International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
Yojana Patil 1 , Prof. P.S. Powar 2
1student, computer engineering, AMGOI wathar, Maharashtra India
2 Professor, computer engineering, AMGOI wathar, Maharashtra India ***
Abstract - Nowadays, photos are shared through social media, and we got to the security of photos. Thus, we'd like to use coding and steganography techniques to hide the critical message in the image and the other way around. Within the planned system, we tend to apply a lossless reversible process for embeddingandextracting the info. Reversibleinformation concealing may be a technique wherever we infix personal data into a cowl image by slightly modifying the pixel values. This Paper used the replacement methodology of mixing the model like convolution neural networks and generative adversarial networks to get meaningfulencryptedpicturesfor RDH. The four-stage specification is intended for the experiment, together with the concealing network, the encryption/decryption network, the extractor, and the recovery network. First, the critical information area unit is embedded into the image within the concealing network through residual learning. Then, within the encryption/decryption network, the quilt image is encrypted into a meaningful image, referred to as the embedded image, through GAN, then the embedded image is restored to the decryptedimage. The initial imageisrequiredtoberecovered; thus, the hidden message is extracted from the receiving aspect. The many applications like social control, medical applications, for example, are keeping patients' data secret, and military applications where the property ofsecret hidden information is in high demand. Also, this application desires lossless recovery of the initial image. Another approach is calculatingthe embeddingcapability oftheimageandfinding the standard of image exploitation SSIM
Key Words: Data Hiding, Deep Neural networks, GAN model.Digitalfootageiswidelyusedinmedia,publishing, medicine, military, and alternative fields. To preserve the integrityofphotographs,itisimperativenottowastetheir content.Theimagehasitsowncharacteristics,suchaslarge amounts of data, high co-relation, and a common secret writing formula. On top of functions, such as image authenticationandwatermarking,avarietyoftechnologies have been developed for footage. Data concealment is a branch of digital watermarking technology that may be essential to confirming the security of a subject matter. Knowledge concealment could also be implemented in variouswaystocomprehendtheaimofuseableembedding
of secret data. Whether or not or not the receiver can recover the quilt image, data Concealment could also be divided into irreversible data concealment and reversible dataconcealment.Informationconcealingwithinthefootage could also be how by that the initial cowl will losslessly recoveroncetheembeddedmessagesunitofmeasuringis extracted, e.g., image data, labels, notations, or authenticationdataintotheencryptedfootage,whereasnot accessing the initial contents. We propose a Reversible Image Transformation (RIT) framework. RIT-based frameworksshifttheprimaryimage'scontenttothecover image'scontent,andsodefendtheprivacyofthe primary image.Qualitysuggeststhattheywillbelosslesslyrestored from the reworked image. therefore, RIT has commonly viewedasasecretwritingthemereferredtoas"Semantic Transfer secret writing (STE)."Because the camouflage image may be quite a plaintext, it's going to avoid the notationoftheoutsiders.So,theoutsiderscanimplantmore dataintothecamouflageimagewithancientRDHmethods forplaintextfootage.
Reversible info concealing inside the encrypted image (RDHEI) has become a hot topic, and plenty of algorithms square measure projected to optimize this technology. However, these algorithms cannot deliver the good'sstrongembeddingcapability.Thus,throughoutthis Paper,wetendtoproposeaclassyRDHEIthemesupported bylosslesspartconversion(LPC).UnlikethepreviousRDHEI algorithms, LPC is galvanized by the planar map coloring question.Itperformsadynamicimagedivisionmethodology todividetheinitial imageintounstable regionsinstead of regularblocksinsidethepreviousRDHEIalgorithms.Inside the technique of LPC, part conversion is performed by region;thatis,pixelsinsideidenticalsquaremeasuresare regeneratedtothesameconversionprice,whichmayoccupy asmallersize.Therefore,theaccessibleareaisreservedto accommodatemoreinfo.LPCcouldalsobeaprocess,sothe initialimageislosslesslyrecoveredonthereceiverside.
WeimingZhangET.Alsuggestedimprovingtheproposed schemeotherwise, plans to encrypt the image code first a pictureonthehood.Atransformedimagerenderslinguistics original linguistic image of another incarnation and goals Mysteryofthefirstimagewiththesamesize.Becauseheis converted Image transformation and restoration of the
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
originalimagefromthefileencryptedimageintotallossand safemodificationAddition2RDHstrategiesalongwithPEEbased RDH e Units in the UES area have been adopted to includeadditionalinformationinthemencryptedimageto fulfillvariousrequestsfortheimage,forexampleAbilityto abstract [1]
Zhenxing Qian et added that the paper proposes a reversiblerecordingschemehiddeninencryptedpixelsusing distribution supply coding. After encrypting the original image, the fragments of the MSB plane are identified and compressedtoaccommodatetheadditionalmysteryfiles.On thereceivingside,thehiddenrecordsareremovedonlywith theembeddedkey,andtheoriginal imageisrestoredonly with the encryption key. When each of the embedded and encryptedkeysmustbedifficultfortherecipient,thehidden recordscanbecompletelyremovedandtheoriginalimage perfectlyrestored [2]
In this article, Xiaochun Cao et al. develop a unique techniquecalledHC_SRDHEIthatinheritstheadvantagesof RRBE and the variable property of RDH strategies in encryptedimages.Isourtechniqueusedmuchmoretohide information compared to the other progressive options? Information hiding is simply an element substitution to replacetheofferedspacewithadditionalsecretdata.Theunit areaforinformationextractionandthecanopyimagecanbe separated, and the unit area is error-free. Experimental resultsonthreedatasetsindicatethatouraverageMERwill approachone.Seventimeslargerbecausethepreviousbest othertechnology.Theperformanceanalysissuggeststhatour design approach has excellent potential for meaningful applications. [3]
Xinpeng Zhang proposeda painting proposing lossless, reversible, and mixed record concealment schemes for ciphertextcontentencryptedusingpublic-keycryptography withprobabilityandhomomorphismproperties.Inlossless mode,thepixelvaluesoftheciphertextcontentarechanged to new values to embed the additional entries in the LSB plans of the ciphertext content pixels. In this way, the embedded records can be extracted immediately from the encrypteddomain,andtheembeddingprocessoftheforms no longer interferes with the decryption of the plaintext's uniqueimage.Inthereversiblescheme,thereductionofthe histogramispre-processedbeforeencryption,and1/2the pixelvaluesoftheciphertextcontentaremodifiedtoembed the records. On the receiver side, data can be extracted in plaintextform. [4]
ThisishowJ.MalathiimplementedaRICH(StableImage Data Hiding) argument in the cryptographic domain. It demonstrates a public key change mechanism that allows NorthAmericatoimplantdatathroughpureXORoperations even when they no longer need access to the critical encryptionkey.Forthedecoderfunction,itisrecommended to use a strong two-elegance SVM classifier to distinguish
value:
betweenencryptedandunencryptedimagepatches,North AmericanactivesanctionsintheUSseparatetheembedded messagetogetherandthenthesingledeadimagesignal [5]
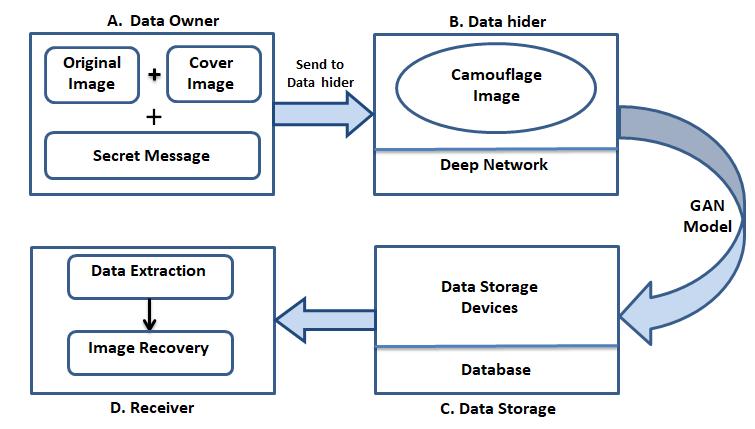
In proposed system develop a system that implements camouflagesthatallowuserstoembedadditionaldatainto camouflages without accessing the original content, it is necessarytorestoretheoriginalimage,ideallywithoutloss, andtocompletelyremovehiddenmessagesona receiving side.
Thesystemhasthefollowingmodules.
A. DataOwner
B. DataHider
C. DataStorageDevices
D. Receiver
Thedataownerareatakescareofthat
a.Inputimage:Theoriginalcoverimageisacolorimage
b. Encrypt one image into another image: The original imageisencryptedintoanotherplaintextimageusingakey. Inthenextstep,camouflageimagesaregenerated,andthey areinputintothedatahider.
The Data Hider section has some of the following functionalities.
a. Data Encryption: Secret data is embedded into camouflageimagesusingadata-hidingkey.InputtotheData storagedeviceisacamouflageimagewithpersonaldata.Data storagedevicesarethenextmodule.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
TheDataStoragedevicessectiondealswith
a. DataEmbedding:Stored(maybeexternal)additional information on camouflage images can be located usinganyRDHdisplaytoopenpicturesoftext.
b. Data Removing: The Storage devices (maybe outsiders)canbeaddedtoCamouflagePhotosusing any classic flat RDH imaging method. The camouflageformattedimageisforwardedandthe dataisaddedasaninputtothereceiver.
Therecipientcanbetheownerofthecontentorsomeone with an authorized key; the receiver will have the key for decryption.
Imagedecryption:Acamouflage imagesoformedfrom the data hider is received by the receiver. The idea was retrievedusingthedecryptionkey
1.Embedding additional data (Text/Audio) into camouflageimagesinareversibleandlosslessmanner.
2.Camouflageimagequalityshouldbeimproved.
3. Deepneuralnetworksareusedtoembedandextract datafromimages
4.TogenerateaGAN(GenerativeAdversarialNetwork) forreal-timesteganography.
5. The original plaintext image must be recovered withouterror
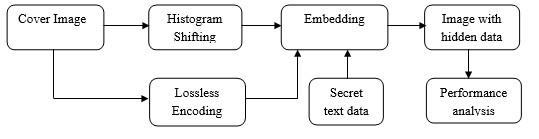
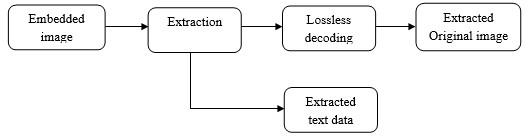
Reversibledatahiding(RDH)coversdataandrecovers theoriginaldataafterward;embeddeddataisremoved.This methodiswidelyusedinmedical,military,andlawforensics imagery.Thereisnotolerancefordistortionoftheunique cover. In the meantime, RDH has been a subject of substantialinvestigationsinceitwasfirstpresented.
Fig.2.RDHEmbedding RDH Extraction
Fig.3.RDHExtraction
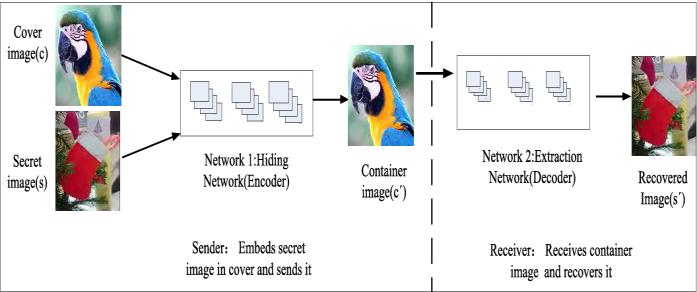
2.GAN(GenerativeAdversarialNetwork)Model
Withtherapiddevelopmentofinformationtechnology, the transmission of information has become strategic. To preventinformationfromchildren,informationsecuritymust beassessed.Therefore,theartofconcealinginformationhas becomeapopularsolution.Inparticular,thereversibledata concealment(RDH)techniqueusesthesymmetricalmethod oftransferringandprocessingsymmetricaldatainthecarrier envelope. Not only can undetected and fully-recognized secret information be transmitted, but it can also be recoveredwithoutanycorruptionbythemediaenvelope.In addition, encryption techniques can protect your email serviceandyourinformationprivately.However,thevector isanencryptedformofciphers,whichhasastronglikelihood ofattractingattackers.Counter-generativeNetworks(GANs) generateencryptedimagesforRDHsignaling.Thenetwork architecture is designed for a four-phase test, including a hiddennetwork.
Fig4.ArchitectureofGAN
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
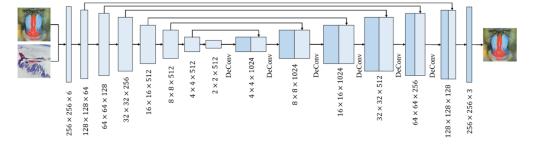
AGANnetworkarchitectureissimilartoaU-Netnetwork structureintermsofitsparametersettings.Therearetwo phasesinthehiddennetwork:acontractionphaseandan expansion phase. Convolutional neural networks typically haveashrinkingphase.InsteadoftheU-Netnetworkoutput, thisonehasa 6-channel 256x256cascadefunctiontensor inputthatissupplementedbya4x4convolutionlayerafter eachdownsampling.Inordertospeedupthetrainingofthe network, each convolution is followed by a LeakyReLU activationfunctionandabatchnormalizationoperation.The leakageruleandbatchnormalizationlevelareusedinthe no-functionmodeltoincreasenetworkspeed
LeakyRelu:-ItisaRelubasedactivationfunction.This functionrunsthegentleslopefornegativevaluesinsteadof convertingthemtoaregularslope.ALeakyCorrectedLinear Scale or Leaky ReLU could be a type of trigger operation supported by Relu; However, negative values indicate a gentlesloperatherthanaflatslope.Inaddition,theincrease constantisdeterminedbeforethecoaching,e.g.nolearning takes place during the coaching. Leaky ReLU runs an improved version of the ReLU activation tool. For ReLU activationwork,thegradientiszeroforallnon-zeroinput values, which could disablethe neurons in the region and should cause the ReLU feedback to die. Leaky ReLU was developedtoaddressthisdisadvantage.InsteadofaReLU activationprocessactingaszerofornegativeinputvalues (x),wetendtorepresentitasasmalllinearelementofx.
f(x)=max(0.01*x,x).
Thereisacontractionphaseandanexpansionphasein thehiddennetwork.Convolutionalneuralnetworkstypically have a shrinking phase. The U-Net network input is a cascaded256x256six-channelfunctionalitytensor,whichis further enhanced during down sampling by four-channel convolutions.ALeakyReLUactivationfunctionandabatch normalizationoperationfolloweachconvolutiontospeedup thenetworktrainingprocess.Everytimeadownsampling step is performed, the number of functional channels is doubled. The number of main channels after seven down sampling operations is 512, and the feature map is 2 × 2. Oversampling the feature map with a deconvolution level (DeConv) smooths the number of main channels in the
dilation step. As a result, all oversampling operations are cascadedwiththefeaturemapfromthereductionstage.
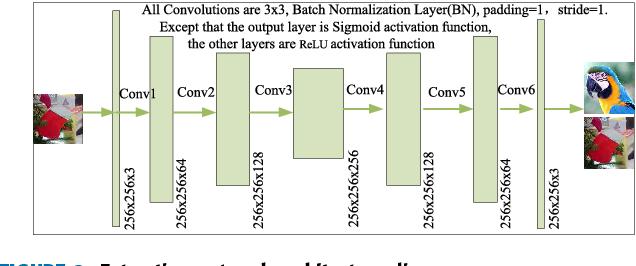
Information can be accurately retrieved from hidden networksusinganextractionnetworkarchitecture.AtCNN, thetaskoperation,theactivationfunction,andthepooling levelareusedtoimprovethenonlinearlearningabilityofthe neuralnetwork.Thehiddennetwork,thedesignednetwork, has six layers of convolution. CNN is used to learn fitting parametersusingnonlinearcapabilities.Ateachlevelofthe network, weight parameters are learned to adjust the mappingbetweeninputsandoutputs.TheeffectsofCNNare similartothoseoflinearmultivariateequationsifthenonlinearoperationsareignored
PearsonCorrelationCoefficient
Correlation:Thecorrelationcoefficientexpressestheratio between the produced images and the original (uncompressed).ρwascalculatedasthePearsonCorrelation Coefficient(CSP)betweenimages.
1.
Yi=Ek(Xi), where Ek () is the encryption function and Yi is the correspondingcipher-texttoXi. ThesizesofXiandYiareidentical.
Xi=Dk(Y0i)ifσ(Dk(Y0i))<σ(Dk(Y1i))=Dk(Y1i)else.
ShowingQualityofImagewithPSNR
3. An illustration's peak signal to noise ratio (PSNR) represents the ratio between the maximum power of a picture and the power of corrupting noise that affects its quality.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
1. Main Option for Users
4. An expert's Mean Square Error (MSE) or Mean Square Deviation(MSD)measuresthecommonerrorsquares,i.e., thecommonsquaredifferencebetweencalculableworthand truevalue.Thefirstmomentofthesquareerrorlossismy favoritemomentinthisriskyoperation.
5. SSIM- Structure similarity (SSIM) index for grayscale image or volume A mistreatment referee because of the referenceimageorvolume.Aworthnearertooneindicates higherimagequality.
SSIM( , )
ThePearsonmethodiswidelyusedinstatisticalanalysis, patternrecognition,andimageprocessing.Inthiscase,the applicationsincludetwoimagesdisplayedinoneimagefile 7.Embedding
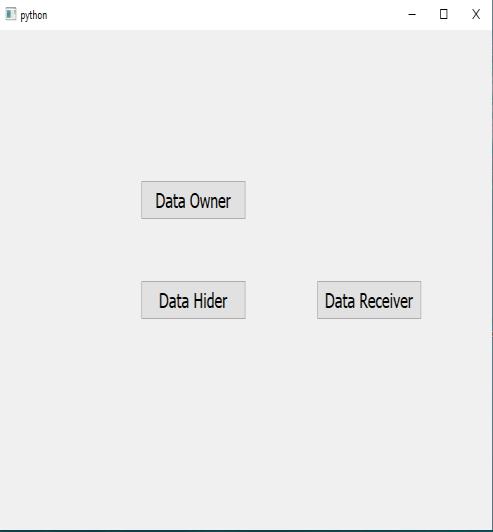
Fig.7.MainWindowofProject
Fig.7showstheProject'sMainWindow,wheretheData owner,Datahider,andDatareceivercanloginfora furtheroperation
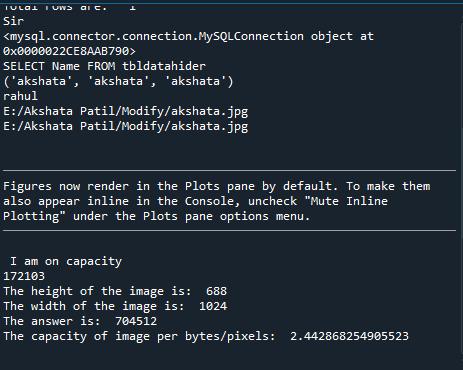
2.CalculationofEmbeddingCapacity
Fig.8.CalculationofEmbeddingCapacity
Fig.8showstheembeddingcapacityoftheimageper bytes/pixels.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
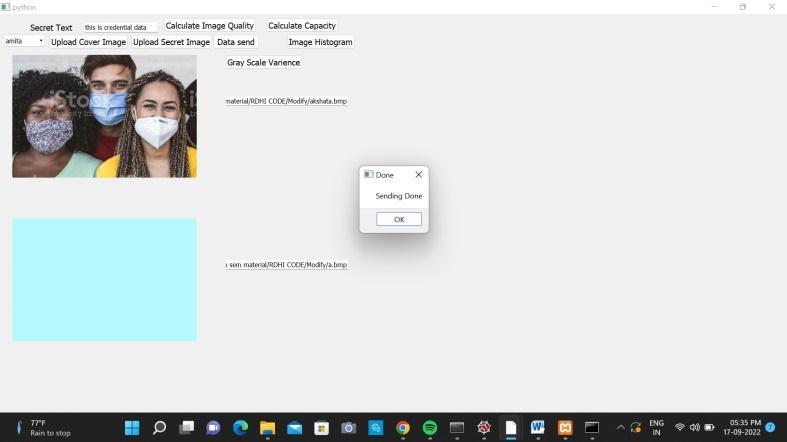
Thefigureshowsthecreationofacamouflageimagewith secretandcoverpicturesandtheentryoftheencryptedfile name by the data hider. Due to the reversibility of the technique,wecombinethetwoimagesintoasingleimage
Fig.11.GANModelEvaluation
Fig.11ShowstheGANModelevaluationanditeration.
6.Metricsforevaluatingimagequality
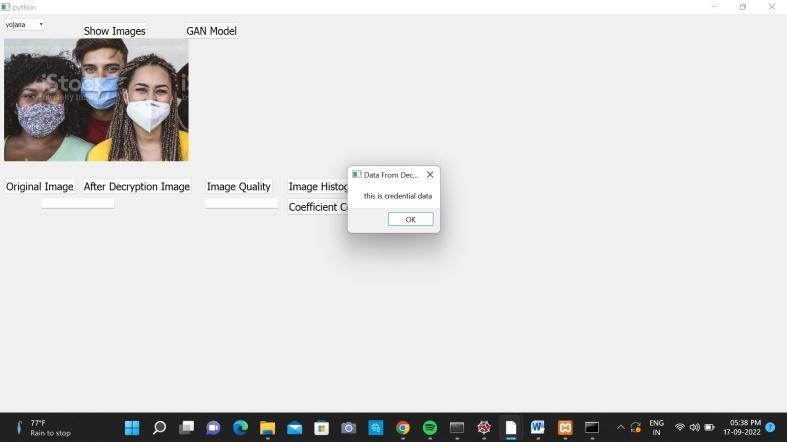
Thereceivercandecrypttheauthorizedfileasshownin Fig.10.Todecryptthefile,weuseanetworkofencoders anddecoders
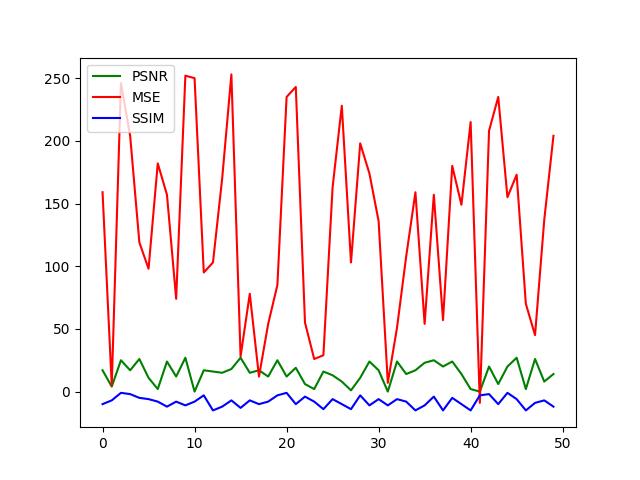
Fig.12ThischartshowsPSNR,MSE,andSSIMasImage QualityEvaluationMetrics
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
Table -1: EvaluationMetrics.
ImageName PSNR MSE SIM
Me.jpg 28.84 254.60 0.89 Devscript.jpg 30.37 178.83 0.86 Test.jpg 39.10 23.96 0.98 Test1.jpg 39.93 19.78
Table1.EvaluationMetrics.
Likealternativehistograms,apicture'shistogramalsoshows frequency.Picturebargraphs,however,showthefrequency ofpixels'intensityvalues.Apicturebargraphshowsgray levelintensitiesonthex-axis,andtheirfrequencyontheyaxis.
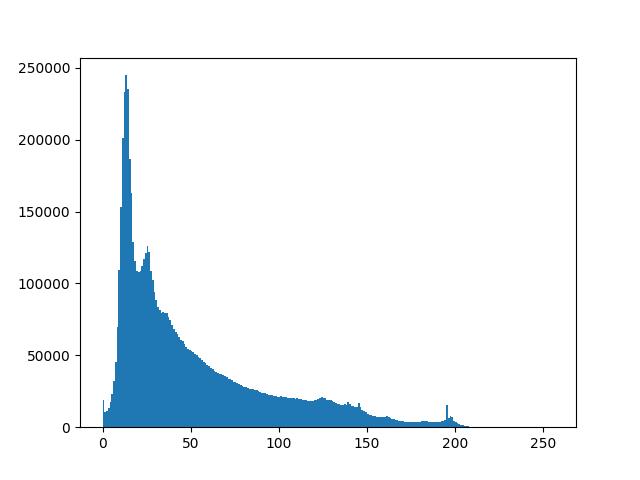
Thisbarchartshowsthevariationinpixelvaluesonthexaxis.It'saneight-bitimage,sothereare256levelsofgrayin it.Asaresult,thex-axisrangesfromzeroto255withaspot offiftybetweenthem

Using the color image process leads to 2 main factors; Foregroundcolorcanbearobustdescriptorthatmakesit easier to spot and extract objects from a scene. Second, a manrecognizesthousandsofshadesofcolorandintensity comparedto24shadesofgray.IntheRGBmodel,eachcolor appearsinitsmainspectralcomponents,red,neutral,and blue. This model is based on the Cartesian coordinate system. Images drawn in the RGB color model contain 3element images. One for each primary, when these three phosphorescent screen images are fed into the associated RGB screen, they combine to provide a composite color image.Thenumberofbitsrepresentingeachelementinthe RGBpackageiscalledelementdepth.ConsideranRGBimage assignedindegreeswhereeachofthebluecolorimageshas noexperiencewithan8-bitimage.
Fig.15showsthegrayscalevariance 11.Co-EfficientCorrelation

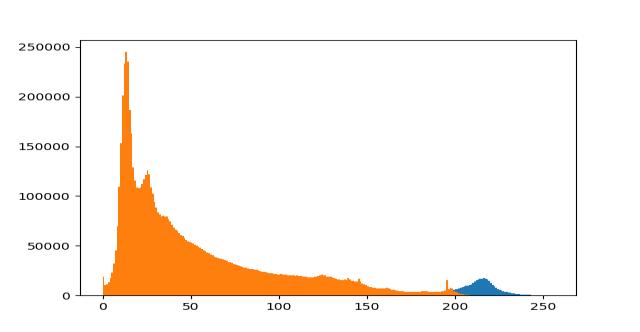
Acountoftheseintensitiescanbefoundontheyaxis.The graphshowsthatalmostallofthebarswithhighfrequencies arewithinthehalfportion,whichisdarker.Meaningthatthe imagewe'vegotisdarker.Andthismaybetestedfromthe imagetoo
Fig.16.Co-EfficientCorrelation
Fig16ShowstheCo-Efficientrelationbetweenimages
Usingreversibleimagetransformation(RIT),wepresenta reversible data concealment framework (RDC-EI). Unlike previous frameworks that encoded plaintext images into ciphertext,thisoneencodesplaintextimagesintociphertext. Embeddinganimageintoanothershotprotectstheprivacy oftheimage.Thus,encryptedphotoshavesomeofthesame shapesasplaintextimages.Dataencryptionanddecryption wereperformedusingCNNandGANmodelsinthispaper. Thistechniquebeginswithembeddingcapacity.Minimizing iterations and improving accuracy are achieved using Self GAN
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
[1]W.Zhang,H.Wang,D.Hou,N.Yu,“ReversibleDataHiding inEncryptedImagesbyReversibleImageTransformation,” IEEETransactionsonImageProcessing,2016.
[2]“Reversible Data Hiding in Encrypted Image with DistributedSourceEncoding”IEEETransactionsonCircuits andSystemsforVideoTechnology2016”Z.Qian,X.Zhang.
[3]X.Cao,L.Du,X.Wei,DanMeng“High-CapacityReversible Data Hiding in Encrypted Images by Patch-Level Sparse Representation” IEEE TRANSACTIONS ON CYBERNETICS, 2015.
[4] X. Zhang, J. Long, Z. Wang, and H. Cheng “Lossless and ReversibleDataHidinginEncryptedImageswithPublicKey Cryptography”IEEETransactionsonCircuitsandSystems forVideoTechnology,2016.
[5]J.Malathi,T.SathyaPriya“SecureReversibleImageData Hiding Over Encrypted Domain via Key Modulation” InternationalJournalofAdvancedResearchinComputerand CommunicationEngineering,vol.6,Nov2017.
[6]X.Zhang,J.Long,Z.Wang,andH.Cheng,“Losslessand ReversibleDataHidinginEncryptedImageswithPublicKey Cryptography”IEEETrans.onCircuitsandSystemsforVideo Technology,2015.
[7]J.Zhou,W.Sun,LiDong,etal.,"Securereversibleimage data were hiding over encrypted domain via key modulation," IEEETrans.onCircuitsandSystemsforVideo Technology,vol.26,Mar.2016.
[8] Z. Qian, and X. Zhang, "Reversible data hiding in an encrypted image with distributed source encoding," IEEE Trans.onCircuitsandSystemsforVideoTechnology,vol.26, Apr.2016
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page870
