International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
Pravin P. Kharat1 , Prof. Pramila M. Chawan2
1M. Tech Student, Dept of Computer Engineering and IT, VJTI College, Mumbai, Maharashtra, India
2Associate Professor, Dept of Computer Engineering and IT, VJTI College, Mumbai, Maharashtra, India ***
Abstract - In simple terms,a vulnerability in cyber security refers to any fault or flaw, or weakness in an information system, internal controls, or system processes of an organization. It can also be defined as a flaw or a fault in the source code design which determines the application malfunctions. Therefore, a good Vulnerability Management plan shouldbe implemented to avoidattacks onthe system or tominimizethedamagesproducedbyacyberattack.Toavoid such damages manual source code inspections or security audits are performed, which requires highly trained cyber securityengineers,anditrequiresmoretime,whichisproneto errors. For this reason, there is a need to automate such processes to discover vulnerabilities. This results in the implementation of the Vulnerability Management System, which will automate security testing for the identification of vulnerabilities caused in the software products.
Key Words: Vulnerability, Vulnerability Management System, Algorithm, Software testing, Web based application.
Manyorganizationshaveembracedthetechnologiessuchas softwareapplications,webapplications,softwareproducts, andmanymoretoexploretheirnewbusinessopportunities andfeworganizationsarebeingforcedtoadopte-commerce duetoadvancementsinsoftwaretechnologies,customers,or competitors. Software applications and web applications have been gaining popularity day by day, and these applicationscomeupwithdifferentcomponentswhichare highlycomplexandwrittenbydifferentsoftwaredevelopers indifferentsmallerchunks.Mostoftheseapplicationsfailto give proper output due to untreated cases or flaws. Therefore, the software application or Operating system which contains untreated cases, flaws, or weaknesses are known as software vulnerabilities. Later, the flaws in the sourcecodeoftheapplicationcanbeexemplifiedasanentry point for the hacker and can be treated as a software vulnerability.
Despite all the security measures, the number of vulnerabilitiesdiscoveredcontinuestogrowasthenumber ofusersusingtheinternethasincreased.Anydevicewhich contains software functions can tend to have source code errors, logical errors, and flaws. Thus, the existence of detectiontechniquesismandatoryforsoftwarevulnerability remediationaswellasprevention.
Toavoidsuchsituationsmanualtesting,securityaudits,or codeinspectionsaretobeperformedbyhighlyskilledcyber security engineers or experts.Butasit islabour intensive and expensive and prone to errors; automating the above stepstodiscoverrespectivevulnerabilitiesforthesoftware applicationsisrequired.
An error or a flaw or a weakness of the application's sourcecodethatanattackerorahackercantakeadvantage ofisknownassoftwarevulnerability.Theseerrorstendto make the system function abnormally and undesirable actions.Theseflawsorerrorsincodemayariseduetothe lack ofknowledgeofthedeveloperorprogrammerwhois developingthesoftwareapplication.Theseflawsmayleadto system crashes, loss of data, reputational damage, major damagetothetargetedsystem,lossofcustomers,personal databeingexposed,etc.
Thecommonsecuritygoalsi.e.,confidentiality,availability, integrity,non-repudiation,andusability,canbeaffectedby thesoftwarevulnerabilities.
Following listed below are cyberattacks associated with softwarevulnerabilities:
Phishing: Phishing is a cyberattack that attempts to steal sensitiveinformation.Thissensitiveinformationcanbelogin credentialsandcreditcarddetails.Thisattackcanalsobea formofsocialengineeringwhereanattackertriestomislead theuserintoclickingamaliciouslinkcreatedbytheattacker, downloading some malicious attachments, or revealing sensitivedata.
DDoS Attacks: Distributed denial of service attack is an attempttospoilanonlineserviceorawebsiteoraserveror networkbymakingitunavailablebysendingmanyaccess requeststhatitcannotmanage.
Computer Viruses: Computer code or a program that modifiesthewayacomputerbehavesisknownasViruses. Theyaremeanttospreadthroughcontaminateddata,files, andinsecurenetworks.Andonceitentersthesystem,itcan replicateandspreadfromoneprogramtoanotherandinfect othercomputersystemsalso.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
Attack Vectors: Attack vector is a malicious term used to discoversystemvulnerabilitypoints,launchcyberattacksor installmalicioussoftware.Followingarethefourimportant attackvectors:Drive-by,Zero-dayattack,MITM(maninthe middle),SQLInjection.
Vulnerability Management System is not only intended to identifyandevaluatevulnerability,butitwillalsogeneratea detail report which will report of the vulnerability point foundinthesoftwareapplicationwhichwillbetested.
Inthissectionsummarizationoftheexistingresearchworkis done.Anewvulnerablemanagementsystemwillbecreated basedontheexistingworkwithadditionalfunctionality.
MădălinaAldea.[1]Theauthorinthispaperhasintroduceda new vulnerability management system i.e., SV – IMS –SoftwareVulnerabilityIntegratedManagementSystem.This system can perform security tests to detect software vulnerabilitiesandtheresultofthistestcanbeviewedupon a dedicated platform. It also gives defines the CVSS i.e., Common Vulnerability Scoring System, which is an international scoring system that describes how severe a vulnerabilityis.
Robert A. Martin.[2] The author in this research paper describesCommonVulnerabilityExposure(CVE)andOpen VulnerabilityAssessmentLanguage(OVAL)whichareapair ofinternational,community-basedeffortsamongstindustry, government,andacademia.WhereCVEisaimedtocreatea means for making vulnerability alerts more applicable to individual enterprises and OVAL is aimed to provide the meansforstandardizedvulnerabilityassessmentandresult in uniform and standardized information assurance parametersforsystems.
GeonLyang Kim.[3] The author of this research paper has introduced a new method for constructing and managing Vulnerabilitiesbycreatingavulnerabilitydatabase.Inthis researchwork,anewNationalVulnerabilityDatabase(NDV) systemiscreatedwhichcanbeusedbyvariousenterprises. While referring a new vulnerability found can also be registeredintheNVDsystem.
ManojKumar.[4]Inthisauthorproposedaframeworkthat usesaknowledgebaseandinferenceengine.Usingthisthe vulnerability management automatically takes required actions,classifies,prioritizes,andmitigatesthevulnerability. Theproposedsystemreducesthethreats,securityrisks,and reputationalandMontereyloss.
Chee-WooiTen.[5]ThisAuthorhasproposedaVulnerability assessmentframeworkthatevaluatesthevulnerabilityofthe SCADA system. This is done at three levels – System, Scenarios,andaccesspoints.Thisframeworkisbasedonthe system which has firewall and password models. This
proposedframeworkalsoevaluatestheimpactoftheattack launched and countermeasures are identified for improvementofcybersecurity.
Jan-MinChen.[6]Inthispaper,theauthorhasimplemented an automated vulnerability scanner that identifies the injection attack vulnerabilities. This system automatically examines the website to find the XSS and SQL injection vulnerabilities. The proposed system also uses NVD i.e., NationalVulnerabilityDatabase.
AndreyFedorchenko.[7]Inthisresearchpaper,theauthor has proposed the process of integrating a vulnerability databasesystem.Thisintegrateddatabasecanbeusedforthe further application of security systems. In this paper, the structureofthevulnerabilitiesdatabaseissuggested,andthe processofvulnerabilitiesdatabasegenerationissuggested.
TodevelopaVulnerabilityManagementSystem(VMS)which willdetectvulnerabilityusingsourcecodeandBinarycode analysis of the software product and also analyze the intensityofthevulnerabilityfound.
A hybrid algorithm is developed which automates the processofscanningsoftwareapplications.Themajorgoalof the proposed algorithm is to automate and increase the accuracyofvulnerabilitydetection.Althoughtheaccuracyis not achieved at 100% but an effort is made to put up the proposedsystemabovetheexistingsystems.Theproposed hybridalgorithmissimilartotheexistingalgorithms.The OWASP results are considered with the output for better reasoningandunderstanding.OWASPresultsareupdatedon theregularbasistoavoidanyinconvenience.
Theproposedsystem’shybridalgorithmismainlybasedon the concept of combining different features which are of differentcomponents.Thiswillresultinthenewalgorithm which will give more impactful results on the respective scans. Therefore, the combination of such features from differentcomponentshasbeendonebasedonoptimization andsophisticationamongothercomponentswiththegoalof increasingtheaccuracyorefficiencyofthehybridalgorithm.
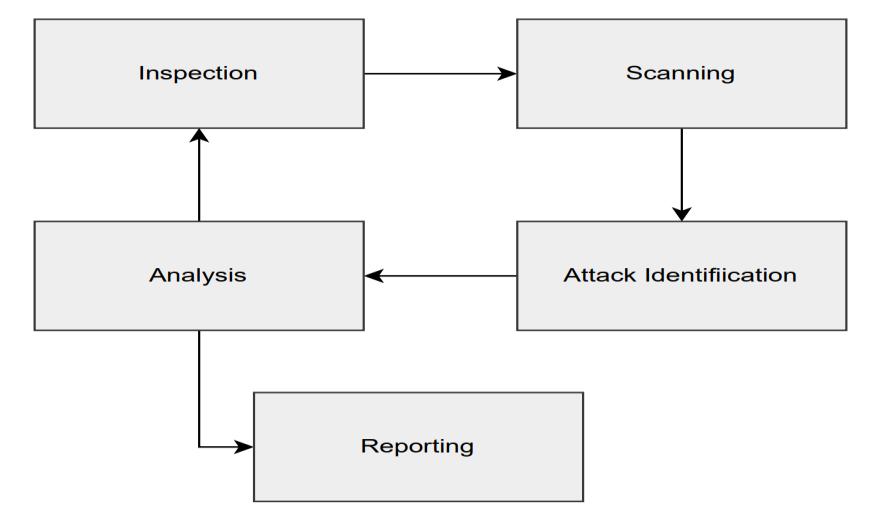
The Hybrid algorithm mainly consists of five phases i.e., Inspection, Scanning, Attack Detection, Analysis, and Reporting.Theinspectionwhichcanalsobecalledcrawling, mainly focuses on fetching information about the application.Themoreinformationgatheredinthisphasethe moresuccessfultheentireexecutedscanwillbe.Afterphase 1,phase2consists ofscanning.Scanningistheprocess in whichthealgorithmwillidentifytheweaknessofthesystem on which the scan is been initiated. Once the scanning
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page977

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
process is completed, the next step will be to identify the attacksorvulnerabilitiesandperformananalysistoidentify thevulnerabilitydefinitionandremediationmethods.Later Reportingphaseisinitiatedtogenerateawellinformative reportforthescanwhichwasperformed.
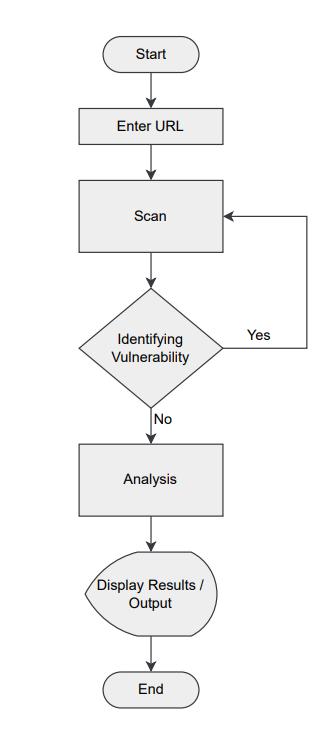
Theinitialstageaccordingtothephasediagramisinspection whichcanbecalledasrequirementorinformationgathering stage. After phase 1, the next process involves mainly crawling and parsing, and identifying new vulnerabilities. Phase 2 is repeated until all the vulnerabilities of the applications are not discovered. A further step includes analysis of the vulnerabilities found to identify proper definitions according to the OWASP and getting proper remediation for the same. Further, this analysis is summarized, and the final report is generated as an end result.
Input:Inputismainlyprovidedbytheuserwhoisgoingto initiatethescanning.ThisinputcanbeanIPaddressorthe URL fortheapplicationwhichneedsto bescanned bythe VMS.
Processing:Thisstepmainlyinvolvesfuzzing,crawlingthe pages,andidentifyingtheweakness,andlatervulnerabilities areidentifiedbasedontheweaknessesidentified.
Output:Outputwillbegeneratedaftertheproperanalysis processisdone.
Fig -1:ComponentofVMS
AdetaileddescriptionoftheflowforthedevelopedHybrid algorithm:
Fig -2:FlowchartforVMS
Fig -3:FlowchartforXSS
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
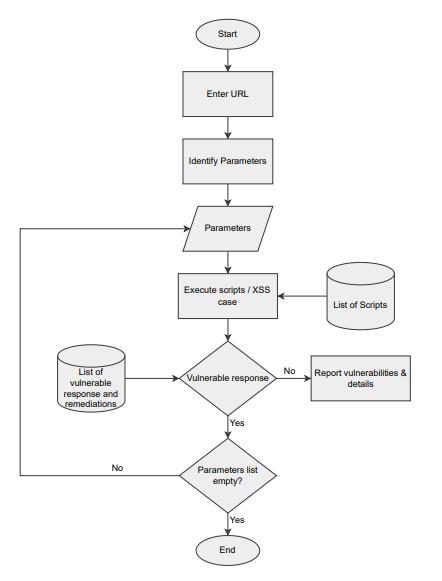
ManydifferentscanningmethodsareusedinVMSalgorithm, considering one following method is used for Cross Site Scripting:
1.ForeachURLinthelistofthevisitedURLs
a)Identifyallparameters
b)Pushtheparametersinthelist.
c)Foreachoftheparameterinthelist
i) give input as a XSS test case or script to the parameterandpasstherequest.
ii)verifytherespectiveresponse
2.ReporttheVulnerability
Theseexperimentsorpracticalwereperformedbyrunning different methods/tool with its respective scripts. These methodswereinstalledandexecutedonVirtualmachineand havethesimilarconfigurationsandresources.
For probing computer networks, Nmap offers several functions, including host discovery, service detection, and operating system detection. Scripts that offer more sophisticatedservicediscovery,vulnerabilitydetection,and other features can extend these features. During a scan, Nmap can adjust to changing network conditions, such as latencyandcongestion.
DirBusterisanapplicationwithaGUIinterfacedevelopedin Java. It is used to find concealed files and directories by brute-forcingfiles&directorieswiththeaimofgainingsome significant information that could help in cyber-attacks. A wordlist could influence how effective such a tool is; the more effective the wordlist, the more effective the instrument.
Cross-Site"Scripter"(alsoknownasXSSer)isanautomatic frameworkforfinding,usingandreportingXSSflawsinwebbasedapplications.Therearenumerouswaystoattemptto get around particular filters, as well as numerous unique codeinjectionstrategies.
ADNS(DomainNameSystem)debuggeriscalledDnswalk. Dnswalk carries out zone transfers for specified domains andexecutesprecisedatabaseintegritychecksinavarietyof ways.
5.whois:
A query and response protocol i.e., WHOIS, which is pronounced "who is," is frequently used for accessing databases that list the registered users or assignees of Internet resources like domain names, blocks of IP addresses, and autonomous systems. On most UNIX systems, the command-line utility used to do WHOIS protocol searches is called whois. Additionally, Referral WhoisisasiblingprotocolofWHOIS(RWhois).
6.Nikto:
Niktoisafreecommand-linevulnerabilityscannerthatlooks forunsafefiles/CGIs,out-of-dateserversoftware,andother issuesonwebservers.Checksarerunonbothgenericand server-specificlevels.Anycookiesthatarereceivedarealso recordedandprinted.ThedatafilesusedbyNiktotorunthe programarenotfreesoftware,buttheNiktocodeitselfis. Niktocanidentifymorethan6700potentiallyharmfulfiles andCGIs,aswellasversion-specificissuesonmorethan270 serversandobsoleteversionsonmorethan1250servers. Niktocanalsoidentifyinstalledwebserversandsoftware andchecksforserverconfigurationelements.
7.Dnsmap:
Dnsmap uses an internal or external wordlist to search a domain for common subdomains (if specified using -w option). There are about 1000 words in both English and Spanish on the internal wordlist, including ns1, firewall services, and smtp. Therefore, an automatic search for smtp.example.comwithinexample.comwillbeavailable.For additional processing, results can be saved in CSV and human-readable formats. Dnsmap should not be executed withrootprivilegesforsecurityreasonsbecauseitdoesnot needthemtofunction.
9.Uniscan:
An open-source program called Uniscan can check web applicationsforseriousflawsincludingcross-sitescripting, blind SQL injection, remote file inclusion, web shell vulnerabilities, and hidden backdoors, among others. In additiontoassessingvulnerabilities,Uniscanhastheability to search Google and Bing for domains using shared IP addresses.
Operating System: Kali Linux or Ubuntu OS or System configuredwithVirtualMachinewithsameOS.Thesystem andvirtual machinesspecificationsareas - processor,2.6 GHZ Core i5, 2 GB RAM, 100 GB HDD and OS as above mentioned.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page979

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
Fig -4:ScreenshotforwebappofVMStool
needs to be improved in order to complete the scanning quickly. To create an algorithm with the ability to identify morevulnerabilities,morestudyandresearchisrequired.
i)Improvecrawlingcapabilities:
Theproposedhybridalgorithmrequiresmoremethodsand functionsforcrawlingmechanismssothatVMSwillbeable to scan all the contents of any URL or a web application, withoutskippinganycontentofthewebpage
ii)ImproveAnalysisandReporting:
VMS algorithms need to improve the accuracy so that the identifiedvulnerabilitycanbestatedwiththeseveritylevel. To obtain high-end accuracy more sophisticated methods mustbeusedduringthescanningprocesswhichwillrequire more research and practical implementation of the algorithm. VMS system can be upgraded for analysis and reporting in such a way that the vulnerabilities can be visualizedandcanbeshowninarepresentablemannerwith theseveritylevels.
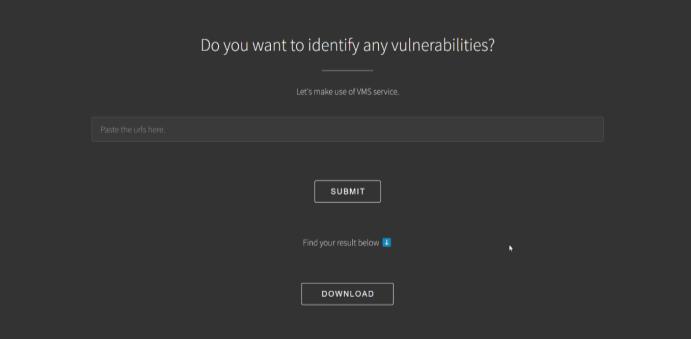
Fig -5:ScreenshotofVMSURLinput
iii)Reducingscanningtime:
Thereneedtobeproperresultswhichisgeneratedinshort timeframewithbetteraccuracyandreporting.Itneedsto improve overall scanning method using more scripts and identificationofmorevulnerabilities.
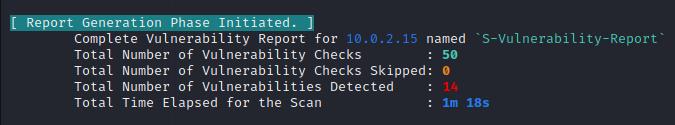
Fig -6:ScreenshotofVMStooloutput
Vulnerability Management System generated better and fasterresultsoverall.ItcanautomatetheVAandPTprocess tillparticularinstance.Also,itisabletoidentifythepresent vulnerabilities and specific remediation based on the vulnerabilityfoundandgeneratereportwithseveritylevels accordingly. The sole disadvantage is that, according to reports,ittakesmoretimetoscanthanthemajorityofthe web scanners utilized in this study. Although its performanceisnotperfect,comparedtoothertools,ithasa largercapacitytodetectmoreflaws.

The proposed Vulnerability Management System basedon the hybrid algorithm extensively work to identify vulnerabilitiesbasedonsoftware-basedapplications.Testing ofsuchapplicationsisdoneforsafeguardingit.Thesuggested hybridmethodpresentsadditionalvulnerabilitiesanddoes soinaprofessionalmannerwhenreportingthosethathave been found. However, because not all of the current vulnerabilities were completely scanned by the suggested hybrid approach. To make sure that "deep" crawling was carriedout,thealgorithm'scrawlingcomponentneededtobe increased.Theresultsalsoindicatethattheproposedmethod
[1] Mădălina Aldea, Daniel Gheorghică, Victor Croitoru, “Software Vulnerabilities Integrated Management System”, 2020 13th International Conference on Communications(COMM),IEEE,2020:pp.97-102,doi: 10.1109/COMM48946.2020.9141970
[2] RobertA.Martin,“IntegratingYourInformationSecurity Vulnerability Management Capabilities Through Industry Standards (CVE & OVAL)”, 2003 IEEE International Conference on Systems, Man and Cybernetics.ConferenceTheme - System Securityand Assurance, pp. 1528 – 1533), doi: 10.1109/ICSMC.2003.1244628
[3] GeonLyangKim,JinTaeOh,DongISeo,JeongNyeoKim, “The Design of Vulnerability Management System”, IJCSNS International Journal of Computer Science and NetworkSecurity,VOL.13No.4,April2013:pp.19–24
[4] ManojKumar,ArunSharma,“Anintegratedframework for software vulnerability detection, analysis and mitigation: an autonomic system”, Indian Academy of Sciences Sadhana Vol. 42, No. 9, September 2017, pp. 1481–1493,doi:10.1007/s12046-017-0696-7
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
[5] Chee-Wooi Ten, Chen-Ching Liu, Govindarasu Manimaran,“VulnerabilityAssessmentofCybersecurity for SCADA Systems”, IEEE Transactions on Power Systems,Vol.23,no.4,November2008,pp.1836-1846, doi:10.1109/TPWRS.2008.2002298

[6] Jan-Min Chen, Chia-Lun Wu, “An automated vulnerability scanner for injection attack based on injection point”, 2010 International Computer Symposium(ICS2010),16-18Dec.2010,pp.113–118, doi:10.1109/COMPSYM.2010.5685537
[7] AndreyFedorchenko,IgorKotenko,AndreyChechulin, “Design of Integrated Vulnerabilities Database for Computer Networks Security Analysis”, 2015 23rd Euromicro International Conference on Parallel, Distributed,andNetwork-BasedProcessing,4-6March 2015,pp.559-566,doi:10.1109/PDP.2015.38
[8] Armold; Hyla, Rowe, “Automatically Building an Information-Security Vulnerability Database”, 2006 IEEE Information Assurance Workshop”, 21-23 June 2006,pp.376-377,doi:10.1109/IAW.2006.1652119
[9] Ching-Huang Lin, Chih-Hao Chen, Chi-Sung Laih, “A StudyandImplementationofVulnerabilityAssessment andMisconfigurationDetection”,2008IEEEAsia-Pacific Services Computing Conference, 9-12 Dec. 2008, pp. 1252-1257,doi:10.1109/APSCC.2008.212
[10] Yu, Y., Yang, Y., Gu, J., & Shen, L. (2011). Analysis and suggestions for the security of web applications. In ComputerScienceandNetworkTechnology(ICCSNT), 2011InternationalConferenceon,Vol.1,pp.236-240
[11] Pravin Kharat, Pramila Chawan, “Vulnerability Management System”, 2021 International Research JournalofEngineeringandTechnology(IRJET),25-28 Nov2021
PravinP.Kharat M Tech. Dept. of Computer Engineering–NIMS,VJTI, Mumbai Prof. Pramila M. Chawan, is workingasanAssociateProfessor in the Computer Engineering DepartmentofVJTI,Mumbai.She has done her B.E. (Computer Engineering) and M.E. (Computer Engineering) from VJTI College of Engineering, Mumbai University.
Shehas28yearsofteachingexperienceandhasguided 85+M.Tech.projectsand130+B.Tech.projects.She haspublished143papersintheInternationalJournals, 20papersintheNational/InternationalConferences/ Symposiums. She has worked as an Organizing Committeememberfor25InternationalConferences and 5 ICTE/MHRD sponsored Workshops/STTPs/FDPs. She has participated in 16 National/International Conferences. Worked as Consulting Editor on – JEECER, JETR, JETMS, TechnologyToday,JAM&AEREngg.Today,TheTech. WorldEditor–JournalsofADRReviewer-IJEF,Inters cience She has worked as NBA Coordinator of the ComputerEngineeringDepartmentofVJTIfor5years. ShehadwrittenaproposalunderTEQIP-IinJune2004 for ‘Creating Central Computing Facility at VJTI’. Rs. EightCroreweresanctionedbytheWorldBankunder TEQIP-I on this proposal. Central Computing Facility wassetupatVJTIthroughthisfundwhichhasplayeda keyroleinimprovingtheteachinglearningprocessat VJTI.wardedbySIESRPwithInnovative&Dedicated Educationalist Award Specialization: Computer Engineering&I.T.in2020ADScientificIndexRanking (WorldScientistandUniversityRanking2022)–2nd Rank- Best Scientist, VJTI Computer Science domain 1138thRank-BestScientist,ComputerScience,India.
