1
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072

1
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
2
Abstract - Technology is growing exponentially in the recent years and most of the organizations store their data in digital format. With the rapid growth in technology, there is a need for maintaining security of data. It is extremely essential as data leak might have a huge effect on the organization. Preventing data leak has become one of the biggest challenges to the organizations. For the security purposes, the organizations have implemented several methods like implementation of policies, Firewalls, VPNs, etc. However, with the enhancement of data theft methods, these security measures are not reliable anymore. Hence there was a need for a system that can prevent data leak. Also, as employees have access to sensitive information of the company, they could leak the information either by negligence or on purpose. Hence, securing the data has become a big challenge for the organizations. In this article, we propose a system that will achieve the information security goals of the organization, and will be capable of detecting data leak at any state of the data. The proposed system mainly focuses on preventing data leak.
Key Words: Data Leak Prevention, Sensitive Data, Data LeakSecurity has become an important factor in our life. Security is required in all sectors of industry. An attacker has various methods to access the confidential information of any organization. Hence, preventing such attackers from accessing the information is the main aim of information security. We need to implement various strategiestosecuretheinformation.
Data leak occurs when unauthorized users can access the confidential or sensitive data to. Data leak can happen intentionally through employees of the organization or maliciousattackers.Itcanalsobeanunintentionalleakby employees.Inanycase,thedataistransferredoutsidethe organization. Data leak usually occurs through email. It can also occur through data storage devices such as laptops.
Data is one of the most precious asset. Therefore, the preventionofdataleakisthemostimportanttaskforany organization.
***
Even with security measures like firewalls, data leak still occurs. In any organization, the employees have access to sensitive data. Hence, there is a chance that the data leak occurs through employees rather than through malicious attackers.
Any organization must deal with three types of data to preventdataleak:
1. Data in motion
It refers to data that is moving from the network to the outsideworldthroughtheinternet.
2. Data at rest
Itreferstodatathatisstoredinthefilesystems,databases andotherstoragemethods
3. Data at the endpoint
Itreferstodatapresentattheendpointsinthenetwork
Most of the organizations scan the emails that have been received from outside the organization for any malicious malwares. But, they do not check the emails sent outside the organization, thereby allowing the sensitive informationtobesentoutsidetheorganization.
MostcommoncausesofDataBreachare:
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

If a machine is infected by viruses and worms, spyware, adware, etc. this might result in corruption and loss of data.Inordertopreventthis,anti-virusshouldbeused.
Ill-intentioned and malicious attackers can hack into the system and steal, modify or delete valuable information. Thiswillcausedataleak.
Data leak prevention (DLP) is the practice for detection and prevention of data breaches and destruction of sensitive data. It is a set of tools and processes used to ensure that unauthorized users do not access, delete or modifythesensitivedata.
NetworkDLPstandsforNetwork DataLoss Prevention. It is a technique for protecting communications over the network such as web applications, emails, and data transfermechanismsoftheorganization.
It helps to prevent the loss of sensitive data on the network. Moreover, it allows the company to encrypt data and to block risky information flows in order to monitor and controltheflowofdataoverthenetworkaccordingtothe regulatorycompliance.
➢
EndpointDLPstandsforEndpointDataLeakPrevention.It protects sensitive data at the endpoints. It also helps the organizationtotrackemployeebehaviors.
It monitors and addresses daily risky actions like sending emails,uploadingdatatothecloud,etc.Itprovidesawider rangeofthreatprotection.
Inthisproject,wewillbeimplementingEndpointDLP
TodevelopasystemforDetectionandPreventionofData Leak.
Fig -1
DLP software classifies data into different categories and checksforviolationsofpoliciesdefinedbyorganizations.
Once these policies are violated, DLP issues alerts, and other protective measures to prevent end users from accidentally or maliciously sharing confidential information.
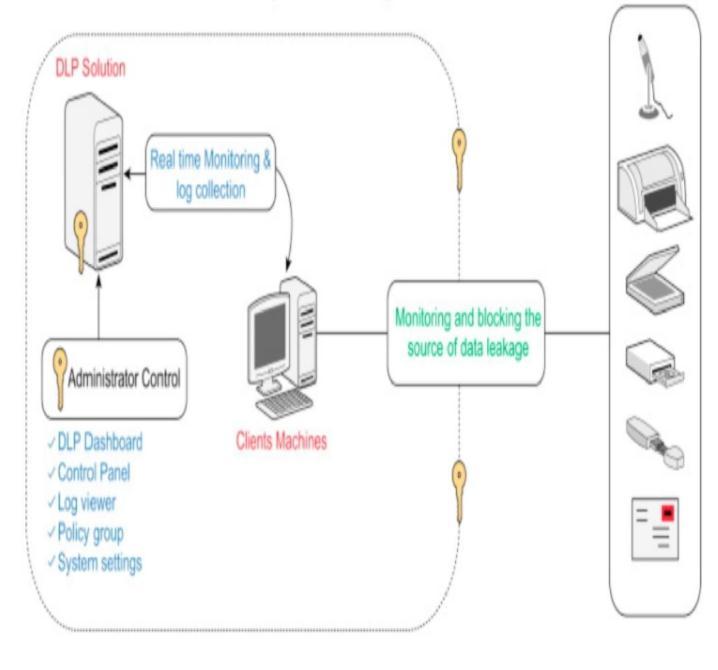
TheDLPcanbeclassifiedintotwotypes: ➢ NetworkDLP ➢ EndpointDLP
Inthissystem,thedatawill besecuredbyusingDLP.DLP is a method to prevent the users from sending sensitive dataoutsidetheorganization.Thesystemisusedtocheck for any activities of data transfer that might lead to data leak.
Thesystemwillcontrolandmonitorendpointactivities.It will also monitor the data in the cloud to protect data at rest,inmotion,andinuse.Itwillalsogeneratereportsand identifyweaknessesinthesystemtoenhancethesecurity.
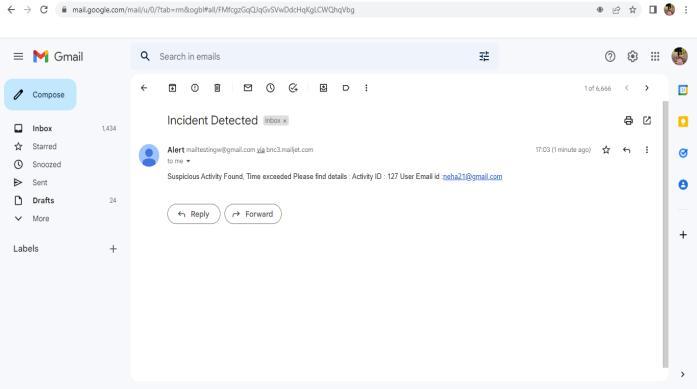
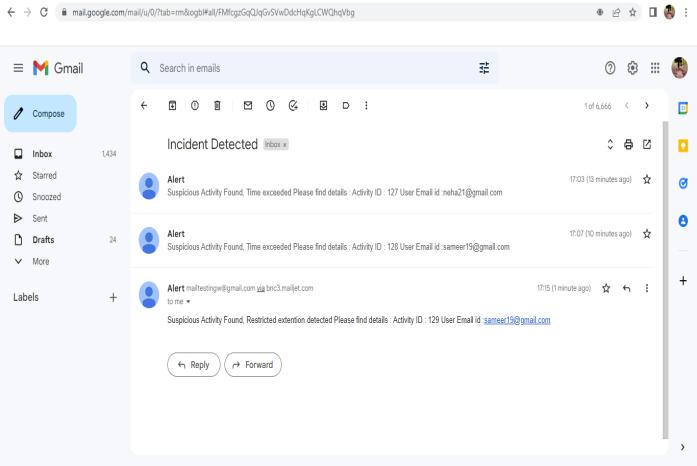
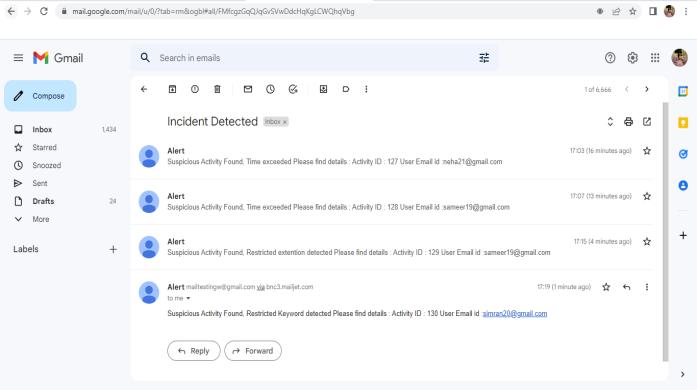
TheproposedsystemsuggestsaSystemforDetectionand Prevention of Data Leak. The system will constantly monitor the activities of the employees and will restrict any malicious activities. If any suspicious activity from employees is found, the system will inform the admin throughgenerationofincidentmail.
Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page 1020
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

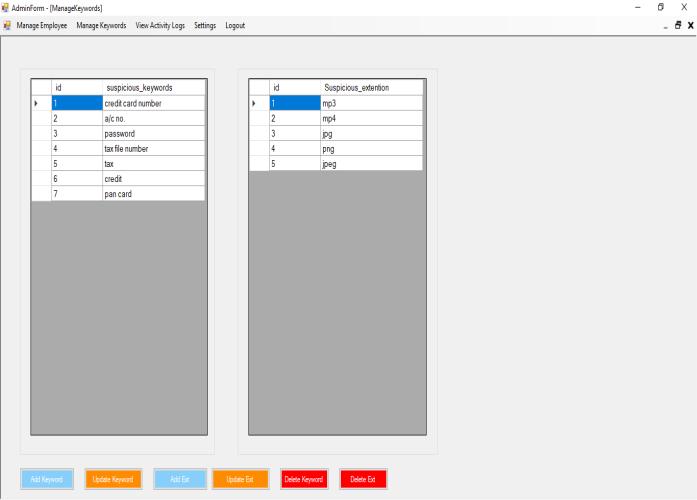
2.3.1 Parameters to Detect and Prevent Data Leak:
Thesystemusesasetofparameterstodetectandprevent DataLeak.Theyareasfollows:
➢ TimeRestriction ➢ ExtensionRestriction ➢ KeywordsRestriction
It is a technique which will restrict any malicious activity from users by applying time constraints. Here, the admin of the system can decide a particular time frame for sending the mails. The mail can be sent only in the time framedefinedbytheadmin.Itwillnotbesentoutsidethe timeframe.
e.g.: The time restriction can be set from 8:00 am to 9:00 pm.Anytransmissionsoutsidethistimeframewilltrigger incidentmailtotheadmin.
It is a technique which will restrict the files with extensions that cannot be read by the system. The followingarethereadablefileformatsforthesystem:
➢ Excel(.xls)
➢ Word(.doc) ➢ PDF(.pdf) ➢ TextFile(.txt)
Transmission of files with extensions other than Excel (.xls),Word(.doc),PDF(.pdf)andTextFile(.txt)willpose a threat to the confidentiality of the information of any organization.
Hence,theExtensionRestrictionfeatureallowstheadmin toblockthetransmissionoffileswithallotherextensions likeJpg,jpeg,png,mp3,mp4,etc.whichcannotbereadby thesystem.
It is a technique which will restrict the transmission of fileswhichincludesanyconfidentialdata.
The admin can define a set of suspicious keywords. The system will check whether the file contains any of the keywords.
If the file contains the suspicious keywords, then the system will block the transmission, else it will allow the transmission.
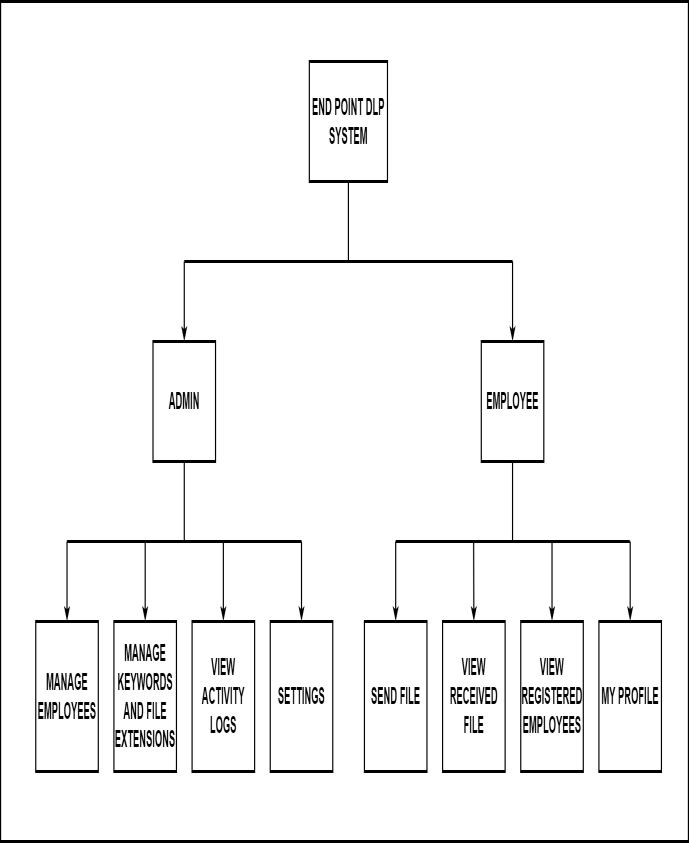
Thesystemhastwomajormodules:
➢ ADMINMODULE ➢ EMPLOYEEMODULE ➢
ADMIN MODULE:
TheAdmincanloginusingthecredentialsprovidedbythe system.
ThefunctionalitiesofAdminModuleare:
The admin has the rights to add, update and delete employee details. After registration of the user, login credentialswillbegeneratedandwillbesentviamail.
Theadmincandefineasetofkeywords.Thekeywordscan beadded,modifiedanddeleted.Adminwillblockthenonreadable fileExtensions.
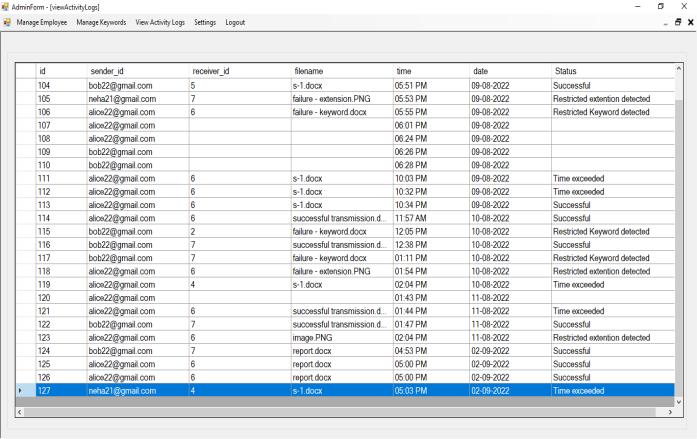
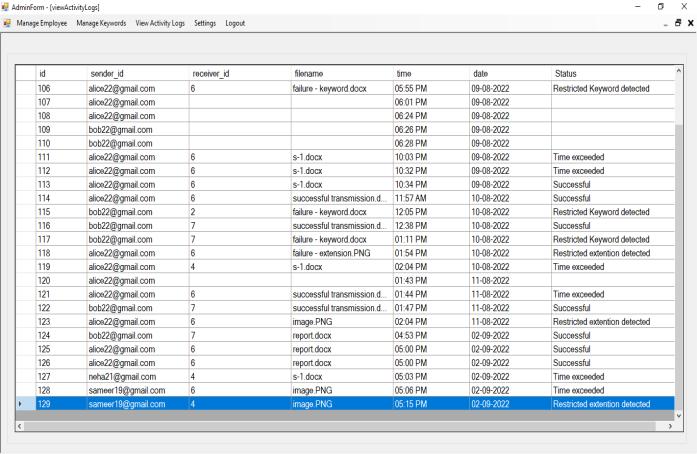
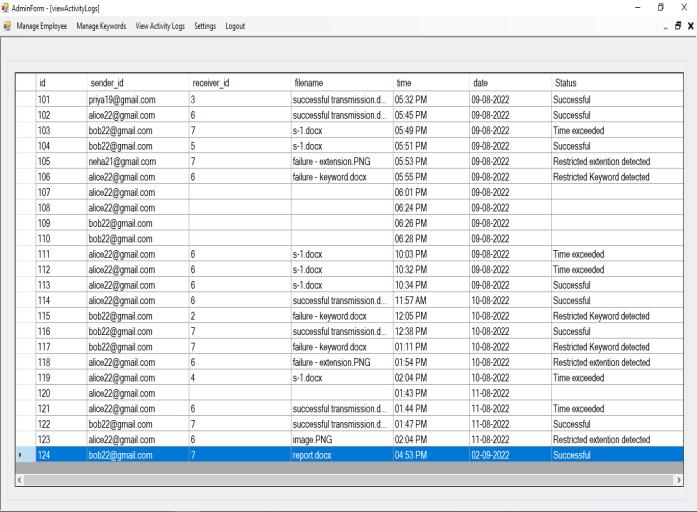
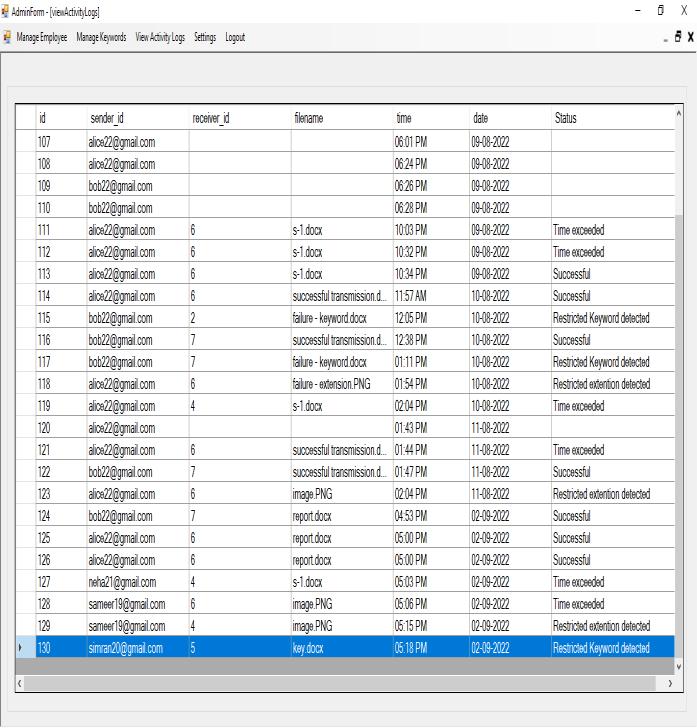
Theactivitylogswillbedisplayedhere.
Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
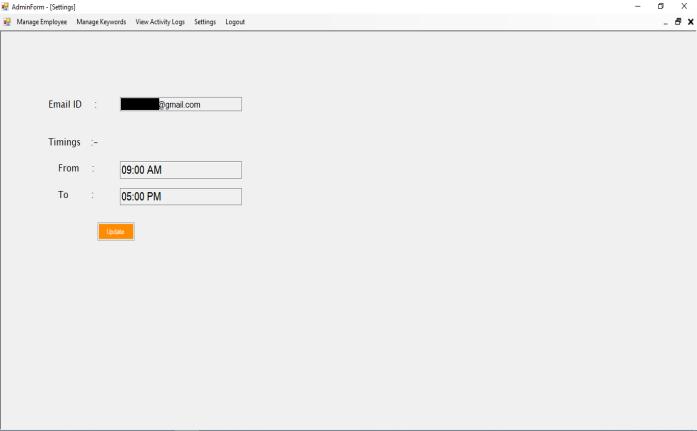
4. Settings:
Theadmincansetatimeframeforsendingemails. Admin willalsoprovideEmailidtoreceiveincidentemail.
➢ EMPLOYEE MODULE:
The employeecanloginusingthecredentialsprovided by thesystem.
ThefunctionalitiesofEmployeeModuleare:
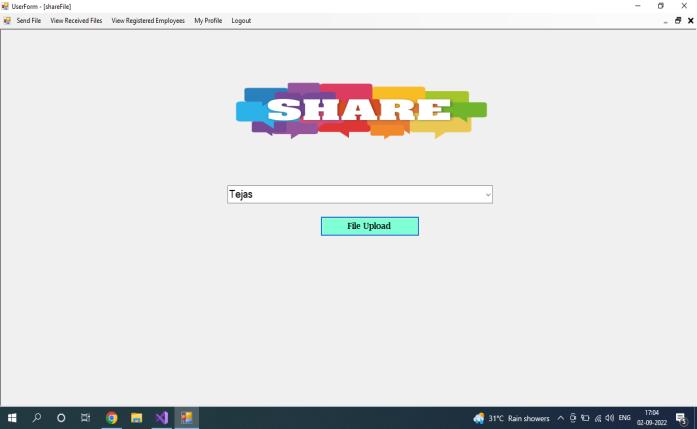
1. Send File:
The employee can send files to anyone inside or outside theorganization.
2. View Received Files:
The employee can download the files received through email.
3. View Registered Employees:
Theemployeecanviewtheprofileof otheremployeesand getinformationliketheiremailid.
4. My Profile:
Theemployeescanviewandedittheirownprofile.
The system constantly monitors the activities of employeestocheckwhetherthereisanymaliciousactivity or not. The employee can send files to anyone inside or outsidetheorganization.
Wheneveranemployeewantstosendafileovermail,the system will check all theparameters and will eitherblock themailorallowthemailtobesent.
Thesystemwillidentifydataleakbasedontheparameters usedtoidentifyDataLeak,i.e.TimeRestriction,Extension Restrictionand KeywordsRestriction.
The system will also generate incident mail to the admin andcreateanactivitylog.
Figure 3. Working
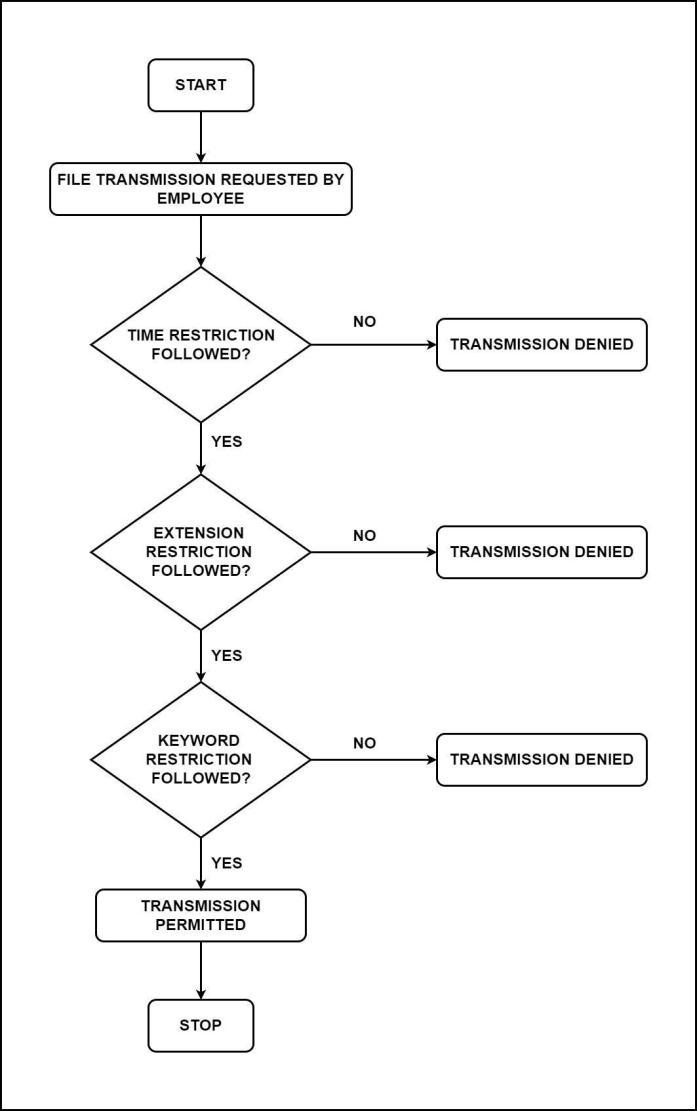
The following are the various case scenarios in which the system is able to restrict the transmission of suspicious data:
In this case, the transmission outside the timeframe mentionedinthesystemisblocked.
Factor value:
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
Aswecanseeinthefigure,thetimesetbyusisfrom9:00 amto5:00pm.
Nowwhenwetrytosendafileoutsidethetimeframe,the systemblocksthetransmission.
CASE 2: Restricted due to Extension:
In this case, the transmission of the file is carried out within the timeframe mentioned in the system, but the extensionforthefileisnotreadable.
An incident email is generated to the admin and the activitylogsarerecorded.
As we can see in the figure, the approved file extensions fortransmissionare:
Excel(.xls)
Word(.doc)
PDF(.pdf)
TextFile(.txt)
Nowwhenwetrytosenda filewithinthetimeframe but with a suspicious extension, the system blocks the transmission.
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
In this case, the transmission of the file is carried out within the timeframe mentioned in the system and the extension for the file is readable, but there are keywords presentinthefile.
An incident email is generated to the admin and the activitylogsarerecorded.
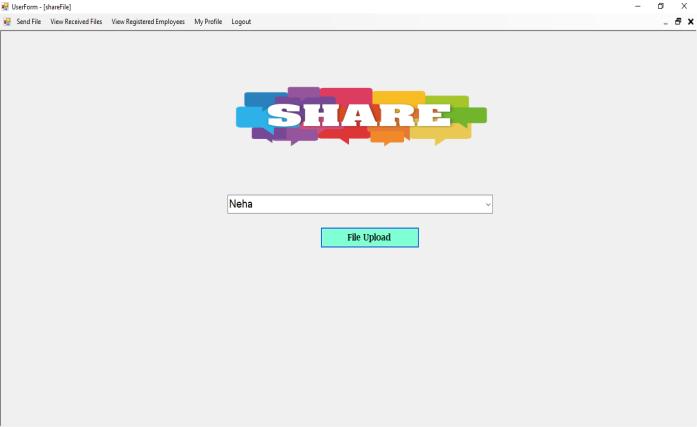

Aswecan see in thefigure, the given set of keywordsare restricted.
Now when we try to send a word file with suspicious keywords,thesystemblocksthetransmission.
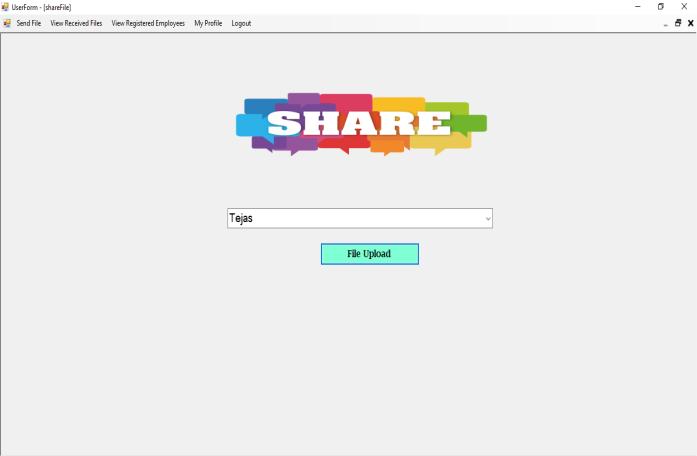
An incident email is generated to admin and the activity logsarerecorded.
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Figure
In this case, the transmission of the file is carried out withinthetimeframementionedinthesystem,thefilehas appropriate extension and it does not contain any keywords.
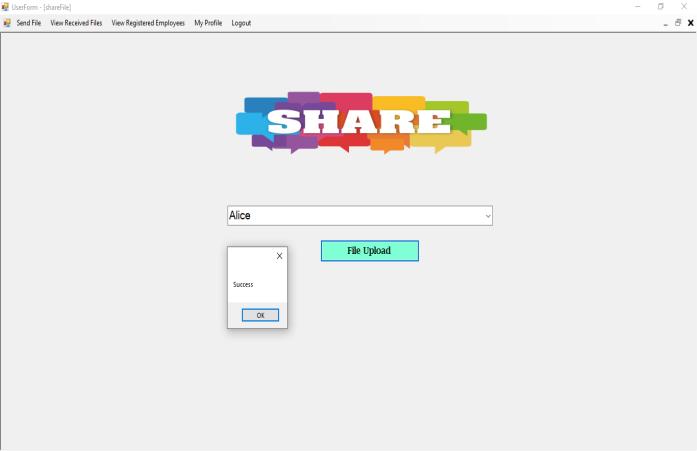
Here, the system allows the transmission and the activity logsarerecorded.
Aswecansee,thesystemshowsasuccessmessage.
Figure
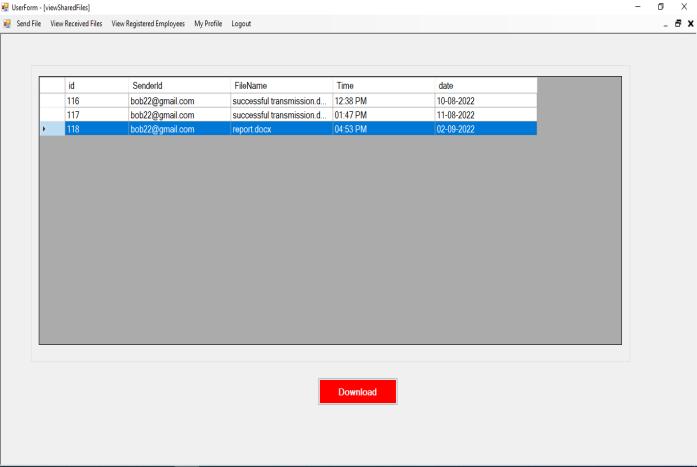
Thereceivercandownloadandviewthefile.
Figure 18: Download Recieved Files
Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page 1025
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN:2395-0072
Data leak is a major issue for many organizations. Data leak can have a disastrous effect on any organization. Hence, preventing data leak is very important. In this paper, a system is proposed for detection and prevention of data leak, which will achieve the security goals of an organization. The proposed method is easy to implement andcanbeusefulformanyorganizations.
[1] S. Czerwinski, R. Fromm, and T. Hodes, “Digital Music Distribution and Audio Watermarking, ”http://www.scientificcommons.org/430256 58, 2007. Availableat:www.researchpublications.orgNCAICN-2013, PRMITR,Badnera399
[2] Y. Li, V. Swarup, and S. Jajodia, “Fingerprinting Relational Databases: Schemes and Specialties,” IEEE Trans.DependableandSecureComputing,vol.2,no.1,pp. 34-45,Jan.-Mar.2015.
[3] Y.CuiandJ.Widom,“LineageTracingforGeneralData WarehouseTransformations,”TheVLDBJ.,vol.12,pp.4158,2014.
[4] Panagiotis Papadimitriou and Hector Garcia-Molina, “Data Leakage Detection,” IEEE Trans, Knowledge and DataEngineering,vol.23,no.1,January2013.
[5] P. Bonatti, S.D.C. di Vimercati, and P. Samarati, “An Algebra for Composing Access Control Policies,” ACM Trans.InformationandSystemSecurity,vol.5,no.1,pp.135,2011.
Aishwarya Jadhav is currently pursuing M Tech from VJTI COE, Mumbai. She has done her B.E (Computer Engineering) from AtharvaCollegeofEngineering.

Prof. Pramila M Chawan, is working as an Associate Professor in the Computer Engineering Department of VJTI, Mumbai. She has done her B.E.(Computer Engineering) and M.E.(Computer

Engineering)fromVJTICollegeof Engineering,MumbaiUniversity. She has 28 years of teaching experienceandhasguided85+M. Tech. projects and 130+ B. Tech. projects. She has published 143 papers in the International Journals, 20 papers in the National/International Conferences/ Symposiums. She has worked as an Organizing Committee member for 25 InternationalConferencesand5 AICTE/MHRD sponsored Workshops/STTPs/FDPs.Shehas participated in 16 National/International Conferences. Worked as ConsultingEditoron–JEECER,JETR,JETMS,Technology Today,JAM&AEREngg.Today, TheTech.World Editor–JournalsofADR Reviewer-IJEF,Inderscience
She has worked as NBA CoordinatoroftheComputer Engineering Department of VJTI for 5 years. She had written a proposal under TEQIP-I in June 2004 for ‘Creating Central Computing Facility at VJTI’. Rs. Eight Crore were sanctioned by theWorldBankunderTEQIP-Ion this proposal. Central Computing Facility was set up at VJTI through this fund which has played a key role in improving the teaching learning process at VJTI.
AwardedbySIESRPwith Innovative & Dedicated Educationalist Award Specialization : Computer Engineering &I.T.in2020
ADScientificIndexRanking (World Scientist and University Ranking2022)–
2nd Rank- Best Scientist, VJTI ComputerSciencedomain 1138th Rank- Best Scientist, ComputerScience,India