisks.GangopadhyayandDharhighlight the allure of social websites for young adults, providing opportunities to connect with both known and unknown individuals.Thegraphindicatesasubstantialuserbasefor socialmediainIndia,underscoringthepotentialvulnerability of personal information. The risk of hacking and misuse becomesapparent,asunauthorizedindividualsmayaccess andexploitpersonaldataforvariouspurposes.
Many users remain unaware of background activities, exemplified by the massive Yahoo breach in 2016, where approximately3billionaccountswerehacked,markingone of the largest security breaches in history. This data underscores the widespread use of social media networks globally, with Facebook leading the pack with 2.23 billion monthlyactiveusersasofOctober2023.Instagram,ranked sixth, boasted 1 billion monthly active accounts. These statistics underscore the magnitude of potential risks associatedwiththeextensiveuseofsocialmediaplatforms. UserdataisstoredonsocialmediabehemothslikeFacebook, Instagram,andWhatsApp,asseeninfigure:

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072

Social media platforms are vulnerable to cybercrime for a numberofreasons,including:
Large user base: Socialmediaplatformshavebillions ofusers,makingthemaprimetargetforcybercriminals seekingalargepoolofpotentialvictims.
Personal information: Users'names,addresses,phone numbers, and email addresses are just a few of the manypiecesofpersonalinformationthatsocialmedia platformsgatherfromthem.Thisdatacanbeusedfor identitytheft,fraud,andothercybercrimes.
Lacking security: Cybercriminals might take advantageofsecurityflawsinsocialmediaplatformsto accessuseraccountsordatawithoutpermission.
User behavior: Usersmayengageinriskybehaviors, such as clicking on links from unknown sources or sharing personal information publicly, which can increasetheirvulnerabilitytocybercrime.
Individualsusesocialmediaplatformstosocializewithone another,sharepersonallifeevents,andvoicetheiropinions onsocioeconomicconcerns. AccordingtoRaySuzette[35], theadvancementofsocialmediahasledtoinstanceswhere individuals commit crimes and then share these criminal activitiesinvariousforms,suchastext,videos,andimages
onsocialmediaplatforms.Justastechnologycanbeused for criminal activities, technology can also play a role in controlling,preventing,protecting,andinvestigatingcrimes.
Thebroadincorporationofsocialmediaintovariousaspects of life has profoundly impacted individuals' viewpoints towardcriminalactivityandvictimization[36].Peopleused to rely their ideas in the past on news articles from newspapersandtelevision.Butthesedays,peopleposttheir experiencesonsocialmediaandasktheirfriendsforhelpin catching criminals, which has a significant impact on how people form these beliefs [37]. Law enforcement uses images, text, and video files from social media as a rich source of information to characterize criminals and prosecutethem.AccordingtoJeremyCrump'sresearch[38], social media was first used by UK police departments in 2008.
To safeguard against the pervasive threats in the digital landscape, individuals and organizations must adopt a multifacetedapproachtocybersecurity:
Cyber-stalking-
Be Mindful of Personal Information: Avoid sharing excessive personal information online, including location details, daily routines, and contact information. Cyberstalkers often exploit readily available data to track and harasstheirtargets.
Secure Online Accounts: Setuptwo-factorauthentication wheneveryoucan,andmakesureeveryonlineaccounthasa strong,distinctpassword.Thisprovidesanadditionaldegree ofprotectionandincreasesthedifficultyforcyberstalkersto obtainunauthorizedaccess.
Cyber Assassination-
Maintain Strong Passwords: Use complex, unique passwords for your online accounts, especially those containing personal or sensitive information. Regularly update passwords and avoid using easily guessable information.
Document Incidents: Keep records of any cyber bullying incidents, including screenshots, messages, or other evidence.Thisdocumentationcanbeusefulifyouneedto involvelawenforcementortakelegalaction.
Hacking-
Be Concerned of Emails and Links: Proceedwithcaution whenyouclickonlinksoropenemailsfromsendersyouare not familiar with. Malicious attachments or links found in phishingemailshavethepotentialtocausehackingissues.
Regularly Back Up Your Data:Performregularbackupsof importantdataandstoreitinasecurelocation.Intheevent

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
ofahackingincidentorransomwareattack,havingbackups ensuresthatyoucanrecoveryourinformation.
SMS Bluffing-
Be Skeptical of Unknown Numbers: Ifyoureceiveatext messagefromanunknownnumber,exercisecaution.Avoid clicking on any links or responding to messages from unfamiliarsources.
Check the Sender's identification: IftheSMSpurportsto be from a reputable company, independently confirm the sender's identification. Use the official methods (website, phonenumber)togetintouchwiththeorganizationdirectly insteadofrelyingontheinformationprovidedinthetext.
Cyber Crouching-
By changing the privacy settings on social networking platforms and other online accounts, one can regulate the accessibility of personal information. Limit access to important information and adjust the settings to your comfortlevel.
Google Alerts: Set up Google Alerts for your name or relevantkeywords.Thisway,youcanreceivenotifications whennewinformationaboutyouappearsonline,allowing youtopromptlyaddressanyconcerningcontent.
Theft crimes
Secure Valuables: Storevaluableitemsinasecuresafethat is both anchored and well-hidden. This provides an additional layer of protection for important documents, jewelry,andothervaluablepossessions.
Be Cautious with Social Media: Avoid broadcasting your travelplansorextendedabsencesonsocialmediaplatforms. Publicizingyourabsencecanmakeyourhomeatargetfor burglars.
Carding-
Inspect the bank statements: Checkyourcreditcardand bankstatementsfrequentlyforanyunusualorquestionable activity.Notifyyourfinancialinstitutionrightawayifthere areanydifferences.
Enable Transaction Alerts: Set up transaction alerts on your credit and debit cards. Many banks offer alerts for transactionsoveracertainamountorforspecific typesof transactions, allowing you to quickly identify and address suspiciousactivity.
Cyber Terrorism-
EnhanceCyberIntelligenceSharing:Encouragethesharing ofcyberthreatintelligenceamonggovernments,intelligence agencies, and private-sector organizations. Timely
information exchange helps in identifying and addressing emergingthreats.
InvestinCybersecurityEducation:Promotecybersecurity educationandawarenessprogramstoempowerindividuals andorganizationstorecognizeandaddresspotentialthreats. Awell-informedpopulationisbetterequippedtocontribute tooverallcybersecurityefforts.
The digital world has endless possibilities, but it also has unspokenrisks.Cybercrimeisanever-changingthreatthat hides in the shadows of social media, waiting to take advantage of our weaknesses. A wide range of tools and resources are at your fingertips to address such issues. Knowing the underlying causes is crucial. Legislators, parents, law enforcement, and educators must work togethertounderstandthediversemotivationsunderlying these online offenses. Schools and colleges should weave cybercrime awareness into their curriculum, empowering students and parents to navigate the online world with confidence.Cybercellsanddedicatedcourts,equippedwith thelatesttoolsandexpertise,needtobestrengthenedand expanded. Only then can we swiftly respond to and effectivelydeterthesedigitaloffenses.Butthebattlewon't bewonbyinstitutionsalone.AcriticalalliancebetweenIT giantsandlawenforcementagenciesiscrucialfortracking andpenalizingcybercriminals.
[1]“SocialMediaUseinLawEnforcement:Crimeprevention andinvestigativeactivities,”LexisNexis,2014.
[2]J.Blomberg,“FightingCrimeThroughSocialMediaand SocialNetworkAnalysis,”SAS,2012.
[3] NW3C, “Criminal Use of Social Media (2013),” NW3C, 2013.
[4]BBCNews,“KimKardashianrobbery:Howdoyousell high-profilediamonds?,”October4,2016.
[5] Symantec, “What is social engineering?,” Symantec Corporation,2015.
[6]M.Sauter,“NineMajorWaysCriminalsUseFacebook,” FoxBusiness,2012.
[7]B.Nahorney,“InternetSecurityThreatReport(2017),” ISTR,2017.
[8]Adil,M.,Khan,R.,&Ghani,M.A.N.U.(2020).Preventive techniquesofphishingattacksinnetworks.Paperpresented atthe20203rdInternationalConferenceonAdvancements in Computational Sciences (ICACS). Doi:https://doi.org/10.1109/ICACS47775.2020.9055943
© 2025, IRJET | Impact Factor value: 8.315 | ISO 9001:2008 Certified Journal | Page1199

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
[9] A. A. Moore, “Cyberstalking and Women: Facts and Statistics,”thoughtco.com,2018.
[10] Bagyavati (2009) ‘social engineering’ in lech j.janczewskiandandrewm.colarikcyberwarefareandcyber terrorism
© 2025, IRJET | Impact Factor value: 8.315 | ISO 9001:2008 Certified Journal | Page1200