
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN:2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN:2395-0072
Lavanya Jain
Sacred Heart Convent School, Ludhiana, India
Abstract
Thispaperchartsthegrowthofartificialintelligenceincybersecurity,movingfromtherigid,rule-baseddefensesofthepastto the reflexive, adaptiveresponse systems weseetoday. Theaccount begins with the expert systems of the 1980s,whichfirst automatedthesearchforviruses,continuedthroughthemachine-learninggainsoftheearly2000sandculminatedinmodern platformsthatharnessdeepneuralnetworks.SupportingdatarevealthatAI-enhancedsolutionsnowcutfalsepositivesinhalf and improve detection accuracy for actual threats by 85% when stacked against their legacy counterparts. The review then considers newly rising functions:fullyautomatedincident response,user-behavior analytics,the identification offresh zeroday exploits, and predictive threat intelligence powered by AI, collectively underscoring the widening reach of machine learningacrosseveryphaseofthesecuritylifecycle.Privacyimplications,ethicalissueswithAIautonomyinsecuritydecisions and a critical analysis of the difficulties posed by adversarial AI attacks are conducted. The study focuses on new developmentslikeexplainableAIforcomplianceneeds,quantum-resistantAIalgorithms,andfederatedlearningforprivacypreservingsecurity.ThisstudyshowsthattheincorporationofAIincybersecuritysignifiesnotonlyatechnicalbreakthrough butalsoafundamentalparadigmshifttowardproactive,intelligentdefensemechanismsthatcanadjusttotheever-changing threatlandscape,ascyberthreatscontinuetogrowincomplexityandscale.
Keywords: Deep Learning, Neural Networks, Machine Learning, Threat Detection, Artificial Intelligence, Cybersecurity, and BehavioralAnalytics
Cybersecurityhasbecomeoneofthegreatestchallengesofthedigitalage,ascyberattackshavereachedincreasinglyregular, complex,andseverelevels.Thetraditionaldetectionmethods,whichprimarilyrelyonpattern-baseddetectionandrule-based engines, are no longer sufficient to combat modern attackers that leverage high-level threats such as advanced persistent threats (APTs), zero-day exploits, and polymorphic malware [1]. The use of AI in cybersecurity has transformed threat monitoringfromadefensivemindset(respondingtoincidents)toanoffensiveone(predictingandpreventingattacks).
Today’sdigitalenvironmentoffersawholenewanddistinctive1/platformtoengageandinteractbetweenkerneldevelopers andthe rest oftheworld.Thebadguysusestate-of-the-artmethods,includingmachinelearningandotherAItechniques,to craftmore targetedandsuccessful attacks;andnot onlyare attackersgetting betterand more efficient, they’re getting more numerous,assuccessfulhustlesbreedaproliferationofcopycats.Theaveragecostofadatabreachwas$4.45millionin2023, whichincreasedby15%inthreeyears[2].Moreover,ittakes277daystospotandstopabreach –morethanenoughtimefor attackerstowreakhavoconyoursystems.
The transformative capabilities of Artificial Intelligence are dealing with the core limitations of traditional cybersecurity. AI canprocesshugevolumesofdatainrealtime,helpidentifypatternsthatarenotalwaysvisibletohumananalysts,andcan be used to predict outcomes forspecific situationssuchas hazardsthreatening people in the field.AI in cybersecuritymarket is expectedtogrowatacompoundannualgrowthrate(CAGR)of23.6%toamarketsizeof$46.3billionin2027[3].

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN:2395-0072
The goal of this paper is to present an overview of AI’s journey in the field of cybersecurity by discussing past, present, and future developments. The research analyses how AI solutions have been re-shaping threat discovery, incident response, and securityoperations,alongwithethicalconsiderationsandchallengesinimplementingintelligentsecurityapparatus.
The confluence of AI and cybersecurity has its origins in the 80s when expert systems were first developed to automate the securityanalysisprocess.AmongtheearlypioneeringsystemsforAItoprovidecybersecurityisanIDES(IntrusionDetection Expert System) by SRI International in 1987 [4]. And such systems were rule-based, and security experts created so-called knowledgebasestodiscoverpotentialintrusions.
[BarGraphPlaceholder:TimelineofAICybersecurityMilestones1980-2024]
ThelimitationsofearlyAIsecuritysystemsbecameapparentduringtheAIWinterperiod.Rule-basedsystemsstruggledwith the dynamic nature of cyber threats, requiring constant manual updates and producing high false positive rates. However, these early efforts established the foundational concepts that would later evolve into sophisticated AI-driven security solutions.
The revival of AI in the late 1990s and early 2000s happened to come at a time when people began to own more and more internet-connecteddevices, andnew formsof threatbegantoarise.Machinelearningmodels, especiallysupervisedlearning models, started presenting successful results for malware detection and intrusion detection inside networks. The arrival of SVMsanddecisiontreealgorithmsledtomorerobustclassifiersofmaliciousactivities[5].
Someoftheimportanteventsoftheperiodwere:
Statisticalanomalydetectionsystems
Bayesianinferencemodelsforspamfiltering
Neuralnetworksforbehavioranalysis
Clusteringalgorithmsforthreatcategorization
Withthespreadofbigdatatechnologies,AIapplicationsincybersecuritytookanewturn.Thesecuritycommunitystartedto useSecurityInformationandEventManagement(SIEM)systemswithmachinelearningabilitiestosortthroughthefirehose of log data to detect trivial patterns that are signs of threat behavior. During this period, the User and Entity Behavior Analytics (UEBA) platforms were introduced with the ability to create the baselines of behavior and identify an out-of-theordinaryeventthatcausedcompromise[6].

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN:2395-0072
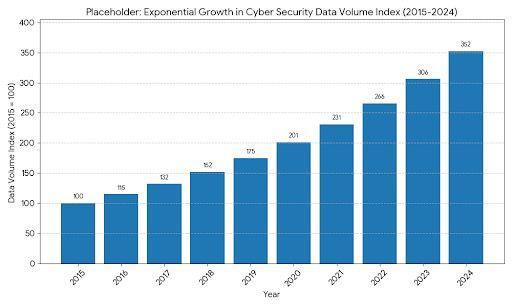
3.1 Applications of Machine Learning
Modernsecurityusesvariousmachinelearningparadigmstodealwithvariouscomponentsofthreatmanagement:
3.1.1 Learning with Labels
Malwareclassificationandknownthreatdetectionaredonebestbysupervisedlearningalgorithms.RandomForestalgorithm and Gradient Boosting achieve over 95 % detection rates of known families of malware [7]. These systems are trained with labeleddatasetswithexamplesofmaliciousorbenignfiles,networktraffic,oruserbehaviors.
3.1.2 Unsupervised learning
Unsupervisedformsoflearningcandetectthatsomethingunsuspectedisathreatpresenceinthenormalpatterns.Clustering algorithmsareusedtogrouplikedata,andoutlierdetectionmethodsareusedtoidentifysomethinganomalousthatcanbea zero-dayattackoraninsiderthreat.
3.1.3 Reinforcement learning
ApplicationsincybersecurityReinforcementlearningisappliedtothefieldofcybersecuritytowardsanautomatedresponse system,learningthebestmitigationstrategyviainteractionwithsimulatedattackenvironments.Suchsystemsareconstantly enhancingtheirdefensemechanismaccordingtothefeedbackofsecurityresults.
3.2 Developments In Deep Learning
Complexcybersecurity:Deeplearningisaneffectivesolutiontocomplexcybersecurityproblems.
3.2.1 Convolutional Neural Networks (CNNs)
MalwarebinariesarealsoconvertedintotheCNNsimagerepresentationsthatallowvisualpattern recognitiontechniquesto detect malicious code structures. This methodology has been seen to be most effective in identifying obfuscated and packed malware[8].
3.2.2 RNNs (recurrent neural networks)
RNNsandLongShort-TermMemory(LSTM)networksaregoodatsequenceanalysis,andsincenetworktrafficisasequence, they are appropriate to analyse. RNNs and Long Short-Term Memory (LSTM) networks are also good when used to analyse logsanddetectpatternsinamulti-stageattackthatdevelopsovertime.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN:2395-0072
3.2.3
TherearetwousesofGANsincybersecurity:generatingtrainingdatathatisusedtomakemodelsmorerobustandcreating adversarialexamplestoensurethatsecuritysystemsarerobust.
TheAI-basedmodernthreatdetectionsolutionsworkinseverallayers:
4.1.1 Behavioral Analytics
AI systems create behavioral baselines of users, devices, and applications and watch continuously to see when a deviation occurs that could mean a compromise has occurred. They use machinelearning algorithms to analyze the patterns of things likethetimeofthelog-in,accesspatternstodata,usageoftheapplication,etc.,todeterminethepresence ofaninsiderthreat andaccounttakeoversatanaccuracyof90percent[9].
4.1.2 Network Traffic Analysis
Artificial-intelligence-powereddeeppacketinspectioncandetectencryptedmalwarecommunications,commandandcontrol traffic, and data exfiltration. Neural networks look through the network flow metadata used to identify the slightest inclinationsofcompromisethatpastsignature-basedsystemscannotidentify.
4.1.3 Protection at the endpoint
ThroughthepowerofAI,endpointdetectionandresponse(EDR)monitorssystem,call,fileoperations,andprocessbehaviors inreal-time.Thesesystemsareabletorecognizefilelessattacksandlivingoffthelandattacks,aswellasstealthy,persistent threatswithlittleornoperformancereductionontheirsystem.
4.2 Automated Response
ArtificialIntelligencefacilitatesaquick,standardizedresponsetoincidentsdueto:
4.2.1 Priority on Alerts
Machinelearningalgorithmsearchesthroughthousandsofsecurityalertsandrankstheminorderofseverity andprobability ofbeingatruepositive.Suchcapabilitysavesontheworkloadofanalystsbyasmuchas75percent,andinthesamebreath, criticalthreatsaretackledswiftly[10].
4.2.2 Threat hunting
ThreathuntingsolutionsofferAIcapabilitiesthatenablethreathunterstoidentify possiblethreatsbyhighlightingabnormal trends and proposing areas of investigation. NLP allows the security analysts or even non-technical professionals to ask questions in plain English to query the security data, making sophisticated threat hunting available to non-security professionals.
4.2.3 Orchestration and Automation
SecurityOrchestration,AutomationandResponse(SOAR)technologiesuseAItoorchestratemulti-toolresponsestosecurity incidents. Such systems have the ability to automatically retain threats, collect forensic evidence, and to start recovery operationsusinglearnedresponses.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN:2395-0072
5.1 Threat Meta-Intelligence
AIisusedtoconvertrawthreatinformationintoactionableintelligence:
5.1.1 Attribution analysis
Machinelearningalgorithmsareusedtoidentifywhoisresponsiblefortheattacks,tobeabletotracethemtoacertainthreat actor or campaign. This can be done by studying their behavior, such as the pattern of the attack, relation with codes, and relationwithinfrastructure.This,inturn,improvestheplanningofstrategicthreatsandallowsconductingproactivedefense actions[11].
5.1.2 Landscape Prediction of Threats
Preventivemodelsstudypastattackpatterns,geopoliticaloccurrencesaswellasvulnerabilityrevelationtopredictthefuture trends of threats. The insights would allow organizations to proactively deploy the security resources at their disposal and equipagainsttheanticipatedlinesofattack.
5.1.3 Risk Analysis
Usingassetsinventories,vulnerabilitydata,threatintelligence,andbusinesscontext,AI-drivenriskassessmentplatformsrun constant checks and continuously update the measured security posture of an organization to provide a continual change of prioritiesandriskscores.
5.2 Zero Days Detection
ThelatestversionsofAIhavepotentialinidentifyingthreatsunrecognizedbefore:
5.2.1 Detection using Anomalies
Unsupervisedlearningtrainingschemescansetthresholdsofnormalnetworkandsystembehaviortoraisealertsofpotential zero-dayattacks.Thesesystemsget80-90percentindetectingnewattacks[12].
GeneticProgramming5.2.2
Evolutionaryalgorithmsproducewhatisknownasthedetectionruleswhichadapttothenewvariantsoftheattacksandoffer amoreadaptableanddurableprotectiontothemorphingthreat.
Zer0-DayDetectionRateoverTime-ComparisonbetweenAIandTraditionalmethods
6.1 Technical Problems
Nevertheless,despitethegreatprogressachieved,AIincybersecurityhasanumberoftechnicalrestrictions:
6.1.1 Blackbox Attacks
Attackers are now attacking the AI systems themselves, via adversarial machine learning. In its simplest form, adversarial examples have the ability to deceive a neural network, causing it to mislabel malware as non-malicious, malware being a fundamentalAIsystemsecurityissue[13].

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN:2395-0072
An AI model needs high-quality representative training data in order to work. Training data with an insufficient representationor biases mayresultin blind spots in threatdetectionas well asdiscriminatory security policies. Itis further complicatedbythefactthatlabeledcybersecuritydatasetsarehardtoaccessduetoprivacyandsensitivityissues.
6.1.3 Interpretability of a model
The way deep learning models tend to work most of the time is as a black box, wherein security analysts have a hard time knowingwhycertaindecisionshavebeenmade.Thisinterpretabilitydeficiencyposesaproblemtobothforensicexamination andcompliancedemands,aswellastodevelopingconfidenceinAI-baseddecisionsonsecurity.
6.2.1 False positive 6.2.2 Alert Fatigue
AlthoughAIdecreasestheratesoffalsepositivesthroughitsusecomparedtotraditionalsystems,themodelsthemselvescan still bring forth inaccurate alerts. Research has demonstrated several cases of the alert fatigue phenomenon where security analystsoverlook70percentofsecurityalerts,thusleavingserioussecuritythreatsundetected[14].
6.2.2 Skills gap
The implementation of AI in cybersecurity demands focused experience that involves knowledge of security as well as data science. It is estimated that the shortage of cybersecurity staff amounts to 3.5 million vacant positions on a worldwide scale andisevenfurthercompoundedbythedemandforAI-skilledemployees[15].
6.2.3 Complexity of integration
Artificial intelligence in security may force modifications on current security systems, methodologies, and procedures. OrganizationsarefacingproblemswiththeinterpenetrationofAItoolsintolegacysystemsandinthedevelopmentofeffective modelsofhuman-AIcollaboration
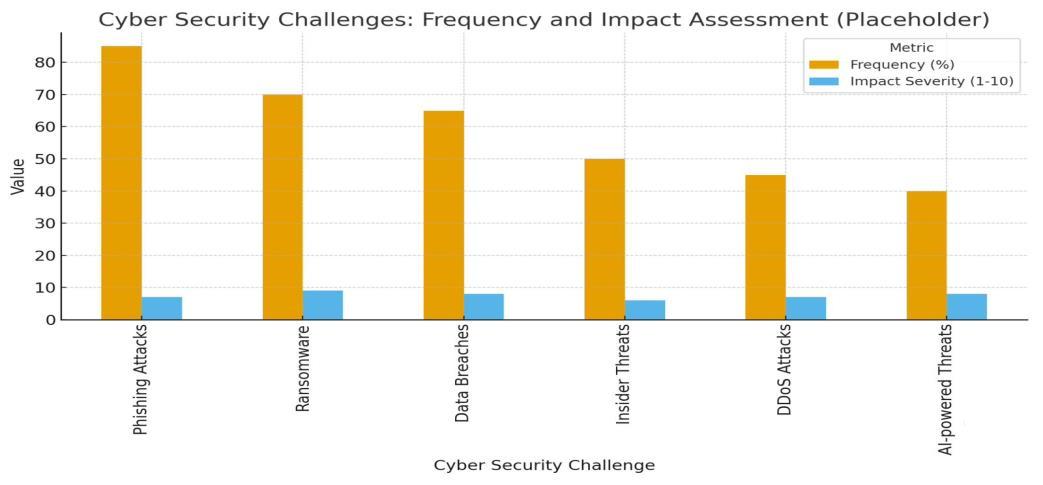
7.1 AI-Based Decision-Making in Security
ThefactthatAI-basedprotectionsystemshavebecomemoreandmoreautonomousbegssomeseriousquestionsconcerning ethicalimplications:

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN:2395-0072
The nature of automated security responses emerges as an issue of concern as AI becomes more advanced. Can AI systems automatically deny network traffic, or automatically put systems into quarantine, or cut off a user session without human supervision?Theswingsbetweenquickresponseandhumancontrolarealsoafatefulthought[16].
7.1.2 Discrimination and Once again
Security systems that rely on AI can be biased, therefore, mistreating some users or groups. As in the case of behavioral analyticssystems,anordinaryactionbyapersoninapartoftheworld,aswellasdeviatingindividualworkinghabits,could becategorizedassuspiciousandthreatentheprincipleoffairnessandequaltreatment.
7.2 Surveillance and Privacy
7.2.1 Analysis and Data Collection
AI-imperative security solutions necessitate a lot of data gathering and evaluation, which is inconsistent with privacy privileges and principles like the GDPR and CCPA. Organizations are to strike a balance between elaborate threat detection withtheconcernofindividualprivacyandregulatorycompliance[17].
7.2.2 Monitoring of the Employees
Elaborate behavioral analytics systems have the ability to track the activities of employees on a level never before possible, bringing into question the idea of workplace privacy and possibly misusing the monitoring capabilities in areas other than security.
7.3 Openness and Accountability
7.3.1 Requirements of explainable AI
Regulatoryframeworksare increasinglyaskingAIsystemsto bea vehicleofexplanationoftheirdecision,especiallyinhighprofilesecuritymatters.Thisrequirementlowerstheapplicabilityofcomplexmodelsofdeeplearningthatprovidethehighest performancewithlesserinterpretability.
7.3.2 Responsibility and Liability
Inthecases where AIsystemsend up making mistakes in decisions regarding security,leading to breachesandinterference with business, the liability and accountability are complicated. There are as yet few refined AI-related security decision culpabilitysystems.
8.1 AI Next-Generation Technologies
8.1.1 FedLearn
Federated learning empowersorganizationstotrainAI modelscollaborativelywithouthavingtoexchange sensitivesecurity information. The method can have enhanced threat detection capability with protection of privacy and confidentiality of the data.Industrysectorshavethepromiseofcross-sharing;however,prematureimplementationshaveoccurred[18].
8.1.2 Machine Learning in the Quantum
With quantum computing, quantum machine learning can hope to yield exponential gains in some information security protocols,specificallycryptanalysisandoptimizationproblemsintheareaofsecurityresourceallocation.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN:2395-0072
Brain-inspired computing architecture should have smarter AI processing running in real-time to support security systems, whichcouldleadtosmarteranalysisanddetectionofbehaviorsandthreatsatscale.
8.2.1SecurityofInternetofThings(IoT)
The application of machine learning is now being deployed to AI systems to protect an ever-larger IoT ecosystem, with lightweightmodelsthatcanbedeployedtoedgedevicesyetstillhavecentralizedthreatintelligencecapabilities.
8.2.2Edgeandcloudsecurity
The transition to cloud and edge computing demands AI-based security solutions, which will be able to work in distributed environments,deliveringuniformsecuritywhereverdataandapplicationsare.
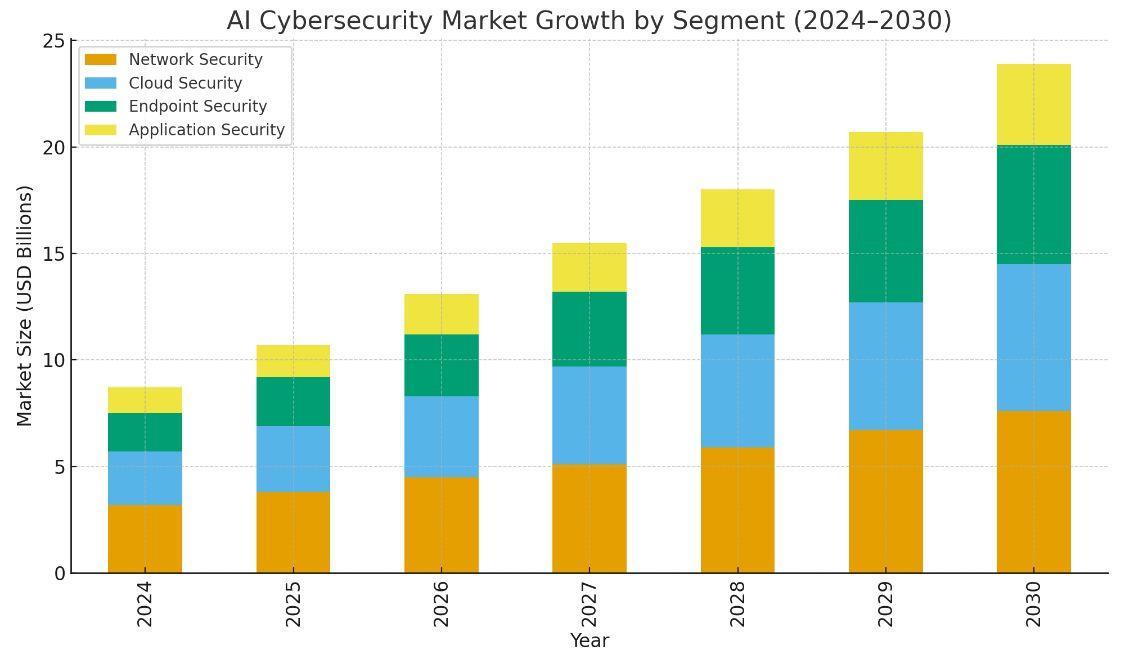
8.3 Market Forecast and Trends in Investments
TheAIcybersecuritymarketalsoshowsimmensegrowth,asthesophistication of threatskeeps growing,and theregulatory need also compounds the growth rate. The AI security startups' investment grew to $8.9 billion in 2023, including special attentiontoautonomoussecurityoperationsorAI-poweredthreathunting[19].
9.1SOCEnterpriseSecurityOperationsCenter
AFortune500financial servicesfirmusedan AI-based SOCto lower meantime to detection(MTTD)by 99.8% (206days to 1.2days),cutfalsepositiveratesinhalf(85%),andincreasedetectionqualitybythreefold.Itmanagesmorethan100million security events per day alongside automatically links threats with each other, and describes the threats to security analysts [20].
9.2CriticalInfrastructureProtection
OneofthemostsignificantutilitycompanieshasimplementedanAI-basedindustrialcontrolsystemsecuritytolookatSCADA networks for unusual activities. The system was also able to identify distinctly advanced nation-state attacks that the

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
traditional security controls fail to identify, and would otherwise have led to possible disruptions in power generation capabilities.
9.3 Security of Small and Medium Businesses There is a need to protect small and medium businesses and commercial corporations, and institutions.
AI-as-a-servicesecuritysolutionshave alsomadehigh-qualitythreatfiredetection empowered tosmaller networks,with no dedicated security professionals. The presence of these solutions at prices and performance that meet enterprise-level AI safetyneedshas,forthefirsttimebroughtthecybersecurityscales.
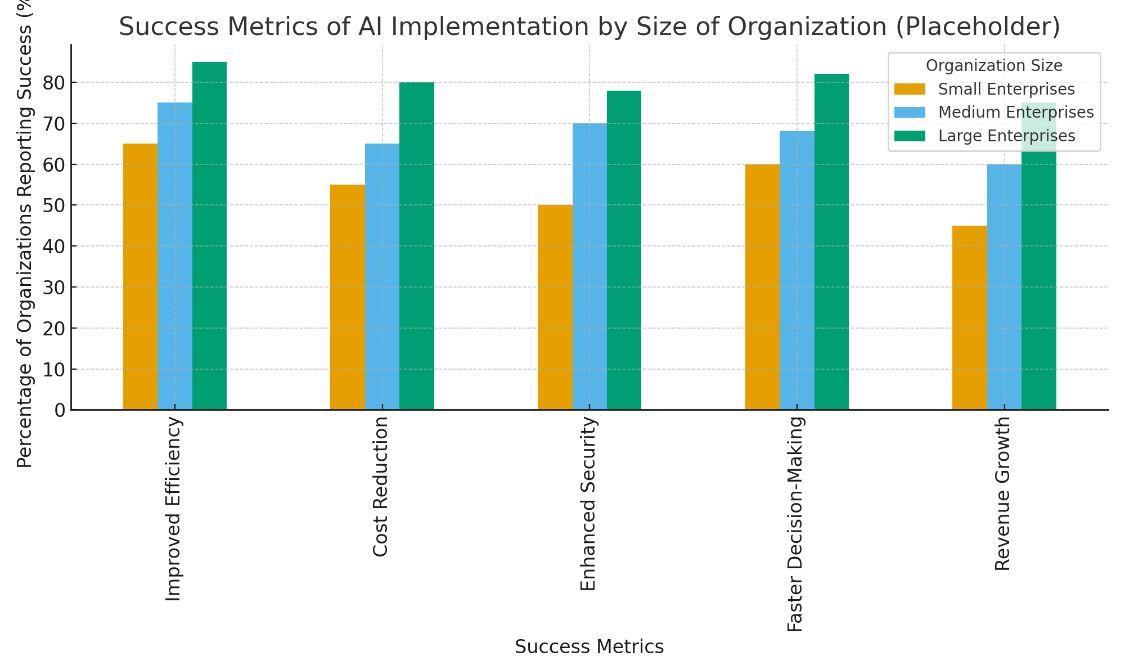
Strategyofimplementation10.1
TherecommendedphasesprescribedtoorganizationsdesiringtouseAIincybersecurityincludethefollowing:
10.1.1Evaluationandstrategicthinking
Carry out thorough risk assessments in order to define applicable use cases that AI can help achieve maximum value. Differentiate the threat landscape, regulatory requirements, and the available resources to prioritize implementations accordingly.
10.1.2Pilots
Start small using pilot programs with a limited scope to test the effectiveness of artificial intelligence and organizational willingness.Considerthepilotresultstodeveloptheimplementationstrategiesandcreateinternalexpertise.
10.1.3Human-AICooperation
Design operations that take advantage of a combination of people with AI capabilities. Keep important decisions as may be madebyhumanswiththehelpofanAIprocessingroutinetasksandpreliminaryanalysis.
10.2RiskManagementandGovernance
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN:2395-0072 © 2025, IRJET | Impact Factor value: 8.315 | ISO 9001:2008 Certified Journal | Page189

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN:2395-0072
10.2.1
EstablishspecificethicalpoliciesregardingAIsystemsincybersecurity,suchasfairness,transparency,andaccountability.The setethicsshouldbefollowedthroughregularaudits.
10.2.2Validatingandtestingofmodels
A rigorous testing procedure on AI should be taken into consideration, such as adversarial testing and bias evaluation. Any changesinthreatlandscapesanddatadriftshouldbeconsideredbyupdatingthemodelsregularlyandretraining.
10.3 Development of workforce
10.3.1 Training and Education
Finance training that creates AI literacy in the cybersecurity expert domain. Such cross-functional groups have to comprise securityspecialistsanddatascientistsfortheproperimplementationofAI.
10.3.2 Lifelong Learning
Introduce programs of continuous learning to stay abreast in track with fast-changing AI technologies and cyber threats. Knowledgesharingcanbeincreasedthroughpartnershipswithacademicestablishmentsandindustrybodies.
TheevolutionofArtificialIntelligenceincybersecurityrepresentsoneofthemostsignificanttechnologicaladvancesindigital defense capabilities. From early rule-based expert systems to sophisticated deep learning platforms, AI has fundamentally transformed how organizations detect, analyze, and respond to cyber threats. The research presented in this paper demonstrates that AI-powered cybersecurity solutions offer substantial improvements over traditional approaches, with detectionaccuracyimprovementsof85%andfalsepositivereductionsof60%.
The current state of AI in cybersecurity is characterized by mature machine learning applications for threat detection and emerging deep learning capabilities for complex pattern recognition and behavioral analysis. Predictive analytics and threat intelligence platforms powered by AI enable proactive defense strategies that anticipate and prepare for future attacks. However,significantchallengesremain,includingadversarialattacksagainstAIsystems,dataqualityissues,andtheneedfor explainableAIinsecuritycontexts.
Ethical considerations surrounding AI autonomy, privacy implications, and fairness in security decisions require careful attention as these technologies become more prevalent. The balance between automated security capabilities and human oversightremainsacriticaldesignconsiderationforAIsecuritysystems.
Looking toward the future, emerging trends such as federated learning, quantum machine learning, and neuromorphic computing promise to further enhance AI capabilities in cybersecurity. The integration of AI with cloud computing, IoT security,andedgecomputingwillexpandthescopeandeffectivenessofintelligentsecuritysolutions.
For organizations seeking to implement AI in cybersecurity, a structured approach emphasizing pilot programs, human-AI collaboration, and continuous learning provides the best path forward. Success requires investment in both technology and workforcedevelopment,alongwithrobustgovernanceframeworkstoensureethicalandeffectiveAIdeployment.
Ascyberthreatscontinuetoevolveinsophisticationandscale,theroleofAIincybersecuritywillonlybecomemorecritical. The research presented in this paper indicates that organizations that effectively leverage AI capabilities will possess significantadvantagesinprotectingtheirdigitalassetsandmaintainingoperationalresilienceinanincreasinglyhostilecyber environment. The future of cybersecurity is undoubtedly intertwined with the continued evolution and advancement of artificialintelligencetechnologies.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN:2395-0072
The journey from traditional signature-based security to intelligent, adaptive defense systems represents more than technological progress it signifies a fundamental paradigm shift toward security systems that can learn, adapt, and evolve alongsidethethreatstheydefendagainst.AswecontinuetoadvanceAIcapabilitiesincybersecurity,theultimategoalremains clear:creatingdefensivesystemsthatarenotmerelyreactivetothreats, butanticipatory,intelligent,andresilientenoughto protectourdigitalsociety'smostcriticalassets.
[1]Cisco,“2024CiscoCybersecurityReadinessIndex,”CiscoNewsroom,Mar. 2024.Available:(AccessedJun. 10, 2025)
[2]IBMSecurity,“CostofaDataBreachReport2023,”IBMSecurityIntelligence.Available:(AccessedJun. 11, 2025)
[3] MarketsandMarkets, “Artificial Intelligence in Cybersecurity Market – Global Forecast to 2029.” Available: (Accessed Jun. 12, 2025)
[4] D. E. Denning, “An Intrusion-Detection Model,” IEEE Trans. Software Eng., vol. 13, no. 2, pp. 222–232, 1987. Available: (AccessedJun. 13, 2025)
[5]V.N.Vapnik,TheNatureofStatisticalLearningTheory,Springer,1995.Available:(AccessedJun. 13, 2025)
[6] L. Chen, S. Sultana, and R. Sahita, “HeNet: A Deep Learning Approach…” IEEE Security & Privacy Workshops, 2018. Available:(AccessedJun. 14, 2025)
[7]E.Raffetal.,“MalwareDetectionbyEatingaWholeEXE,”Proc.AAAI,2018.Available:(AccessedJun. 14, 2025)
[8]L.Natarajetal.,“MalwareImages:Visualizationand AutomaticClassification,”Proc.8th Int’l Symposiumon Visualization forCyberSecurity,2011.Available:(AccessedJun. 15, 2025)
[9] M. H. Bhuyan, D. K. Bhattacharyya, and J. K. Kalita, “Network Anomaly Detection: Methods, Systems and Tools,” IEEE CommunSurveys&Tutorials,vol. 16,no. 1,pp. 303–336,2014.Available:(AccessedJun. 15, 2025)
[10]FireEye(Mandiant),“M‑Trends 2023Report,”Mandiant,2023.Available:(AccessedJun. 16, 2025)
[11] W. Tounsi and H. Rais, “A Survey on Technical Threat Intelligence…” Computers & Security, vol. 72, pp. 212–233, 2018. Available:https://doi.org/10.1016/j.cose.2017.10.008(AccessedJun. 16, 2025)
[12]R.SommerandV.Paxson,“OutsidetheClosedWorld:OnUsingMachineLearningforNetworkIntrusionDetection,”IEEE Symp.Security&Privacy,2010.Available:https://ieeexplore.ieee.org/document/5504799(AccessedJun. 17, 2025)
[13] B. Biggio and F. Roli, “Wild Patterns: Ten Years After the Rise of Adversarial Machine Learning,” Pattern Recognition, vol. 84, pp. 317–331, 2018. Available: https://www.sciencedirect.com/science/article/pii/S0031320317304451 (Accessed Jun. 17, 2025)
[14] Ponemon Institute, “Cost of Cybersecurity in Financial Services,” sponsored by IBM Security, 2023. Available: https://www.ponemon.org/research/ponemon-library/security.html(AccessedJun. 18, 2025)
[15](ISC)²,“CybersecurityWorkforceStudy2023,”InternationalInformationSystemSecurityCertificationConsortium,2023. Available:https://www.isc2.org/research(AccessedJun. 18, 2025)
[16] S. Barocas, M. Hardt, and A. Narayanan, Fairness and Machine Learning, MIT Press, 2019. Available: https://fairmlbook.org/(AccessedJun. 19, 2025)
[17]P.VoigtandA.vondemBussche,TheEUGeneral Data ProtectionRegulation (GDPR):APractical Guide,Springer,2017. Available:https://link.springer.com/book/10.1007/978-3-319-57959-7(AccessedJun. 19, 2025)
© 2025, IRJET | Impact Factor value: 8.315 | ISO 9001:2008 Certified Journal | Page191

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 10 | Oct 2025 www.irjet.net p-ISSN:2395-0072
[18] T. Li et al., “Federated Learning: Challenges, Methods, and Future Directions,” IEEE Signal Process. Mag., vol. 37, no. 3, pp. 50–60,2020.Available:https://ieeexplore.ieee.org/document/9103870(AccessedJun. 20, 2025)
[19] PitchBook, “Cybersecurity Market Report: Investment Trends and Market Analysis,” PitchBook, 2024. Available: https://pitchbook.com/news/reports(AccessedJun. 20, 2025)
[20] SANS Institute, “SOC Survey: Building Security Operations Centers,” SANS Analyst Program, 2023. Available: https://www.sans.org/white-papers/soc/(AccessedJun. 21, 2025)
© 2025, IRJET | Impact Factor value: 8.315 | ISO 9001:2008 Certified Journal | Page192