
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net


Volume: 12 Issue: 06 | Jun 2025 www.irjet.net
Km Shweta1 , Sambhav Agrwal2
1M.Tech. (CSE) Scholar, Department of Computer Science and Engineering, S. R. Institute of Management and Technology Lucknow, Uttar Pradesh, India
2Assistant Professor, Department of Computer Science and Engineering, S. R. Institute of Management and Technology Lucknow, Uttar Pradesh, India
Abstract- Recent incidents of information breaches highlight the urgent need for secure methods to protect sensitive data from unauthorized access. Researchers have proposed various techniques, with Visual Cryptography (VC) emerging as a promising approach due to its combination of secret sharing and image processing.Unlikeconventionalencryptionmethodsthat are time-intensive, VC divides an encrypted image into multiple shares, which can only be decrypted by the human visual system. However, despite its advantages, VC has vulnerabilities, such as susceptibility to hacking and undetected tampering. This concern is particularly critical in the banking sector, where secure transactions anduserauthenticationareessential.Thoughbiometrics are commonly used for authentication, they are not foolproof, as hackers can exploit stored biometric data. Toaddressthese issues, the studyproposesa robust VC method enhanced with Steganography and an XORbased image processing technique, aiming to create a more secure and efficient system for banking transactions.
Keywords: VisuallCryptography, Steganography, Image Processing,lSecretSharingScheme,BankinglSystem
Digital information and data are now more commonly shared over the Internet than ever before. The quality and reliability of global computing networks for digital information and data sharing has increased the digital media’s success. Digital photographs, film, and audio have been revolutionized with the way they can be captured, processed, distributed, and manipulated, providing a wide variety of educational, cultural, business, and military uses, as well as other areas. Computers and networking facilities have become more widespread and less expensive. Creative solutions to data management, access and dissemination have provided many benefits for the digital multimedia industry,primarilyduetopropertiessuchasdistortionfree transmission, portable management and fast editing[1]. Withgrowingdevicedependencyatall levels of our lives, personal and confidential information is
increasingly processed and distributed using computer systems.Butthisrevolutionhasbroughtnewthreatsand computer crimes with it as evidenced by the increasing number of computer attacks and break-ins. Replicating importantinformationwillgiveintrudersgreaterchance to access it. At the other hand, having only one copy of the database means there is no way to restore it if that copy is lost. Therelis therefore a tremendous needlto handle informationlin a safe and accurate manner. Secretlsharing is of great relevance in such situations Theintentofthisresearchistostudytheavailablevisual cryptography based schemes and performance analysis of these schemes onithe basis of different parameters (pixeliexpansion, the number ofisecret images, imageiformat and types of sharesigenerated), with a view to develop a new, more efficient technique to overcome the problem encountered in the existing schemes. In the present work, we proposed to design efficientvisualcryptographybasedschemeforproviding security. Here, mainly concentrated authenticationlmethod useslXOR operation-basedlVisual Cryptography andlSteganography image processingltechniques to ensurelauthentication and securityloftheinformationlstoredinthelbankdatabase.
Kafri and Keren[1] suggested that a secret sharinglscheme could be created, in whichlthe secret imagecouldbevisually reconstructedlbysuperimposing randomlgrids. Each grid wouldlconsist of black and whiteipixels, a transparency. Naor andiShamir [1] later implemented a similar implementation called Visual SecretiSharing (VSS). This methodican securely shareiinformation about the image (printed text,ihandwritten notes,ipictures, etc.), and the human visualsystemcandecodeoriginalsecrets.
Forasetofnparticipants,avisualcryptographyscheme (VCS)isalmethodofencodingasecretimage,consisting of a collectionlof black andlwhite pixels, intoln shadow images called shares,lwhere each participantlreceives one share. Only the participant’s qualified subsets can visually recover the secret image by photocopying their

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net
sharesontotransparenciesandstackingthem,butthere is no information about the secret image in any prohibitedsetofparticipants.
The most generalitype of VCS addresses the situationiwhen the permitted subsetsiof participants have been handpicked from the set of participants. For the general access structure this type of visualicryptographic scheme is knownias the VCS. One particularicase, known as a (k,n)i-threshold VCS, is concerned with the scenarioiwhere any permitted set X of participantsiis a subset ofiP i.e X € P, so that X's cardinalityiisatleastik.Inthis case,anyqualifiedisubset of k orimore participants can visuallyirecover the secretiimage, while prohibited sets of participants consistingiof k-1 or feweriparticipants have noisecret image information. The principal difference betweenla traditional thresholdlscheme and alvisual threshold schemeliesinthehiddenrecoveryprocess.Atraditional thresholdlscheme typicallylinvolves finite- field computations; while the human visual system performs the computation in a visual-threshold scheme. The decryption process in (k, n)-VCS typically can not be successful unless at least k pieces are collected and superimposed[2].
Theinnovationofvisualcryptographyliesinthefactthat humanvisualsystemcandecodetheencryptedmessage directly; no sophisticated computation or machine intervention is needed. This is the exact reason why visualcryptographyhasattractedconsiderableattention sinceiitsinceptionandasiaresultextensiveresearchihas been carried out in this field. In this thesis, we mainly dealwithgrayscaleandblack&whitetypesofimagesas the original nature of VC. The different model for computation has been proposed in the literature while working with different aspects of the VCS and assessing itwithrespecttoseveralparameters.
Thetechniquesoferrordiffusiondistributethepixelsas evenly as possible in order to make changes in average efficiency of the shares. Error diffusionlis an adaptiveltechnique which quantifies each pixellaccording to both the inputlpixel and its neighbours. Failure propagation causes overall tonal output to stay the same and fails to localize tone level distribution[48]. For each pixel, the initial pixel value is compared to the errors of its previous neighbors and a thresholdwillbeappliedtothatchangedvalue.
Based onlthe concept of expanded visuallcryptography, Zhou et al.[3] set out to develop these strategies by presenting images of halftonelgrayscale that hold valuable visual information. That dramatically improves thevisualcryptographysecuritymodel.Severalscholars, along with Zhou, introduce novel strategies through which halftone images can be exchanged with clear visual significance that is of a higher quality than those displayedbyusingstrategiesoferrordiffusion.
p-ISSN:2395-0072
Wang et al.[4] us suggested another system only for booleanoperations.Thecomparisonisalsogreaterthan other systems for the exchange of probabilisticlvisual cryptography.lThefieldofcontrastbetweenhalftoneland grayscale VClis important, because thelcontrastldetermines just how obvious the visuallsecret is retrieved. Cimatolet al.[5] used a technique known as reversing technique to create a visual cryptography system of perfect comparison. The inverting process changes black pixelslto white pixelslandvicelversa.
ThischaptermainlyfocusesprecedingVCSresearchand theknowledgeneededtofurtherexploreVCschemes.In specificmultipleparadigmshavebeenadoptedintheVC research areas, including standard VC, expanded VC, dynamicVC,colorVCandprogressiveVC.Differentstudy results were evaluated and the efficacy, as well as the degreeofcomplexity,wereidentified.Ingeneral,various examples have also been discussed to illustrate the secret sharing schemes. In VC authentication and creationofcheatingfreeVCS,severalfeaturesofVChave beenreviewedandanalyzed.
The following objectiveshave been set to achieve the proposed goals described above in the problem definition:
Development of a new algorithm on visual cryptography based approach to solve the existing drawbacks of different techniques along with experimentalverifications.
Development of secure and more general scheme forsharingthesecretmessage.
Analyzes authentication methodluses XOR operationlbased Visual Cryptographyland Steganography image processingltechniques to ensurelauthentication andlsecurity of thelinformationstoredlinthebankldatabase
3.1 Introduction
Steganography comes from the Greek term steganographic, meaning veiled writing. It's Secret Communication science. The purpose of steganography istoconcealfromunauthorizedpartythepresenceofthe post. Modern protected image steganography is a process of moving the embedded information to the targetwithouttheattackerfindingit.Itispossibletouse a lot of different carrierifile formats, but digitaliimages are the mostipopular becauseiof their Internetifrequency. There is a wide variety ofisteganographic techniquesifor hiding secret informationiin images, some areimore complex than othersiand all of them have strong andiweak points respectively

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net
3.2 Overviewlof Steganography
Technically, the wordlSteganography signifies covered orlhidden writing. The historical history can beltraced back tol440 BC. Though the termlsteganography was invented only at thelend of the fifteenth century, steganographyusegoes back manycenturies.Inlancient times messages were hidden behind waxiwriting tables,iwritten on rabbit stomachs,ior tattooed on slave scalp. For decades, invisibleiink was used for playing by childreniandpupils,andforiseriouscovertworkbyispies andterroristsi[6].
Many of today'sisteganographic systems useias cover media multimedia items such as picture, audio , video etc. as people also transfer digital images through email andlother Internet communication.lModern steganography makes use of thelopportunity to hide information in digitallmultimedia files andlat network packetllevel[7]aswell.
3.3lImage SteganographiclTechniques
Several Steganographiclimage file format techniques existwhicharelasfollows[8]:
3.3.1 SpatiallDomainlTechnique
There arelmany versions oflspatial steganography, all of whichchangelsomebitsdirectlyinthepixellvaluesofthe image when hiding data. Steganography based on the leastisignificant bit (LSB)iis one of theisimplest techniquesithat masks a hidden message ofipixel values without perceptibleidistortions in theiLSBs. Changes in the LSB ideals areiimperceptible to our human eye. Embedding pieces of messages may be achieved either easily or at random. [9]. Many of the spatial domain methods include the Least SignificantiBiti( LSB) substitution method, the Matrixiembedding. Advantages ofLSBstrategyforspatialdomainare:
Theoriginalimageisnoteasytodegrade.
Capability shielding is more important i.e. more detailscanbecontainedinthepicture.
LSBstrategyhasitsdisadvantages:
Durabilityispoor
Easyattackswillruinsecretrecords
3.3.2 MaskinglandlFiltering
Maskingland filtering isla technique of steganography that can be applied onlgray scalelimages. Masking andlfiltering are close to putting watermarkslon an imageprintedon.Thesemethodsembedthelinformation in thelmore critical places than simply shielding it from thenoiselevel.lWatermarkingtechniqueslcanbelapplied because of loss compression without fear of image
p-ISSN:2395-0072
destruction, as they areimore integrated intoithe image [10].
3.3.3 TransformlDomainlTechnique
The Frequencyldomain the messagelis embedded into transformed image coefficients which provide more informationlhiding power and more robustnesslagainst attacks. Transform domainlembedding can be considered a domainlof embeddingltechniques for whichla variety of algorithmslhave beenlsuggested [11]. Some transforming domain techniquesldo not appear to be dependent on imagelformat, and conversions to lossless and lossless format may be outdone. Domain transformtechniquesarelofvarioustypes[12]:
i. DiscretemethodfortheFourierltransformation (DFT).
ii. Themethodofdiscretelcosine transformationl(DCT).
iii. DiscreteTechniquefor WaveletlTransformationl(DWT)
3.3.4
In thisltechnique, store informationlby signal distortionland measure the deviationlin the decoding process from the original cover. Distortionltechniques require knowledge oflthe original coverlimage during theldecoding process wherelthe decoder functionslto check for differenceslbetween the originallcover image andlthe distorted coverlimage to restore the secretlmessage. In this procedure, the addition of a series of changes to the cover image produces a stegoimage.iThis series of modifications isiused to suit the code needed to transmit theisecret message. The message is encoded using pseudo-randomlyiselected pixels. If the stegoimage at the specified message pixel isidifferent to the coveriimage, theimessage bit isia 1. Otherwise theibit of a message is a 0. Theiencoder should adjust the 1 valueipixels in suchia way that image's mathematical properties arelnot affected. If an intruder interferes with the stego-imagelby cropping, scalinglor spinning, it will be quickly detected by the receiver.[13]
Steganalysislisthebreakdownofsteganography,landthe study of secret content detection [14]. Steganalysis is mainly aimed at breaking steganography and detecting stegoimage.Nearlyallalgorithmsofsteganalysisrelyon steganographic algorithms which implement statistical differences between the image of the cover andlthe stego.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
Steganalysis is of three distinct types:
i. Visualattacks:Hiddeninformationwasdiscovered, which helpsitoiseparateithe imageiintoibit planes forifurtherianalysis
ii. Statisticaliattacks: Active or aggressive predictive Attacks. Passive attacks include recognizing the locationorabsenceofahiddenmessageorthecode usedtoinsertthem.Ansuccessful attack isusedto analyzethe duration of embeddedimessages or the locationiof hidden messages orithe secret key used intheiembedding.
iii. Structural attacks: Application file format changes as the data to be protected becomes inserted, recognizing such characteristic changes in structure will help us find the location of image / textfiles.
3.5 Steganalyticltools
A variety of steganalytic devices are available on the market, such as PhotoTitle,l2Mosaic and StirMark Test etc.Thosethreesteganalyticltoolscanremovelanyimage from steganographic content. To do this, two methods are used to delete hidden message: crack apart and resample[15].
4.1 Introduction
Recent and rapid developments in imaging and communication technologies have resulted in a mass generationandtransmissionofdigitalimages,eventually increasing its number of applications in nearly all fields suchasremotesensing,medicine,agriculture,forensics, defense and banking etc. As content is sensitive to insecure electronic attacks, this involves successful and safetransferofimagesacrossthenetworks.Thecurrent work is based on VisuallCryptography, and itsluses for bankingsystemauthentication.
Two users have tolopen a joint accountland want to operatelin such a waylthat if bothlare present thenlonly bank will be able to carry out the transaction otherwise not because of mutual trust. For two images, welobtain secret imagelin binarylform using these pictures, then dividelit intolshares[36] using (2,2)-VCSXOR when underlyingloperation islXOR. In the next step, to generate two shares, one of thelshares previously generated as a secretlimage is assumed and furtherldivided using thelsame scheme. Reconstruction from shares of the secret image. Now check the reconstructedimageforitsvalidity
4.2
The banking systemlprovides the facilitylfor joint account keeping and functions either independently or
together. In the case of an individual operation,lit does notlmeanhavingajointaccountlbutitgivesflexibilityto work independently to the participants of the joint account.Inlsomecasesitlisnotsociallysafe.
Suppose Aland Blhave a joint accountland A is unfavorable to B and wants to remove all the moneylfrom the accountlat a later time. In this scenario A cheats B. It is assumed in the proposed method thatltransaction is feasible only whenlboth users arelavailable. It also ensures that no one canlmisuse the data stored in theldatabase because shareslare random noisellike pictures and no one can getlany clue fromla single shareleven if they apply enormouslcomputing power andltime. Gray imageslof both users are takenlas inputland analyzed for furtherluse of the proposed system.
The overall processlis divided intoltwo phases: phaselof encryptionandphaseofdecryption
Encryption phaselis further broken down intolPreprocessing,ImageFusion,andHidetextinImage (Steganography), Secret Image and Share Generation. It isshowninFigure4.1.
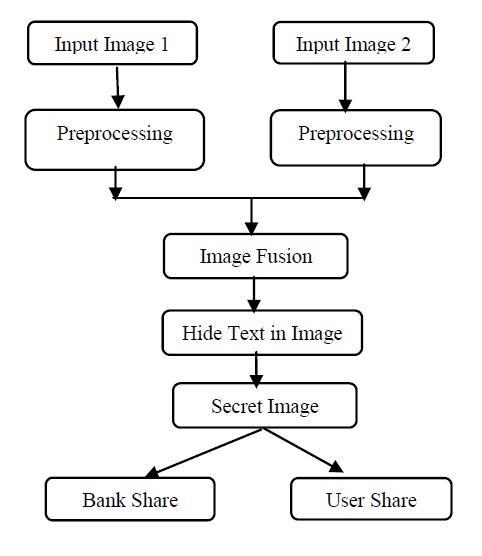
Figure4.1:Encryptionphase
4.2.2. Preprocessing
The facial picture needs to be submitted to the bank at theltimeofregistrationlforjointaccountluserAandluser B. Preprocesses and creates shared identities of users A and B by the respective authority; this common user identityAandBisconsideredahiddenpicture

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072

5. SIMULATIONlRESULTlAND DISCUSSION
5.1lIntroduction
This segment examines how the suggested approach works. On proposed Visual Cryptography, based on steganographyschemes,thesimulationsoftheproposed algorithmscanbeusedinthebackingsector
5.2 Simulationltool andlSoftware
MATLAB:ThelMATLABisthelanguageofhighefficiency forfunctionalcomputation.Itincorporateslcomputation, visualization,land programming in a user-friendly environment where mathematical representation uses problemsandanswerstocommunicate.MATLABlisused asalsimulationtoolforsettingupnetworkarrangements and setting uplthe transmission of data betweenlnumerous nodeslin the network. The central programming in MATLAB and the commandslare used aslsimulation tool. MATLAB isla software application that helps you to control, simulate, measure, math and applicationthedata.Itcanbeusedtodobothverybasic andverycomplextasks.
5.2.1. MATLABlas altool for datalanalysis
Informationtypicallyarrivesintables.Youmayhaveany measurement,forexample,asafunctionioftime,likethe averageitemperature as a functioniof a month. This dataiwill have two columns,ione for theimonth and the other for aitemperature measure. Or you might have several replicatesion an experiment whereithe average weight of certain organisms has been observediin environmentswithdifferentilevelsoffood.Thisdataican be reported as a table with the numberiof rows corresponding to the number of repeat tests and the number of columns equal to the amounts measured for food.
Diverse tasks, viz. Preprocessing,lconversion of imageslfrom gray tolblack and white, formation of shares,lreconstruction of thelsecret is also carried out using thelfunctions described in the toollbox. Initially user image is perceived to be gray andlresize to
makelthe display of both userlimages similar. In this firstly implement the base paper results, and then comparetheproposedmethodology.
5.3 1 Proposed Method: The base paper has been implemented with steganography and results have been verifiedwithbasecoderesults.
Original Images
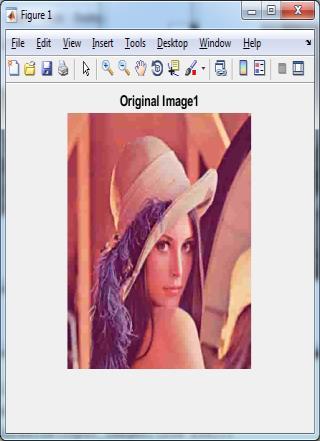
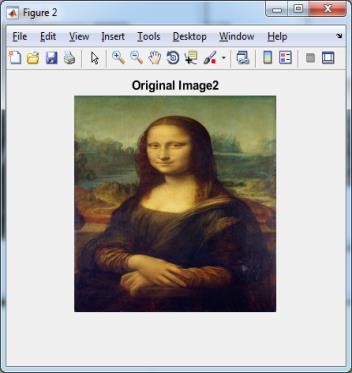
Figure5.1:OriginalImages
Original gray scale images
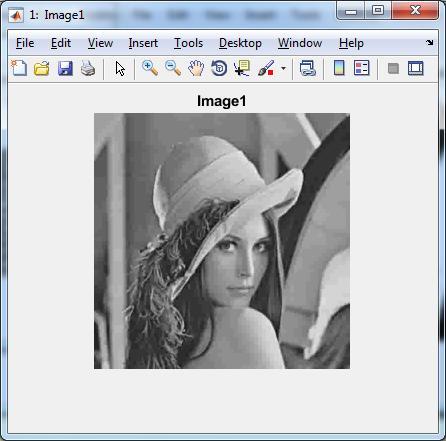
Figure5.2:Originalgrayscaleimages
Preprocessed Images
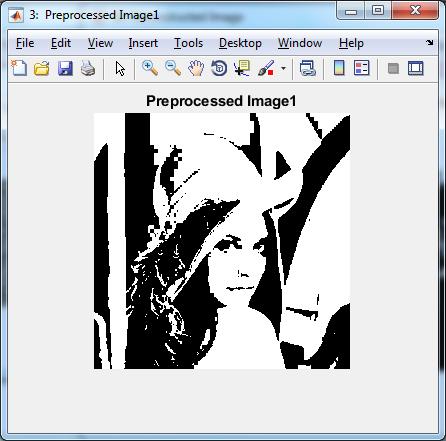
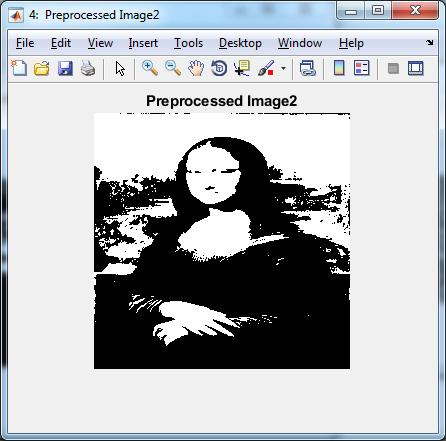
Figure5.3:PreprocessedImages

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
Concatenated Image
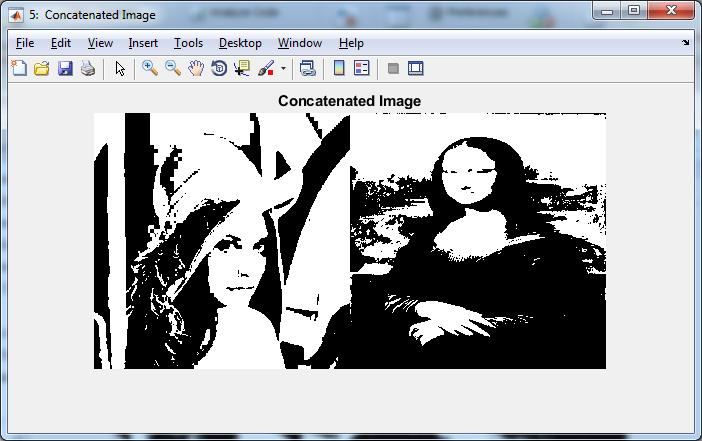
Figure5.4:ConcatenatedImages
Secret Image:it contains a hidden text message in image as ( email id is xyz123@gmail.com and password is 12345)
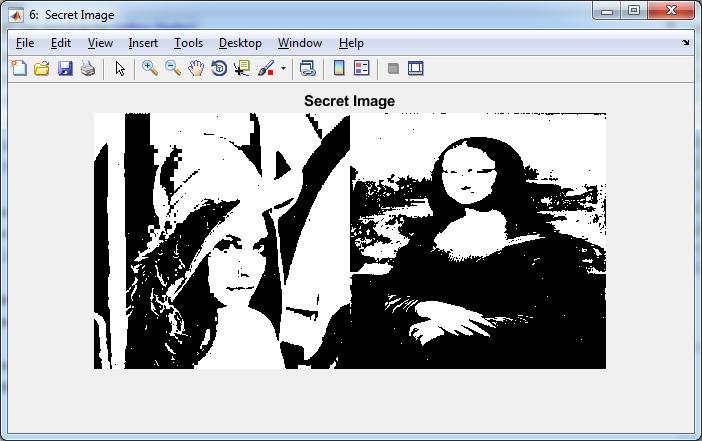
Figure5.5:SecretImages
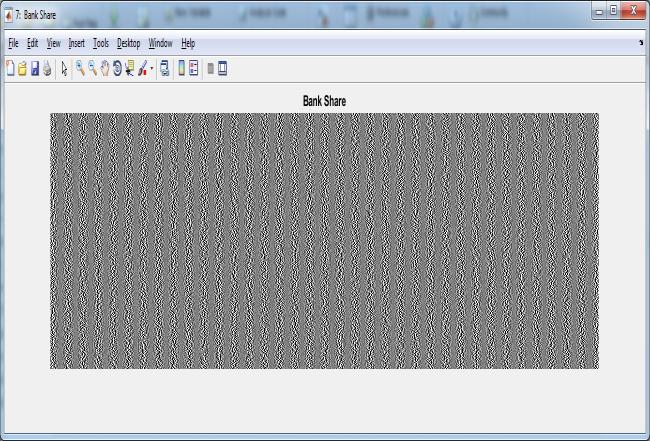
Bank Share
User Share
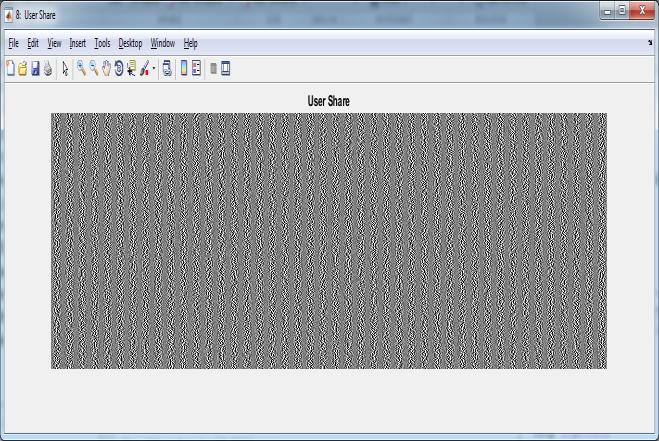
Figure5.7:UserShareImage
The User Share is again divided into User Share1 and UserShare2.
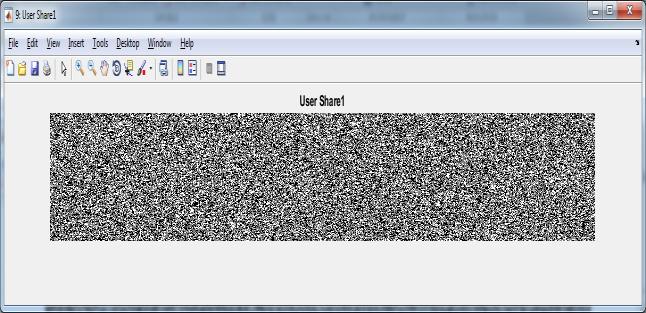
Figure5.8:Share1Images
Figure5.9:Share2Images

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
Reconstructed Image
Finallywegetreconstructedimageandthetextmessage
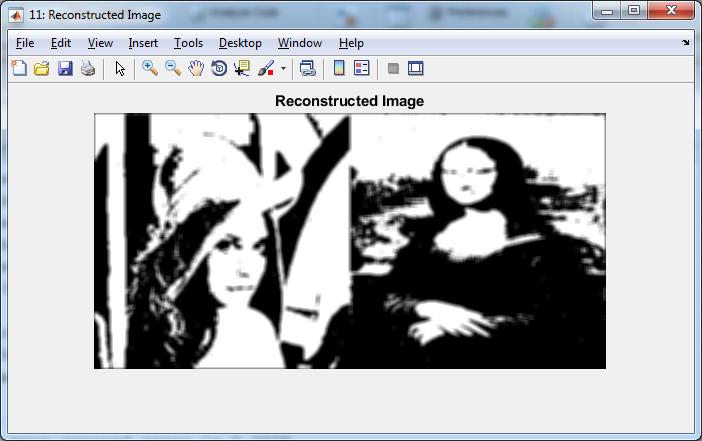
Figure5.10:ReconstructedImage
The text message is completely decoded and displayed as below, (email id is xyz123@gmail.com and password is 12345)It can be seen that the inserted text message anddecodedtextmessagearesame.Itwillallowuserto loginandstartbankingonline.
Figure5.11:EmailIdtoaccessbankingonline
Here is the performance parameters comparison for bothtechniquesusingLenaandMonalisaimagesdataset.
Table5.1:PerformanceParametersComparison
Methodolo gy
Basework 00293 153347 117678 09936
Proposed work 00010 301525 270359 09990
Here we can see the proposed method is better than base method. Figure 5.1 and Figure 5.2 are original images and gray imagesltaken as inputlwhile Figure 5.3 is preprocessed binarylimages obtained fromlgray
images Figure 5.2 respectively. Figure 5.4 showed as concatenatedimageandSecretimageasshowninFigure 5.5 is obtained from the Figure 5.3. After that Secret image Figure 5.8 is divided into user shares Figure 5.9 Figure 5.6 is a bank share image. Reconstructed secret image as shown in Figure 5.8 is obtained by using the shares Figure 5.6, Figure 5.6 and Figure 5.7 .Table 5.1 shows performance parameters comparison for both techniquesusingLenaandMonalisaimagesdataset.
6.1lConclusion
Visual cryptography is an important technique for the security of images showing crucial information. As albranchofsecretsharing,lVChasdrawnmuchlattention asitslsecurity mechanismlinvolvingtheconsiderationlof both image processingland cryptography. Withlthe developmentlof VC in thelareas of dealing withldifferent types oflsecret images,lthe applicationslof VC appear tolbe flourishing and morelpractical. However, comparedltotheawarenesslofVCsecretimageltypes,the authentication oflits shares is stilllfar fromlbeing maturely researchedland cheating immunelVC is becominglmore and morelvital for the securitylof the wholelVClprocess. There are varieties of applications of VCs, but for all the applications, the important requirement is the security of the information in the distributedsharesamongtheparticipant.
In thislmethod original imagelis secured byldecomposing it intoln shares. Thislwork mainly focuseslon issues related tolthe identity theft andlcustomers data securitylin the jointlaccount transaction.lFor secure Banking Transactionlin joint account operationlthis work proposedla methodlthat is based onl(2, 2)-VCS-XOR with Hide text in Image (Steganography). Experimentallresults show thatlreconstructed secret imagelis same in sizeland qualityofltheoriginallsecretimage.
Therearevariousproblems leftunsolved.Someofthem like the following, may be the core issues for future work:
The quality of the recovered secret images is not perfect. In future, the improvement of the image quality without any additional computation can be considered.
The design of new access structures for VCS with enhancedcontrast.
Visual cryptography scheme with recursion can be extendedtodifferentVCS.
DesignbasismatricesforIPmodel

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN:2395-0072
Visual cryptography scheme can be applied to different digital applications for tamperproof and reliable transmission of information with low computational capabledeviceslikemobilephone,digitalcameraetc.
[1] M.NaorandA.Shamir,―VisualCryptography,‖ Advances in Cryptology ,EUROCRYPT-94, LNCS-950, pp. 1–12, Springer, Berlin, Heidelberg,1994.
[2] B. W. Leung, F. Y. Ng, D. S. Wong, ―On the security of a visual cryptography scheme for color images,‖ Pattern Recognition Journal, Elsevier,Vol.42,no.5,pp.929-940,May,2009.
[3] S. K. Das and B. C. Dhara, ―An image secret sharing technique with block based image coding,‖ , 2015 Fifth International Conference on Communication Systems and Network Technologies,pp.648-652,April,2015.
[4] C.Y. Wang, N.S. Shiao, H.H. Chen, and C.S. Tsai, ―Enhance the visual quality of shares and recovered secret on meaningful shares visual secret sharing,‖ in Proceedings of the 4th International Conference on Uniquitous InformationManagementandCommunicationICUIMC’10,2010.
[5] F. Liu and W. Yan, Visual Cryptography for Image Processing and Security : Theory, Methods, and Applications, 2nd edition, Springer,2015.
[6] M. Naor and B. Pinkas, ―Visual authentication and identification,‖ Advances in Crypto, Crypto-97, LNCS-1294, pp. 322–336, Springer, Berlin,Heidelberg,1997.
[7] D. Chaum, ―Secret-ballot receipts: true voterverifiable elections,‖ IEEE Security & Privacy Magazine,vol.2,no.1,pp.38–47,Jan.2004.
[8] H. Luo, J.-S. Pan, Z.-M. Lu, and B.-Y. Liao, ―Watermarking-Based Transparency Authentication in Visual Cryptography,‖ in SeventhInternationalConferenceonIntelligent Systems Design and Applications (ISDA 2007), pp.609–616,2007.
[9] R.J. Hwang, ―A Digital Image Copyright Protection Scheme Based on Visual Cryptography,‖ Tamkang Journal of Science and Engineering, vol. 3, no. 2, pp. 97–106, Sep. 2000.
[10] F. Liu and W. Q. Yan, ―Various Problems in Visual Cryptography,‖ in Visual Cryptography for Image Processing and Security, pp. 23–61, SpringerInternationalPublishing,2014.
[11] H. Koga, ―A General Formula of the (t, n)Threshold Visual Secret Sharing Scheme,‖, Advances in Cryptology, ASIACRYPT 2002, Lecture Notes in Computer Science, vol 2501.
pp. 328–345, Springer, Berlin, Heidelberg, 2002.
[12] S. J. Shyu, ―Efficient visual secret sharing scheme for color images,‖ Pattern Recognition, vol. 39, no. 5, pp. 866–880, May 2006.
[13] Y. F. Chen, Y. K. Chan, C. C. Huang, M. H. Tsai, and Y. P. Chu, ―A multiple-level visual secretsharing scheme without image size expansion,‖ Information. Sciences., vol. 177, no.21,pp.4696–4710,2007.
[14] T.MonothandP.B.Anto,―Contrast-enhanced visual cryptography schemes based on additional pixel patterns,‖ in Proceedings2010 International Conference on Cyberworlds,CW2010,pp.171–178,2010.
[15] T.MonothandP.B.Anto,―Contrast-Enhanced Visual Cryptography Schemes Based on Perfect Reconstruction of White Pixels and Additional Basis Matrix,‖ , In Computational Intelligence, Cyber Security and ComputationalModels.AdvancesinIntelligent SystemsandComputing,vol412.pp.361–368, Springer,2016.
[16] P. Li, P.J. Ma, X.-H. Su, and C.N. Yang, ―Improvements of a two-in-one image secret sharingschemebasedongraymixingmodel,‖, Journal of Visual Communication and Image Representation, vol. 23, no. 3, pp. 441– 453, 2012.
[17] C.Kraetzer,Y.Q.Shi,J.Dittmann,andH.J.Kim, Digital forensics and watermarking : 16th International Workshop, IWDW 2017, Magdeburg,Germany,August23-25,2017.
[18] L. Dong , D. Wang , M. Ku and Y. Dai, ―(2, n) Secret Image Sharing Scheme with Ideal Contrast,‖ 2010 International Conference on Computational Intelligence and Security , pp. 421-424,Dec.2010.
[19] W.Hu,M.Li,C.Guo,L.Y.-M.P.In,andU.2015, ―Areversiblesteganographyschemeofsecret imagesharingbasedoncellularautomataand least significant bits construction,‖, Mathematical Problems in Engineering, vol. 2015,ArticleID849768,11pages,2015.
[20] X. Wu, W. Sun, ―Extended capabilities for XOR-based visual cryptography, IEEE Transactions on Information Forensics and Security , Vol. 9, Issue: 10, pp. 1592 - 1605, Oct.2014.
[21] X. Yan, S. Wang, X. Niu, and C. N. Yang, ―Halftonevisualcryptographywithminimum auxiliary black pixels and uniform image quality,‖DigitalSignalProcessingJournal,vol. 38,pp.53–65,2015.