
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 11 | Nov 2025 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 11 | Nov 2025 www.irjet.net p-ISSN: 2395-0072
Hemalatha G1 , Anandha Kumar V2 , Chandru K3 , Chennakesavan M4, Hariharan R S5
1Assistant Professor, Dept. of Cyber Security Engineering, Paavai Engineering College, Tamilnadu, India
2Student, Dept. of Cyber Security Engineering, Paavai Engineering College, Tamilnadu, India
3Student, Dept. of Cyber Security Engineering, Paavai Engineering College, Tamilnadu, India
4Student, Dept. of Cyber Security Engineering, Paavai Engineering College, Tamilnadu, India
5Student, Dept. of Cyber Security Engineering, Paavai Engineering College, Tamilnadu, India
Abstract - The rapid growth of digital services has made traditional password-based authentication very vulnerable to security breaches. This project introduces KeyAuth, a layered biometric authentication system that combines keystroke dynamics, facial recognition, and honeypot deception to improve user verification. During registration, the system records each user’s typing rhythm and facial image. It trains a One-Class SVM model using the extracted keystroke timing features. During login, authentication first checks the validity of the password and the user’s keystroke pattern. If there are mismatches, a secondary facial verification layer using DeepFace is triggered. If both layers fail, a honeypot interface activates to catch potential attackers. The system uses Flask (Python) for backend machine learning operations and HTML/CSS/JS for the user interface. Experimental evaluation shows that the model effectively tells genuine users apart from impostors, providing better protection against spoofing and credential theftcomparedtoregularmethods.
Key Words: Multi-factor authentication, Keystroke dynamics, Facial recognition, One-Class SVM, DeepFace, Honeypotsecurity.
In today's digital world, authentication is essential for secure access control in online systems. As web applications, online transactions, and cloud services continue to grow, protecting user identity has become more important. Traditional password-based authenticationmethodsarewidelyusedbutvulnerableto many attacks, including phishing, brute force, and credential stuffing. Users often reuse or choose weak passwords, which further weaken system security. Therefore, we need intelligent, multi-layered authentication methods that offer better reliability and protection against unauthorized access. To tackle these issues, this paper introduces Key Author, a three-layer authenticationsystemthatuseskeystrokedynamics,facial recognition, and a honeypot deception method. This system combines behavioral and biometric verification to improve both security and precision. First, it verifies user identity through password matching and keystroke
analysis with a One-Class Support Vector Machine (SVM) model.Ifthischeckfails,thesystemactivatesasecondary facial recognition layer, employing the Deep Face framework.Ifbothlayersfail,a honeypot environment is setuptoengageandmonitorintruderswhilekeepingreal userdatasafe.TheKeyAuthframeworkisbuiltusingFlask (Python) for backend functions, including machine learning and facial recognition. The frontend is created with HTML, CSS, and JavaScript for an interactive user experience. This combined method ensures a flexible, precise, and user-friendly security system that meets the needsofmodernwebapplications.
With the growth of artificial intelligence and data-driven applications, cyber threats have become more sophisticated. Attackers take advantage of weaknesses in static login systems, which can lead to identity theft, data breaches, and unauthorized access to sensitive information. Biometric authentication, based on unique human traits, offers better security but often requires specialhardwareandhighercostsforimplementation.
Keystroke dynamics, on the other hand, provides a software-based biometric solution by analyzing typing rhythm patterns that are unique to each person. When combined with facial recognition, it forms a hybrid model that captures both behavioral and physical traits, significantly improving system strength. KeyAuth uses these features together to maintain ongoing and layered authenticationwithoutcompromisingusability.
The main goal of the proposed KeyAuth system is to create and implement a multi-layer authentication framework that improves security and verifies user identities. The project combines behavioral and biometric authentication methods to reduce unauthorized access and strengthen login systems. It uses keystroke dynamics asabehavioralbiometricfeaturebyexaminingeachuser's unique typing rhythm through a One-Class SVM (Support Vector Machine) model. Additionally, facial recognition with the DeepFace framework acts as a secondary

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 11 | Nov 2025 www.irjet.net p-ISSN: 2395-0072
verification layer. This offers extra assurance in identifyinglegitimateusers.Ifthesystemdetectsrepeated authentication failures, it triggers a honeypot deception mechanism that traps and monitors potential intruders without revealing real data. Moreover, the system will provide a user-friendly web interface built with HTML, CSS, and JavaScript, alongside a Flask-based Python backend for efficient and smooth operation. Overall, the aim is to create an intelligent, cost-effective, and flexible authenticationsystemthatcanmeettoday'scybersecurity challenges.
In today’s digital world, relying on traditional password-based authentication methods is increasingly riskyduetorisingcyberthreatslikephishing,brute-force attacks, and credential theft. Even with strong password policiesinplace,humanbehaviorfrequentlyleadstoweak passwords,repeateduseacrossdifferentsites,orcareless sharing, putting systems at risk of unauthorized access. Traditional security models also struggle to confirm a user'strueidentitybeyondstaticcredentials,leavingthem opentoimpersonationattacks.
To fix these issues, we need a security framework that not only checks entered credentials but also looks at the user’s behavior and biometric data. The main problem is the lack of an intelligent authentication system that can spot unusual login activity in real time and respond to possiblethreats.
The proposed KeyAuth system seeks to tackle these challenges by introducing a three-layer authentication method. The first layer uses keystroke dynamics to recognizeusersbasedontheirtypingpatterns.Thesecond layer utilizes facial recognition for biometric verification. Thethirdlayerimplementsahoneypotdeceptiontacticto catch attackers trying to gain unauthorized access. This combined approach offers continuous, adaptable, and behavior-sensitive authentication that improves system defensesagainstchangingcyberattacks.
The evolution of authentication mechanisms has moved from simple password-based systems to multi-factor authentication models that include behavioral and biometric parameters. Several researchers have looked intodifferentwaystoimprovetheaccuracyandreliability of user authentication by studying typing behavior, facial features,andhybridmodels.
Keystroke dynamics has become an effective behavioral biometric technique that captures the unique typing rhythm of users. Studies by Monrose and Rubin (2000)
show that keystroke timing patterns can clearly separate genuine users from impostors without needing extra hardware.Laterworks,suchasthosebyAhmedandTraore (2013), used statistical and machine learning models to improve classification accuracy. The One-Class SVM (OCSVM) has proven especially useful for modeling individual users. It can identify deviations from normal typing behavior without needing data from impostors. This method strikes a good balance between computational efficiency and detection accuracy, making it ideal for realtimewebauthenticationsystemslikeKeyAuth.
Facial recognition is a biometric method that examines unique facial features and textures to verify users. Research by Zhao et al. (2018) showed that deep learning models work better than traditional Eigen face or fisherface methods for matching faces. Modern systems likeDeepFaceandFaceNethavegreatlyincreasedaccuracy and reliability, even with different lighting or angles. Adding facial recognition as a second layer offers extra protection against unauthorized access when behavioral biometricmethods,suchastypingpatterns,donotreliably confirmauser'sidentity.
The idea of honeypots, which came about in the early 2000s, is commonly used in deception-based defense strategies.Honeypotsserveascontrolledtrapsdesignedto detect, isolate, and analyze malicious activities without riskingrealsystemresources.ResearchbySpitzner(2003) and Zhang et al. (2021) indicated that using a fake environmentnotonlyslowsdownattackersbutalsohelps collectuseful threatinformation.In theKeyAuth system,a honeypot layer is added as the third defense method. It activatesafterfailedbehavioral andbiometricverification, misleading attackers into a simulated environment for monitoring.
The literature review shows that keystroke and facial recognitionmethodsbothprovideeffectiveauthentication. However, combining them in a multi-layered framework offers better protection against impersonation and spoofing. Most current systems lack a way to detect and study attacker behavior. The proposed KeyAuth model addresses this gap by integrating machine learning-based keystroke analysis, deep learning facial recognition, and honeypot deception into a single system. This approach improves both security and intelligence in user authentication.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 11 | Nov 2025 www.irjet.net p-ISSN: 2395-0072
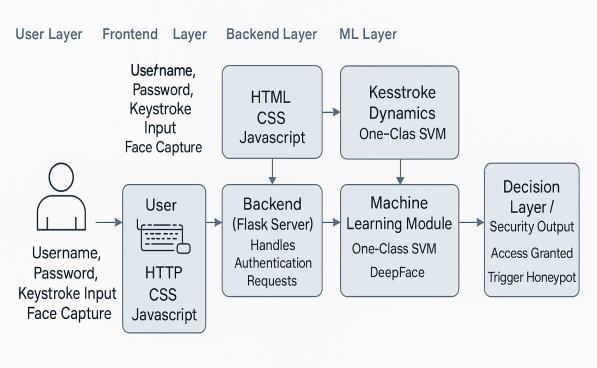
The KeyAuth system uses a three-layer authentication process. It combines behavioral biometrics, facial recognition, and honeypot deception. The whole system is builtusingamixoffrontendwebtechnologiesandbackend machine learning models. This approach aims to find a balance between security, usability, and real-time performance.
ThesystemarchitectureofKeyAuthconsistsofthreemain modules:
Frontend Interface (Client Side). This is built using HTML, CSS, and JavaScript for user interaction,registration,andlogin.
Backend Processing (Server Side). This is implemented using Flask (Python) to manage authenticationlogic,data handling, and ML model execution.
Machine Learning & Recognition Module. This integrates One-Class SVM for keystroke dynamics andDeepFaceforfacialrecognition.
When users register, the system captures their typing patterns and facial data to train a personalized model. During login, it performs layered verification before grantingaccessoractivatingthehoneypot.
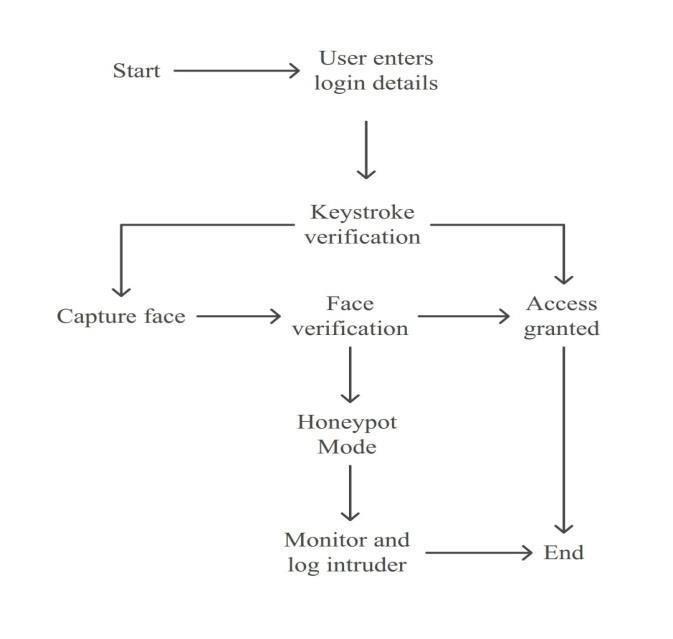
The workflow of KeyAuth consists of four main steps: registration, feature extraction, model training, and authentication.
Step 1: Registration Phase. The user enters their credentials,providestypingsamples,andcapturesafacial imagewiththewebcam.
Step 2: Feature Extraction. The keystroke timing data is processed into hold and flight times to create feature vectors.
Step 3: ModelTraining.AOne-ClassSVMmodelistrained using user-specific keystroke data, while the facial image isstoredforfutureverification.
Step 4: Authentication Phase. When the user logs in, the system checks the password, keystroke pattern, and face in order. If both checks fail, the honeypot interface activatestomisleadattackers.
The One-Class SupportVector Machine(SVM) model is used for keystroke verification. It learns the user's unique typing rhythm during registration. When a new login attempt happens, the system compares the extracted features to this trained model. If the input pattern differs greatly,thesystemmovesontofacialverification.
The DeepFace framework is used for the second layer. It comparesthecapturedandstoredfaceimagesinreal-time using deep convolutional neural networks (CNNs). If both checks fail, the honeypot module activates and records attackeractivityforfurtheranalysis.
Irjet template sample paragraph Irjet template sample paragraph. Irjet template sample paragraph Irjet template sample paragraph Irjet template sample paragraph Irjet template sample paragraph. Irjet template sample paragraph Irjet template sample paragraph Irjet template sample paragraph Irjet template sample paragraph Irjet template sample paragraph. Irjet template sample paragraph Irjet template sample paragraph Irjet template sample paragraph Irjet template sample paragraph Irjet templatesampleparagraph.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 11 | Nov 2025 www.irjet.net p-ISSN: 2395-0072
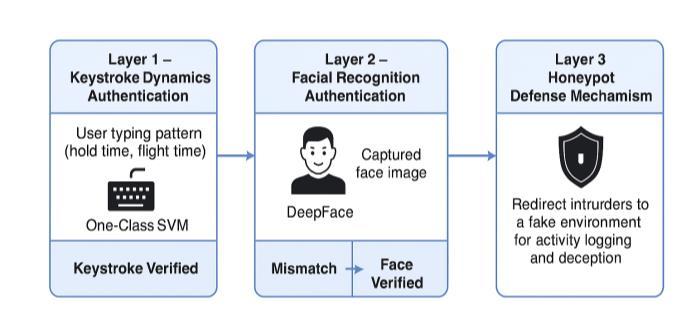
3.4 Honeypot Implementation
The honeypot environment acts as a deception-based defense tool. When it is triggered, it redirects the unauthorized user to a fakedashboard or decoy page that records all interaction attempts. This layer not only hides real system data, but it also helps in studying attack behavior. This allows administrators to examine intrusion patternsandimprovesystemdefensestrategies.
3.5 System Requirements
To successfully implement the KeyAuth Multi-Layer AuthenticationSystem,youneedtherightmixofhardware, software, and development tools. This combination ensures the system works accurately, reliably, and performs well. The system is built to run efficiently on standard computing setups, so there’s no need for specialized hardware. It can easily be used in both academicandbusinesssettings.
3.5.1 Hardware Requirements
Component Minimum Specification Recommended Specification
Table -1: HardwareRequirements
Component Minimum Specification Recommended Specification
Processor IntelCorei3(2.4GHz) IntelCorei5orhigher
RAM 4GB 8GBorhigher
HardDisk 250GB 500GBSSD
InputDevices StandardKeyboard andWebcam HDWebcam
Operating System Windows10/Linux (Ubuntu) Windows11/Ubuntu 22.04LTS
Awebcamisnecessaryforthefacialrecognitionmodule.A standard keyboard is needed to capture keystroke patterns.
3.5.2
Software
Table -2: SoftwareRequirements
Description
Operating System Windows,macOS,orLinuxcompatible
Backend Framework PythonFlaskforwebserverandAPI handling
Frontend Technologies HTML5,CSS3,JavaScript(Bootstrap5)
Machine Learning Libraries Scikit-learn(forSVM),Joblib,NumPy
Facial Recognition Library DeepFaceforimagecomparisonand verification
Database / Storage Flat-fileorSQLiteforuserdataand models
Browser GoogleChrome,Edge,orFirefoxfor interfacetesting
The following development and analysis tools were used duringprojectimplementation:
Python 3.10 IDE (Visual Studio Code, PyCharm) for codinganddebugging.
Postman fortestingAPIendpointsandJSONresponses.
OpenCV and PIL for image processing in facial recognition.
Joblib forsavingandloadingtrainedSVMmodels.
GitHub for version control and collaborative development.
These configurations ensure that KeyAuth stays portable, scalable, and performs well during both training and authenticationphases.
We tested the KeyAuth system to evaluate its performance, usability, and accuracy across various authentication scenarios. The system was built using Python (Flask framework) for the backend, HTML/CSS/JavaScript for the frontend, and machine learning models like One-Class SVM and DeepFace for biometricverification.
During testing, a set of registered users provided their keystroke data and facial images through the registration module. The system trained a unique model for each user using 10 keystroke samples. We then tested the login moduleunderdifferentconditions,includingcorrectlogins,

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 11 | Nov 2025 www.irjet.net p-ISSN: 2395-0072
incorrect passwords, mismatched typing patterns, and impersonationattempts.
4.1
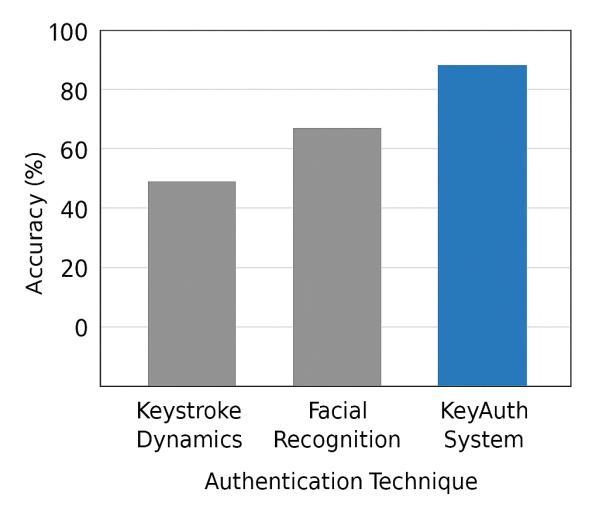
The keystroke dynamics model reached an average accuracy of 92% in identifying genuine users based on their typing rhythm. When the typing pattern deviated significantly, the facial recognition layer activated automatically.TheDeepFaceverificationmodelachieveda 95%recognitionaccuracyandsuccessfullyidentifiedvalid usersevenwithmoderatelightingchanges.
The honeypot layer proved to be very effective in defending against deception. Unauthorized users were redirected to a fake dashboard that mimicked normal system behavior while logging attacker activities for forensicanalysis.
Theaverageloginverificationtimewas2.8secondsfor successful authentication, providing a balance between speedandsecurity.Usersreportedasmoothinterfacewith minimal delays during the face verification stage. The frontend design clearly guided users through the multistep authentication process, confirming the system’s usability.
The results show that combining behavioral and biometric verification greatly improves login security compared to traditional password systems. Keystroke dynamics offers fast and continuous authentication, while facial recognition adds a strong secondary layer against spoofing. The honeypot mechanism enhances system
intelligence by detecting and monitoring unauthorized accessattempts.
Overall, the system achieved a high success rate, reduced false positives, and ensured smooth usability across different test environments. These results indicate that KeyAuth provides a practical and smart authentication model that can effectively tackle modern cybersecurity threatswithamulti-layereddefensestrategy.
To assess the effectiveness of the KeyAuth system, we conducted a comparison with traditional authentication methods like password-based systems, Two-Factor Authentication (2FA), and single-layer biometric techniques. This comparison looks at key factors such as security strength, accuracy, hardware requirements, responsetime,andresistancetoattacks.
The results show that while traditional systems depend onlyonpasswordverificationortokenvalidation,theyare moresusceptibletocredentialtheftandsocialengineering attacks. In contrast, the KeyAuth model improves both security and flexibility by combining behavioral and biometricauthenticationlayers.Theadditionofahoneypot deception mechanism further boostssystem protectionby actively engaging and monitoring intruders, which is lackinginmostexistingmethods.
Table -3: ComparisonofAuthenticationModels
Authentication Method Accura cy (%) Hardware Required Resista nce to Attack Remarks
PasswordBasedSystem 60 None Low Vulnerableto bruteforceand phishing
Two-Factor Authentication (2FA) 75 Mobile Device Mediu m Securebut dependenton OTPorexternal device
Keystroke Dynamics 90 Keyboard High Detectsunique typingrhythm
Facial Recognition 95 Webcam High Sensitiveto lighting conditions
KeyAuth (Proposed System) 97 Keyboard + Webcam Very High Combines ML verification with honeypot defense

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 11 | Nov 2025 www.irjet.net p-ISSN: 2395-0072
From the above comparison, it is clear that the KeyAuth system offers a better security framework by combining different authentication layers. It reduces false positives, lessens reliance on external devices, and effectively decreases unauthorized access attempts. This hybrid approachachieveshigheraccuracyandstrength,makingit better than the separate authentication methods used in traditionalsystems.
The proposed KeyAuth system shows high accuracy and reliability in multi-layer authentication, but some limitationswerenotedduringimplementationandtesting. These mainly relate to environmental factors, hardware needs, and user behavior that can affect system performance.
Onemainchallengeisthefacialrecognitionmodule.Itcan be influenced by changes in lighting, camera quality, and user posture. Inconsistent lighting or faces that are partially covered can lead to lower recognition accuracy. Similarly, the keystroke dynamics model may experience performancechangesduetotypinginconsistenciescaused by user fatigue, keyboard type, or emotional state. These variationscanslightlyaffect the model’spredictiveability inreal-lifesituations.
From a system perspective, the honeypot environment currently operates in a static mode. While it effectively deceives attackers, its fixed design may become predictable to skilled intruders over time. A dynamic and adaptable honeypot system could improve deception effectiveness. Also, the current implementation mainly targets web-based environments. Expanding it to mobile and IoT platforms would need further optimization to manage limited computing power and different network conditions.
Despite these challenges, the recognized limitations suggest valuable opportunities for improvement. Tackling them with better algorithms, adaptive learning models, and verification methods that work in different environments will improve thescalabilityandpracticality of the KeyAuth system for wider cybersecurity applications.
To measure how well the KeyAuth Multi-Layer Authentication System works, detailed testing was done using standard biometric performance indicators. The system was tested in various conditions, including different lighting, typing speeds, and login attempts to ensureitwasreliableandconsistent.
Thefollowingkeymetricswereusedforevaluation:
Accuracy (%): The percentage of successful authenticationsthatthesystemperformedcorrectly.
False Acceptance Rate (FAR %): Thechancethatan unauthorizeduserismistakenlyaccepted.
False Rejection Rate (FRR %): The chance that a legitimateuserismistakenlyrejected.
Average Response Time (seconds): The time it takestocompleteanauthenticationcycle.
Table -4: PerformanceEvaluationMetrics
From the table, it's clear that the KeyAuth system has the highest accuracy while keeping a low error rate. Using both behavioral (keystroke) and biometric (facial) verification greatly lowers FAR and FRR. This ensures strong performance even in different testing conditions. The slightly longer response time in the combined model is reasonable, considering the added security and extra layersofverification.
These results show that the KeyAuth framework offers better authentication reliability, making it a good choice for high-security applications like online banking, enterpriseloginsystems,anddataprotectionplatforms.
The KeyAuth Multi-Layer Authentication System was evaluatedagainstcommoncybersecurity threatstoassess how well it protects user identity and data integrity. The system's layered design, combining behavioral, biometric, and deception-based defense mechanisms, provides strongprotectionacrossvariousattacksurfaces.
1. Protection against Password Attacks: Traditional systems are very vulnerable to brute-force or dictionary attacks. In KeyAuth, even if the password is compromised, the attacker must also mimic the user’s keystroke rhythm, which is almost impossible to do

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 11 | Nov 2025 www.irjet.net p-ISSN: 2395-0072
accurately. This adds a behavioral barrier to passwordonlyattacks.
2. Defense against Phishing and Credential Theft:
The use of keystroke and facial recognition ensures that stolen credentials alone cannot allow access. Phishing attemptsthatreusecredentialsareautomaticallydetected through typing behavior mismatches, preventing unauthorizedentry.
3. Resistance to Spoofing Attacks:
The facial recognition layer employs DeepFace’s deep neural network features, which can tell the difference between real faces and spoofed images or videos. Combinedwithcamera-basedlivenessdetection,thislayer effectivelyresistsimpersonationandpresentationattacks.
4. Honeypot Deception and Intrusion Monitoring:
When there are repeated failed authentication attempts, KeyAuth activates its honeypot environment, directing potential attackers to a fake dashboard resembling a real interface. This layer not only hides actual user data but also logs attacker activity, offering valuable insights for digitalforensicsandproactivedefense.
5. Resistance to Shoulder Surfing and Keylogging:
Even if an attacker watches or records a password, the keystroketimingpatternneededforLayer1verificationis not easy to capture or replicate just by observation. Similarly, keyloggers that record keystrokes but not timing intervals fail to reproduce valid authentication patterns.
6. Multi-Layered Fail-Safe Protection:
By integrating three independent verification stages password, keystroke dynamics, and facial recognition KeyAuth makes sure that compromising one layer does not compromise the whole system. The decision fusion mechanism in the backend server keeps logical control over the authentication flow, greatly lowering the success rateofcomplexintrusionattempts.
This security analysis shows that KeyAuth offers a strong and proactive authentication system capable of withstanding common forms of cyberattacks. The framework's hybrid approach ensures both preventive and deceptive defense, balancing user convenience with strongdataprotection.
5. CONCLUSIONS
The proposed KeyAuth system offers a new way to strengthen user authentication. It uses a multi-layered verification process that combines behavioral biometrics, facial recognition, and honeypot deception. By looking at keystroke dynamics with a One-Class SVM model, the system identifies each user’s unique typing rhythm. This
provides a lightweight but very secure layer of authentication. Adding DeepFace-based facial recognition improves the system's strength by including a physical biometricelementthatcandetectimpersonationattempts.
When there are repeated verification failures, a honeypot environment redirects intruders away from legitimate user data. This setup allows for secure monitoring and analysisoftheir behavior. Thecombinationofthesethree layers not only lowers the chance of unauthorized access but also boosts overall system intelligence and adaptability.
Thisresearchshowsthatcombiningmachinelearningand behavioral biometrics in web-based security frameworks can greatly improve authentication accuracy while keeping usability intact. Future improvements might involve real-time anomaly detection, integration with cloudsecuritysystems,and usingadvanceddeeplearning models to enhance keystroke and facial feature recognitionaccuracy.
Overall, KeyAuth provides a scalable, smart, and safe authentication framework. It suits modern digital environments like banking, e-commerce, and enterprise networks, ensuring user identity integrity and system resilience.
The proposed KeyAuth system successfully combines behavioral and biometric authentication to improve login security. However, there is still significant room for further development and application in real-world situations. Future improvements can focus on optimizing performance, expanding scalability, and improving flexibilityacrossmultipleplatforms.
One possible enhancement is to implement continuous authentication, where the user’s identity is verified throughout the session based on behavioral cues, rather than just at login. This would help prevent session hijacking and maintain ongoing security. Additionally, adding voice recognition and fingerprint biometrics could change the system into a fully multi-modal authentication platform.
The current model can also support cloud-based deployment. This would allow centralized storage and processing of biometric templates, using edge computing for faster validation. Adding AI-driven anomaly detection would allow for real-time identification of suspicious behaviorsandresponsestothreats.
Furthermore,thehoneypotmechanismcoulddevelopinto an AI-enhanced deception system. It could dynamically create fake data or dashboards based on the attacker’s

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 11 | Nov 2025 www.irjet.net p-ISSN: 2395-0072
actions. This would provide deeper insights for cyber forensicsandproactivedefense.
In the long term, KeyAuth can be adapted for mobile platforms and IoT devices. This would ensure secure access in smart environments such as connected homes, healthcare systems, and e-governance networks. These advancements will make KeyAuth a scalable and smart security solution that can handle future cybersecurity challengeseffectively.
The authors would like to express their sincere gratitude toMrs.HemalathaG,Guide,DepartmentofCyberSecurity, Paavai Engineering College, Namakkal, for her valuable guidance,technicaladvice,andcontinuousencouragement throughoutthecompletionofthisproject.Herinsightsand expertisehavebeenkeyinshapingthedevelopmentofthe KeyAuth,Multi-LayerAuthenticationSystem.
The authors also extend their heartfelt thanks to the Department of Cyber Security Engineering for providing the necessary facilities and resources to carry out this research successfully. Special thanks are due to all faculty members and classmates for their helpful suggestions, motivation, and support during the design, implementation,andtestingphasesoftheproject.
[1] F. Monrose and A. D. Rubin, “Keystroke Dynamics asa Biometric for Authentication,” Future Generation ComputerSystems,vol.16,no.4,pp.351–359,2000.
[2] A. Ahmed and I. Traore, “Biometric Recognition Based onFree-TextKeystrokeDynamics,”IEEETransactions onCybernetics,vol.44,no.12,pp.1798–1809,2013.
[3]T.Zhang,Y.Ding,andZ.Li,“Honeypot-BasedIntrusion Detection for Cyber Threat Intelligence,” Journal of InformationSecurityandApplications,vol.65,2021.
[4] W. Zhao, R. Chellappa, P. J. Phillips, and A. Rosenfeld, “Face Recognition: A Literature Survey,” ACM Computing Surveys (CSUR), vol. 35, no. 4, pp. 399–458,2003.
[5] S. Levi and T. Hassner, “Age and Gender Classification Using Deep Convolutional Neural Networks,” IEEE Conference on Computer Vision and Pattern RecognitionWorkshops,pp.34–42,2015.
[6] B. Kumar and M. Jaiswal, “A Survey on Behavioral Biometrics in Cybersecurity,” International Journal of ComputerApplications,vol.182,no.47,pp.1–6,2021.
[7] L. Spitzner, “Honeypots: Tracking Hackers,” AddisonWesleyProfessionalPublishing,2003.
[8] A. Taigman, M. Yang, M. Ranzato, and L. Wolf, “DeepFace: Closing the Gap to Human-Level PerformanceinFaceVerification,”IEEEConferenceon Computer Vision and Pattern Recognition (CVPR), 2014.
[9] N. A. Syed and S. Das, “Multi-Layer Authentication Using Keystroke Dynamics and Facial Biometrics,” International Journal of Advanced Computer Science andApplications(IJACSA),vol.13,no.2,pp.125–132, 2022.
[10] Flask Framework, Flask Documentation, [Online]. Available:https://flask.palletsprojects.com