International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN:2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN:2395-0072
Abstract - Cloud computing is an on-request access model for registering assets most quite typified by the OpenStack project. As of delivery Liberty, OpenStack upholdsprovisioningExposedmetal,Virtualmachine(VM) and compartment based has. These various hosts cause variousoverheads.Subsequently,theprincipalobjectiveof this paper is to measure that above experimentally through a progression of tests. The accompanying drivers areutilizedinthiscycle:IronicforExposedmetalorMetal as a Service (MaaS), nova-figure for VMbased hosts, and nova-DockerforDockerbasedcompartments. Weutilizea private-cloud to look at the various choices. This cloud is then used to analyze the unique has with regards to executionbyutilizingdifferentopen-sourcebenchmarking devices. Welikewisemeasureboot-uptimes.The result of thesebenchmarksisgatheredandresultsarelookedat. In thispaperweexamineourlearningsaswellastheunique designsandtweakingthatwecarriedout.Accordingly, we give a bunch of suggestions in view of the benefits what's more,hindrancesof eachhostinpresentand futurecloud organizations.
Keywords: Bare Metal, Virtual machine, CPU, OS, Metal as a Service, Cloud.
Cloud computing brings a whole new arrangement of incentives to big business figuring conditions by offering benefitslikeapplicationversatility,functionaladaptability, further developed economies of scale, asset effectiveness, dexterity improvement and that's only the tip of the iceberg. The National Institute of Standards and Innovation [1] characterizes Cloud as a model for empowering pervasive, helpful, on-request network admittance to a common pool of configurable figuring assets (e.g., networks, servers, capacity, applications, and administrations) that can be quickly provisioned also, delivered with negligible administration exertion or specialist organization cooperation. Generally it is assumed that the origins of Cloud registering can be followed back to the applications needed to share framework assets given by centralized server PCs. IBM
then, at that point, contributed a ton of time and exertion in creating strong time-dividing answers for further develop proficiency among clients and costly shared PC assets. Today, the most ideal way to further develop asset use, and simultaneously rearrange server farm the executives, isthroughvirtualization. Virtualizationalludes to the demonstration of making a virtual variant of something. It abstracts the physical equipment shaped by bunches of servers into enormous collected pools of sensible assets. This, in turn, can then be divided and offered back to clients as VMs. Today, Infrastructure as a Service (IaaS) is generally inseparable from VMs. inside IaaS, the OpenStack project is a notable open source software. The OpenStack mission is to deliver the pervasive Open Source Cloud Computing stage that will address the issues of both public and confidential mists notwithstanding of size, by being easy to execute and hugelyversatile[2].Cloudsuppliershavebegunconveying uncovered metal foundation as an on-request administration, like leasing of virtual servers. Exposed metal figure administrations are acquiring quick prominence as they give the versatility of cloud without virtualization above and proposition devoted servers to the client on a pay-more only as costs arise premise. Onrequest provisioning of uncovered metal servers brings a basic issue. Dissimilar to virtual machines, uncovered metal process administrations are related with unusual provisioning latencies. In specific cases, the provisioning time goes from hours to days or even weeks, contingent upon the scope quantification knowledge of the cloud supplier being referred to. Besides a "saved example" develop ordinarily on offer with virtual machines, isn't accessible for uncovered metal servers. These are chiefly in light of the fact that while satisfying client demands for physical servers, the cloud supplier can't financially use and benefit from the product definition that virtualization brings through handles, for example, over-commit proportions. In view of the difficulties examined above, just satisfaction SLOs (Service Level Objectives) are generally on offer with uncovered metal register, and not provisioning-time SLAs (Service Level Arrangements) whereabreakisrepaidwithslippagepunishment.Noneof the standard exposed metal specialist organizations for
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN:2395-0072
example, IBM, AWS and Oracle offer provisioning time ensures [3]. The resulting non-determinism around demand satisfaction time - which is undeniably more prominent for exposed metal administrations contrasted with virtualized administrations - doors the on request model expected by big business clients of public mists. To mitigate the effect, venture clients need to independently plan and pre-arrangement for top interest of exposed metal servers, or need to leave on limit separately arranging.Thisissub-standard,contrarytowhatwouldbe expected of the cloud model, costly, and by and large, influencescloudreception.
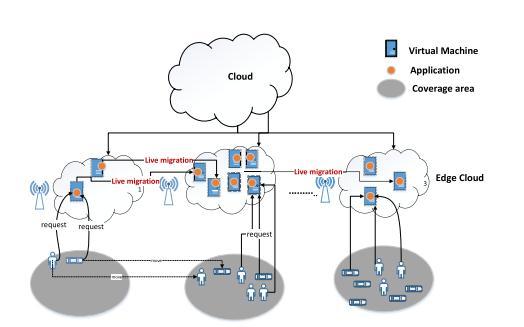
Live movement requires the ability to copy the complete state of a source machine to a goal machine over an organization. In standard IaaS fogs, the machine being movedisa VManditsstatesaretakencareofinmemory. Thusly, living relocation is easy. Many existing, truly virtualizationprogramming,forinstance,VMwaresupport live development. Regardless, uncovered metal fogs don't haveavirtualizationlayer,andthusly,machinestatesexist ingenuinegear.Pastexaminationshaveexhibitedtheway thatlivedevelopmentcanbecompletedintheOS layer.In any case, in uncovered metal fogs, live development plans should be independent of the OS for the going with reasons. In the first place, cloud clients should be pondered autonomously from cloud chairmen. If a live migration plot depends upon an OS, the live movement undertakings ought to be performed by the client. Nevertheless,itisunreasonabletoguessthatclientsought to anticipate unusual help and perform live migration as required. Hardware performance data is dependent upon thegenuineexecutionseasonofutilizations,highIOPSand lowdormancy stockpiling gadgetsaddtothepresentation of I/O serious positions what's more, FLOPS is a proportion of provisioned figuring assets, as well as high organization transfer speed for quick correspondence. By and by, nonetheless, the mind boggling responsibilities have different attributes to distinguish tuning factors and investigate bottlenecks if exists and along these lines execution assessment with different situations is fundamental for understanding the climate sent. Exposed metalserversarebroadlyaccessiblewithdifferentchoices toaddadditional CPUcenters,memory,andnearbyNVMe as well as high organization data transfer capacity. Enormous information clients with information concentrated application might use these arrangements when in an upward direction scaled bunches create preferred execution over developing many quantities of product servers. Moreover, further developed execution brings about inflating cost proficiency as more assets are immediatelyreturnedforadditionalutilization.
Ironic (bare-metal) allots the entire server equipment to the heap. Thusly, applications can run locally on the have and completely use the hidden equipment. Nonetheless, this is a solitary inhabitant choice as unused equipment assets can't be shared or re-utilized by others inside the server farm. As a result exposed metal will in general diminishbyandlargeusagerates,furthermore,ismuchof the time not a practical choice. Moreover, from an Ironic ventureviewpoint,exceptional augmentationsareneed to permitadmittancetoequipmentassets.Executionofthese expansions restricts the rundown of upheld equipment and prompts increment the expense of creating and keeping up with the OpenStack Unexpected driver. The othertwosortsofhoststendedtointhispapersurvivethe previously mentioned limits by presenting a level of reflection through a hypervisor and the holder motor separately. This expansion comes to the detriment of execution. Nova-register utilizes KVM as a matter of course; a sort one hypervisor [9] and all the more explicitly the KVM-QEMU pair. Nova-libvirt ( [10] driver deals with the correspondence between OpenStack and KVM. While VMs succeed at detachment, information trades between visitors and hypervisors are slower KVM utilizes equipment virtualization highlights in the processorsto restrictoverheads,and upholds Para virtual gadgets through Virtio [12], a virtualization standard for organizationandplategadgetdriverswhereasitwerethe visitor's gadget driver "knows" it is running in a virtual climate, and participates with the hypervisor. The two highlights will quite often decrease virtualization overheads. As opposed to running a full OS in a VM, holders accomplish comparative cycle separation by changing a common OS (working framework level virtualization). This kills the requirement for a Visitor OS; applications run in their own secluded client space; a sandbox which is showed through Linux bit highlights such as namespaces and groups. The aggregate of these client spaces is overseen by the holder motor which accesses actual assets through the host working framework.ThedisposalofGuestOSinholdersempowers them to be morelightweightand quicker thanVMs inthis way fundamentally diminishing boot time. The novadocker driver brings forth Docker holders. Docker compartments envelop a piece of programming by a total file system that contains everything expected to run an application:Code,runtime,frameworkdevices,framework libraries whatever can be introduced on a server. One of the most famous ways of gathering usage measurements like CPU, memory, and plate use is through introducing specialists (otherwise called have specialists) on the host
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN:2395-0072
complex BodenRussell et.al [8] propose introducing host specialists on servers and occasionally gathering use measurements. These measurements are put away in a periodseriesdataset.Inanycase,inexposedmetalmists, the occupants may not approve cloud administrators to introduceanyspecialistsinthehostcomplexoftheserver as these specialists would gather delicate client or framework related data, disregarding security and protection approaches. In-processor firmware functionalities like Intel's administration motor (ME), AMD'sfoundationsecurity processor(PSP),andIBM's onchipregulator(OCC)give equipmentlevel usageinan OSskeptic way. Exclusive BMC firmware usefulness, for example, figure use each second (CUPS) utilizes these inprocessorfirmwarefunctionalitieswithoutincludinghostcomplexworkingframework.Thus,CUPSmeetsprotection and security prerequisites. Nonetheless, to utilize CUPS usefulness, cloud administrators need to purchase firmware licenses and update the current arrangements. This increments functional expenses essentially and may notbereasonableforthecurrentorganizations.Besides,it permits estimating just the processor use. A comparative usefulness should be empowered by all the eager for power equipment gas pedals (e.g., GPUs, brilliant NICs) to track down thegeneral serveruse. This, be thatasit may, further adds to the functional overheads. While planning NASCENT, we consider potential expansions to recognize usage of these gas pedals. G. J. Popek et al. [9] run extraordinaryobservingspecialistsatthehypervisorlevel (i.e., have complex). This is utilized to perform liverelocationofVMstolessservers,power-offunusedservers for energy the board, or recognize compromised VMs. Running checking specialists at the hypervisor level jam theclients'securityonaccountofIaaSmists(VMs),onthe grounds that observing specialists don't run inside the VMs. In any case, in BMaas cloud, just occupants have full oversight of the host-complex of an exposed metal server. In any case, BMaaS cloud administrators can't introduce any specialists even in the host complicated as these specialists can be abused to gather delicate clients, occupants or framework related data, disregarding security and protection objectives vowed to the inhabitants. Thus, they can't take on these answers for BMaaSmistspracticallyspeaking.
AComputehostorhostisahuboverseenbyOpenStackto start up a VM, or a compartment. It runs different OpenStack administrations like the Neutron specialist, ceilometer, a nova specialist, Open v Switch (OVS), an informing client (RabbitMQ), etc. An Ironic host is an
uncovered metal hub oversaw by Open-Stack. The actual server is completely distributed to the heap and runs no OpenStackservices.ADockerholderinsideaprocesshave isalludedtoasDocker.AVMinsideafigurehaveisalluded to as VM.Note that during the assessment stage, a specific serverissingled ona missiontostayawayfromvarieties. This is the server under test. In situations where correspondence to a far off VM or compartment is required,thenanalternateserverassociatedwiththeToR is utilized to restrict the quantity of organization bounces toone.Toguaranteelike-with-likeistried,theframework under test is dependably a similar server. There is no systems administration traffic beyond the tests as the groupisrestrictiveandunsupported.
This plan unquestionably diminishes virtualization above appeared differently in relation to product VMMs. An assessment of item VMM and BLMVisor models is shown inFig.1.InthethingVMMtheguestOSrunsonaVM
Besides, receives to digital gadgets made through the VMM. Permission to a digital contraption is modified over absolutely to a hypothetical vicinity of verbal exchange of the backend driving force with inside the VMM, and the backend driving force offers a virtually true tool access. A equipment frustrate from the real contraption is first gottenthroughthebackenddrivingforce.Then,thedigital tool promises a digital frustrate to inform the contraption driving force of the visitor OS. These special site visitors circle receives to and interface adjustments motive
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN:2395-0072
virtualizationabove.ThehypervisorlicensesthevisitorOS to control actual gadgets certainly via their community factors of verbal exchange. Moreover, the hypervisor doesn`tintrudeonhardwaremeddles(nownolongereven clock bargesin).Taking the wholelotintoaccount,upsets are surpassed certainly directly to and controlled through thevisitorOS.Thisplanforgoescontraptionvirtualization what is more, VM booking, likewise giving execution situations which are almost same to the ones of exposed metallicevents.
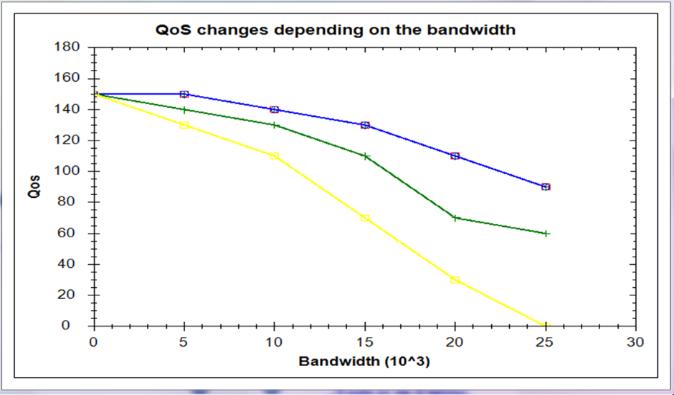
Initial trade the difficulty right into a Linear Programming (LP) trouble with the aid of using watching for that everyone the migration duties are carried out preciselyonthedeadlines.Wethen,planoneextraversion of useful resource exchange, and use the version to iterativelytradethepathofmovementfromtheLPsolver. The trade begins off evolved with a essential path of movementfromLPsolver,andplanstolocateansuperior answer for the number one trouble. The useful resource exchange version proposed with the aid of using us can assurethattheplanafteratradeisatthisfactorfunctional. Since the effect of the LP solver influences the inevitable effects, we subsequently endorse numerous groundbreaking computations to choose the correct one from the plans added with the aid of using the LP solver. We survey the creation of our technique via expansive proliferations. In particular, we ponder the creation of 5 great estimations used to choose the hidden path of movement in our technique. The effects show off the manner that our proposed method can attain tremendous QoS and has a quick blend velocity below diverse era settings.
Migration time shows how a good deal time it takesfora VMemigratefromanpartcloudtoanother. By the usage of the pre-reproduction technique, the VM migrationtimemaybemodeledby
Where MT is the relocation season of the stayVMrelocation,MisthedimensionsoftheVMmemory, Bisthecompanytransmissionpotentialamongthesupply and goal machines, and d is the filthy rate. The real relocation time li have to be beneath Neath a cutoff time.
Duringthechange,it'sfaracceptedthattherelocationtime limaybesteppedforwardearlierthanthecutofftimes.As the underlying association from the LP problem basically affectstheoutcomes of our concern,atlengthyclosing we foster some transformative calculations consisting of the hereditary calculation and molecule swarm development totunedownarespectablebeginningassociation.
QoS is a feature of the first-class want for the help going forwalksonaVMindevelopment.Ifanhelppatronneeds a excessive QoS, the reminiscence of the VM can be invigorated with a excessive records fee all through the development. Name this fee as reminiscence untidy fee. Since untidy fee concludes the concept of agency, we use grimy fee and agency fee equally. In bendy facet enlisting, the threshold fogs are always dispatched in a phone backhaulnetwork.Thebackhaulfactscirculaterestrictthe various facet fogs in reality influences the VM migration time and QoS. In numerous applications, the QoS could increase vehemently with the disgusting fee, however the datingmightnot be instant. Regardless,for ease, weusea direct version in the difficulty plan. Since our proposed computations needn`t trouble with the instant version of the QoS and grimy fee, our proposed estimations absolutely paintings beneath neath numerous models. So this doubt does not effect the overall lodging of our proposedestimations.
Todegree boot-upinstances,theOpenStack logsareused. Anexampleisstatedtobetobehadwhilstitreachesthe” login” stage. Although this technique isn't always overly accurate, it's miles a top sufficient estimation of the time required for a aid to come to be usable. Depending at the taskexecutionlength,theboot-uptimeforacomputingaid tocometobetobehadtoaconsumercanalsoadditionally or won't be relevant. If the task goes to run for days or months then the above values aren't important. But for quick jobs (< 1-2 h), then the variations are massive sufficient to prefer field primarily based totally setups. While the Boden record suggests boot-up instances of 5s and3srespectivelyforVMsandcontainers,wedidnowno longer see any optimization that could justify such improvements. We expect that the authors used the time takentoallocateanaid,nownolongerthetimeinwhichit turnsintousable.WhileaVMinstantiationisquick,itdoes now no longer suggest that it's miles able to coping with utility load. For our measurements, we expect that a computing aid is prepared whilst it is able to be ssh-ed in
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN:2395-0072
and now no longer simply pinged or seen with inside the horizoninterface. Notethatthemeasuredtimeconsistsof moving the photo from the Glance repository to the server, This influences Bare- Metal worse than VMs or Container as it's miles a obligatory step at some stage in provisioning whilst different alternatives can use host primarily based totally caching mechanisms at the compute.
To intercept I/O get admission to to a check in, the hypervisor configures the CPU to reason a“VMgoout” occasionupongetadmissiontotothecheckin`s portcope with. A VM go out is an occasion wherein the CPU passes manipulate from the visitor OS to the hypervisor. One of the write only states of the PIC is saved in a check in that stocks the port cope with with the end-of-interrupt (EOI) check in. Therefore, the hypervisor have to configure the CPUtoreasonaVMgooutoccasionwhilegettingaccessto this shared port cope with to intercept the write I/O get admission to to the PIC check in. Since the EOI check in is accessedfrequently,VMexitsarisefrequently. Incontrast, interruptsinmulti-middlestructuresaremanagedviaway of means of the IOAPIC, nearby APIC, and MSI(-x) mechanisms. Since those mechanisms haven't any writebest states, the hypervisor does now no longer want to intercept write I/O get admission to to them. As a result, the wide variety of VM exits is decreased significantly. Note that VM exits are highly-priced operations; thus, fewer VM exits are higher in phrases of performance. Performance at some stage in regular execution changed into measured, together with community throughput, latency, variety of VM exits, reminiscence consumption, machinebenchmarks,andadatabasebenchmark.
Before and after stay migration, BLMVisor has not anything to do; however, it nevertheless incurs a few overhead for a few VM exits and paging events (i.e., the EPT).Ifvirtualizationcanbegrewtobecomeonandoffas required, overhead in everyday execution will become 0 and overall performance same to that of bare metal machines may be achieved. This dynamic beginning and preventing of the hypervisor entails issues. The first trouble is protection, i.e., if the hypervisor is living in reminiscence, it isn't blanketed while the EPT is grew to becomeoff.Thiswillnownolonger
BecomplexifthevisitorOSmaybetrusted;however,this canbemitigatedviawayofmeansoferawhichcanaffirm reminiscence content. The 2d trouble is the way to begin thehypervisor. Sincevirtualizationisgrewtobecomeoff, there's no occasion to by skip manage to the hypervisor. Thismaybemitigatedviawayofmeansofputtinginafew agentapplicationwithinsidethevisitorOS.
This paper has provided BLMVisor, a stay migration scheme for bare-steel clouds. BLMVisor exploits a completely skinny hypervisor to permit pass-via get right ofentrytobodilygadgetsfromthevisitorOS.Tocarryout stay migration, the hypervisor captures and reconstructs bodily tool states, together with each unreadable and unwritable states. Unreadable states are captured not directly via way of means of tracking accesses to tool registersandthebehaviorsofthegiventool.
Unwritable states are reconstructed not directly via way of means of cautiously controlling the tool. A prototype implementation primarily based totally on Bit Visor helps stay migration of PIC/APIC, PIT further to the CPUs and memory. Performance become evaluated in a sequence of
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN:2395-0072
experiments that showed BLMVisor achieves overall performancethisissimilartothatofabare-steelmachine. In future, the overhead of memory-extensive workloads might be decreased via way of means of dynamically beginningandpreventingthehypervisor.
[1] “Final version of nist cloud computing definition published.” [Online]. Available: https://www.nist.gov/newsents/news/2011/10/ final-version-nist-cloud-computing-definitionpublished
[2]O.Sefraoui,M.Aissaoui,andM.Eleuldj,“Open stack: toward an open source solution for cloud computing,” InternationalJournalofComputerApplications,vol.55,no. 3,2012.
[3] “Ironic project: Open stack bare metal provisioning program.”[Online]. Available:https://wiki.openstack.org/wiki/Ironic
[4] “Open stack nova.” [Online]. Available: https://wiki.openstack.org/wiki/Nova
[5] “Kvm.” [Online]. Available: http://www.linuxkvm.org/page/MainPage
[6] “Docker driver for open stack nova.” [Online]. Available:https://github.com/openstack/nova-Docker
[7]W.Felter,A.Ferreira,R.Rajamony,andJ.Rubio,“An updated performancecomparisonofvirtual machinesand linuxcontainers,”in Performance Analysis of Systems and Software (ISPASS), 2015 IEEE International Symposium On.IEEE,2015,pp.171–172.
[8] “Passive benchmarking with docker lxc, kvm & openstack v 2.0,” April 2014. [Online]. Available: http://www.slideshare.net/ BodenRussell/kvm-anddocker-lxc-benchmarking-with-openstack
[9] G. J. Popek andR.P.Goldberg,“Formalrequirements for virtualizable thirdgenerationarchitectures,”ACM,vol. 17,no.7,pp.412–421, [10]“Libvirt:Thevirtualizationapi.”[Online].Available: http://libvirt.org/
[11] “Under the hood with nova, libvirt and kvm,” OpenStack Summit, 2014. [Online]. Available: https://www.openstack.org/assets/ presentationmedia/OSSummitAtlanta2014
[12] “Paravirtualized drivers for kvm/linux.” [Online]. Available:http://www.linux-kvm.org/page/Virtio [13] “Docker: Build, ship, run.” [Online]. Available: https://www.docker.com/ [14] “Openvswitch.” [Online]. Available: http://openvswitch.org/ [15] “Devstack project.” [Online]. Available: http://docs.openstack.org/developer/devstack/ [16] “Lempelzivmarkov chain algorithm.” [Online]. Available:https://en.wikipedia.org/wiki/LempelZivMarko vchainalgorithm
[17]“Hutter.” [Online]. Available: https://cs.fit.edu/mmahoney/compression/textdata.html [18]“Nuttcp.”[Online].Available:http://www.nuttcp.net/ [19] “Netperf.” [Online]. Available: http://www.netperf.org/netperf/ [20]“Bandwidth: a memory bandwidth benchmark.” [Online].Available:https://zsmith.co/bandwidth.html [21] “Sysbench.” [Online]. Available: https://github.com/akopytov/sysbench [22] “Hostpassthrough.” [Online]. Available: https://libvirt.or/formatdomain.htmln#elementsCPUAlloc ation
[23] “Welcome to openstack documentation.” [Online]. Available:http:docs.openstack.org/liberty/ [24]“containersindocker1.11doesnotgetsamemtuas host.”[Online]. Available: https://github.com/docker/docker/issues/22297 [25] “Ibmnetperf.” [Online]. Available: http://www.ibm.com/support/ knowledge enter/SSQPD32.4.0/com.ibm.wllm.doc/runnetpe [26]G.Hulme,“Containersand security q&a: Putting a lid onrisk.” [Online]. Available: http://containerjournal.com/2016/04/13/ containers-security-qa-putting-lid-risk/ [27] “Welcome to kollas documentation!” [Online]. Available:http:ocs.openstack.org/developer/kolla
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page1831