International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
1M. Tech scholar, Dept. Of Systems and Signal Processing, JNTU-GV College of Engineering Vizianagaram(A), Andhra Pradesh, India.
2Associate Professor, Dept. of Electronics and Communication Engineering, JNTU-GV College of Engineering Vizianagaram (A), Andhra Pradesh, India. ***
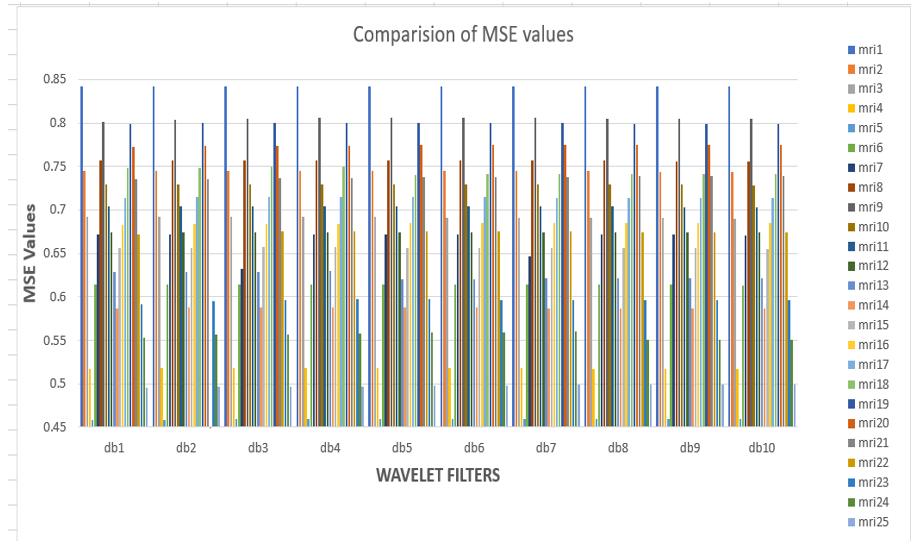
Abstract – Inthispaper,wearediscussingabouttheHybrid transforms-basedwatermarking,encryptionandcompression of bio-medical images. The entire system is designed using MATLAB Software with the version of 2021a. Nowadays, Medical information plays an important role in medical diagnosis, transferring of that information should be done in an encrypted manner. Proposed novel Image Watermarking which is based on the Discrete Wavelet Transform (DWT), Hessenberg Decomposition (HD) and Singular Value Decomposition (SVD). Inverse Discrete Wavelet Transform (IDWT) used for retrieval of image. In this, watermark is embeddedintosub-bandscoefficient.Sub-bandcoefficientsare marked by adding a watermark of the same size of the three sub-bands.Comparisonofembeddingawatermarkatvertical (LH), horizontal (HL) and diagonal (HH) details. Here, Compression scheme applied on the watermarked image to reduce size of the data without losing its quality. AES encryption is used for security and proposed methodology analyzed on data sets of MRI of brain images and Retina images. The performance metric is analyzed after dewatermarkingwithdifferentordersofDaubechieswaveletsby using parameters like Peak Signal to Noise Ratio (PSNR), Mean Square Error (MSE), Root Mean Square Error (RMSE) and Compression Ratio (CR).
Words: Image Watermarking, DWT, HD, SVD, IDWT, Compression, AES Encryption
Watermarking is a process of embedding information into a digital signal such as image, video, audio data to easily identify the ownership of the original data.Therefore,itwillbeembeddedinawaywhichmakesit difficult to be visualize with the human eye and to be removed.Ascomputersaremoreandmoreintegratedvia the network, the distribution of digital data is becoming faster,easier,andlessefforttomakeexactcopies.Oneofthe presentresearchareasistoprotectdigitalwatermarkinside theinformationsothatownershipofinformationwillnotbe claimed by the third party. The working domain of the watermarking is either spatial or frequency. Medical data exchangebetweenthedepartmentsisnotjusthospitals,but betweenhospitalsindifferentgeographicalareas. Medical
images require strict security measures. The medical information can often be shared to the professionals to improve treatment Huge amount medical data should be processed in hospitals for clinical and medical purpose of research. Malicious attacks on this medical data repots shouldbeavoidedandalsocancreatemedicalimageswith watermarks certification. Image quality is distorted in the spatialandtransformdomains.Theprocessofinsertingand extracting watermarking process. In the original image, a watermark(hiddenimageinformation)isinserted.IfImages areretrievedfromthedatabase,allowingphysicianstosee AuthenticationPhasewithExtractionwatermark.However, upon successful watermark extraction, created and the doctorcanproceedwiththediagnosistrust.Developmentof theDWT-HD-SVDAlgorithmBasedonthewatermarkused for this study A series of biomedical images are hidden under the cover image Embedding and retrieval of watermarks in data can be analyzed. This transformation includesfrequencyandLocationinformation,asopposedto theFouriertransform.Here,Signalenergyisconcentratedin specific wavelet coefficients with the discrete wavelet transform.Thispropertyisusefulwhenimagecompression is needed. lossless compression is used to Minimize data size. Encryption and decryption are Used the security. Proposal performance of medical data storage is also evaluatedbymultiplemetricssuchasmeansquarederror (MSE),peaksignalsignal-to-noiseratio(PSNR),root-meansquareerror(RMSE),andCompressionratio(CR).
A safer and more robust digital watermarking method based on encryption algorithms and asymmetric RSAEncryptiontechniqueshavebeenproposedtoprotect hidden things (DWT) and singular value decomposition (SVD) Thepowertoestimateembeddingawatermarkinthe low-frequency sub bands of the host image. Transmitted biomedical images and visual data are Watermark encryptionalgorithmanduseofthisalgorithmcompression, watermarking,Encryptiontoprotectdata.medicalimaging combined with security analysis of A study of encryption/watermarking (E/W) systems found that Wavelet transform (DWT) and singular values Decomposition Techniques to Reduce Ambiguity (SVD)
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
Guaranteedbysingularvaluedecomposition(SVD).Digital Watermarking Method Combining Discrete Wavelets Transformation by Singular Value Decomposition (DWT) Show that DWT-SVD produces good images uses block encryption techniques to achieve this. Watermark image encryption and compression, the method relies on watermarks. Distributors need to know each user`s encryption key to complete the process processing, managementanddistributionofprivatekeys;Errortryingto improve watermark security Watermark extraction takes time.proposedanewimagewatermarkingapproachbased on DWT-HD-SVD, AES encryption are trying to improve watermarksecurityandwatermarkextraction.
ThissectionpresentsthethreetechniquesDWT,HD,and SVD used in the proposed watermark method. MultiresolutiontimescalesignalofDWTcanimprovewatermark performance. HD performs as the matrix transforms have further improved robustness. In addition, SVD-based watermarking schemes have improved performance in defendingagainstgeometricattacks.
TheDiscreteWaveletTransformisthetransformusedin bothNumericalandfunctionalanalysis.Waveletissampled. This transform uses discrete values. This conversion includes Advantages of collecting both frequency and locationinformation,ContrastwiththeFouriertransform. signal energy Focus on specific wavelet coefficients in discreteWavelettransform(DWT).Thispropertyisuseful forimagescompression.Amulti-resolutionrepresentation calledDWTusedtoDecodestepbystepfromlowresolution tohighresolution.DWTseparatesthesignalintotwohalves. HighFrequencyandlowfrequency.highfrequencysegment representstheedgecomponent,andthelowfrequencyisthe section and is again divided into a high frequency section and a low frequency section. Since the human eye is not sensitivetoedgevariations,Highfrequencycomponentsare usuallyused.
HDisatypeofmatrixdecompositionscanbeusedfor squarematrixdecomposition.An×nsquarematrixXcanbe decomposedbyusingHDasshownby
PHPT =HD(X),
where P is an orthogonal matrix and H is an upper Hessenbergmatrix,andhi,j=0wheni>j+1.HDiscomputed by the Householder matrices. Householder matrix Q is an orthogonalmatrixanditisexpressedas
Q=(In −2µµT)/µT µ, where µ is a non-zero vector in Rn, and I n is a n × n identity matrix. n−2 steps are in the overall procedure. Therefore,HDiscomputedas P=(Q1Q2 ...Qn−2)TX(Q1Q2 ...Qn−2) ⇒H=PT XP ⇒X=PHPT
Itisafactorizationofthatmatrixintothreematricesin linear algebra. It possesses some unique algebraic characteristics and communicates key geometrical and theoreticalinsightsintolineartransforms.Itisalsohaving several interesting data science applications. It is a signal processingtechniquethatiswidelyemployed.SVDisused for noise reduction and image compression, among their things.
A isamxnmatrixthatyouobtainedfromanimageor anotherdatasource.Theorthogonalmatrices U and V are orthogonalmatricesand ∑ isadiagonalmatrix.Findingthe eigenvaluesandeigenvectorsof A and isthefirst stepincalculatingtheSVD.
The columns of V are formed by the eigenvectors of ,whilethecolumnsofUareformedbytheeigenvectors of A Singular values in S are also square roots of eigenvaluesfrom A or …singularvaluesarealways numbersthataregenuine.
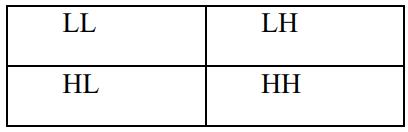
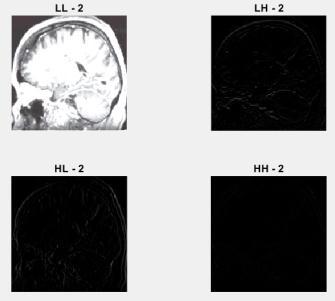
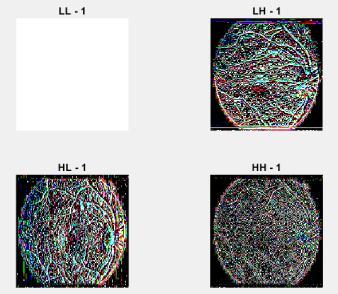
Here, LL band filter in 1-stage DWT decomposition contains a lot of information from the original image. Vertical, horizontal, skew(diagonal) information of the originalimagesisincludedintheLH,HL,andHHbands. LL bandOnlyimagescanreproducetheoriginalimage.Other bandsareignored.
Itisnormallyactsonthehostimage,orthehostimageis first segmented into numerous small blocks and then decomposedusingSVDtogeneratesingularvalues,which are used to incorporate watermark information. The SVD coeffects’sizeisconstant,thesingularvaluescandescribean image’sessentialalgebraicproperties,andsingularvalues are likely to vary substantially when the image is slightly disrupted.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
Encryptionisessential toInternetsecuritytoday. The encryptionsystemtransformsandencryptssensitivedataas Code with mathematical calculations.only the correct key reveals the original data and make sure it's safe from everyoneExceptauthorizedparties.encryptionisHidedata bytransformingitintoasecretcode.
Data encryption and decryption research known as cryptography.Forcomputers,whatisplaintext?Ciphertext referstoencrypteddata,butunencrypteddata.
Therearethreemaintypesofencryptionsforsecurity, theseareAES,DES,andRSA.AdvancedEncryptionStandard (AES) is best Encryption standard. AES Encrypts data in single blocks rather than as individual bits. the Block size indicatesthenameofeachAEStypeofencrypteddata.Here, samekeyisusedforencryptionanddecryption.Decryption, althoughthetechniqueisimplementedSeparately.
Thisprocessinvolvesencryptionanddecrypt, butthe only difference is the decryption Implemented in reverse order.
=AES ( )
Where, isthepreviousencryptedblockand isthe encryptionkey.
Imagecompressionisa techniquefordiminishingthe irrelevanceandredundancyofimagedatasothatitcanbe stored or transmitted in a more Efficient manner. Image compressionistheprocessofShrinkingthesizeofanimage withoutsacrificingitsquality.
Inafileandsendorcommunicatewithothers.Oneof the most widely used transform techniques for image compression of medical images using wavelets is Discrete Wavelet Transform (DWT). This DWT is very useful for compressing signal and shows better results for medical grayscaleimages.
While using DWT the important parameters that are taken into consideration are testing the image, wavelet function, number of iterations and calculation complexity. Thesewaveletstransformsareusedtoprocessandimprove signals in fields like medical imaging where image degradationisnottolerated.
Thedatasetsconsideredinthisprojectareasetofretina imagesandMRIofbrainimages.
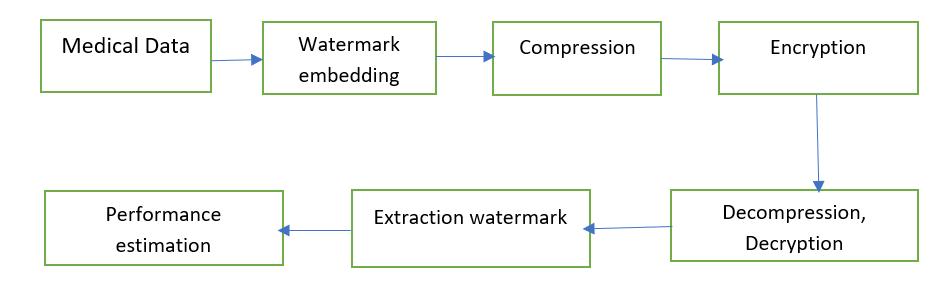
Here,wedesignanalgorithmfortheapplicationof thewatermark.watermark,encryption,andcompressionare representedinthisalgorithm.Intheprocessofwatermark embedding,twolevelDWTisappliedonthehostimageand thelowfrequencysubbandwasthenobtainedandsubband was further processed by HD and SVD. In addition, the scalingfactorisaddedtocontrolthewatermarkembedding strength.Thenewvaluewassubdividedonceagaintogeta newsingularvaluewhichwasusedtoreconstructfrequency sub band. Finally, the watermarked image was formed by makingusingofnewsubbandaftertheprocessofinverse discretewavelettransform.Afterthatapplythecompression on the watermarked image and the AES encryption is applied to the compressed image. The decryption and the decompressionareconductedseparately.
1. Starttheprogram
2. Lookatthefirstimageintheinput(coverimage).
3. Open Dataset 2 (Host image) or image 2 (input image).
4. Resizetheimage1to300X300.
5. Resizetheimage2to300X300andgenerateakey valuetoapplywaveletsontheimages.
6. To partition the image for watermarking, use the DWTapproachusingthehaarwavelet.
7. AfterapplyingtheDWTtotheimage,itisseparated intofoursub-bands:h-LL,h-LH,h-HL,h-HH.
8. HDisperformedonLL,anditisshownasPHP T = HD(LL).
9. ExtracttheRGBcolorfrominputimage1andinput image 2, apply SVD algorithm on red, green, and bluecolorandSVDtoHi.e.,HUwHSwHVT w=SVD(H).
10. WisappliedwithSVD,i.e.,UwSwVT w =SVD(W).
11. Compute an embedded singular value HS∗ w by addingHSwandSwwithascalingfactorαbyHS∗ w= HSw +αSw
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
12. The watermarked sub-band H∗ is generated by usingtheinverseSVD,i.e.,H∗ =HUwHS∗ wHVT w
13. Apply the watermarking with some intensity and gettheoutputimagewiththehelpofIDWT.
14. Save the watermarked image with the help of imwritecommand.
15. Applythecompressiononthewatermarkedimage and save the compressed image in a secret folder withthehelpofimwritecommand.
16. Apply the encryption to the compressed watermarkedimage.
TheoperationofDWTwasappliedtothewatermarked image, and the low frequency approximate coefficient of Which was further decomposed. The Watermark was obtainedundertheutilizationoftheoriginalhostimageand thenewlyformedsingularvalue.
1. Starttheprogram
2. NowReadthesecretfolder.
3. SavetheDecrypted&decompressedimagewiththe helpofimwritecommand.
4. Readthewatermarkedimage.
5. Apply the DWT technique with Haar wavelet to divide the image for watermarking. The image is then divided into 4 sub-bands i.e., ωm -LL, ωm-LH, ωm -HL,ωm-HH.
6. HDisperformedonLLw byPwHwPT w =HD(LLw) Apply SVD to Hw, i.e., HU∗ wHSb∗ wHV∗ w T = SVD(Hw) andExtracttheRGBcolorfromoriginalimageand applySVDalgorithmonred,green,andbluecolor. TheextractedsingularvalueS∗ w isgainedby S∗ w = (HSb∗ w − HS∗ w)/α.The extracted watermark W∗ is reconstructed by inverse SVD, which is describedbyW∗=Uw2S∗ wV-Tw2.
7. Apply the watermarking with some intensity and getoutputimagewithhelpofIDWT.
8. Save the extracted watermark with the help of imwritecommand.
9. CalculatetheparameterslikeMSE,PSNR,RMSEand CRofwatermarkedimage.
In this section, the performance measures were evaluated and proposed algorithm is evaluated using the available dataset. which are based on the TCGA and _test datasets is presented in this work. The TCGA dataset contains50images,_testdatasetcontains 25images.
S.No Dataset type
Sizeof dataset No.ofimages
1 TCGA 14MB 50
2 Test dataset 6MB 25
Manyofwatermarkingalgorithmsareunabletoprovide better qualityandimperceptibilityoftheimage have been subjected to performancemeasures.Toaddress thisissue, this work is to perform DWT-HD-SVD watermarking by comparingtheperformancemeasuresofthewatermarked image.


The cover image is at the left, at the same time as the watermarkimageisattheright,asshowninfig.5(a).When we apply the watermark embedding to the MRI of brain database all the images arehidden under cover image but earlierthanmakinguseofthewatermarkthepre-processing levelisinvolved.
Asillustratedinfig5(b),theinputimagesarerescaledtoa consistentsize.
International Research Journal of Engineering
Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072

Itistheaveragedvalueofthesquareofthepixel-by-pixel differencebetweentheoriginalimageandstego-imagewhich givesusameasureoftheerrorproducedinthatcoverimage byusingthedataembeddingprocess.
The wavelets are applied to both the input image andthewatermarkedimageafterthepre-processingstage, dividingtheimagesintofoursub-bands:LL-1,LH-1,HL-1, HH-1,LL-2,LH-2,HL-2,andHH-2. Here, theLL sub-bands containingthemostinformation.
As illustrated in fig.5(d) the left image shows the watermarkedimageafterthewatermarkingphasetheimage issubjectedtocompressionandencryption.Theencrypted imagewillbelikeshownintheaboverightmostfigure.
WhereP,Qrepresentstheheightandwidthoftheimage respectively.
•m(i,j)representstheoriginalimagespixel valueand
•n(i,j)representsthepixelvaluesofembeddedimage.
To find the watermarked image’s quality loss in comparison to the original image. The PSNR of an image affectsitsimperceptibility. PSNRiscalculatedbyusingthe formulaasfollows.
PSNR = 10 log10 = (L*L/MSE)
Here,Listhevalueoftheimageheight.For8-bitimage, L=255.Anyimagewithabrightnessofgreaterthan30DBis acceptable in the application of multimedia. In medical imagingthedataqualityisparamount,andPSNRofaround 50Dbindicatesthattheimageisofhighqualityandthatthere hasbeennosignificantdegradationintheimage comparedtotheoriginal.
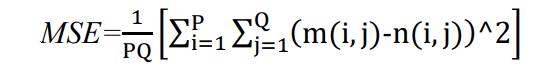
ThesquaredrootofMSEisusedtocalculateRMSE.Itisa metricusedtoindicatehowmuchapixelchangesinmeansof processing. Because RMSE is dependent of scale, it should onlyusetoevaluatethepredictionerrorsofdifferentmodels forasinglevariable,notbetweenthevariables.
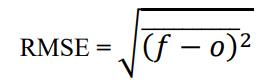
The decrypted image is generated by applying the decryptiontothecompressedimage,asshowninfig.5(e).The extractedwatermarkedimageispresentedontheright.By applying the De-watermarking, the Brain MRI image was retrievedfromthewatermarkedimage.


Somequalityofmeasurescanbeusedtodetermine thedistortioninthewatermarkedimagebycomparingitto theoriginalimage.Thefollowingsectionsarewidelyused.
Where, f=forecasts (unknown results) 0=observed values (knownresults)
The squared root of MSE is used to calculate the Root Mean Square Error (RMSE). The Root Mean Square Error Imagecompressionistheprocessofreducingthesizeofan image file in bytes without sacrificing the images’ quality. Moreimagescanbesavedineachamountofdiscormemory spacebecauseofthesmallerfilesize.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
Where,letn1,n2denotethenumberofbitsintheoriginal andcompressedimages
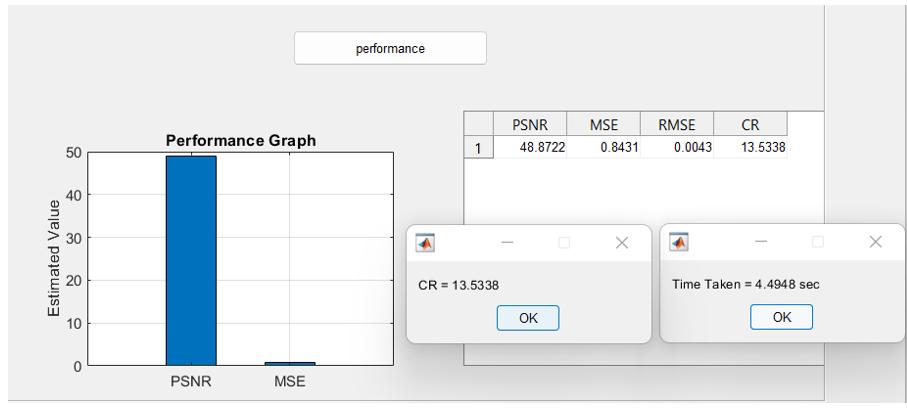
Thisfigureshowstheperformancemeasuresandgraph fortheBrainMRIdatabaseandthetimetakenfortheentire watermarking and de-watermarking is around 5 sec. The encryptedandcompressedimagesarestoredinaseparate folder.
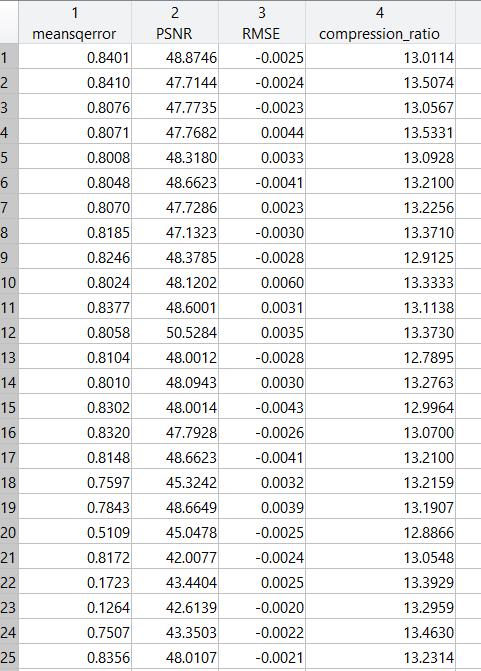
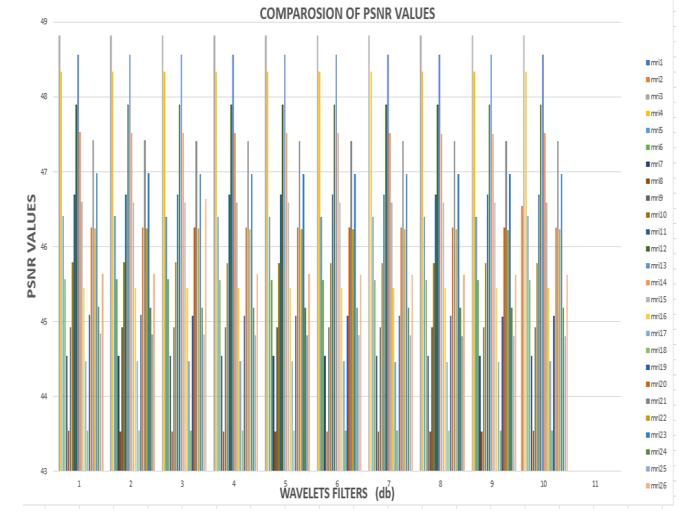
Chart -2: MSEforBrainMRIfordifferenttypesofordersof dBfilters
ThisMSEfigureshowstheresultfortheMSEvaluesofthe Brain MRI dataset for different orders of the Daubechies wavelet filters. The Mean Square Error (MSE) is used to determinethedegradationofimage.
Chart -1: PerformancemetricesfortheBrainMRIDataset usingthedb1waveletfilter
Chart -3: PSNRforbrainMRIfordifferenttypesoforders ofdBwaveletfilters
This figure showsthe results for PSNR values of the Brain MRIdatasetfordifferentordersoftheDaubechieswavelet filters.Todeterminetheimperceptibility,PSNRiscalculated totheextractionofwatermarkedimages.
Inthispaper,theproposedimagewatermarkingsystem is based on DWT-HD-SVD transforms. The invisibility and robustness of this method are analyzed by the numerical simulationtrailsandtheresultsshownthebetterquality.
In addition, the comparison with the related works is listed and the corresponding metric values show that the proposedmethodhasabetterperformancewhichisusedto securetheimagestransferredviatelemedicineasmuchas possible.Theseimagesarewatermarkedwiththepatient’s
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
details to avoid any mistake between the patient’s radiographs. As a result, during the extraction, the doctor willbeabletocheckwithcertaintythatthereportsbelongto thetreatedpatient.
[1] D.Bouslimi,G.Coatrieux,M.Cozic,andC.Roux,“A jointencryption/watermarkingsystemforverifying the reliabilityof medical images,”IEEE Trans. Inf. Technol.Biomed.,vol.16,no.5,pp. 891–899,Sep. 2012.
[2] M.N.A.Wahid,A.Ali,B.Esparham,andM.Marwan, "A comparison of cryptographic algorithms: Des, 3DES,AES,RSA,andblowfishforguessingattacks prevention,"J.Comput.Sci.Appl.Inf.Technol.,vol.3, pp.1–7,Aug.2018.
[3] S.Haddad,G.Coatrieux,A.Moreau-Gaudry,andM. Cozic,"JointWatermarking-Encryption-JPEG-LSfor MedicalImageReliabilityControlinEncryptedand Compressed Domains," in IEEE Transactions on Information Forensics and Security, vol. 15, pp. 2556-2569, 2020, DOI: 10.1109/TIFS.2020.2972159.
[4] Sumedh P. Ingale1, Prof. C. A. Dhote,” Digital Watermarking Algorithm using DWT Technique,” International Journal of Computer Science and MobileComputing,Vol.5Issue.5,May-2016,pg.0109
[5] Sunesh, Vinita Malik, Neeti Sangwan, Sukhdip Sangwan.” Digital Watermarking using DWT-SVD Algorithm,” Advances in Computational Sciences and Technology ISSN 0973-6107 Volume 10, Number7(2017)pp.2161-2171©ResearchIndia Publications
[6] Thakkar, F.N. and Srivastava, V.K., 2017. A blind medical image watermarking: DWT-SVD based robust and secure approach for telemedicine applications. Multimedia Tools and Applications, 76(3),pp.3669-3697.
[7] W. Puech and G. Coatrieux. Chapter 10: Coding: EncryptionWatermarking-CompressionforMedical Information Security. Compression of Biomedical Images and Signals, A. Na¨ıt-Ali and Christine CavaroMenard, Digital Signal Processing, ISTEWiley,May2008.
[8] Puech,W.(2008).[IEEE2008FirstWorkshopson Image Processing Theory, Tools and Applications (IPTA)-Sousse,Tunisia(2008.11.23-2008.11.26)] 2008FirstWorkshopsonImageProcessingTheory,
Tools and Applications - Image Encryption and CompressionforMedicalImageSecurity.,(),1–2. doi:10.1109/ipta.2008.4743800R.Nicole,“Titleof paperwiththeonlyfirstwordcapitalized,”J.Name Stand.Abbrev.,inpress.
[9] S.Haddad,G.Coatrieux,A.Moreau-Gaudry,andM. Cozic,"JointWatermarking-Encryption-JPEG-LSfor MedicalImageReliabilityControlinEncryptedand Compressed Domains," in IEEE Transactions on Information Forensics and Security, vol. 15, pp. 2556-2569, 2020, DOI: 10.1109/TIFS.2020.2972159.
[10] S. P. Metkar and M. V. Lichade, “Digital image securityimprovementbyintegratingwatermarking andencryptiontechnique,”inProc.IEEEInt.Conf. Signal Process., Computer. Control (ISPCC), Sep. 2013,pp.1–6.
[11] Sumedh P. Ingale1, Prof. C. A. Dhote,” Digital Watermarking Algorithm using DWT Technique,” International Journal of Computer Science and MobileComputing,Vol.5Issue.5,May-2016,pg.0109
[12] Sunesh, Vinita Malik, Neeti Sangwan, Sukhdip Sangwan.” Digital Watermarking using DWT-SVD Algorithm,” Advances in Computational Sciences and Technology ISSN 0973-6107 Volume 10, Number7(2017)pp.2161-2171©ResearchIndia Publications
[13] Thakkar, F.N. and Srivastava, V.K., 2017. A blind medical image watermarking: DWT-SVD based robust and secure approach for telemedicine applications. Multimedia Tools and Applications, 76(3),pp.3669-3697.
[14] W. Puech and G. Coatrieux. Chapter 10: Coding: EncryptionWatermarking-CompressionforMedical Information Security. Compression of Biomedical Images and Signals, A. Na¨ıt-Ali and Christine CavaroMenard, Digital Signal Processing, ISTEWiley,May2008.
[15] W. Puech and J.M. Rodrigues. A New CryptoWatermarking Method for Medical Images Safe Transfer.InProc.,12thEuropeanSignalProcessing Conference (EUSIPCO'04), pages 1481–1484, Vienna,Austria,2004.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
