
AREA
00. Implementation Resources
04. Context of the Organization
05. Leadership
06. Planning
07. Support
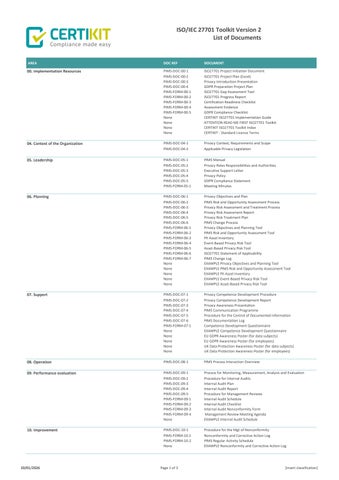

AREA
00. Implementation Resources
04. Context of the Organization
05. Leadership
06. Planning
07. Support
DOC REF
PIMS-DOC-00-1
PIMS-DOC-00-2
PIMS-DOC-00-3
PIMS-DOC-00-4
PIMS-FORM-00-1
PIMS-FORM-00-2
PIMS-FORM-00-3
PIMS-FORM-00-4
PIMS-FORM-00-5
None
None
None
None
PIMS-DOC-04-1
PIMS-DOC-04-2
PIMS-DOC-05-1
PIMS-DOC-05-2
PIMS-DOC-05-3
PIMS-DOC-05-4
PIMS-DOC-05-5
PIMS-FORM-05-1
PIMS-DOC-06-1
PIMS-DOC-06-2
PIMS-DOC-06-3
PIMS-DOC-06-4
PIMS-DOC-06-5
PIMS-DOC-06-6
PIMS-FORM-06-1
PIMS-FORM-06-2
PIMS-FORM-06-3
PIMS-FORM-06-4
PIMS-FORM-06-5
PIMS-FORM-06-6
PIMS-FORM-06-7
None
None
None
None
None
PIMS-DOC-07-1
PIMS-DOC-07-2
PIMS-DOC-07-3
PIMS-DOC-07-4
PIMS-DOC-07-5
PIMS-DOC-07-6
PIMS-FORM-07-1
None
None
None
None
None
08. Operation
09. Performance evaluation
10. Improvement
PIMS-DOC-08-1
PIMS-DOC-09-1
PIMS-DOC-09-2
PIMS-DOC-09-3
PIMS-DOC-09-4
PIMS-DOC-09-5
PIMS-FORM-09-1
PIMS-FORM-09-2
PIMS-FORM-09-3
PIMS-FORM-09-4
None
PIMS-DOC-10-1
PIMS-FORM-10-1
PIMS-FORM-10-2
None
DOCUMENT
ISO27701 Project Initiation Document
ISO27701 Project Plan (Excel)
Privacy Introduction Presentation
GDPR Preparation Project Plan
ISO27701 Gap Assessment Tool
ISO27701 Progress Report
Certification Readiness Checklist
Assessment Evidence
GDPR Compliance Checklist
CERTIKIT ISO27701 Implementation Guide
ATTENTION READ ME FIRST ISO27701 Toolkit
CERTIKIT ISO27701 Toolkit Index
CERTIKIT - Standard Licence Terms
Privacy Context, Requirements and Scope
Applicable Privacy Legislation
PIMS Manual
Privacy Roles Responsibilities and Authorities
Executive Support Letter
Privacy Policy
GDPR Compliance Statement
Meeting Minutes
Privacy Objectives and Plan
PIMS Risk and Opportunity Assessment Process
Privacy Risk Assessment and Treatment Process
Privacy Risk Assessment Report
Privacy Risk Treatment Plan
PIMS Change Process
Privacy Objectives and Planning Tool
PIMS Risk and Opportunity Assessment Tool
PII Asset Inventory
Event-Based Privacy Risk Tool
Asset-Based Privacy Risk Tool
ISO27701 Statement of Applicability
PIMS Change Log
EXAMPLE Privacy Objectives and Planning Tool
EXAMPLE PIMS Risk and Opportunity Assessment Tool
EXAMPLE PII Asset Inventory
EXAMPLE Event-Based Privacy Risk Tool
EXAMPLE Asset-Based Privacy Risk Tool
Privacy Competence Development Procedure
Privacy Competence Development Report
Privacy Awareness Presentation
PIMS Communication Programme
Procedure for the Control of Documented Information
PIMS Documentation Log
Competence Development Questionnaire
EXAMPLE Competence Development Questionnaire
EU GDPR Awareness Poster (for data subjects)
EU GDPR Awareness Poster (for employees)
UK Data Protection Awareness Poster (for data subjects)
UK Data Protection Awareness Poster (for employees)
PIMS Process Interaction Overview
Process for Monitoring, Measurement, Analysis and Evaluation
Procedure for Internal Audits
Internal Audit Plan
Internal Audit Report
Procedure for Management Reviews
Internal Audit Schedule
Internal Audit Checklist
Internal Audit Nonconformity Form
Management Review Meeting Agenda
EXAMPLE Internal Audit Schedule
Procedure for the Mgt of Nonconformity
Nonconformity and Corrective Action Log
PIMS Regular Activity Schedule
EXAMPLE Nonconformity and Corrective Action Log
A.1 Control objectives and controls for PII controllers
A.2 Control objectives and controls for PII processors
A.3 Control objectives and controls for PII controllers and PII processors
PIMS-DOC-A1-2-1
PII Analysis Procedure
PIMS-DOC-A1-2-2 Legitimate Interest Assessment Procedure
PIMS-DOC-A1-2-3 PII Controller-Processor Agreement Policy
PIMS-DOC-A1-2-4
PII Processor Assessment Procedure
PIMS-DOC-A1-2-5 Letter to Processors
PIMS-DOC-A1-2-6
PIMS-DOC-A1-2-7
Privacy Impact Assessment Process
Privacy Impact Assessment Report
PIMS-FORM-A1-2-1 Records of Processing Activities
PIMS-FORM-A1-2-2 PII Analysis Form
PIMS-FORM-A1-2-3 PIA Questionnaire
PIMS-FORM-A1-2-4 PII - Initial Questionnaire
PIMS-FORM-A1-2-5 Legitimate Interest Assessment
PIMS-FORM-A1-2-6 Consent Request Form
PIMS-FORM-A1-2-7 Contract Review Tool
PIMS-FORM-A1-2-8 PII Processor Assessment
PIMS-FORM-A1-2-9 Privacy Impact Assessment Tool
PIMS-FORM-A1-2-10
PIMS-DOC-A1-3-1
PIMS-DOC-A1-3-2
PIMS-DOC-A1-3-3
PIMS-DOC-A1-3-4
Data Processing Agreement
Privacy Notice Procedure
Website Privacy Policy
CCTV Policy
PII Principal Request Procedure
PIMS-DOC-A1-3-5 PII Principal Request Register
PIMS-DOC-A1-3-6
PIMS-DOC-A1-3-7
PII Principal Complaint Procedure
PII Principal Complaint Register
PIMS-FORM-A1-3-1 Privacy Notice Planning Form - PII Principal
PIMS-FORM-A1-3-2 Privacy Notice Planning Form - Other Source
PIMS-FORM-A1-3-3 PII Principal Request Form
PIMS-FORM-A1-3-4 PII Principal Request Rejection
PIMS-FORM-A1-3-5 PII Principal Request Charge
PIMS-FORM-A1-3-6 PII Principal Request Time Extension
PIMS-DOC-A1-4-1
Records Retention and Protection Policy
PIMS-DOC-A1-4-2 Privacy and Data Protection Policy
PIMS-DOC-A1-4-3 Data Masking Policy
PIMS-DOC-A1-4-4 Data Masking Process
PIMS-DOC-A1-4-5 Information Deletion Policy
PIMS-DOC-A1-5-1 Procedure for International Transfers of PII
PIMS-FORM-A1-5-1
Records of PII Disclosures
PIMS-FORM-A1-5-2 Records of PII Transfers
None
None
None
None
None
None
None
None
None
None
None
None
None
None
None
None
EXAMPLE Consent Request Form
EXAMPLE Legitimate Interest Assessment Form
EXAMPLE PII - Initial Questionnaire
EXAMPLE PII Analysis Form
EXAMPLE Privacy Impact Assessment
EXAMPLE PII Principal Request Form
EXAMPLE Privacy Notice - CCTV
EXAMPLE Privacy Notice - Employment
EXAMPLE Privacy Notice - Newsletter Signup
EXAMPLE Privacy Notice - Online Purchase
EXAMPLE Privacy Notice - Website Enquiry
EXAMPLE Privacy Notice Planning Form - Other Source
EXAMPLE Privacy Notice Planning Form - PII Principal
EXAMPLE Website Privacy Policy
EXAMPLE Records of PII Disclosures
EXAMPLE Records of PII Transfers
PIMS-DOC-A2-2-1 PII Processor Policy
PIMS-FORM-A2-2-1 Records of Processing Activities
PIMS-FORM-A2-2-2 Processor Employee Confidentiality Agreement
PIMS-DOC-A2-4-1 Processor Security Controls
PIMS-DOC-A2-5-1 Customer PII Transfer Policy
PIMS-DOC-A2-5-2 PII Disclosure Procedure
PIMS-FORM-A2-5-1 Records of Processor PII Transfers
PIMS-FORM-A2-5-2 Records of Processor PII Disclosures
PIMS-FORM-A2-5-3 Sub-Processor Agreement
PIMS-DOC-A3-3-1
Social Media Policy
PIMS-DOC-A3-3-2 HR Security Policy
PIMS-DOC-A3-3-3 AI Security Policy
PIMS-DOC-A3-3-4 Information Security Policy
PIMS-DOC-A3-3-5 Physical Security Policy
PIMS-DOC-A3-3-6 Anti-Malware Policy
PIMS-DOC-A3-3-7 Network Security Policy
PIMS-DOC-A3-3-8 Electronic Messaging Policy
PIMS-DOC-A3-3-9 Cloud Computing Policy
PIMS-DOC-A3-3-10 Acceptable Use Policy
PIMS-DOC-A3-4-1
PIMS-DOC-A3-5-1
PIMS-DOC-A3-6-1
PIMS-DOC-A3-7-1
PIMS-DOC-A3-7-2
PIMS-DOC-A3-8-1
InfoSec Roles Responsibilities and Authorities
Information Classification Procedure
Information Labelling Procedure
Information Transfer Procedure
Information Transfer Agreement
Access Control Policy
PIMS-DOC-A3-9-1
PIMS-DOC-A3-10-1
PIMS-DOC-A3-11-1
PIMS-DOC-A3-11-2
PIMS-DOC-A3-11-3
PIMS-DOC-A3-11-4
PIMS-DOC-A3-12-1
PIMS-DOC-A3-12-2
PIMS-DOC-A3-12-3
User Access Management Process
Supplier Information Security Agreement
Incident Response Plan Ransomware
Incident Response Plan Denial of Service
Incident Response Plan Data Breach
Incident Management Policy
Information Security Incident Response Procedure
PII Breach Notification Procedure
PII Breach Register
PIMS-FORM-A3-12-1 PII Breach Notification Form
PIMS-FORM-A3-12-2
None
None
PIMS-DOC-A3-13-1
PIMS-DOC-A3-13-2
None
PIMS-DOC-A3-14-1
PIMS-DOC-A3-15-1
PIMS-DOC-A3-16-1
PIMS-DOC-A3-17-1
Breach Notification Letter to PII Principals
EXAMPLE PII Breach Notification Form
EXAMPLE Breach Notification Letter to PII Principals
Legal, Regulatory and Contractual Requirements Procedure
Legal, Regulatory and Contractual Requirements
EXAMPLE Legal, Regulatory and Contractual Requirements
Records Retention and Protection Policy
Operational Systems Audit Plan
Information Security Summary Card
Information Security Awareness Training Presentation
PIMS-DOC-A3-18-1 Schedule of Confidentiality Agreements
PIMS-DOC-A3-18-2 Non-Disclosure Agreement
PIMS-DOC-A3-19-1 Clear Desk and Clear Screen Policy
PIMS-DOC-A3-20-1 Procedure for the Management of Removable Media
PIMS-DOC-A3-20-2 Physical Media Transfer Procedure
PIMS-DOC-A3-21-1 Procedure for the Disposal of Media
PIMS-DOC-A3-22-1 Mobile Device Policy
PIMS-DOC-A3-22-2 BYOD Policy
PIMS-DOC-A3-22-3
User Mobile Device Policy
PIMS-DOC-A3-23-1 User Password Policy
PIMS-DOC-A3-24-1 Backup Policy
PIMS-DOC-A3-25-1 Logging Policy
PIMS-DOC-A3-26-1 Cryptographic Policy
PIMS-DOC-A3-27-1
Secure Development Policy
PIMS-DOC-A3-27-2 Secure Coding Policy
PIMS-FORM-A3-28-1 Requirements Specification
PIMS-DOC-A3-29-1 Principles for Engineering Secure Systems