International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072
Abstract - Duetotheavailabilityofadditionalattackers,the need for secure communication is an absolutely essential aspectofthecommunity.AccordingtoM-AODV,thecollapseof the bundle is primarily caused by the attacker's presence. If access is discovered quickly enough, the offender can be identified and disconnected from the network before any potentially dangerous interest or corrupted data can occur. The suggested M-AODV functions similarly as a barrier, protecting you from intrusion. The suggested device enables the gathering of data regarding entry tactics that may be applied to strengthen the access point. The previous device's overall performance is the best and safest network to determinetheaccuracyofthevalues,andthedeterminationof the agreement cost depends on the packets that connect the nodes to the network. The efficacy of the suggested M-AODV prevention techniques as well as the presence of Blackhole attacks(BAODV),OldPrevention(M-AODV),andtheefficacyof the same old direction are assessed. The receiver then recognises the droppings, sets the autumn limit, and recognises the presence of the attacker inside the system, which represents the attacker effect and also influences the performance of the network router. As a result, the performance of the proposed defence system is higher. The proposedM-AODVoverallperformanceismeasuredbywayof performance metrics and the result displays overall performance improvement.
Key Words:- M-AODV ,Balckhole ,VANET , MANET , AdaptiveCruiseControl.
The term"vehiclead networks" (VANETs) refersto a tiny subsetofmobileadnetworks(MANNETs)whosenodesare automobiles,trucks,buses,andmotorbikes.Thismeansthat factors like the road's route, which combines traffic with trafficlaws,haveanimpactonhowthenodescanmove.Itis assumed that VANET resolve to the supported by a fixed infrastructurethatassistsspecificservicesandmayenable accesstostaticnetworksduetotherestrictednodemobility. Critical sites, such as slick roads, service stations, risky intersections,orregionsthatareparticularlysusceptibleto hazardous weather, will be dispersed with consistent infrastructure.ItispossibletoimaginetheVehicularAd-hoc Network (VANET) as a network of moving vehicles that interactinanon-autonomousway.Duetotrafficcongestion, which causes unexpected changes in system topology, the
effectiveandefficientdisseminationofinformationisputto the test. People who live in wealthy nations may struggle daily with traffic congestion. Road traffic conditions also haveanimpactonpublicsafetybecauseitisestimatedthat 1.2 million people die on the world's highways each year. Duetothis, governmentsandthe carindustryare putting moremoneyintoimprovingroadefficiencyandsafetywhile alsoloweringtheenvironmentalimpactoftransportation.A widerangeofopportunitieshaveemergedasaresultofthe usageofcommunicationtechnologyandinformationforthis purpose. One of the most promising areas for research is communication between vehicles and sidewalk units, or especially current Vehicular Ad-hoc Net-work (VANET) traffic.
TheDSRClists more than100VANETprogrammesthat it recommends.Thesesafetyandsecurity-relatedapplications fallundermultiplecategories.Theycanalsobedividedinto OBU-to-RSUorOBU-to-OBUapplications.Listedbelowarea fewoftheapplications:
VANETs are a type of ad hoc router protocols that were developedforusageinMANETsandevaluatedforuseinthe VANETspace.Itisnecessarytoassignauniqueaddressto eachparticipatingsiteinordertousetheseaddress-based routesandtopology.Asaresult,weneedasystemthatmay beusedtogivevariousaddressestodistinctcars.However, theserulesdonotensurethattherewon'tbeanyduplicate addressesonthenetwork.[3,4]
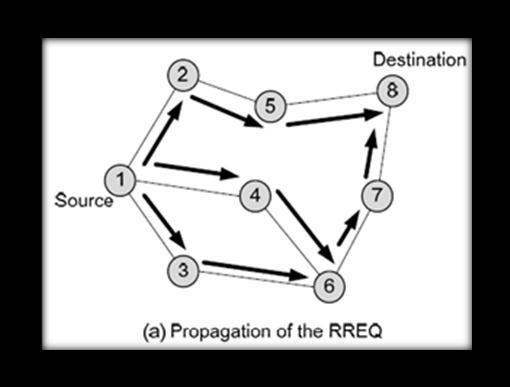
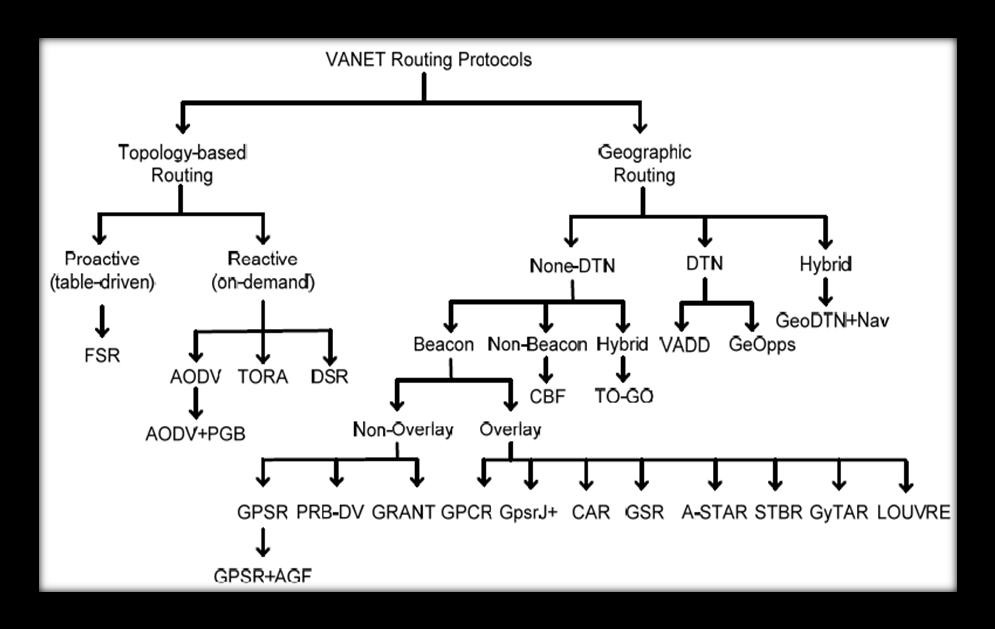
Figure2showstheVANETtaxfortheseroutes,whichare classed according to topology and nation (based on geography).Asaresult,thespeechalgorithmsnowutilised in mobile ad networks are less appropriate in the VANET space.Whenasingledatapacketissenttoitsdestination, themostrecentunicastrouterprotocolsarediscussedinthis section.
a. Topology-based Routing Protocols: - These router protocols transport packets using the network data that is accessible on the network. Additionally, they can be separated into active (table-driven)andreactive(on-demand)routes.
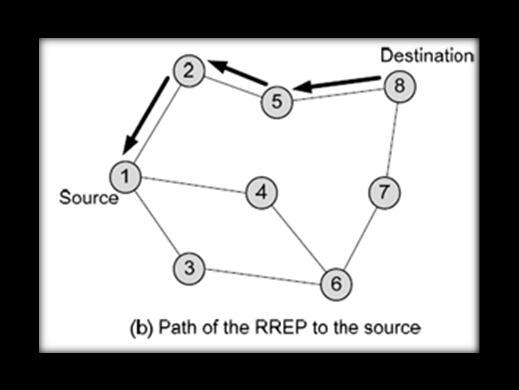

Whenonlyasmallnumberofroutesareavailable forusageatanygiventime,SourceRouting(DSR) and Ad hoc On-demand Distance Vector (AODV) routesuseroutedecisionsonacase-by-casebasis and maintain just used routes, lowering network load. A functional route is especially useful in the caseofavanetsystembecausethecommunication between vehicles will only employ a very small numberofpaths.Avectorroutingdistanceprotocol, AODV(AdhocOn-demandDistanceVectorRouting) distributesroutesasadirectedandvectordistance. The network can start up by itself thanks to the specificroutingfunctionsperformedbyeachmobile host in the system. To avoid the Bellman-Ford problem of "counting to infinity" and track loops, sequencenumbersareusedtocontrolmessages.
Duetoitsinherentstrength,theVANETisvulnerabletoboth internal and external opponents, which poses serious technological difficulties in terms of dependability and secure paths. The attacker's driving style is a risky and expensive technique to lessen traffic on the network and raisethelikelihoodofhavingarecklesspath,asopposedto roadconstruction.
The existence of a Blackhole attacker is the cause of the violent behaviour on the network. In addition to offering safety guarantees, some nefarious or malicious vehicles undermine the system by delivering subpar services or putting the vehicles of users in perilous circumstances. Therefore,acrucialcomponentofVANETdefenceistheact of detecting those vehicles that are immoral or harmful. Cruelusersofautomobilesmayactcruellyinonewayand cruellyinanother.Thenetworktrafficpacketsareallthrown ontothenetworkbytheattacker,whoalsohastheabilityto generate fake information on the network. Due to the
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072
packets' significant loss to the network, offensive vehicles generateoverhead.Althoughpacketredistributionreduces networkdelays,itisunabletoeliminatetrafficcongestion anddoesnotadequatelymanagetrafficconditionsduetothe existence of blackholes. Proposed SDSR Detect and stop harmfulvehiclestoenablesecuredeliveryofmulti-hopdata packets.
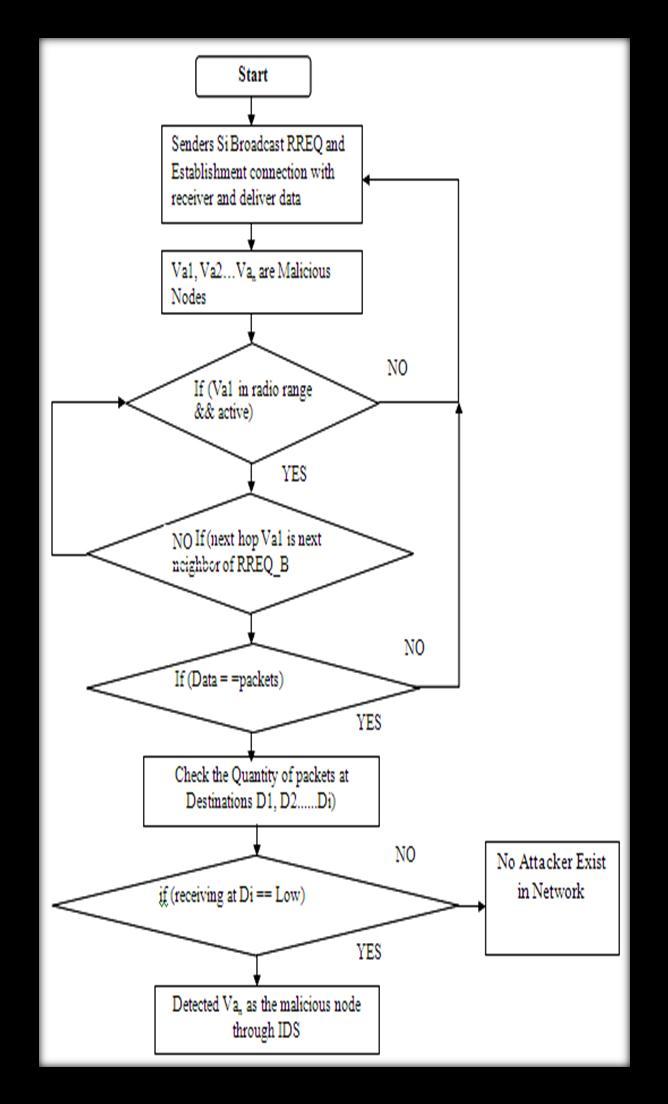
TherecommendedDefensePlan'sflowchartshowsthesteps totakeinordertospottheattacker'scombativeactivityon VANET.Todeterminewhichnodesareconsistentlydropping packetsthroughoutanetwork,detectionisnecessary.
DSRrouteprotocolisoverall(BAODV).Forallmodules,the rangeofnodeconditionsisthesame.Thesuggestedsecurity system's overall performance serves as proof of performance.
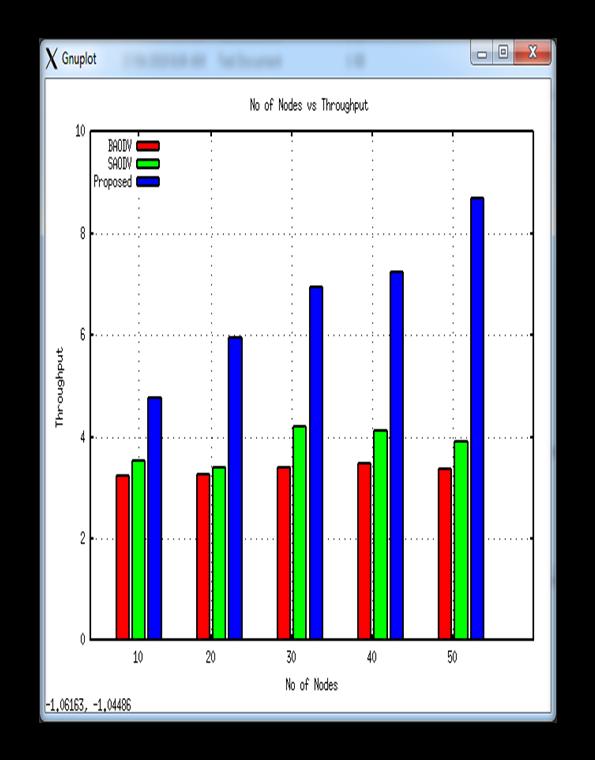
Throughput,alsoknownasnetworkthroughput,in vehicular networks refers to the rate at which a message reaches the destination vehicle across a communication channel. This data can be added over a physical or logical link or bypassed through a specific network device. The throughput is often expressed in bits per second (bit/s or bps), but it can also be expressed in statistics packets per timeslotorfactspacketspersecond.Thisgraphshowsthe throughput.
PerformanceoftheplannedsecureDSR,therelaxedAODV (M-AODV), and the blackhole AODV (BAODV) (DSR). If a hostile device enters the network and transmits data, the outcomemaybecompromised;however,iftheSDSRattack strategy is used, throughput performance is once again improved. In all node density scenarios where the performanceisreduced,the throughputatthetimeofthe black hollow node in the community is minimal. The MAODV's performance restores the network's overall performance, but the proposed system also enhances performance.
ThepriorM-AODVandBlackholeAODVareusedtogauge howsuccessfultheproposedprotectionmechanismwiththe
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072
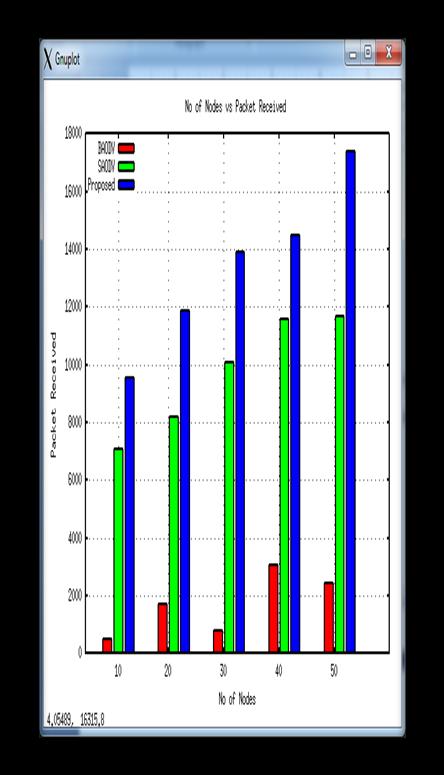
Because of the attacker's bad behaviour, a lot of trafficstatuspacketsaredroppedinthenetwork.Vehicles regularlysendandreceivetrafficdataacrossthenetworkto determinetheoptimumdrivinglocationontheroads,and the route protocol's presence is crucial for VANET. The potential data drop in BAODV, M-AODV, and SDSR is only evaluatedonthisgraph.
Here,theattacker'sactivityontheentirenetworkoftraffic data obtained from the network lowers to only roughly 22500packetsofdata.Duetotheattacker'smisbehaviourin releasingthedatapackets,vehiclesisbusyresubmittingthe request,whichiswhythedataisdeclining.However,after implementing secure SDR communication, the security standardsfordependablecommunicationwereimproved, and data loss was decreased in comparison to the prior securityM-AODVscheme.Inthecaseof40and50nodes,the moredatalosingisevident.
acceptanceofBAODVdataissmallcomparedtoSADV andSDSR.thatmeansthatthelossofblackholedatais significant and if we use the proposed SDSR for data retrieval is high, that indicates in all node congestion conditions. That indicates that receiving when dangerous nodes are not really important within the source to the point that ends the network under infection.Theattackervehicleusesdatapacketsonthe networkandreducestheactualnetworkperformance butintheproposedschemetheperformanceincreases whichshowsbetteracceptancecomparedtoM-AODV
ContactVANETtocompletethevehiclesenderrequest and maintain traffic on the roads. In this graph the
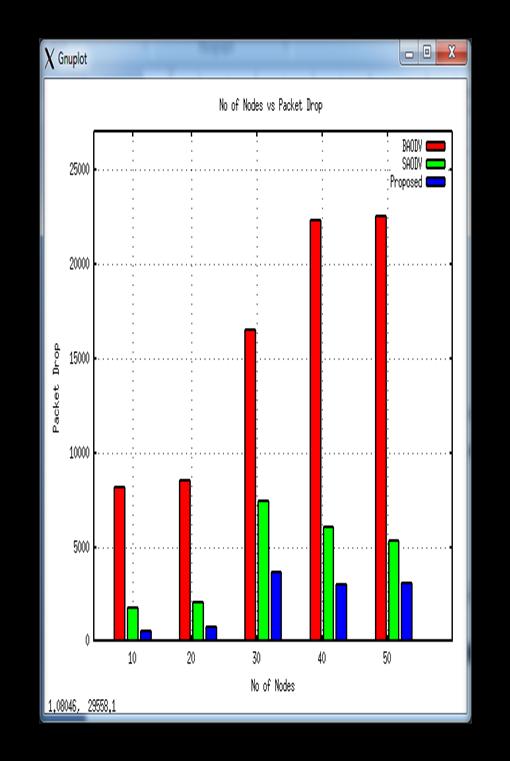
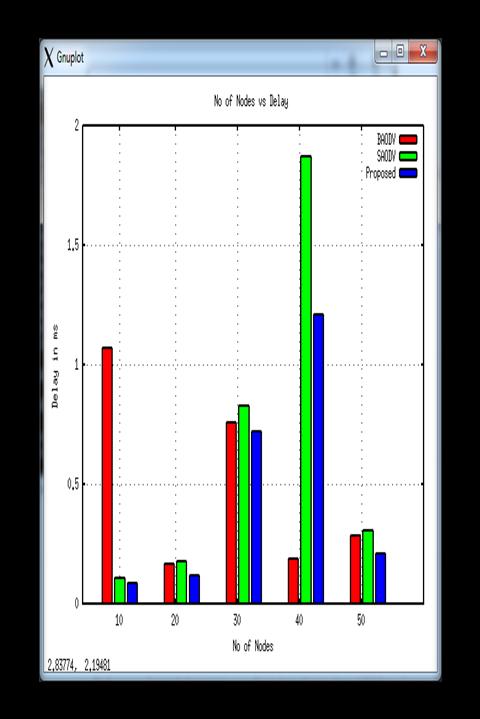
Thedelayreasoninroadtrafficisvehiclesinroadismore andthetrafficstatusinformationisnordeliveredtovehicles properly.Thefollowervehiclesarecontinuouslysendsthe trafficrequestforrecognizesthetrafficstatus.Thevehicles aredriveonthatpathaccordingtothetrafficinformationof beginning vehicles. Traffic data is also detrimental if it is deliveredoverthenetworke.g.didnotbehaveproperlydue to the presence of the Blackhole invader (BAODV). In this graphtheperformancedelayismeasuredanditisnotedthat the BAODV delay performance remains high in all node
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072
congestion conditions. The development of delays is even higherforM-AODVbuttheminimumfortheproposedSDSR system. The proposed Blackhole attacker system protects network performance and provides the delivery of applicationpackagesinlinewithVANET'snormaloperation.
communication.SecurityonVANETtoimproveopt-outand PDR.Improvingpackethandlingalsoimprovesperformance byreducingdelaysandhighs.Althoughtheattackcreatesa more difficult situation, it is necessary to investigate the impactoftheattackonthetracksystemsthatcreateasecure vehicle environment. The proposed SDSR reduces packet collapseandduetothepresenceoftheattackerthefallout closescompletelyandremovestheinvaderinfectionfrom thenetwork.
ThepresenceofanattackeronVANETworksbesttodetect itusingalocationdetectionsystemortheGlobalPositioning System(GPS)toidentifyarealdangerousvehicleorcurrent location.Thelocation-basedsystemalsoimprovesadditional performanceduringdelaysandhighs.
1. Sourav Kumar Bhoi, Eabitra Mohan Khilar, "A Secure Routing Protocol for Vehicular Ad Hoc Network to Provide ITS Services", International conference on Communication and Signal Processing,April3-5,2013.
2. Sumra, Irshad Ahmed, Iftikhar Ahmad, Halabi Hasbullah, and J-L. bin Ab Manan. "Classes of Attacks in VANET." IEEE Saudi International Electronics, Communications and Photonics Conference(SIECPC),2011,pp.1-5, 2011.
3. SarahMadi,HendAl-Qamzi,"ASurveyonRealistic Mobility Models for Vehicular Ad Hoc Networks (VANETs)", IEEE 10th IEEE International Conference On Networking, Sensing And Control (ICNSC),2013.
Thepresenceofmaliciousvehicles/vehiclesdegradesthe performance of In presence of blackhole attacker packets drooping isimprovedand receptionand transmissionare greatlyreducedcomparedtonormalcommunication.Inthis studytheproposedSDSRprotectionsystemidentifiesand prevents the network from single and multiple blackhole attacksonVANET.Theproposedmethodisdeterminedby thereductionofthepackagecountingaboveacertainlimit andthenthepotentialattackeronthenetwork.Thenumber of vehicles crossing the road and terminals such as RSU units. The RSU unit monitors traffic information sent to vehicles within a certain distance to identify other traffic conditionsinmovingvehicles.RSUsurveillancedetectsthe presenceofanattackerandsubsequentlyblocksit.Inthis paper VANET's list of features such as environment, standards and network construction were discussed. At VANETtofindandproduceatrafficrequestroutetoforman important component used for outstanding and relevant
4. JakubJakubiakandYevgeniKoucheryavy,“Stateof the Art and Research Challengies for VANETs”, Proceedingsofthe5thannualIEEECCNC,pp.912916,2008.\
5. Mengjiong Qian, Yong Li, Depeng Jin, Lieguang Zeng", Characterizing the Connectivity of Large Scale Vehicular Ad-Hoc Networks", IEEE Wireless Communications and Networking Conference (WCNC):Networks,2013.
6. R. G. Engoulou, M. Bellaïche, S. Pierre, and A. Quintero, “VANET Security Surveys,” Computer Communication,Vol.44,pp.1–13,May2014.
7. Anas Abu Taleb, "VANET Routing Protocols and Architectures:AnOverview",JournalofComputer Science,2018.
8. Duduku,V.,V.A.Chekima,F.WongandJ.A.Dargham, "ASurveyonRoutingProtocolsinVehicularAdHoc Networks", International Journal Innovative ResearchofComputerCommunicationEngineering, pp.12071-12079,2015.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page277

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072
9. JairJoseFerronato,MarcoAntonio,SandiniTrentin, "Analysis ofRoutingProtocols OLSR, AODV andZRPin Real Urban Vehicular Scenario with DensityVariation",IEEELatinAmericaTransactions
Volume:15,Issue:9,pp.1727-1734,2017.
10. A.P. Jadhao, Dr.D.N.Chaudhari, "Security Aware RoutingSchemeInVehicularAdhocNetwork",IEEE ProceedingsoftheSecondInternationalConference on Inventive Systems and Control (ICISC 2018), 2018.
11. KumudDixitPriyaPathakSandeepGupta,"ANew Technique for Trust Computation and Routing in VANET",IEEE,2016.
12. Trupil Limbasiya, Debasis Das, "Secure Message Transmission Algorithm for Vehicle to Vehicle (V2V)Communication",IEEE,2016.
13. KhaoulaJeffane,andKhalilIbrahimi,"Detectionand Identification of Attacks in Vehicular Ad-Hoc Network",IEEE,2016.
14. MengjiongQian,YongLi,DepengJin,LieguangZeng, "Characterizing the Connectivity of Large Scale Vehicular Ad-Hoc Networks", IEEE Wireless Communications and Networking Conference (WCNC):NETWORKS,2013.
15. Sourav Kumar Bhoi, Rajendra Prasad Nayak, Debasis Dash and Jyoti Prakash Rout, "RRP: A Robust Routing Protocol for Vehicular Ad Hoc Network against Hole Generation Attack ", International conference on Communication and SignalProcessing,pp.1175-1179April3-5,2013.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal
