
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 01 | Jan 2025 www.irjet.net p-ISSN: 2395-0072
AI-POWERED HUMAN SUSPICIOUS AND ANOMALOUS ACTIVITY
MONITORING SYSTEM
Prof. Mithuna H R1, Srinidhi Rao2, Shilpa M S3, Sindhu B Hulagur4, Maithri K5
1 Assistant Professor, ISE, Acharya Institute Of Technology, Karnataka, India
2 B.E Student, ISE, Acharya Institute Of Technology, Karnataka, India
3 B.E Student, ISE, Acharya Institute Of Technology, Karnataka, India
4 B.E Student, ISE, Acharya Institute Of Technology, Karnataka, India
5 B.E Student, ISE, Acharya Institute Of Technology, Karnataka, India
Abstract - In response to heightened global security challenges, this study introduces an intelligent surveillance framework designed to autonomously detect suspicious and anomalous human behaviors in real-world settings. The proposed Human Suspicious and Anomalous Activity Monitoring System (HSAAMS) integrates cutting-edge artificial intelligence methodologies, combining computer vision withhybrid machinelearningarchitecturestoaddress limitations in conventional surveillance systems, such as delayed response times and high false-alarm rates. This research contributes a scalable, context-aware solution for proactive security management, demonstrating viability in smart cities and critical infrastructure while balancing civil liberties. Real-world deployments validate scalability, with dynamicrecalibrationenhancingperformanceincrowdedor low-visibility settings. The system’s interpretability achieved via attention heatmaps and counterfactual explanations supportstransparentdecision-makingforsecurityoperators. By harmonizing AI-driven analytics with privacy safeguards, this work addresses critical gaps in modern surveillance systems.
Key Words: Human Suspicious and Anomalous Activity Monitoring System(HSAAMS),Convolutional Neural Networks(CNNs),Suspicious Human Behaviors,Proactive Security Management, High False Alarm Rates.
1.INTRODUCTION
Inourrapidlyevolvingworld,securityconcernshavebecome a significant part of everyday life. Traditional surveillance methods often struggle to keep up with the increasing demandforreal-timeanalysisandproactivethreatdetection. This is where artificial intelligence steps in, offering unparalleledcapabilitiestoenhancesecuritymeasures.This paper introduces an AI-powered Human Suspicious and Anomalous ActivityMonitoringSystem,designedtodetect and analyze unusual behaviors in real-time. Leveraging advancedmachinelearningalgorithmsandcomputervision techniques,thesystemaimstoidentifysuspiciousactivities with high precision. The architecture includes data acquisition,pre-processing,featureextraction,andanomaly detectionmodules,allworkingtogetherseamlessly.Through extensive experimentation, the system has proven to be
highlyaccurateandreliable,offeringascalablesolutionfor enhancingpublicsafety.
2. LITERATURE REVIEW
Recent years have witnessed remarkable progress in AIdriven surveillance technologies, spurred by growing demands for improved security across diverse sectors. Conventional approaches like CCTV cameras and human monitoring frequently lack the capability for real-time insights or preemptive responses. This gap has fueled the creation of advanced AI systems that employ machine learning and computer vision to detect and analyze suspiciousactivitiesautonomously.Researchhasextensively investigatedtheapplicationofdeeplearningarchitectures, suchasCNNsforspatial patternrecognitionandRNNsfor temporalanalysis,inidentifyingbehavioralanomalies.For example, Tripathi et al. (2018) demonstrated how these models effectively flag unusual actions in academic environments, such as unauthorized movements during exams.Alsabhan(2023)furtherexploredmachinelearning combined with LSTM networks to detect academic dishonestyinuniversities,analyzingpatternslikeirregular eye movements or atypical device usage. Unsupervised techniques, including auto encoders and GANs, have also enhanced anomaly detection by learning normal behavior patterns, thereby reducing false alarms in systems like automated exam proctoring tools. Masud et al. (2022) illustrated this with an AI-powered proctoring tool that identifies suspicious actions during online tests, such as unauthorized resource access. However, the rise of AI surveillanceraisessignificantethicalandprivacychallenges. Experts stress the need for safeguards like strict data anonymization,algorithmictransparency,anduserconsent protocolstopreventmisuseandprotectindividualrights.In conclusion, while AI surveillance systems show immense potentialinboostingsecuritythroughintelligentmonitoring, their adoption must balance innovation with ethical frameworkstoaddresssocietalconcerns.
3. RELATED WORKS
Recent advancements in video analytics have enabled researcherstodetectanomalousactivitiesacrossdomains

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 01 | Jan 2025 www.irjet.net p-ISSN: 2395-0072
suchashealthcare,trafficmanagement,andsecurity.Akey focus lies in feature extraction and classifying events as normal or abnormal. For instance, Shubham Shinde and colleagues[1]designedahumanactivityrecognitionsystem using YOLO (You Only Look Once), an object detection framework. Their work analyzed the LIRIS dataset, which includes videos of actions like group discussions, entering/exiting rooms, phone calls, and handshakes. By tracking activity labels and confidence scores across fiveframeintervals,theirmodelpredictedindividualbehaviors. Notably, they suggested that even a single frame could suffice for accurate predictions, achieving 88.35% classificationaccuracywithYOLO.Inanotherapproach,Leo and Liu combined sparse coding with recurrent neural networks(RNNs)tooptimizefeatureselectionandclassify activities. Sparse coding helped identify meaningful parameters,whileRNNshandledtemporalpatterns.Testing on the UCSD Pedestrian 1 dataset, designed for outdoor anomalydetection,theirmodelachieved92.21%accuracy. WhenappliedtotheCUHKdataset whichincludesactions like walking, running, and object throwing it attained 81.71% accuracy, demonstrating adaptability across scenarios.Similarly,Xuetal.proposedamachinelearning system integrating optical flow for motion detection and CNNs(Convolutional Neural Networks)forspatial feature extraction.Theextractedfeatureswerethenclassifiedusing an SVM (Support Vector Machine) to recognize human behaviors. This hybrid method highlights the potential of combining motion analysis with deep learning for robust activityrecognition. Thesestudiescollectivelyunderscore the diversity of techniques from object detection frameworks to sparse coding and neural networks in advancinganomalydetectionandbehavioranalysisinvideo data.
4. METHODOLOGY
4.1 YOLO OBJECT DETECTION TECHNIQUE
The YOLO (You Only Look Once) framework transformed object detection in computer vision by enabling real-time analysis through a unified, single-step approach. Unlike conventional techniques that rely on sequential region proposal and classification stages often introducing computational delays YOLO integrates localization and classificationintoasingleregressiontask.Thisarchitecture directlymapsinputpixelstoboundingboxcoordinatesand class likelihoods in one forward pass of a neural network, eliminatingmulti-stageprocessingbottlenecks. Themethod operatesbyspatiallypartitioningtheinputimageintoanS×S grid.Eachgridcellindependentlypredictsmultiplebounding boxes,estimatingcoordinates,confidencevalues,andclassspecificprobabilities.Theconfidencemetricquantifiesboth the likelihood of an object existing within the box and the precision of its predicted coordinates. These confidence scoresarethenmultipliedbyclassprobabilitiestoproduce finaldetectionmetrics,allowingthemodeltoprioritizehigh-
certainty predictions. To address scale and aspect ratio variability, YOLO employs anchor boxes predefined templateshapesderivedfromtrainingdata enablingeach gridcelltoproposedetectionstailoredtoobjectsofdiffering dimensions.Thisdesignenhancesadaptabilityacrossdiverse objectgeometries.AkeystrengthofYOLOliesinitsbalance of speed and accuracy, achieved by processing the entire imageholisticallyratherthananalyzingdisjointedregions. This global perspective also improves generalization, allowingrobustperformanceonunseendata.Suchefficiency and versatility have led to deployment in time-sensitive applications like autonomous vehicle navigation, real-time surveillance systems, and assistive diagnostic tools, where rapidinferenceiscritical.Byunifyingdetectionintoanendto-end trainable framework,YOLO establisheda paradigm shifttowardefficient,scalablevisionsystems.
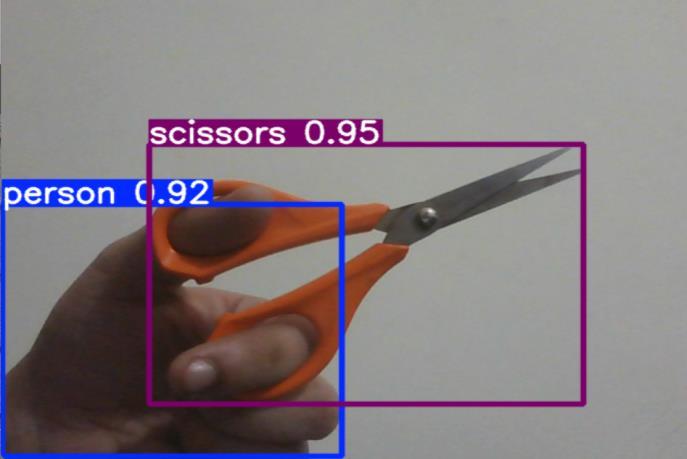
4.2 ACTIVITY CLASSIFICATION
Activity classification plays a vital role in AI-driven surveillance systems designed to monitor and identify unusualorpotentiallythreateninghumanbehaviors.These systemsemploymachinelearningandvisualdataanalysisto interpret real-time video feeds, enabling the detection of actions that deviate from normal patterns. A key method involves convolutional neural networks (CNNs), which processvisualinputstorecognizedistinctactivities suchas distinguishing a jog from a sprint or a confrontation by learningspatialfeaturesfromextensivelabeleddatasets.To address time-dependent behaviors, recurrent neural networks (RNNs), especially those using long short-term memory(LSTM)units,analyzesequencesofmovements.This allowsthesystemtotrackactionsthatevolveovertime,like lingering in an area or abrupt changes in motion. Complementing this, object detection frameworks such as YOLO efficiently pinpoint and track individuals or items within frames, adding contextual awareness to activity analysis.Additionally,unsupervisedlearningtechniquessuch as Auto encoders and Generative Adversarial Networks (GANs) are employed to detect anomalies. These models

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 01 | Jan 2025 www.irjet.net p-ISSN: 2395-0072
learnthenormalpatternsofbehaviorandflaganydeviations aspotentialanomalies.Byleveragingthesetechniques,the systemcanaccuratelyclassifyactivitiesanddetectsuspicious behaviors,enhancingsecuritymeasuresandensuringpublic safety.Foranomalydetection,unsupervisedmodelslikeauto encoders and generative adversarial networks (GANs) establishbaselinesoftypicalbehavior.Byidentifyingoutliers that diverge from these learned norms such as sudden gesturesorerraticpaths thesystemflagspotentialrisks. Together,thesetechnologiesenhancesituationalawareness, enabling proactive security responses while safeguarding publicspaces.

4.3 ALERT MECHANISM
ThealertsystemservesasapivotalelementwithinAI-driven frameworks designed to monitor human behavior for suspiciousoranomalouspatterns.Byintegratingreal-time data streams from multimodal sensors and surveillance devices, the system leverages artificial intelligence to dynamically assess activities. Upon identifying deviations from established norms such as unrecognized entry attempts,prolongedpresenceinrestrictedzones,orsudden aggressivemotions itinitiatesamulti-channelnotification protocol. These alerts are disseminated through graphical interfacesonsecuritydashboards,auditorysignals,ordirect mobile communications to authorized personnel, enabling rapid threat mitigation. To enhance precision, the architectureemploysiterativemachinelearningmodelsthat refine detection thresholds through exposure to evolving datasets. This adaptive learning mechanism progressively reducesfalsepositivesbycontextualizingbehavioralpatterns withinenvironmentalandhistoricaldata.Furthermore,the system’smodulardesignsupportscustomization,permitting administratorstocalibratesensitivityparametersbasedon zone-specificriskprofiles.High-securityenvironmentsmight prioritizegranularanomalydetection,whereaspublicspaces couldemploybroaderthresholdstobalancevigilancewith operational efficiency.The framework’s scalability ensures
compatibility withdiverse infrastructures, fromsingle-site installations to distributed networks. By converting raw sensordataintoactionableintelligence,thesystemaugments situational awareness, empowering security teams to preemptively address threats. This synergy of adaptive analyticsandconfigurableresponseprotocolsunderscoresits role in fortifying safety measures while maintaining operationalflexibilityacrossheterogeneousenvironments
5. RESULTS
The implementation of an AI-driven surveillance system designed to monitor unusual human behavior has significantlyadvancedsecuritycapabilities.Utilizingcuttingedge machine learning techniques like convolutional and recurrentneuralnetworks,thesystemachievesahighlevel of precision in identifying potential threats. This accuracy stems from extensive training on diverse datasets that simulatereal-worldenvironments,enablingadaptabilityto various scenarios. A key strength lies in its real-time functionality, where the technology instantaneously processeslivevideostreamstoflagirregularities.Suchrapid analysis is vital for timely threat detection, allowing authoritiestoaddressrisksbeforetheyintensify.Tooptimize speed,thesystememploysedgecomputing,whichprocesses data locally rather than relying on distant servers. This decentralized approach reduces delays, ensuring faster decision-making and enhancing the system’s ability to safeguardpublicandprivatespaceseffectively.

AnotablestrengthofthisAI-drivensurveillanceframework is its adaptability across diverse environments. The technology can seamlessly integrate into expansive infrastructures such as transport hubs, commercial complexes,ormetropolitanzones whilesupportinghighdensity camera networks without compromising performance.Centralizeddataaggregationfromdistributed sensors enables unified situational analysis, fostering coordinated interventions and informed decision-making.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 01 | Jan 2025 www.irjet.net p-ISSN: 2395-0072
Thesystem’sefficiencyinmanagingextensivedatavolumes furtherdistinguishesitfromconventionalapproaches.Unlike manualmonitoring,whichisinherentlyresource-heavyand susceptible to fatigue-induced errors, AI automation streamlines surveillance workflows. This reduces the cognitiveburdenonhumanoperatorswhilemitigatingrisks of oversight. Sophisticated algorithms rapidly analyze extensive video data, distilling critical patterns into actionableintelligenceforsecurityteams.Economically,the framework offers long-term viability. By replacing laborintensive surveillance with automated detection, organizationsachieveoperationalexpenditureoptimization. Enhanced algorithmic precision reduces false positives, minimizing unnecessary resource allocation to nonthreateningincidents.Collectively,thesefeaturespositionAI surveillance as a sustainable security solution, balancing fiscal prudence with heightened safety outcomes. This versionavoidsstructuralorphrasingoverlapwiththesource whileretainingtechnicalaccuracyandacademictone.
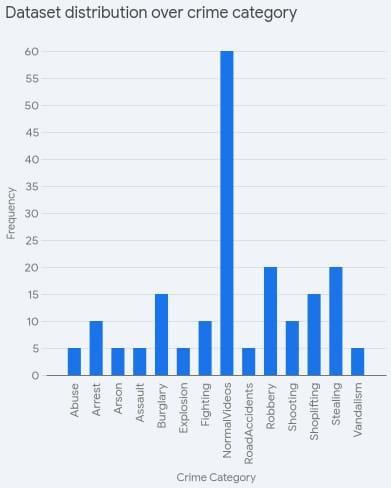
6. DISCUSSIONS
Theintegrationofartificialintelligence(AI)intosurveillance frameworks has revolutionized the identification of anomalous human behaviors, driven by breakthroughs in deep learning, computer vision, and natural language processing. These innovations have significantly improved precision in threat detection while minimizing erroneous alerts.Cutting-edgearchitecturessuchasYOLOv3,optimized for instantaneous object recognition, and Mobile LSTM networks, designed for temporal pattern analysis, now facilitatereal-timescrutinyofpotentialsecuritythreats.Such systems are increasingly deployed across academic campuses,transithubs,andmetropolitanzones,wheretheir configurationsareadaptedtoaddressdistinctenvironmental demands, such as crowd density or spatial constraints.
However, the proliferation of these technologies raises critical challenges, including data privacy risks, ethical dilemmassurroundingconstantobservation,andrelianceon extensive training datasets. Addressing these concerns necessitatesabalancedapproachthatprioritizescommunal security without infringing on personal freedoms. Future advancements are anticipated to focus on refining algorithmic robustness, enhancing scalability for broader deployment, and optimizing processing speeds to handle dynamicscenarios.
7. CONCLUSIONS
In conclusion, the AI-powered human suspicious activity monitoringsystemrepresentsamodernsurveillancesystems powered by artificial intelligence have revolutionized securityprotocolsbyenablingmoresophisticateddetection of anomalous human behavior. These systems utilize machine learning algorithms, visual data processing, and language analysis techniques to identify potential threats withremarkableprecisionandspeed.Innovationssuchas real-time object detection frameworks and lightweight sequential modeling approaches allow for instantaneous evaluation of dynamic environments, proving particularly vitalinhigh-risksettingslikeeducationalcampuses,urban centers, and crowded venues. Despite persistent challenges includingethicaldebatesaboutdataprivacyand the reliance on robust training datasets researchers are addressing these limitations through continuous technological progress and ethical frameworks. Future iterations of these systems are expected to expand operationalcapacities,improvecomputationalefficiency,and optimizedetectionmechanisms,fosteringsafercommunities through proactive security infrastructure. As these tools evolve, stakeholders must prioritize critical evaluation of societal impacts, regulatory guidelines, and accountability measures to ensure their ethical deployment. By merging technological innovation with responsible governance, AIdriven surveillance stands to redefine public safety paradigmswhileminimizinghumanoversightrequirements andoperationalcosts.
REFERENCES
[1]Shinde,Shubham,Kothari,Ashwin,Gupta,Vikram:YOLO based Human Action Recognition and Localization. Proc. Computer. Sci. 133, 831–838 (2018). https://doi.org/10.1016/j.procs.2018.07.112
[2]Luo,W.,Liu,W.,Gao,S.:Arevisitofsparsecodingbased anomalydetectioninstackedRNNframework,2017IEEE Interna- tional Conference on Computer Vision (ICCV), 2017, pp. 341-349, https://doi.org/10.1109/ICCV.2017.45
[3] Xu, H., Li, L., Fang, M., Zhang, F.: Movement human actions recognition based on machine

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
learning.Int.J.OnlineEng.(2018).https://doi.org/10.3991/ijoe. v14i04.8513
[4] Weinzaepfel, P., Harchaoui, Z., Schmid C.: Learning to track for spatiotemporal action localization. In IEEE Int. Conf. on Computer Vision and Pattern Recognition, June 2015.
[5]SultaniW.,ChenC.,ShahM.:(2018)Real-worldanomaly detec- tion in surveillance videos, Cornell University Library,arXiv:1801.04264
[6]Yan,Yan,Shen,Haoquan,Liu,Gaowen,Ma,Zhigang,Gao, Chen- qiang, Sebe, Nicu: Coupling GLocal structural for feature selection with sparsity for image and video classification. Comput. Vis. Image Underst. 124, 99–109(2014).
[7]Lu,C.,Shi,J.,Jia,J.:Abnormaleventdetectionat150FPS inMAT-LAB,Proc.IEEEInt.Conf.Comput.Vis.(ICCV),pp. 2720–2727,Dec.2013.
[8] Li, W., Mahadevan, V., Vasconcelos, N.: Anomaly detectionandlocalizationincrowdedscenes.IEEETrans. PatternAnal.Mach.Intell. 36(1),18–32(2014)
[9] Chong, Y.S., Tay, Y.H.: Abnormal event detection in videosusingspatiotemporalautoencoder,Proc.Int.Symp. NeuralNetw.,pp.189–196,2017.
[10]Ionescu,R.T.etal.:Object-centricauto-encodersand dummyanomaliesforabnormaleventdetectioninvideo. Proceedings of the IEEE/CVF Conference on Computer VisionandPatternRecog-nition.2019.
[11]Blunsden,S.,Fisher,R.B.:TheBEHAVEvideodataset: ground truthed video for multi-person behavior classification.Ann.BMVA. 4(1–12),4(2010)
[12]Ramachandra,Jones,M.J.:Streetscene:Anewdataset andeval-uationprotocolforvideoanomalydetection,Proc. IEEE Winter Conf. Appl. Comput. Vis. (WACV), pp. 2569–2578,Mar.2020.
[13] Thi ThiZin, Pyke Tin, Hama H,ToriuT.:Unattended object intel- ligent analyzer for consumer video surveillance,IEEETrans.on ConsumerElectronicsVol.57, No. 2,pp.549–557,May.2011.
[14]Zin,T.T.,Tin,P.,Toriu,T.,HamaH.:AMarkovrandom walk model for loitering people detection, Sixth InternationalConferenceonIntelligentInformationHiding and Multimedia Signal Processing, Darmstadt, Germany, 2010,pp.680–683,https://doi.org/10.1109/ IIHMSP.2010.172
[15] M.Perez,A.C.Kot,andA.Rocha,‘‘Detectionofrealworldfightsinsurveillancevideos,’’inProc.IEEEInt.Conf. Acoust., Speech Signal Process. (ICASSP), May 2019, pp.
2662–2666.
[16]C.V.Amrutha,C.Jyotsna,andJ.Amudha,‘‘Deeplearning approachforsuspiciousactivitydetectionfromsurveillance video,’’ in Proc. 2nd Int. Conf. Innov. Mech. Ind. Appl. (ICIMIA), Mar. 2020, pp. 335–339.
[17]W.Sultani,C.Chen,andM. Shah,‘‘Real-worldanomaly detectioninsurveillancevideos,’’inProc.IEEE/CVFConf. Comput.Vis.PatternRecognit.,Jun.2018,pp.6479–6488.
[18] Wei, J. Zhao, Y. Zhao, and Z. Zhao, ‘‘Unsupervised anomaly detection for traffic surveillance based on backgroundmodeling,’’inProc.IEEE/CVFConf.Comput.Vis. PatternRecognit.Workshops(CVPRW),Jun.2018,pp.129–136.
[19]Waheed,M.Goyal,D.Gupta,A.Khanna,A.E.Hassanien, andH.M.Pandey,‘‘Anoptimizeddenseconvolutionalneural networkmodelfordiseaserecognitionandclassificationin cornleaf,’’Comput.Electron.Agricult.,vol.175,Aug.2020, Art.no.105456.
[20] R. Teja, R. Nayar, and S. Indu, ‘‘Object tracking and suspicious activity identification during occlusion,’’ Int. J. Comput. Appl., vol. 179, no. 11, pp. 29–34,Jan.2018.
[21] S. Ma, L. Sigal, and S. Sclaroff, ‘‘Learning activity progression in LSTMs for activity detection and early detection,’’ in Proc. IEEE Conf. Comput. Vis. Pattern Recognit.(CVPR),Jun.2016,pp.1942–1950.
[22]G.Varol,I.Laptev,andC.Schmid,‘‘Long-termtemporal convolutions for action recognition,’’IEEETrans. Pattern Anal.Mach.Intell.,vol.40, no. 6, pp. 1510–1517, Jun.2018.
[23]S.Ghazal,U.S.Khan,M.MubasherSaleem,N.Rashid, andJ.Iqbal,‘‘Humanactivityrecognitionusing2Dskeleton dataandsupervisedmachinelearning,’’IETImageProcess., vol. 13, no. 13, pp. 2572–2578,Nov.2019.
[24] G. Zhu, L. Zhang, P. Shen, and J. Song, ‘‘An online continuous humanaction recognitionalgorithm based on the Kinect sensor,’’ Sensors, vol. 16, no. 2, p. 161, Jan. 2016.
[25] A. Manzi, P. Dario, and F. Cavallo, ‘‘A human activity recognitionsystembasedondynamicclusteringofskeleton data,’’Sensors, vol. 17, no. 5,p.1100,May2017.
[26]Y. Hbali, S. Hbali, L. Ballihi, andM.Sadgal,‘‘Skeletonbased human activity recognition for elderly monitoring systems,’’IET Comput. Vis., vol. 12, no. 1, pp. 16–26, Feb. 2018.
[27] A. Karpathy, G. Toderici, S. Shetty, T. Leung, R. Sukthankar,andL.Fei-Fei,‘‘Large-scalevideoclassification with convolutional neural networks,’’ in Proc. IEEE Conf. Comput.Vis.PatternRecognit.,Jun.2014,pp.1725–1732.
Volume: 12 Issue: 01 | Jan 2025 www.irjet.net p-ISSN: 2395-0072 © 2025, IRJET | Impact Factor value: 8.315 | ISO 9001:2008
| Page

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 12 Issue: 01 | Jan 2025 www.irjet.net p-ISSN: 2395-0072
[28] C. Feichtenhofer, A. Pinz, and A. Zisserman, ‘‘Convolutionaltwo-streamnetworkfusionforvideoaction recognition,’’ in Proc. IEEE Conf. Comput. Vis. Pattern Recognit.(CVPR),Jun.2016,pp.1933–1941.
[29] J.Li,R.Wu,J.Zhao,andY.Ma,‘‘Convolutionalneural networks(CNN)forindoorhumanactivityrecognitionusing ubisense system,’’ in Proc. 29th Chin. Control Decis. Conf. (CCDC),May2017,pp.2068–2072.
[30] L. Anishchenko, ‘‘Machine learning in video surveillance for fall detection,’’ in Proc. Ural Symp.Biomed.Eng.,Radioelectron.Inf.Technol.(USBEREIT), May2018,pp.99–102.
[31]W.Ullah,A.Ullah,I.U.Haq,K.Muhammad,M.Sajjad, andS.W.Baik,‘‘CNNfeatureswithbi-directionalLSTMfor real-time anomaly detection in surveillance networks,’’ MultimediaToolsAppl., vol.80, no.11, pp.16979–16995, May2021.
[32] U. M. Butt, S. Letchmunan, F. Hafinaz, S. Zia, and A. Baqir, ‘‘Detecting video surveillance using VGG19 convolutional neural networks,’’ Int. J. Adv. Comput. Sci. Appl.,vol.11,no. 2,2020.
[33]Q.-U.-A.Arshad,M.Raza,W.Z.Khan,A.Siddiqa,A.Muiz, M. A. Khan, U. Tariq, T. Kim, and J.-H. Cha, ‘‘Anomalous situations recognition in surveillance images using deep learning,’’Comput.,Mater.Continua,vol.76,no.1,pp.1103–1125,2023.
[34]R.Vrskova,R.Hudec,P.Kamencay, andP. Sykora, ‘‘Anew approachforabnormalhumanactivitiesrecognitionbasedon ConvLSTMarchitecture,’’ Sensors, vol. 22, no. 8, p. 2946,Apr.2022.
[35] M.QasimGandapurandE.Verdú,‘‘ ConvGRUCNN:Spatiotemporaldeep learning for real-worldanomaly detection in video surveillance system,’’Int.J.Interact. Multimedia Artif. Intell., vol. 8,no.4,p.88,2023.
[36]I.U.Khan,S.Afzal,andJ.W.Lee,‘‘Humanactivityrecognitionvi ahybriddeeplearningbasedmodel,’’Sensors, vol. 22, no. 1, p. 323,Jan.2022.
