
Volume: 12 Issue: 02 | Feb 2025 www.irjet.net p-ISSN: 2395-0072


Volume: 12 Issue: 02 | Feb 2025 www.irjet.net p-ISSN: 2395-0072
T M Sushma, Prajwal H Rao, Vinay Kumar L, Yashwanth B R, Sanjay Kumar Reddy
Abstract The advancement of cloud computing and webbased development has driven the adoption of containerization and virtualization. These technologies offer enhanced scalability, security, and efficiency in software development. This paper explores key concepts, including containerization, virtualization, types of virtualization, container orchestration, microservices, sockets, and load balancers. The study integrates findings from existing literature and discusses practical applications in modern computing environments. Additionally, this research highlights thesignificance ofthese technologies in improving resource allocation, reducing operational overhead, and enhancing the agility of software development lifecycles. By examining the interplay between containerization and orchestration, this paper provides insights into the benefits and challenges associated with deploying cloud-native applications in dynamic and distributed environments. The advancementofcloudcomputingandwebbaseddevelopment hasdriventheadoptionofcontainerizationandvirtualization. These technologies offer enhanced scalability, security, and efficiency in software development. This paper explores key concepts, including containerization, virtualization, types of virtualization,containerorchestration,microservices,sockets, and load balancers. The study integrates findings from existing literature and discusses practical applications in moderncomputingenvironments.
Index Terms Web-Based IDE, Cloud Development, Docker Containers, Kubernetes, Monaco Editor, xterm.js, Authentication, Microservices, Secure Code Execution, RealTime Collaboration, Software Development Environments, RemoteCoding,CI/CDIntegration.
Traditional computing environments required dedicated infrastructure,leadingtohighmaintenancecosts andlimited scalability. Virtualization and containerization have revolutionized computing by allowing multiple applications toruninisolatedenvironments.Theseadvancementsprovide greaterflexibility,allowingbusinessestodynamicallyallocate computing resources based on demand. Moreover, they enable developers to create consistent environments across variousstagesofthesoftwaredevelopmentlifecycle,reducing compatibilityissuesanddeploymentfailures.
The adoption of cloud computing and distributed architectures has further accelerated the need for these technologies.
Organizations leverage virtualization to optimize data center efficiency, while containerization streamlines the developmentanddeploymentofcloud-nativeapplications.By integrating both approaches, enterprises can achieve a balance between performance,resourceutilization, and costeffectiveness.
Thispaperdelvesintothesetechnologiesandtheirrolesin modern cloud-based development environments, exploring their benefits, challenges, and use cases in various industry applications. Traditional computing environments required dedicated infrastructure, leading to high maintenance costs and limited scalability. Virtualization and containerization have revolutionized computing by allowing multiple applications to run in isolated environments. This paper delves into these technologies and their roles in modern cloud-baseddevelopmentenvironments.
• Research into cloud-native applications, virtualization, and containerization has evolved significantly, leading to numerous studies analyzing their design, scalability, and securityaspects.
• Oyeniran et al. (2024) examined microservices within cloud-native applications, emphasizing their modular structure and scalability. Their study identified key design patterns that enhance microservice efficiency, includingAPIgateways,servicediscovery,andautomated load balancing. The research highlighted the role of microservices in improving software resilience and reducingdeploymentcomplexity.
• Watadaetal.(2019)providedacomprehensivereviewof containerization, discussing its technological advancements and existing security concerns. Their research detailedtheshiftfrom monolithic architectures to containerized applications, focusing on container security challenges such as runtime vulnerabilities and isolationmechanisms.Thestudyproposedbestpractices International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 02 | Feb 2025 www.irjet.net p-ISSN: 2395-0072
for mitigating security risks, including container image verificationandruntimemonitoring.
• Wessels et al. (2011) explored the use of WebSockets in remote data visualization, demonstrating their significance in real-time communication. Their study emphasized the advantages of WebSockets in interactive applications, particularly in cloud-based integrated developmentenvironments(IDEs).Thisresearchlaidthe groundwork for incorporating WebSockets into microservices architectures requiring real-time data exchange.
• Naeem et al. (2016) presented an overview of virtualization technologies, categorizing them into hardware, OS, and network virtualization. Their study compared traditional hypervisors like VMware with modern lightweight containers, illustrating the benefits of containerized environments in optimizing resource utilization and improving deployment speeds. The research also discussed the growing trend of serverless computingasanalternativetofull-scalevirtualization.
• Zhang (1998) introduced the Linux Virtual Server as an earlysolutionforscalablenetworkservices.Hisresearch explored load balancing techniques, demonstrating their effectiveness in distributing workloads across microservices. The study remains relevant in modern cloud infrastructures, where distributed load balancing plays a crucial role in optimizing application performanceandensuringhighavailability.
• The findings from these studies contribute to a deeper understanding of cloud-native technologies and their implications for scalable computing. The literature highlights best practices in microservices adoption, container security, virtualization strategies, and load balancing techniques, which continue to shape the developmentofmoderncomputingenvironments.
• The evolution of cloud-native applications has driven extensive research into microservices, containerization, and virtualization. Several studies have explored the design patterns, scalability, and security of these technologies.
• Oyeniranetal.(2024)analyzedtheroleofmicroservices in cloud-native applications, highlighting their modular nature and improved scalability. The study emphasized how breaking applications into smaller services enhances maintainability and fault isolation. Their work also discussed various design patterns that optimize microservices for performance, including API gateways, servicediscovery,andloadbalancingtechniques.
• Watada et al. (2019) provided an extensive review of containerizationtrends,techniques,andopenchallenges. Their research examined the evolution of container technologies, from early Linux container implementations to modern orchestration tools such as Kubernetes. The paper underscored the security concerns associated with containerized environments, including runtime vulnerabilities and container escape attacks,andproposedmitigationstrategies.
• Wessels et al. (2011) focused on WebSockets and their impact on remote data visualization. The study demonstrated how WebSockets facilitate real-time communication between distributed applications, making them ideal for cloud-based integrated development environments. Their work laid the foundation for using WebSockets in scalable microservices architectures that require lowlatency data exchanges.
• Naeem et al. (2016) presented an overview of virtualization and cloud computing, detailing various virtualization techniques such as hardware, OS, and network virtualization. The study examined how hypervisors like VMware and Hyper-V enable the efficient use of computing resources while maintaining strong isolation between virtual machines. Their work also explored the shift toward lightweight virtualization with container technologies, which offer faster deploymenttimesandloweroverhead.
• Zhang (1998) introduced the Linux Virtual Server as an earlysolutionforscalablenetworkservices.Hisresearch demonstrated how load balancing techniques improve the performance and availability of distributed applications. The study remains relevant today, as modern cloud platforms continue to leverage advanced load balancing methods to distribute workloads efficientlyacrossmicroservices.
• These studies collectively provide a comprehensive understanding of modern computing technologies. The insights gained from this literature survey inform best practices in designing scalable, secure, and efficient cloudnativearchitectures.
• Traditional computing environments required dedicated infrastructure, leading to high maintenance costs and limited scalability. Virtualization and containerization have revolutionized computing by allowing multiple applications to run in isolated environments. These advancements provide greater flexibility, allowing businesses to dynamically allocate computing resources based on demand. Moreover, they enable developers to

Volume: 12 Issue: 02 | Feb 2025 www.irjet.net p-ISSN: 2395-0072
create consistent environments across various stages of the software development lifecycle, reducing compatibilityissuesanddeploymentfailures.
• The adoption of cloud computing and distributed architectures has further accelerated the need for these technologies. Organizations leverage virtualization to optimize data center efficiency, while containerization streamlines the development and deployment of cloudnative applications. By integrating both approaches, enterprisescan achieve a balancebetween performance, resourceutilization,andcost-effectiveness.
Containerization involves packaging applications and their dependencies into lightweight, portable containers. Unlike virtual machines, containers share the host OS kernel, reducing resource overhead. Technologies such as Docker have popularized containerization by providing secure and consistent environments for code execution. Containerized development ensures security, scalability, and dependency management. The implementation of Kubernetes further enhances containerized workloads by enabling dynamic resourceallocation.
One of the significant advantages of containerization is its role in DevOps and continuous integration/continuous deployment (CI/CD) pipelines. By using containers, developers can create reproducible environments that eliminate inconsistencies between development, testing, and production stages. Additionally, containers facilitate microservicesarchitecture, whereapplicationsarecomposed of loosely coupled services that can be deployed and scaled independently. This approach improves fault tolerance, enhances application agility, and optimizes resource utilization.
Security is a crucial aspect of containerization. Best practices include using minimal base images, implementing proper access control mechanisms, and continuously scanning container images for vulnerabilities. Tools like Docker Security Scanning and Kubernetes Network Policies help ensure secure containerized deployments. Containerization involves packaging applications and their dependencies into lightweight, portable containers. Unlike virtual machines, containers share the host OS kernel, reducing resource overhead. Technologies such as Docker have popularized containerization by providing secure and consistent environments for code execution. Containerized development ensures security, scalability, and dependency management. The implementation of Kubernetes further enhances containerized workloads by enabling dynamic resourceallocation.
Container orchestration automates the deployment, scaling, and management of containerized applications. Kubernetes is a leading orchestration tool, ensuring efficient resource utilization and high availability. Orchestration platforms handle container networking, load balancing, and fault tolerance, making them essential for large-scale applications.
Orchestration systems provide declarative configuration management,enablingdeveloperstodefineapplicationstates using YAML or JSON files. Kubernetes’ core components include the API server, etcd for state management, controllers,andschedulers.Thesecomponentsworktogether to automate container lifecycle management, ensuring resilienceandselfhealingcapabilitiesindistributedsystems.
Container orchestration also supports service discovery andloadbalancing.Kubernetesusesabuilt-inDNSserviceto facilitate inter-container communication, ensuring that microservices can dynamically find and interact with each other. Load balancers distribute traffic efficiently across container instances, improving application responsiveness andpreventingbottlenecks.
Security features within orchestration frameworks include role-basedaccesscontrol(RBAC),networksegmentation,and automated secrets management. These capabilities help maintain the integrity of containerized applications in multitenant cloud environments. Container orchestration automates the deployment, scaling, and management of containerized applications. Kubernetes is a leading orchestration tool, ensuring efficient resource utilization and high availability. Orchestration platforms handle container networking,loadbalancing,andfaulttolerance,making them essentialforlarge-scaleapplications.
Socketsenableinter-processcommunication(IPC)between applications. They facilitate data exchange over networks, playing a crucial role in client-server architectures. WebSockets, for instance, provide real-time bidirectional communication, making them ideal for web-based applicationssuchaschatapplicationsandcollaborativeIDEs.
Traditional socket communication follows the TCP/IP model, where applications establish connections using sockets bound to specific IP addresses and ports. There are different types of sockets, including stream sockets (TCP), datagram sockets (UDP), and raw sockets. Each type serves distinctusecases, rangingfromreliable data transfer tolowlatencycommunicationindistributedsystems.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 02 | Feb 2025 www.irjet.net p-ISSN: 2395-0072
In modern web applications, WebSockets allow persistent connections between clients and servers, reducing the need for repetitive HTTP requests. This is particularly useful for real-time applications such as online gaming, live stock market updates, and collaborative document editing. WebSockets operate over the WebSocket protocol, which provides lowlatency communication by maintaining a single connectionforongoingdataexchange.
Security considerations for socket communication include encrypting data with TLS, implementing authentication mechanisms,andusingfirewallrulestopreventunauthorized access.Propersocketmanagementensuresefficientresource usage and protects applications from potential denial-ofservice (DoS) attacks. Sockets enable inter-process communication (IPC) between applications. They facilitate data exchange over networks, playing a crucial role in clientserver architectures. WebSockets, for instance, provide realtime bidirectional communication, making them ideal for web-based applications such as chat applications and collaborativeIDEs.
Virtualization enables the creation of multiple virtual instances of hardware or software on a single physical machine. This abstraction allows organizations to optimize resource utilization and improve scalability. Virtualization techniques include hardware, OS, network, and storage virtualization. The primary benefit is the ability to run different operating systems and applications on a single hardware infrastructure, reducing costs and increasing efficiency.
1) Types of Virtualization:
• Hardware Virtualization: Uses a hypervisor to create multiple virtual machines (VMs) on a single physical system.ExamplesincludeVMwareandHyper-V.
• OS Virtualization: Runs multiple isolated user-space instances on a single operating system kernel. Docker andLXCareexamplesofOS-levelvirtualization.
• Network Virtualization: Abstracts networking resources to create virtual network environments, improving networksecurityandefficiency
• Storage Virtualization: Pools storage resources to create a unified storage system, optimizing storage managementandaccess.
E. Cloud Provider and Its Use Case in the Project
Cloud providers offer a range of services that enhance the deployment, scalability, and security of cloud-native applications. Among them, Amazon Web Services (AWS) provides essential tools that integrate seamlessly with containerizationandorchestrationframeworks.
1) Amazon Web Services (AWS): AWS offers services like Amazon Elastic Kubernetes Service (EKS) and AWS Fargate, which facilitate automated container deployment and management. AWS Lambda enables serverless execution, minimizing infrastructure overhead while improving cost efficiency. In this project, AWS services can be leveraged to deployKubernetesclusters,manageauthenticationwithAWS Cognito, and implement load balancing using AWS Elastic LoadBalancer(ELB).UseCasesintheProject
• Scalability: AWS EKS ensures seamless scaling of containerizedapplicationsbasedontrafficdemand.
• Security: AWS Identity and Access Management (IAM) and AWS Cognito provide secure authentication and accesscontrol.
• CostEfficiency:ServerlessofferingssuchasAWSLambda reduce operational costs by dynamically allocating resourcesasrequired.
• Data Persistence: AWS S3 ensures reliable and scalable storageforpersistentapplicationdata.
• Continuous Deployment: AWS CodePipeline enables automated CI/CD processes, streamlining deployment workflows.
By integrating AWS services into the project, developers can build a resilient, scalable, and cost-effective cloud-native application that leverages containerization and orchestration technologies efficiently. Cloud providers offer a range of services that enhance the deployment, scalability, and security of cloud-native applications. Major cloud providers include Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP), each offering tools that integrate seamlessly with containerization and orchestration frameworks.
Traditional Web applications lack direct access to a system’sterminal.Technologiessuchas:
• xterm.js: A browser-based terminal emulator enabling interactiveshellaccess.

• MonacoEditor:Alightweight,feature-richeditorusedin VSCodeandvariousweb-basedIDEs.
These tools enable web-based IDEs to offer near-native developmentexperiences.
A. Architecture Overview
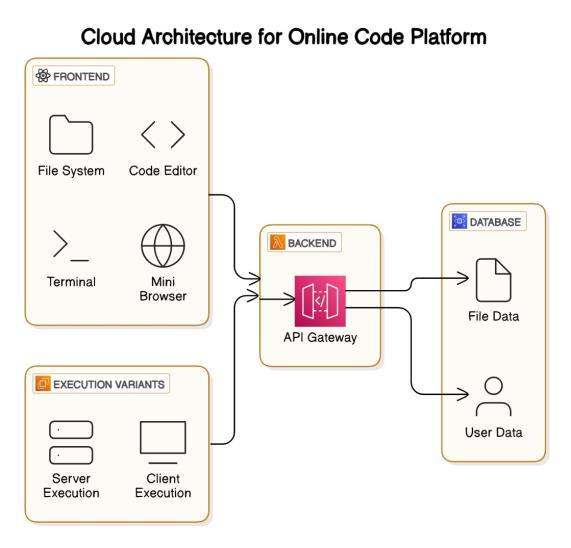
Fig.1.Systemdiagram
The system follows a microservices-based architecture withthefollowingcomponents:
• Frontend(React+TailwindCSS):Providesauserfriendly interfacewithMonaco-basedcodeediting.
• Backend (Node.js + Express + WebSockets): Manages authentication, session handling, and real-time interactions.
• Execution Environment (Docker + Kubernetes): Runs usercodesecurelyinisolatedcontainers.
• File System (Persistent Storage): Ensures code persistencebetweensessions.
• Authentication (JWT + OAuth): Implements secure user authenticationmechanisms.
B. Execution Workflow
1) Ensuring a seamless execution workflow is critical in cloud-native environments. The system follows a structuredapproachtohandleuserauthentication,code execution,andterminalinteractionefficiently.
2) User Authentication: The user logs in via OAuth, providing secure access control and identity verification. OAuth facilitates multi-user authentication, ensuring that only authorized users can interact with thesystem.
3) Container Allocation: Upon successful login, a unique container is allocated to each user using Kubernetes. This guarantees an isolated environment for code execution,enhancingsecurityandresourceefficiency.
4) CodeEditing:TheMonacoeditorprovidesaninteractive interfaceforuserstowrite andeditcode.Withfeatures likesyntaxhighlightingandreal-timeerrordetection,it enhancesthedevelopmentexperience.
5) Terminal Interaction: The xterm.js terminal enables realtime interaction with the containerized execution environment. Users can run commands, debug programs, and receive immediate output within the browser-basedterminal.
6) Code Compilation and Execution: The system compiles and executes the code within the allocated container, ensuring consistent execution environments across different users. The use of containers prevents dependency conflicts and enhances application portability.
This execution workflow optimizes user experience, ensures high availability, and maintains security in a multiuserdevelopmentenvironment.
A. Performance Evaluation
The web-based IDE was tested under different workloads to evaluate latency, container allocation time, and resource consumption.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 02 | Feb 2025 www.irjet.net p-ISSN: 2395-0072
Deleteafolderwitha fileinit Thefileisdeleted Withfolder
Createa fileusing shell Anewfileiscreated
Deletea fileusing terminal Thefileisdeleted
Click on a particular file The contents of that file are shown in the editor
Editthecontents ofthefile The content is updatedandsaved
B. Security Analysis
The system underwent security testing for vulnerabilities suchas:
• Container Breakout Prevention: Implemented sandboxing techniques to prevent users from accessing unauthorizedresources.
• Authentication Robustness: Enforced OAuth-based authentication with JWT tokens to ensure secure user sessions.
The increasing demand for collaborative and cloud-based development has led to the rise of web-based Integrated Development Environments (IDEs). These platforms offer developers a seamless coding experience without requiring extensive local setups. This paper presents the design and implementation of a scalable web-based IDE that integrates features such as authentication, real-time code execution usingDockercontainers,abrowser-basedterminal(xterm.js), andaMonaco-basedcodeeditor.Thesystemensuressecurity through containerization and supports multi-user collaboration via Kubernetes orchestration. The study also explores challenges in performance, security, and usability whilediscussingpotentialfutureimprovements.
A. Applications
Web-basedIDEsarebeneficialfor:
• Remote Development: Enables coding from any device withoutlocalsetup.
• EducationandTraining:Facilitatesprogrammingcourses withoutrequiringsoftwareinstallation.
• Enterprise Development: Streamlines development workflowsbyintegratingwithCI/CDpipelines.
B. Future Enhancements
• AI-Assisted Code Completion: Integrate AI-powered suggestionsforimprovedproductivity.
• Support for Additional Languages: Expand support for compiledlanguagessuchasC++andRust.
• DistributedExecution:Implementserverlessexecutionto optimizeresourceutilization.
• Enhanced Collaboration Features: Introduce real-time codesharinganddebuggingtools.
Virtualization and containerization have transformed modern computing, offering efficient resource management and scalability. Container orchestration further simplifies deploymentandmanagementofapplications.Theintegration of microservices, sockets, and load balancers enhances system reliability and performance. Future research should focus on optimizing these technologies for AI-driven applicationsandedgecomputingenvironments.
The adoption of cloud-native technologies has not only streamlinedsoftwaredevelopmentbutalsorevolutionizedIT infrastructuremanagement.Theabilitytodeployandmanage applications at scale using containerization has reduced operational complexities and costs while improving system resilience. Additionally, automation through orchestration tools like Kubernetes ensures better fault tolerance, selfhealingcapabilities,andefficientresourceutilization.
Security remains a critical concern in containerized environments. Future advancements should address enhanced security measures, including zero-trust architectures, automated vulnerability scanning, and encryptedservicecommunication.
Incorporating AI-driven monitoring tools could further optimizeresourceallocationandthreatdetection.
Moreover, emerging trends such as serverless computing and hybrid cloud environments present new opportunities for optimizing cloud-native applications. Serverless solutions minimizeinfrastructuremanagement,allowingdevelopersto focussolelyonapplicationlogic,whilehybridcloudstrategies

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 02 | Feb 2025 www.irjet.net p-ISSN: 2395-0072
provide flexibility by balancing on-premises and cloud deployments.
In conclusion, virtualization, containerization, and orchestration will continue to shape the future of cloud computing. Continuous improvements in security, automation, and performance will further enhance the efficiency of cloud-native environments, making them indispensable for modern software development and enterprisesolutions.
Virtualization and containerization have transformed modern computing, offering efficient resource management and scalability. Container orchestration further simplifies deploymentandmanagementofapplications.Theintegration of microservices, sockets, and load balancers enhances system reliability and performance. Future research should focus on optimizing these technologies for AI-driven applicationsandedgecomputingenvironments.
The author expresses gratitude to Acharya Institute of Technology for providing resources and support in developingthisproject.Specialthankstofacultymembersfor theirvaluableguidancethroughouttheresearch.
[1] O.C.Oyeniran,A.O.Adewusi,A.G.Adeleke,L.A.Akwawa, and C. F. Azubuko, ”Microservices architecture in cloudnativeapplications:
Designpatternsandscalability,”ComputerScienceandIT Research Journal, vol. 5, no. 9, pp. 2107–2124, Sep. 2024.4
[2] J. Watada, A. Roy, R. Kadikar, H. Pham, and B. Xu, ”Emerging Trends, Techniques and Open Issues of Containerization:AReview,” IEEE Access, vol. 7, pp. 152443–152451, Oct. 2019, doi: 10.1109/ACCESS.2019.2945930
[3] ]A. Wessels, M. Purvis, J. Jackson, and S. S. M. Rahman, ”Remote Data Visualization through WebSockets,” in Proceedings of the 2011 Eighth International Conference on Information Technology: New Generations, Las Vegas, NV, USA, 2011, pp. 1050-1051, doi: 10.1109/ITNG.2011.182
[4] M. M. Naeem, H. Mahar, F. Memon, M. Siddique, and A. Rauf, ”An Overview of Virtualization and Cloud Computing,” Scientific International (Lahore), vol. 28, no. 4,pp.3799–3803,Jul.–Aug.2016
[5] W. Zhang, ”Linux Virtual Server for Scalable Network Services,” National Laboratory for Parallel and DistributedProcessing,Changsha,Hunan,China,1998