International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
1Student, Department of Software Systems, Vellore Institute of Technology, Tamil Nadu, India 2Student, Department of Analytics, Vellore Institute of Technology, Tamil Nadu, India ***
Abstract – Diffie-Hellman Key Exchange is an exponential key exchange technique which allows two users to exchange a secret key securely. This techniquecanfurtherbeextrapolated for encryption of messages. In this paper, we use RSA to encrypt the Diffie Hellman key exchange, which prevents the possibility of a man-in-the-middle attack and keeps the entire chat truly end-to-end encrypted. A detailed discussion regarding works related to this field and the novelty provided by this work in particular has also been discussed. In addition to the RSA, the AES256 algorithm is also discussed with reference to the Diffie Hellman Key Exchange. A detailed statisticalanalysis witha comparison of all the algorithmshas also been provided.
Key Words: (CipherText,PlainText,Encryption,Decryption, Man-in-the-middle (MITM) attacks, Elliptic curve cryptography
One of the most important developments in public-key cryptographywastheDiffie-Hellmankeyexchange,which isstillusedinavarietyofsecurityprotocolstoday.Itallows two people who have never met before to create a secure keythatthey canusetoencrypttheir communications. In hospitals, the medical records of patients are stored in a highlyconfidentialcloud.However,sometimestheyhaveto besentfromonedepartmenttoanotherorevenfromone hospitaltoanother.Inthisprocessthatdatacanbehacked andcanbecorrupted.Themostcommonmethodologyused to prevent attackers from hacking or getting a hold of a messagewouldbetoencryptthemessagethroughcode.In
suchasituation,ifnoexternalsourcecancrackthecode,the datawillbesafe,butthatcannotbepromisedorfool-proof; what would happen if one can’t arrange for a code beforehand?TheDiffie-Hellmankeyexchangewasthefirst widely utilised solution to this problem. Even over an insecure channel that enemies may be watching, the technique allows persons who have never met before to safelyconstructasharedkey.
Symmetric algorithms, which can be used to encrypt the majority of the data but are less efficient than public key algorithms, are the most effective kind of encryption. Althoughsharingsensitivedata,databreacheshavebecome
morefrequent.Inmanyfields,thishasbeenthecase.Those whodemandhigherdegreesofsecurityyethaven'treceived alotofattention;forinstance:Healthcare.Thegoalofthis projectistoemployblockchaintechnologytoprovidesafe data sharing and communication. The RSA and AES256 encryption methods, as well as the Diffie-Hellman Key Exchange, encrypt messages from end to end. The DiffieHellmankey'smainpurposeistobuildsharedsecretsthat canbeusedtoproducekeyssafely.Thesekeyscanthenbe combinedwithsymmetric-keymethodstosendinformation securely.
Onamathematicallevel,theDiffie-Hellmankeyexchange's security is based on one-way functions. These are calculationsthatarestraightforwardinonedirectionbutfar morecomplicatedintheother.Whileimplementingthiswe are considering the situation where two clients are communicatingwitheachotherandsharingsensitivedata.
EmmanuelBresson,OlivierChevassut,DavidPointchevaetal. [1] observed that the third tier in the treatment of group Diffie-Hellmankeyexchangeutilizingpublic/privatekey.The first tier was created for a scenario in which the group membership is static, while the second was created as an extensionofthefirsttoallowformembershipchanges.The groupDiffie-Hellmankeyexchangeisgivennewfeaturesin thisarticle,includingstrongcorruption,concurrentprotocol executions,tighterreduction,andastandardmodel.
Rewagad, Pawar et al. [2] researched on security of the secrecy of data kept in the cloud by combining digital signatures and Diffie Hellman key exchange with the AdvancedEncryptionStandardencryptiontechnique.Evenif thekeyintransitishacked,theDiffieHellmankeyexchange facilityrendersituseless,becausethekeyintransitisuseless withouttheuser'sprivatekey,whichisonlyaccessiblebythe legitimateuser.Thisproposedthree-waytechniquemakesit difficult forhackers to break thesecuritysystem, securing datastoredinthecloud.Chia-HuiWang,Yu-ShunLiuetal.[3] workedtowardsconsiderablystrongerprivacyprotectionfor anend-to-endVoIPtosignificantlyimproveVoIPsecurityand prevent hostile eavesdroppers. This trustworthy solution uses the Elliptic-Curve Diffie-Hellman algorithm for key negotiation as well as the key generation function for dynamically updating keys during a VoIP conversation
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
session. During the end-to-end call session, this 2-tier key distributiontechniqueprovideseffectiveandrobustsecurity forVoIPvoicepackets.Thisproposedsystemhasbeentested overtheInternetusinganopen-sourceSIP-basedphone
Jin Wook Byun, Dong Hoon Lee et al. [4] focused on two secureN-partyEKEprotocolsinwhichclientscangeneratea common group session key using only their different passwords, and we proved their security using the group computationalDiffie-Hellman,computationalDiffie-Hellman, and3multi-decisionalDiffie-Hellmanassumptions.Designing N-Party EKE protocols in a dynamic environment and provingthemethodsinthestandardassumptioncouldbethe nextstep
RadekFujdiak,PetrBlazeketal. [5]highlighteddifficulties arediscussed,andthreecryptographicencryptionsolutions (AES,ChaCha,andOTP)arecomparedintermsofthecore IoTtriadofperformance,security,andcost.Inareal-world application,westudyencryptiontechniquesandcharacterize theirenergyusage.Thefindingsarevaluableindetermining thecostofenablingsecurityfeaturesandindeterminingthe mostefficientencryptionstrategy.
MohammedRiyadhAbdmeziema,DjamelTandjaouibetal.[6] worked on Particularly resource-intensive cryptographic primitivesarebeingoffloadedtothirdpartiesassuggestedin thepaper.Asaresult,limitednodesenlistthehelpofmore powerfulentitiesinordertocreateasharedsecretwithany remoteentityinasecuremanner.Formalvalidationofour protocol's security attributes in order to evaluate it is performed.Bothcommunicationandprocessingexpensesto see where we might save energy are also looked at. The resultsrevealthatthisapproachsavesasignificantamountof energywhilemaintainingitssecurityfeatures.
Neetesh Saxena, Narendra S. Chaudhariet et al. [7] in the research, EasySMS, an efficient and secure protocol that enablesend-to-endencryptedSMScommunicationbetween end users. The protocol's operation is demonstrated using two separate scenarios. The suggested protocol's study reveals that it can protect against a variety of attacks, including SMS disclosure, over-the-air modification,replay attack,man-in-the-middleassault,andimpersonationattacks.
AvijitMathur,ThomasNewe,WalidElgenaidi,MuzaffarRao, GerardDoolyandDanielToaletal.[8]saidthegoalofthis studyistolookatasecureend-to-endIoTsystem.Itenables wirelesssensors/devicestoconnecttoanyPContheplanet whilemaintainingdataandnetworksecurity.Thestrategy suggested in this paper can defend an IoT solution from a variety of threats, including data breaches, unauthorized access,anddenialofservice(DoS).Thefindingssuggestthat thetechnologiesinstalledoremployedareeffective.When compared to their counterparts in previously published studies, they are superior in terms of time and energy consumption.
Patgiri et al. [9] said that the main goal is to provide the Diffie-Hellman Algorithm with guaranteed security. As a result,privateDHdoesnotsharethedatawiththedesignated partyinapublicmanner.Instead,duringthekeyexchange protocol,privateDHencryptsallshareabledatawiththeAES algorithm.Toavoidaman-in-the-middleattack,privateDH getsthepublickeyusingtheRSAtechnique.Asaresult,how tosecuretheDiffie-Hellmanalgorithmagainstseveraltypes ofpotentialfutureassaultsisshown.
Hasib et al. [10] worked on the fundamental mathematics underpinningtheAESandRSAalgorithms,aswellasabrief discussion of various cryptographic primitives often employedinthefieldofcommunicationsecurity,ispresented inthiswork.Italsocoversmultiplecomputationalchallenges, aswellasaninvestigationofAESandRSAsecurityaspects againstvarioustypesofattacks,aswellascountermeasures.
Onamathematicallevel,theDiffie-Hellmankeyexchange's security is based on one-way functions. These are calculationsthatarestraightforwardinonedirectionbutfar morecomplicatedintheother.
While implementing this we are considering the situation wheretwoclientsarecommunicatingwitheach otherand sharingsensitivedata.Theprocedurefortheproposedmodel isasfollows:
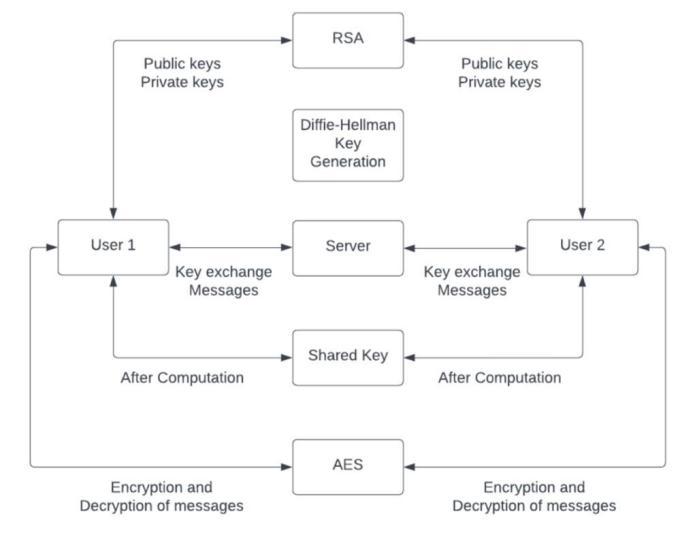
The process starts with the initiation of a server which handles the duty of exchange of messages betweenthetwoclientsinanencryptedway.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
GenerationofDiffieHellmanparameters,generator and prime are done by the server script itself for enhancedencryption.
Identify the applicable funding agencies here. If none,deletethistextbox.
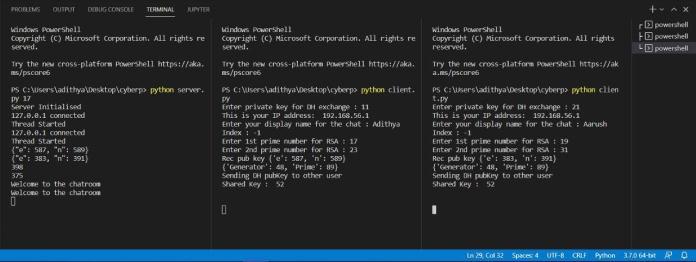
Now,weconnectbothclientstotheserverusingtheserver's IPaddress.Onceconnected,theclientsexchangetheirRSA publickeysandontheotherhand,theservertransmitsthe Diffie-Hellmanparameterstobothclients.Theuserschoosea privatekeyfortheDiffieHellmankeyexchangeandcompute theirrespectivepublickeys.
ThesepublickeysareencryptedusingtheRSApublickeyof theotherusersandareshared.Oncebothclientsreceivethe Diffie-Hellman public keys of the other client, the clients computethefinalsharedkey.Thethusobtainedkeycanbe utilizedforencryptingallcommunicationbetweenthetwo clients.SinceweuseRSAtoencrypttheDiffieHellmankey exchange, wehelp prevent the possibility ofa man-in-themiddle attack and keep the entire chat truly end-to-end encrypted.
Elliptic Curve Cryptography, a technique for performing public-keycryptographybasedonthealgebraicstructureof elliptic curves over finite fields, is the foundation of the algorithm.ThetrapdoorfunctionisusedbytheDHaswell, muchlikemanyothermethodstopublic-keycryptographyis used. The following is a straightforward concept for comprehendingtheDHAlgorithm.
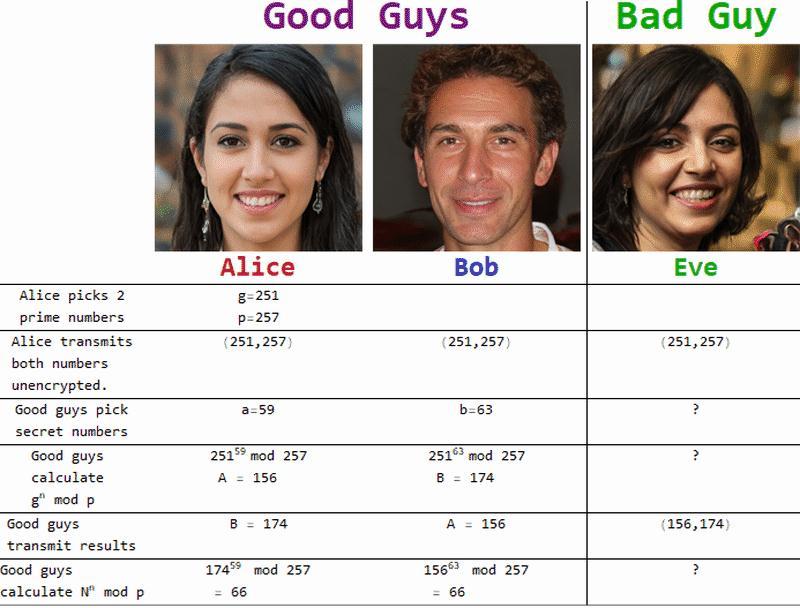
1) The first partychooses the prime numbers gand pand informsthesecondpartyofthem.
2)Thesecondpartythenchoosesasecretnumber(let'scallit a),computesgamodp,andtransmitstheresult calllet'sit result A back to the first party. Remember that just the outcomeisgiventotherecipient;thesecretnumberisnot.
3)Thefirstpartythenfollowssuit,choosingasecretnumber bandcomputingtheresultBinamannerakinto.
4)Thesecondpartyistheninformedofthisoutcome.
5)ThesecondpartycalculatesBamodpusingthereceived valueB.
6) The first party computes Ab mod p using the received numberA.Thesolutiontostep5isthesameastheanswerto step4,whichiswherethingsgetinteresting.Thismeansthat regardless of the sequence of exponentiation, the solution willbethesameforbothparties.
Fig.3:Flowchartfortheproposedsystem
The Diffie-Hellman key exchange, also known as an exponential key exchange, is a technique for digital encryptionthatmakesbreakingcodesstatisticallyimpossible by using numbers raised to particular powers to create decryptionkeysbasedonelementsthatareneverphysically conveyed.
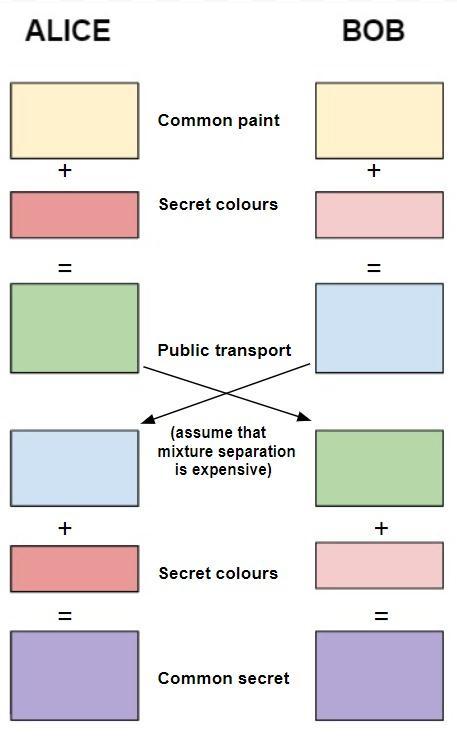
Fig.3Diffie-HellmanKeyExchange
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
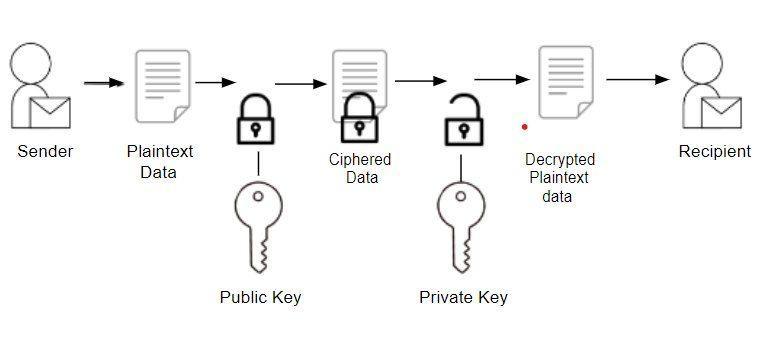
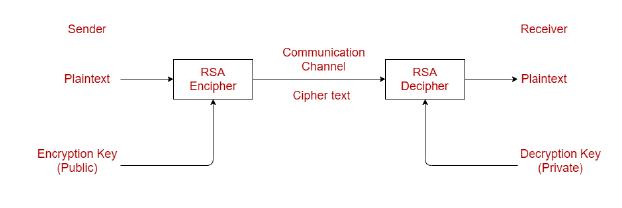
Asymmetric cryptography uses the RSA algorithm. Asymmetricmeansthatitusesboththepublickeyandthe privatekey,whicharetwoseparatekeys.Asimpliedbythe name,theprivatekeyiskeptsecretwhilethepublickeyis distributedtoeveryone.
AESemployssymmetrickeyencryption,whichencryptsand decrypts data using just one secret key. The US National Security Agency has authorised the Advanced Encryption Standardasthefirstandonlypubliclyavailablecypherfor securingtop-secretdata.Eachunitofdataisreplacedwitha different one based on the security key, which is the fundamental tenet of all encryption techniques. AES was createdasasubstitution-permutationnetwork,tobemore precise.AESusesakeyexpansionmechanismthatleverages theinitialkeytogenerateasetofnewkeysknownasround keys, adding additional security. Multiple rounds of modificationareusedtogeneratetheseroundkeys,eachof whichmakesthemmoredifficulttocracktheencryption
Fig.
Actionsrequired:
MAJORGENERATION
1.ChoosePandQ,twoprimenumbers.
2.Determinensuchthatn=P*Q.
3.Determine(n)suchthat(n)=(P-1)(Q-1)
4.Chooseatinyexponentesuchthatitisanintegerandnota factorofn,andthatitsvalueis1e.(n)
5.publickeyis(n,e)
6.Determinedsuchthatitequals(k*(n)+1)/eforsome integerk.
7.Thesecretcodeis(n.d)
ENCRYPTION
Textcypher=pemodn p=plaintext
DECRYPTION
Plaintextisequaltocmodn. c=cyphertext,etc.
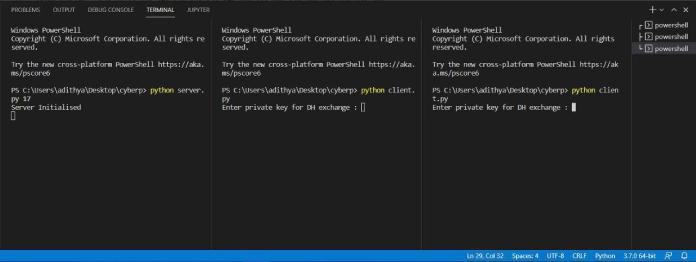
Fig.
Using an XOR cypher, which is an operation pre-built into processorhardware,theinitialkeyisfirstappendedtothe block.Afterthen,eachdatabyteisreplacedwithanewone accordingtoaspecifiedtable.The44array'srowsarethen shifted:thesecondrow'sbytesaremovedonespacetothe left, the third row's bytes are moved two spaces, and the fourthrow'sbytesaremovedthreeplaces.Thefourbytesin eachcolumnarethencombinedbyamathematicalprocess thatmixesthecolumns.Thenextstepistoaddtheroundkey totheblock(justlikethefirstkeydid),andtheprocedureis repeatedforeachround.
Thisresultsinciphertextthatdiffersgreatlyfromplaintext. ThesamemethodisusedinreverseforAESdecryption.The AES encryption method has several stages, each of which performs a crucial task. A far more complex outcome is obtained by using a different key for every round. The relationshipbetweentheoriginalandencryptedcontentis obscuredthroughbytereplacement,anonlinearmodification ofthedata.Dataisdiffusedbymovingtherowsandcolumns around,andencryptionismademoredifficultbybytesbeing switchedaround.Whilemixingdiffusesthedatavertically, shiftingdoessohorizontally.Theendproductisanextremely complexformofencryption.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
Fig.7PrivateKeyExchange Exchangeofmessages
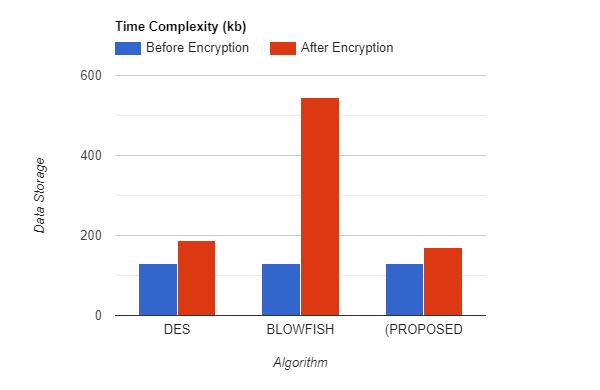
Comparison between DES, Blowfish and the proposed algorithmisdoneontermsofthespaceoccupiedbeforeand afterencryption.
Fig.8Exchangeofmessages
Comparison between the standard RSA algorithm run timeandtheruntimeofthreadsintheproposedalgorithm hasbeendone.
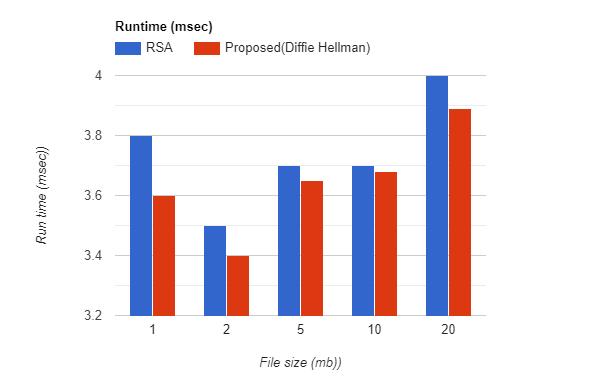
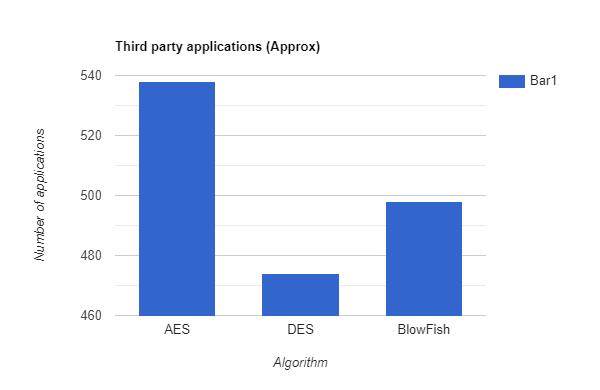
Our proposed algorithm does not use any third party applications and hence reduces the time and space complexity.
This paper presents a proposed solution of using RSA algorithmtoencryptDilleHellmanKey-Exchange.Wealso compared the runtime complexity of the standard RSA algorithmwithourproposedsolutionandwefoundthatthe proposed solution has a better runtime complexity. Our proposed solution is also most efficient in space-time complexity. Since our proposed solution does not use any third-party applications, it reduces the time and space complexity. Our future work will explore more on this conceptandwewillapplymorealgorithmsinasequentialor parallelwaytoensuresecureenvironmentfordatastorage.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
[1] [1] Nan Li, "Research on Diffie-Hellman key exchange protocol," 2010 2nd International Conference on Computer Engineering and Technology, 2010, pp. V4634-V4-637,doi:10.1109/ICCET.2010.5485276
[2] Bresson, E., Chevassut, O., & Pointcheval, D. (2001, December). Provably authenticated group DiffieHellman key exchange the dynamic case. In InternationalConferenceontheTheoryandApplication ofCryptologyandInformationSecurity(pp.290-309). Springer,Berlin,Heidelberg.ComputerEngineeringand Technology,2010,pp.
[3] Wiener,M.J.(1990).CryptanalysisofshortRSAsecret exponents. IEEE Transactions on Information theory, 36(3),553-558..
[4] Boneh, D.(1999).Twentyyearsof attacksonthe RSA cryptosystem.NoticesoftheAMS,46(2),203-213.
[5] Kocher, P. C. (1996, August). Timing attacks on implementationsofDiffie-Hellman,RSA,DSS,andother systems.InAnnualInternationalCryptologyConference (pp.104-113).Springer,Berlin,Heidelberg
[6] Boneh,D.,&Franklin,M.(1997).Efficientgenerationof shared RSA keys. In Annual international cryptology conference(pp.425-439).Springer,Berlin,Heidelberg.
[7] Biryukov, A., Khovratovich, D., & Nikolić, I. (2009, August).Distinguisherandrelated-keyattackonthefull AES-256.InAnnualInternationalCryptologyConference (pp.231-249).Springer,Berlin,Heidelberg.
[8] AlHasib,A.,&Haque,A.A.M.M.(2008,November).A comparative study of the performance and security issues of AES and RSA cryptography. In 2008 third international conference on convergence and hybrid informationtechnology(Vol.2,pp.505-510).IEEE.
[9] Kumar, B. S., Raj, V. R., & Nair, A. (2017, April). Comparative study on AES and RSA algorithm for medical images. In 2017 international conference on communication and signal processing (ICCSP) (pp. 0501-0504).IEEE.
[10] Boneh, D.(1999).Twentyyearsof attacksontheRSA cryptosystem.NoticesoftheAMS,46(2),203-213.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal
