
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 03 | Mar 2025 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 03 | Mar 2025 www.irjet.net p-ISSN: 2395-0072
Rutuja Rajole,
1 Senior Design Engineer, Tata Technologies Ltd
Abstract - The increasing dependency on Software-Defined Vehicles (SDVs) has led to various security vulnerabilities within in-vehicle networks, whichcan impactthedriversafety, personal information, and driver’s assets. In thebeginningera of security methods used are no longer able to address the rapidly changing threat possibilities. The purpose of this project is to implement a complete TARA analysis approach which is uniquely designed for the security needs of SDVs. My project strategy involves a multi-layered threat analysis framework. These will help us to identify, evaluate,andreduce potential security threats effectively. Considering the TARA method, we are targeting to reduce security risks, boost our ability to detect threats, and make the overall safety of software defined vehicles better.
Key Words: TARA, SDV, IVN, cybersecurity, attack, asset
1. INTRODUCTION
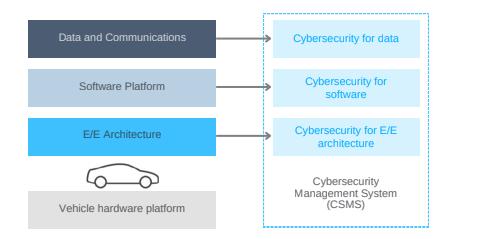
ThreatAnalysisandRiskAssessmentisnecessarymethod whichisusedtoupgradethecybersecuritywithinSoftwareDefinedVehicles.Intheeraofzonalarchitectures&domain architectures vehicles are becoming more self-analyzed, connectedandautomated,theyareexposedtoanincreasing numberofcyber-attacksthatcouldrisksafety,functionality, anduserprivacy.TARAanalysisisplayingacrucialrolein identifying and evaluating the cyber-attack. TARA allows industrialisttodevelopandimplementcompleteandrobust solutions. TARA is in line with industry standards that is ISO/SAE21434whichisthecybersecuritystandard,which provides a robust framework for analyzing cybersecurity risks across the vehicle's lifecycle and architecture. The process involves many stages that are identifying assets, setting up attack scenarios, examining risks, evaluating impacts,andmeasuringrisks.Bythoroughlyinvestigating potential cyber-attack and their impact on vehicle architectures and driver’s safety, TARA framework allows organizations to prioritize risks severity and make robust decisionsonthenecessarysecuritymeasures.
2.
1. The identification of Essential features and functionalities in SDV. The above task has been successfully completed, by focusing on the some particular crucial ECU functionalities that will go
through TARA analysis based on their value to the vehiclesafetyandoperation.
2. The complete analysis of the architecture design requirements for the SDV world. There are main two tasksubdivision.
a. TheStudyofarchitecture:Inthiscompletestudyof thearchitecture,ithasboththeelementslikehardware andsoftwarecomponentstocreateanadaptablesystem. Itcoversvariouslayerslikethehardwarecomponents (i.e.CPUs,sensors,ECUs)andtheotherbigcomponent Software framework that supports vehicle functionalities.
b. CheckingofCyber-attackvulnerabilities:Inthiswe are more focuses on the major potential pathways wherethecyberthreatscouldexploitweaknessinside thearchitecturethusitleadstoamajordisaster,which includesthevulnerabilitiesincommunicationinterfaces, and software update process, here comes major one centralizedcontrolunits
3. Evaluatetheexistingcybersecurityvulnerabilities and threats specific to the SDV. Applying effectively cybersecuritymeasurestoaddressidentifiedrisks.Then analyzing how well these cybersecurity solutions improve the resilience of SDV against the potential threats
A thorough and flexible framework for controlling cybersecuritythreatsinsoftware-definedvehiclesisoffered bytheTARAtechnique.Manufacturersanddeveloperscan enhancesecurityposture,proactivelyresolvevulnerabilities,

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 03 | Mar 2025 www.irjet.net p-ISSN: 2395-0072
and guarantee the dependability and safety of SDVs by implementingTARA.Thisstrategy not onlycontributes to theprotectionofvitalautomotivesystemsbutalsofosters user trust by showcasing a dedication to strong cybersecurityprocedures.

3. Cybersecurity Features:
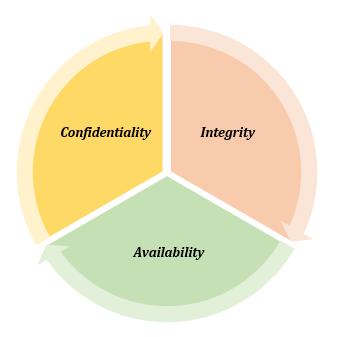
TheCIAmodelofcybersecurityis
1. Confidentiality:
An organization's attempt to ensure that data is kept private or hidden are referred to as confidentiality. Making sure that individuals withouttheappropriateauthorisationareunableto accessassetsthatarecrucialtoyourcompanyisa crucial part of protecting confidentiality. For instance, in order to diagnose the data, suppliers andvendorsshouldhaveminimalaccesstoanyof your vehicle networks. Confidentiality can be violated in a number of ways. This could entail direct attacks meant to obtain access to systems that the attacker is not authorised to view. An attackermayalsotrydirectlytogetintoadatabase orapplicationinordertostealorchangedata.
2. Integrity:
Integrityentailsensuringthatyourdataisreliable and unaltered. Only when your data is genuine, accurate,andtrustworthyisitsintegritypreserved. Integrity is frequently compromised on purpose. For instance, you may have maintained certain informationaboutyourcar'sbrandingtoincrease sales,butifitisfalse,thosewhoarelookingintoit mightconcludethatthecompanyisunreliable.An attacker could circumvent an intrusion detection system (IDS), modify file settings to permit unwantedaccess,ormanipulatethesystem'slogsto concealtheattack.Accidentalviolationsofintegrity arealsopossible.Someonemightinadvertentlytype theincorrectcodeorcommitanotherthoughtless error. You can employ digital certificates, digital signatures,encryption,orhashingtosafeguardthe integrityofyourdata.
3. Availability:
Dataisfrequentlyworthlessunlessitisaccessible toboththeorganization'semployeesandtheclients theyserve,evenifitiskeptprivateanditsintegrity preserved.Thisimpliesthatapplications,networks, andsystemsmustbeoperatingattheappropriate timesandintheappropriatemanner.Accessingthe data shouldn't take too long, and those who have accesstocertaininformationshouldbeabletouse it when they need to. Organizations can utilize redundant servers, networks, and applications to guaranteeavailability.
4. Cybersecurity Threat types:
1. Spoofing:
When a hacker assumes the identity and data of anotherindividualinordertoperpetratefraud,this isknownasidentityspoofing.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 03 | Mar 2025 www.irjet.net p-ISSN: 2395-0072
2. Tampering:
Wheninformationisalteredwithoutpermission,it isreferredtoasdatatampering.
3. Repudiation:
Threats of repudiation occur when a malevolent person conducts a malicious or unlawful action within a system and subsequently denies any involvementintheattack.
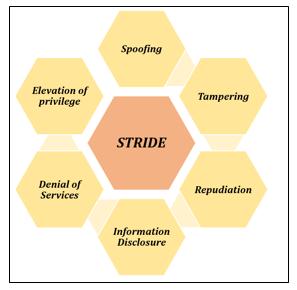
Fig: STRIDE
4. Information Disclosure:
Information leaking is another name for informationdisclosure.
5. Denial Of Service(DOS):
Attacksknownasdenialofservice(DoS)preventa legitimateuserfromaccessingresourcesthatthey oughttobeableto.
6. Elevation of Privilege:
Anauthorizedorunauthorizeduserinthesystem canobtaininformationthattheyarenotpermitted toviewbyelevatingtheirprivileges.
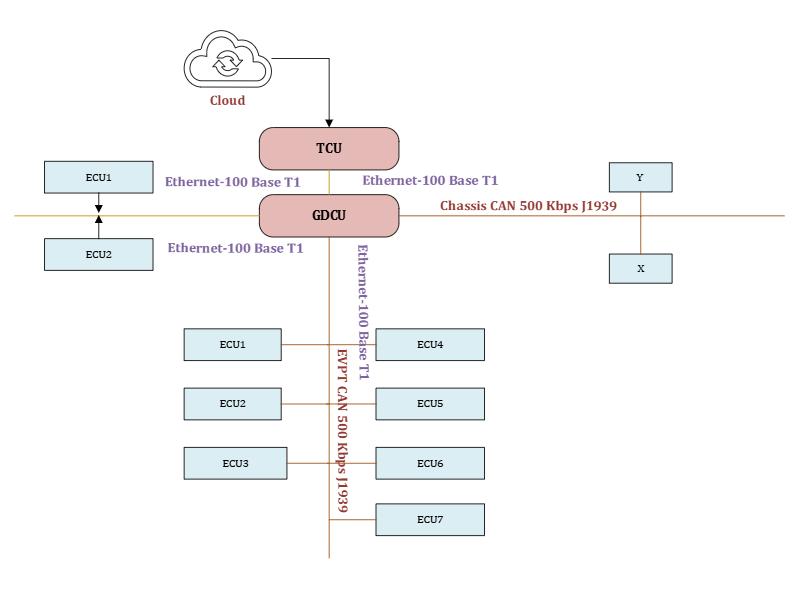
5. TARA Analysis of EV powertrain architecture:
1. DetailedAnalysisofArchitectureRequirementsfor SDVs
Thereismaintwotasksubdivision.
a. Study of In-Vehicle Architecture: Study of the SDV architecturewhichinvolveszonal,domainarchitectures and which involves HPCs, focusing on its hardware, software, and connectivity layers to understand how various ECUs interact to each other and supporting various vehicle functionalities, application and SDV features.
b. The Cyber-Attack Risks Identification involves performingtheAnalysisoftheIn-vehiclearchitectures whichinvolveszonal/domaincontrollerarchitecturesto
discover possible paths that attackers can attack or manipulate, such as CAN/Ethernet communication interfaces, OBD connectors, software updates, and centralizedECUslikedomaincontrollersorHPCs.
2. Basedonthecriticalityprioritizationofthevehicle functionsandapplications:Havetoidentifyandfocuson animportantvehiclefunctionalitieswhichareessential for the safety, operation and especially for the user experience,privacy.Thesefunctions,suchasADAS,V2X communication,infotainmentsystems,andpowertrain control,areselectedforTARAanalysisbasedontheir importanceandpossibleimpactifharmed.
3. Threat Analysis and Risk Assessment analysis of selectedfunctionalitieswhichwillbebasedondriver’s safety and privacy, vehicle important operation, SDV featuresandpowertrain operations,Performa robust TARA analysis on the selected functionalities by identifyingassociatedassets,evaluatingpossiblethreats andrisks,andassessingtheimpactofsuccessfulattacks. Evaluatingrisksbycombiningpossibilityandseverity, then propose reduction strategies such as encryption algorithms,secureupdates,orredundancytoenhance theoverallcybersecurityofSDVs
6. Analysis of Threat Scenario:
a) EV Domain Controller Area Network
Threat Scenario:
1. Potential threat scenarios for an Electric Vehicle(EV)DomainControllerAreaNetwork (CAN bus) considering the cybersecurity properties of confidentiality and asset type spoofing
Confidentiality Breach:
Scenario:Anattackerobtainsunauthorizedaccess totheEVPowertrainCANbusnetworkandinterchange confidential data transmitted between different ECUs withintheEV'spowertraindomain.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 03 | Mar 2025 www.irjet.net p-ISSN: 2395-0072
Thisdatacouldinclude:
o Informationaboutbatteryvoltage,current, temperatureandstateofcharge.
o Details about motor speed, torque and derateinfo,regenerationinfo
o Signals sent from the brake pedals, accelerator pedals and steering wheel to controlacceleration,brakingandsteering.
o Thedatafromvehiclecontrolunitsuchas fuel economy, various fault status, Telltale statusetc.
Impact: Disclosure of this confidential data could haveseveralnegativeimpacts:
o Compromised battery data could lead to inaccurateestimatesofthevehicle'sremaining driving range, causing inconvenience to the driver.
o Tampering with motor controller data couldpotentiallyaffectvehicleperformanceor evenlead to safetyhazards andalsosafety of thedriver.
o Interchangedcontrolcommandscouldbe used by attackers to understand how the vehicle operates and potentially develop opportunitiesforfutureattacks.
o Tamperingoffaultdatacanleadtodriver’s lifeifanyfaulttelltalewillnotblink.
Asset Type Spoofing:
Scenario:Aharmfuldevicemimicstheidentity ofanauthorizeddomaincontrollerECUonthe CANbus.Aftersuccessfullygainstheaccessof ECU,attackertheninjectinaccuratedataonthe CAN bus or alter existing CAN data.
Let’sconsidertwopossibilities:
o AHackermightmimicabatterysensorand sendfakedataindicatingagoodhealthof batteryevenifit’sdefective.Thiscandelay requiredmaintenanceofbatteryunitand alsodisplaywronginformationofbattery parameters.
o An unauthorized person might mimic a control unit like the motor controller/ vehicle control unit and send inaccurate commands. This can potentially affect vehicle handling or even lead to safety risks.
Impact: Asset type spoofing can have serious consequences:
o DegradedPerformance:Fakedatafromaspoofed sensorcouldleadtothevehicleenteringlimp homemodeorexperiencingunexpected behaviour.
o SafetyHazards:Spoofedcontrolcommandscould trickthevehicleintoperformingunsafeactions, whichwillimpactthedriver'ssafety.
o ReducedSystemReliability:Thepresenceofa spoofeddevicecandisturbthecommunicationon
theCANbus,hamperingtheoverallreliabilityof thevehicle'ssystems.
Impact Rating for Confidentiality Breach and Asset Type Spoofing on EV CAN Bus
Let's breakdown the potential impact of confidentiality breaches and asset type spoofing on an EV Powertrain networkintodifferentcategories
Safety:
o Severity:High
o Description: Tampering with confidential CAN communication data between ECUs or mimicking authorized ECUs can lead to the safety-critical activities such as unexpected braking, loss of steeringcontrol,orcompletesystemfailures.These scenarios can cause a high risk of accidents and injuries.
Finance:
o Severity:Medium
o Description:Whilefinanciallossesmightnotbe immediate,asecuritybreachcouldleadto:
i. Costlyrepairs:Incorrectdatafromspoofed sensors might resulting of unnecessary repairsorreplacementsofcomponents.
ii. Warranty claims: Malfunctions caused by attacks might not be covered under warranty,becauseofwhichfinancialissues mayoccurtodriver/vehicleowner.
iii. Recall campaigns: In severe cases, It will impact manufacturer financially s well if vehicle to be returned or any particular ECUtobereplacedbymanufacturerunder someclaims.
Operational:
o Severity:High
o Description:Confidentialitybreachesandspoofing candisturbtheoperationalcapabilitiesoftheEV:
i. Reduced driving range: Inaccurate range estimationduetoduetoinaccuratebattery datacanleadtoinconvenienceanddisturb plannedjourneysanditwillbeharmfulin caseofanyemergency.
ii. Limitedfunctionality:Thevehiclegoesinto limp home mode due to malfunctioning causedbyspoofedsensorsontheVehicle CANnetwork.
iii. Increased downtime: Understanding of issues and then diagnose them will take some time which will cause vehicle unavailability
Privacy:
o Severity:High
o Description: The privacy impact depends on the specificdataaltered/tampered:
i. Limitedprivacyimpact:Interchangeddata might only include non-personal informationlikebatteryvoltageormotor speed.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 03 | Mar 2025 www.irjet.net p-ISSN: 2395-0072
ii. Moderate privacy impact: In some cases, interchangeddatamightrevealthedriver's location or driving habits, which will eventuallyhampersdriver'sprivacy.
ThecreationandupkeepofSDVsthatincorporatetheTARA methodologypromoteamoresecureandrobustautomotive ecosystem. It contributes to the protection of vehicle networks and raises public confidence in the security and dependabilityofcutting-edgeautomotivesystems.
[1]TeriLenard;AnastasijaCollen;NielsAlexanderNijdam; MeriemBenyahya.ASystematicReviewofThreatAnalysis and Risk Assessment Methodologies for Connected and AutomatedVehiclesARES2023,August29–September01, 2023,Benevento,Italy
[2]JherrodThomas.HATARA:ANovelApproachbyFusion ofHARAandTARAforSystemSafetyandSecurityAnalysis, February,2024
[3] Loskin, Ilona. TARA+AD: Threat Analysis and Risk AssessmentforAutomatedDriving–CybersecurityofRoad Vehicles,2023
[4] Meriem Benyahya, Anastasija Collen, Sotiria Kechagia, andNielsAlexanderNij-dam.2022.Automatedcityshuttles: Mapping the key challenges in cybersecurity, privacy and standards to future developments. Computers & Security 122(112022),102904
[5] ISO/SAE 21434:2021Road vehicles Cybersecurity engineering
[6]TaxonomyandDefinitionsforTermsRelatedtoDriving Automation Systems for OnRoad Motor Vehicles J3016_202104
o https://www.fortinet.com/resources/cyberglossar y/cia-triad