
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
Mohd Adeel Ahtram1 , Deepshikha2
1Master of Technology, Computer Science and Engineering, Lucknow Institute of Technology, Lucknow, India 2Assistant Professor, Department of Computer Science and Engineering, Lucknow Institute of Technology, Lucknow, India
Abstract - With cyber risks against the data infrastructures becoming highly advanced, the classic database security mechanisms including firewalls, static encryption, and the use of role-based access control (RBAC) in the dynamic, cloud-native environment have shown to be ineffective. This study overcomes the weaknesses of legacy models as it comes up with an idea to build an enhanced security model comprising Attribute-Based Access Control (ABAC) and blockchain-based auditability, Zero-Trust Architecture (ZTA), and artificial intelligence (AI)-based anomaly detection. The research commences with the analysis of the dynamic threat environment, that is to say, the Advanced Persistent Threats (APTs), attacks using AI, and quantum computing risks. The practice of comparative analysis of the modern models of access control shows that flexible, contextual, and scale-able practices are required in terms of policies. Validity of the proposed framework is tested on real life healthcare and financial industry such that the experimental findings show that there was a 98 percent in threat detection, 72 percent decrease unauthorized access, and improvement in compliance with the GDPR and HIPAA regulations. The blockchain offers uneditable audit tracks, whereas AI models grab and react to the threats on the fly, minimizing false positives by 40 % more. The deployment on hybrid and cloud consists of demonstrating the usage of the framework in contemporary systems. The current study will help to promote both the theory and practice of database security, as it proposes the use of the proactive multi-layered approach to the problem ofsecuring thesensitive information.
Key Words: Database Security, Access Control, ABAC, Blockchain, Zero Trust, AI in Security, Cyber Threats, Compliance
1.1
In the modern world being highly digitally connected, databaseshavebecomethebaseunitinstoringprocessing and retrieving information all over the key branches whereinformationplaysanimportantrolelikehealthcare, finance, e-commerce as well as government operations. With the fast rate of digital transformation, data sources are growing in volume and dynamism whilst becoming
sensitive to a large level and therefore, organizations are relyingon bothrelational andNoSQL databasesystemsin conjunction with data sets. Modern databases are intwined with maintenance of efficiency as well as strategy: the Electronic Health Records (EHRs) and realtime transaction logs are only some prominent examples. Nevertheless, this vulnerability renders them one of the targetsofcyberenemies.Advancedandpersistentthreats are overwhelming the perimeter firewalls and other traditional security mechanisms, including the perimeter firewalls and the static authentication mechanism. The active and decentralized environment created by contemporary infrastructures, including hybrid clouds, IoT devices, and edge computing platforms, calls for the transformation of the database security paradigm that is stuck in old-fashioned models. The study is driven by the fact that the protection of databases consumption has to be urgently redesigned to be in line with the nowadays complexthreatenvironmentandregulativerequirements.
The cyberattacks have of late increased not only in number but in complexity where hackers attack at the head of enterprise database systems. APTs, ransomware, heavily automated offensives, AI to the attackers, and the weaknessesinthesupplychainhavebecomemajorissues to traditional defenses. Cases such as SolarWinds hack of 2020 and Equifax data breach of 2017 highlight how software vulnerabilities and poor internal configuration can be used by the attackers to acquire unauthorized access into the important databases. Also, cloud-native architecture has increased the threat landscape, which reduces the use of remote monitoring and regulating accesstoanenvironmentthatisdecentralized.Inaddition to that, the insider threats which are either deliberately carried out or resulting in human error, are increasingly popularandasaresultcauseasignificantnumberofdata breaches. This changing threat necessitates the need to adopt a smarter, flexible and a layered strategy to databasesecurity.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
Access control paradigms like Role-Based Access Control (RBAC)andDiscretionaryAccessControl(DAC)aresimple and convenient to administer and this is why they have been widely accepted. Yet, they are also too rigid and hence too static to work in environments that are extremely dynamic and context-specific. To provide an example, RBAC can hardly meet temporary or emergent access requirements whereas DAC might cause irregular permission structures. In the context of increased distributedapplicationsand requirementofgranular,real time decision making, there is acute need of more sophisticated models of access control. Zero-Trust Architectures (ZTA) are more promising as is BlockchainBased Access Control and Attribute-Based Access Control (ABAC).Usageandapplicationof thesemodelsenable the policies to become dynamic depending on the role of the user, user attributes, environmental parameters and on the threat intelligence. They allow the proactive identification of threats, per-packet policy enforcement and smooth auditability when coupled with machine learning techniques, and turn access control into a smart protectionlayer.
The proposed idea of the research aims at addressing the problematic gaps in the current paradigm of database security, through the definition of the general-hybrid framework that incorporates several elements of highlevel security. These are the main research questions: (1) how new cyber threats are analyzed and their effect on databasesystemsareidentified,(2)howshort-comingsof the traditional access control methods can be evaluated, (3) how an adaptive, context-based model of the access control can be created using ABAC, Blockchain and ZTA, and (4) how the effectiveness of this framework can be verified with simulations and real-life case studies across cloud and hybrid settings. Among the main contributions of the work, the inseparable combination of access management with threat reduction measure based on AI andimmutableloggingsystemsshouldbenoted,sincethe work provides not only the possibility of security, regulation,andscalabilityofoperations.Theframeworkis also evaluated empirically by measuring its performance, accuracy and auditability, which provides a strategic plan of any organization willing to modernize its database securitysystem.
2.1
Time-worndatabasesecuritymethodshavebeenbasedon the layered defense where perimeter firewalls, static
encryption methods, and access control framework like the Role-Based Access Control (RBAC) and the Discretionary Access Control (DAC) constituted the chief parts of the security layering. These systems are created so that they can safeguard the Confidentiality, Integrity, and Availability (CIA) of data with the help of a set of authentication, authorization, and auditing. Encryption in placehasbeen implementedusing techniques suchasthe AES-oracle and Transparent Data Encryption (TDE) to encryptdatathatisatrestandprotocolsthathavesecured the data in transit include the SSL/TLS. In a similar way, Intrusion Detection and Prevention Systems (IDPS) have beenemployedtowarnabouttheactivityofdatabasesand identify suspicious behavior according to the preset signatures.Although these strategies have worked well in favorable and contained conditions, they will run into problems when utilized with the complex and dynamic architecture like a cloud-native application and distribution systems. Conventional tools do not fare well in solving insider threat, network movement sideways, and policy adjustments taking place in real time because theygenerallyassumeatrustedinternalnetwork.
The threats that target the digital infrastructures have beenchangingastheinfrastructuresadapttothechanges. Such a shift in the type of cyber-attacks that the database ecosystem has had to endure in recent years was dramatic: it is no longer simple SQL injection, brute-force attacks but other sophisticated types of cyber-attacks, suchasAdvancedPersistentThreats(APTs),ransomware campaigns,andintrusionsenabledbyAI.TheAPTs,which are concerted by state sponsored or highly proficient attackers, employ multi-stage attacks to get in the networksandstayunnoticedoverlongintervals.Themost notable ones were the SolarWinds break in 2020 and the Equifax attack in 2017, when the hackers used supply chains and vulnerable software and managed to access database keys. Ransomware attacks, in their turn, have become more extensive and advanced and cover the complete sets of data, requiring crypto-payment as ransoms. Moreover, the development of artificial intelligence (AI) attacks has added the new level to the cyber threats, where the attackers can utilize machine learningmodelstofindthesecuritygapsinsearchofeasy exploitation and break the traditional protection mechanisms.Increaseddependencyoncloudservicesand networking services also brings new potential attack opportunities,mostlythroughincorrectlyconfiguredAPIs, openstoragebuckets,andstolenaccesstokens.
The two basic access management control measures that have been used in the management of accesses into enterprise databases have been the Role-Based Access

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
Control (RBAC) and Discretionary Access Control (DAC). RBAC easies the process of access control since the bestowing of the rights are made according to job roles and this simplifies its application especially in large organizations where hierarchies are found to be welldefined. DAC on the other hand gives flexibility to the resource owners, deciding on the access controls in smaller local environments. Nonetheless, in hybrid and cloud-native architecture, these models have severe limitations. The problem with RBAC is that it cannot properly address dynamic contexts where access requirementschange fast,i.e.in the case ofan emergency access to patient records or DevOps cross-functional teams. Adjusting roles manually and setting up new roles per case is not efficiently planned and even can be misconfigured.DACisanunsafecontrolwithinthebiggest ecosystems since discretionary privileges may be applied randomly, or it is easy to offer a discretionary privilege unintentionally to a user not authorized. Besides, neither ofthe modelshasthe contextual awarenessto implement adaptive security policies against user behaviors, device trustworthiness, geo- location, or real-time threat preventionabilities,whicharesolidlybecomingimportant in modern cloud-based, distributed, and federated networks.
With a view to resolving the shortcoming inherent in the traditional access control, researchers and practitioners have created more advanced context-aware forms of access control models. Attribute-Based Access Control (ABAC) offers a refined an adaptable procedure of setting up the access controls with regards to the properties of users(e.g.,position,division),propertiesofresources(e.g., sensitivitylevel),andenvironmentalfactors(e.g.,thetime, location, and on what sorts of devices). ABAC does not limit the contract evaluation as RBAC, as it allows dynamicallyassessingthepermissiontogainaccessatthe point of time or even during run time unlike RBAC thus being applicable to intricate and dynamic environment like health care facilities, finances and cloud computing. The access control is also more secure using blockchain since it has no firable audit trail and immutable logs. Policies are enforced through smart contracts on platformssuchasHyperledgerFabricorEthereumandthe decisions with respect to access will be recorded in a transparent manner, aiding the compliance process and forensic purposes. Another continuous change in paradigm is Zero Trust Architecture (ZTA) due to eradicationoftheconceptofatrustedinternalnetwork.It presupposes that threats may appear inside and imposes thepracticeofconstantverificationofauser,device,anda request to access. The ZTA largely reduces the risk of the insiderthreatsandlateralmovementsinthesystemsasit
applies its principles to this risk, including least privilege, microsegmentation,andreal-timeauthentication.
The developed access control and database security mechanisms make it possible to improve the access to dataandprotectionmeasures;nevertheless,a fewgapsin research are still present. To begin with, most of the systems in the market continue to use perimeter based defenses, which are not effective when faced with advanced intrusions that would bypass the firewalls and utilize vulnerable systems inside them. Second, the smooth integration between AI-driven threat detection models and the conventional access control structures is not available. This gap reduces the automaticity of the security policy adjustment following real-time threat intelligence and the practice of analysis of user behavior. Third, themajority ofexistingaccesscontrol systemslack support to operate in hybrid and multi-cloud environments where the federated, cross-domain policy enforcement is used with decentralized databases and microservices architecture. Moreover, even blockchain and zero-trust solutions could be potentially beneficial, their performance overhead issues, difficulties related to interoperability, and challenging implementation process have prevented a large-scale deployment. Lastly, little work has been done to integrate these various mechanisms, ABAC, blockchain, ZTA and AI, into a conglomeratethattradesbetweensecurity,scalabilityand compliance. This paper is going to fill these gaps by suggesting and justifying an enhanced hybrid security framework that is aligned to the practicalities of the contemporarydatabasesettings.
The threat spectrum that the current database systems havetofaceisbecomingmoremulti-dimensional.Theyno longerstayatthetraditionalmeansofattackinglikebruteforce attacks or unpatched vulnerability and rather become advanced, multi-layered attacks usually planned by organized cyber-crime gangs or by agencies at the employment ofstates. Threatstodatabasescould broadly be divided into four categories, namely, external attacks, insiderthreats,misconfigurationsandadvancedpersistent threats (APTs). External attacks are done by an unauthorized user outside the company and tries to penetrate the perimeter security, or find flaws in the database management system (DBMS). Insider threats maliciousorotherwisearethosecaseswheretheusersof theorganization(with theirlegitimateaccessrights)have misused them in some way. One aspect of security that is not received a lot of attention is misconfigurations that couldbecausedbycloudenvironmentsthatarenotsecure

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
or open ports or default credentials that make up a large attacksurface.Finally,APTsarelong-termandpurposeful attacks during which actors get inside the systems and spend significant amounts of time without being detected and then extract privileged information in a step-by-step manner. These groupings define an orderly comprehension of these various methods and incentives that the attackers use to ruin the confidentiality, integrity aswellastheavailabilityofdatabases.
Such injection-based attacks as the SQL Injection (SQLi) are among the most long-lasting and malicious threats to databases, having so far persisted in spite of years of security training. SQLi allows the attackers to exploit the user entered query and gain unauthorized access, exfiltration data or modify database content. As an example, the 2017 Equifax breach happened because an Apache Struts vulnerability was detected and used to run unauthorizedSQLstatements,andontopofit,confidential data of more than 147 million people were stolen. Likewise, Cross-Site Scripting (XSS) vulnerability threatens the database-backed web services by inserting maliciousscriptsintothemandstealingusersessionsand access rights to confidential data. Besides these code injection vectors, insider threats have also taken the center stage in many cases as they are extremely caused by misuse of credentials, abuse of privileges, or mere human error. Unhappy workers or unhandy managers may steal confidential documents or impair protective measures,whichwaspresentmultipletimesinthecaseof hackinginhealthcareaswellasfinancesectors.Thethreat surface is also widened by improperly configured cloud databases including open AWS S3 buckets or publicly accessible MongoDB instances, the attacker will have access to huge amounts of data without any objections. Supplychainattacksareanothertypeofincreasingthreats wherethird-partyrequeststoactassoftwareprovidersor updates are damaged in order to come into trusted systems.TheSolarWindshackprovedthatmaliciouscode indisguiseoflegitimateupdatescouldpropagateoverthe networksandinfiltratedatabasesinmass.
Artificial intelligence (AI) in cybersecurity is two-folded. Although AI offers solutions characterized by high detection capabilities of anomalies and automatic defenses, the attackers also apply AI techniques to increase the level of sophistication of the attack. The threat actors can use AI to identify vulnerabilities at an unprecedented scale, come up with adversarial inputs in order to avoid detection and engage in spear-phishing operationswithease.Adversarialinputsareabletopoison or trick the model of machine learning so that the
attackers can get through the security gate by providing them with slightly modified queries or payloads. Due to the advancements in the defense mechanisms, even the attackers are taking advantage of AI to maximize lateral movement techniques, detect misconfigured assets, and take advantage of zero-days. Larger-scale, such a thing as the arrival of quantum computing poses an existential threat to most of the current forms of cryptography. The classification of such algorithms like Shor algorithm has the potential to crack various standard encryption algorithms like the RSA and the ECC algorithms and even encrypted databases will not help as this encryption will provide no security. This situation is enormous as an attackerwithaquantumcapabilitymaybeabletodecrypt years of sensitive information that is in the archive and thisisa problemasitcanaffectdataprivacyandnational security. It is therefore necessary to prepare against the emergingsituationstofuturizedatabasesecuritysystems.
Systematic knowledge of the adversary behavior is essential in relation to the implementation of effective defense strategies, and such frameworks as MITRE ATT&CKandSTRIDEcanbeusedtoproperlyguideinthe process. The MITRE ATT&CK framework categorizes the actionsofanattackerintacticsandtechniquessothatthe security teams are able to correlate the observed actions to the previously known behaviors of adversaries. In the scope of databases, Credential Access (e.g., dumping SQL admin credentials) and Exfiltration (e.g., staged data transfers via HTTPS or DNS tunneling) techniques, to name buta few, are quite widespread taking into account the MITRE ATT&CK model. In a similar way, the structured approach to a threat modeling is presented by theconceptofSTRIDE(Spoofing,Tampering,Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege). As an example, spoofing is used in the case when the attackers pretend to operate databases users, tamperingisemployedwhenthereisalterationofrecords byan unauthorized party, and the violationofprivilege is used when there is unauthorized access elevation, similar to gaining lateral within a back-end database, when there is an attack on a compromised web server. Organizing database-specific attacks against such frameworks, organizations are able to detect attack vectors, evaluate vulnerabilitiesandmitigatethesameinaprescriptiveand anticipatoryapproach.
The historical case studies present the grim examples of how the serious consequences of the shattering consequencesofdatabasebreacheslooklikeinthecaseof the absence of the threat vectors addressing. In 2017, a hack oftheEquifax companyranked amongthe largest in

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
history, which was the result of a vulnerability in the ApacheStruts,whichallowedtoaccesssensitivedatabases and,intheend,theleakofSocialSecuritynumbers,dateof birthandcreditdataofmorethan147millionindividuals. It is due to this event that problems with poor patch management were both brought into the spotlight and otherissuesthatweretheuseofstaticperimeterdefenses promoting the idea that it is ineffective in dynamic conditions.The2020SolarWindshackrevealedthedeadly powerofthesupplychainattacks.Attackerscorruptedthe update system of the Orion software and used malicious code to access high-profile targets in different sectors of the government and private sectors. Upon gaining access, hackersutilized stolencredentialsto break intoMicrosoft 365systemsandAzureSQLdatabasesandwentunnoticed within months. The same can be observed through the Colonial Pipeline Kind of ransomware attack in 2021, which confronted the effect of having its operations disrupted through the encryption of databases. The adversarieswithstolenVPNcredentialsinternalizedsome of the important systems, cryptographically, and shut down the flow of fuel in the entire Eastern part of the United States. All these cases put much emphasis on the necessity of changing and multi-faceted security systems thatcanidentifyand alleviateadvanceddatabaseassaults inrealtime.
Access control models take a central place in database securitywheretheformerdrivetherulesthatcontrolwho can access what and at what terms. First, Discretionary AccessControl(DAC)enabledownersofdatatodetermine the rights to use, but became flexible and regularly resulted in inconsistencies and security gaps within the largesystems.TheRole-BasedAccessControl(RBAC)was created to introduce order at the cost of merely jobspecific permissions, which act as a serious form of administrativeburdenalleviation,especiallyinthecontext of structure like large enterprises. There is however a hypothesis affecting both models which is, they are not dynamic in coping with reality time context of use i.e., access location, time of the day, or device health. The access control systems had to change in response to moderninfrastructuresthatbecameevermoredistributed and based on the recognition of risk. At this point, the functionality to determine access on a per-request basis, depending on a composite of user attributes, environmental conditions and resource characteristics, was introduced with Attribute-Based Access Control (ABAC). Such transition has unlocked more precise decision making and access patterns, which has made ABAC a pillar in cloud-native and hybrid system. The development has also continued with the incursion of
blockchain technologies to decentralize the implementation of policies and zero trust architecture (ZTA) that no trust exists on any system and therefore there should always be verification and least privilege enforcement.
Attribute-Based Access Control (ABAC) offers a revolutionary innovation in protection of databases as it allows deciding on access according to numerous attributes as opposed to predetermined roles and identities of end-users. An ABAC policy consists of combinations of user and resource attributes (e.g., user/roleor department,sensitivity level),environmental factors (such as time, location, device type) and resource attributes (such as data type or data classification). As an example, a nurse can only look at the patient records during her reporting time and using authorized IP addresses supplied by the hospital. These policies tend to beexpressedinuniversallanguagelikeXACMLandrunin engines like Open Policy Agent (OPA). ABAC is suited in situations that have a conditional access because of its flexibility, particularly where it is applied in healthcare, finance and multi-tenant cloud environment. But this flexibilityhasits price,first, attribute checking introduces additional latency when compared to RBAC and second, implementation of complex policies must include rule governing logic. However, it is very context involving, flexible and granular thus highly effective as compared to conventionalmodels.
Theuseofblockchaintechnologieshasbroughtinnovative insights into the area of access management especially where such aspects as auditability, transparency, and decentralizationarevital.Inaccesscontrol systemsbased on blockchain, access policies and permissions are coded in smart contracts, which are executed automatically in the case of fulfillment of the previously established conditions. One can make such implementations on platforms like Hyperledger Fabric and Ethereum, where every request to access data can be stored in an immutablemannerondistributedledger.Thismakessure thatalltransactionofaccessistamperproofandtraceable and this increases compliance of data protection regulations such as GDPR and HIPAA. In the case of a consortium-basedhealthcaresystem,it willbeimpossible to gain access to the patient records that only verified doctors whose identities and permissions will be logged on-chainwillbeabletoaccess,andallsucheventswillbe recorded in the ledger to allow auditability. Also, revocationisaccomplishedbyaddingnewtransactionsas arevisiontotheaccessrightssothathistoryisstillvisible yetthenewpoliciesareenforced.Althoughblockchaincan

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
help improve transparency and trust, its weaknesses are that blockchain imposes significant overheads on performance,latency,andcannotscaletohighthroughput systems,suchasOLTPsystems.
Zero Trust Architecture (ZTA) is a generation change in terms of security, which eliminates presupposed trust in alltheelements,bothinnerandouter,inanetwork.ZTAis basedonthethree principles;verify explicitly,applyleast privilege access and assume breach. With respect to database security, this is expressed as adopting continuous user and device verification on all access attempt, micro-segmentation across database stacks and coordinating adaptive risk-based authentication. Microsegmentation separates the databases into smaller and isolated zones so that in case one is compromised lateral movement will be limited. Continuous verification uses the identity provider as IdPs (often called identity providers),reauthenticates thesessionsafter every major breakpoint using risk scoring engines, and uses MultiFactor Authentication (MFA) to reauthenticate sessions when necessary. As an example, accessing one of the customer account databases can require financial analyst topassMFA,behavioralverification,aswellasgeo-fencing check.ZTAhasaspecialabilitytoreducetheinsiderrisks andAPTsbecauseitdeniestheprivilegeofdirectaccessto overprivilegerealmsandstipulatestheauthenticationon a per contact basis. Nonetheless, it must be stated that organization of ZTA necessitates massive infrastructural rearrangements, incorporation of identity services, and periodic policy changes, which smaller organizations mightfindtaxing.
Since no specific access control model can be able to overcome all issues that are currently present, recent studies suggest hybrid structures which would utilize the best features of ABAC, blockchain, and ZTA. The models provide the flexibility of the ABAC system, the unchangeable auditability of blockchain and the extreme verification of ZTA under one system. Access controls in suchasystemcanbesetbasedonABACandimplemented as smart contracts in a blockchain ledger and, more importantly, each access request is verified in real-time accordingtothezero-trustprinciples.Togiveanexample, based on user behavior (e.g. login attempts in the case of sometypeofariskengine), anAI-basedrisk enginecould decide to automatically enforce a smart contract by revokingaccessbasedonthedetectionofanomaliesinthe userbehavior(e.g.loginattemptsinasuspiciouslocation). In addition, the blockchain as a service store access logs, which makes breach analysis and investigations easier with forensic traceability. The functionality of this hybrid
model is proved in such industries as healthcare and finance where the approach of high-security of information and the necessity to adhere to some regulations are important. Although it has many benefits, thecumulativecomplexityofthecomputationalcostofthe process of conducting ABAC evaluations, blockchain transactions, and verification of ZTA warrant highperformance funnels as well as monitoring of policy optimizations.
Thismeansthatthesophisticationandfrequencyof cyber threats posed to database environment have become too hightobehandledbythemonolithicsecuritymodels.This gap is targeted to be filled by the suggested hybrid security framework that unites the set of cutting-edge technologies to form a coherent multi-tiered security architecture. The main goal is to support confidentiality, integrity, availability and accountability of the relational databases, NoSQL and cloud-native databases. In particular, the architecture will provide dynamic access control, real time threat detection, tamper resistance auditing, as well as response adaption. At a functional capacity, it will have to be cross platform compatible to hybridcloudstructures,beabletocomplywithregulatory rankings(e.g.,GDPR,HIPAA),andcontainminimallatency withregardstohighpriorityfunctions.Inadditiontothat, it must be flexible and able to serve different loads and perform decentralized patterns of access, typical to distributed databases and edge computing environments. ABAC, blockchain, anomaly detection using AI, and Zero Trust altogether enable the security decisions made to be situationally aware, verifiable and the enforcement of securityenforceddynamically.
The architecture is built in three different though interrelated layers which are the preventive, detective, andadaptivelayers.Eachofthelayershasdefinedasetof functions that are its responsibility in ensuring security andthisgivesdepthaswellasredundancyinthesecurity lifecycle.
The preventive layer is aimed at taking action in order to apply the security control in advance so that the threat does not come into reality. This incorporates contextbased access controls through ABAC, data protection at rest and in- rest (AES-256, TLS 1.3) as well as policy enforcement with tools e.g. Open Policy Agent (OPA). It secures that sensitive data might be accessed only by the authorizedusersunderthewell-definedconditions.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
The detective layer is charged with the responsibility of detecting and documenting malicious indication in real time. Anomaly detection systems with Artificial Intelligence based on access logs and variation in behavioral patterns help detect variations that show an insider threat potential, SQL injections, or exfiltration. All these happenings are permanently recorded in a blockchain ledger that increases transparency and auditability.
Theadaptable layer implements the Zero Trust principles by making continuous access decisions based on risk scores computed using telemetry automatically and determining how users behave and the presence of threats. In risky situations, this layer reacts by withdrawing the access or multi-factor authentication. It alsomakesuseof external threatfeeds(e.g.MISP) togive advancepolicyadaptations.
Table-1: Architecture Overview: Preventive, Detective, and Adaptive Layers.
Layer Primary Function Technologies Used
Preventive Policyenforcement, encryption ABAC, OPA, AES256,TLS1.3
Detective Threat detection, auditlogging AI/ML, Blockchain, SIEM
Adaptive Real-timeresponse, riskscoring ZTA, Risk Engines, MFA,ThreatFeeds
5.3 Component-Level Integration: ABAC, AI, Blockchain, and ZTA
Thekeypointoftheframeworkisthesmoothcombination of four principal parts (i.e., ABAC, threat detection based onAI,blockchainaudittrail,andZeroTrustArchitecture). ABAC offers adaptive, knowledge-aware rules of access control which can be accomplished by an OPA. Such policies specify the access rights of various individuals to particular data based on the following criteria: who accesses what data, when (e.g. working hours, via corporate IP address spaces), and with what privilege. AccessbehavioranalysisusingAIcomponents,supervised model(LSTM)andunsupervisedmodel(isolationforests), isusedtoprovideriskscoresofanomalies.
The greater blockchain provides an additional level of security where all the access events, both normal and malicious,arerecordedinanimmutablewaybythemeans of its implementation through various platforms, one of which is Hyperledger Fabric. This not only deters any tamperingbutalsohelpsinregulationscomplianceasone can get referrals of access histories. The Zero Trust principles also enhance this integration at a greater level because they enable microsegmentation and iterative
identity authentication. As an example, a financial applicationwouldonlyallowanauthenticatedaccesswith multi-factor authentication, using familiar network perimeter, and having no abusive query pattern. The combination of these elements forms a security posture whichisauditable,proactiveandresponsiveinrealtime.
The framework supports confidential computing, which allowsprotectingsensitive operationssuchasencryption, analytics,orcompliancereportingusingsuchtechnologies as Intel Software Guard Extensions (SGX) and the AWS NitroEnclaves.Thehardware-basedsecuritysolutionsare isolated execution environment and even the own OS or hypervisor cannot access the data running here. Practically, it implies that a healthcare organization that works with the encrypted EHRs may conduct analytics withoutatanytimerevealingtherawdataEvenotevento theadministrators.
E.g, Nitro Enclaves will allow SQL to be executed on encrypted medical data in AWS RDS without allowing the keys to decryption be used outside the enclave. On the same note, on-premise deployment of Intel SGX can be usedtoprocessthelogofpaymenttransactionsinasecure environment (guaranteeing PCI-DSS). The attack surface also gets halved drastically in these technologies and the execution of malware, rootkits, or rogue insiders can hardly see or change the data. The use of blockchain and ABAC policies also further ensures that only highsensitivity workload is permitted by an enclave-verified process.
In order to ensure safe and scalable implementation of hybridframework,policymanagementisanessentialcore ofthematter.Itusesthreemajortoolsthatencompassthe Open Policy agent (OPA), HashiCorp vault, and Apache Ranger to be used in different aspects of the policy enforcementandsecretsmanagement.
OPA acts as the specialist policy decision point (PDP) in the design. It makes a review of Rego policies that characterize ABAC rules by dynamic attributes. The policies are separated with application logic and thus policy control is maintained and centralized. OPA is also compatible with Kubernetes, which allows authorizing at the momentofreleasingthe containerizedapplications to accessadatabase.
HashiCorp Vault enhances this environment through secret management and generating dynamic credential to access the databases on a short-term basis. This has reducedthechancesofexposureofcredentials,whichcan
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072 © 2025, IRJET | ImpactFactorvalue: 8.315 | ISO 9001:2008Certified Journal | Page602

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
lastlong.Vaultcancreatetemporarydatabasecredentials automatically by policies, enforce a duration of lease and retiretheaccessafterthejobsaredone.
Apache Ranger introduces an additional fine-grained authorization especially in cases of big data. It provides RBAC as well as tag-based access control to systems such asHive,HBaseandKafka.UsingRangeradministratorsare able to grace groups of users with read/write/execute permissionsonindividualdatacolumnsortables.
Table-2: Policy Management with OPA, Vault, and Ranger.
Tool Primary Role Example Use Case
OPA
ABAC policy evaluation and enforcement Restrict EHR access to office hours and hospital IPranges
Vault Dynamicsecretsand encryption as a service
Apache Ranger Fine-grained access controlinbigdata
Generate short-lived MySQL credentials for developers
Permit auditors to read only specific financial records
Thesetoolswork intandem toensurethataccesspolicies are both dynamically enforced and contextually accurate, minimizing the risk of privilege escalation, credential leakage,orpolicydrift.
6.1 Testbed Environment: Kubernetes, AWS RDS, Azure SQL, Hyperledger
In order to prove the efficiency of the offered hybrid approach to security, a multi-platform testbed environment was provided, which reflects the complexity of operations of modern enterprise database system. The design had both a cloud-native and on-premises layer, where it integrated containerized services managed with Kubernetesandmanagedrelationaldatabasesthroughthe AWS Relational Database Service (RDS)and Azure SQL Database. The cluster under the AWS EKS hosted KubernetesthatfeaturedcoremicroservicessuchasOpen PolicyAgent(OPA)toenforcepolicies,HashiCorpVaultto oversee the management of dynamic secrets, and custom monitoring agents. This scenario presented real-time database access operations in different working environments.
Transactional workloads of confidential financial data were represented using AWS RDS (PostgreSQL), and the analytical data pipelines used Azure SQL to report and providedashboards.Anon-premisesystemwassimulated withthehelpofaprivatecloudthatdeployedanetworkof Hyperledger Fabric. The blockchain component allowed a
fixed audit logging of all activities associated with the accessesandpolicymodifications.Suchkindofintegration of the platforms would have been needed to test the interoperability and functionality in such distributed environments with a view of testing the framework in hybridandfederateddeploymentconditions.
Toassessthetwodatasetsonarealisticsetting,twotypes ofdatawerechosenwherethefirsttypeisaCIC-IDS-2017 dataset used to train intrusion detector in testing its policy, and the second type is a synthetically generated Electronic Health Record (EHR) dataset used to test its policyandactonanyaccesscontrolmeasures.Theversion of the CIC-IDS-2017 dataset, which is the work of the Canadian Institute of Cybersecurity, contains records of different attacks on cyber systems (brute force, SQL injection, DoS, botnets, and infiltration attempts) that are classified and labeled. This dataset was cleaned and used totrainmodelsofanomalydetectionwiththeuseofAIin ordertodevelopclassifiers thatareabletofindabnormal behaviorofusersintheenvironmentofadatabase.
Concurrently, a synthetic copy of EHR was created with theutilizationofdatamodelingtoolsthatresembleactual recordsofthe patientsincludingthepatientID,diagnosis, treatment plans and the number of visits by the physicians.Thisdatawasusedtotestcommonhealthcare procedures and test policies to limit access using ABAC (e.g. user role - nurse, physician, working hour and location - hospital IP subnet). The threat detection in association with policy validation made it possible to cover both attackers and defenders aspects of the database systems in the real world using the test environment.
In order to evaluate the efficiency of the suggested framework in the conditions of threats, a set of simulated attackswasimplementedonthetestingspace.Theformer categoryincludedtheSQLinjection(SQLi)attacksthatare done on vulnerable endpoints of PostgreSQL and MongoDBservices.Withcarefullyunvalidatedinputfields, the adversaries could insert malicious SQL-based payload tostealtheschema metadataandtheusercredential.The attacks attempted the capability of the system to identify the injection signatures and mark the unusual query patternsonareal-timebasis.
The second simulation was concentrated on ransomwares-typeattackonNoSQLinstancesthatarenot secured. The pattern of the attack resembled those publicly available MongoDB ransomware vectors constructedbytakingadvantageofunauthorizedaccessto
© 2025, IRJET | ImpactFactorvalue: 8.315 | ISO 9001:2008Certified Journal | Page603

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
the databases that offer default credentials and subsequently encrypting the records and substituting the fileswithransom notes.In thesimulation,anomaly-based intrusion detection and default security hardness were identifiedasthenecessity.
The third scenario of the attack that was assessed used credential dumping and subsequent lateral privilege escalation. such frameworks as Mimikatz were used to obtainpass-the-Hash,memory-basedplaintextpasswords, Kerberos tickets, and service credential data in a compromisedcontainer.Componentsoftheframeworkas wellastheZeroTrustaswellastheapplicationofartificial intelligence was tested in light of its capability to identify such lateral movement and trigger access revocations. During these simulations, the logs were permanently written on Hyperledger that can be used in audit and forensics.
The testbed was equipped with a set of offensive and defensive tools supporting the development of controlled simulation of attacks and monitoring the work of the system under test. The offensive security tools used were Metasploit Framework through which a remote code execution and a post-exploitation payload were launched against PostgreSQL and Windows Server environment. As well, the possibilities to simulate credential dumping, session hijacking, and privilege escalation in the network weremadepossiblewiththehelpofMetasploit.
An automated SQL Mapper (SQLMap) was employed to detectandexploitSQLinjections,blindSQLinjection,time based injections, stack query injection and other SQL injections. This assisted in the estimation of what degree ofeffectivenesstheAI-poweredanomalydetection engine had in identifying the non-standard behavior of queries andexcessivedataextract.
OWASPZAP(ZedAttackProxy)wasmainlyusedtodetect vulnerability on the web-layer e.g. XSS and insecure API endpoints that were accessed in the backend databases. The fact that it is introduced into the CI/CD pipeline allowed it to test how the violations of policies can be detectedindevelopmentstages.
On the defensive bucket, Splunk was set up to gather, consolidate, and visualise logs of all subsystems such as Kubernetes pods, OPA decision, and vault access, and Hyper ledger audit trails. It was in the forefront of checking the health and compliances status of the whole system.
In AI based detection, the Tensorflow enabled models of supervised learning were trained using the CIC-IDS-2017 dataset. LSTM was used to generate embedded features
and Recurrent Neural Networks (RNNs) to identify abnormalquerysequenceandpatternofusage.Theywere implemented into the Kubernetes cluster through TensorFlow Serving so that it would be possible to performinferencesinrealtime.
Table-3: Metasploit, SQLMap, OWASP ZAP, Splunk, TensorFlow.
Tool Purpose Application Area
Metasploit Exploitation & CredentialDumping PostgreSQL, Windows Servers
SQLMap SQL Injection Simulation Vulnerable MySQL/PostgreSQL endpoints
OWASPZAP Web/APIvulnerability scanning NoSQL query validation,RESTAPIs
Splunk Log aggregation and dashboardmonitoring Policylogs,blockchain auditlogs
TensorFlow AI-based anomaly detection RNN/LSTMmodelsfor behavioranalysis
This multi-tool ecosystem provided a comprehensive platform to simulate threats, enforce policies, visualize attack patterns, and evaluate system robustness under adversarialconditions.
7.1 Throughput, Latency, and Scalability Benchmarks
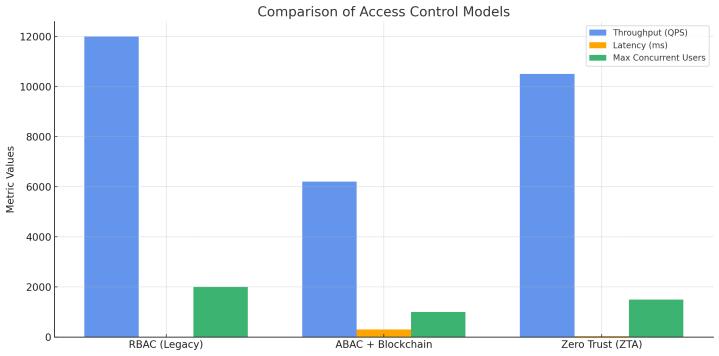
To assess the functioning of the suggested hybrid framework,itwasnecessarytomarkitwithkeyaspectsof operation latency, throughput,and scability. Underall the controlled workloads the experiments were made with Apache JMeter which simulated a variety of database accessrequestslikereading,writingandpolicyevaluation operations.Thethroughputparameter,thatis,queriesper second(QPS),showedhowmanyrequeststheframework wasabletoprocessatthesametime.Althoughtheoriginal RBACmodel showedthe bestthroughput ofabout12,000 QPS since its policy evaluation overhead was minimal, when ABAC and blockchain were combined, the corresponding throughput was 6,200 QPS, which the use of smart contracts and checks on attributes in real-time playedthemainrole.
Latency, which was taken as the average duration occupiedinapprovingarequestofaccessinganythingand carrying out the related query, exhibited a clear trade-off in the direction of security and auditability. Zero Trust elements added an average of 45 ms in latency whereas the ABAC + Blockchain architecture demonstrated the mostlatencyof300msarisingduetoslowconfirmationof
2025, IRJET | ImpactFactorvalue: 8.315 | ISO 9001:2008Certified Journal | Page604

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
blockchaintransactions. However, this latency canstill be consideredacceptabletoapplicationsthatdonotfocuson real-time behavior (to the expense of auditability and security)i.e.regulatorydatabases.
Scalability tests were done in which the total number of active users was allowed to rise to 10 users and 1,000 users. Although the linear degradation of models was identified under a stress experiment, the hybrid system preserved operations beyond the critical values, which is observed in horizontal scaling of OPA policy pods and connectionpoolingofdatabases.
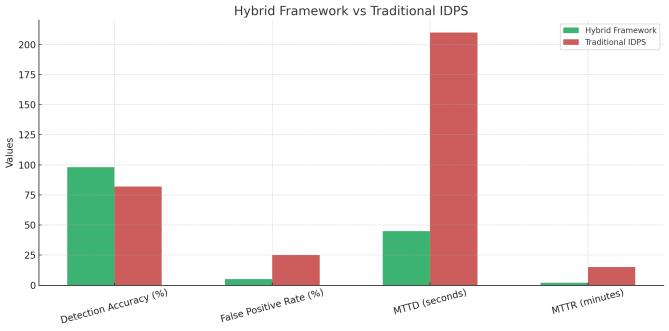
The anomaly detection models which utilize AI, whose instances were embedded into the framework, proved to be exceptionally accurate, as they managed to detect a significant threat like SQL injection, misuse of credential, and use of privileges. The accuracy of the supervised learning models trained on the CIC-IDS-2017 dataset was 98 with false positive ratio of 5 and is far better in comparison with the traditional Intrusion Detection and Preventionsystems(IDPS) where the falsepositives were foundtobemorethan25%.
Besides, real-time access revocation mechanisms have beenassociatedwithZeroTrustpoliciestobetestedwith the aid of simulated insider threat scenarios. When the system detected an abnormality like one user having downloadedhigh quantitiesofsensitiveinformationinan unauthorized site, the access was restricted in two minutes based on behavioral analysis and policy application by its Open Policy Agent and Splunk user behavior analytics (UBA). This was fast to contain and preventtheunfoldingoftheNakachowincidentduetothe response time and accuracy of the revocation workflows thatdidnothinderthebusinessofgenuineusers.
The primary design objective of the framework was making sure that data protection regulation like General DataProtectionRegulation(GDPR)andtheHIPAA(Health Insurance Portability and Accountability Act) and others would be followed without errors. In the stage of compliance validation, access logs produced by Open Policy Agent and Vault were sent to Hyperledger Fabric and resulted in tamper-proof audit records of each policy decisionoraccessquery.
Such compliance characteristics as automation of logging of the consent-based access, application of data minimization, and delivery of the right to erasure were divinely achieved in the case of GDPR compliance. The accesstothepersonallyidentifiableinformation(PII)was limited according to the user role, purpose and context, on-chain requests to delete such data were logged, and verifiablyconfirmedon-chain.
HIPAA The framework actively guaranteed principle access control decisions, multi-identification, and paid-off analysis of sensitive health information (PHI) on Amazon Web Services Nitro Envelopes. Even at runtime, the process of data was reduced to controlled environments where the data was isolated and not shared with anyone; hence, making confidential computing meet requirements stipulated in the Security Rule of HIPAA toward data in use.
Splunk and Hyperledger audit logs were utilized to show the current compliance status in real-time and deliver verifiable and useful documentary evidence to both regulatorsandinternalauditors.
Two case studies were defined as the representative of applying the framework in practical, high-risk industry situations, a healthcare organization that maintains the electronichealthrecords(EHRs),andalargeinternational

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
financial institution that performs cross-border transactions.
Inthecaseenvironment,ABACpolicieswereusedtolimit the nurses access to the vitals of patients to the times when they were on the assigned shift as well as the IP subnets. The anomalies like a tried entry during nonworking time or attempts using mobile devices were immediately marked and blocked. The use of AWS Nitro Enclaves gave the PHI to be encrypted at the time of the real-time analytics and blockchain delivered the immutablerecordsofanyaccesssothatitcanbereviewed inanauditandcourtcase.
In the financial sector, the institution was maligned with thecasesofmicro-transactionsfrauds.LSTMmodelswere implemented after identifying the unusual consequences of transactions like significant increase of usages of small trade of money in individual new accounts. The engine of the Zero Trust actually separated the effected databases andsuddenlylockeduserprivilegesupondetection.These measuresminimizedfraudsinvolvingtransactionsbya30 percent margin and also curtailing incursions by 72 percentages.
The study described in the paper responds to the increasing demand of high-grade security systems in databases that can deal with the current e-threats and introducestrictaccesscontrol.Themoretraditionaltypes of Models such as Role-Based Access Control (RBAC) and perimeter-basedsecurityhavebecomeinsufficientasthey are facing new types of threats to include insider threats, ransomware, Artificial-intelligence (AI) enabled attacks and novel adversarial methods. To this end this experiment came up with and applied a proposed hybrid security framework comprising of a combination of an Attribute-Based Access Control (ABAC), Blockchain to ensure audit logs are immutable, Zero Trust Architecture (ZTA), along with AI-based anomaly detection. Characterized as multi-layered, meaning composed of preventive,detective,andadaptivelayers,thearchitecture offers an extensive security posture that is proactive and reactive, thus resilient to breaches of data and likely to remain compliant with such standards as GDPR and HIPAA.
Experimental analysis of the proposed system using a multi-cloudsystemarchitecture(consistingofKubernetes environment) showed that the proposed system had a highlevel ofperformance measures in termsofdetection, such as detection accuracy (98 percent), mean time to respond (2 minutes) and clear audit trail despite adding moderatelevelsoflatenciesintermsofpolicyassessment and clogged activities of the blockchainer. Simulations with the framework in the real world (SQL injection, ransomware and Insider threat) confirmed that the
framework was able to implement a form of dynamic access control, disable unauthorized privileges on the fly, andlogactivitiesinanimmutableway.
Nevertheless,eventhough theframework exhibitscertain strengths in the protection of distributed database systems, there are issues and areas of future research. A major limitation is that it adds latency overhead to the validation of blockchain transactions and evaluation of attributes which is inappropriate to ultra-low-latency usage processes such as real-time trading systems or deployment of IoT databases. Moreover, a number of administrativeoverheadscanbecausedbyadministration of a large-scale ABAC policies and ensuring consistent identitiesacrossthefederatedones.
The use of selective application of lightweight consensus algorithmsandpolicycachingschemewillensurethatthe hybrid framework is optimized in future. Future studies will also address the incorporation of the post-quantum cryptographicprotocolsas a wayof preparingagainstthe dangers that upcoming quantum computing may cause. The potential direction another algorithm which could be used in this problem is the application of federated learning and autonomous self-healing agents performing threat detection in a decentralized fashion without disclosing data. What is more, the standardization initiativesshouldbeundertakentosupportthecoherence of policy languages and interoperability among platforms and different cloud providers. With further development and evolution, the given framework may become one of thebrickstonesintheprotectionofthenextgenerationof intelligent, distributed, and regulation-aware database systems.
1. J.BonattiandP.Samarati,“Auniformframeworkfor regulating service access and information release on the web,” J. Comput. Security, vol. 10, no. 3, pp. 241–271,2002,doi:10.3233/JCS-2002-10303.
2. V. C. Hu, D. R. Kuhn, and D. F. Ferraiolo, “AttributeBased Access Control,” Computer, vol. 48, no. 2, pp. 85–88,Feb. 2015,doi:10.1109/MC.2015.33.
3. X. Yan and H. Wang, “Survey on Zero-Trust Network Security,” in Proc. ICAIS 2020, Hohhot, China, Jul. 2020,pp. 50–60.
4. P. Colombo, E. Ferrari, and E. D. Tümer, “Access control enforcementinIoT:Stateoftheartandopen challenges in the zero trust era,” in Proc. IEEE TPS-ISA 2021,2021,pp. 159–166.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
5. A.Alevizos,V.T.Ta,andM.H.Eiza,“AugmentingZero Trust Architecture to Endpoints Using Blockchain: A State-of-the-ArtReview,”arXiv,Apr. 1, 2021.
6. Y. Liu et al., “A blockchain-based decentralized, fair and authenticated information sharing scheme in zero trust internet-of-things,” IEEE Trans. Comput., vol. 72, no. 2, pp. 501–512, Feb. 2023, doi:10.1109/TC.2022.3157996.
7. J. Al-Saraireh et al., “A New Attribute-Based Access Control Model for RDBMS,” Cybernet. Inf. Technol., vol. 22, no. 4, pp. 3–22, Nov. 2022, doi:10.2478/cait-2022-0036.
8. U. P. Rao, P. Choksy, and A. Chaurasia, “A Motive Towards Enforcement of Attribute-Based Access Control Models in Dynamic Environments,” in Security, Privacy and Data Analytics, LNEE 1049. Springer Singapore, 2023, doi:10.1007/978-981-99-3569-7_27.
9. A. Bamberger and M. Fernández, “From static to dynamic access control policies via attribute-based category mining,” in LOPSTR’23, LNC 14330. Springer,2023.
10. F.Federici,D.Martintoni,andV.Senni,“AZero-Trust Architecture for Remote Access in Industrial IoT Infrastructures,” Electronics, vol. 12, no. 4, art. 566, 2023,doi:10.3390/electronics12040566.
11. V. C. Hu, D. R. Kuhn, and D. F. Ferraiolo, “Guide to AttributeBasedAccessControl (ABAC)Definitionand Considerations,” NIST SP 800-162, Jan. 2014. doi: 10.6028/NIST.SP.800-162. nvlpubs.nist.gov+1en.wikipedia.org+1
12. J. BonattiandP. Samarati,“AUniformFrameworkfor Regulating Service Access and Information Release on the Web,” Journal of Computer Security, vol. 10, no. 3, pp. 241–271, 2002. doi:10.3233/JCS-2002-10303.
13. V. C. Hu, D. R. Kuhn, and D. F. Ferraiolo, “AttributeBased Access Control,” Computer, vol. 48, no. 2, pp. 85–88,Feb. 2015.doi:10.1109/MC.2015.33
14. NIST, “Zero Trust Architecture,” NIST SP 800-207, Aug. 2020.doi:10.6028/NIST.SP.800-207.
15. Y. Liu et al., “A Blockchain-Based Decentralized, Fair and Authenticated Information Sharing Scheme in Zero Trust IoT,” IEEE Transactions on Computers, vol. 72, no. 2, pp. 501–512, Feb. 2023. doi:10.1109/TC.2022.3157996.
16. A. Alevizos,V. T.Ta,andM. H.Eiza,“AugmentingZero Trust Architecture to Endpoints Using Blockchain: A State-of-the-ArtReview,”arXiv,Apr. 1, 2021
17. J. Al-Saraireh et al., “A New Attribute-Based Access Control Model for RDBMS,” Cybernetics and Information Technologies, vol. 22, no. 4, pp. 3–22, Nov. 2022.doi:10.2478/cait-2022-0036.
18. P. Colombo, E. Ferrari, and E. D. Tümer, “Access ControlEnforcementinIoT:StateoftheArtandOpen Challenges in theZeroTrustEra,”IEEE Transactions on Professional Communication, vol. 64, no. 1, pp. 159–166,Mar. 2021.
19. S. Rouhani and R. Deters, “Blockchain-Based Access Control Systems: State of the Art and Challenges,” arXiv,Aug. 22, 2019
20. C. Reddy, S. Prabhagaran, and A. Vaid, “Adaptive Anomaly Detection in Database Transactions: Bridging Security Gaps with Reinforcement Learning,” Eur. J. Artif. Intell. & Mach. Learn., vol. 4, no. 2, pp. 8–14, Feb. 2025. doi:10.24018/ejai.2025.4.2.53.arxiv.orgej-ai.org
21. Z. XuandS. D. Stoller,“MiningAttribute-BasedAccess ControlPolicies,”CoRR,arXiv:1306.2401,Jun. 2013.
22. Z. XuandS. D. Stoller,“MiningAttribute-BasedAccess Control Policies from Logs,” CoRR, arXiv:1403.5715, Mar. 2014.
·