
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 02 | Feb 2025 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 02 | Feb 2025 www.irjet.net p-ISSN: 2395-0072
Pritish Dinesh Sathe1 , Pratik Prakash Mohod2
1Computer Engineer, Amravati
2Mechanical Engineer, Amravati ***
Abstract - TheControllerAreaNetwork(CAN)protocol, that allows seamless communication between electronic controlunits(ECUs),hasemergedasthecoreofin-vehicle communication. Modern cars, however, are now in considerable cybersecurity threat due to their original design,whichprioritizedefficiencyanddependabilityover security.Thisworkinvestigatestheintrinsicproblemsinthe CANprotocol,suchasitslackofauthentication,encryption, andvulnerabilitytomessageinjectionattacks.Furthermore, todemonstratethatreal-worldattacksarefeasible,wegive experimental validation via CAN bus simulations with programs such as Vector CANoe and Python's Scapy. This study proposes a multi-layered method that combines cryptographic approaches, IDS, and AI-based security modelstoimprovethesecuritysystemmodel.
Keywords: Automotive security, CAN protocol, Cybersecurity, Intrusion Detection System
With the development of connected and autonomous vehicles, the automobile industry has seen significant transformationinrecentyears.TheControllerAreaNetwork (CAN) Protocol, an effective and reliable communication technologythatlinksseveralECUsinacar,isattheheartof thischange.BOSCHcreatedtheCANprotocolinthe1980s, long before cyber risks became a major concern. The securityconstraintsofCANhavebecomeamajorconcernas vehiclesbecomemorenetworked[1].
Withincreasedsoftwareandconnectivityandtechnological advancement,thegapsinCANprotocolhavestartedtopose moreandmoresecuritythreats.Forexample:
Attackerscanexploittheinsecuresensitivedataas thereisnoencryption.
The absence of authentication does allow the attackertoinjectmaliciousmessagesthroughthe maliciouscode.Potentiallydisturbingtheimportant functionalities of the vehicle such as steering, braking,infotainmentsystemetc.
Reply attack can disturb the functioning of operations.
Inthiswork,wehaveevaluatedtheCANprotocol'ssecurity flaws and investigated how they affect vehicle safety. Additionally,wehavesuggestedafewtacticstoreducethe dangers. Additionally, we have used simulation tools like CANoe and Python Scapy to validate some of the assault models.Thepaper'sconclusionsemphasizethenecessityof improvingsecurityinthecurrentvehiclesystems.
Previous studies on this topic have uncovered and highlighted number of vulnerabilities in the CAN protocol whichincludesitsvulnerabilitytolackofencryption[2],lack ofauthenticationmeasures[3]andmessageinjectionattacks [4]. Although earlier studies have suggested solutions including cryptography algorithms [5] and intrusion detectionsystems[6],majorityofthesestrategiesfocuseson thediscreteproblemsratherthananintegratedframework. By combining existing vulnerabilities and putting forth a thorough,multi-layeredsecurityapproach,thispaperadds much needed value by filling up the remaining gaps. To improvetherobustnessofCANnetworks,wealsointegrate advancetechnologieslikehardware-basedsecuritysolutions andAI-basedanomalydetection.
The Control Area Network protocol is a message-based communicationsystem,whichallowsmultipleECUnodesto send and receive data without any central controller. The architectureofthisprotocolincludes:
Nodes:Thedevices(ECUs)connectedinanetwork.
CAN Bus: Physical communication medium to ensuretransmissionofmessageswhichisusually twistedpaircable.
Terminatingresistors:Topreventsignalreflections attheendoftheCANbus.
Messagearbitration:A methodthatusesmessage identifierstoprioritizehighprioritymessageswhen multiplenodestrytotransmitatthesametime

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 02 | Feb 2025 www.irjet.net p-ISSN: 2395-0072
Data Transmission: All nodes of the network can transmitandreceivethedata,butnotatthesame time.
DataCollisiondetectiontechnique:Thetransmitting node can stop if it detects another node trying to transmitatthesametime
The protocol consists of four data frames namely remote,data,error,andoverload.
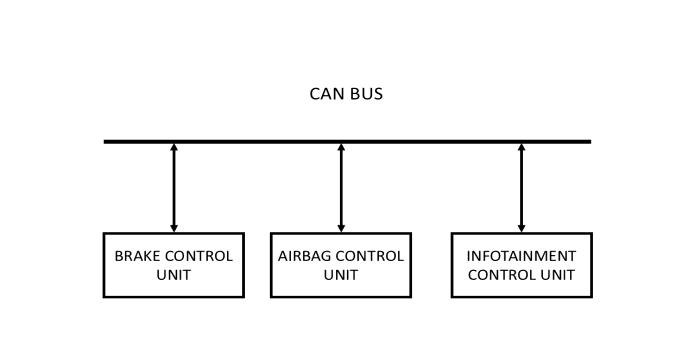
Figure -1:ACANBusconnectingvariousECUs(E.g.,Brake ControlUnit,AirbagControlUnit,InfotainmentControl Unit)
TheCANprotocolworksoverthephysicalanddatalinklayer oftheOSImodel.
The CAN protocol is used in various range of applications fromcontrollingthesafetysystemslikeAirbagcontrol,brake control.Itisalsoinvolvedinfeatureslikeinfotainmentand climate control for e.g. Despite all these features, the protocol lacks in the security feature which makes it easy targetforthevariouscyberattacks.
4. SECURITY VULNERABILITIES IN CAN PROTOCOL
4.1. LACK OF ENCRYPTION
OneofthebiggestissuesinCANprotocolisthatthemessage sent over the CAN bus is always in plaintext and not encrypted.ThatmeansanyonewhohasanaccesstotheCAN bus can read the sensitive data in the message such as brakingcommandoreventheenginestatus.Thatmakesit very vulnerable to cyberattacks. Even if an attacker eavesdroppingonsomeone’scar’sinternalcommunications, hewillhaveanideaaboutthestatusofthevehicle.[7]
Another major issue with the CAN network is lack of authenticationofthemessages.SinceCANdoesnotverifies
whoissendingthemessagethatmeansahackercansend fakecommandsintothenetworkandcancauseproblemfor thevehiclesystem.Fore.g.,Anattackercouldsendasignal todisablethebrakes,ortheycouldlockthesteeringwheel, puttingthedriver’slifeintorisk.[8]
TotestthevulnerabilitiesoftheCANnetwork wesetupa simulationenvironmentusingVectorCANoeandScapy.And theresultsthatwefoundareasfollow:
1. Injected messages were accepted by the ECUs withoutanyresistance.
2. Repeated injections found noticeable disruptions, likeerraticbraking
3. Duetothelackofauthentication,spoofingmessages wasveryeasy.
EXPERIMENTAL
VectorCANoe:Asimulationtoolusedfortestingand analysingCANnetwork.Usedtosimulaterealworld likescenariofore.g.,injectingmaliciousmessages intotheCANbus
Python’sScapy:APythonlibraryfordevelopingand sending customCAN frames.Inthis project,some messages were written with specific IDs and payloads.
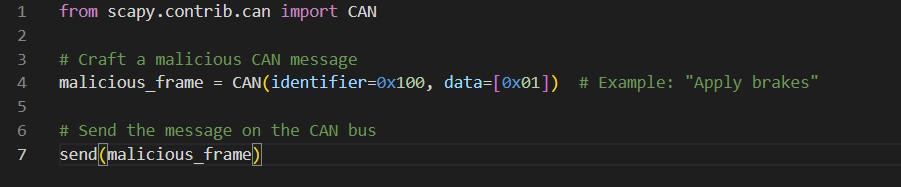
SIMULATION ENVIRONMENT:
Hardware:
1) CAN bus simulator connected to an OBD-II emulator.
2) ECUs simulated using virtual nodes in Vector CANoe.
Software:
1) Vector CANoe configured with a virtual CAN network.
2) Python script executed in parallel to inject maliciousmessagesontheCANbus.
Performance Metrics:
Detection Accuracy: With98%accuracyforAI based IDS trained on normal as well as malicioustrafficpatterns.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 02 | Feb 2025 www.irjet.net p-ISSN: 2395-0072
False Positive Rate: 2% of occasional misclassification of legitimate messages as malicious.
Training Dataset:
Normal Traffic: 10,000 messages captured fromastandardCANbus.
Malicious Traffic: 5,000 injected messages simulating attacks. e.g., message injection, replayattacks.
Algorithm Used:
Supervised Learning Algorithm: Random ForestClassifier.
Features Extracted: MessageID,Payload,Frequency, Timestamp
5.2. VISUALISATION:
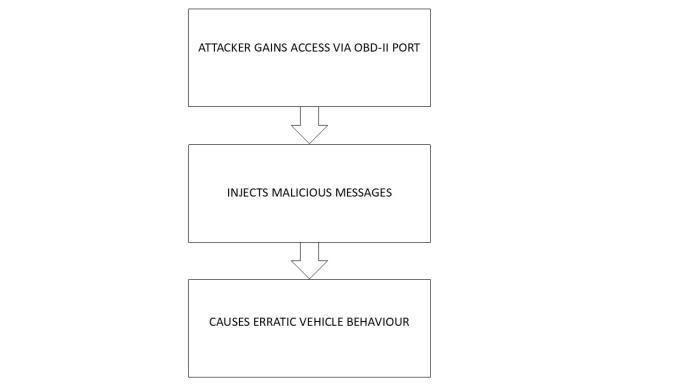
Figure -2: Flowchartofattack
Step 1: AttackerconnectstotheCANbusviatheOBD-IIport orremotelythroughacompromisedsystem.
Step 2: Attacker sends the malicious message on the bus. (e.g., Apply brakes, disable brakes, display wrong indications)
Step 3: Vehiclestartsbehavingerraticcausingdiscomfortto thedriver.
ATTACK MODEL SIMULATION:
We tested 2 types of attack scenario to evaluate vulnerabilitiesofCANprotocol.
1. Message Injection Attack: Injected malicious message with ID 0x100 and payload 0x01 (to be interpreted as “Apply Brakes”) the impact of this was brake pressure increased abruptly within <5 seconds andsteeringwheellockedintermediately due to conflicting commands. Time taken for the injectedmessagetospreadacrosstheCANbuswas
<1 ms andnoerrorsweredetectedduringinjection duetolackofauthenticationmechanism.
2. Replay Attack: Capturedalegitimatemessagewith an ID 0x200 and payload 0xFF (interpreted as “increasethrottle”)andreplayeditrepeatedly.The impact of this attack was the vehicle experienced unintendedaccelerationwithin <3 seconds witha spiked engine RPM causing an erratic behavior. Successrateofthisexperimentwas95%.
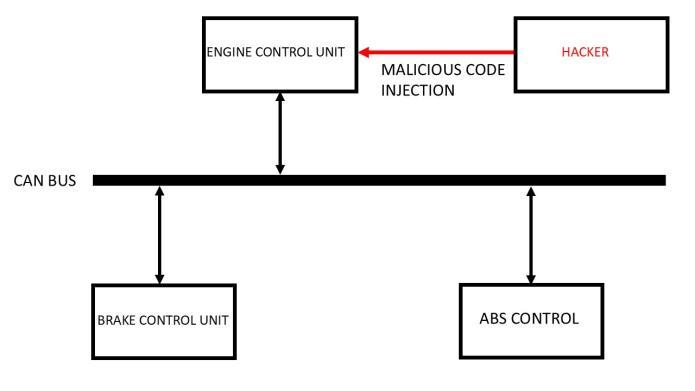
Figure -3:Attackersendingmaliciouscodetohackthe CANbus
Thetablebelowcontainsexperimentalresults.
Table -1: Attack Model Simulation
ATTACKTYPE EFFECT TIMETOIMPACT
MessageInjection ErraticBrakingand Steering
ReplayAttack Unintended Acceleration
<5Seconds
<3Seconds
Injectedmessagesacceptedwithoutanyresistance Allthemessageswereconsideredaslegitimateby the ECUs due to the lack of authentication mechanism.Fore.g.,MessagewithanID0x100and payload 0x01 caused increased abrupt brake pressure.
Repeatedinjectionscausednoticeabledisruptions. Erratic braking and steering observed within less than5secondsofrepeatedinjections.Sendingthe samebrakecommandfivetimesinquicksuccession caused the brake padel to engage/disengage unpredictably.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 02 | Feb 2025 www.irjet.net p-ISSN: 2395-0072
6.1.
With this paper, we suggest integration of cryptographic techniqueslikemessageauthenticationcodes(MACs)and digital signatures to secure the CAN network. The comparisonforsomepopulartechniquesisgivenbelow:
Table 2: Comparison of Cryptographic Techniques
TECHNIQUE LATENCY SECURITYLEVEL
AES-128Encryption 0.5 High
MAC with HMACSHA256 0.3 Medium
DigitalSignature 1.2 VeryHigh
1. AES-128 Encryption: Itisasymmetricencryption techniquewithasecretsharedkey.Itissuitablefor thereal-timeapplicationsduetoitslowlatency.
2. MAC with HMAC-SHA256: This adds the cryptographic checksum to the messages for integrityverification.Itisconsideredaslesssecure thantheDigitalSignatures.
3. Digital Signatures: Digital Signatures provide strong authentication and non-repudiation. Also, requireshighercomputationalresourcesmakingit lesssuitableforthesystemswhicharetime-critical.
WehavealsotestedtheAI-basedIDStodetectanomaliesin CANTraffic.WiththehelpofSupervisedlearningalgorithm, we trained the system on normal and malicious traffic patterns. With 98% detection, results were accurate and impressive.
Forsafeguardinginfuture,werecommendupgradingtothe CANFDprotocol.Whichsupportshighpayloadsandstricter error-handling mechanism. Additionally, CAN FD with Ethernet-based protocolscan further enhancethesecurity system.
7.1 Case Study 1: Jeep Cherokee Hack (2015)
In year 2015, researchers demonstrated on how they can hackintoaJeepCherokeethroughitsinfotainmentsystem. Theytookcontrolofthebrakesandsteeringofthevehicle, provingthathowdangerousCANvulnerabilitiescanbe.[10]
In year 2016, Hackers exploited flaw in the Tesla vehicle throughitsCANnetworktounlockthedoorsandstartthe engine.Teslarespondedquicklytothisthreatbydeveloping overtheyearsecuritypatches.Still,theincidenthighlighted theneedforstrongersafeguards.[11]
Withthis,wecansafelyconcludethattheCANprotocolstilla cornerstoneoftheautomotivecommunicationbutitneeds bettersafetymeasurestokeepupwiththemodernthreats andsafeguardthevehicleaswellasthedriver.Byusingthe Cryptographic protections, AI based solutions, Intrusion DetectionSystemswecansignificantlyimprovethesafetyof CANnetwork.Movingforwardresearcherscanexplorethe hardware-level security implementations and AI driven anomalydetectiontostayaheadofthecyberthreats.
[1] Bosch. (2023). CAN Specification. Retrieved from https://www.bosch.com
[2] ISO 11898. (2023). Road Vehicles – Controller Area Network (CAN). International Organization for Standardization
[3] Checkoway, S., et al. (2011). Comprehensive ExperimentalAnalysesofAutomotiveAttackSurfaces. USENIXSecuritySymposium.
[4] Koscher,K.,etal.(2010).ExperimentalSecurityAnalysis ofaModernAutomobile.IEEESymposiumonSecurity andPrivacy
[5] Miller,C.,&Valasek,C.(2015).RemoteExploitationof anUnalteredPassengerVehicle.BlackHatUSA
[6] Groza, B., Murvay, P., Van Herrewege, A., & Verbauwhede, I. (2012). LiBrA-CAN: A Lightweight BroadcastAuthenticationProtocolforControllerArea Networks.InternationalConferenceonCryptologyand NetworkSecurity.
[7] ISO/SAE21434.(2021).RoadVehicles–Cybersecurity Engineering. International Organization for Standardization.
[8] Greenberg,A.(2015).HackersRemotelyKillaJeepon theHighway–WithMeinIt.Wired.
[9] Petit,J.,&Shladover,S.E.(2015).PotentialCyberattacks onAutomatedVehicles.IEEETransactionsonIntelligent TransportationSystems.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
[10] Hoppe, T., Kiltz, S., & Dittmann, J. (2011). Security Threats to Automotive CAN Networks – Practical Examples and Selected Short-Term Countermeasures. ReliabilityEngineering&SystemSafety.
[11] Greenberg,A.(2016).Tesla’sCarsNowHaveSelfDrivingHardware.Wired. BIOGRAPHIES


Mr.PritishDineshSathe Computer Science graduate and working in the Automotive Softwaredomain
Volume: 12 Issue: 02 | Feb 2025 www.irjet.net p-ISSN: 2395-0072 © 2025, IRJET | Impact Factor value: 8.315 | ISO 9001:2008
Mr.PratikPrakashMohod Mechanical Engineerwitha focus onAutomotiveIndustry