International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072
***
Abstract - Self-defense for running applications is a security-based technology. It keeps an eye on the running program, which keeps an eye on incoming traffic to see whether any incoming attacks are present. If they are, it blocks them by using the information from the current application. By evaluating the inputs and preventing the inputs that could enable assaults in the application, it is claimed to enhance the security aspects of software. RASP reduces the reliance of applications on external hardware, such as firewalls, for runtime security protection. We outline the fundamental ideas behind Runtime Application SelfProtection Technology (RASP), a relatively new security strategythatissoontobewidelyadopted.
Key Words: SelfProtection,Security,NetworkTraffic
Networks are expanding in size, becoming more complicated, and becoming harder to secure. In order to better detect risks, security providers are incorporating new methodologies into their software products, such as studyingusers'typicalroutines.Applicationsarescattered and complicated, thus application security strategies should be divided up to allow for a more in-depth investigation of the system's data. Attacks are becoming more sophisticated, and present access safeguards are no longer able to stop them. Due to shortcomings in applicationsecurity,productionapplicationsareatdanger. Once they take place on a network, security issues have verylittlevisibility.
There’sastrongneedofmodulethatcan:
• By keeping an eye on and analysing exploitation attempts, you can spot attack trends and prevent callers fromaccessingtheapplication.Context-awaredetection
• Recognize and record how an application performs, interactswithitsecosystem,andflowsdatainandout.
• Identify unusual searches, application inputs, feature usages,andcomparetothedatabase.
• Recognize typical application usage patterns and documenttheminthedatabase.
Ifsomethingisstrange,denyaccesstothefeatures.
• When an application has known vulnerabilities, defend against assaults without the requirement for development fixes.
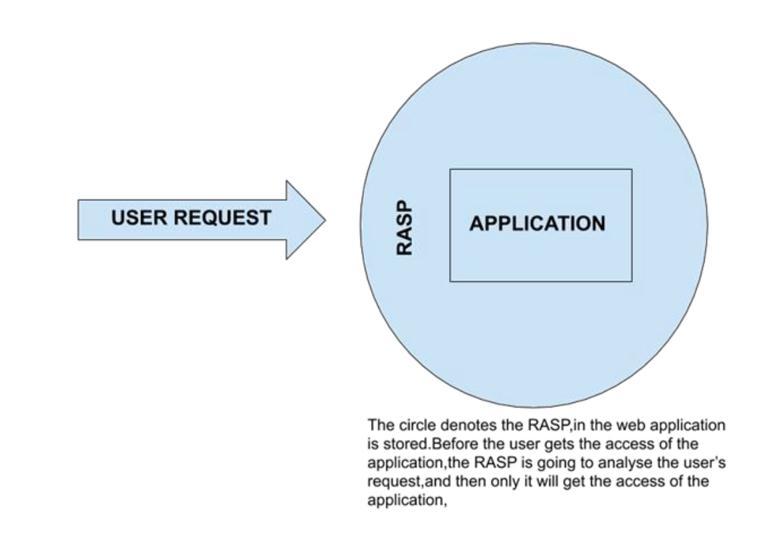
RASPisasecuritytechnologythatisbuiltorlinkedintoan application or application runtime environment and is capable of controlling application execution as well as detectingandpreventingreal-timeattacks[1].
RASP prevents attacks by self-protecting or automatically reconfiguringin responsetoparticularnetwork situations withouthumanintervention(threats,faults,etc.).
Whenanapplicationisexecuted(runtime),RASPbecomes active, causing the programme to supervise itself and identify fraudulent input and behavior. RASP processes boththeapplication'sbehavioranditscontextinrealtime.
As a result, regular security analysis is used, with the system responding appropriately to any detected attacks. [2].
Web applications are a common target, and attackers commonly employ them to gain access to a system (network)[3].
Maintaining network security while preserving the flexibility needed by web application developers is the primary security goal of a business. The idea that a web application firewall (WAF) is the best security measure is one that is frequently expressed. Before running the web application, WAF filtering and code testing methods are implemented, evaluating incoming traffic flow for known attack patterns and blocking inputs from reaching the application. The consensus is that a WAF's signature base andpatternmatchingenginedeterminehowtrustworthyit is.
Therearetwousedcasesinvolved:
I. The Self Protecting tool placed inside the application
User attempting to log in while still logged in: This user action can be viewed as suspicious, and the user is prompted to log out first to preserve the integrity of the programme.FeaturesoftheProposedSystem'sSecurity.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072
a. Whenauserlogsinorout,thelogfilesareprinted with their timestamp and distinctive ID (such as theiraccountnumber).
b. A Boolean value is always set to true whenever a log-inaction iscarriedout. Iftheuserlogsout, the valuejustbecomesfalse.
c. Userswhoarealreadyloggedincannotloginfrom another tab of the browser without first logging out.
d. The aforementioned modifications, which were performed during the course of this project, were notexistentinthesystemthatwasinplacebefore.
e. Using the current system, we were able to access the information and identify suspicious and harmful activity. The application in our suggested solution does not access the database or modify any source code. We create logs for each login and logouteventtohelpusdetectnefariousbehaviours likeseveral usersusing the sameaccounttologin. By analysing the real-time generated logs, our applicationwilllookforanyanomalousactivity.
f. Since we won't be accessing the database, we will save all of the routine actions in the logs itself insteadofthedatabase,whichwashowthesystem was set up before. Without altering the source code, our suggested application will function as a general-purpose add-on that keeps track of both normal and aberrant activity. It runs in parallel in the background. As opposed to the prior system, where we had to access the database and modify the source code, the application in the existing system was not general-purpose for any web application.
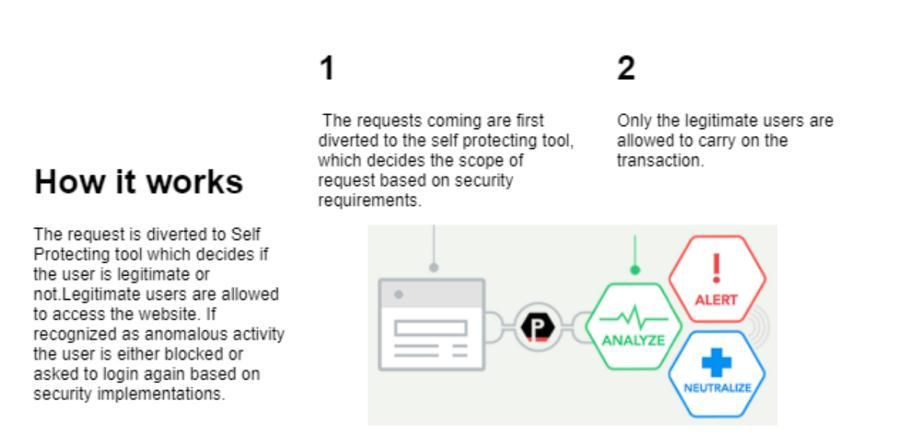
a. When a user attempts to commit SQL injection, their behavior is deemed suspect, and they are prohibited from accessing the website. The fundamentalblockdiagramisdisplayedinFig.1.3.
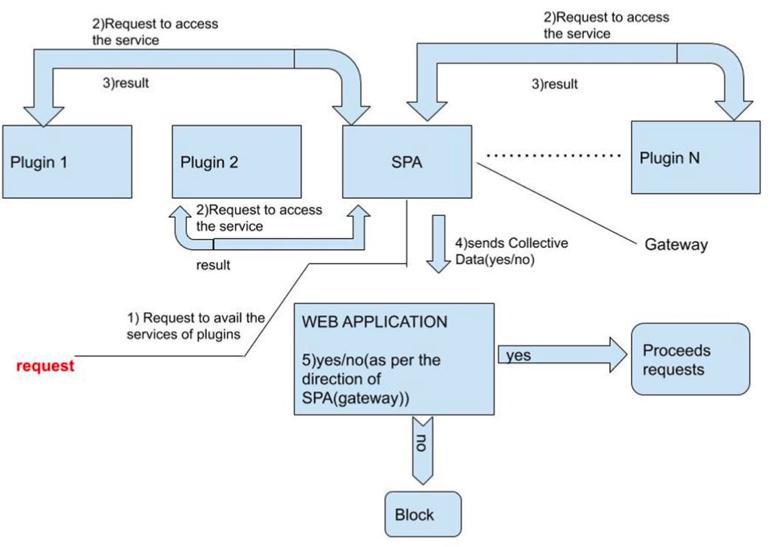
b. The website prints a 404 message if a SQL injectionisexecuted.
c. The aforementioned modifications, which were performed during the course of this project, were notexistentinthesystemthatwasinplacebefore.
d. Wewerelookingthroughtheerrorlogfilesonthe current system to find unusual requests and suspiciousactivity.Theself-protectingmechanism is included in the application and does not access the database in our suggested system. We use the self-protecting tool within the programme to detect harmful activities like SQL injection inside the application. This tool also aids in preventing injection assaults made to the website. Our programme uses a self-protecting tool, as shown infigurebelow,toexamineallanomalousactivity.
Fig- 2 :Workingof2nd case
Fig- 1 :Workingof1st case
Fig- 1 :BlockDiagramofProposedSystem
International Research Journal of Engineering and Technology (IRJET)

e-ISSN: 2395-0056
Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072
RASP limits attacks and only permits authorised users to accesstheprogrammebydistinguishingbetweenintruders and legitimate users for information. It serves as an additional layer of security for the application and keeps intruders out while it is running. Even small vendors can employruntimeself-protectingapplicationstosecuretheir products because they are affordable. The size or kind of theapplicationhasnobearingonit.
Server Web Apache (Apache HTTP Server)
Open-source web server software includes Apache HTTP Server. The term "web server" refers to a device that enableswebsiteownerstopublishmaterialonline.
i. Selected a web application and following was implemented:
a. Disable the web application access from remote system
b. UnderstandingApacheHTTPServer
c. Creating a Virtual Host in Apache and direct all communication of each web application through thateachHostwhenaccessremotely
ii. Apache's HTTP request interpretation includes loggingthefollowinginformationinafile: a. thedateandtime, b. theURLormodulethatwasrequested, c. andanyunusualactivity.
iii. The development of a Java classthatwill read the followinginputandprintittotheconsole a. WebApplicationName b. Userlogindetails
iv. Calling the JAVA Class from Apache and provide theinputs.
There are numerous phases involved in traffic analysis, such as gathering network data, examining that data, and analysingittoimprovesystemperformance.
i.
ii. ActivePassive
Create a second Java class that analyses the CSV file's contents and transforms it into scenarios or policies (a seriesofinstructionsintheformofatxt,prop,orXMLfile) thatpreventusersfromaccessingthewebsite.
We access the GET request in the Apache proxy when the usertriestoaccesstheprogrammeusingtheURL,and we extract the account number from there. We have our detailstobeobtainedwithinformationtakenfromtheGET request header. These details are subsequently transmittedtoaPerlscript,wherevalidationoccurs.Atthe back end, we execute the Perl script, which calls the Java executable file. The header information is checked against the user's previously collected data. Jar file running in the background does validation. We read the JAR log file and do the appropriate tests. This log file is read in Jar, and userauthenticationisverified.
The information will be provided by the Jar file, and we have established the prerequisites for carrying out the action.Thespecificaccountnumberobtainedfromthelog fileandtheGETrequestinApache(accountnumberofthe user if the user has logged in or logged out). The log file containsallinformationoneachuser'sloginorlogout.
Jar generates 0 or 1 depending on the data in the log file. Values 0 and 1 show that the user has previously logged outandhasn'tdonesorecently,respectively.Thisdatawas submittedtoaPerlscript.So,welooktoseeiftheuserhas engaged in any suspicious behaviour. If so, a message about unauthorised access is displayed. An error notice therefore develops if the value is 1. It prevents the user from using the application. If the number is zero, the user has logged out and is now free to utilise the website. He can then carry out any function within the application. Creatinga newaccountorloggingintoanexistingone can bedonenext.
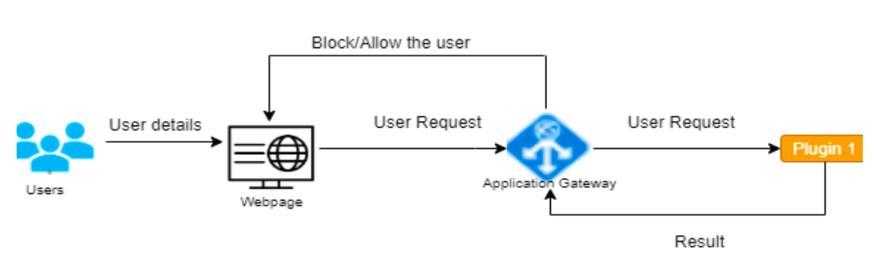
We send the user request to the gateway when a user attempts to access an application via a URL, and the gateway then sends the information to the plugin. The
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072
plugins check for the presence of binary SQL injection patterns, and if they do, they return 0 otherwise. If the resultis0,theuserisprohibitedfromvisitingthewebsite; otherwise, they are permitted. If a pre-existing account is accessed, we verify that the username, password, and account number are correct and that the user has logged out.Accessisnotpermittedifitisinvalid.Allowtheuserto carryoutoperationslikecheckingthebalance,transferring money, withdrawing money, or closing the account if it is valid.Deletetheentry from thedatabase iftheusercloses theiraccount.
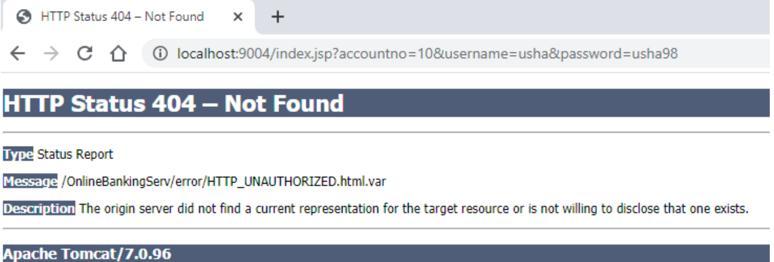
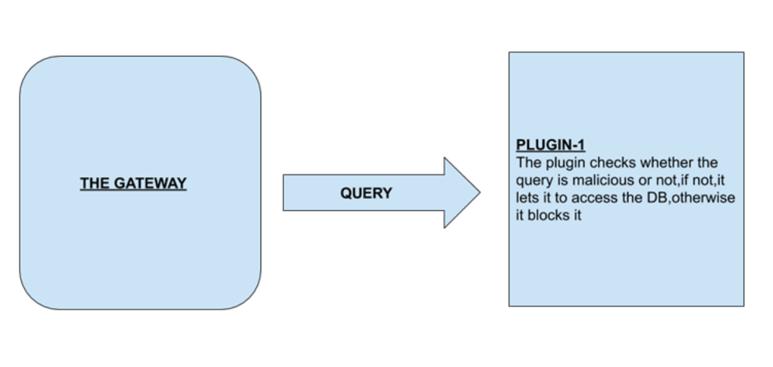
Fig -7 : illegitimateusernotallowedtoaccesswhenselfprotectingtoolisused
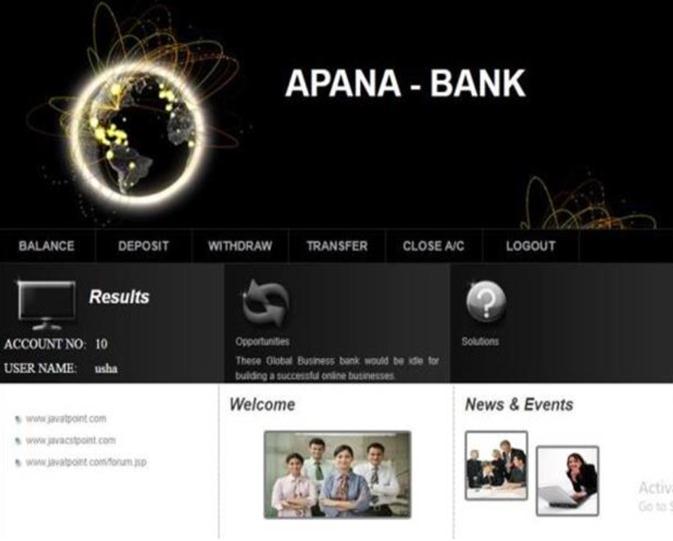
Fig – 4: Implementationof2nd case
Self-Protecting Applications are software friendlier, rely littleonthetypeofsoftware,andrequireminimaltechnical expertisetoutilize.Theyalsoofferarespectableservicefor safeguarding Web Applicationsagainstcriminal activity.It preventsdataleakageandshieldstheapplicationfromthe outside world. It safeguards the system from emerging dangers posed by any user simply by evaluating the patterns of user behavior. With its extremely transparent and practical methods, SPA, in contrast to other security software that is difficult to use and incompatible, can be utilizedbyanywebsite,fromastraightforwardsinglepage web application to a large social media application. Additionally, it doesn't call for any modifications to the Application's source code. SPA is therefore genuine softwareforprotectingWebapplications.
[1] Gartner, IT Glossary, http://www.gartner.com/itglossary/runtime-application-self-protection-rasp/
[2] Veracode, https://www.veracode.com/security/runtimeapplication-self-protection-rasp
[3] Zhongxu Yin, Zhufeng Li&Yan Cao “A Web Application Runtime Application Self-protection SchemeagainstScriptInjectionAttacks”2018
[4] SalemiMacro"AutomatedrulesgenerationintoWeb ApplicationFirewallusingRuntimeApplicationSelfProtection"2020
[5] Amal Saha and Sugata Sanyal. Application layer intrusion detection with combination of explicitrule-based and machine learning algorithms and deployment in cyber-defence program! https://arxiv.org/pdf/1411.3089.pdf, November 2014.
[6] Alexander Fry. Runtime application self-protection (rasp), investigation of the eectiveness of a rasp solution in protecting known vulnerable target applications. https://www.sans.org/readingroom/whitepapers/ application/runtime-

e-ISSN: 2395-0056
Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072
application-self-protectionrasp-investigationeffectiveness-rasp-solutionprotecting-vulnerabletarget-applications-38950,April2019.
[7] VivekGite.Linuxincrondinotifymonitordirectories for changes and take action. https://www.cyberciti.biz/faq/linuxinotifyexamples-to-replicate-directories/, December 2018.
[8] Adrian Lane. Understanding and selecting runtime application self- protection. https://securosis.com/assets/library/attachments/ Understanding_RASP_Immunio_V2.pdf,August2016.
[9] Dariusz PałkaMarek and ZacharaMarek Zachara. Learning web application rewall - benets and caveats. https://www.researchgate. net/publication/226351120_Learning_Web_Applica tion_Firewall_-_Benefits_and_Caveats,August2011.
[10]
Amal Saha and Sugata Sanyal. Application layer intrusion detection with combination of explicitrule-based and machine learning algorithms and deployment in cyber-defence program! https://arxiv.org/pdf/1411.3089.pdf, November 2014.