
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
Ashish Kumar Mishra1 , Deepshikha2
1Master of Technology, Computer Science and Engineering, Lucknow Institute of Technology, Lucknow, India
2Assistant Professor, Department of Computer Science and Engineering, Lucknow Institute of Technology, Lucknow, India
Abstract - Cloud databases have become the rapid adoption which has revolutionisedthe aspect of storing and management of the data with the help of scalability, flexibilityandsavingof cost.Butthismovehas introduced a lot of privacy concerns, because a lot of sensitive data is stored and processed on third party servers. Confidentiality and integrity of data are of utmost importance in controlling risks involved in cloud environments like unauthorized access, data breach, insider threat, etc. Addressing the above challenges, cryptographic techniques have been proven as a cornerstone to provide privacy preserving storage of data without compromising on functionality. The present review paper analyzes techniques of cloud databases' cryptographic methods such as symmetric and asymmetric encryption, homomorphic encryption, searchable encryption, attribute based encryption (ABE), secure multi party computation (SMPC), differential privacy. We are then able to evaluate these techniques in their security, performance, and practicality, and specify strengths and shortcomings. Furthermore, we detail key challenges like computational overhead, key management and complying with regulatory standards. Finally we outlines future research direction such as post quantum cryptographic scheme, lightweight cryptographic scheme and integratedcryptographic scheme with artificial intelligence (AI) for better privacy preservation. The objective of this paper is to provide the researchers and practitionerswithasolidbackgroundonthestate oftheart approaches for privacy preserving data storage in cloud databasesandtosuggestmethodsontheiradvancement.
Key Words: Privacy-Preserving Data Storage, Cloud Databases, Cryptographic Techniques, Homomorphic Encryption, Searchable Encryption, Attribute-Based Encryption(ABE),DataConfidentiality.
1.1.Background and Motivation
The role of cloud databases in modern computing is so hugethatitcanverywellbedescribedasacornerstoneof modern computing. Unparalleled scalability, flexibility, and cost efficiency for data storage and management are theusualthemesthatclouddatabasesplaywith.Inrecent times, organizations with their diverse business are
shiftingtheirdatatothecloudplatformstotakeadvantage of these benefits. While this has however increased privacy and security concerns. Since the sensitive data is stored in third party servers, it increases the concern of unauthorized access, data breach and insider threat. Because of the cloud environment characteristics that are common and distributed, data confidentiality, integrity and availability have become top priorities. However, these challenges can be tackled using privacy preserving mechanisms, which enable users to securely store and processthedataandalsodonotloseonfunctionality.This goal has been achieved using cryptographic techniques and offered strong solutions on how to protect data residinginadatabaseincloud.

1.2.Problem Statement
Butasyoucansee,alltheseadvantagesofclouddatabases don’t necessarily mean that you are not faced with any challengesifyouusesuchstructures,especiallyintermsof dataprivacy.Itisnoteasytoensurethatthesensitivedata thatarestoredinthecloudissecure;withmanyriskssuch as an unauthorized access, data leakage, or even insider threats. Resources are also shared in the cloud: eavesdropping,andmoredangeroussidechannel exploits arepossiblebetweencustomersbeingservedbythesame resource.) On top of these are legal and regulatory risks,

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
not to mention those pinpointed regulations as the General Data Protection Regulation (GDPR) or Health Insurance Portability and Accountability Act (HIPAA). To address these challenges, solutions must be unique in order to create the balance among security, performance, andusability.
1.3.Objectives
The primary contribution of this paper is to deliver a detailed review of cryptographic methods for conducting privacypreservingdatastorageinclouddatabases.Ittries toidentifystrengths,limitationsandapplicabilityofthese techniques in the real world cloud environments. The paper aims to learn exactly how effective these tools are for addressing privacy concerns, by way of evaluating the current state of the art and identifying areas for improvement. In addition, it points out the tradeoff that comes with deploying cryptographic solutions, and explains how the latter may be used to address the changingdatastoragerequirementsofcloudstorage.
2.OVERVIEW OF CLOUD DATABASES AND PRIVACY CONCERNS
2.1.Cloud Database Architecture
Modern cloud databases are key components of the systems that store, manage and process data over distributed environments. Insightsonhow they adopt the resources of cloud service providers to provide scalable, optimal and cost effective solutions for data storage and accessing are given. Cloud databases are often composed ofseveralparts,themainonesbeingstorage,computation andmanagement.Thestoragecomponentistheonewhich storesthedatainthedataacrossmanydistributedservers and provides redundancy and fault tolerance. The compute component serves to perform query execution and data processing with the help of the distributed computing frameworks for stream processing of enormous workloads. The database administration tools such as monitoring, access, and optimization of the database by the management component. There are two broad categories to which cloud databases can be classified;NoSQL(non-relational)clouddatabaseandSQL (relational) cloud database. For instance, SQL databases likeMySQLandPostgreSQLareperfectforstructureddata and heavy complex queries.[6] On the other hand, NoSQL databases like MongoDB and Cassandra are more applicable for unstructured or semi structured data with highscalabilityandhighflexibility.Whichofthesetypeto choose depends on the exact requirements of the application, data structure, query complexity, and how nicelyitneedstoscale.

Althoughtheyareincrediblyuseful,clouddatabasesentail several privacy issues because they are so shared and distributed. Confidentiality, integrity, and availability of data are critical and any compromise could cause loss of money, legal implications and a bad name. Confidentiality of data pertains to keeping sensitive information away from unauthorized access and integrity of data to keep data accurate and unaltered. Availability precludes the situation where authorized users are not able to access data when needed. In cloud environment, there are many users and applications sharing the same infrastructure; hencethreatstothoseprinciplesareabundant.Incloudit faces the risk of data leakage, unauthorized access and eavesdropping. Attackers could take advantage of severe vulnerability in cloud infrastructure or tap the data traveling in transit. These risks are worsened when combined with insider threat, where malicious actors withintheorganizationusetheirprivilegestoabusethem. Cloud databases must also adhere to very strict legal and regulatory rules and regulations including the General Data Protection Regulation which is applicable in the European Union and the Health Insurance Portability and Accountability Act which applies to the United States. In additiontoclouddatabasemanagement,theseregulations requirekeencontroloverwheredataisstored,processed, andshared,furthercomplicatingtheprocess.
The tool I apply to overcome the privacy problem of database of clouds is cryptography. To ensure that sensitiveinformationissafefromallthemaliciousparties that attempt to intercept it, data is both encrypted at rest and in transit with cryptographic techniques. Encryption keeps data unreadable byconvertingitintoa form that is unreadable, and such data is only readable now with the right keys for maintaining confidentiality. Data integrity verifying mechanism such as digital signatures and hash functionsthatdeterminealterationofdataareavailablein the cryptographic techniques. On top of this, you are able toalsoachievesecureaccesscontrolandensureaccessto

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
changingorreadingdataforanauthorizeduser.Although it has a price, which is, it is secured based on security, performance, and usability trade offs. However, encryptingthedatastronglyincreasesdatasecurity,butat the same time it also increases overhead of computation and latency thereby reducing the system performance. They may also be faced with the same challenges that affect usability of complex cryptographic protocols that require significant expertise to implement and manage. When building privacy preserving mechanisms for cloud databases, such a balance is key on striking. Considering factors like sensitive data, performance constraints, and regulatory compliance, cryptographic solutions for the world of application have to be customized. Using Cryptography, we can reduce the potential risks of violating privacy, and earn trust in data storage systems basedoncloud.
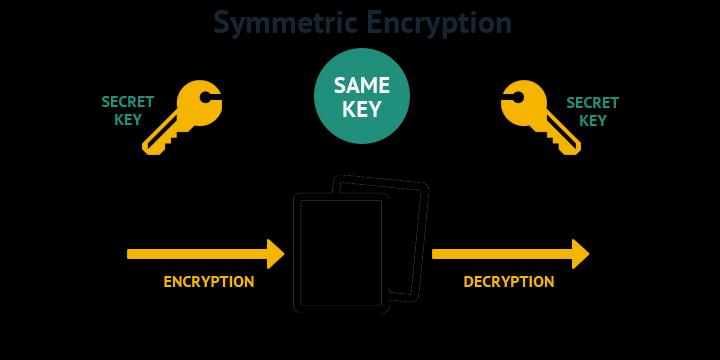
Among the different cryptographic techniques, symmetric key cryptography is one of the most used to guarantee data privacy in cloud databases. It is accomplished with a great efficiency and speed using one key for encryption anddecryption.ItiscommonlyusedbecauseAEShashigh security and good performance. For encryption of large amounts of data at rest in a cloud database, symmetric encryptionisoftenusedbecausethesensitiveinformation is still kept confidential even if storage infrastructure is compromised. It is applicable in the real time scenario because of its efficiency and its low latency is of utmost importance. However, symmetric key cryptography has somerestrictioninkeymanagementarea.Whenweareon shared environment (multi users) then securely sharing and storing the encryption key is tough and if the key anyone broke then all the data gets compromised. However, these work, and many others, make it possible, and symmetric encryption is therefore an extraordinarily usefultoolinkeepingdataprivateinclouddatabases.
Asymmetrickeycryptosystemorpublickeycryptography employs a pair of keys i.e. one key for encryption and other key for decryption. A popular algorithm is the RSA (Rivest Shamir Adleman) or ECC (Elliptic Curve Cryptography).Thisisa veryuseful technique forsharing securedataandkeysinclouddatabases.Forinstance,data is encrypted with the recipient’s public key so that only the recipient can decrypt the encrypted data using their privatekey.Asymmetricencryptioneliminatestheneedto storeasinglekeythereforereducingtherisk thatasingle key could be compromised. It is also widely used to generate digital signatures that verify the integrity of the data and ensure its authenticity. But general encryption that is asymmetric is really computationally expensive, making it unfeasible to use the compute power necessary to encrypt large datasets. Thoughlimited in this way,it is essential in allowing secure communication and service accesscontrolinthecloud.
Homomorphic encryption is a groundbreaking cryptographictechniquewhichallowsforcomputationsto directlybeperformedacrossencrypteddata withoutever having to decrypt it. This allows for privacy preserving dataprocessinginclouddatabases(i.e.,wherethecontrol volume floats in the cloud, rather than being tethered to physical servers) for application such as secure data analytics, and machine learning. For instance, an encryption service provider can perform computation on an encrypted data for the user and return the encrypted result to the user, who then decrypts locally. This protection as private way prevents the raw data to be exposed to the cloud provider. Unfortunately, homomorphic encryption is unfortunately plagued by quite grave performance and scalability issues. This, however, renders impracticable for several real time applications due to the need for too much computational overhead involved in homomorphic operations to comparewithtraditionalencryption.Stillfurther,research isongoingtomakeiteasiertouseinclouddatabaseswith homomorphicencryption.
Searchable encryption is a cryptographic technique that allows encrypting data and search over it without decrypting it. It is especially useful for cloud databases in which user queries on encrypted datasets while maintaining privacy. With Symmetric Searchable Encryption (SSE), users can query the ciphertext with keywords and receive the results that are relevant. This guarantees that the cloud provider is oblivious of the plaintext of the data and the search queries. Searchable encryptionhowever,comesatthecostofsearchefficiency vs. security. Additional computational resources are often

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
needed for more secure schemes and they may affect performance. However, searchable encryption is one of thebestapproachestoallowingsecureandefficientquery processinginclouddatabases,despitethetrade‐offs.
AttributeBased Encryption (ABE) is a cryptographic approach, which allows to realize finegrained access control, encrypting a data using a user attribute. In cloud databases, ABE enables dynamic access policies in that data can be encrypted so that only users with certain attributes (e.g., role, department, or clearance level) can decrypt them. ABE make it especially useful in environments where people access the system and thus the access control enforcements need to be flexible and secure. For example, healthcare cloud database can be encrypted so that patient records are only accessible to the authorized medical staff. However, the key management and policy definition associated with ABE becomemorecomplexastheencryptionanddecryptionof thedatarelyontheattributesandpoliciesrelatedwiththe data.However,ABEisapowerfultoolforprovidingsecure and scalable access control for cloud databases, above thesechallenges.
SecureMultiPartyComputation(SMPC)isacryptographic method to allow a set of parties to jointly compute a functionality over their inputs avoiding that any of the partiesleaktheirindividualinput.SMPCisuseful incloud databases where several users or organizations should process the distributed data among themselves and without revealing private information, e.g., fordistributed data processing. For instance, financial institutions can jointly perform risk assessment using SMPC and avoid revealing their proprietary data. Because only the final computation results are shared, SMPC ensures the confidentiality of the raw data. However, SMPC is computationally intensive and limited for large scale coordination amongst participants, thereby making it infeasible in large scale cloud environment. However, these have to be overcome, for SMPC is a promising method to facilitate privacy preserving collaboration basedonclouddatabases.
A cryptographic technique that allows for preserving privacy in aggregate data analysis is differential privacy. The way it does it is by making the result of its data queriesnoisier,ina carefullycontrolled way,so that each data point cannot be inferred from the result. Differential privacyiswellusedinapplicationsoftheclouddatabases such as data analytics and machine learning where aggregate insights are required without leakage of sensitive information. For instance, differential privacy
can be adopted by a cloud analytics platform to create statistical reports while keeping individual users out of them.Differentialprivacyisthusanimportantnotion,yet, asever,a key challenge istofind ways to balanceprivacy withdatautility.However,ifnoiseisaddedtoomuch,the accuracy of results will be compromised; however, if too littleisadded,privacycanbecompromised.Nevertheless, differentialprivacyisaveryimportanttoolforsupporting privacypreservingdataanalysisincloudenvironment.
4.1.Security
Sincesecurityisonethemajorconcernswhenwewantto evaluate cryptographic techniques for privacy preserving data storage in database in the cloud, it is obviously important. Different techniques are equally resistant to the common attacks like brute force attack, side channel attack etc. AES is a representative of symmetric key cryptography,whichisbasedonlargekeysizesandstrong algorithmsallowingtoprotectagainstbruteforceattacks. Nevertheless, it is susceptible to key management problems; compromisation of one key implies all encrypted data. The reason is owing to asymmetric key cryptography like RSA and ECC which are more secure as itusestheseparatekeysforencryptionanddecryptionso astomakethekeycompromiselittlemoredifficult.Yet,it can be attacked on its mathematical foundations – being abletofactorlargeintegersorsolveellipticcurvediscrete logarithms – which is the scope of this thesis. In fact, homomorphic encryption provides the ultimate security for privacy preserving computations as the data is never decrypted during processing. But, it is prone to side channel attacks as well as relies on very complex mathematical operations. Searchable encryption provides the means for querying on encrypted data while maintaining a desired security which depends on the scheme and the trade off between search efficiency and privacy. However, its security is based upon a compound with the proper management of attributes and policies. Secure Multi Party Computation (SMPC) guarantees confidentiality of the data during joint processing, howeversecurityoftheSMPCreliesonthehonestyofthe contributingpartiesandthestrengthofthecorresponding protocols. Differential privacy focuses on protecting an individual’s data point in aggregate analysis but its securityisdependentoncarefulcalibrationofnoiselevels. There are uniquesecurity strengths and vulnerabilitiesof each one and the choice depends on the specific threat modelandapplicationrequirements.
Cloud databases, adoption of cryptographic technique, depends upon performance, which decides efficiency of system and user experience. The most efficient of the

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
threeissymmetrickeycryptographywhichallowsforfast encryption and fast decryption without a lot of overhead on the computer. This means it is good for encrypting a large amount of data in real time applications. Although asymmetric key cryptography is much more secure, it is computationally expensive and hence latency intensive, thus, not a very good fit for large scale data encryption. Although groundbreaking in capabilities, homomorphic encryptionhasseverescalabilityissuesandcomputational overhead, and is therefore not competitive in practical terms for real time applications. Searchable encryption offers a reasonable tradeoff between functionality and performance but its efficiency is not sensitive dependent on the specific scheme and the complexity of the queries. In addition to this, mechanisms for fine grained access control introduced by ABE result in additional computational complexity which can influence performance in large deployments. SMPC is very expensive as it involves extensive communication and coordination with the participating parties, which hurts scalability. Efficient in terms of computation, differential privacy is however highly sensitive to the parameters associated with privacy and data utility, which can make analyticsinaccurateandslow.Inshort,theperformanceof cryptographic techniques spans a wide range and the choice depends on the application’s needs, e.g., latency, scalability,andresourceconstraints.
Nowadays, cryptographic techniques must be highly usable and practical to be successfully implemented in cloud databases. It is widely supported and easy to implement and so is a practical option for many applications. This, however, makes deployment in multiuser environment complex due to its key managementchallenges.Wemayfindtheasymmetrickey cryptography, though more complex, best for secure data sharing and key management, but also challenging to implement without some experience and infrastructure. Despite being still in early stages of adoption, homomorphic encryption lacks widespread support in existingcloudsystems,andsignificantexpertiseisneeded toimplementit.Theusabilityofsearchableencryptionfor allowingsecurequeriesisrelativelypracticalbutdepends ontheparticularschemeandthetrade-offsthathavebeen madebetweenfunctionalityandsecurity.But,deployment of attributes and policies may be complex enough that it may fall short. SMPC is however very specialized and highly coordinated among participants, so its integration into existing systems is difficult. However, the implementation of cloud based analytics is thriving, despitetheneedforcarefulcalibrationandexpertisewith respect to the more reinforced differential privacy. Usability and practicality of cryptographic techniques, in the broader sense, are related to ease of implementation, interoperability with existing systems and needed expertise.
By means of a comparative analysis of cryptographic techniques it becomes evident that no particular solution can work in all situations due to the tradeoffs between security, performance and usability that each of the techniquesimplies.Efficiencyand easeof implementation arethefeaturesofsymmetrickeycryptography,butwhilst it struggles with key management. However, asymmetric key cryptography is more secure, allows secure data sharing but also tends to be computationally expensive. However, homomorphic encryption is notoriously slow, making generalizability quite difficult. Searchable encryptionisgoodcompromisebetweenfunctionalityand security, but at the expense of a tradeoff between search efficiency and privacy. However, ABE provides fine grain access control, but complicates key and policy management. Although secure collaborative processing can be achieved with SMPC, it is resource intensive and hard to realize. However, the level of data utility must be carefully calibrated against individual data point privacy under differential privacy. To aid the decision making, a comparison table of strengths and weaknesses of each technique will be provided for easier selection of an appropriate approach based on specific cloud database applications. Through an understanding of these tradeoffs, organizations can make intelligence decisions towards the balance between performance, security, and usabilitydesired.
5.1.Performance Overhead
The biggest challenge in using cryptographic techniques for privacy preserving data storage in cloud databases is the security vs efficiency challenge. Finally, encryption as well as performing secure computations with computational overhead may reduce system performance and introduce latency. For instance, homomorphic encryptioncomeswithstrongprivacyguarantees,butdata processingisterrible.Symmetricencryptionisalsosecure but not efficient as asymmetric encryption; therefore, it can’t be used in real time applications with large databases. Particularly, the compromise between security and performance is incredibly critical when it is about cloud environment, where scalability and responsiveness are necessary. The solution to this challenge is to explore lightweight cryptographic algorithms and optimization techniques that achieve lightweight at the expense of computational overhead while retaining the level of security.In essence,therehastoexistanoptimal balance, which still remains an open issue, particularly for applications that require high levels of security as well as highlevelsofperformance.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
Key management is a fundamental requirement to effectively use of cryptographic technology in cloud databases.Cryptographickeygeneration,distribution,and storage are very complicated operations, especially in a large scale, multi-s user environment. For example, symmetric key cryptography entails secure facilities for sharing and storing keys (should a single key be compromised, all encrypted data will be exposed). This risk is mitigated by asymmetric key cryptography which uses different keys for encryption and decryption purposes,butalsoposesthechallengesofmanagingpublic and private key pairs. Moreover, Attribute Based Encryption (ABE), as well as Secure MultiParty Computation (SMPC) techniques have very sophisticated keymanagementsystemforthehandlingofattributesand policies, as well as distributed keys. Lack of good key management exposes the security vulnerabilities such as key leak or access by unauthorized person, which ultimately erodes the effectiveness of the cryptographic solution. A major challenge is to develop robust and scalable key management systems that are compatible withanexistingsystemofclouddatabases.
The other problem of cloud databases is that legal and regulatorystandardshavetobefollowedbycryptographic solutions. Organizations have to follow a complex landscape of privacy laws as well as industry specific regulationssuchastheGeneralDataProtectionRegulation (GDPR) in the European Union and the Health Insurance Portability and Accountability Act (HIPAA) in the United States. However, the restrictive rules set in place as regards the storage, processing and communication of data require the operators to resort to cryptographic techniques that ensure the good data confidentiality, integrityandavailabilitywarranties.However,conforming is not always easy, as cryptographic solutions need to be adapted to the specificities of a regulation. For example, under GDPR, data is supposed to be minimised and an individual has the right to erasure, which may not serve some of the cryptographies that rely on persistence of data. A challenge facing organizations that have to follow thiswhile still ensuring the security and functionalities of theclouddatabase.
The pace of technological advanced rapid that it provides too little of time in new threats to the development of traditional cryptographic techniques. One of the foremost emerging threats is quantum computing, which can efficiently break such widely used cryptographic algorithms as RSA and ECC, for example, by solving (for example) integer factorization and discrete log problem. Post-quantum cryptography is an area of research in
developing quantum resistant algorithms and there is a long way to go before all of the cryptographic primitives and algorithms are replaced by those based of these new techniques.Inaddition,duetotheriseofnewthreatssuch asAPT,sidechannelattacks,andAIbasedattacks,security for cloud databases becomes new challenge. A constant demandexists forcontinuousinnovationincryptographic techniques and proactive detection, as well as mitigation, ofvulnerabilities.Neitherthelongtermsecurityofdatain cloud environments, nor ensuring that data is secure and privateinthecloud,ispossiblewithoutsecuringdata.
Interoperability is a significant challenge in cryptographically securing various cloud platforms and database systems. Different architectures and protocols thatisclouddatabasesarebasedupon,makeitdifficultto guarantee compatibility and seamless cryptographic techniques integration. For example, a cryptographic solution built for applying to a SQL based cloud database may not work well with NoSQL. Further, as more cloud adoption leads to multi-cloud and hybrid cloud deployments with data distributed across multiple platforms, interoperability only becomes further complicated. The standardized protocols and frameworks are needed in order to achieve the protocols and frameworks that allow the cryptographic techniques to work consistently and securely across other systems. Although it is hard to achieve such a standardization because of the heterogeneity in cloud platforms and the fast evolution of the cryptographic technologies. To facilitate widespread adoption of privacy preserving cryptographic solutions in cloud databases, one must addresstheinteroperabilityissues.
This review paper, in conclusion, explored the part of cryptographic techniques in the abidance of private storing data in cloud database. It then analyses the strengths, weaknesses, and the applicability of either symmetric and asymmetric encryption, homomorphic encryption, searchable encryption, Attribute Based Encryption(ABE),SecureMultiPartyComputation(SMPC) and differential privacy. Each technique has its advantage and disadvantage in solving a particular privacy concern as data confidentiality, integrity, and secure data sharing, andthechallengesariseinperformance,keymanagement and scalability. This comparative analysis highlights that the choice of cryptographic solution depends on it having an optimized solution for the specific conditions that surround its application including the sensitivity of the data, the complexity of the queries, and the regulatory environment. Building trust (the equivalent of trust on a handshakefortraditionaldatabasesystems)towardcloud databases through cryptography is an absolute requirementinorderfororganizationstousethebenefits

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 04 | Apr 2025 www.irjet.net p-ISSN: 2395-0072
of cloud computing without succumbing to its risks of unintendedexposure,breach,andinsider.
This paper puts great emphasis on the fact that cryptographic techniques are becoming increasingly important in the era of computing in the clouds, where data private and security are unarguably of great importance. As cloud databases progress further, the demand for good cryptographic solutions will only increase.Despitethesechallenges,performanceoverhead, key management, regulatory compliance, new challenges such as quantum computing, and interoperability across differentplatformcloudsareallstillsignificantones.Why isthisaddressed,andhowdoweresolvetheseissues?We just touched on this, but it is essential to continue and innovate research, and collaborate with academia, industry, and policymakers to address them for future initiatives. Next is to create post quantum cryptographic algorithms,lightweightencryptionmethodsandAIdriven privacy preserving mechanisms. In parallel, moving forward, the need will also exist to fix cryptographic protocols and the frameworks, to guarantee interoperabilityandtakecryptotoagreaterextent.
1) Shoukat, M. A. Khan, and S. U. Rehman, "A survey on privacy-preserving techniques for cloud data storage,"IEEEAccess,vol.8,pp.456–470,2020.
2) R.A.Popaetal.,"Cryptographictechniquesforsecure cloud storage," in Proc. IEEE Symp. Security Privacy (SP),2013,pp.123–137.
3) C.Gentry,"Fullyhomomorphicencryptionusingideal lattices," in Proc. 41st Annu. ACM Symp. Theory Comput.,2009,pp.169–178.
4) M. Armbrust et al., "A view of cloud computing," Commun.ACM,vol.53,no.4,pp.50–58,2010.
5) D. X. Song, D. Wagner, and A. Perrig, "Practical techniques for searches on encrypted data," in Proc. IEEESymp.SecurityPrivacy(SP),2000,pp.44–55.
6) J. Bethencourt, A. Sahai, and B. Waters, "Ciphertextpolicy attribute-based encryption," in Proc. IEEE Symp.SecurityPrivacy(SP),2007,pp.321–334.
7) O. Goldreich, S. Micali, and A. Wigderson, "How to play any mental game," in Proc. 19th Annu. ACM Symp.TheoryComput.,1987,pp.218–229.
8) C. Dwork, "Differential privacy," in Proc. 33rd Int. Colloq.AutomataLang.Program.,2006,pp.1–12.
9) S. Kamara and K. Lauter, "Cryptographic cloud storage," in Proc. Int. Conf. Financial Cryptography DataSecurity,2010,pp.136–149.
10) M. Naveed, S. Kamara, and C. V. Wright, "Inference attacks on property-preserving encrypted databases," in Proc. ACM SIGSAC Conf. Comput. Commun.Secur.,2015,pp.644–655.
11) P. Mell and T. Grance, "The NIST definition of cloud computing," NIST Special Publication, vol. 800, no. 145,pp.1–7,2011.
12) Z. Brakerski and V. Vaikuntanathan, "Fully homomorphic encryption from ring-LWE and securityforkeydependent messages,"inProc.Annu. Cryptol.Conf.,2011,pp.505–524.
13) A. Boldyreva, N. Chenette, and A. O’Neill, "Orderpreserving encryption revisited: Improved security analysis and alternative solutions," in Proc. Annu. Cryptol.Conf.,2011,pp.578–595.
14) R. Agrawal, J. Kiernan, and R. Srikant, "Orderpreserving encryption for numeric data," in Proc. ACMSIGMODInt.Conf.Manage.Data,2004,pp.563–574.
15) M.Bellare,A.Boldyreva,andA.O’Neill,"Deterministic andefficientlysearchable encryption,"in Proc.Annu. Cryptol.Conf.,2007,pp.535–552.
16) S. Goldwasser and S. Micali, "Probabilistic encryption," J. Comput. Syst. Sci., vol. 28, no. 2, pp. 270–299,1984.
17) A. Juels and B. S. Kaliski, "PORs: Proofs of retrievability for large files," in Proc. ACM Conf. Comput.Commun.Secur.,2007,pp.584–597.
18) K.Ren,C.Wang,andQ.Wang,"Securitychallengesfor the public cloud," IEEE Internet Comput., vol. 16, no. 1,pp.69–73,2012.
19) Y. Zhang, J. Katz, and C. Papamanthou, "All your queries are belong to us: The power of file-injection attacks on searchable encryption," in Proc. USENIX Secur.Symp.,2016,pp.707–720.
20) L. Xu, X. Huang, and W. Susilo, "Post-quantum cryptography for cloud databases: A survey," IEEE Trans. Cloud Comput., vol. 10, no. 3, pp. 1234–1245, 2023.
21) T. Li, J. Li, and Y. Wang, "Lightweight cryptographic techniques for IoT-enabled cloud databases," IEEE InternetThingsJ.,vol.11,no.2,pp.987–999,2024.
22) A.Kumar,S.Sharma,andR.Singh,"Blockchain-based privacy-preservingdatastorageforclouddatabases," IEEE Trans. Dependable Secure Comput., vol. 12, no. 4,pp.567–580,2025.