
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
Anil B Alde1 , Vikas T. Humbe2
1School of Technology, S.R.T.M.U.N, Sub-Campus, Peth, Latur, Maharashtra, India
2School of Technology, S.R.T.M.U.N, Sub-Campus, Peth, Latur, Maharashtra, India
Abstract - Visual Cryptography (VC) is a cryptographic technique that splits a secret image into shares, revealing no information individually but reconstructing the image when stacked together. This paper compares two VC methods: Random Grid Visual Cryptography (RG-VC) and Visual Cryptography using Codebook (VC-CB). We analyze their principles, implementation, security, efficiency, and applications. Our findings show that RG-VC offers simplicity and perfect security, while VC-CB provides scalability and flexibility. These insights help inselectingthe appropriate VC method for various applications and further research work.
Key Words: VisualCryptography(VC),RandomGrid Visual Cryptography (RG-VC), Visual Cryptography usingCodebook(VC-CB),Security
1. INTRODUCTION
Visual Cryptography (VC) is a powerful cryptographic technique for secure image sharing, with applications in securecommunications,authentication,andwatermarking. VC divides a secret image into multiple shares that individually reveal no information [1]. However, when shares are superimposed one above the other, the secret imageisrevealed[2]asfiguredoutinFig.1.
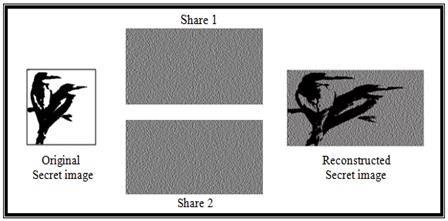
This paper compares two VC methods: Random Grid VisualCryptography(RG-VC)andVisualCryptographyusing Codebook (VC-CB). We analyze their principles, implementation,security, efficiency, andapplications. The paper is structured as follows: Section 2 discusses the principles of VC-CB and RG-VC, Section 3 compares their features, Section 4 details their algorithms, Section 5
presentsexperimentalresults,andSection6concludeswith keyinsights.
Naor and Shamir [3] presented a VC-CB in 1994, in whichacodebook,apredefinedsetofpatternsorcodes isusedtoencodethesecretimageintoshares.
Eachsharecontainsaportionofthesecretimage,and whencombinedaccordingtothecodebook,theoriginal imagecanbereconstructed.
UnlikeRandomGridVisualCryptography,whichrelies on random patterns, this approach uses a predeterminedsetof codes toencodeanddecodethe secretimage.
Thesecurityofthismethoddependsonthesecrecyof the codebook. If an adversary gains access to the codebook,theycaneasilyreconstructtheoriginalimage fromtheshares.
The encryption of pictures by two random grids was firstintroducedbyKafriandKerenin1987[4]andwas neglectedfortwodecadesuntil 2007[5]inwhichthe secret image is divided into multiple shares, each of whichcontainsrandomgridsofblackandwhitepixels. Thesesharesaredistributedamongparticipants.
Torevealthesecret,theparticipantssuperimposetheir sharesontopofeachother.Onlywhenthesharesare overlaidinthecorrectalignment,doesthesecretimage becomevisible.Individually,thesharesdonotprovide anyinformationabouttheoriginalimage.
This technique relies on the randomness of the grid patterns to achieve secrecy. The random grids are designedinsuchawaythattheyrevealthesecretwhen overlaidcorrectlybutremainmeaninglessotherwise.
VisualCryptographyusingCodebook(VC-CB)relieson predefined codebooks to encode and decode shares. The secretimageisdividedintoblocks,andeachblockismapped toacodeinthecodebook.Sharesaregeneratedbasedonthe codesinthecodebook[6].VC-CBinwhich2-out-of-2abasic

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
matrix,calledacodebookwithallofthecodewordbeingof thesize2X2subpixelsisemployedasdepictedinFig.2.But designingthematrixforencryptionisalsoadifficulttask[7]. Thiscodebookencodesasecretimagetogeneratetwosecret imagescalledshares.
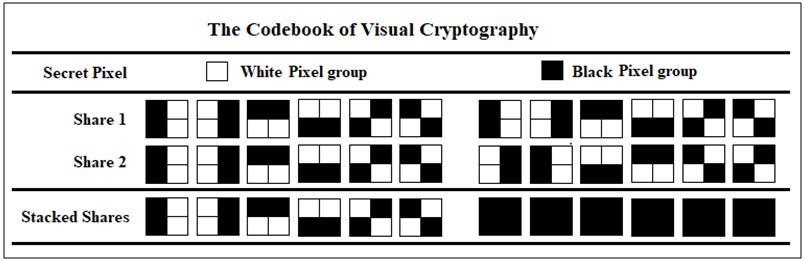
InFig.2whereVisualCryptographyincludestwogroups,a whitegroupwithsixcasesandablackgroupwithsixcases.If acertainpixelofthesecretimageiswhite,share1andshare 2areassignedcodewordbyrandomlyselectingoneofthesix casesinthesharegroup.Onthecontrary,ifthesecretpixelis black,thecodewordareselectedfromtheblackgroup.The sizeofthesharedimagesShare1andShare2becomelarger thanthatofthesecretimage[8][9].
Toovercomethedrawbackofthecodebook,researchers conferred on another VSS scheme by the random-grid algorithm(RGVSS),whichwasfirstpresentedbyKafriand Kerenin1987[4],butneglectedfortwodecadesuntil2007 [5].RandomGridVisualCryptography(RG-VC)operatesby dividingthesecretimageintoagridofrandompixels.Each shareconsistsofagridwithrandomblackandwhitepixels. Whenstackedtogether,thesharesvisuallyrevealthesecret image.InRG-VCeachpixelistreatedasagridandthecolour ofthegridisrandomlyassignedasillustratedinFig.3

DuringtheencryptionprocessofRG-VC,theGridR1colour ofthefirstshareisrandomlyassignedandtheGridR2colour ofshare2iseitherthesameorcomplementarydependingon thecolourofthecorrespondingsecretpixel.Shyu[5]extends the kafri’s scheme to propose three algorithms offering differentlighttransmissionswhicharedemonstratedinFig. 3. Ifthe pixel of the secret image is white,thenR1andR2 havethesamecolour.Besidesthat,ifthepixelofthesecret imageisBlack,thenR1andR2arecomplementaryincolour. Thisgenerates100%blackinblackareasand50%blackin white areas when the two shared images are stacked one aboveanother.
InModel2,ifthepixelofthesecretimageisWhite,thenthe coloursofR1andR2arethesamecolouranditgeneratesthe samecolourwhenthesesharesareoverlapped.Ifthepixelof thesecretimageisBlack,thenthecolourofR2israndomly assigned. This generates 75% black in the black areasand 50% black in the white areas when the two shares are overlappedoneabovetheother[3].
InModel3,ifthepixelofthesecretimageiswhite,thenthe colourofR2israndomlyassigned;besidesthat,ifthepixelof asecretimageisblackthenR2iscomplementaryincolourto R1.Thisgenerates100%blackintheblackareasand75% blackinthewhiteareawhensharesarestackedtogether.
Inallthreemodels,nomatterwhatthecolourofthesecret pixelis,theprobabilityofitbeingblackinthesharedimageis 1/2. This ensures the security of the secret image. The contrastsproducedbythethreemodelsare50%,25%,and 25%, which are sufficient for an observer to identify the confidentialinformationinthestackimagewiththenaked eye.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
VC-CB AND RG-VC
TherearesomanydistinguishablefeaturesbetweenRandom Grid Visual Cryptography and Visual cryptography using Codebook which are helpful for further research work as showninTable1.
Table - 1: FeaturesofVC-CBandRG-VC
Feature VC-CB RG-VC
Nature of Shares Structured patterns fromacodebook
Security Dependsonthesecrecy ofthecodebook
Efficiency Higher computational andstorageoverhead
Applications Multi-party authentication, secure printing
Flexibility / Complexity Depends on codebook design
Random grid Patterns
Perfectsecuritywith randomgrids
Highefficiency
Secure image sharing, authentication
Flexible in grid size andcomplexity
VC-CB: Invisualcryptographyusingthecodebooktechnique, shares contain structured patterns corresponding to codewordsfromacodebook.VC-CBimplementationrequires creating and managing codebooks, encoding and decoding blocks, and maintaining codebook security. It may involve complexalgorithmsandadditionalcomputationaloverhead [10]
RG-VC: Inrandomgridvisualcryptography(RG-VC),shares contain random grid patterns resembling noise. ImplementationofRG-VCinvolvesrandomlyassigningblack andwhitepixelstogrids.Itisrelativelystraightforwardand computationallyefficient[4]
VC-CB: Itssecuritydependsonthesecrecyofthecodebook.If thecodebookiscompromised,thesecurityoftheschemeis compromised. Careful management of the codebook is essentialtomaintainsecurity[11].
RG-VC: Itoffersinherentsecurityduetotherandomnature of share generation. It provides perfect security, where knowledge of one share reveals no information about the secretimage[1].
VC-CB: VC-CBmayhavehighercomputationalandstorage overhead due to codebook management and
encoding/decoding processes.It maynot beas efficientas RG-VCincertainscenarios[12].
RG-VC: RG-VC is efficient in terms of computation and storage. It requires minimal processing overhead and producesshareswithlowcomplexity[13]
VC-CB: VC-CBissuitableforapplicationswherescalability, flexibility,andmanageabilityareimportant.Itiscommonly used in multi-party authentication, secure printing, and digitalwatermarking[11].
RG-VC: RG-VC is suitable for applications requiring simplicity, efficiency, and perfect security. It finds applicationsinsecureimagesharing,authenticationschemes, andwatermarking[13]
VC-CB: Implementationmaybemorecomplex,asitinvolves creatingand managinga codebook.Generatingsharesand reconstructingtheoriginalimagemayalsorequireadditional computationalsteps[14].
RG-VC: Implementation is relatively straightforward, as it primarily involves generating random grid patterns. No complexencryptionalgorithmsarerequired[15]
VC-CB: Shares may be easier to manage and distribute, as they are generated based on a predefined codebook. However,theneedtokeepthecodebooksecureaddsanextra layerofcomplexity[16]
RG-VC: Sharesareeasytodistributeastheyconsistofsimple gridpatterns.However,aligningthesharescorrectlytoreveal the secret imagemay require careful manual alignmentor additionalcomputationaltechniques[17]
VC-CB: Flexibility depends on the design of the codebook. Adding or modifying codes in the codebook may require updatestothesystem[18]
RG-VC: Offersflexibilityintermsofthesizeandcomplexityof the grid patterns. Different sets of random grids can be generatedfordifferentimages[4]
VC-CBandRG-VCofferdistinctadvantagesandtrade-offs. VC-CBoffersscalability,flexibility,andmanageability,making itsuitablefordiverseapplicationsOntheotherhand,RG-VC excelsinsimplicity,efficiency,andsecurity.Itissuitablefor scenarioswhereperfectsecurityisparamount[11].

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
The choice between VC-CB and RG-VC depends on the specificrequirementsoftheapplication,includingsecurity level,computationalresources,andeaseofimplementation.
RG-VC
Input: Loadsecretimage
Pre-processing:
Converttheloadedimageintoabinaryformat(Blackand White)usingathresholdof0.5iftheimageisnotalready Binary
Input shares:
Getthedimensions(rowsandcolumns)ofthesecretimage. Initializethesharesmatrices(‘share1’,‘share2’)having thesamedimensionsasthesecretbinaryimage.
Codebook Definition:
Defineacodebookthatspecifiesthepixelpatternsfor whiteandblackpixels.
Codebookfor2-out-of-2schemes:
o Whitepixel:‘[[1,0],[1,0]]’or‘[[0,1],[0,1]]’
o Blackpixel:‘[[1,0],[0,1]]’or‘[[0,1],[1,0]]’
Generate Shares:
Foreachpixelinthesecretimage: If thepixeliswhite(pixelvalue=1):
Randomlyselectapatternforawhitepixelfromthe codebook Ifthepixelisblack(pixelvalue=0):
Randomlyselectapatternforablackpixelfromthe codebook.
Assigntheselectedpatterntothecorrespondingpositions inthesharematrices.
Output:
DisplayShare1andShare2.
RevealanddisplaysecretimagesbysuperimposingShare1 andShare2.
Input: Loadthesecretbinaryimage.
Pre-processing:
Converttheloadedimageintoabinaryformat(blackand white)usingathresholdof0.5
Generate Shares:
InitializetwomatricesShare1andShare2ofthesame sizeasthebinaryimage.
For white pixels (pixel value = 1):
Generatetworandomsharesbydefiningsets1a=[0, 1]ands1b=[0,1].
Assign the first element of each share to the correspondingpixellocationinShare1andShare2.
For black pixels (pixel value = 0):
Generatetworandomsharesbydefiningsets0a=[1, 0]ands0b=[0,1].
Assign the first element of each share to the correspondingpixellocationinShare1andShare2.
Output:
DisplayShare1andShare2images.
Reveal and display secret images by superimposing Share1andShare2oneaboveanother.
The experimental results of Visual Cryptography using Codebook(VC-CB)inwhichsharesaregeneratedbasedon pre-definedpatternsortemplatesstoredinacodebook.Each templatecorrespondstoaspecificcombinationofblackand white pixels that encode a part of the secret image. To generateshares,thesecretimageisdividedintoblocks,and foreachblock,theappropriatetemplatefromthecodebookis selected and XORed with it to generate a lossless secret image.
Random Grid Visual Cryptography(RG-VC) is another methodology that helps to overcome all the drawbacks of traditional Visual Cryptographysuchas expansionin pixel andlowcontrast[19]andalsogeneratesalosslessresultant secretimageatthereceiversideasthatofVC-CBasshownin Fig.4,Fig.5andFig.6.



Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
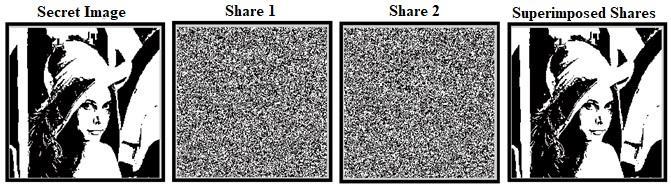
The main difference between RG-VC and VC-CB lies in their complexity, efficiency (generation time), share size, storagerequirementandcomputationalresourceswhichare describedasfollows
RG-VCgeneratessharesusingarandomgridofblackand whitepixels.Thecomplexityprimarilydependsonthesizeof the secret image (dimensions M X N), resulting in a time complexity of O (M X N). This approach involves straightforwardoperationsforsharegeneration,makingit relativelysimple.
VC-CBgeneratessharesbasedonpre-definedpatternsor templatesstoredinacodebook.Thecomplexitydependson thesizeofthecodebook(K)andthenumberofblocksinthe secretimage(B).Therefore,thetimecomplexityisO(KXB). Generation of shares using templates from the codebook involvesadditionallookupoperationsandXORoperations, which may result in a higher computational complexity comparedtoRG-VC.
RG-VC typically involves simpler operations for share generation, which may result in faster generation times comparedtoVC-CB,especiallyforsmallerimages.However, forlargerimages,thetimecomplexityofRG-VC(O(M×N)) couldbecomealimitingfactor.
VC-CB:VC-CBcanbemoreefficientintermsofsharesize andstoragerequirementssinceitgeneratessharesbasedon predefined templates. By selecting appropriate templates from the codebook, VC-CB can achieve a more compact representationofsharescomparedtoRG-VC.However,the initial setup involving the creation and storage of the codebookmayrequireadditionalcomputationalresources.
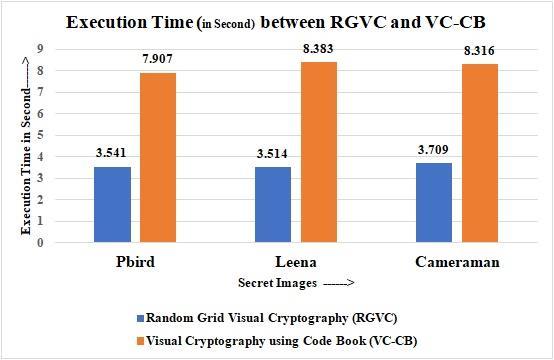
From above Fig. 7, it is clear that RG-VC comparatively require half of the execution time as that of Visual Cryptography using codebook
5.3 Storage requirement
VC-CBcanpotentiallyoffermorecompactrepresentations ofshares,leadingtolowerstoragerequirementscompared withRG-VC,especiallywhendealingwithalargenumberof Shares[20]
VC-CBmayprovidemoreflexibilityintermsofcontrolling share properties and security levels by designing and managingthecodebookappropriately.
5.5
VC-CBmayrequiremorecomputationalresourcesinitially forthecreationandstorageofthecodebook.However,once the codebook is generated,share generation may be more efficientcomparedtoRG-VC,particularlyforlargerimages.
This paper provides a comprehensive comparison of two Visual Cryptography techniques: VC-CB and RG-VC. RG-VC offers simplicity, efficiency, and perfect security, makingit suitableforsecureimagesharingandauthentication.VC-CB provides scalability and flexibility, ideal for multi-party authenticationandsecureprinting.
Futureresearchcouldexplorehybridapproachescombining the strengths of both methods and investigate new

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
applicationsinemergingfieldssuchasIoTandblockchain and developing efficient algorithms for large-scale VC applications.
The authors acknowledge the support received from the MAHAJYOTI, Nagpur and School of Technology, Swami Ramanand Teerth Marathwada University, Nanded, SubCampus,Peth,Laturforconductingthisresearch.
[1] ShruthiHR,RanjanKumarHSandPrasannaKumarH R,“AVisualSecretSharingTechniqueforSecure And FastTransmissionofImage,”InternationalJournalof InnovativeResearchinComputerandCommunication Engineering,Vol.2,Issue4,April2014
[2] S. Shivani, “Multi secret sharing with unexpande meaningfulshares,”Multimed.ToolsAppl.,vol.77,no. 5,pp.6287-6310,Mar.2018,doi:10.1007/s11042-017453
[3] M.NaorandA.Shamir,“Visualcryptography”, in Proc. Adv.Cryptology-Eurocrypt,vol.950.1995,pp.1–12.
[4] O. Kafri and E. Keren, “Encryption of pictures and shapesbyrandomgrids,”Opt.Lett.,vol.12, no.6,pp. 377–379,Jun.1987.
[5] S.J.Shyu,“Imageencryptionbyrandomgrids,”Pattern Recognition.,vol.40,no.3,pp.1014–1031,2007.
[6] Y.F.Chen,Y.K.Chan,C.C.Huang,M.H.Tsai,Y.P.Chu, “Amultiple-levelvisualsecretsharingschemewithout imagesizeexpansion”,Inform.Sci.177(21) (2007) 4696–4710.
[7] T.H.ChenandK.H.Tsao,“Thresholdvisualsecret sharingbyrandomgrids,”J.Syst.Softw.,vol.84,no.7, pp.1197–1208,2011.
[8] Y.Hou,S.WeiandC.Lin,“Random-Grid-BasedVisual CryptographySchemes,”IEEETransactiononCircuits andSystemsforVideoTechnology,vol.24,No.5,May 2014
[9] ChandramathiS.,RameshKumarR.,SureshR.and HarishS.,“Anoverviewofvisualcryptography,”Int.J. Comput.Intell.Tech.,vol.1,no.1,pp.32-37,2010.
[10] G.Ateniese,C.Blundo,A.DeSantis,andD.R.Stinson, “Visualcryptographyforgeneralaccessstructures,” Inf.Comput.,vol.129,no.2,pp.86-106,Sep.1996, doi:10.1006/inco.1996.0070.
[11] G.Ateniese,C.Blundo,A.DeSantis,andD.R.Stinson, “Extendedcapabilitiesforvisualcryptography,”
TheoreticalComputerScience,vol.250,no.1-2,pp. 143-161,Jan.2001,doi:10.1016/S03043975(00)00220-5.
[12] T.H.ChenandK.H.Tsao,“Thresholdvisualsecret sharingbyrandomgrids,”J.Syst.Softw.,vol.84,no.7, pp.1197–1208,2011,doi:10.1016/j.jss.2011.02.017.
[13] Y.Hou,S.Wei,andC.Lin,“Random-Grid-BasedVisual Cryptography Schemes,” IEEE Trans. Circuits Syst. VideoTechnol.,vol.24,no.5,pp.733-744,May2014, Doi: 10.1109/TCSVT.2013.2273735.
[14] R.R.M.KumarandS.P.Raj,“Asurveyonvisual cryptographyschemes:Techniquesandapplications,” JournalofInformationSecurity,vol.5,no.2,pp.87101,2014,doi:10.4236/jis.2014.52010.
[15] Y.F.Chen,Y.K.Chan,C.C.Huang,M.H.Tsai,andY.P. Chu,“Amultiple-levelvisualsecretsharingscheme withoutimagesizeexpansion,”Inform.Sci.,vol.177, no. 21, pp. 4696–4710, 2007, doi: 10.1016/j.ins.2007.04.018.
[16] T.H.ChenandK.H.Tsao,“Thresholdvisualsecret sharingbyrandomgrids,”J.Syst.Softw.,vol.84,no.7, pp. 1197–1208, Jul. 2011, doi: 10.1016/j.jss.2011.02.017.
[17] S.J.Shyu,“Imageencryptionbyrandomgrids,”Pattern Recognition,vol.40,no.3,pp.1014–1031,2007,doi: 10.1016/j.patcog.2006.08.003.
[18] M.K.Lee,J.J.Kim,andS.H.Kim,“Asecureand FlexibleVisualcryptographyschemeusingcodebook forprotectingimagesecrets,”JournalofVisual CommunicationandImageRepresentation,vol.29, pp. 166-175, Jul. 2015, doi: 10.1016/j.jvcir.2015.04.010.
[19] G.Deepa,“TheComparativeStudyonVisual CryptographyandRandomGridCryptography.”IOSR JournalofComputerEngineering(IOSR-JCE),Volume 12,Issue,PP04-14,2May-Jun.2013.
[20] H.K.Lee,T.T.Lee,andS.W.Lee,“Efficientandflexible visualcryptographyschemewithsecretimage recovery,”JournalofComputerScienceand Technology,vol.25,no.4,pp.761–773,Jul.2010,doi: 10.1007/s11390-010-0976-2.