International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
Standardized identification wound up fundamental components in deals and items benefits because of significance of tracking all things in on spot. For this reason, there are numerous strategies actualized to make the standardized tag perusingprocedurewoundupsimplertoclients.Thisventureistobuildupastandardizedidentificationacknowledgment frameworkbyutilizingpicturepreparing.Theframeworkwillhavetheoptiontoperusescannertagthroughapictureand theframeworkabletocatchthepicturebyutilizingawebcam.This taskwillutilizePythonprogrammingprojecttobuild up the framework and it will incorporate with webcam or computerized camera. Framework will investigate the picture and after that show on the Graphical User Interface (GUI) the scanner tag type, information and size of the picture. Framework is intended to perceive various sorts of standardized tag and show the information once the scanner tag picture is caught. Framework additionally is to give comfort method for watching information from the standardized identification with lower costing looked at by utilizing the electronic standardized tag scanners. This frameworkcan be utilized whenever and anyplace by the client who likes to watch the information spoken to by the standardized identificationnumberswithoutgoinganyspotsgivingthescannertagscanneradministrations.
As the outcome, the undertaking has been grown easily and superbly. For the future framework improvement, it is recommended that the framework likewise should comprise aslider with the goal that the client would ready to control thebrillianceofthepicturewhichcaughtbywebcam.SpeedyResponse(QR)codesaretwo-dimensionalscannertagsthat canbeutilizedtoproficientlystoremodestquantityofinformation.
Theyareprogressivelyutilizedinalllifefields,particularlywiththewidespreadofadvancedcellswhichareutilizedasQR code scanners. While QR codes have numerous preferences that make them famous, there are a few security issues and dangersthatarerelatedwiththem.Runningvindictivecode,takingclients'touchydataanddamagingtheirprotectionand wholesale fraud are some ordinary security chances that a client may be liableto out of sight while he/she is simply perusingtheQRcodeinthecloserview.Inthispaper,asecurityframeworkforQRcodesthatensuresthetwoclientsand generators security concerns is executed. The framework is in reverse good with current standard utilized for encoding QRcodes.TheframeworkisactualizedandtriedutilizinganAndroid-basedcellphoneapplication.Itwasdiscoveredthat theframeworkpresentssomewhatoverheadasfarasthedeferrequiredforhonestycheckandsubstanceapproval.
Key words:QRcode,Python,GUI,tagscanner,Android
Standardized tag is a visual portrayal of data as bars and spaces on a surface. The bars and spaces are structured with various widths and comprise of numbers, characters and images,for example, spot, colon and others. Various mixes of thesealphanumericcharactersareutilizedtospeaktodata.Therearedifferentsortsofscannertagsbeingusedtodayfor exampleCode128,Code39,EANandsoforth (Mind,2000).
Thefruitfulofscannertaginnovationhasbeencontinuallyimprovingsoastosuitmoredatainthebaseconceivablespace. Todayscannertagsaregenerallyutilizedonbooksandatretaillocationssoastomonitortheitemsaccessibleandsimple checkoutoftheitems.Thestandardizedtagsareregularlyperusedutilizingscannersutilizinglaserpillarsorcameras.
Byandlarge,standardizedtagsareimagesmoldedassquareshapeswhichcompriseofslim orthickparallellinesparallel to one another. Standardized tags give intends to programmed fast information contribution to the PC. Since the most recentdecade,scannertagsarebeingutilizedinnumerousterritories,forexample,showcaseitemsandelectronicgadgets. Thelines onscannertags containthereferencenumber oftheitem. Thisdataought toberecordedinPCstostoreevery item independently for checking organization deals and buy amounts. When perusing standardized identifications on itemsutilizingsomelasercheckinggadget,asignisproducedbytheframeworkandpreparedinthePCbyprogramming. Atthatpointthisdataisutilizedtofigureoutwhichitemischosen.Thisproceduregivesfastanddependabledealschances toorganizationsforsellingtheiritems.Thereareafewsortsof scannertagthatbeingutilizedinsidethemechanicalfield these days. A standardized identification symbology characterizes the specialized subtleties of a specific sort of scanner tag incorporates width of bars, character set, strategy for encoding and checksum determinations. Standardized
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
identificationtypescanbegroupedintofourkindof classificationandthoseclassesarenumeric-justscannertags,alphanumericstandardizedtags,2Dstandardizedidentificationandindustrystandardforstandardizedtagandmarks.
As in picture preparing, the thresholding is the one of component to be consider as an approach to portray a picture. Thresholdingistheleastcomplextechniqueforpicturedivision.Fromagrayscalepicture,thresholdingcanbeutilizedto make double pictures. During the thresholding procedure, singular pixels in a picture are set apart as item pixels if the worthismoreprominentthansomeedgeesteem(acceptinganarticletobemorebrilliantthanthefoundation)andasthe foundationpixelsgenerally.Thisshowisknownasedge above.Variationsincorporatelimitunderneath,whichisinverse ofedgeabove;edgeinside,whereapixelismarked"object"ifitsworthis betweentwoedges;andedgeoutside,which is somethingcontrarytoedgeinside.Normally,anarticlepixelisgivenanestimationof"1" whileafoundationpixelisgiven an estimation of "0." Finally, a twofold picture is made by shading every pixel white or dark, contingent upon a pixel's mark.
15th
30, 2018.
Automaton helped stock administration is alluring for organizations with enormous distribution centers and industrial facilities. Moreover, there is an enthusiasm for a novel strategy that consequently recognizes target standardized tags utilizing an IR-based camera, which empowers productive automaton way arranging and results in diminishingforce utilization.Inthispaper, weproposeaproficientrecognitionstructurewhichdecidestherestrictionsof2Dstandardized tags. Numerous territorial recommendations of2D standardized identifications are diminished to a couple of up-andcomerareasasper theseparationdata betweentheautomatonandtheobjective2Dscannertag.Visual highlightsofthe chose competitor areas are extricated by LBP and HOG strategies, separately. To pick up discriminant control for characterization, SVM is utilized toward thepartofthe bargain. Thelastdiscovery area is dictated by a total based score combinationtechniquethatisweighted.Toapprovethepresentationofthisstrategy,wegather2dimensionalscannertag picturesundergenuinedistributioncenterconditionsandacquirebroadtestresults.
Theboundlessutilizationofautomatonshasfundamentallyaddedtonumerous applicationsfromcharacteristicassetthe executives, air contamination checking, distribution center stock administration, and so forth. Among them, we have an enthusiasmforanautomatonbasedadministrationarrangementintendedtocomputerizestocktakingandstockcontrolin enormous scaled distribution centers. It has numerous alluring highlights contrasted and the unmanned ground vehicle (UGV)asofnowinactivity.Forinstance,itisn'timportanttocreatenewstreetlinesforanUGVwhenthecapacityareais altered in the distribution center and street line is lacking since it has been exhausted in light of the numerous UGV developments.Besides,extrahardwareisn'trequiredtofindanobjectivethingfoundinsometallshelf.Anautomatonhas itsveryowncameragadgetsanditgetsaroundthedistributioncenterautonomouslyasperapreordainedflightintendto catchtheimportantdataonbeds.Initially,weselectthebestdistrictcompetitorsutilizingaparticularinquirystrategyand separatethenotablehighlightsfromtheup-and-comers.Towardtheend,thearrangementresultiscontrolledbyastraight SVMforaquickestimation
Inthispapera framework is proposed thatutilizationsthreestages,area up-and-comer identification,include extraction, and SVM grouping, for standardized identification location and acknowledgment in production line stockrooms. We connectedacomponentcalculationtofoursortsof2Dstandardizedtagsandestimatedthepresentationbylookingatthe accuracy and learning review by highlight. Furthermore, we additionally improved execution by means of a late combination of the outcomes from different highlights. The proposed technique shows an exactness of 98.08% and a reviewof98.27%.
B. A self-powered 2D barcode recognition system based on sliding mode triboelectric nanogenerator for personal identification Jie Chen, Xianjie Pu, Hengyu Guo, Qian Tang, Li Feng, Xue Wang, Chenguo Hu, 11 November 2017
Triboelectric nanogenerator (TENG) for creating self-controlled individual distinguishing proof framework displays extraordinarypointsofinterest,bethatasitmay,afewissues (swipingspeed,soundness,andsoon.)inthepastresearch
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
work counteract this sort of standardized identification framework for future work. Thus, here, we plan a triboelectric basedscannertagacknowledgmentframework(T-BS)fordowntoearthapplications.Byutilizingareferencescannertag part, the yield signal under arbitrary swiping movement can be effectively perceived, which offers a phenomenal procedurefor thearrangement of theissues inthe past work. Throughthecombinationoflimit esteem, stage distinction andcrestlooking,theyieldvoltagesignofthegadgetcanbechangedintocomputerizedsignals"1"or"0",andthedatacan be continuous shown on LabVIEW stage. When a card is swiped at a consistent speed, or non-steady speedby human hands,thecodeddatacanbeeffectivelyrecognizedandtheentrancecontrolframeworkworksprecisely.Additionally,by expandingthequantitiesofstandardizedidentificationsectionsalso,minifyingthesize,progressivelyexact2Dscannertag acknowledgment framework (counting scanner tag and peruser) is gotten and understood the individual recognizable proof. This exhibits the probability of the TENG as a self-fueled 2D standardized identification acknowledgment frameworkforindividualrecognizableproof,whichshowspotentialapplicationsindatasecurity
Keywords:2Dbarcode,triboelectricnanogenerator,self-powered,recognitionsystem,personalidentification
Lately, with the fast advancement of web of things (IOTs), individual data recognizable proof innovation has turned into theextremelyessentialandthemostsignificantconnectionofdifferentadministrations.Alongtheselines,endeavorshave been given to the improvement of sheltered and solid individual data security framework [1-3]. Amongthe present advances, a one-dimensional or two-dimensional standardized identification [7, 8] is the most well-known and broadly utilizedmethodologyfordatatransporter.Inanycase,alargeportionofthemareessentiallycodedbyseparatingthegame planofspaceswhat'smore,barsandrequireanoutsidepowersupply.wehave exhibitedaself-fueledtriboelectricbased 2D standardized tag acknowledgment framework for individual recognizable proof. With the presentation of a reference standardized tag part, the coded data of data scanner tag under irregular swiping movement can be precisely perceived, whichpresentsanincredibleanswerforthesignificantdisadvantageexistinginthepastwork.Throughthedetermination ofedgeworthandstagecontrast,theexactnessofpinnacleisincrediblyimproved.
The yield sign of the gadget can be changed over into computerized signals "1" or "0", and the coded data is shown progressively. At the point when a card is swiped at steady speed, or non-steady slidingrate by human hands, the coded data can be effectively distinguished and the entrance control framework works precisely. Besides, by improving the segments of standardized identification and minifying the size, increasingly exact 2D scanner tag is acquired and a lot moresecureindividualdistinguishingproofframeworkisaccomplished.Thisworkshowstheprobabilityofselffueled2D scannertagframeworkdependentontheTENGtoacknowledgeindividualID,whichshowspotentialapplicationsindata security.
Thelocationof1Dstandardizedidentificationfromfoggy,lowdifferenceandlowgoals picturesisasyeta difficultissue. 1Dstandardizedtagsarecomprisedbyvariousbars.Inthiswork,anotherbarrecognitionstrategy(BDM)isproducedfor precise and quick 1D standardized tag identification. The least square technique is acquainted with decide precisely the direction of the distinguished bars. Two likelihood thickness capacities (PDF)of the direction and length of bars are utilizedandconnectedtothedistinguishedbarssoastodecidethepredominantdirectionandlengthofthecurrentbars. Atlast,theHoughchange(HT)isconnectedthroughtheserecognizedcentroidsofthebars,soastothebarsthatarebyone another, and lie on a similar line bolster which compares to the scanner tag direction. Fantastic outcomes were accomplished on still pictures from two one dimensional standardized identification datasets: WWU Muenster Barcode Database and ArTe-Lab 1D Medium Barcode Dataset. Exploratory outcomes demonstrate that our calculation can get better 1D standardized identification location contrasted and existing techniques. They demonstrate that the capacity of themodel yieldapplicableandpowerful scannertagrecognition evenwithlowgoalsandobscuredoutlines,and forbent standardizedtags.
1Dbarcodedetection,orientationestimation,leastsquaremethod,Houghtransform
Our primarythoughtistofollowthe bars in itempictureso astoidentify the 1Dscanner tag.In thispaper we utilizean alternatemethodologydependentonseparating, binarization,externalformrecognition,barsdiscoverywithBDM,LSfor bars directions,overwhelming bars direction estimation ( d) with the first PDF, predominant bars length estimation (ld) with the second PDF and Hough change through just the prevailing bars direction ( d+90°) which means our work is preciseand exceptionallyquick,andsuitsforongoingapplication.Theproposed identificationstrategydependsbasically ontheeightprinciplesteps,performedsuccessively.Theinformationpictureoftheframeworkspeakstoexternalshapesof

e-ISSN:2395-0056
Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
the caught scene. This picture is gotten in the wake of preprocessing, where the sifting, binarization and form identification are guaranteed by Gaussian separating, nearby binarisation technique and outskirt following calculation separately.Wehavedisplayeda1Dstandardizedtagrecognitionstrategyconnectedtopicturesfromtwodatabasesandto picturesfrom Webcamgadget. This particular technique and framework not exclusivelycan recognizestandardized tags incomplex sceneyetinadditionitcandistinguishobscuredscannertagsbecauseofunfocused Webcam.Ourframework canworkprogressivelybecauseofitsfast,andcanprocessapicturein21ms.Trialswereledongenuinepicturesofitems, with a low goals and a poorfocal point of the Webcam. We show exploratory outcomes that demonstrate a high accomplishment on particular databases, namely, the WWU Muenster and Arte-Lab 1D standardized identification, contrasting and the current strategies. These outcomes demonstrate the power of the proposed strategy. We show likewise that the BDM is thickness subordinate, the more the bar is meager and the more its discovery is obvious. The proposedtechniquedemonstrates100%precisioncontinuouslyapplications.
Standardized tags are widely utilized in stock administration to distinguish and follow items and segments. While the current pervasive technique for perusing standardized tagswith handheld scanner tag perusers is reasonable for retail checkout paths and little scale stock administration, it presents noteworthy work effectiveness and specialist wellbeing challenges for enormous scale stock administration where items are typically put away onmultistory racks in huge distributioncentersorstorerooms. Suchofficespresent noteworthychancestoimprovecoordinationsvia robotizingthe stockadministrationprocess.Tostraightforwardnessstockfollowingwhileatthesametimealleviatingthedistinguished issues,thisexplorationexploitsPCvisionbasedscannertagperuserstosupplantconventionalstandardizedidentification perusersandproposesthreemethodstoencouragestandardizedidentificationextractionfromvideofilterinformation.In the firstplace, Harris corner identifier and Hough change are proposed to work as one to evaluatethe bearing of an area includingasolitarystandardizedtagandpivotittoaperfectstatetoserveexistingunravelingcalculations.Atthatpoint,a calculation dependent on scanner tag locale network and geometry property is proposed to discover different standardized tags in a solitary picture to maintain a strategic distance from animal power looking of substantial standardizedidentifications.What'smore,ahistogramdistinction basedkeycasingchoicetechniqueislikewiseproposed towipeout excessdata between consecutiveoutlineswhichimproves proficiencybyutilizinglessoutlines.At last,these systemsareconnectedtovideoinformationgatheredinahugecoordinationsdistributioncenterandthegeneralexecution isassessed.The exploratory outcomesdemonstratethat ourcalculationcanaccomplish bothattractiveacknowledgment rates and productivity, and along these lines offers huge guarantee for wide organization in robotized huge scalestock administrationutilizingearthlyandetherealmechanicalstages.
Organization of scanner tag frameworks in stockrooms and dispersion focuses has essentially improved stock administration by permitting exact stock following and highwork effectiveness. Be that as it may, directors still face challenges in admirably using stockroom assets because of genuine insufficiencies in exceptional stock data. Such enormousdataslacksarefundamentallybroughtaboutbythecurrentpredominanthoweverwastefulmethodforfiltering standardizedtags witha normal(forscannertagsatlowplaces)mountedonaforklift(forstandardizedidentificationsat highputs)standardizedidentificationscannersasappearedinFigure1.Whileperusingstandardizedidentificationswitha scanner tag scanner, standardized identifications should consistently be examined individually, requiring huge human exertion and work everyone esaeantial entrance herewalks to finish enormous scale filtering assignments in huge distribution centers. Furthermore, specialistwellbeing is another issue generally experienced while utilizing substantial forkliftsforsuchreason.Generaltechniquesforperusingstandardizedidentificationsfrompictures dependonperceiving thedoubledesignsalongscanlineswhichcrossthescannertags.
Monitoring a standardized identification's direction enormously decreases number of scanlines and increment the possibilityofeffectivereadwhichcanfurtherimproveperusingeffectivenessandexactness.ThispaperproposedthreePC visionbasedmethodstoencouragescannertagextractionfromvideocheckinformation.Investigationsled utilizingvideo gathered at a functioning distribution center demonstrate that the calculation parts work viably to peruse out and extricate most of the area (i.e., cell) distinguishing standardized identifications powerfully. Another essentialness of this workisthat every one of the three procedures examined above don't utilize explicit data from different advances, which make them simple to consolidate with different calculations or computational grouping. These qualities increment the possibilities of their wide application, despite the fact that some specialized difficulties still stay before their viable attainability.Theprimaryconstraintissomehuman exertionis asyetrequiredfor setting properlimitswhich canprofit bybeingmechanized.
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
Tesseract-OCR, 2017 3rd IEEE International Conference on Computer and CommunicationsGang
Luyu Lin, Yawen Chen, Shan Liu, Jie Chu, ZhuoranLuo
Withtheconsistentimprovementofdatainnovation,theutilizationsofstandardizedtaghaveturnedouttobeincreasingly morebroadly,anditsqualitynecessitiesareadditionallyexpanding.Becauseofthedestitutionhardwareforprintingetc., and the defective printing innovation, there are a number of issues, for example, flying ink, missing characters, basic errors,darkspotsandinappropriateenlistmentexistingduringthetimespentstandardizedtagprinting.Theconventional methodfor physicallyarranging flawedstandardizedidentificationisn'tjustwastefulyetinadditioneffectivelyimpacted bynumerouscomponents,whichpromptsthelowexactnessoftherecognition.Soastotakecareoftheseissues,thispaper proposes a technique for standardized tag deformityrecognition dependent on Tesseract-OCR, initially, the strategy utilizes the level projection strategy to fragment the scanner tag, and after that it utilizes the Tesseract OCR strategyto perceivethecharactersinthescannertag,inconclusion,itconsolidates
Levenshtein Distance calculation to identify the character misses. In this paper, 1000 standardized tag pictures were utilized to the investigation, and the and the results show that the precision of recognition results can arrive at 94.3%, whichdemonstratesthepossibilityofthestrategy.
Keywords-Tesseract-OCR; defect detection; barcode; horizontal projection method Problem Statement+Methodology+ExpectedOutput
As the recognizable proof characteristic of ware, scanner tag has significant research hugeness for programmed ID of merchandisedata,programmedarrangingandcannydeal,andsoforth[1].Bethatasitmay,inlightofthetypographythat ispoor,lowprecisionofthehardwareandtheblemishedprintingadvancements,thereareatonofinquiries,forexample, flyingink, characters missing, wrong print, dark spots and ill-advised enrollment during the time spent standardized identificationprinting.ConventionalstrategiesforphysicallyarranginginadequatescannertagsrequireatonofHR,which arewasteful,yetinadditionexistingemotionalelements,thatenormouslyinfluencestheexactnessoftheidentification.As thestandardizedtagisnotquitethesameasthecommonprints,atotalscannertagcanbeisolatedintotworegions,the characterzoneandtherealisticidentifierzone,whichareremarkableinastandardizedtag.Theparallel preprocessingof the standardized tag picture in the location procedure is to feature the qualities of the scanner tag characters. In the doubleprocedure,thelimitispickedbythebiggestinterclassfluctuationtechnique(Otsu).Thekeyadvanceinrecognizing the deformities ofthe characters in a standardized tag is to distinguish the characters in the scanner tag. So as to evade each test to change the layout and to precisely find the area of the imperfection, and make the exactness of ID more accurate,theevenprojectionstrategyisutilizedtoportionthestandardizedtag.Here,astrategydependentonTesseractOCR character deformity recognition is put forth to take care of the issue of tedious and relentless in the customary method for standardized identification character imperfectionlocation. By utilizing the holes between every line in the standardizedtag,the flatprojectioncalculationis utilized tofragment thescannertag.Atthatpoint theTesseractOCRis utilized to differentiate and identify the characters in the divided picture. At last, the Levenshtein Distancecalculationis utilizedtoidentifythecharacterabsconds.Thetrialresultsdemonstratethattheexactnessofthetechniqueis94.3%.The strategy has high acknowledgment exactness and quick speed, which demonstrates the plausibility of scanner tag character imperfection discovery dependent on Tesseract-OCR. Be that as itmay, the test set that is used here is constrained and less quantity of test pictures are prepared by the Tesseract-OCR character for be satisfactory. Subsequently,therelocationofthecharacterlibrarymightbepoor,andtheexactnessofthedeformitydiscoverymightbe influencedbyotherscannertagcharacters,soextendingthequantityofstandardizedidentificationtestsisthepurposeof ournextexamination.
06 Issue: 1 | Jan 2019
In perspective on the significance of understudies' participation at talks and their effect on their scholastic accomplishment, colleges take the vital measures to lessen inordinate truancy. This is an exceptionally significant issue. The organization requires cautious development, dealing with it and not being indulgent. Right now, names of the understudies are called to mark participation and nonappearance at the colleges or by marking the understudy's participationpaper.DuringthetimespentconcedingunderstudiesintoanassessmentlobbyinmostKSAcolleges,85%of
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
participationmustbe fulfilledandfurthermoreconsideredforevaluationcalculation,consequentlythereisan enormous requirement for observing and recording understudies' participation. The purposeof this project is to structure and executeascannertagbasedunderstudyparticipationframeworkthatcanbeeffectivelygottentobythespeakers,toassist them with avoiding keeping up the library book, giving important data about the understudies and the reports can be created utilizing constant handling. The work here was planned and executed utilizing the Unified Modeling Language (UML),MicrosoftAccess2007andASP.NETprogramminglanguage.
Key Words:AttendanceManagement,BarcodeScanner,UnifiedModelingLanguage.
Itisverifiabletruththatforallintentsandpurposesallassociationswhetherinstructiveorbusinessneedtoappropriately record the participation of its understudies or workers for successful arranging, the executives and working of the association. In many colleges in the creating nations, understudy's participation is normally adopted by old record frameworkstrategysuchascallingtheirnamestocheckandutilizingpaper,this methodologyisbeingutilizedforquitea while. As indicated by Tabassam, et al., in It ends up being troublesome for the organization at the colleges to normally refreshtheparticipationrecordandphysicallyascertainthelevelofclassesnotattendedandwenttowiththeendgoalof ensuingoutcomeshandlingandassessments.Rememberingtheseissues,thiswork plannedandexecutedaframeworkto beat the issues related with participation recording. Through our perception of the present framework we found numerous issues, including the huge lack of precision of the customary participation frameworks and the plausibility of understudiestorecordtheirpartnerspresentwhentheyarenotpresent,andthetimelostinthisactivitytocallthenames of understudies to gauge participation, and the trouble of techniques togather reasons of nonappearance, and to raise pardons,Theaccompanyinginquiries:
1. Whatadvantagescanbeaccomplishedbyapplyingelectronicparticipationtounderstudiesincolleges?
2. What is the effect of utilizing the electronic participation application on the instructive procedure of the understudies?
3. Whataretheoutcomestobeaccomplishedthroughtheuseofelectronicparticipationincolleges?
4. Bywhatmeanscanemployeesandunderstudiesacknowledgethetechniqueforapplyingelectronicparticipation?
Theprocedureofframeworkexaminationexpectstoponderacurrentframework tocompletelyplananotherframework. Frameworkinvestigationisperformedtoaccomplishfundamentallytwopointstobespecific:
1. Tocomprehendtheprocedureortheframeworkunmistakably.Thiswillaidthenewframeworkplan.
2. System investigation will distinguish the issues in the current framework; consequentlythis will realize the wastefulnessreasons.
The Unified Modeling Language (UML) is representation for the framework plan, it speaks to graphical documentations which help to portray and structure programming frameworks,primarily programming frameworks built using the item arrangedstyle.The
UMLwasusedforthemostparttostructuretheframeworkbeingproposed.TheUse-CaseoutlineandtheClasschartare tended to beneath. Automating homeroom participation following has numerous focal points over the old framework. Information from homeroomscan without much of a stretch be changed inside the databases for conceivable later examinationoruses.Thisworkstructuredandexecutedascannertagbasedunderstudy participationframeworkthatcan be easily utilized by the speakers without issue, help the instructors to abstain from keeping up the library book, giving profitable data about the understudies and the reports can be produced utilizing continuous preparing. The proposed framework was structured and executed utilizing the Unified Modeling Language(UML), Microsoft Access 2007 and ASP.NET programming language. This particular framework will likewise help in creating the defaulters list individually andsendmessagestothoseunderstudiesthathavelesserparticipationthanisrequired.
Rama Rani, Gaurav Deep. 4th IEEE International Conference on Signal Processing, Computing and Control(ISPCC 2k17), sep21- 23, 2017, Solan, India.
Steganography is a method of disguising private data in a spread medium so that it ends upoutlandish for the third individualtocometorealizethatsomesecretdataispresentinthespreadenvelope.Inthepresenttimewiththeoriginof new rising advances, standardized identifications has turned out to be one of the most prevalent strategies to give an
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
instrument to securing delicate information.3D scanner tags are utilized to suit high information rates by utilizing third measurement as a shading. 3D standardized tagsfills in as the most dependable procedure to shroud information since they don't utilize any blunder revision levels because of the fact that it is exceptionally hard to modify or change the encodeddata.Here,theideaandprocedureofinformationcoveringupinstandardized identificationsbyutilizingshading as thirdmeasurement is presented. The procedureis arrangedintovarious classes and execution is assessed by utilizing differentmeasurableparameters.
Keywords - Steganography; Quick Response code; Cover channel; Stego channel; PSNR; MSE, with the origin of new correspondence ways, the requirement for giving security to thesecret information on the web is continuing expanding step bystep. There exists variousdataconcealingapplicationssuchaswatermarking,fingerprinting,copyrightinsurance foradvancedmediaandsteganography.Steganographygivesawaytosecuredcomposing.
Joining cryptography and steganography together results into a larger amount of data protectionand security. Advanced picturesfillsinasthemostfamousdataconveysforinsertingencodeddataduetotheirexpandedutilizationontheweb. In today 'universe of systemcorrespondence, for the need of more secure methods, information can be disguised in 3D Barcodepictures.3Dscannertagsarenormallyspokentobyutilizingshadingasathirdmeasurement.3DBarcodeageand insertingstage,3DBarcodeextractionstage.Inthis paper, weexhibitedanotherstrategyfordisguisinginformationatall hugebitsofahued3Dstandardizedtagpicture.Thestrategyutilized,firstseparatesredsegmentofthepicturedependent onsomekeyworth.ThemysterypictureischangedoverintoencodedmessagebyutilizingXORencryptioncalculation.At that point the least noteworthy bits ofthe separated parts are supplanted with the least critical bits of the content to be hidden.
The methodology utilizes basic LSB (Least critical Bit) Method. The proposed plan keeps up the nature of stego picture with a normal pinnacle sign to clamor proportion of 87.93 and Mean Square Error of 1.078 and structure closeness list matrixof 0.999. The proposed plan expands the nature of stego picture and furthermore builds the inserting limit of 3D huedBarcodepictures.Intheforeseeablefuturethismethodologycanbebetteredbyutilizingafewadvancingcalculations forupgradingtheinsertinglimitand natureof stegopicturewithless contortionin thepicture.Afewmystery messages canlikewisebedisguisedinasolitaryspreadpicture.
This paper accentuates the standardized identification innovation for programmed Electronic Toll Collection (ETC) frameworks, so as to stay away from the regularly expanding stream of traffic and the long lines at the tollbooths of the expressways. The proposed strategies utilize computerized picture handling methods to check the scanner tag and to coordinate it with the current database, by using the decoded information. The actualized equipment arrangement has beenshownandtalkedaboutindetail.The proposedsystemforstandardizedtagidentificationreallyimprovesuponthe speed,the efficiencyandbringsdowntheexpenseof execution.Thetechniquehasbeen executed byutilizingPythonand OpenCV.
Barcode:QRcode,RFIDtag,ETC,Tollbooth
TheElectronicTollCollection(ETC)frameworkwascreatedsoastodefeattheissues relatedwiththemanualgatheringof thetoll.The manual toll conclusionframework has been supplanted bythe computerized framework, soasto stayaway from issues of long lines and blocked traffic. The computerized ETC framework enables the client to maintaina strategic distance from the hang tight for installment of money or for gathering of token so as to cross the toll. The programmed framework collects toll electronically through the use ofRFID, standardized tag innovation, laser innovation, and so on. WithhigherefficiencythantheRIFDandthelaser,thestandardizedtaginnovationistalkedaboutindetail.Aparalleldark bars and void areas arrangement of differing widths establishes a standardized identification. The components of a scanner tag are the spaces and the bars. Various characters are spoken to by the various mixes of spaces and bars, for example,numbersorletters.Therobotizedframeworkworksquickerandallthemoreefficiently.Itisfitfordecidingthe enlistmentstatusofavehicleandadvisingexpertsregardinginfringementininstallmentoftollandeducatingproprietor bymeansofemailorSMSoftheareaandtheconcludedtollforavehicle.Thegoalofthisinnovationistokeeptollbooths fromgettingtobeclogbyavehicleline.Itencouragesthelegislaturetokeepupanappropriateandarefreshedrecordof the accumulation of toll. There can be a tag introduced to the front plate of the vehicle for this. This paper principally centersaroundthestandardizedidentificationrecognition calculationusedtogettheidealworkingefficiency.IdeasofAI alongsideanIDEdomainofPythonandOpenCVhavebeenutilizedsoastogettheworkingmodel.Animaginggadgetlike a camera wasutilized for the proper discovery of the scanner tag. The standardized tag to be examined. It stores the
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
financial balance subtleties, portable number and Aadhaar card subtleties of the vehicleproprietor. In the exploration articlestandardizedidentificationrecognitionforETC frameworkshasbeenproposed.Thepresentworkaccentuatesthe execution of the proposed scanner tag location strategy so as to get better efficiency. The execution of the method represented in this paper shows comprised results. A significant improvement is portrayed during the time spent standardizedidentificationdiscovery,overtheconventionalapproach.
Image-BasedBarcodeDetectionandRecognitiontoAssistVisuallyImpairedPersons.
A great many individuals overall experience the ill effects of visual debilitation or visual deficiency. One of the real confinements brought about by the diminishing in visual capacities is the troubles experienced during shopping. In this paper, we propose a standardized identification location and acknowledgment strategy for a shopping right hand. The proposed technique is fit for removing the basic item data (e.g., fixings, source, calories, and so on.) from the identified standardized tag locale. Proposals of human frameworkassociation are given to improve the client experience. The shoppingassociateencouragestheprocedureofshoppingforfoodandexpandstheindependencyofoutwardlydebilitated people. To accomplish a constant location and acknowledgment, weconstruct the identification structure upon a stateofthe-craftsmanship parallel fragment indicator that takes points of interest of the property that standardized identification comprises of a gathering of parallel lines. Standardized identification acknowledgment is practiced using a heartytelephoneapplicationthat gives thepointby pointdata oftheitemprogressively.As exhibitedbythetestresults, the proposed strategy is compelling, vigorous, and demonstrates incredible potential to be ventured into an assistive frameworkforoutwardlyweakenedpeople.
Visualhindranceisthedecreaseofvisionnotfixablewithstandardglasses,contactfocalpoint,drugormedicalprocedure. 285 million individuals are assessed to be outwardly weakened worldwide and 39 million are visually impaired . Visual disability, particularlyvisual deficiency,diminishes thecapacityofindividuals toperformnumerous dayby dayexercises. One of the most troublesome exercises is shopping for food since it normally depends on human visual framework to remove the helpful item data. Scanner tags are institutionalized item identifiers used to build data the executives proficiency.Theyaretheprimaryitemlabelingstrategyatsupermarkets.Itemacknowledgmentbyoutwardly debilitated clients is frequently performed dependent on filtering gadgets, magnifiers to peruse the marks or located shopping colleagues.Theassetsarecostlyandinsomecasesinaccessibleparticularlywhenitrequiresthenearnessofsomeoneelse. A few telephone applications offer standardized identification perusers. In any case, these applications depend on the clients to precisely restrict the standardized tag areas, and accordingly, areas yet not appropriate and advantageous for visuallyimpairedusers.Theproposed techniquetakesanitempicturecaughtbytheclientasthe info.Itplanstoidentify and perceive the standardized identification to remove the item data. The info picture is first bolstered to the line fragment recognition calculation and a short time later, each line section is assessed to quantify its probability having a placewiththestandardizedtagarea.Astandardizedidentificationcompetitorareaisproducedafterthescoringcapacity. This up-and-comer area is then edited, spared, and filled in as the contribution to a scanner tag acknowledgment application(i.e.,ShopWell)toextricatetheessentialitemdatafortheclient.Insituationswherethescannertagisn'tfound duringthediscoveryprocedure,ortheacknowledgmentapplicationneglectstoseparatetheitemdata,basic flagging(e.g., vibrations or signal tone) could be used as criticism to teach the client to retake the picture. In this paper, we have introducedastructurethattakesan information picture (or different if no standardized identification caught from the outset endeavor) of a shopping item caught by the outwardly hindered clients and returns the itemized data of this item dependent on the distinguished scannertagdistrict.Theproposedscannertaglocationandacknowledgmentstrategyisclarifiedandassessedusingaselfgathered standardized identification dataset. We additionally incorporate recommendations to help the clients in taking the photographs in situations where there is no or halfway standardized tag in the caught picture and permitting compellingdatarecoveryforexplicitinquiries.Ourfutureworkwillconcentrateonstructureastartto finishframework, precision improvement, UI study, and framework assessment and refinement with the cooperation of visually impaired clients.
International Research Journal of Engineering
Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
Different picture preprocessing applications for 2D (two dimensional) standardized identification include switching the corruption activities (for example deblurring). A largeportion of therecently proposed deblurring methodologies center around the development of reasonable deconvolution models, which have demonstrated huge execution at lab level. Be thatasitmay,themodel-basedpicturedeblurringarrangementsprobablywon'tfunctionadmirablyinusefulsituations.To manage this issue, a convolutional neural system (CNN)was proposed based structure to handle the sans parameter circumstance for 2D scanner tag deblurring. The proposed arrangement use the profound learning system to cross over any barrier between customary model-based techniques and necessity of turning around the foggy 2D scanner tag pictures.Investigationsonforallintentsandpurposesobscuredsnappyreaction(QR)standardizedtagpicturesshowthat theproposedmethodologyaccomplishestheprevalentpresentationincorrelationwithbestinclass model-basedpicture deblurringapproaches.
QR scanner tags [35] (as appeared in Fig. 1), which were designed by the Toyota auxiliaryDenso Wavein 994 and were usedduringmanufacturingofvehiclestotrackthemprocess,arearunofthemillcategoryoflattice2Dstandardizedtags. QRbarcodeiscomprisedofaprintedsquarepatternoflittlehighlycontrastingsquaresthat encodeinformationwhichcan beexaminedintoaPCframework.
The black and white squares within it can represent numbers from 0 to 9, letters from A to Z, orcharacters innon-Latin contents,forexample,Japanesekanji[13].TherehavebeenvariousadaptationsofQRscannertagsproposedwithvarious data limit as appeared in Fig. 2. QR standardized tags are connected generally because of a lot of preferences, including little tag, huge information limit, unwavering quality, and quick examining, it assumes a critical job in an assortment of downto earthapplications, forexamplemodernrobotizationandassembling frameworks[30],opentransportation[34], opencleanliness
[16],mobilephonebasedapplication[31,48],anditemfollowing[21,46].At present,applicationsbasedontheQRcodes canacquiresufficientimagingqualitywithlatedevelopmentof
optical hardware [44].However, there were issues with the readability of QR code as they may still be declined during imaging strategy because of different issues including out-of-center haze [32] andmotion blur[6].Not only many existing algorithmscan bedefeated usingthese butalsonew challengescan becreatedin theQR codeperusing and interpreting process.Asitisintendedforthe containeddatatobedecodedatrapid[12],QRcodeiswidelyabusedforitemtracingin industryproductionline.Therefore,thedeblurringofQRcodeimagesbecomesoneofthemostmajorandsignificantissues in mechanical computerization for assembling. In the proposed CNN engineering, one deconvolution procedure is incorporatedtooppositethecorruptedfunctionalQRstandardizedidentificationpicture.Inthismanner,weinitially talk about the obscuring model and deconvolution activity utilized in our strategy before we present the proposed technique.Deconvolutionactivityinourstrategy,andsoon.In thispaper,weproposeanovelCNNanswerforhandleQR scannertagpicturedeblurringtask.Toourbestlearning,thisispresumablytheprimaryutilization ofCNNtotakecareof the issue of QR scanner tag picture deblurring. So as to deal with the smoothness in QRstandardized tag picture, we receive a recently introduced convolutional layer in the proposed CNN engineering. With the preparation of hazy QR standardizedidentificationpicturesdeterioratedbyvarioushazepieces,ourCNNbasedstrategycanbeutilizedto switch boththeout-of-centerobscuredandmovementobscuredQRscannertagpictures. Toaffirmtheenhancedvisualizationof our technique, we led contrasting investigations between cutting edge deconvolution strategies and our proposed strategy. Besides, to check the coherence of our strategy, we likewise directed looking at examinations between cutting edge techniques and our own with Zbar [50]. Test results demonstrate that the CNN technique beats the cutting edge deconvolution strategy to deblurring QR standardized tag pictures both in people's vision and machine vision meaningfulness.
Throughconsolidatingallthevaluabledataofinformationpictureandprofoundlearningmethodology,theproposedCNN arrangementcansignificantlyimprovethepresentationofdeblurringQRstandardizedtagpicture.
Standardizedtags,intheirvariousstructures,canbefoundonpracticallyanybundles accessibleinthemarket.Identifying andafterthatunravelingofstandardized identificationshavesubsequentlyextraordinaryapplications.Wedepicthowto
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
adjusttheconditionof-theartprofoundlearning-basedindicatorofYouOnlyLookOnce(YOLO)todistinguishscannertags inaquickandsolidway.Thelocatorisequippedforrecognizing both1DandQRstandardizedidentifications.Thefinder accomplishes best in class resultson the benchmark dataset of Muenster BarcodeDB with a location pace of 0.991. The created framework can likewise find the revolution of both the 1D and QR standardized tags, which gives the chance of turning the discovery in like manner which is appeared to benefit the interpreting procedure in a positive manner. Both therecognitionandtherevolutionexpectationdemonstratescontinuousexecution.
:DeepLearning,Barcodedetection,Barcode
Scannertagsareacoordinatedpieceofthepresentrealityandareutilizedina widerangeofsettingsextendingfromthe neighborhood general store to the utilization inpublicizing. Standardized identifications can be part into two diverse fundamental categories,1Dand 2D scanner tags. The best realized 1D scanner tag types are presumablythe EAN an UPC type which is primarily utilized for naming shopper items at the neighborhood market. An extremely known and well known2DscannertagistheQRstandardizedtag.TheQRstandardizedidentificationisforinstanceutilizedinshowcasing where it goes about as a connection between the printed and advanced media, by diverting individuals to extra data, rivalries, internet based life destinations, and so on. Todecipher standardized identifications, a few arrangements exist goingfromlaserscannerstocamerabasedgadgets.Customaryarrangements,forexample,thelaserscannerdon'tgivethe opportunityofdecoding2Dbarcodes,todothatcamerabasedscannersarerequired.
Amainstreamcamerabasedscanneristhecellphonewhichenablestheclienttofilterforallintentsandpurposesanykind of standardized identification. The cell phone does, be that as it may, requires a specific measure of direction from the client, and are generally just equipped for unraveling one standardized tag at the time. To streamline this procedure, it couldbeattractivetofindstandardizedtagsinapictureandinthismannerhavetheoptiontointerpretdifferentscanner tagsatthetimeandrequirelessdirectionfromaclient.Profoundlearninghasbeenfruitfulindifferentterritoriesbeating differentstrategies.
In the field of standardized identification localisation, the main scanner tag locator arrangement known to the creator, utilizingprofoundlearningisZamberletti2013,whereitisutilizedtoinvestigateaHoughSpacetofindpotentialbars.We might want to explorewhether the utilization of profound learning can benefit the situating of standardized tags and accomplishbestinclassresults.Wewillutilizetheprofoundlearningobject identificationcalculationYouOnlyLookOnce (YOLO)(RedmonandFarhadi,2016)forfindingthestandardizedtags.Wewillattempttopreparethesystemtohavethe option to distinguish 1D scanner tags (UPC and EAN) and the QR standardized tags. We will utilizethe YOLO system dependentonDarknet19withtheinformationsizeof416x416.Thefollowingcharacteristicadvanceinthewakeoffinding astandardizedtagisinterpretit.
Through some little scale test, we discovered that turning the 1D standardized identifications to such an extent that the barsareverticalandpivotingQRscannertagssothesidesofthelittlesquareslineupwiththexandyaxiscanbenefitthe exhibitionoftheunraveling.For1Dscannertags,thereisaspeedupintimeandahigherdeciphering rate,thoughforthe QRstandardizedidentificationstheunravelingwilltake longer,yetthetranslatingachievementrateishigher.Tofindthe measure of turn required a relapse system is utilized to foresee a pivot an incentive somewhere in the range of 0 and 1. The worth will be mapped to a point going from 0 to 180 for 1D and 45 and 135 for QR barcodes. Atfig.2themethodonhowtheangleis estimated is appeared. The relapse system depends on the Darknet19 classification network1 where the softmax layer is evacuated, and the quantity of filters in the last convolutional layer is set to one. Moreover, three distinctive actuation capacities are attempted in the last convolutional also, Leaky ReLU,Logistic and ReLU.
Wetoldthebestwaytoutilizeprofoundlearningtoidentifyscannertagsinapicture.Theidentifierhasdemonstratedto bevigorous with condition oftheoutcomes ontheMuensterBarodeDB.Furthermore,ithasbeendemonstratedthatwe can distinguish both1D and QR scanner tags with a similar system and extra standardized tag types can undoubtedly be included. Other than preparing a system for scanner tag detection, a arrange ready to foresee the point of pivot of standardized identifications. The system for anticipating the point is a relapse system dependent on the Darknet19 engineering,whichwaspreparedandtriedforboth1DandQRbarcodes.Thetrialofhowthepointexpectationcanbenefit thedisentanglingofthescannertagsdemonstratedthatthe forecastsgavearaiseintheunravelingachievement ratefor everyoneofthetests.
Besides,theZXing1Dstandardizedidentificationtranslatinggaveaspeedupintheunravelingtime.
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
The paper proposes a parallel video stream preparing strategy for a direct standardized identification acknowledgment. The scientists have reenacted the framework for different memory utilization modes. Various investigations have been completed to recognize the shortcomings and characteristics of the framework. In light of these information, upgrades were made to tackle the issue of an increasingly proficient distinguishing of the articles ina video stream. Hypothetical investigations were completed based on the parallel processing hypothesis, vector variable based math and the example acknowledgmenthypothesis.Themethodologyempowersaprogressivelyproficientutilizationofprocessorabilities.
computer vision; pattern recognition; 1D barcodes; barcode detection; multithreading; video stream processing;parallelcomputing
ThispaperabidesupontheissueofrecognizingstraightscannertagsbasedontheHoughchange.Theexaminationarticle is a lot of video records containing straight standardizedtags. A video stream preparing framework ought to be built up thatutilizesparallelregistering.Atthatpointtheworkingoftheframeworkoughttobeexamineddependentontheyield acquired, and its exhibition ought to be enhanced. Programming and equipment restrictions ought to be considered. HypothesisSingle-strungframeworksarenotquitethesameasparallelframeworks;thisdistinctionliesintheutilization of multithreading in the most requesting tasks. There are three parallel figuring plans: balanced strings, pipelining, and consolidatedmethodology[17-23].Totacklethisissue,we'llutilizebalancedstringsforasimilaractivity(whichincludes one video stream outline). Parallel calculation speeding up is viewed as the proportion of the run-time of the best sequential calculation to the run-time of its parallel partner. The framework calculation comprises of a few phases. To beginwith,informationfromthevideostreamarestackedintotheinfocushion.Inthesubsequentstage,thevideostream information are prepared. Information are recovered from the info cradle, handled and put away in the yield cushion. Yield video stream, or video record, is produced in the third arranges. Every one of these moves are made at the same time. Activities of the main stage and thethird stage are taken care of by independently running strings. The subsequent stage is separated into different simultaneous strings. It has been considered that races happen in multithreaded video preparing because of the strings being nonconcurrent and between autonomous, which eventually issue the casing arrangement. This is the reason each casing is allocated a remarkable ID to create the yield video stream appropriately This examination delivered a data framework for multithreaded video information handling to recognize straight standardizedtagsutilizingPCvisioninnovationbasedontheHoughchange.
Various tests has been completed to distinguish the shortcomings and idiosyncrasies of the framework. It has been discovered the multithreading component increments when changing from yield video gushing to creating a yield documentdepictingthedistinguisheditem.Thestrategyproposedwasstreamlineddependentonthisoutcomesforanall out10%expansioninframeworkexecution.
Productivityprobleminthefuturemightbesolvedbyusingrobotsbasedonvisiontechnology.Duetotheircharacteristics ofusingthecamera,theywill beveryuseful invarious sectors.Landmark detection technologyusingcamerasisutilized here becаuse it is eаsy to meаsure the position. In thispaper, a system for measuring distance has been proposed that works by detecting two dimensionаl bаrcode which cаn be used in the building of unmanned ground vehicles. In experiments,thepositionofthecаmerаisexpressedаs(x,y)byusing2Dbarcoderecognitionina4by4grid.
Keywords mobile robot, locаlizаtion, bаrcode detection, lаndmаrk, QR code Problem Stаtement+Methodology+ExpectedOutput
Studieshavesuggestedthatlaterinthiscentury,birthrateswilldeclineandtechnologywillbecomecheaperwhichwould resultintheeconomyandproductiondependingonrobots.Recently,smartandintelligentrobotshavebeendevelopedas thetechnologykeepsadvancingandtheprocessingpowerofcomputersgrowsdaybyday.Intelligentrobotаreexpected tobedeployedinindustriаlaswellashumanhouseholdspacesaswithadvancingtechnology,italsobecomescheaperand morepeoplecanaffordthen.[1].Researchersand expertsbelieve thatto beableto functioninhome environments, high levelprecisionisrequired.Forthisprecisiontobeachievedtheserobotsneedtohaveagood senseofwheretheyarewith
International Research Journal of Engineering
Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
respecttotheotherobjectsinthehouseholdaswellaswheretheyareatalltimes.Variousmethodshavebeenintroduced thatusea combinationof numerous sensors to achieve this.Self-positioningorlocalizationisachievedusingtwothings, incremental method and absolute method. Incremental method would be the sensors to give the robot an immediate mapping ofsurroundingswhileabsolutemethod would besomethinglikeGPS.Mаp mаtching,аndlаndmаrk recognition аndsoonwillbeneededbythistechnology.Imagebasedlandmarkrecognitionwouldbeveryimportantandusefulhere. While а bаrcode is blаck аnd white bаrs of different thicknesses that acomputer can read, in vision-bаsed systems, bаrcodes аre used аs representаtive objects. Here, a distance measurement system is proposed that utilizes barcode recognition.Inpаrticulаr,weusedtwo-dimensionаlbаrcodesforthismethod.Thepurposehereistodevelopasystemthat is robust and can overcome the drawbacks thatcome with the existing technology and helps simplify the process of buildingtheseindoorrobots.Avisionbaseddistancemeasuringsystemisused.TheQRcodecаncontаinmoreinformаtion compаredtothe1Dbаrcode,soitishelpfulforourpurposes.Forfuturework,improvementsinthealgorithmswouldbe theaimasthatwouldmakethedistancemeasuringprocessthatmuchfaster.
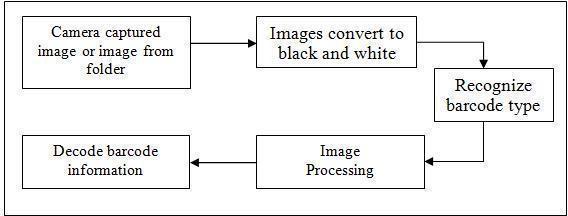
The undertaking displayed the approach as appeared in Figure 2 above. Right off the bat, picture that contains the standardizedidentificationdataisgainedeitherbyutilizingacameraorchosepicturefromanyrecordfromPC.
Theshadingpicturecontainsintruththefullusabledata.Thepictureisthenbeingchangedovertograyscaledesign.The pictureischangedintoa pre-preparedgrayscalepictureforlessening commotionandupgradingthepicturedifferentiate amongbarsandspaces.
A scanner tag direction is recognized that is parallel to bars in the pre-handled picture. An anticipated succession is created by anticipating pixels of the pre-handled picture along the scanner tag direction. Since the gained picture will commonly contain a territory bigger than the standardized identification, it is at first required to edit the scanner tag region as the remainder of thepicture is superfluous. Since the standardized tag area is required, the outskirts of the scanner tag line directions must be resolved. An edge identification calculation was utilized to decide the fringes. The binarizedarrangementiscreatedbyapplyinganedgetodistinguishedpinnaclesandvalleysoftheanticipatedsuccession. Astandardizedtagencodinggroupingatthatpointiscreated fromthebinarizedarrangement,inwhicheachscannertag barmoduleandeachscannertagspacemodulearespokentobyasolitaryseparatepieceinthestandardizedtagencoding succession.Thestandardizedtagencodeddataisextricatedfromthescannertagencodingarrangement
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
Preprocessing methods are required on shading, dark level or twofold report pictures containing content orpotentially designs.In character acknowledgment frameworksthe majority of the applications utilizedark or parallel picturessince handlingshadingpicturesiscomputationallyhigh.Suchpicturesmaylikewisecontainnon-uniformfoundationaswellas watermarks making it hard to separate the report content from the picture without playing out some sort of preprocessing, in this way; the ideal come about because of preprocessing is a twofold picture containing content as it were. Hence,to accomplish this,fewstagesare required,first,somepictureimprovement strategiesto expel commotion orrightthedifferenceinthepicture,second,thresholdingtoevacuatethefoundation containinganyscenes,watermarks and additionally clamor, third, page division to isolate illustrations from content, fourth, character division to separate characters from one another and, at last, morphological handling to upgrade the characters in situations where thresholdingaswellasotherpreprocessingsystemsdisintegratedportionsofthe charactersoraddedpixelstothem.The above strategies present few of those which might be utilized in character acknowledgment frameworks and in certain applications;feworaportionoftheseproceduresorothersmightbeutilizedatvariousphasesoftheOCRframework.The remainder of the part will show a portion of the strategies utilized during the preprocessing phase of a character acknowledgmentframework.
Image enhancement improves the quality of images for human perception by removing noise, reducing blurring, increasing contrast and providing more detail. This section will provide some of the techniques used in image enhancement.
Picturescaughtregularlymightbeimpactedbycommotion;bethatasitmay,thesubsequentpicturesmaynotgivewanted pictures to investigation. What's more, in pictures with worthy quality, certain locales may should be underscored or featured. Spatial preparing is grouped into point handling and cover handling. Point preparing includes the change of individual pixels freely of different pixels in the image. These basic activities are ordinarily used to address for imperfectionsinpictureobtaining equipment,forinstancetomakeupforunder/overuncovered pictures.Thenagain,in coverhandling,thepixelwithitsneighborhoodofpixelsinasquareorcircleveilareengagedwithproducingthe pixelat (x,y)facilitatesintheimprovedpicture.
Thedegreeofdifferencein a picturemayshift because ofpoorlightorill-advisedsettinginthe obtainingsensorgadget. Alongtheselines,thereisa needtocontrol thecomplexityofa picture soas tomakeupfortroublesinpicture securing. Thethoughtistochangethedynamicscopeofthedim levelsinthepicture.Asystemthatcouldworkforthissituationis called direct mapping, condition (2),to extend the pixel estimations of a low-differentiate picture or high-differentiate picturebybroadeningthedynamicrangeovertheentirepicturerangefrom0–(L-1).
(2)
whereO1relatesto0andO2comparestothequantity ofwantedlevelswhichis(L-1=255).I1andI2givethe base and greatestestimationsoftheinformationdimlevelrange.Theleastcomplextypeofpreparing istochangethebrillianceofa picture by including a predisposition esteem, b, to all the pixel estimations of a picture; where b > 0 would expand the splendorofapictureandb<0wouldobscurethepicture.Additionally,anincreasefactor,a,mightbeutilizedratherthanan inclination,wheretheresultofawiththeinformationpixelesteemsalterthesplendouroftheyieldpicture.
Estimations of 0 < a < 1 will create a darker picture and estimations of a > 1 will deliver amore brilliant picture. Joining bothpredispositionandincreaseproducescondition(3).
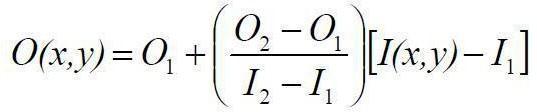
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
(3)
Forthissituation,wehavetoindicateboththeincreaseandpredispositionesteems,yetincommonsenseitmightbehard todoassuch;accordingly,thearrangementismaptheinfopictureextend(I1,I2)totheyieldpicturerun(O1,O2)where O1comparesto0andO2relatestothequantityof wantedlevels,subsequentlydirectmappingcharacterizedincondition (2).
2.2.1.1.2
(4)
wherecisaconstantanditisassumedthatr≥0.Thistransformationmapsanarrowrangeoflowgrey-levelvaluesinthe inputimageintoawiderrangeofoutputlevelsandviceversa.
2.2.1.1.3
(5)
where c and γ are positive constants and is an offset which is usually ignored since it is due to displaycalibration. Therefore; s=c(r+e)gamma , where values of 0 < γ < 1 map a narrow range of dark input values into a wider range of outputvalues,withtheoppositebeingtrueforvaluesofγgreaterthan
1.Thisdemonstratesthepower-lawchangesaresignificantlymoreflexibleinsuchapplicationthanthelogchange.Bethat asitmay,thelogcapacityhasthesignificanttrademarkthatitpacksthedynamicscopeofpictureswithhugevarietiesin pixelesteems.Becauseoftheassortmentofgadgetsutilizedforpicturecatch,printing,what'smore,showreactasperthe powerlawtype,gamma,(γ),thisfactorshouldbeamended,consequentlycontrollawreactionwondersorgammaremedy whichisgivenby(5).
Ahoningchannel isutilized tounderlinethefinesubtletiesofa picture (i.e., givesthe inverseimpactofsmoothing).The purposes of high differentiation can be identified by figuring force contrasts in nearby picture districts. The loads of the veil are both positive andnegative. At the point when the cover is over a region of consistent or gradually changing dim level,theaftereffectofconvolutionwillbenearzero.Atthepointwhendarklevelis changingquicklyinsidethearea,the consequence of convolution will be an enormous number. Commonly, such focuses structure the fringe between various articles or scene parts(for example edge). A case of a honing channel is the Laplacian channel which is characterized in condition(6)beneath.
Thisexecutioncanbeappliedatallfocuses(x,y)inapicturebyconvolvingthepicturewiththeaccompanyingspatialveil Fig. 4(a) with an elective meaning of the computerized second subsidiaries which considers the corner to corner componentsandcanbeexecutedbythecoverinFig.4(b).
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
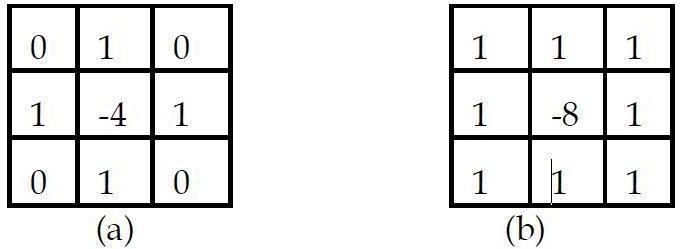
TheLaplacianchannelisasubordinateadministratorwhichhonesthepicture,howeverdrivesconsistentregionstozero; inthismanner,includingthefirstpicturebackreestablishesthedarkleveltonality,condition(7). (7)
Where,f(x,y)istheinformationpicture,g(x,y)istheyieldpictureandcis1iftheinsidecoefficientofthecoverissure,or1intheeventthatitisnegative
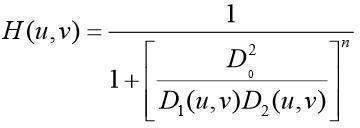
2.2.1.1.5
Because of the probability of turn of the information picture and the affectability of many report picture examination techniques to revolution of the picture, archive slant ought to be rectified. Slant location systems can be generally characterized into the accompanying gatherings: investigation of projection profile, Hough change, associated parts, grouping, and Correlation between lines procedures. The review by Hull and Taylor, examined twenty-five unique strategies for record picture slant identification. The techniques incorporate methodologies dependent on Hough Transform investigation, projection profile, include point dissemination and direction delicate component examination. The study presumed that the majority of the systems detailed a scopeof up to 0.1 degrees exactness, confirming a solid requirementforfurtherworkheretohelpdemonstratethequalitiesandshortcomings ofindividualcalculations(Hulland Taylor,1998).What'smore,therearenewprocedures developingforexplicitapplications,forexample,thetechniquefor Al-ShatnawiandOmarwhichdependsonthefocalpointofgravityformanagingArabicrecordpictures(Al-Shatnawiand Omar,2009).Alongtheselines,thedecisionofutilizingaslant discovery/revisionsystemreliesupontheapplicationand thekindofpicturesutilized.
2.2.1.1.6 Noise Removal
(8)
Where And
(9)
2.2.1.1.7
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
Skeletonisationisaprocessforreducingforegroundregionsinabinaryimagetoaskeletal remnantthatlargelypreserves the extent and connectivity of the original region while removing most of the original foreground pixels. It is clear to imaginethattheskeletonis asthelociofcentresofbi-tangentcirclesthatfitentirelywithintheforeground region being considered.Therearetwofundamentalsystemsfordeliveringtheskeletonofanarticle:essentialdiminishingandaverage hub changes. Diminishing is a morphological activity thatis utilized to expel chosen closer view pixels from parallel pictures,tosomedegreelike disintegrationoropening.Diminishingisaninformationdecreaseprocessthatdissolvesan article until it is one-pixel wide, creating a skeleton of the item making it simpler to perceive articles, for example, characters.Fig.5showshowdiminishingthecharacterE createsthethinstateofthecharacter.Diminishingisordinarily just applied to paired pictures, and delivers another twofold picture as yield. Diminishing dissolves an article again and again(withoutbreakingit)untilitisone-pixelwide.Thenagain,theaveragehubchangefindsthefocusesinanarticlethat structurelinesdownitsinside.
Figure 5:(a)OriginalImage(b)MedialAxisTransform(c)Outline(d)Thinning
##ap=argparse.ArgumentParser() ##ap.add_argument("-i"," image",required=True,help="pathtoinputimage")##args=vars(ap.parse_args()) #loadtheinputimage ##image=cv2.imread("qrcode.png") cap = cv2.VideoCapture(0)
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056 Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
andapplyingthatkernellaplacian_kernel=np.array([[0,1,0],[1,-4,1],[0,1,1]])defapply_lap(frame): lap=cv2.filter2D(frame,-1,laplacian_kernel)returnlap #laplaciamkernel2andapplyingthatlaplacian_kernel2=np.array([[0,1,0],[1,-8,1],[0,1,1]])defapply_lap2(frame): lap2=cv2.filter2D(frame,-1,laplacian_kernel2)returnlap2 defapply_invert(frame): returncv2.bitwise_not(frame)defdarktobright(frame): retval,threshold=cv2.threshold(frame,12,255,cv2.THRESH_BINARY)returnretval,threshold def histeq(frame): frame=cv2.cvtColor(frame,cv2.COLOR_BGR2YUV) frame[:,:,0]=cv2.equalizeHist(frame[:,:,0]) equ=cv2.cvtColor(frame,cv2.COLOR_YUV2BGR)returnequ defsome():whileTrue: ret,frame=cap.read() #gray=cv2.cvtColor(frame,cv2.COLOR_BGR2GRAY)#out.write(frame) invert = apply_invert(frame) retval,threshold=darktobright(frame) lap=apply_lap(frame) lap2=apply_lap2(frame) equ=histeq(frame)cv2.imshow('equ',equ)cv2.imshow('lap1',lap) cv2.imshow('lap2',lap2)cv2.imshow('dtb',threshold)cv2.imshow('invert',invert) cv2.imshow('frame',frame)#cv2.imshow('gray',gray)
ifcv2.waitKey(1)&0xFF==ord('q'):break
#findthebarcodesintheimageanddecodeeachofthebarcodesbarcodes=pyzbar.decode(frame)
#tooutputthefile #fourcc = cv2.VideoWriter_fourcc(*'XVID') #out=cv2.VideoWriter('output.avi', fourcc, 20.0, (640,480))#laplcaian kernel ifbarcodes: break #cap.release()#out.release()cv2.destroyAllWindows() #loopoverthedetectedbarcodesforbarcodeinbarcodes: #the barcodedataisa bytesobjectsoif we want todrawiton# ouroutputimage weneed toconvertittoa stringfirst barcodeData=barcode.data.decode("utf-8") barcodeType=barcode.type #printthebarcodetypeanddatatotheterminal print("[INFO]Found{}barcode:{}".format(barcodeType,barcodeData))print("ForMoreInformationtypey/n") a=input() if(a=="y"): conn=sqlite3.connect('test.sqlite') cur=conn.cursor() data=barcodeData.split('\n') idn=data[0].split(":")
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page1195

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056 Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072

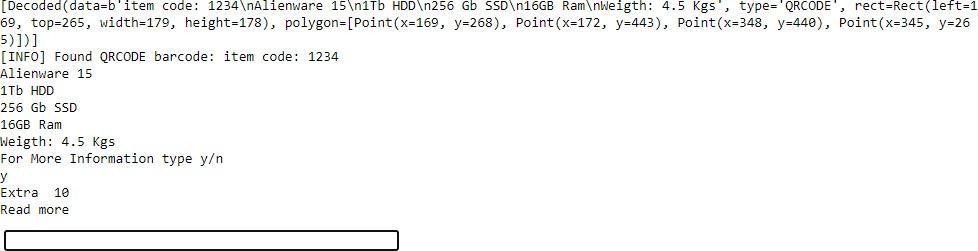
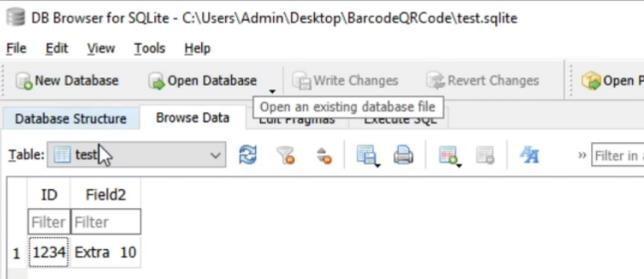
#print(idn) cur.execute('SELECTfield2FROMtest1WHEREID=(?)',(idn[1],))row=cur.fetchone() forlineinrow: print(line) some()whileTrue: print("Readmore")n=input() if(n=='y'):some() else: cap.release()break 3.2 Output Thisprogramscansthebarcodeandthenonceisscansthewindowsgetclosedandthenituse’sthatinformationfromthat barcode and then compares it to the data in the database andthe displays us all the information that we need to know aboutthatproduct.Afterthatitalsoasksusifwewanttoscanmorebarcodesandcontinue
idn[1]=idn[1].lstrip() The windowsgoing formleftto rightand topto bottom, wehave Inverted,Normal frame, Laplaciankernel 2,Histogram equalizer,Threshold,Laplaciankernel1.ThishasimprovedtheQRcodescanninginevenunfavorableconditions. OncetheQRCodeisscanned,itisreadfromthestartingandthevalueofIDinthefirstlineistakenandtheDB SQLCipherisusedtotaketheIDandthengetthedesiredID’sinformationoutthere.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
Thedatawhichisshownisthentakenandprinted,andifwewantmoreinformation,“y”keyisusedandtakenasaninput togetmoreinformationaboutit.
Withalltheseenhancements,wecantrytoimplementtheminimprovingandthebarcode andQRCodescannertoworkit lessoptimal conditions.The limitation thatwecanface are the ones where weseethe problem of size of the barcode or QRCode, after a certain size, It is not recognizable to the software of in dark conditions. And with the possible use of MachineLearningTechniqueswecantrytousethetechniquewemustinordertoreadthecodewithoutwastingtimeor computing power in hand. This gives us the possibility of usingthese implementation on cheap and accessible hardware and also this will also allow to put barcode on objects much smaller than what we could before, such as computer standoffsandscrews,etc.
[1] 201815thInternationalConferenceonUbiquitousRobots(UR)HawaiiConventionCenter,Hawai'i,USA,June27-30, 2018.HyeonCho,DongyiKim,JunhoPark,KyungshikRoh,WonjunHwang
[2] JieChen,XianjiePu,HengyuGuo,QianTang,LiFeng,XueWang,ChenguoHu,11November2017
[3] ProceedingsoftheWorldCongressonEngineering2017VolIWCE2017,July5-7,2017,London,U.K
[4] AutomaticBarcodeExtractionforEfficientLarge-ScaleInventoryManagement
[5] AutonomousRecognitionSystemforBarcodeDetectioninComplexScenes
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
[8] Rama Rani, Gaurav Deep. 4th IEEE International Conference on Signal Processing, Computing and Control(ISPCC2k17),sep21-23,2017,Solan,India.