

When Investors Ask the Cyber Question
A Cost-Benefit Framework for Private Equity and Hedge Fund Managers
What LPs Are Asking and Why It Matters Now
According to the Private Funds CFO Insights Survey 2025, LP scrutiny of cybersecurity has increased materially. Forty-seven percent of CFOs report that investor questions about cybersecurity have risen over the past 12 months. Ninety-one percent say LPs are asking very detailed or moderately detailed questions during due diligence, and roughly two-thirds report that LPs always or sometimes ask about cyberattack readiness policies.
This scrutiny is no longer abstract. The questions LPs raise are increasingly specific, documented, and standardized. Industry due diligence questionnaires used across private equity and hedge fund investing have expanded their focus on technology risk, governance, and cybersecurity practices, reflecting how central these issues have become to fund oversight.
When LPs send these questionnaires, they are typically asking practical questions. What frameworks are followed. What certifications or attestations can be demonstrated. How cyber risk is assessed across the portfolio. What incident response procedures are formally documented. These questions are no longer satisfied by narrative explanations. They require evidence.
This shift has also become more structural. The ESG Data Convergence Initiative, which includes more than 500 participating GPs and LPs representing approximately $59 trillion in assets under management, has introduced cybersecurity as a formal metric for its 2026 reporting cycle. Portfolio companies are asked to document specific cyber risk management activities, with results benchmarked across the initiative’s dataset.
For fund managers, the implication is straightforward. LPs are increasingly able to compare cybersecurity posture across portfolios using consistent formats. Where portfolio companies cannot document their practices in ways LPs recognize, fundraising discussions tend to become more difficult, particularly when compared with peers that can provide clearer evidence.
The same survey indicates that a majority of CFOs believe strong cybersecurity protocols are now considered baseline expectations by investors. Against this backdrop, two practical questions follow. What does it cost when portfolio companies or targets cannot answer the cyber question clearly. And what is the most efficient way to establish documented cyber governance at a cost that makes economic sense.

The Market Price of Cyber Risk
The financial consequences of cyber incidents are well documented, particularly in public markets. When a material breach is disclosed, share prices often react quickly, and the effects can persist beyond the initial announcement.
Multiple studies have examined this dynamic. Analysis summarized in business and academic research shows that companies commonly experience short-term stock price declines following major breach disclosures. Separate analysis by Comparitech, reviewing more than 100 breached public companies, found that affected stocks underperformed the NASDAQ index over the six months following disclosure, with particularly pronounced effects in sectors such as healthcare. In that analysis, share prices tended to reach their lowest point several weeks after disclosure before gradually recovering.
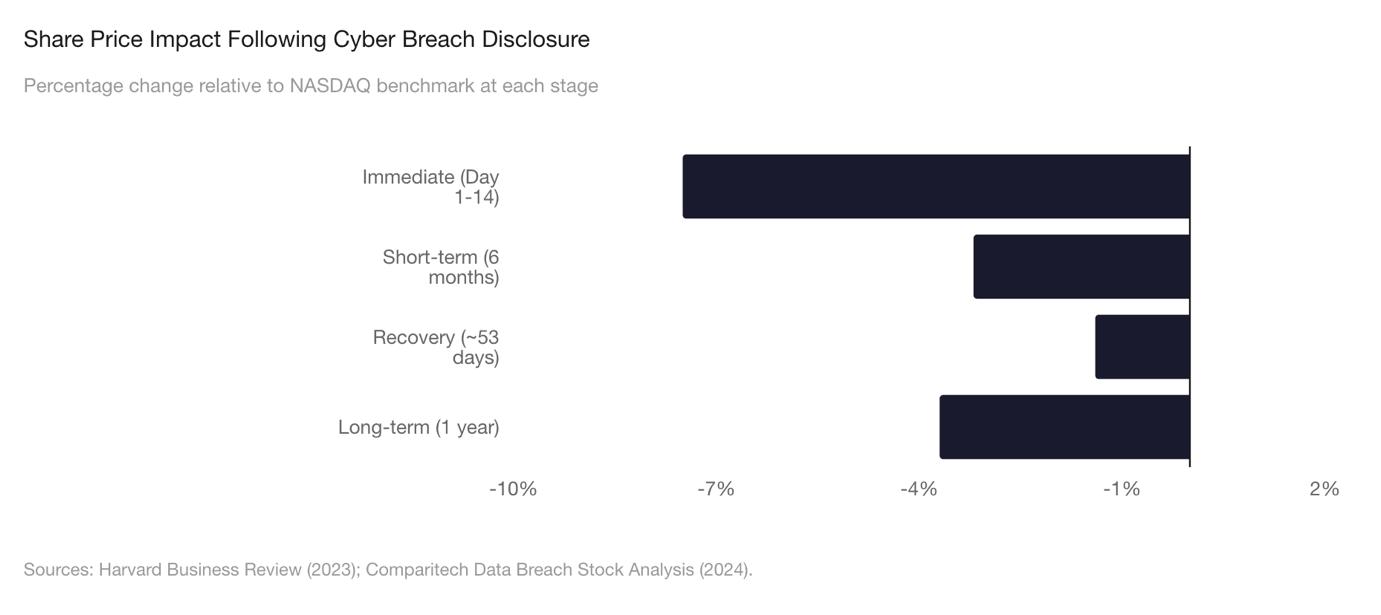
For private companies, the impact is less visible but no less relevant. High-profile transactions have demonstrated that undisclosed cyber incidents discovered during due diligence can materially affect deal outcomes. The reduction in Verizon’s acquisition price for Yahoo following the discovery of historical breaches remains a widely cited example. Surveys of corporate buyers consistently indicate that cybersecurity weaknesses identified late in a transaction can delay deals, require renegotiation, or in some cases halt transactions altogether.
Conversely, buyers regularly report that companies with clearer security governance, established controls, and recognizable standards move through diligence more smoothly. While the precise valuation impact varies by transaction, cybersecurity maturity increasingly functions as a friction reducer rather than a last-minute risk factor.
ISO 27001 remains one of the most widely recognized benchmarks for information security governance, requiring a documented information security management system, formal risk assessment processes, and evidence of ongoing improvement. In cross-border

transactions, it is often complemented by SOC 2 reporting, particularly for technologyenabled businesses operating in US markets. The overlap between these frameworks allows many organizations to pursue both more efficiently than approaching them independently.
Regulatory Pressure and Why LPs Are Asking
LP interest in cybersecurity is closely tied to regulatory exposure. When portfolio companies face compliance failures, the consequences can affect exit timing, transaction value, and fund reputation. LPs are asking more detailed questions because regulatory expectations continue to rise.
In the United States, SEC cybersecurity disclosure rules effective from late 2023 require public companies to disclose material cybersecurity incidents within four business days and to include annual disclosures on cyber governance and risk management. Portfolio companies preparing for IPOs must have governance structures in place well in advance of filing.
Additional reporting obligations are expected under the Cyber Incident Reporting for Critical Infrastructure Act once final rules are adopted. Together, these developments explain why cybersecurity has become a standard feature of LP questionnaires. Investors need confidence that portfolio companies will not introduce regulatory or operational risks that undermine returns.
The Digital Operational Resilience Act came into effect in January 2025 for EU financial entities. It requires documented ICT risk management frameworks, incident reporting processes, and regular resilience testing. Financial services portfolio companies operating in the EU must now demonstrate compliance as part of ongoing supervisory oversight.
The NIS2 Directive has expanded cybersecurity obligations across sectors including energy, transport, healthcare, digital infrastructure, and financial services. Member states were required to transpose the directive by October 2024, and enforcement activity is beginning in jurisdictions that have completed implementation.
Framework Costs and the Point-in-Time Problem
Fund managers and portfolio companies face a wide range of cybersecurity frameworks, each with different costs, recognition, and implementation demands.
ISO 27001 and SOC 2 Type II remain the most widely recognized formal standards, particularly for companies selling into regulated or enterprise markets. Both typically require specialist support, structured audits, and ongoing maintenance. NIST CSF is widely used as a reference framework but is not certifiable in the same way. Cyber Essentials provides a more accessible baseline for UK companies, focusing on core

technical controls, but it does not address broader governance, incident response, or operational resilience.
*Not certifiable frameworks. Costs represent typical mid-sized organization.
A common limitation across certification-based approaches is that they represent a point in time. Controls can drift between audit cycles, documentation may fall out of sync with practice, and internal reviews are often delayed due to competing priorities. A certificate alone does not necessarily reflect current risk.
Cost is another structural issue. Traditional ISO 27001 consulting engagements commonly run tens of thousands of dollars per company, before audit and ongoing maintenance costs are considered. Enterprise governance, risk, and compliance platforms add further expense and often require dedicated expertise to operate. For diversified portfolios, aggregate spend can become significant without necessarily producing current, comparable data across companies.
A Different Approach for Hedge Funds and Private Equity
Against this backdrop, many hedge funds and private equity firms are exploring complementary approaches that sit alongside formal frameworks rather than replacing them.
For hedge fund managers, the challenge during investment analysis is often how to assess cyber risk when a target does not yet hold formal certifications. Structured assessment tools that translate security practices into standardized maturity scores can provide useful insight, particularly when benchmarked against peers of similar size and sector. This allows cyber risk to be discussed alongside other diligence factors using comparable, nontechnical language.
For private equity firms, usability across the portfolio is critical. Many portfolio companies do not have dedicated security teams, and tools designed for large enterprises often go unused. Approaches that allow operational leaders to assess risk, track progress, and generate consistent documentation across multiple frameworks tend to be adopted more effectively.

One example is RateYourCyber, a structured cyber risk assessment platform designed to produce a quantified view of security maturity across multiple domains and to benchmark results against peer groups. Rather than functioning as a certification, it is intended to support continuous measurement and improvement, helping companies understand where they stand and where gaps remain relative to recognized frameworks.
RateYourCyber was shortlisted for Security Innovation of the Year at the Computing Security Excellence Awards 2026, an independently judged industry award that recognizes products demonstrating practical innovation and impact. That recognition reflects a broader trend toward tools that emphasize comparability, repeatability, and clarity for non-specialist stakeholders.
From a portfolio perspective, structured assessments and centralized reporting can provide current, consistent data at a cost materially lower than engaging traditional consultants on a company-by-company basis. This is particularly valuable during LP reporting and exit preparation, where up-to-date evidence matters more than historic certification.
Continuous Measurement, Not Point-in-Time Certification
One of the clearest lessons from recent years is that cybersecurity governance is not a one-off exercise. Continuous measurement allows portfolio companies to demonstrate progress over time, identify emerging gaps earlier, and respond more effectively to evolving threats and regulatory expectations.
When LP questionnaires arrive, current data showing improvement and alignment with recognized frameworks is more persuasive than relying on certificates issued years earlier. For fund managers, this shifts cybersecurity from a reactive compliance exercise into a more manageable operational discipline.
Conclusion
Cybersecurity governance has become a material component of risk management and value protection across private markets. Companies that can clearly document their practices tend to encounter fewer obstacles during diligence, while those that cannot often face delays, additional scrutiny, or renegotiation.
For hedge funds, structured cyber risk assessment improves investment insight. For private equity firms, enabling portfolio companies to manage and document cybersecurity more effectively reduces LP friction and operational risk. In both cases, the underlying economics are increasingly clear. Modest, well-directed investment in governance and measurement can prevent disproportionately costly outcomes later.

When LPs ask the cyber question, the strongest response is not a defensive explanation. It is current data, clear documentation, and evidence of ongoing improvement, presented in terms that align with how investors already evaluate risk and capital allocation.
About the author:
Andrey Darenberg, founder, RateYourCyber.com: Last 12 years in cybersecurity, with 10 years in governance consulting. Corporate strategy, investments and venture capital background, finance by training. PhD in Finance, MBA, IT Systems Analysis and Design (Oxford), C-DORA-P, ISO 27001 Lead Auditor, C-DPO, CE auditor, IASME auditor.
