
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 08 | Aug 2025 www.irjet.net p-ISSN:2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 08 | Aug 2025 www.irjet.net p-ISSN:2395-0072
Alby Alphonsa Joseph 1, Dr. Venifa Mini G 2
1Research Scholar, Department of Computer Science and Engineering, Noorul Islam Centre for Higher Education, Tamil Nadu, India
2Assistant Professor, Department of Computer Science and Engineering, Noorul Islam Centre for Higher Education, Tamil Nadu, India***
Abstract - The integration of IoT and cloud systemsoffers advanced data services but also increases the risk of DDoS attacks. Existing methods like MLP, Random Forest, and Naive Bayes often fail to detect attacks accurately, especially in large datasets, leading to high false positives and poor service quality.
This paper presents a real-time DDoS detection algorithm using a dedicated dataset. It achieves high accuracy, low false positives, and maintains strong network connectivity, even during attacks. The algorithm handles large, fast data streams efficiently, ensuring continuous service and meeting SLA requirements.
MATLAB simulations show that the proposed method outperforms existing techniques in accuracy, reliability, and classification performance.
Key Words: DDoS Detection, Cloud Security, Machine Learning, IoT Networks, Hybrid Cloud, Traffic Analysis, AnomalyDetection,Real-TimeMitigation.
1.INTRODUCTION
Most organizations are increasingly adopting cloud computing, driven by the growth of e-commerce and internet-based trading. To optimize costs and efficiently utilize computing resources, many firms opt for a hybrid cloud model a combination of both public and private cloud infrastructures. However, hybrid and distributed cloudenvironmentsarefrequentlytargetedbyDistributed DenialofService(DDoS)attacks[1].
DDoS attacks disrupt services by overwhelming the network with excessive traffic, rendering them inaccessible to legitimate users and often resulting in significant financial losses. Before launching an attack, cybercriminals typically gain control over a large number ofcompromiseddevices.Duetoitsvastinternetfootprint and growing digital economy, India has become an attractive target for financial espionage and cybercrime. Cloud-related threatscanleadtothe loss ofcritical assets anddata.
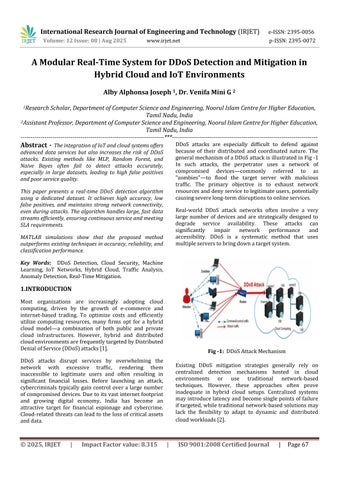
DDoS attacks are especially difficult to defend against because of their distributed and coordinated nature. The generalmechanismofaDDoSattackisillustratedinFig-1 In such attacks, the perpetrator uses a network of compromised devices commonly referred to as "zombies" to flood the target server with malicious traffic. The primary objective is to exhaust network resourcesanddenyservicetolegitimateusers,potentially causingseverelong-termdisruptionstoonlineservices.
Real-world DDoS attack networks often involve a very large number of devices and are strategically designed to degrade service availability. These attacks can significantly impair network performance and accessibility. DDoS is a systematic method that uses multipleserverstobringdownatargetsystem.
Existing DDoS mitigation strategies generally rely on centralized detection mechanisms hosted in cloud environments or use traditional network-based techniques. However, these approaches often prove inadequate in hybrid cloud setups. Centralized systems mayintroducelatencyandbecomesinglepointsoffailure iftargeted,whiletraditionalnetwork-basedsolutionsmay lack the flexibility to adapt to dynamic and distributed cloudworkloads[2].

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 08 | Aug 2025 www.irjet.net p-ISSN:2395-0072
The proposed detection model architecture is a distributed framework designed to identify and mitigate DDoS attacks across multiple layers of the network specifically, the edge, fog, and cloud layers. Each of these layers plays a distinct role in managing malicious traffic. Edge nodes function as the first line of defense by performing initial filtering of incoming data. Fog nodes carry out intermediate-level traffic analysis, while cloud nodesareresponsibleforcentralizedandcomputationally intensivemitigationtasks.
This hierarchical structure facilitates a scalable and decentralized approach to traffic processing, significantly enhancing detection accuracy. By enabling early interception of malicious traffic closer to its source, the architecturealsoreduceslatencyandacceleratesresponse times.
This architectural model is particularly well-suited for Internet of Things (IoT) environments, where computing resources are distributed across both on-premises infrastructure and cloud-based platforms. By deploying mitigation nodes at multiple layers, the model effectively distributes the workload, alleviates potential bottlenecks, and minimizes the overall impact of DDoS attacks on networkperformance.
The layered design allows each node to operate independentlyorcollaboratively,dependingonthenature and scale of the attack. This flexibility enables rapid, adaptive responses to various attack patterns and traffic volumes [3]. The decentralized framework improves system resilience, reduces latency during active attacks, and ensures the continuous availability of critical services making it an effective solution for comprehensive DDoS mitigation in hybrid cloud environments.
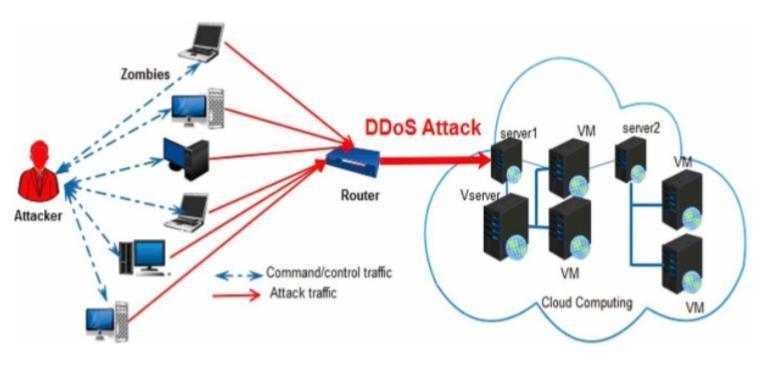
Distributed and collaborative DDoS (Distributed Denial of Service) mitigation techniques leverage a network of distributed resources and inter-organizational collaboration to enhance the detection, prevention, and responsetoDDoSattacks.
Distributed mitigation focuses on deploying multiple nodes or systems across geographically diverse locations to collectively detect and neutralize DDoS attacks. These techniques enhance resilience and reduce single points of failure.
Edge Computing: Edgenodesareusedtoprocess network trafficcloser to its source, enabling realtime detection and mitigation of malicious traffic before it reaches the core infrastructure. This approach minimizes latency and prevents congestionatcentralservers.
Traffic Analysis: Distributedmonitoringsystems are employed to examine traffic patterns across various nodes. Each node performs local traffic analysis and reports any anomalies to a centralized controller. This model enables early detection of abnormal behavior and helps in quickerresponse[4].
Load Balancing: Incoming traffic is intelligently distributed across multiple servers to prevent overloading any single resource. This ensures continued availability of services for legitimate users,evenduringanactiveDDoSattack.
Collaborative DDoS mitigation involves coordinated efforts among various entities such as organizations, Internet Service Providers (ISPs), and cloud service providers toshareinformationandpoolresourcesinthe fightagainstDDoSattacks.
Information Sharing: Acollaborativeframework can be established to facilitate the exchange of threat intelligence related to DDoS attack patterns. This may includeintegrating feeds from threatintelligenceplatformsintosystemssuchas SDMTA (Smart Distributed Mitigation and Traffic Analysis)toenhanceearlydetectionandresponse capabilities[5].
Collective Filtering: Multiple organizations can work together to filter malicious traffic at the

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 08 | Aug 2025 www.irjet.net p-ISSN:2395-0072
network perimeter before it propagates further. This can be achieved by implementing adaptive firewall rules and intrusion prevention systems that dynamically respond to shared threat intelligence.
Cloud Provider Collaboration: Partnering with cloud service providers such as Amazon Web Services (AWS) allows the use of their DDoS mitigation tools, including AWS Shield and AWS Web Application Firewall (WAF). These cloudbased protections can be integrated with onpremises systems to form a unified, robust defensestrategyagainstDDoSattacks.
3. Detection Algorithms
DDoSdetectionalgorithmsaimtoidentifymalicioustraffic byanalyzingnetworkbehaviorusingvariousapproaches. Thekeytypesareasfollows:
3.1 Statistical Analysis
Threshold-Based Detection: Setspredefined limits(e.g.,packetspersecond);raisesalerts whenlimitsareexceeded.
Statistical Tests: Uses techniques like Z-tests or Chi-square tests to detect significant deviations fromnormaltrafficpatterns.
3.2 Signature-Based Detection
Detects known attack patterns using predefined signatures.
Effectiveforknownthreatsbutlessusefulagainstnew or evolving attacks.Tools like Snort are commonly usedforthismethod.
3.3 Anomaly-Based Detection
Builds a model of normal behavior to detect unusual activity.
Machine Learning: Uses classifiers like SVM, Random Forest, or Neural Networks trained on labeleddata.
Unsupervised Learning: Uses clustering methods such as K-Means to detect outliers without labeled data, identifying suspicious patterns.
4.Proposed System Architecture for DDoS Detection and Mitigation
The proposed system is built on a modular, scalable architecture that integrates multiple components to
enablereal-timedetectionandmitigationofDDoSattacks. Thearchitectureisstructuredintofourkeylayers: Traffic Monitoring Layer, Feature Extraction and Preprocessing Layer, Attack Detection Layer, and Mitigation and Response Layer These layers work in coordination to identify anomalies in network traffic, classify them using machine learning techniques, and initiate appropriate responseactionstomitigatepotentialthreats[6].
4.1. Traffic Monitoring Layer
Thislayerisresponsibleforcapturinglivenetwork traffic using packet-sniffing tools such as Scapy. It operates passively, monitoring incoming and outgoing packets without interfering with regular network functions. It collectsdetailedpacket-levelinformationincludingsource and destination IP addresses, protocols, packet sizes, and timestamps. This non-intrusive approach ensures seamlesstrafficanalysisinreal-time.
After capturing the packets, this layer extracts relevant features such as packet rate, source and destination byte counts, protocol type, and flag sequences. The extracted data is then cleaned, normalized, and transformed to ensure it is suitable for machine learning analysis. This step includes handling missing values, outliers, and nonnumeric entries, thus improving the overall accuracy and reliabilityofthedetectionmodel.
This layer utilizes machine learning algorithms to classify network traffic as normal or malicious. The classification isbasedonpatternslearnedfromhistoricalandreal-time data. The model is continuously trained and updated, enabling it to adapt to evolving attack strategies and detect zero-day threats more effectively than static, rulebasedsystems.
Upon detection of malicious traffic, this layer takes immediate action to prevent further damage. It automatically enforces mitigation strategies such as applying firewall rules, blocking suspicious IP addresses, andrate-limitinghightrafficflows.Additionally,allattackrelated logs are stored in Firebase Firestore, which supports real-time monitoring through a Streamlit-based dashboard. This dashboard provides network administrators with visual insights into detected threats, historical trends, and real-time alerts to support swift incident response.Overall, this intelligent, layered architecture ensures efficient, adaptive defense against DDoS attacks. The integration of Firebase for real-time data storage, Streamlit for visualization, and automated

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 08 | Aug 2025 www.irjet.net p-ISSN:2395-0072
firewall actions for mitigation enables a robust, scalable solution capable of protecting modern networks from sophisticatedcyberthreats[7].
Table -1: ComparativeAnalysisofSecurityAlgorithmsfor DDoSDetection
Summary Table
Algorithm Strengths Weaknesses
Multi-Layer Perceptron Non-linear pattern learning, largedataset training
Random Forest Robustto overfitting, handleshighdimensional data
Computational lyintensive, highfalse positiverates, longerpacket analysistime
Computational lyexpensive, slowreal-time detection,high falsepositive rates
NaïveBayes Simple,fast, less computationa lresources Assumes feature independence, lower accuracy, higherfalse positive rates
DataMining Algorithms Identifies patterns,cust omizable
Results
Detection accuracy: 94.5%, false positives: 7.8%
Accuracy: 96.1%, detection delay: ~2.1s
Accuracy:8 7.2%,false positives: 10.3%
InformationTechnologies, vol. 17, no. 4, pp. 32–51, 2017.
[3] M.HaddadiandR.Beghdad,“Dos-ddos:taxonomiesof attacks, countermeasures, and well-known defense mechanisms in cloud environment,” Edpacs, vol. 57, no.5,pp.1–26,2018
[4] X. Jing, Z. Yan, X. Jiang, and W. Pedrycz, “Network traffic fusion and analysis against ddos flooding attacks with a novel reversible sketch,” Information Fusion,vol.51,pp.100–113,2019.
[5] N. Bharot, P. Verma, S. Sharma, and V. Suraparaju, “Distributed denial-of-service attack detection and mitigation using feature selection and intensive care request processing unit,” Arabian Journal for Science andEngineering,vol.43,pp.959–967,2018.
[6] N. Z. Bawany, J. A. Shamsi, and K. Salah, “Ddos attack detection and mitigation using sdn: methods, practices, and solutions,” Arabian Journal for Science andEngineering,vol.42,pp.425–441,2017.
[7] X. Qin, T. Xu, and C. Wang, “Ddos attack detection usingflowentropyandclusteringtechnique,”in2015 11th International Conference on Computational IntelligenceandSecurity(CIS),2015,pp.412–415.
Extensivedata preprocessing, high computational complexity, higherfalse
Effectiveon known attacks, struggles withnovel ones
Thedevelopedsystemoffersareal-time,scalablesolution for detecting and mitigating DDoS attacks using machine learning and cloud tools. Its modular design ensures future upgrades, making it a strong defense for IoT and enterprisenetworksagainstevolvingcyberthreats.
[1] K. Srinivasan, A. Mubarakali, A. S. Alqahtani, and A. Dinesh Kumar, “A survey on the impact of ddos attacksincloudcomputing:prevention,detectionand mitigation techniques,” in Intelligent Communication Technologies and Virtual Mobile Networks: ICICV 2019.Springer,2020,pp.252–270.
[2] W.Alosaimi,M.Zak,K.Al-Begain,R.Alroobaea,andM. Masud, “Mitigation of distributed denial of service attacks in the cloud,” Cybernetics and
© 2025, IRJET | Impact Factor value: 8.315 | ISO 9001:2008 Certified Journal | Page70