
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
Sameer Pathan1 , Sumedh Vartak2 , Yash Zagade3, Prof. Bhavesh Panchal4
123Department of Computer Engineering, Rajiv Gandhi Institute of Technology, Mumbai
4Assistant Professor, Department of Computer Engineering, Rajiv Gandhi Institute of Technology, Mumbai
ABSTRACT - As more and more common and sophisticated cyber-attacks happen, you should have a strong defence system in place to detect and respond to such threats in a quick manner. The project attempts to create a Security Operations Center (SOC) setup that is powered by a Security Information and Event Management (SIEM) system to monitor as well detect cyber threats in real time. Second, we built a simulated working environment with VirtualBox, and open-source toolslikeWazuh,Suricata,ModSecurityandDVWA(Damn Vulnerable Web Application) were installed and configured. It includes functioning as the central SIEM to collect and analyze data from different sources and reveals suspicious activity. We had then simulated common attacks such as Denial of Service (DoS), file tampering and some web-based exploits, and observed how the system detects and react to them. This hands-on setup does more than show how different security layers work together, but how important it is to have real time monitoring,loganalysisandautomatedresponsesecurity for protecting systems from such modern cyber threats.
Key Words: Cybersecurity, Virtualized SOC, SIEM, Wazuh, Denial Of Service (DOS), File Integrity Monitoring (FIM), Suricata.
Intoday’scyberawareworld,thecyberthreatshavereached new levels, and they are both frequent and sophisticated such that they could put lives and companies in grave danger.Attackersarealwaysdeprivingnewwaystoexploit the system vulnerabilities, from simple phishing scams to complexnetworkintrusions.Thegrowingthreatlandscape makesacentralizedsystemthatallowmonitoring,detecting, and responding to suspicious activities in real time is practicallyamust.
The idea of this project is to design and build a Security OperationsCentre(SOC)utilizingtheSecurityInformation and Event Management (SIEM) approach to showcase the ways in the identification and mitigation of electronic threats. Wazuh is the heart of the system; it’s a powerful opensourceSIEM toolcapableofcollectingandanalysing logs from many sources to detect potential threats. In variationalenvironment,Wazuhisdeployedasthecentral brain of the security setup with all other components workingasnecessaryfunctionality.
TheDamnVulnerableWebApplication(DVWA)isusedto simulaterealworldvulnerabilities.Thedeliberatelyinsecure webapplicationwithinthelibraryallowsthesafetestingof common attack techniques, including SQL injection and Cross Site Scripting attacks. Host DVWA to the system so thatithassomethingtomonitor,andseeliveimplicationsof attacks.
WealsoaddModSecurity,aWebApplicationFirewall,tothe setup in order to help defend against web-based threats. ModSecurity will help to block malicious traffic coming in before it reaches DVWA with the OWASP Core Rule Set enabled.So,inturningtoprotecttheirusersandtheirdata, thisisastrongfirstlineofdefenceagainstattackstowards thewebapplication.
Suricata is deployed on the network level as intrusion detectionsystem(IDS).ThisTrafficmonitoringhelpsdetect abnormalpatternsuchasscan,DDoSattempts,unauthorized accessattemptsoranyotheronthenetwork.Italsohaswell developeddeeppacketinspectioncapabilitiesthatallowitto beusefulidentifyingthreatsearlyonintheattackchain.
Another important layer that we have added as part of Wazuh’s built in sys-check feature is File Integrity Monitoring Itrecordsanychangesmadetosensitivefilesor directories particularly in the DVWA environment and hence any unauthorized modifications can be captured straightaway.
WiththeActiveResponsefeaturesofWazuhset,finally,we cansetcertainActiveResponsefeaturestotakesomeaction automatically in the event those threats are identified. Consider, for example, when Wazuh detects a brute force attack or a DoS pattern and it can temporarily block an attacker’sIPaddressbyupdatingthefirewallrulestogive theadministratortimetoinvestigateandreact.
Alltogether,thesetoolscreateamultilayered,lightweight security environment as a proof of concept for how a modern SOC canbe buildusingopen-source technologies. Suchsetupprovidesaclearandhandsonunderstandingof activitiestodetectandcountercyberthreatsrangingfrom host to the whole network By having this setup, one will haveahands-onideaabouthowtodetectandmitigatecyber threats

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
Thepaper[1]presentsacybersecuritysolutioninlinewith SIEMthatdetectsandreactstothreatsinrealtime.Suricata andSplunkareintegratedintothesystem,andtogetherwith it, the monitoring of network traffic compliance with intrusiondetection,andcompliancewithsystemeventsare enabled.Also,honeypotshelptodrawin,recordandstudy maliciousactionsforearlierthreatidentification,andfora moreoverallviewofsecuritymonitoring.
Unfortunately, the system has some drawbacks. Since the threatthatitreliesonisstaticdetectionruleswhichleadsto threats that are simple or evolved it cannot catch sophisticatedthreats.Withoutmachinelearning,thesystem has no ability to change itself to deal with new attack patterns. Also, attackers may be able to bypass honeypots andthesystemcanfightwithencryptedtrafficandcomplex obfuscationtechniques.Thislimitationsuggeststheneedfor the future implementations to have more dynamic and adaptivecharacteristics.
The paper [2] gives an example of a practical approach to building an Security Operations Center (SOC), couple with Wazuh,andasuitableFileIntegrityMonitoring(FIM)system to protect your servers. The use case that is focused on is real-time analysis of the logs, alerting and visualization to detect security threats. This is done with ELK tools (Elasticsearch, Logstash, and Kibana), and with adding features for intrusion detection, vulnerability assessment, andactiveresponse,thisisextendedwiththeWazuhsystem.
FIM adds to this and helps monitor non authorized file changeswhichensurestheintegrityofthedata withinthe system.Itcansomehowsolvetheproblemofidentifyingand reactingsuspiciousactivity,buttherearedownsides.
Itisimportanttonotethecomplexityofsettingthisupand keepingitingoodworkingorderwhenteammembersare nottechnicallysavvy.Inaddition,scalingthesystemtothe size of greater environments might result in performance troubles.Althoughpowerful,Wazuhcanalsogeneratemany falsealertsatahighrateunlessproperlytuned.Thesecond challengeisthatmostdetectionrulesarehandcreated,thus slowing responses and not having any mechanism of automaticthreatintelligence.Overallthepaperlaysagood groundworkforSOCdeploymentyetitalsosuggestspoints for improvementin termsof automationandscalabilityin cyberattackprevention.
Thepaper[3]discusseswhyithasbecomesoimportantfor SIEMsystemstohavebecomekeyinstrumentsindefending modern digital environments against sophisticated cyber threats. This enables organizations to gather and analyze securitydatafromdifferentsourcesandthencentralizeits monitoring as well as threat detection supported by these systems. Despite the importance of traditional SIEMs, the paper notes several challenges of them. The problem is processing the ‘masses’ of log data they need to process,
which can gum up performance and slow down threat detection. Often weighing in on the high side for false positives and on the low side for rapid threat pattern changes,SIEMscannotkeepup.Theycanalsobeintegrated with complex IT systems, which further reduces their efficiency. Technologies such as machine learning and automation may improve their capabilities, but such incorporationoftechnologiesbringswiththemnewissues including the increased complexity of the system, need of skilled professionals, and more resources. The study highlightsthatSIEMtoolsneedtoremainasunwaveringand asprimeaseveriftheywanttostayrelevantintheeverso progressiveworld,intermsofmodernsecurityneedsandto detectandtackleattacktrendsinrealtime.
Thepaper[4]explains thedetail SecurityInformationand Event Management (SIEM) systems approach is provided: how SIEM systems collect, normalize and analyze security data in real time. It presents log management and event correlation as components that enhance the detection of threats early and support incident response, as a part of SIEM. The authors compare open-source and commercial SIEMtoolsregardingtheirfunctionalityandimplementation. Itshould,however,benotedthatthereareseveralchallenges mentionedwiththepaper.Usageoflargevolumedataisoften an Execution problem for SIEM systems and it causes Performance problems or a number of missed threats. In addition,theyalsoproducefalsepositives,asruleaccuracyis lacking, and it needs to be set up and managed by skilled professionals.Ithasprivacyconcernswhenwehavetostore sensitive security logs in a centralized system. While in cybersecurity,SIEMisabsolutelynecessary,thescalability, automation,andusabilityofitmustimprove.
Objectives of the project are to simulate, monitor and respondtocyber-attacksbyusinganopen-sourceSecurity Information and Event Management (SIEM) system in a virtualized setup. Based on the methodology we have developed this, is structured through a series of practical phases starting from creating a simulated environment, installingmonitoringtools,carryingoutattacksimulations, andengaginginrealtimeresponsetoathreat.
First,anOracleVirtualBoxvirtual labwascreatedvia two Ubuntubasedvirtualmachines(VMs),whichistosaythat these were virtual machines running Ubuntu. The SIEM Serverwasconfiguredtobeonemachinewiththeabilityto store, analysis and respond to each security events it collected.ThesecondmachinewastheTargetSystemthat contained vulnerable applications and security tools. To network these machines, a host only adapter was used to bringthemtogetherinsuchawayasnetworkedmachines wouldbeacrossanisolatednetworknottobeinterferedon byexternalfactors.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
Management of log collection and event correlation was performedbyWazuhManagerontheSIEMServer.Agents constantly provided data to Wazuh and, on occasion, they triggeredalertsforsuspiciousactions.Tohandledataindex anddeliverrealtimevisualinsights,theELKstackcomposed ofElasticsearch,Logstash,Kibanawasadded.Wazuhsend’s logstoElasticsearchusingFilebeat,whichcouldthendisplay securityalertsthroughtheKibanainterface.
Several critical components were deployed on our Target Machineinordertoreplicateareal-worldattacksurfaceon it. To simulate exploitable web vulnerabilities, Damn VulnerableWebApplication(DVWA)wasinstalled.AWeb Application Firewall (WAF) in the form of ModSecurity monitoredandfilteredthemaliciousHTTPtrafficaimedat DVWA.AnotherIDSwasalsodeployedtowatchforstrange networkbehavioursuchasscanningthroughportsordenial of service attempts; this is Suricata. On this machine the WazuhAgentalsoactivelywatchedlogfiles,filechanges,and systemprocesses,andsentsuchinformationtotheWazuh AgentwhichinturntransmittedittotheWazuhManagerfor centralanalysis.
OncevirtualSOCenvironmentwasdeployedandconnected, variouscyberattacksweresimulatedonthetargetmachine (192.168.56.102) to check whether it can detect and response the monitored cybersecurity events. They performed a stealth network scan (i.e. a test of what the trafficlookslikefromanoutsidehostagainstthetargetVM usingNmap)withSuricatarunningonthetargetVMasan OpenFlowAONagentabletoinspectlivetrafficinrealtime. Duringthis,aSlowLorisDenial-of-Service(DoS)attackwas performed against the DVWA web application to evaluate howthesystembehavestowardsapplicationlayerthreats andhowModSecurityiscapabletoidentifyandlogabnormal HTTPbehaviour.Further,IenabledWazuh'sFileIntegrity Monitoring (FIM) capabilities to monitor unauthorized changesincriticaldirectories,/var/www/html/DVWAbeing one of them, and to alert as soon as someone tries to intervenetamperingthem.TheWazuhAgentonthetarget systemgeneratesallalertsthataretransmittedtotheWazuh ManagerontheSIEMServer(192.168.56.10)andvisualized through Kibana dashboards in real time for the incident analysisandrapidresponse.
OntheSIEMServertheActiveResponsefeatureofWazuh was activated for extending protection features of the system.Specificthreatsignatures,repetitiveDoStrafficor vulnerability scans would now be countered by having predefined firewall rules running to block offending IP addresses with this. The results from these two examples provedthatsuchanautomationcanreducedramaticallythe timebetweendetectionandresponsewithaproactiveSIEM setup.
Overall, this methodology showcases the practical implementationofanopen-sourceSOCenvironmentcapable of real-time cyber threat monitoring and response. The
projectdemonstratesalowcosttodeploystrategytosecure networked systems against increasingly moving cyber threats via integration of tools such as Wazuh, Suricata, ModSecurity,theELKstack.
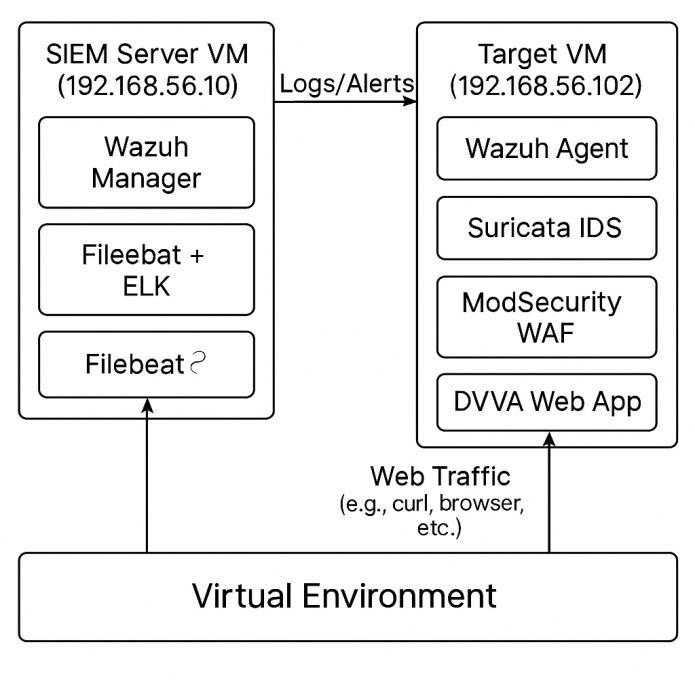
Avirtualizedlabiscreatedtobuildthearchitectureofthe proposed system in a simulation, similar to a real-world networkenvironment.ThesetupiscomprisedoftwoUbuntu basedvirtualmachines:oneistheSecurityInformationand Event Manager (SIEM) server and the other is a target machinewithvulnerableendpointandwheretheattackwill takeplace.But,frombothVMs,ahostonlynetworkisused thatconnectsthemandutilizesanisolatedcommunication for controlled testing and analysis, without internet interference.
The central node where the security related data is aggregated, processed, and visualized with an IP of 192.168.56.10.ItrunstheWazuhManagerthatwillcollect logscomingfromWazuhagents,willanalyzethemfollowing pre-configuredrulestoidentifyanypossiblethreats.These logs are forwarded to the ELK stack using filebeat forwardingthemtoElasticsearch,Logstash,andKibana.Log data is indexed and stored on Elasticsearch, Logstash processes the log data and filters out alerts and activities, while Kibana gives the user an easy-to-use dashboard to immediatelyseethealertsandactivitiesinrealtime.
However, the target machine with IP 192.168.56.102 is configuredinordertoruncomponentstosimulatethetype of a typical web facing server. Among them evolve Damn Vulnerable Web Application (commonly referred to as DVWA), a testbed to assess common web-based

International Research
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net
vulnerabilities.ModSecurityisinstalledasaWebApplication Firewall(WAF)toprotectthewebapplicationforincoming HTTPrequestsandblocksmaliciouspayload.Also,Suricata isinstalledasaNetworkIntrusionDetectionSystem(NIDS) anditwillmonitortrafficpatternsandwheretheymayfind asuspiciousbehaviorsuchasportscansordenialofservice attacks.
Tomonitorthelocalsystem,theWazuhAgentinstalledon the target VM is crucial. It messages each time a file is changed, a process started, and the console is written to. AccordingtoFileIntegrityMonitoring(FIM),itisconfigured tofollowanyunapprovedmodificationincriticalfolderslike theDVWAfolder(/var/www/html/DVWA).Italsogivesyou an immediate alert if someone is attempting to tamper or intrude.
The Suricata, ModSecurity and the Wazuh Agent all push theiralertstotheSIEMserverwhereWazuhrunsthedata andprovidesactionableinsight.Thesealertsarevisualized withKibanadashboardstodetecttherealtimethreats.The Wazuh Active Response module is configured to respond automaticallytosomealertconditions,forinstancetoblock IP’sinvolvedinbadactivity
Atthesametime,thisarchitecturedescribeshowavirtual setup with a few open-source tools can be efficiently integrated together and form a lightweight Security Operations Center (SOC). The system can support such continuous monitoring, threat detection, and automated response and is appropriate for cybersecurity training, experimentationandinsmallscaleenterpriseenvironments.
Acoupleofcyberattackscenarioswereruninacontrolled virtual environment to evaluate the effectiveness of the deployedSIEMsetup.ThisconfigurationconsistedofaSIEM Server(192.168.56.10)withWazuhManagerconnectedto theELKstackandaTargetMachine(192.168.56.102)with DVWA,ModSecurity,SuricataandWazuhAgent.Realtime monitoring was accomplished through Kibana dashboard withrespecttosecurityeventsandalerts.
In order to simulate a web-based attack, a command injectionwasattemptedbycraftingandattemptingtousea curlrequestfortheDVWAapplicationthatwashostedon the Target Machine. When the malicious request actually executed, ModSecurity, which is acting as the Web Application Firewall (WAF), intercepted an blocked the malicious request, returning a 403 Forbidden response. Thealogentrythatcontainstheinformationrelevantinthe Apache log was first captured by the Wazuh Agent, integrated with the web server, then forwarded to the Wazuh Manager, where it generated an alert. The Kibana dashboardhadstartedshowingthisalertalongwithsource
IPaddress,natureoftherequestandtimestampastheyhave beendisplayedonit.
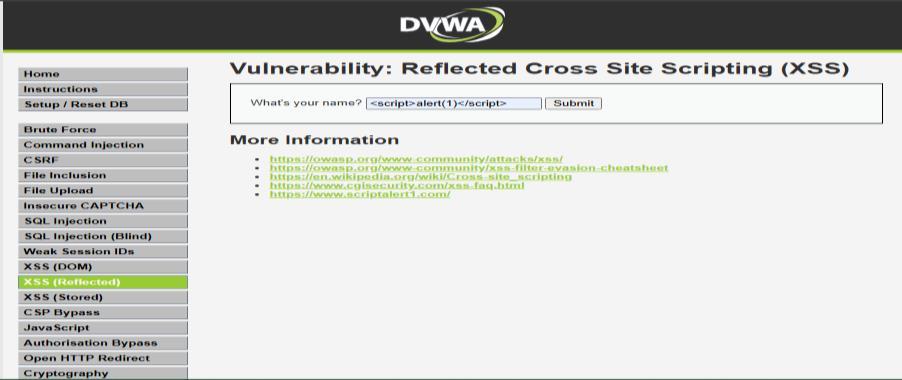
Observation: The result of this test are given below and verifiedthatthesystemwasabletoblockinrealtimeany suspiciouswebtraffictovulnerablewebapplications,with strongprotectionforvulnerablewebapplications.

For the evaluation of the File Integrity Monitoring’s effectiveness, it was intentional to modify a file in the /var/www/html/DVWA directory. When this path was altered,theWazuhAgent,whichwasconfiguredtomonitor it, immediately started monitoring it. This generated a correspondingalertwhichwassenttotheWazuhManager and eventually displayed in the Kibana dashboard. It includedtheprecisefilepath,thetypeofchange,filehashes potentiallybeforeandafterthechange.
Observation: This experiment validated the system’s immediate capability to detect and report unauthorized changes to files to provide forensic analysis support, with assuranceoftheintegrityofsensitivewebapplicationfiles.
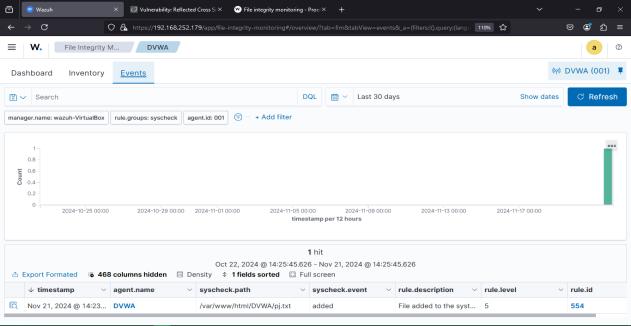
Figure 4: File integrity alert triggered by the addition of new file

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
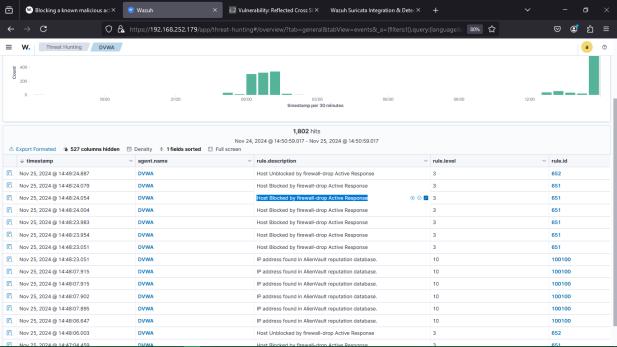
ToevaluatetheabilityofthepresentSIEMinfrastructureto detect and mitigate against the DoS attack launched, the DVWA web server was targets with a Slowloris Denial Of Service (DoS) attack. The purpose of this is to create numerousincompleteHTTPrequeststotheserversoitcan keeptheconnectionsopenandwastetheserver’sresources. Suricataasanintrusiondetectionsystemwasabletofindthe abnormal traffic pattern accurately and Wazuh observed system level anomalies accurately. When it detected the unknown IP address, the Wazuh Active Response module wastriggeredtoautomaticallyexecuteafirewalldropscript withaspecifieddurationontheattacker’sIPaddress.
Observation: It was demonstrated the robustness and efficiency of automatically defending in a single SIEM environmentthesystemsuccessfullyneutralizedthethreat inrealtimewithoutanymanualintervention.
It was practical deployment of Security Information and Event Management (SIEM) system in controlled virtual environmentasacyberthreatmonitoring&reactingsystem. The system successfully detected and mitigated different kinds of attacks, such as denial of service, malicious web requests,aswellasunauthorizedfilechangesbyintegrating someopen-sourcetools,Wazuh,Suricata,ModSecurity,and FileIntegrityMonitoring(FIM).
Havingprovedthecapabilitynotonlytoidentifysuspicious activitybutalsototakeautomatedresponseactionssuchas blocking malicious IP addresses, the system relieved the need for continual manual intervention. By utilizing these tools, all security events on the infrastructure could be visibleinrealtimeandanalyzedverynicelywithonetool, theKibanadashboard.
This project demonstrates, in general, how a lightweight, inexpensive,andcustomizableSIEMsystemcanbedeployed on virtual machines with free tools. For academic labs or small organizations, it gives good base for building a proactivedefensemechanism.Futuremayincludeenlarging
theattacksurfaceorevenintegratingcloudservicesoreven implementationofmachinelearningtobemoreIoTideasof catchingmorecleverthreats.
TheauthorsexpresstheirsinceregratitudetoProf.Bhavesh Panchalforhisinvaluableguidanceandsupportthroughout thisresearchproject.
[1] Z. S. Younus and M. Alanezi, "Detect and Mitigate Cyberattacks Using SIEM," 2023 16th International ConferenceonDevelopmentsineSystemsEngineering (DeSE), Istanbul, Turkiye, 2023, pp. 510-515, doi: 10.1109/DeSE60595.2023.10469387.
[2] N. Akshai Sankar and K. A. Fasila, "Implementation of SOCusingELKwithIntegrationofWazuhandDedicated File Integrity Monitoring," 2023 9th International ConferenceonSmartComputingandCommunications (ICSCC), Kochi, Kerala, India, 2023, pp. 350-354, doi: 10.1109/ICSCC59169.2023.10334992.
[3] M.Cinque,D.CotroneoandA.Pecchia,"Challengesand Directions in Security Information and Event Management (SIEM)," 2018 IEEE International Symposium on Software Reliability Engineering Workshops(ISSREW),Memphis,TN,USA,2018,pp.9599,doi:10.1109/ISSREW.2018.00-24.
[4] I. Bachane, Y. I. K. Adsi and H. C. Adsi, "Real time monitoringofsecurityeventsforforensicpurposesin Cloud environments using SIEM," 2016 Third International Conference on Systems of Collaboration (SysCo), Casablanca, Morocco, 2016, pp. 1-3, doi: 10.1109/SYSCO.2016.7831327.