International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
1
, J S Rajashekar2
Student1 , Professor2 , Department of Electronics and Instrumentation Engineering Dayananda Sagar College of Engineering, Bangalore, India ***
Abstract - The Internet of Things (IoT) is a network connected objects like sensors; actuators, electronics and software that are future requirements of any industry and modern society. These embedded systems are made to provide state-of-the-art facilities to exchange data over the internet. IoT technology can be efficiently used in various sectors like agriculture, healthcare, transportation, water and wastewater management, product manufacturing, power generation & distribution etc. Blockchain has emerged as a key technology is quickly rising to the top, especially considering its widespread use. The integration into workplace networks still faces some difficulties. IoT raises security and privacy issues because data authentication and exchange are handled solely through the central server. The main server model and blockchain technology is added while a component about IoT to label such certainty and problems. Three primary characteristics, namely, extensibility, inactivity, and network longevity, impact security measures without them, internal attack mitigation would be difficult. Using block chain can upgrade net conservation, efficiency and certainty. Recovery after events is fairly simple because the block chain stores the entire history of modifications to device configuration.
Key Words: Blockchain Technology, Internet of Things (IoT), Sensors, Embedded Systems, Data authentication
Dataisgatheredfrommultipleselector,sensors,andapparatusinamanufacturingsettingtherighttoapproachand commandthedata,isthedataitself.ItisbeingcreatedbythingsthatareallowingontheInternet,likeIndustrialIoTrefersto such a circumstance (IIoT). The development of Industry 4.0 and the IIoT creates opportunities for connecting preprogrammedcomputercontrolschemesforremoteobservationandquickresponsetosituationsnecessitatingconcurrent handling.Additionally,theuseofsensorsmayresultinanumberofbenefitsoverotherindustrialarchitectures.Blockchain, often known as a Distributedashared ledger, is a cryptographically protected, unchangeable store of information. Digital advantagecanbetradedandstoredwithouttherequirementforoutsidesupervision.Devicesthatdownloadconfigurationfiles fromacentralizedservermusthaveconfidenceinthatauthority;otherwise,thedeviceissusceptible.Ablockchaineliminates theneedforacentralizedauthority.Peer-to-peeristhedirectexchangeofstrengthbetweendevices.
InInformationtechnology,theterm"InternetofThings"referstothelinkbetweenon-devicesandtheinternet.The devicesshouldbeconnectedwirelessly,openingupnewopportunitiesforsysteminteractionsaswellasnewpossibilitiesfor themanagement,succeeding,andinitiationofimprovedserviceability.IoTadeviceshaveperformanceandresourcelimitations bydesignwhencomparedtonetworkdevicesinenterprisecontexts.Whencreatingmanagementandmonitoringsystemsfor IoTdevices,thismustbetakenintoaccount.IoTdeviceheterogeneityemploysmultipleconfigurationsandoffersvariedlevels ofmonitoringfordiversereasons.Enterprisenetworksettingssimilardeviceheterogeneitymakesitpossibletoadaptcurrent networkmonitoringandmanagementtoolsforIoTimplementation.Asthebackboneofcommunicationwithincommunitiesor businesses,undertakingnetworksandpopularentrancenetworksareacommonlyusedpresentingenablerglobally.Theentire enterprise sector is in constant need of stronger, more secure connection for all nodes. Networks are being developed systematicallyandareopen to new ideas.Theprimary innovation needto be on thefollowing crucial elements boosting networkefficiency,boostingsecurity,anddecreasingusingblockchaintechnologytosavemaintenanceexpenses.
The term "System Requirements Specification"(SRS) or "Requirements Specification" is used in the requirements engineeringcommunitytorefertoacontractthatdetailsvariouspracticalissuesofastructure,generallyafirmwaresystem andalsosometimesasystemthatcombinessoftwareandhardware.Throughoutvariousphasesoftheforecastlifecycle,an SRSisusedtohelpthemajorstakeholderssharethesystem'svision,aswellastostreamlinecommunicationandthegeneral projectadministrationandsystemevolutionprocesses.AbetterSRSoffersanumberofadvantages,includingestablishingthe foundationforaccordancebetweenthepurchaserandthesupplierprovidingabasisforapproximatebudgetandprogramme, offeringacontrolforconfirmationandaffirmationandservingisafoundationforfuturepreservationactivities.ASRSmay further be included in contracts or request for proposals documents related to a project. A SRS typically attach to a
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
predeterminedarrangementthatprovidesaspecificdocumentconstruction andadditionalusefulsuggestions.SRStemplates must,bydefinition,bemodifiedandtailoredtotherequirementsofthecompanyinquestion.
Thisstageinvolvesdeterminingtheproject'sfeasibilityandpresentingabusinessschemethatincludesaverysimple projectoutlineandsomecostevaluate.Duringsystemanalysis,thefeasibilityofthesuggestedsystemmustbestudied.This willsecurethattheofferedresolvewon'tputatensiononthecompany.
Akeydocument thatestablishes theframework for the processof productadvancement istheSystem Requirement Specification(SRS).Itincludesadescriptionofthestructure'skeyfeatureinadditiontoitsrequirements.ASRSissimplyan organization'sassessmentofaclient'sorpotentialclient'soperationalneedsandcircumstancesatacertainmomentintime priortoanyrealoutlineorimprovementwork.Itisasymbolicprotectionschemethatensuresespeciallyatanyspecifiedtime, theassociationandathecustomerarebothawareoftherequirementsofexchangefromthatperspective.Theinclusionof programmingrequirementinformationreduceseffortrequiredforadvancementsincecarefulreviewofthereportcanfind oversights,falseassumptions,andvariabilityearlierintheimprovementcirclewhentheyaresecuretofix.AlthoughtheSRS may required to be modified, it does supply a substructure for moving forward with creation assessment. Simply said, determiningthenecessityofprogrammingisthefirststepineveryproductimprovementprocess.Decodingclientthoughts andinformationintoaformalarchiveiswhattheSRSreferstoastheoutputoftheprerequisitestage.Therefore,thestage's outputiscomposedofformal requirementsthatare,ideally,completeandconsistent,whereasthe data lacksall ofthese characteristics.
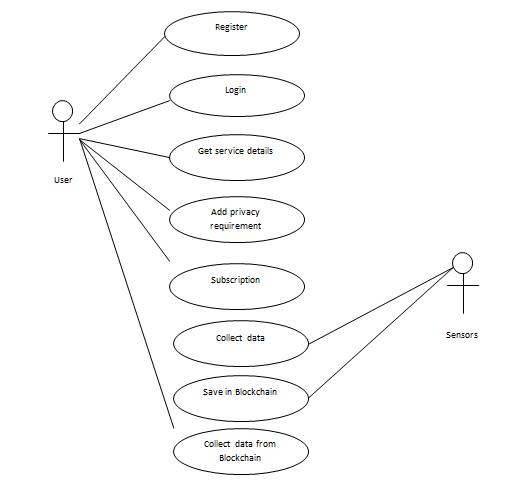
Functionalrequirementsspecifyhowasoftwarestructureshouldworkandcountertospecificinputsorconditions. Computations,dataclearing,andotherlimitedfunctionalitymaybeamidstthem.Oneofthemostcrucialelementsintermsof theoverallmechanismofmodulesistheproject'sfunctionalrequirements.Fig1showstheentrydetailsintheSRSsoftware, Serviceproviderscanregister,adddeviceinformation,addprivacypolicies,andadddevicespecifications.Transferredfromthe sensortotheserver,theinformationissavedintheblockchain,theuserhasaccesstothesensorinformation,andtheusercan makepayments.Theframework mustprovidecrucialsecurityinaddition tobugpreventionandmustpreventtheentire processfromcollapsing.Securitybecameamajorworryforanassociationwheninnovationbegantoadvanceatarapidpace. Givingsecurityrequiresasignificantinvestmentoffinancialresources.Bugtrackingensuresthatunauthorizeduserscan't accesscrucialissuedatawithoutpermissionwhiledeliveringthehighestlevelofsecuritycurrentlypossible.Multipleverified clientsreceivedifferentmysterypasswordsfromthebug-followingframework,resultinginlimitedfunctionalityforallclients.
Fig 1: IoTdevicesregistrationonBlockchain.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
Thesystemwillbeusedcontinuouslybymanyfactors.Performancebecomesasignificantconsiderationastheframework willberunonauniquewebserverandasingleparticularserverthatarebothunseen.Althoughseveralcustomersareusing the framework continuously, it shouldn't fail. All of its customers should be able to access it quickly. For instance, there shouldn'tbeanyirregularityconcurrentlyiftwotestspecialistsaresimultaneouslytryingtonotifythelocationofabug.
Focusingonthesubsequentchallenges,suchasconfirmation,exposure,andempiricalofIoTorwirelessasensorsinthe industrialaplatform, is necessary fully govern every smart device. We must make sure that the individuals tracking the product'smanufactureordocumentationarereputableandpossesstheappropriatecredentials.Eventhoughindustry4.0uses smartdevicestohandlealldataandactivities,therearestillsomesecurityconcernsthatcouldcompromisesensorsandIoT devices,henceexponentiallyslowingdowncorporategrowth.Therefore,itisnecessarytoindexingeachsensorthatrecognize dataintotheblockchaingridinordertogiveclarityandtrackwhereaboutsofeachemployeeandproduct.Additionally,itis necessarytoregularlygatherandverifydatafromeachregisteredIoTdevice.SothatoncetheinformationorIoT/sensorsare cast,nothingshouldbeuptoexchange,adjust,orpaththem.Blockchaintechnology,whichallowsforeasytrackingofalldevice activities including data collection, product documentation, manufacturing, and shipment, can, however, resolve these concerns.Thecompromisedsensorordevicemayenterthesystemfastoreasily.Asaresult,beforeofferingservices,allIoT deviceswillscheduleintheblockchaingrid.
Priortoreceivingassistance,IoTdevicesmustscheduleontheBlockchaingrid.Acontributionappealmustfirstsenttothe grid,positionwillbecheckedbyminernodes.Additionally,minersuseinformation-accessingdevicestoverifytheauthenticity orlegalityof eachsensor.Aftersuccessful confirmation or substantiation, miners will producea split key that will aidin subsequentconfirmation.Finally,utilisingthesharedkeybetweensquintjunctionandsensors,allsensorsawillassembletheir allocateblinksensors.EachInternetofThings(IoT)deviceoruserisconnectedtonearbyorsubscribingpeerdevices.Each organizationorusermustregisterontheblockchaingridinordertoenjoytheservicesofferedbytheindustrysupplier.When auserrequestsaproductfromtheindustry,wehavetreatedthemascustomersforthesakeofourframework.Similartothis, wecountanindustryproviderasaprovideranytimeitshipsthecustomer'sorder.Everytimeauserorderstheshipmentofa goods, they must register and construct their user profile on the blockchain. The user includes information about their identification, the product, paymentdetails,etc.in that profile. The usercanaccess or utilize the productonce theyhave successfullyregistered.Forproductandserviceoperations,securityandprivacyarecrucial.
WecanmanageandkeeptrackofanyIoTdevicethatisintegratedintoourblockchaininfrastructure.Ifitrequirenew arrangementsorsituations,atrustedcustomeraddsthemtotheblockchain,wheretheyareoptionallyordirectlyaccessedby theIoTdevice.Middlewarefetchesfreshdataandalertsuserswhenasuccessfulorafailedattempt.ThisimpliesthatIoT network management can be decentralized. All configurations are known provenances, distributed, and immutable. The followingtraitsareachievedbymakinguseofblockchaintechnology.Thesucceedingchallenges,suchasconfirmation,clarity, andempiricalofIoT/wirelesssensorsintheproductionplatform,needtobetheemphasisofeverysmartdevice.Wemust makesurethattheindividualstrackingtheproduct'smanufactureordocumentationarereputableandpossesstheappropriate credentials.Eventhoughindustry4.0usessmartdevicestohandlealldataandactivities,therearestillsomesecurityconcerns thatcouldcompromisesensorsandIoTdevices,henceexponentiallyslowingdowncorporategrowth.Thedesignthatare communicated in the examine document and evolved in the outline phase are actually put into practice during the implementationphase.Inordertoprovidetherequiredfinalresult,executionshouldbeaflawlessplotoftheoutlinedocument inanappropriateprogrammingalanguage.Choosingthewrongprogramminglanguageorusinganinappropriateapproachof programmingfrequentlyresultsintheproductbeingdamaged.Itisidealfor thecodingstagetobestraightrelatedtothe outlinephaseinthesensationiftheoutlineisintermsofobjectorientedphrasethenexecutionshouldbeideallyconveyedout inanobjectorientedapproach.
Additionally, it is necessary to regularly gather and verify data from each registered IoT device. So that once the informationorIoT/sensorsarecast,nothingshouldbeabletoexchange,remake,ortracethem.Blockchaintechnology,which allowsforeasytrackingofalldeviceactivitiesincludingdatacollection,productdocumentation,manufacturing,andshipment, can,however,resolvetheseconcerns.Additionally,wemustexplainthenecessarysmartagreementjustaswewritethecopy, rules,codes,andarticlebetweentheorganizations.Withoutanyfurtherinterference,allsensororIoTdevicesorjunctioncan calculate their consensus outcomes. Using blockchainatechnology, each IoTadevice or user involved in the production or deliveryofaproductmustfirstregisterorlogintothenetworkinordertoutilizeorprovidetheservices.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
AllsensororIoTdevicescancomputetheircommonresults.Usingblockchaintechnology,eachIoTdeviceoruser involvedintheproductionordeliveryofaproductmustfirstregisterorlogintothenetworkinordertoutilizeorprovidethe services.TheIoTaapparatusorasensorsaregatheredintheablockchaintotrackeachsensoractivity.Inordertoassuresecurity andtransparencyamongusersinvariouslocations,theblockchainprojectistypicallyutilizedtoforceddetailsfromsensors andtoadditionallyconserveandextractitintoblockchain.Withthehelpofablockchainmechanismandseveralsecurity indicators,thesuggestedframeworksignificantlyincreasedthesecurityofwirelesssensors.Thesuggestedframeworkistested againstthelikelihoodthatanattackwouldsucceed,thesystem'scapacitytodetectanassault,andaalterationattack.IoTcould presentanumberofsecurityandprivacyconcerns.ThesewerefoundbasedonobservationsoftheinteractionsbetweenIoT components.
OnlythealternativesforresolvingtheproblemsanddifficultiesinIoTisablockchaintechnology.Theworkdescribethe possibility for blockchain combination with IoT. The numerous IoT and blockchain technologies requisition were also discussed.Thistechnologycanbeusedforavarietyofengineeringservices.Butitisimportanttothoroughlyresearchthe preciseconsequencesofeachtechnology.Blockchainoffersmorefreedominhowyoucanaccessthedata.
[1]Geetanjali Rathee,M.Balasaraswathi2,K.PrabhuChandran3,SharmiDevGupta4 C.S.Boopathi5.AsecureIoTsensors communicationinindustry4.0usingblockchaintechnology
[2]KristiánKoštál,PavolHelebrandt,MatejBelluš,MichalRiesandIvanKotuliak.ManagementandMonitoringofIoTDevices UsingBlockchain.
[3]Chanson,AndreasBogner,DominikBilgeri,ElgarFleisch,FelixWortmannLeveraging,BlockchainTechnologyto ProtectSensorDataMathieu.Privacy-PreservingDataCertificationintheInternetofThings.
[4]ManojKumara,PradeepKumarMallickb.BlockchaintechnologyforsecurityissuesandchallengesinIoTNallapaneni.
[5] Dr. D. Sivaganesan. A Data Driven Trust Mechanism Based on Blockchain in IoT Sensor Networks for Detection and MitigationofAttacks
[6]AlbertoRodriguesdaSilva,JanVerelst,HerwigMannaert,DavidAlmeidaFerreira1,PhilipHuysmans.EffectsTowardsa SystemRequirementsSpecificationTemplatethatMinimizesCombinatorial.
[7]SabahSuhail,RasheedHussain,RajaJurda,AlmaOracevic, KhaledSalah,RaimundasMatulevičius,ChoongSeonHong, Blockchain-basedDigitalTwins:ResearchTrends,Issues,andFutureChallenges
[8]Suhail,RasheedHussain,RajaJurdak,andChoongSeonHong,TrustworthyDigitalTwinsintheIndustrialInternetofThings withBlockchain,
[9]GüntherPernulandMarietheresDietz.2020.UnleashingtheDigitalTwin'sPotentialforICSSecurity.
[10]DimitrisaGeneiatakis,IoannisaKounelis,RicardoaNeisse,IgorNai-FovinoGaryaSteri,andGianmarcoaBaldini.Securityand PrivacyaIssuesforanIoTbasedSmartHome.
[11]NoriaaFoukia,DavidaBillard&EduardoSolana.PISCES:AFrameworkforPrivacybyDesigninIoT.
[12] ArijitaUkil, SomaaBandyopadhyay, Joel Joseph, VijayanandaBanahatti & SachinaLodha. Negotiation-based PrivacyaPreservationSchemeinInternetofThingsPlatform.
[13]Jong-HyoukaLeeandMarcaPilkington.HowtheBlockchainaRevolutionWillReshapetheConsumerElectronicsIndustry.
[14]ChristianaCachin.ArchitectureoftheaHyperledgerBlockchainFabric.
[15]NigelDavies,NinaTaft,MahadevSatyanarayanan,SarahClinch,BrandonAmos.PrivacyMediators:HelpingIoTCrossthe Chasm
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 09 | Sep 2022 www.irjet.net p-ISSN: 2395-0072
[16]FangyuanSui,FangfengCheng,QinglinQi,MengZhang,HeZhang,andFeiTao.Bigdata-drivendigitaltwin-drivenproduct design,manufacturing,andservice.
[17]SatoshiNakamotoBitcoinisapeer-to-peerelectroniccurrency.ReportonTechnology.Manubot,2019.JournalofIoTin Social,Mobile,Analytics,andCloud,June2022,Volume4,Issue2105
[18]IbrahimYitmen,ChristopherSantiGötz,andPatrikKarlsson.2020.Theapplicability,interoperability,andintegrabilityof Blockchain-baseddigitaltwinsforassetlifecyclemanagementarebeinginvestigated.
[19]JiewuLeng,GuoleiRuan,PingyuJiang,KailinXu,QiangLiu,XueliangZhou,andChaoLiu.2020.AsurveyofblockchainenabledsustainablemanufacturingandproductlifecyclemanagementinIndustry4.0.
[20]GüntherPernul,MarietheresDietz,andBenediktPutz.2019.ADistributedLedgerapproachtoDigitalTwindatasharing security.
[21]ChaoZhang,GuanghuiZhou,HanLi,andYanCao,ManufacturingBlockchainofThingsfortheConfigurationofaData-and KnowledgeDrivenDigitalTwinManufacturingCell,2020.
[22]GüntherPernul,BenediktPutz,MarietheresDietz,PhilipEmpl,andBenediktPutz.2021.EtherTwinisablockchain-based informationmanagementsystemforsecuredigitaltwins
[23]AndreaUrbinati,ClaudioMandolla,AntonioMesseniPetruzzelli,GianlucaPercoco,andClaudioMandolla.Acasestudyof theaerospaceindustryincreatingadigitaltwinforadditivemanufacturingusingblockchaintechnology.
[24]XiongbingFang,SihanHuang,GuoxinWang,YanYan,andSihanHuang.2020.Forthedigitaltwinofaproduct,blockchainbaseddatamanagementisused.
[25] Haya R Hasan, Khaled Salah, Raja Jayaraman, Mohammed Omar, Ibrar Yaqoob, Saa Pesic, Todd Taylor, and Dragan Boscovicareamongthemembersofthesquad.2020.ABlockchain-BasedApproachtoDigitalTwinCreation.
[26] F. Shahid, C. Maple, A. Ahmad, and G. Jeon. A. Khan, F. Shahid, C. Maple, A. Ahmad, and G. Jeon. Spiral Digital Twin FrameworkandTwinchainforSmartManufacturingBlockchain-baseddigitaltwinsfortheindustrialinternetofthings
[27]TrondKvamsdal,AdilRasheed,andOmerSan2020.Fromamodellingstandpoint,whatarethebenefits,constraints,and facilitatorsofadigitaltwin?[28]ChapterThirteen-Empoweringdigitaltwinswithblockchain.PethuruRaj.2021.Blockchain TechnologyforSecureandSmartApplicationsinaVarietyofIndustries
[29]J.S.Rajashekar, P.P.Greeshma.Blockchain-basedDigitalTwinsfortheIndustrialInternetofThings
[30]Moily,Ashwini,GuruPrasanna,KeerthiS.Shetty,andSanjaySingh."ModelcheckingmessageexchangeinLocationBased Services",InternationalConference
[31]ShashankKathar,HarshHardel,ZeeshanAlam,ShraddhaPhansalkar,RajaniSajjan."AuctionSystemforAgriculturalTrade UsingBlockchainTechnology[32]JSRajashekar,GreeshmaPP.BlockchainforIndustrialInternetofThings.
[33] Chao Wang, Wei Duan, Jianzhang Ma, Chenhui Wang. "The research of Android System architecture and application programming",Proceedingsof InternationalConferenceonComputerScienceandNetworkTechnology.
[34]"InformationSystemsDesignandIntelligentApplications",SpringerScienceandBusinessMediaLLC,2018
[35]AlbertoRodriguesdaSilva."LinguisticPatternsandLinguisticStylesforRequirementsSpecification(I)",Proceedingsof the22ndEuropeanConferenceonPatternLanguagesofPrograms-EuroPLoP'17,2017.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
