Research Paper
Engineering
E-ISSN No : 2454-9916 | Volume : 3 | Issue : 10 | Oct 2017
SECURE DATA SHARING BY ENCRYPTION OF IDENTITY BASE WITH REVOCABLE STORAGE 1
Rutambh Trivedi | Shyamsundar Kosbatwar 1 2
2
Department of Computer Engineering, SKN Sinhgad College of Engineering, Pune, India - 411041. Professor, Department of Computer Engineering, SKN Sinhgad College of Engineering, Pune, India - 411041.
ABSTRACT A Cloud computing is really a feasible way for sharing the data and its fast and reliable. It can be beneficial for both society and the users who are using that. But sometime it happens that user upload the data to the cloud server and it contains the very valuable information or private information. That’s why it is necessary to keep the track of the data and secure that by crypto graphically, Identity based encryption can be useful for develop the crypto graphical tool for this issue. Thus we cannot ensure that its will be static. Main issue is that the when the certain user’s authorization will expire than it should be removed from the Process, and also ensure that the user who is revoked cannot access the data that is previously shared. For maintaining this issue we are developing the recoverable storage identity based Encryption RSIBE, with giving cipher text and security of forward and back end user. In this user revocation will also include. The security model will also developed. When we compared our RSIBE it can be beneficial for the users in the areas of performance, functionality and efficiency and it can also be low in the cost. And then at the end we will provide the implementation results for comparing. KEY WORDS: Cloud computing, Revocation, Cipher text, Security, Identity Based, Data Sharing. INTRODUCTION: Cloud Computing is feasible for the give the huge amount of complex computing and the benefits to the user and the in cloud computing the user can access his/her data at any platform and anytime and anywhere for example mobile devices and personal computers that’s why it’s really convenience way for the users. There are many cloud available this time for example Apple’s, Microsoft’s, Amazon’s S3.But the primary concern for this is the issue of the security in the cloud. First of all when user upload the data to the cloud it’s no longer in his/her hands so user can’t control the data and that’s why user don’t think that’s its secured. The second concern is that the cloud is the open environment so the number of attacks will be huge. That’s why it’s necessary to give authorization to the users that when the authorization expires they can’t access the data. That’s why users wants to share the data only with those who had the authorization and cannot use the valuable information or misuse that. Main problem is the use the access of identity base encryption for the given system. MATERIALS AND METHODS: Technologies Used: During the solution development, following hard-wares were used: • 250 GB HD • 4GB RAM • Cloud Environment • Wireless Router
Table 3: Comparison of Security and Functionality with Previous Works Schemes
Model
Libert and Vergnaud
Assumption PKU PCU CA DKE FS BS
Adaptive
DBDH
✓
✗
✓
✗
Seo and Emura Adaptive
DBDH
✓
✗
✓
✓
✓ ✗
✓
✗
Liang et al.
Adaptive
DBDH
✗
✗
✗
✓
✓ ✓
Our scheme
Adaptive
ℓ-dBDHE
✓
✓
✓
✓
✓ ✓
PROPOSED METHODOLOGY Cipher text extension introduced by this paper, the number of cipher text to shared data available is same as the number of share data updated. Proxy reencryption can be useful for terminate the problem of efficiency. But that requires the user to interact with cloud so that shared data can be converted to Cipher text.
Software Requirement: • ASP.NET • Cloud Environment Results: Table 1: Comparison of Communication and Previous work Schemes Private key size Update key size
Ciphertext size
Libert and Vergnaud
O(log N )τG1
O(r log N/r)τG1
O(1)τG1 + O(1)τG2
Seo and Emura
O(log N )τG1
O(r log N/r)τG1
O(1)τG1 + O(1)τG2
Liang et al.
O(1)τG1
O(1)τG1
O(1)τG1 + O(1)τG2
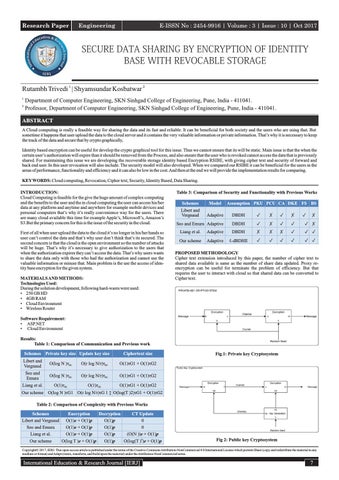
Fig.1: Private key Cryptosystem
Our scheme O(log N )τG1 O(r log N/r)τG 1 ‡ O(log(T )2)τG1 + O(1)τG2 Table 2: Comparison of Complexity with Previous Works Schemes
Encryption
Libert and Vergnaud O(1)e + O(1)p Seo and Emura O(1)e + O(1)p Liang et al. O(1)e + O(1)p Our scheme O(log T )e + O(1)p
Decryption
CT Update
O(1)p O(1)p O(1)p O(1)p
0 0 (O(N ))e + O(1)p O(log(T )2)e + O(1)p
Fig 2: Public key Cryptosystem
Copyright© 2017, IERJ. This open-access article is published under the terms of the Creative Commons Attribution-NonCommercial 4.0 International License which permits Share (copy and redistribute the material in any medium or format) and Adapt (remix, transform, and build upon the material) under the Attribution-NonCommercial terms.
International Education & Research Journal [IERJ]
7