
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
Tejasva Jadhav
Cybersecurity Research Enthusiast, BCA Graduate Birla Institute of Technology Mesra, Jaipur Campus Jaipur, Rajasthan – 302017, India
Email: Jadhavrk2007@gmail.com
Abstract - This research proposes a dual-layer surveillance framework aimedat enhancing bordersecuritybyintegrating AI-powered satellite imagery analysis with communicationlevel cybersecurity threat monitoring. The visual layer uses machine learning models such as YOLOv8 and Vision Transformers to identify unauthorized troop gatherings, suspicious vehicle movements, or sudden terrain alterations near sensitive border regions. Concurrently, the cybersecurity layer monitors wireless traffic, GPS spoofing attempts, and potential signal jamming, providing a hybrid defense against both physical and digital intrusions. This unified system addresses modern hybrid warfare challenges and proposes a scalable model for use by defense and intelligence agencies)
Key Words: BorderSecurity,SatelliteSurveillance,AIThreat Detection, Cybersecurity, GPS Spoofing, Signal Jamming, IntrusionDetection
1.INTRODUCTION
India’sborderregions especiallyalongtheLoCandLAC havefacedincreasingthreatsfrombothphysicalintrusions andmoderndigitalwarfare.Incidentslikethe2020Galwan Valley clash and frequent drone incursions in Punjab and Jammu underscore the need for real-time, wide-area surveillance.Simultaneously,cyberoperationssuchasGPS spoofing, signal jamming, and network intrusion have targeteddefenseinfrastructureandbordercommunications
Traditional methods manned posts, drones, and ground sensors arelimitedbyterrainandlatency.Withadvances in AI and satellite imaging, it is now feasible to automate bordersurveillanceanddetectcyberthreatssimultaneously.
Thispaperproposesadual-layersystemcombiningAI-based satellitevisionwithcommunication-layerthreatdetection offeringreal-timesituationalawarenessofbothphysicaland digitalthreatsacrossborderzones.
Manystudieshaveexploredsatelliteimageanalysisusing convolutionalneuralnetworks(CNNs),objectdetectionvia YOLO, and Vision Transformers for identifying terrain changes or large vehicles. Separately, research in cyber
defensehasfocusedonnetworkintrusiondetectionsystems (IDS),GPSspoofingdetection,andelectromagneticjamming countermeasures.
However,currentliteraturelacksacombinedsystemfor border surveillance that fuses satellite imagery with cybersecurity intelligence. This paper fills that gap by proposing a two-layered approach for simultaneous monitoring.
2.1 Layer 1: Satellite Surveillance with AI
Thislayerfocusesonmonitoringphysicalactivityinand around border areas using satellite imagery combined with artificial intelligence. With advancements in computervision,satellitedatacannowbeprocessedin nearreal-timetodetectthreatsorunauthorizedactions withoutrelyingsolelyongroundpersonnel.
Unauthorizedmilitaryencampments:
AI models can identify patterns resembling temporaryorpermanentmilitarycamps suchas tent arrangements, vehicle clusters, or artificial structures especially in previously unoccupied zones. This helps in flagging possible infiltration basesorforeigntrooppresence.
Convoyorvehiclemovement:
Movement of groups of vehicles, especially in sensitive regions, is detected through frame-byframecomparisonofimagery.Thesystemcantrack movement patterns, distinguish military vehicles from civilian ones, and alert authorities in case of unusualactivity.
Terrain disruption near fenced or sensitive areas:
Changes in land texture or topography, such as digging,trenchformation,orcollapsedfencing,can indicate intrusion or tunneling attempts. These anomaliesaredetectedusingsemanticsegmentation andchangedetectionalgorithms.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072
A deep learning pipeline continuously processes incoming satellite images, comparing them to previous frames, and automaticallyraisesalertsforanomaliesbasedonpredefined threat signatures. The entire system is GPS-integrated, providing accurate geolocation data for rapid response. Trainingcanbeconductedonopen-sourcesatellitedatasets or synthetic datasets created to simulate various threat scenarios.
Thislayeraddsadigitaldimensiontothebordersurveillance framework by detecting and preventing cyber-based intrusions or disruptions. As border infrastructure increasingly relies on smart sensors and wireless communication, securing these digital channels becomes critical.
Monitoring of wireless signals (Wi-Fi/LoRa) in bordersensornetworks:
WirelessprotocolslikeWi-FiandLoRaareusedto connect surveillance devices, sensors, and communicationsystems.Thislayerensuresthatany unauthorizedaccessattempts,roguetransmissions, or suspicious changes in signal behavior are promptlyidentified.
GPS spoofing detection using sensor fusion and timinganalysis:
GPS spoofing can misguide autonomous systems, UAVs,orvehiclesbysendingfalsepositioningdata. Thesystemusessensorfusion combininginputs from multiple sources like IMUs and satellite signals along with precise time discrepancy analysistodetectsuchattacks.
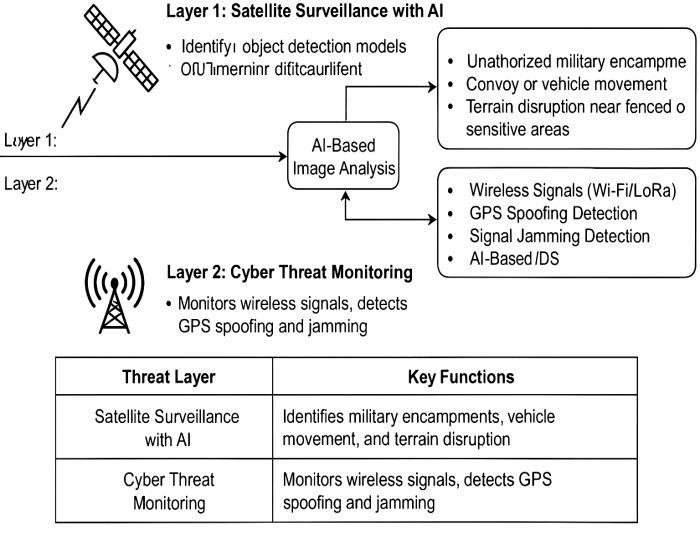
Detection of signal jamming or denial-of-service attacksoncommunicationnetworksSignal:
jamming can disable surveillance networks by flooding communication channels. This system monitors for unusual signal patterns, high packet loss,orlatencyspikes,whicharesignsofjammingor DoSattacks.
LightweightanomalydetectionusingAI-basedIDS:
An intrusion detection system (IDS) powered by lightweight machine learning models runs at the edge, continuously scanning network traffic for anomalies.Itcanidentifyunknownattackvectorsor protocolmisusewithoutrelyingonbulkysignaturebasedmethods.
This paper proposed a dual-layer surveillance framework combining AI-based satellite image analysis with cyber threatdetectiontoenhancebordersecurity.Thevisuallayer detectsphysicalthreatssuchasunauthorizedencampments andterraindisruptionsusingmodelslikeYOLOv8,whilethe cybersecurity layer monitors GPS spoofing, jamming, and wirelessanomalies.
Together, these layers provide real-time situational awareness and early threat detection, addressing both physical and digital vulnerabilities. The integration of AI enablesautomatedmonitoring,reducinghumaneffortand responsetimeincriticalscenarios.Additionally,theuseof low-power networks and scalable architectures ensures suitabilityforremoteandresource-constrainedregions.
The proposed system offers a scalable and cost-effective solutionfordefenseapplications,withstrongpotentialfor integration into national surveillance infrastructure and smartbordertechnologies.
[1]J.Redmon,S.Divvala,R.Girshick,andA.Farhadi,“You OnlyLookOnce:Unified,Real-TimeObjectDetection,” in Proc. IEEE Conf. Comput. Vis. Pattern Recognit. (CVPR),2016,pp.779–788.
[2]A.Dosovitskiyetal.,“AnImageisWorth16×16Words: Transformers for Image Recognition at Scale,” arXiv preprint arXiv:2010.11929,2020.
[3]S. Bhosale, R. Patil, and M. Kale, “Cybersecurity ChallengesinBorderManagement,”in Proc.IEEEConf. Cybersecurity Trends,2021,pp.45–50.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
[4]A.Kaushik,“DetectionofGPSSpoofingAttacksinCyberPhysical Systems,” in Advances in Computer CommunicationandComputational Sciences,Springer, 2022,pp.123–130.
[5]G. Mishra, “AI and Satellite Imaging for Border Monitoring,” ISRO-DRDO Research Digest,vol.12,pp. 33–38,2023.
[6]A. Z. Khan, “Low-Power Anomaly Detection in LoRa Border Networks,” Int. J. Res. Appl. Sci. Eng. Technol. (IJRASET),vol.11,no.6,pp.900–905,2023
BIOGRAPHY

Volume: 12 Issue: 06 | Jun 2025 www.irjet.net p-ISSN: 2395-0072 © 2025, IRJET | Impact Factor value: 8.315 | ISO 9001:2008 Certified
Tejasva Jadhav is a BCA graduate specializing in AI-based security and cyber-physical threats, preparing for anM.Sc.inCybersecurity
| Page268