

LINE CARD
European analytics firm sets up in Toronto
ACypriot software solution designed for video monitoring has come to Canada, establishing an office in the Toronto area. Kipod, based in Cyprus, was founded in 2009 and incorporated in Canada under the name Kipod Video Analytics. The solution offers mobile access, video content searching (for people, vehicles, events, etc.), incident management, video sharing, alarm-based alerts and reporting tools.
“You can preset different types of alert,” explains Vitaly Vishnepolsky, head of business development, at Kipod’s Toronto location. “They could be driven by events that are happening or sounds… You can
preset an alert based on gunshots or screams or a car crash or the sound of broken glass, etc.”
The solution can be used by end users, but Vishnepolsky says many of the clients are monitoring centres or telco operators who resell the service. The company has customers across Europe (it also operates a U.K.-based sales office) and North and South America. Utilizing a Cloud-based infrastructure, the software solution can be deployed on top of an existing VMS and the user pays a monthly service fee. An on-premise edge server version is also available.
— Neil Sutton
FLIR acquires DVTEL for US$92M
Wilsonville, Or.-based FLIR Systems announced late last year that it has acquired DVTEL for approximately US$92 million in cash.
DVTEL’s products include VMS and video analytics software, visible and thermal security cameras, as well as servers and encoders.

According to a statement from FLIR: The combination enables FLIR, with its existing FLIR-branded thermal and visible cameras as well as its Lorexbranded security systems, to be a
full-spectrum end-to-end security system provider, serving the consumer, small and medium business, enterprise and infrastructure-level markets.
“DVTEL adds a suite of professional-grade security software and hardware that is very complementary to our current solutions and fits very well with our strategy to offer end-to-end solutions in the enterprise and infrastructure segments of the security market,” says Andy Teich, president and CEO of FLIR, in a statement.
Tech Systems sets up Canadian operation
Antoinette Modica has joined American systems integrator Tech Systems to manage the company’s expansion into Canada.
Buford, Ga.-based Tech Systems was founded in 1987 by Darryl Keeler and now employs more than 250 people across 40 states. It serves
mostly enterprise customers across multiple verticals including health care, education, utilities, manufacturing and transportation. The company’s Canadian footprint up till now has been to manage customers north of the border from its U.S. operations and through local con-
tractor relationships. Many of those Canadian customers are owned by a U.S. parent that Tech Systems also serves.
By hiring Modica, the company aims to develop a much larger presence here.
“This is the next step [for me],”
says Modica, who was previously general manager at Mitsubishi Electric Sales Canada.
The initial target, says Modica, is to expand the customer base in Ontario and ultimately spread out across the country.
— Neil Sutton
Senstar acquires VMS and analytics expertise
Carp, Ont.-based Senstar, best known for its perimeter protection products, announced in April that it has purchased Waterloo, Ont.-based Aimetis.

The deal, according to Senstar’s parent company Magal S3, is valued at approximately US$14 million.
Aimetis is a developer of video analytics and video management software — technology that has obvious synergies with perimeter solutions,
says Stewart Dewar, product manager at Senstar. “One of the attractive aspects of Aimetis was that they have outdoor-quality video analytics that can — and are — being used for perimeter protection,” he says.
“[We are] answering that need that we haven’t been able to answer up until now… What if someone wants to use their camera system — and all the investments they’ve made in cameras and lighting, etc. — to get perimeter detection through analytics,” adds Dewar. “You can imagine it’s a perfect complement to a tradition sensor with the analytics. They can work very well together. People often want a certain degree of defence in depth.”
Up until now, Senstar did not integrate with Aimetis’ products, but that will be a top priority for Senstar in order to take full advantage of the technology.
Senstar currently supports numerous VMS manufacturers, including Genetec, says Dewar, and will continue to do so.
“We see [the Aimetis acquisition] primarily as a broadening of our portfolio,” says Dewar. “Now we have more to offer.”
Dewar says Aimetis will operate as a subsidiary under Senstar and its personnel will also be able to access and sell the Senstar portfolio into the markets they serve.
— Neil Sutton
Andy Teich, FLIR
Toshiba launches school support program
Toshiba’s surveillance division recently launched a new program to meet the needs of its K-12 and high education clients.
The program includes special pricing, but also places an onus on ongoing support, says Greg Hartzell, director of Toshiba Surveillance & IP Video Products, since uptime is vital to school users.
“What we’re really trying to do is meet the needs of an education institution. Surveillance is a high priority for them. What a lot of schools need to avoid the most is if there’s some sort of an incident and they go back to grab the video and the video is not there or not useable,” he says.

is able to offer, adds Hartzell, is a commissioning service where a Toshiba employee will perform a site visit in collaboration with the integrator who installed the equipment. The additional service will check that the systems are fully optimized, providing the best possible resolution, working within the school’s bandwidth limitations or available number of hard drives.
The company will also offer end user training to enable them to get the most out of their system — providing for viewing, searching and exporting of key video.
school district, drill down to an individual school and then select options including blueprints as well as indoor or outdoor camera feeds.
Users can receive automated reports on a daily, weekly or monthly basis, which will provide details on alerts, as well as day and night snapshots of every camera on the system to confirm they are fully operational (i.e. aimed properly, all in focus and providing good images both day and night). The reports by branded to the installing integrator, providing an additional touch point with the customer.
Samsung to become Hanwha

Tom Cook, Hanwha Techwin
A key element the company
As part of the school program, Hartzell says Toshiba will provide a mapping service that allows an administrator to view an entire
Hartzell says Toshiba has been offering these services more informally up till now, but decided to launch it as a program in a more official capacity since it has been well received. He adds that there are no plans currently to adapt it to other vertical markets and that it is well suited to the needs of educational institutions.
— Neil Sutton
Axis to market Canon products
Axis Communications has taken the lead on marketing Canon network video products in North America, Europe, the Middle East and Africa.
“If you’re a Canon reseller, you’re more than welcome.”
— Fredrik Nilsson,Axis Communications
The two companies combined in April 2015 when Canon agreed to acquire the Swedish security products company for US$2.8 billion. Up until now, there was little to report post-acquisition, with both companies maintaining their operations at arm’s length, but this new announcement signals a major change in how Canon surveillance products will be sold in North America.
Until recently, Canon had relied on manufacturer’s representative firms in North America, explains Fredrik Nilsson, vice-president, Americas, Axis, but those duties will now fall to Axis employees. The company has retrained 300 staff (a combination of tech support, marketing and sales) on the Canon portfolio, in order to bring those products to market here. Additionally, Axis’s established distribution and channel partners in Canada and the U.S. will have access to the entire Canon portfolio.

Fredrik Nilsson, Axis Communications
have been revised but there are no immediate changes on the horizon as far as R&D or branding is concerned, says Nilsson. As such, there is some overlap in the Axis and Canon portfolios, and it will be up to Axis staff to explain the best product fit for the customer base. However, he adds, Canon does have some specialized products in the PTZ and low-light categories that would have some appeal to certain verticals.
“We have to help the customer to choose the right product. The good thing is they all support ONVIF,” he says.
Samsung Techwin America is now known as Hanwha Techwin America.
The announcement comes just over a year after South Korea-based Hanwha first acquired the company.
“Basically, it’s a name change.”
— Tom Cook, Hanwha Techwin
Tom Cook, Hanwha Techwin’s vice-president of sales, North America, said during a conference call to media that it was otherwise business as usual for the company.
“Everything else remains the same. Our R&D, our manufacturing, our sales and marketing structure… Basically it’s a name change.”
The company wanted to make a public announcement prior to a dealer summit in Puerto Rico, as well as prior to ISC West, held in Las Vegas in April.
The Samsung name will continue to appear on the company’s surveillance products, at least until the company sees fit to make a change, said Cook.
“If you’re a Canon reseller and integrator, you’re more than welcome to join the Axis partner program. We have outreach to all of them,” explains Nilsson.
The go-to-market strategy may
Over the long-term, there will be more coordination between Canon and Axis product development, says Nilsson. “That will come, step by step.”
— Neil Sutton

“As we look down the future, it will be our decision… whether or not we keep the Samsung brand on our products or if we decide to change it to something else.”
Greg Hartzell, Toshiba
LINE CARD
Bosch and Sony to partner on video products and sales
Under a new partnership agreement, Bosch Security Systems’ sales and marketing organization will serve and support all of Sony’s video security customers worldwide, except in Japan.
Bosch Security Systems and Sony Corp. will also collaborate in the development of products and solutions in the field of video security applications.
Sony will bring its expertise in video image quality and performance to the partnership, while Bosch will add an extensive set of video analytics at the edge to interpret data as well as technologies to achieve efficient bitrates and mini-
“This unique partnership [with Sony] also supports Bosch’s vision concerning the Internet of Things.”
— Gert van Iperen, Bosch Security Systems
mum storage requirements.
“This partnership will revolutionize the video security industry since it combines the unique technological expertise and strengths of two leading companies in the field of video security applications. Customers can prosper from Sony’s superior image quality, like its 4K solutions, combined with Bosch’s bitrate management and video analytics,” says Toru Katsumoto, dep-
uty president of imaging products and solutions, sector president of professional products group, Sony.
“This unique partnership also supports Bosch’s vision concerning the Internet of Things. Video security cameras and more specifically the data they are collecting play an important role in the further development of the Internet of Things,” says Gert van Iperen, president of Bosch Security Systems.
Sony’s video security customers will be served and supported by a dedicated sales and marketing team within the Bosch Security Systems organization, offering customer support, after-sales service and training in different languages in more than 50 countries.
“The global Bosch Security Systems organization will support the dedicated sales and marketing team responsible for Sony-branded products as well as Sony’s customers to grow the business by excellent support and service,” van Iperen says. Sony will continue to develop and manufacture its video security products under its brand.
— Neil Sutton
Caliber touts cell-based surveillance service
An Ontario monitoring firm says it has patented technology that allows it to take advantage of cellular technology to transmit surveillance footage more effectively.
Stoney Creek, Ont.-based Caliber Communications, incorporated two and a half years ago, now holds about 12 patents related to a protocol modified from TCP/IP, as well as compression technologies that optimize transmission via cellular networks.
Company founder Alex Vourkoutiotis says the company has purchased OEM surveillance equipment and modified it such that it can achieve high speed transfer over cellular.
“LTE is a very fast medium to begin with and we’ve been able to push the envelope forwards,” says Vourkoutiotis. “At the same time, we can monitor our cameras remotely at our monitoring station through cellular 24x7 and stay within bandwidth limitations that make it very affordable and cost effective for us to do so without using any infrastructure from a remote site.”
The company’s additional patents cover range extension (using surveillance units further away from a cellular tower than would typically be possible) as well as low power consumption through solar-powered technology.

Caliber operates a monitoring centre from its office in Stoney Creek and is able to offer its clients Cloud-based services as well as some analytics on the back end (e.g. licence plate recognition and facial recognition) based on the clients’ requirements.
Most of the uptake for its service thus far has come from construction companies looking to monitor building sites — often in harsh
weather conditions (i.e., through the typical Canadian winter).
One particular construction customer, Aecon Group, used the company’s surveillance equipment, testing the effect of low light levels during winter on solar-based power sources. Vourkoutiotis says the equipment maintained 100 per cent uptime, even in the absence of daylight hours. Aecon wanted the equipment for one particular reason. It was measuring the impact of nearby trains of seismic activity and required video footage to be sure that the prescence of a train going by matched the seismic results.
Approximately 70 per cent of Caliber’s customers are in the construction business.
The other 30 per cent operate in markets the company is developing.
Caliber employs about 30 people including Gordon Stockdale, the company’s business development manager who joined earlier this year. Stockdale says retail is also an emerging market for Caliber, particularly on the supply chain management side. Stockdale was previously with GardaWorld before joining Caliber, and before that TJX Canada/Winners. Other potential markets include transportation, utilities, education, and municipalities.
— Neil Sutton
By Neil Sutton

IThe appetites of IT giants
f we don’t wake up and smell the coffee, Microsoft will eat our lunch.”
I’ve heard words to that effect for years now. And it’s not just Microsoft… IBM, Apple, Google, Cisco. All of these companies have been cited as potential disruptors of the physical security market. It’s almost as if their massive reputations are enough to cast a shadow over the entire industry.
I have serious doubts that will ever come to pass. Microsoft isn’t much more likely to take away your customers than Häagen Dazs is. I think the initial fear was that a company the size of Microsoft might decide it needs to create a physical security division and start blowing away the competition.
That hasn’t come to pass in a substantial way. The truth is that all the aforementioned tech companies participate in the physical security arena, but they do so in ways few expected them to.
Cisco has probably made the biggest overtures in the traditional physical space, but the main role that they and the likes of Microsoft and Amazon play today is in providing infrastructure






solutions for security.
I’ve been writing about the Cloud and how important it is for security for several years now. I can tell you, especially after visiting the most recent ISC West show in Las Vegas, that Cloud is here to stay. Its significance is almost on par with the advent of IP solutions in the surveillance world, partly because it’s an evolution of that same trend.
Ask a surveillance vendor how their Cloudbased offerings work and many of them will casually mention Microsoft or Amazon as an infrastructure partner. These companies have become part of the security ecosystem. They are more interested in providing bandwidth and hosting space than they are in challenging the traditional surveillance market with their own hardware solutions.
Admittedly, Google has stepped into the security equipment arena. Google’s acquisition of Nest, which later purchased Dropcam, has given the company immediate access to hardware, but even then, it’s tough to draw a straight line



between physical security and Google. It feels far more like the company is testing the waters of the as-yet unproven home automation market than a ploy to topple established camera manufacturers.
To suggest that the intentions of all these companies are completely benign is naïve, but I firmly believe they should be viewed as a support mechanism or as a partner rather than a threat.
The security industry is changing. Equipment, by itself, is no longer enough to impress customers. Camera resolution is nice to have, but it’s not always going to be the subject of the first question asked by the customer. A camera’s intelligence and ability to parse out complex data (i.e., analytics) is what will drive the security industry forward.
To be sure, Microsoft, IBM and all the others are going to play an increasing role in security, but I suspect they’ll bring their own lunch to the party. Everyone can go home feeling full.







































CAMERA CORNER
By Colin Bodbyl




TStore outside the core
Remote and edge-based technologies have increased surveillance storage options
he last major change in CCTV storage technology was when recording moved from VCRs to NVRs with hard drive disks, but now new storage techniques are fighting for market share. While hard drive disks in a local NVR are still the most popular choice for storage, two other techniques are quickly gaining popularity, Cloud storage and SD card or “edge” storage.
“Streaming video to the Cloud is a reliable back up for critical cameras or events.”
Cloud storage has rapidly gained popularity over the last few years for storing everything from family photos to company documents. Cloud storage has many things working in its favour including that it is constantly backed up so redundancy is standard. Up time on cloud storage is typically over 99.9 per cent and video can easily be accessed from anywhere in the world. As storage needs increase, end users can also add more Cloud storage with the click of a mouse, opposed to adding hardware, which would be necessary when adding storage to a local NVR.
For video surveillance however, Cloud storage has other unique challenges, the largest one being that HD video surveillance systems stream an enormous amount of data. For single camera systems that only store video on motion, Cloud storage is an acceptable choice. However, for commercial systems that either need constant recording, or have dozens of HD cameras, the Cloud often cannot handle the bandwidth. While streaming HD movies into a home is now

commonplace, this type of streaming relies on download bandwidth. Storing video in the Cloud relies on the upload speed of your Internet connection, which is typically far slower than download speeds.
For Cloud storage providers in the video surveillance space the challenges are obvious. The best solution these companies can provide is a hybrid version of Cloud storage, where traditional storage is still used onsite with only the most critical video being backed up to the Cloud.
On the opposite end of the spectrum is SD card storage, also known as edge storage. Integrators had mixed responses when manufacturers first introduced edge storage. Some thought it a brilliant method for reducing the cost of expensive NVRs. Others were concerned about the security of storing video on the camera. After all, what if someone destroyed the camera? All the recorded video would be lost.
The truth is, edge storage is near perfect on paper. Storing video
on each device significantly reduces the costs of the NVR and in some cases means users do not need an NVR at all. Storing video at the edge also means that there is no load on the network or bandwidth usage unless someone is actually viewing video from the camera.
The challenges with SD card storage stem from their intended use. SD cards were not designed to read and write video 24/7 for years on end. At best SD cards are designed for short intense bursts of use followed by hours or days of downtime. When SD cards are used as a storage method for constant video recording their lifespan is drastically reduced, and users risk SD card failure where recordings are completely lost.
While neither Cloud nor SD card storage works well as a primary means of storage for medium and large video surveillance systems, both technologies are excellent choices for redundancy or fail-over storage. Streaming video to the Cloud is a reliable backup
for critical cameras or events. SD cards offer an excellent method for failover recording, should a camera lose connection with the NVR.
Both technologies are also well suited for very small systems of less than four cameras. Rather than forcing homeowners to purchase an NVR to record a single camera, manufacturers can provide cost effective SD or Cloud storage options.
Local NVRs with hard disk drives will remain the dominant form of storage for video surveillance in the near future. However, it is a refreshing change to have both inexpensive options for small systems as well as alternative solutions for creating redundancy in larger systems.
For an industry that has historically been tied to VCRs and more recently NVRs any new storage options are a welcome change.
Colin Bodbyl is the director of technology for UCIT Online (www.ucitonline.com).
Product Previews Supplied by Bosch

New starlight camera family
Bosch Security Systems
Bosch cameras with new starlight technology are the gold standard in low light video performance. The latest starlight cameras now offer better light sensitivity, a choice of resolutions, dynamic ranges up to 120 dB and up to 60 frames per second. Plus, video analytics at the edge as standard, with no additional investment in license fees, makes high quality images more relevant.
us.boschsecurity.com

MIC IP 7000 HD
Bosch
Security Systems
The MIC family of ruggedized PTZ cameras provides reliable surveillance in the most difficult outdoor locations by combining high-quality HD imaging with an IP68/NEMA 6P-rated architecture. The cameras deliver the highest quality images in areas with extreme conditions like roads or highways, transportation facilities, city surveillance and critical infrastructure sites. They withstand a range of harsh conditions – from -40 to +60 degrees Celsius with up to 100 percent humidity to rain and snow, high wind gusts and significant vibration.
us.boschsecurity.com
For more information on products from Bosch Security Systems, view a recent video from Brian Wiser, president of sales for North America.

Video analytics at the edge
Bosch Security Systems

After only 20 minutes, operators can miss 90% of the activity on a screen. Video Analytics at the edge assists by alerting when predefined alarms are triggered. It adds metadata to video footage at the point of capture. This enables you to stream only what’s relevant, retrieve evidence quickly and trigger alarms when needed. In the next 12 months, Bosch IP cameras, IP 4000 family and above, will come fully equipped with video analytics at the edge as standard.
us.boschsecurity.com
FLEXIDOME IP panoramic camera family
Bosch Security Systems

DINION IP ultra 8000 MP
Bosch Security Systems
With the DINION IP ultra 8000 MP, Bosch enables you to see every detail, everywhere. Covering a large area and identifying objects at a great distance is challenging. That’s why the 4K ultra HD technology in this camera offers 12MP sensor resolution to deliver amazing detail even when zoomed in. The 30 FPS rate for a 4K ultra HD camera captures fast moving objects in high resolution. This provides the level of detail that makes the difference when collecting video evidence. us.boschsecurity.com

Blind spots can seriously undermine the reliability of a video surveillance solution. With the FLEXIDOME IP panoramic cameras, you will never have to deal with blind spots again. The cameras offer a full 180-degree or 360-degree overview in a single image, a choice of 5 or 12 megapixel resolution and high frame rates to ensure moving objects are easily captured. Choose FLEXIDOME IP panoramic cameras to oversee everything in superb clarity and significantly improve video surveillance operations.
us.boschsecurity.com
DINION IP bullet 4000 & 5000 cameras
Bosch Security Systems

The DINION IP 4000 and IP 5000 bullet cameras are designed to make installation easier with automatic varifocal and a dedicated surface mount box that enables fast and easy cable handling, while ensuring an IP66 dust- and watertight installation. With 720p or 1080p HD resolution they deliver detailed images, and built-in infrared illumination ensures object detection at a distance of up to 30 meters even at night.
us.boschsecurity.com


Bosch Video Management System 7.0
Bosch Security Systems
Bosch VMS 7.0 empowers security operators to effectively manage high-resolution video streams in their day-to-day work. Among the new features in Bosch VMS 7.0 is the use of streamlining technology to automatically show the optimal resolution on a screen. The Bosch VMS will use a lower-resolution stream when operators need to view many cameras simultaneously and switch to a higher-resolution stream when enhanced pictures are required. This latest version also encrypts communication between Bosch cameras and the VMS.
us.boschsecurity.com



Capturing details in extreme environments 24/7 Punishing winds, relentless rain, huge temperature fluctuations, clouds of dust or high-impacts. No matter how tough conditions get, with MIC IP 7000 HD cameras your surveillance operation never stops. Learn more at www.boschsecurity.com/hdsecurity
Our focus is providing you with a 360-degree overview in a single image



Never miss a thing with FLEXIDOME IP cameras. Blind spots can seriously undermine the reliability of your video surveillance solution. With the range of FLEXIDOME IP panoramic cameras from Bosch, you will never miss a thing. Thanks to a choice of 5 or 12 megapixel sensor resolution at high frame rates and fish eye lens, a complete overview without blind spots and easy capture of moving objects significantly improves the quality of every video surveillance operation. So you can capture objects of interest with superb clarity, eliminate blind spots and always see the bigger picture. Learn more at www.boschsecurity.com/hdsecurity
What to expect in
From Cloud to home automation to the ever-evolving surveillance industry, we asked some of security’s leading experts for their predictions for the new year

By Linda Johnson
With a new year upon us, it is traditional for SP&T News to reach out to the industry and take its pulse. Depending on whom you ask, security is either pacing itself for a marathon or breaking into a sprint. This year we asked experts in five fields — M&A, home automation, CCTV, cyber security and mobility — to give us their take on the directions they see the industry taking and how these may alter the competitive climate.
Mergers & Acquisitions
Leonard Sudermann, president of Calgary-based Securex Financial Corp., which provides financing to security alarm companies, sees little activity in the year ahead and a tougher competitive environment.
The consolidation at the upper end of the industry that started a few years ago, he says, is done; the larger players, such as Voxcom Security Systems and Protectron, have been consolidated by ADT.

Moreover, he does not expect to see much consolidation in the lower end of the market. Few companies are well enough capitalized to be able to finance their internal growth, combined with an acquisition.
Some companies could acquire capital through dealer programs, but, with only one major player in the industry right now, there’s a dearth of programs available to the smaller dealers.
“And ADT now is ratcheting up their terms, making it harder for
Leonard Sudermann

the other companies to compete with the better financed, door-knocking firms, the Vivints and that,” he says.
SecurTek Monitoring Solutions and Counterforce, which also does acquisitions, are among the few that have dealer programs, Sudermann adds. And while some companies would like to sell, there are not a lot of buyers.
“There may be some activity, on the right terms and conditions with vendor take-back financing, for example. I see it as being fairly limited. I see Securex being involved to a degree, but I don’t see it throughout the broader industry,” he says.
This lack of M&A activity, he adds, marks a change for an industry where there used to be a great deal of consolidation. “That consolidation was driven by companies like Voxcom and Protectron. Chubb is out there still, and Honeywell. But they don’t do a lot of acquisitions. It’s not their business model.”
Looking beyond Canada, the London, U.K.based market research firm Memoori Business Intelligence is predicting M&A in physical security will start to increase.
“Mergers and acquisitions in the physical security industry have been on a roller-coaster ride over the last 15 years. With an upswing in 2015, [Memoori] predicts that industry M&A will start a new cycle of growth during the next few years,” a recent article by the firm states.
In 2015, the article says, the value of deals increased to US$5.7 billion. The two most high profile deals — the acquisition of Axis Communications by Canon for US$2.8 billion and the merger of Kaba Holdings and Dorma Holdings — accounted for more than 80 per cent of the total value of acquisitions that year.
An increase in acquisition activity in the middle market during the last three years, along with ongoing problems of terrorism and political and economic uncertainty in some regions, are, the article says, “making the industry generally confident that investment will continue to flow into the physical security market.
“We forecast that the trend in M&A across the physical security industry will increase to US$6,500 million [US$6.5 billion] by 2020. We expect that some of the major conglomerates may sell off parts of their security products businesses, and this will provide a great opportunity for the specialist manufacturers to continue their M&A strategy.”
In the video surveillance sector, Memoori expects “leading Chinese manufacturers, which have significant market shares in some western markets, could have good reason to acquire western companies with leading IP technology at the enterprise level.”
Home automation
Several trends will affect the home automation market this year, says Blake Kozak, principal analyst at IHS. During the last year, the market has seen a slow down in growth primarily because many early adopters already have a system.

systems out there. We need to continue to see those being converted.”
Many companies have done a good job with that, he says, but they face a further challenge: another reason for the slowdown is that there has not been much expansion of the home automation pie.
While the total number of smart-home subscribers is increasing, the historical 18 to 20 per cent penetration rate for monitored systems in North America has not increased significantly.
Fragmentation, too, Kozak says, will continue to affect the market over the next year or so, especially in regard to connectivity, with Thread, HomeKit, ZigBee, Z-Wave, the various forms of WiFi and Bluetooth. Both Bluetooth and DECT ULE will likely play a larger role in the market, he expects, while it’s unclear how Thread and HomeKit will affect the market over the next year.
“What’s interesting will be: will this add to the fragmentation? The challenge is, even IKEA is starting to come out with their smarthome and automation solutions and really targeting a way to get into the market at a lower price. That adds to the fragmentation: when you have a company such as IKEA coming out with different offerings.”
CCTV
In CCTV, says Katie Brink, industry analyst at Cleveland, Ohio-based The Freedonia Group, we will see products, such as cameras and monitors, become increasingly commoditized.

Prices have fallen, and, as manufacturing capabilities have grown stronger, it’s become more difficult to compete. Thus, many companies have focused on trying to diversify and stand apart from the competition. That’s brought a move to introduce special features, such as thermal imaging cameras, extreme-weather cameras and high-light or low-light cameras.
“So the challenge some companies are having is identifying how to educate their existing folks. You look at a lot of the traditional service providers — an ADT, Protection 1, Monitronics — there was an incredibly large number of legacy
“There’s been a shift towards the analytics, the video management.”
— Katie Brink,The Freedonia Group
However, while some end users will always want the latest and best technology, she adds, most people setting up a security system aim primarily to meet their needs and work within a budget. “So features such as thermal imaging or the high-light situation tend to be more niche or used in high-security areas where there’s a

Blake Kozak
Katie Brink
real need for security, vetting and paying attention to the perimeter,” she says.
“As a result, there’s been more of a shift towards the analytics, the video management, making the systems more flexible so that you can leverage them better. That’s really what will drive video surveillance going forward because, with analytics, you can help monitor people who are doing the monitoring — so the security guards do their jobs more efficiently.”
This may help reduce the number of guards needed because, rather than requiring many guards to watch several screens, the system can detect a problem, bring it up and point it out to a single person who is reviewing the screen. Or it could reduce the number of screens: there could be just two or three, and a guard can pull up the one needed when there’s an issue.
Another trend that will grow in importance, especially in retail, Brink says, is the use of analytics and leveraging the software not only for security but also for other purposes to help drive revenue. A store can use analytics to monitor operations or see if their marketing is working effectively.
“Going forward, the amazing capabilities of analytics, which have been growing more capable and will continue to do so, are going to help with that,” she says.
“In each industry, as manufacturers and software developers work with the end users and say, What needs do you have? How can we leverage the analytics to help you out in other ways, I think it’s going to increase the use of video surveillance.”
Cyber security
Kevin Lonergan, senior analyst at Toronto-based IDC Canada, says his company has seen strong growth in managed security services in Canada over the last few years, and they expect the trend to continue.
This is happening mainly because Canadian businesses, outside large enterprise organizations, are having difficulty finding and retaining highly-skilled IT
security professionals. “Our survey results show that Canadian organizations ranked a lack of security staff availability as the No. 1 reason for migrating to managed security services,” he says.
“Cyber criminals are using passwordcracking tools to identify passwords in seconds.”
— Kevin Lonergan, IDC Canada
“They need to have people there, available or on call 24x7, and there’s just not enough professionals out there to fill in all those gaps. Staff retention is also a big problem. Because they’re in such high demand, these people will jump around.”
According to the survey, Lonergan adds, another major reason for the move to a managed model was lack of security threat knowledge (ranked third in importance). Organizations now have four or five different mobile devices they have to support and make sure are secured. “The attack surface has grown so much, and it’s hard to find people who have knowledge of all these different threats.”
Survey data also showed the main roadblocks organizations face when trying to improve IT security is a lack of budget and lack of non-IT employee security knowledge.
“Organizations are saying that, despite email being 25 years old and people being on the Internet for 20 years, people are still clicking on links they shouldn’t; people are still falling for simple phishing scams. They just don’t have the knowledge,” he says.

“So, despite knowing that there’s a lack of proper security knowledge amongst their employees, organizations still admit to training very little of their staff on a yearly basis.”
Karl Sigler, threat intelligence manager at Chicago, Ill.-based Trustwave, says poor password security and manage-
ment remain top of the list of things to look out for in 2016. The strength of passwords as an authentication control is more important than ever before.
“Cyber criminals are increasingly using automated password-cracking tools to identify passwords in a matter of seconds. This is because all too often users stick with default passwords or don’t want to have to remember a long, complex sequence of numbers, letters and characters.”
Through 2016, Sigler says, e-commerce will continue to be a prime target for cyber criminals, who are seeking Personal Identifiable Information (PII) and payment card data. Trustwave has seen e-commerce grow as their “Top Target Asset” for the past three years. Rising from 48 per cent in 2012 to 54 per cent in 2013, it is now at 64 per cent for retail breaches in 2014. “It is safe to say that we expect compromises of e-commerce sites to continue to dominate our investigations through 2016 and beyond,” he says.
Mobility
Daniel Bailin, director, strategic business development and innovation at Austin, Tex.based HID Global, says the trend to using mobile phones to open doors will continue to grow. Interest in this technology increases as smart phones become more central to people’s lives. We’ll also start to see “wearables,” smart personal devices used now mainly to track activity levels, being used to open doors.
some of these new products will continue to support NFC, the technology used with smart cards, more and more use cases in future will also support Bluetooth.
“The advantage of Bluetooth is that you have a somewhat longer read range, so it will make it a little bit more user friendly. And you open up some new use cases that you didn’t have when you were just supporting NFC,” he says. “Smart devices over Bluetooth give you more options for how you interact with the door.”
For the near future, mobile credentials will likely co-exist with cards or whatever other credentials are already in an organization’s system, says Katie Brink at Freedonia. In some companies, for example, executives have a card but are also issued mobile credentials. The rest of the employees may just have a card.
Currently, their use has been mainly for security. Some hotels have mobile credentials for room keys, sometimes allowing guests to check in via a mobile app. Universities have used them for student IDs, where they’re also used to access dormitories or buildings after hours. It’s easier to get in (they hold their phone up to the reader at a door), they don’t have to worry about losing a card, and the phone is always with them.

Generally, people want more options in access control than just the smart card.
“When smart cards were the only choice, we picked smart cards. But, just as there are many choices in this mobile phone world, we’re going to see the same expectation [in access control]. Part of this overall trend is called the consumerization of IT. The idea is that, I have a flexible, personalized experience in my personal life, and I expect to have that same range of choices in my enterprise life.”
Moreover, Bailin says, while
However, Brink adds, the common belief is that mobile will dominate. “As it becomes the standard to have a smart phone and technology develops, it’s eventually going to switch — and for many uses beyond security,” she says.
“But it will take time. It depends on companies’ needs. Some end users want the latest and greatest, or want to stand out to customers, especially hotels or universities that are trying to attract and retain students. Those are probably areas that will move quickly. But for a regular office, which already has cards, what’s the point in upgrading to a new system? You might upgrade when you start having issues.”
Linda Johnson is a freelance writer based in Toronto.
Daniel Bailin
Kevin Lonergan

By Linda Johnson
There’s more to life than security
Newer uses for surveillance tools include business intelligence, operations management, marketing, and potentially
much, much more
Whether they’re monitoring new-born pandas or providing a record of the construction of a new sports stadium, surveillance cameras are being used in new ways every day.
For the security industry, the growing use of cameras for non-security purposes is proving beneficial. As cameras become smaller and smarter, they’re taking on useful roles in areas such as marketing, operations and compliance, thus opening up new opportunities with existing customers and a way to attract new ones.
“Over the last two to three years, video surveillance cameras have adopted many more applications outside just the pure video surveillance and security setting,” says Aaron Dale, market analyst, security and fire, at the research firm IHS. “People have been using non-security cameras in niche applications for quite a while, but more recently, it’s become more mainstream.”
The primary non-security use of surveillance cameras, he adds, is business intelligence — the use of cameras to increase efficiencies and profit line. Often, the initial infrastructure has already been set up for security, thus providing an added incentive to upscale. This application is most prevalent in the retail market.
Kevin Saldanha, director of product management for IT cameras at Clovis, Calif.-based Pelco by Schneider Electric, says intelligent video analytics inside a camera produce heat maps that
retail store managers can use to see how customers move about the store. If a store has just set up a new end-cap layout, a display at the end of an aisle, for example, the manager will want to know whether it’s attracting customers.
“That’s valuable business intelligence that the people who change configurations of stores can use to great advantage in improving their business operations and effectiveness. So, the ROI for these types of applications is readily apparent,” he says.
“There’s a lot of this technology being used in anything from missile guidance to drones.”
— Aaron Dale, IHS
Cameras are also used in retail to see how a store is operating, an application especially useful for multi-site companies, Saldanha says. Managers with many stores can call up cameras in all the different stores and see what’s happening in each. They can compare activities and efficiencies: what level of traffic each store has, how employees help customers and how long people are waiting in check-out queues. Long line-ups can cause a store to lose customers. If operations staff see long waits in a particular store, they might decide to open another checkout or even to retrain staff to work more efficiently.
Dan Cremins, global leader of product management at Ottawa-based March Networks, says the collected meta-data helps retail marketing and operations people identify trends that could affect the business. “The real trick of this is to be able to take the information you’re seeing from all the different stores every second, every hour, and be able to chart it out into a dashboard to see trends over time. You may see that one particular store constantly has people waiting in line much longer than all the other stores. So, you can look at the video, talk to the manager and get to the root of the issue.”
Retailers are also beginning to use surveillance cameras, he adds, to help determine conversion rates: a comparison of the number of people who enter a store with the number who purchase something (number of transactions). This information is important primarily to specialty retail stores, particularly clothing stores.
Cremins says many retail owners and managers are using cameras to conduct operations audits. A camera takes snapshots at regular intervals, and a manager can then review the shots to make sure that operational, compliance and performance standards are being met in their absence.
The compliance aspect makes the operations audit function particularly useful to financial institutions, he adds. Many banks have opening and closing procedures they are required to follow to discourage robberies.
“Operations people want to make sure each branch manager is actually doing this. So by tak-

ing a snapshot at 9 o’clock or right before, you can see, yes, I see the manager and the employees; they’re gathered together. They’re following the process,” he says. “Banks have processes in place, and they need a tool to be able to ensure that all their branches are compliant.”
Retail marketing has also taken advantage of the merger of analytics and meta-data coming from cameras to develop dynamic marketing, says Jim Murray, senior product manager for video at Torrance, Calif.-based AMAG Technology. Thus, public view monitors can change what they display depending on the number and type of people that may see it.
“The monitor is dynamically deciding: do I want to show that you’re being watched, show just an image of what’s being viewed by the camera that’s open to public view, or do I want to show marketing material that corresponds to a promotion that’s going on right now,” he says.
Even more targeted is some digital signage, which identifies customers by characteristics such as gender and age and then displays an advertisement deemed most suitable for that group, Dale says. Digital signage is being used in ever more inventive ways. In a recent Porsche campaign, for example, a video surveillance camera with embedded object detection functionality was paired with a digital signage advertisement at the side of a highway.
“It would detect that a Porsche had driven by, and it would then display that particular advertisement,” he says. “We’ve seen a lot of these types of applications recently.”
On industrial sites, Saldanha says, managers are using video assets to fulfill functions such as monitoring adherence to safety processes. A piece of equipment may need to be checked at regular intervals, for example. “Sometimes, they want to know that physically somebody went there, did their job, because it was important that that process be followed for the safety of people and equipment in that area.”
Thermal imaging cameras have made possible other non-security applications on industrial work sites, he adds. They’re sometimes used to map moisture paths and detect leaks that may be hard to see. And, because the first sign of a problem in a machine is often an out-of-control temperature, they are also used to ensure machines are functioning properly, replacing the visits by an inspector with a handheld thermal scanner.
Thus, at power plants and stations, which run very expensive equipment and want to avoid power outages, thermal cameras are used to produce heat maps of sensitive portions of equipment, Saldanha says.
“If you have thermal cameras with intelligent, thermographic analytics in them, you can continuously monitor the heat maps at different points on a piece of equipment. And, if anything goes out of control, you have immediate notification via analytics alarms from the camera, which tell you: this particular point, which is supposed to be in this temperature range, has now gone out of it,” he says.
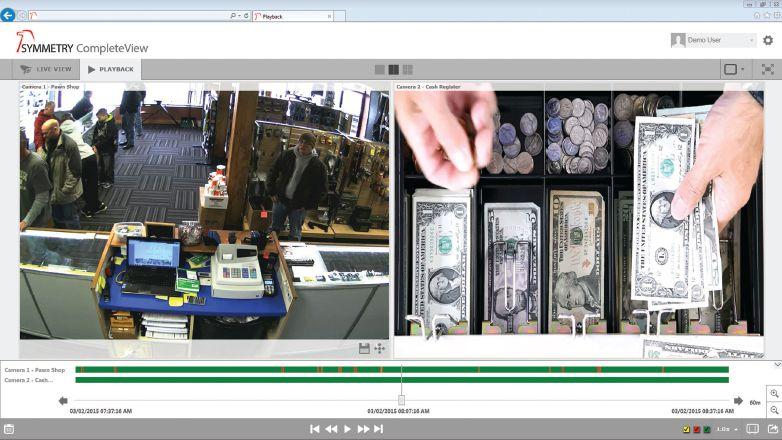
AMAG Symmetry software offers multiple views of a retail establishment, including POS transactions. Retail has emerged as a leader in discovering new uses for surveillance tools, including useful applications like heat-mapping and customer line-up management.
In another industrial application, cameras are used with RFID tags attached to products moving along an assembly line to help determine where each piece is located on the line, Murray says. “So if, for example, the RFID tag isn’t read properly, a manager can go to the camera to see what’s going on and perhaps manually enter in the ID of that product.”
“The meta data that comes out of the camera can be stored and shared and is always widening.”
— Jim Murray,AMAGTechnology
Murray says the non-security use of cameras has increased primarily because the cost of IP cameras has dropped significantly, while quality has been improving. The processors in cameras with on-board processing capabilities are getting better and faster, and thus the range of analytics that can be done at the camera is growing.
“It means the meta-data that comes out of the camera that can be stored and shared is always widening; there’s more valuable data coming out of the camera,” he says.
The trend has also been driven by Cloud technology, as well as the ability to make cameras more aesthetically pleasing and less intrusive, a feature particularly important in the residential market.
Using cameras for non-security purposes is a boon for security professionals, Cremins says. Integrators are always trying to expand their businesses, but it’s difficult to repeatedly return to the same customers and try to sell them the newest, higher-megapixel camera.
“But if they can go to an existing customer and say, I can offer you more than just a security solution to solve more of your problems, then there’s
more money in it for integrators. And they’re making their customers happier,” he says.
While people are coming up with new ways to use cameras in other industries — in automotive, for example, where features like night vision and lane departure detection are being built into cars — the main opportunities in the near future will continue to be in the retail and residential markets, Dale says. There is still in both areas a lot of room for expansion, he adds. He does not see cameras moving into very many non-niche environments, although there are indications that gaming and defence are two possible applications.
“There’s a lot of this technology being used in anything from missile guidance systems to drones.”
Murray believes the use of non-security cameras will continue to expand in many areas. They’re already being used in “intelligent stadiums” to determine queue length and in parking lots to identify which levels are full. He also sees a growing use in remote health care.
“It will provide more reasons for people to have cameras in their home. They can have an appointment with a doctor, and they don’t need to go in. They can use cheap video conferencing through the phone or PC. Cameras can be used to meet with people in professions that are under-staffed,” he says.
Cremins says the use of non-security cameras to monitor compliance, especially in safety protocols, will lead to widespread adoption of the technology across many verticals. Employees in many workplaces are required to wear safety helmets and vests.
“Think about any application, not just retail, but wherever people have to wear safety clothing,” he says. “If you had a tool to be able to work across all your locations to make sure that, every hour, employees are wearing their safety gear, what better solution is there than video?”
Linda Johnson is a freelance writer based in Toronto.

SECURITY ALL THE WAY TO THE EDGE
Manufacturers say they are working together to help mitigate cyber attacks on surveillance products
By Andrew Elvish
Long before the term Internet of Things (IoT) became “a thing,” the IP-physical security industry was working with multi-sensor systems to manage video surveillance, access control, and automatic licence plate recognition sensors to capture, analyze and store data. Genetec’s systems were built on an open-architecture, and because of this, we were positioned to expand and integrate new sensor devices or “things,” like smart phones used as mobile surveillance cameras, intercom systems, and body-worn-cameras. As the IoT became more mainstream for broader markets and the consumer public, as we expected, vulnerabilities have to come into sharp focus.
The IoT is a network of physical objects, devices, vehicles, buildings and other items that have embedded electronics, software, and network connectivity. A wide variety of sectors and applications, including environmental monitoring, infrastructure management, medical and health-care systems, and transportation are adopting the benefits of the IoT — and especially
the consumer market.
By allowing things — or sensors, as we refer to them in IP-physical security — to be used and controlled remotely across an existing IP network infrastructure, the IoT creates opportunities for more direct integration between the physical world and computer-based systems. The benefits are improved efficiency, accuracy and economic benefit. We are also aware that any system is only as secure as its most vulnerable point. When working with extended IP-based and federated physical security systems, multiple access points will naturally result in increased opportunities for cyber-attacks. We know that even one improperly secured or protected edge devices, like a camera, can be the gateway to put an entire system at risk.
Cyber attacks hit close to home
A recent story in the press reported of a hacker that accessed an unprotected baby monitor and had been speaking directly to the child in the room. With this disturbing violation, consumers are finally becoming more aware of the vulnerability of their default or easy-to-guess passwords for the sensors and devices in their homes.
Similar sensor device technology is attached to large corporations, municipal infrastructures, law enforcement, and citywide surveillance. These edge devices are connected to vast security system networks and storage locations, containing highly sensitive data which can affect both public safety and human life.
So, while the idea of a stranger connecting with a child over an audio or video monitor is
both shocking and upsetting, the consequences of a security breach from edge devices within larger security systems, has the potential to cause damage on an even greater and more devastating scale.
How can we protect our data?
A poorly or improperly secured sensor device could allow hackers to gain access to a video management system, which could be subsequently connected to an access control system, data storage, communications systems, or the Cloud. By leveraging the vulnerability of a single camera, a hacker could gain access to read, disrupt, alter, cut the video feed or lock an organization’s sensitive, private, and critical data.
Camera manufacturers have become increasingly involved in the security of their edge devices and are aware of the impact vulnerabilities can have on an entire network. Some already publish recommendations on how to keep their cameras secure, but, if end-users do not follow these guidelines, then they are of little help.
The task now is for the physical IP-security industry to put new measures in place to help mitigate these risks.
Ensuring better security at the edge
At Genetec, we collaborate with an ecosystem of over 200 manufacturing partners, who collectively produce 2,700+ cameras and other sensor devices. We work closely with camera manufacturers to reduce and secure any vulnerabilities that exist between edge devices and the archiver — that part of our security platform that manag-

es, saves, and archives video data. The key is to ensure that the front-end is as secure as the backend when video data is being managed, moved, and stored; either on-premises or in the Cloud.
One of our strategies for 2016 is to work with and influence camera manufacturers to implement better standards to follow more rigorous security practices. At a very basic level, this includes having camera manufacturers require users to set a unique password whenever they install a new camera.
Camera manufacturers often set default passwords, like 123456 or admin, which many end-users never change when they install the devices. This means that if a hacker knows the make, model or even the manufacturer of a camera, they can easily gain access via these default passwords. By requiring that users setup their own, unique passwords at installation, we can make it that much more difficult for hackers to gain access.
Increasingly, and particularly when it comes to edge devices, we err on the side of security instead of ease-of-use and compatibility. While this may lead to more effort on the part of manufacturers, developers, installers and the IT department, we must take these steps to assure physical security systems are secure by default.
Multiple layers of defence
Beyond being deterred by a secured sensor device at the edge, we know that hackers will quickly move on and attempt to break into the database via sniffing networks or by grabbing unencrypted data in transit. They will even make attempts by installing malware to grab data before it gets encrypted.
Staying ahead of hackers and other unwelcome entities trying to exploit the increased number of network gateways into physical IP security systems, we are taking the Security-of-Security very seriously, and to new levels. This strategy incorporates multiple and varied lines of defense, including encryption, multi-layer authentication and authorization.
Encryption and authentication
Encryption is the process through which data is encoded so that it is scrambled and rendered useless, if intercepted, to unauthorized users. While encryption can effectively hide contents or ensure the confidentiality of data, additional security measures are required to protect the integrity and authenticity of data. Even if a hacker is unable to get access to video data, simple encryption cannot keep that data from being spoofed, nor does it prove the authenticity of the data transmitter.
The process of authentication allows a user, client, or server to determine whether an entity is who they claim to be. For example, through authentication, an operator can be certain that
they are connected to their security system when logging on to a video surveillance server so that they don’t fall prey to a man-in-the-middle attack. There are several methods of authentication including; basic (username/password combinations), certificates, claims-based, multi-factor and biometrics.
Today, we are using one of the latest protocols that can be employed to better protect physical security systems. TLS provides protection by using digital certificates to first authenticate the counterpart in the communication and then negotiate a symmetric session key that is used to encrypt data during the conversation.
This process provides greater security for communication over a network because it protects communication channels between servers and client applications, as well as between the servers themselves. TLS is just one example of a multilayered approach to protecting physical security systems that is a vital component of our approach to the security-of-security.
Maintaining privacy
In addition to protecting sensitive data from hackers and other outside entities, it is also important to be able to manage who, within your organization can see your data and what they can do with it.
Increasingly, public and private companies, various levels of government and law enforcement are federating and sharing data and video footage. In essence, they are taking advantage of the IoT to share video footage with each other. This greatly increases their ability to quickly respond to and mitigate criminal activity. Sharing video data across IP networks requires that security professionals must have the means to guarantee that their sensitive data stays private, viewable and accessible only to authorized users, even in the event of theft or interception.
Comprehensive, finely grained privileges allow security personnel to define all the access rights for private data, computing resources and applications within their system. Only authorized entities are allowed to review sensitive data and video exports out of system storage must be explicitly authorized — quite often by multiple parties.
Partnership with Bosch
At Genetec, we share the initiative for the security-of-security with many of our technology partners. One such partner is Bosch Security Systems. According to Konrad Simon, a Product Manager in the company’s IP Video division, Bosch takes a 360 degree view of data security. Because video and related data are often highly critical and sensitive, Bosch has a systematic four-step approach to maximizing security by considering physical safety and cyber security simultaneously.
The first step is to create trust. Based on certificates, Bosch ensures trusted communications between cameras and network components by assigning each element an authentication key that serves to verify all components from Bosch cameras to a video management system or viewing clients.
Once trusted communication between the components has been established, the next step is to secure the data. When it comes to safeguarding surveillance data, the safe storage of the encryption keys used to secure the data is paramount. Bosch implements encryption at the hardware level. All Bosch IP-cameras and recoding solutions are factory-loaded with a trusted platform module (TPM) that safely stores all encryption keys used to protect all streamed and recorded data. Even in the event of a data breach, the information is useless to anyone without the certificates’ private keys.
The third step is to manage user access rights. Video surveillance data can range from merely sensitive to top secret, and even networks with trusted devices and secure data transfer can fall victim to human error. To mitigate the risks associated with human error, the video cameras made by Bosch offer management options for individual user access rights and support existing industry standards, including Microsoft’s Active Directory.
Finally, all of Bosch’s video surveillance solutions comply with leading industry standards in public key infrastructure (PKI) for the management of digital encryption certificates.
Working together
Ultimately, a comprehensive approach to the security-of-security requires that the sensors at the edge can capture data and move it to a unified security system for management, analysis and storage with strong encryption that is accessible only to authenticated and authorized end-users. Bosch-integrated data security systems bring peace of mind by protecting both valuable data and privacy while ensuring that video information cannot be tampered with. As the challenge of safeguarding data continues, Bosch experts are actively contributing by transferring well-established IT standards and authentication methods to the security industry.
By understanding the complexities our connected world, and through collaborative efforts, Genetec and its technology partners, like Bosch, are working together to assure that video data is protected at the sensor, during transit and analysis, all the way to storage and long-term archiving.
Andrew Elvish is the vice-president of product management and marketing at Genetec (www. genetec.com). Konrad Simon, product manager, IP Video, Bosch Security (www.boschsecurity.us) also contributed to this report.

SPLIT DECISIONS
Analytics are making more and more security-based choices. Drawing the line between machine and human intelligence has become an increasingly complex issue
By Treena Hein
Software is playing an increasing role in many of our decisions. From suggesting we check our car’s tire inflation level to autocorrecting our text messages, the line is shifting between letting software influence our decisions and letting it make decisions for us.
This phenomenon is also found within the security industry. Analytics — powerful software able to automate or semi-automate surveillance and response tasks and decisions — are becoming more prevalent, and for good reason.
Chandra Rangan, vice president of marketing at Hewlett Packard Enterprise Security Products, spells out the need for analytics by comparing
security settings today with those from 10 years ago. He likens security back then to protecting a castle, focusing on a single target with defences surrounding it. Now, he says, it’s so much more complex, with moving targets, huge amounts of data coming in from many sources, new operations technology, use of the Cloud and more.
“A decade ago, it was a hundred events per second on a network and now it’s hundreds of thousands of events per second,” he explains. “Some organizations are looking at millions. When that kind of increase happens, the way you look at things has to fundamentally change.”
Although demand for analytics is strong because of its potential to enable security providers to make sense of large and continual amounts of

data, its use right now is uneven. “Cybersecurity uses quite a lot of analytics — think spam filters, monitoring of credit card usage patterns, etc. — but analytics for physical security (monitoring and analyzing video surveillance footage, for example) lags far behind,” notes Dr. Parthipan Siva, a computer vision developer at Waterloo, Ont.based security software firm Aimetis, which was recently acquired by Senstar.
Uses and limitations
Whether analytics are being used for physical security or cybersecurity, it’s all about providing quicker, but still accurate, identification of specific parameters or unusual behaviour.
In the physical world, analytics might be employed in a search for a particular person’s face or to identify unusual crowd movements. In the digital world, analytics might be used to flag unusual login activity.
Rangan identifies three broad tasks that the security industry wants analytics to provide. “Customers are looking to analytics to eliminate data, to reduce false positives,” he notes. “Also, customers want better baselining. Analytics establish baselines automatically, identifying different patterns from historic patterns.” Lastly, analytics are in demand for automating response decisions. “How much can my analytics tell me about something, and what can be done with a high degree of confidence?” Rangan asks. “How do I speed up my response and empower my security force to make better higher-level decisions?”
The first two, screening data and creating baselines, are very inter-related. Imagine, Rangan says, 10 different possible security incidents, and the need to make sure events within those 10 are real. “The only way I can figure out what is real,” he explains, “is through a baseline.”
So, analytics, notes Katherine Brink, industry analyst with the Freedonia Group, is about analyzing both individual security events and identifying trends or patterns, the latter helping a company provide better overall security to all its clients. “Trends might be there for many reasons
and those have to be analyzed, but analytics is a way for security companies to analyze situations in more detail,” explains Brink. For example, she notes that IP cameras now have software integrated within them, with more options than ever before that can be used to analyze an image.
Trust in the software
As we all know, computer decision-making is not yet perfect, and in the security industry, the stakes involved are very high.
“A decade ago, it was a hundred events per second on a network and now it’s hundreds of thousands.”
— Chandra Rangan, Hewlett Packard Enterprise Security Products
“If you have two or three security guards and a bank of screens, it’s so easy to miss a detail, so automation helps with that,” Brink notes. “You want to reduce human error, but analytics have only recently increased to being feasible to use and have a long way to go. There are false alarms and a tendency for the analytics to notice too much and not narrow things down enough. So there’s a back and forth going on right now.”
Alarms are another physical security arena where analytics are being used, but again Brink says an accuracy balance has yet to be struck. “Alarms are far more automated, but there have been so many false alarms, and again it’s a back and forth,” she explains. “There’s more automation but human checks are still needed where appropriate, and it’s not cost effective if you have to do too many checks. Yes, analytics lowers the labour needs for surveillance, but you don’t want labour costs to be higher because of so many false alarms.”
Siva notes that “for some environments, even when properly configured, the rate of false alarms
due to lighting or severe weather conditions can be high. This results in the need for human verification of individual alarms to filter out false alarms…[so] it’s essential for users to carefully evaluate the accuracy of any analytics they want to invest in.”
Another roadblock to analytics accuracy is systems integration. “Most video analytics systems require intricate configuration for each camera in your security system for proper functionality,” Siva notes. “For larger infrastructures with hundreds or thousands of cameras, this becomes a heavy burden for system integrators.” This is especially true if the analytics and video management system are not from the same tech provider.
Outside of video surveillance and alarms, Siva points to automatic licence plate recognition as another area where analytics can help provide more efficient security. He believes that as prices drop for cameras and computational power grows, analytics will be used in many more access control scenarios, such as parking lot gates that automatically open when an authorized licence plate is recognized. Facial recognition systems are yet another area.
Siva notes that “Deep Learning” by computers has demonstrated success in many different fields in the last few years, including his field of expertise, computer vision (where algorithms are applied for interpretation of visual data). “Multiple industries are currently focused on machine learning systems and there’s a strong shift towards building and using toolboxes to bring machine learning to a level where any software developer can use it,” he notes. “This shift will allow the video analytics industry to grow faster. However, to make use of these new technologies, we will need specialized parallel hardware, such as graphical processing units (GPU), as part of the camera or as part of the security system server installations.”
Rate of adoption
As with other technologies, the use of analytics will grow as it becomes more precise and affordable. “It will become prevalent in a fair

number of security products in the near future,” predicts Brink, “but the industry adoption may not be as fast outside of high security areas.” However, precision and cost aside, Brink identifies an important factor that may speed the adoption of analytics in security. “It’s the ‘big data’ scenario,” she says. “Most companies know they have to invest in security to help prevent shrink and loss, but that doesn’t make you any money. But analytics can help you with your security and to make money.” Take retail, for example. “If you have cameras throughout your retail store, that’s a security purpose, but with analytics you can see trends and patterns over time, understand traffic flow,” Brink notes. “It helps with organizing merchandise and changing traffic flow and with marketing. But it takes investment to find out how much it can be useful.”
Rangan agrees. “Analytics can do many other things than security,” he says. “It can help customers identify vast amounts of data so they can meet regulations for example. But most customers are not
“You want to reduce human error, but analytics have only recently increased to being feasible to use and have a long way to go.”
— Katherine Brink, Freedonia Group
running analytics beyond security. One in 10 is trying out something.”
Rangan foresees analytics being used to monitor power grids (failure rates, the difference between operational failure and a security incident) and in manufacturing settings as well.
Siva adds that the capacity of video analytics to track individuals and vehicles can also be used by facility managers for planning purposes. The software can provide things like general activity patterns, identification of which areas of a facility are used most, and calculations of the number of people moving through certain entrances, for example.
Within security, Rangan sees adoption being first among firms with staffs of at least 20 people with a reasonably secure opera-
tions centre. He believes there will be a very heavy focus on cybersecurity analytics in retail and healthcare to head off threats like hacking. There is 10 times the activity in selling health care records compared attempted theft of credit card data, Rangan notes, and large healthcare networks now need more than firewalls and anti-virus programs — they need to be able to monitor large amounts of data for anomalies, which is exactly what analytics provides.
Outlook
The speed at which analytics ends up being adopted remains to be seen, but one thing’s for certain, according to experts.
“There will always be human verification needed for the foreseeable future within the security

realm,” says Brink, “but this will become faster and more efficient with analytics.” Rangan agrees. “We don’t see, from a practical perspective, security technicians or other types of technicians being replaced by software, but analytics and machine learning will be used to free up and empower human beings.”
Siva’s view is similar. He believes that autonomous software decision-making is unrealistic because it demands 100 per cent accuracy. “Imagine a spam filter that automatically deletes every email it believes is spam, rather than placing them in a spam folder for you to recover it,” he says.
“Similarly, [imagine] an automatic licence plate recognition system where you cannot enter a facility because your licence plate is unrecognized is not realistic. There must always be a human failover. The goal of the analytics system should be to minimize the number of times human failover is needed.”
Treena
Hein is a freelance writer based in Pembroke, Ont.
Product Previews

HD-TVI 1080p cameras
Speco Technologies
Intensifier and IR camera models are now available in full HD-TVI. Cameras that feature heater circuitry and anti-moisture glass to reduce fog and condensation, as well as wide dynamic range, are now available in full HD 1080p resolution over coax. Previously only available in 960H, the new HD-TVI HT7246T and HT5940T provide detailed images at any time, day or night. The HT7246T utilizes Intensifier technology, allowing users to see HD colour video in low light without IR LEDs by amplifying existing light.
www.specotech.com

VMS migration
OnSSI
Ocularis 5 provides current Ocularis users with a comprehensive migration path that includes backward compatibility to virtually all previous versions of OnSSI’s VMS software. Among the new features included in Ocularis 5 are Critical Camera Failover that ensures continuous sight by switching to a failover camera in as little as two seconds, hardware efficiency, allowing generic settings to be copied across multiple channels for faster installation, and stronger network security with end-to-end encryption. Ocularis 5 is offered in three models: Professional, Enterprise and Ultimate. www.onssi.com
Articulating wall mount
Video Mount Products
The FP-XMLPAB “extra medium” low profile articulating wall mount features tilt and list adjustment capabilities. The FP-XMLPAB holds most 32- to 52-inch flat panels up to 100 lbs. It features a closed depth of 1.5 inches and a fully opened extension of 16.2 inches along with a fully adjustable 15 degree tilt, 3 degrees list adjustment and ± 45 degrees of rotation. It also includes an integrated cable management system, an integrated level, and 600mm x 400mm maximum flat panel hole pattern. www.videomount.com

Bullet cameras
Toshiba Surveillance & IP Video Products
The IK-WB82A bullet IP camera features three-megapixel resolution (2048 x 1536), adaptive IR LEDs and H.264 Smart Code high-compression technology. Smart Codec addresses the bandwidth issue by effectively reducing the video packet size. It allocates more bandwidth to mov ing objects or critical areas of interest, and less to background images. The IK-WB82A incorporates features such as Adaptive IR, True Day-Night Imaging, and True Wide Dynamic Range to handle high-contrast scenes. www.toshibasecurity.com


PTZ dome network camera
Axis Communications
With 4K Ultra HD resolution and high-speed pan/tilt and powerful zoom functions, the new AXIS Q6128-E is suitable for both indoor and outdoor installations, in low light and challenging environmental conditions. PTZ dome cameras with Axis’ Sharpdome technology enable coverage of large areas with great detail when zooming in. Speed Dry function provides sharp images even in rainy conditions and simplifies dome cleaning.
www.axis.com
Panoramic dome IP camera
LILIN Americas

Featuring an M12 industrial Ethernet connector, rather than a standard RJ45, the new LILIN FD2452V-M12 five megapixel sensor 360° panoramic IP camera is an advanced video solution to help monitor and deter crime, vandalism or terrorism on public transportation systems. With its impact-resistant polycarbonate dome cover, the camera can withstand tough conditions such as vibrations, shocks, bumps and wide temperature fluctuations. It is also vandal-resistant, and features an active sensing alarm that can detect attempts such as blocking or spray-painting.
www.lilin.us
Web-based VMS Qognify

Thermal PTZ domestyle camera FLIR Systems
VisionHub is a web-based video management solution (VMS) which accommodates Qognify’s home grown fully-integrated video analytics suite, including the a Suspect Search application. The VMS is an open platform that leverages video as the main sensor the control room, while integrating third party Access Control Systems (ACS) using a dedicated module. www.qognify.com
The FLIR TCX PTZ (Pan-TiltZoom) is a thermal PTZ camera that is compatible with the industry’s top video standards and includes onboard Video Motion Detection (VMD) analytics. The FLIR TCX PTZ uses a thermal camera to provide accurate alarm assessment and visual verification. Using thermal, security professionals can see clearly in complete darkness, in challenging lighting conditions, low-contrast scenes, inclement weather, or heavily landscaped areas to help determine the correct response strategy.
www.flir.com/tcx-ptz
Product Previews
Video recorder
Exacq
The exacqVision LC-Series Una recorder includes exacqVision video management system software, server and integrated PoE+ camera ports. Users can connect up to 16 cameras per recorder and store up to 12 TB of video per system. The high output power supply provides up to 25 watts per camera and a maximum of 100 watts per eight cameras and 200 watts per 16 cameras. Users can view and administrate live and recorded video directly from the recorder using the included exacqVision client or remotely using a web browser or exacqVision client.
www.exacq.com

Affordable IP cameras
Honeywell
The Performance Series IP Family now includes a new lineup of affordable, high-quality IP cameras. The lineup introduces seven new IP cameras in dome, ball, and bullet design suitable for commercial settings such as office buildings, retail stores and warehouses. Select cameras from the new collection use Motorized Focal Zoom technology, which auto-focuses the lens after zoom operation. This allows the installer to fine-tune camera focus and field-of-view off the ladder. Additionally, each camera captures clear images with high-resolution pixel detail. www.honeywellvideo.com
IP video appliances
Razberi Technologies
The Razberi ServerSwitchIQ is a new generation of all-in-one, intelligent IP video surveillance appliances. The product line is optimized to reduce the impact of megapixel cameras on the IP network. The new appliances are compatible with leading VMS and IP camera providers and represent a complete suite of video recording appliances scalable for enterprise-wide to rugged locations. All models include Cloud-based cyber security and health monitoring features. The appliances embed a managed PoE switch, server and video storage.


4K Ultra HD IP cameras
Geutebruck
www.razberi.net
Panoramic surveillance solution
IDIS
The Super Fisheye enables complete 360-degree panoramic surveillance in high-definition, to give operators complete situational awareness without blind spots. The camera increases security by eliminating common delays associated with panning, tilting, and zooming. Featuring dual camera- and client-side dewarping (including via mobile devices), the 5MP Super Fisheye allows operators to split the 360° view into smaller, more focused images of key areas.

www.idisglobal.com
Video management software
Wavestore
V6 Video Management Software Wavestore’s graphical display has been updated with new icons and graphics. The addition of dockable components and configurability of the live event stream window provides an enhanced user experience which gives the ability for individual operators to arrive at their pre-customised screen layouts each time they log in. V6 also introduces camera shortcut keys using the keyboard number pad for added convenience and security enhancements to protect against malicious hacking attempts, including enhanced encryption and a high-security password policy. www.wavestore.com
Mini-dome and bullet cameras
Illustra Essentials mini-dome and bullet IP cameras are available in 1 and 2 megapixel outdoor mini-dome and bullet varifocal models. These cameras utilize a 2.8-12mm varifocal lens. Beyond the field of view, the Illustra Essentials varifocal cameras have true day/night IR illumination to capture high quality video in low light situations. While producing low light colour video, Illustra Essentials also features noise reduction and reduced storage costs with efficient bandwidth usage. The Illustra Essentials varifocals provide high performance wide dynamic range to simultaneously view high contrast areas. www.illustracameras.com


Geutebruck has extended its 4K Ultra HD IP camera range: 30 frames per second and 8 megapixels per image ensure that users can see every detail. Hence end users can identify the driver and licence plate of the vehicle that damaged another car in the parking lot or when returning goods they can prove to the sender that the scratches did not happen on their premises. The back-focus feature makes camera installation easier: The camera focuses automatically with the click of a mouse. This function can also be triggered manually.
www.geutebrueck.com

IP camera range
Pelco by Schneider Electric
The Sarix Enhanced Next Generation Camera Range includes features such as 130dB WDR and 60 ips that make it applicable for a variety of applications, including oil and gas, gaming, airports and seaports, and Safe City environments. Sarix with SureVision 3.0 delivers the best possible image resolution in difficult lighting conditions.The complete line of solutions is designed with reliability and fault tolerance.
www.pelco.com
Illustra
Product Previews

Modular camera
Vicon Industries
The latest cameras from Vicon provide wide scene coverage and highly accurate object detection with increased resolution. The new IQeye 9 Series has increased processing power to effectively run analytics and VMS applications at the edge. With on-camera storage and true day/night capability, these cameras are available in H.264 with up to 5MP resolution, and provide high quality megapixel images. Proprietary IQzip technology compresses bandwidth thereby allowing additional storage capacity. ONVIF and PSIA compliant, the series works with all leading NVRs and VMS providers.
www.vicon-security.com

Hybrid NVR
3xLOGIC
The VIGIL V250 Hybrid NVR is a 2U chassis hybrid NVR with an 8-port POE switch and 16 analogue looping inputs. This NVR comes standard with a 2TB hard drive, and VIGIL Server and Client software. By combining an NVR and analogue DVR in the same chassis, users can replace an old DVR without the expense of replacing existing cameras or network infrastructure, while gaining the ability and benefits of adding IP cameras. Among the target markets for the V250 Hybrid are replacement of old (up to 16 channel) analogue systems, typically in the small to medium-sized footprint and primarily in the retail/convenience store sectors.
www.3xlogic.com
Edge camera Avigilon
The H4 Edge Solution Camera line combines high-definition imaging, self-learning video analytics, network video recorder functionality, and embedded Avigilon Control Center video management software. The camera records video directly to an onboard solid-state drive and eliminates the need for a separate network video recorder. The cmera line offers deployment options ranging from standalone installation, multi-camera solutions, to integration into a conventional network video surveillance system.
www.avigilon.com
Bridge appliance
Eagle Eye Networks


Network cameras
Canon Canada

The Eagle Eye Bridge 304w is an on-premise bridge appliance that connects both wireless and wired cameras to the Eagle Eye Cloud Data Center, as part of the Eagle Eye Security Camera Video Management System. The Bridge 304w supports up to 15 high definition IP cameras, of which six can be wireless. It works with wireless and wired cameras from a range of manufacturers, including wireless cameras from Axis, Bosch and Hikvision. www.eagleeyenetworks.com

Flexible camera system Arecont Vision
The MegaVideo Flex IP camera series offers a security solution for installations that require a flexible and compact design. It is suitable for inconspicuous surveillance applications or for use in equipment such as in ATMs (automated teller machines) and other tight spaces while delivering megapixel (MP) high definition video. The indoor/outdoor camera series features a choice of 1.2MP, 1080p, 3MP, and 5MP resolution models. MegaVideo Flex is a true day/night camera. NightView technology in the 1.2MP model ensures coverage in areas where little light is present. www.arecontvision.com
4K network camera
Sony
The new SNC-VB770 camera achieves high resolution and sensitivity, in addition to low noise due to its image processing and fullframe 35mm Exmor sensor. The SNC-VB770’s E-mount lens series accommodates a variety of lens options from wide angle to telephoto, allowing easy integration into a range of video capture applications. The camera’s Intelligent Cropping feature lets users capture a full view while cropping images in its native 4K resolution from multiple images at the same time. www.sonybiz.ca

Five new network cameras share core technologies including a Genuine Canon Lens for capturing high-clarity, virtually distortion-free video, and Canon’s DIGIC DV III Image Processor. Models include: the VB-R12VE (outdoor) and VB-R13 (indoor) vandal resistant indoor fixed dome network cameras (also available, the TVB-R13VE with audio and external I/O support); the VB-H651V vandal resistant indoor fixed dome network camera; and the VB-H652LVE infrared vandal resistant outdoor fixed dome network camera. www.canon.ca

2MP PTZ camera
Dahua Technology USA
With a 12x optical zoom, this compact, 2MP high-resolution PTZ camera provides 30fps@1080p and 60fps@720p. Embedded with an IR cut filter for varying lighting conditions and wide dynamic range (WDR) technology (120dB) to capture important details in scenes with both bright and dark areas, the camera provides images at any time of day. The new Pro Series PTZ offerings provide a choice of either an indoor, in-ceiling (DH-SD42AC212TN-HN-(I) model suitable for suspended ceilings or a surface mount model designed for installation on hard ceilings.
www.dahuasecurity.com



