International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN:2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN:2395-0072
Department
Abstract - Since Satoshi Nakamoto published white Paper on Bitcoin in 2008, blockchain has (slowly)became one of the foremost mentioned strategies for securing data storage and transfer through decentralized, trust-less, peer-to-peer systems. This analysis identifies peerreviewed literature that seeks to utilize Blockchain for cyber security functions and presents a scientific analysis of the foremost often adopted blockchain security applications. In this proposed work, we are introducing blockchain technology in cybersecurity where IOT security, availability and decentralized storage of data and many more applications will be add on into the system. Thus the Intelligence Agencies and Cybersecurity Cell does not face any issues or drawbacks while operating, although cybersecurity is itself a very secure but after introducing blockchain in it, it will be impossible toseize.
Keywords – Blockchain in cybersecurity, roles, uses cases, methodology, making of more secure system.
India is home to a population that is unmoving in numerous socio-economic backgrounds. As per the living standards of individuals, a large vary of devices area unit in use - from high-end secured electronic devices to inexpensive mobile phones. This makes it troublesome for authorities to line uniform legal and technical standards to control data-protection. Additionally, digital attainment and awareness among thepopulationisverylow
Cyber-Securityreferstotheactofprotectiveandmaking certain the protection of laptop systems and electronic devices from targeted cyber-attacks, opportunist malware (- viruses, trojans and bugs) or accidental introductionofmalwarebyusers.
So, the main motto of this project is to ensure more secure system which is unbeatable and overcome the drawbacks which was faced earlier. This proposed application of blockchain in cybersecurity will work as decentralized system i.e. it every user will get to know activities and with the help of it, it will notify whenever anyoutsidertriestoinvadeitandifsomehowifinvasion is successful it will be impossible to change aur retrieve the data as each block in blockchain requires a security
key if anyone to tamper it, it will automatically become invalid.
Cybersecurity protects both raw and meaningful data, but only on internet-based threats. Organisations implement information security for a wide range of reasons. The main objectives are typically related to ensuring confidentiality, integrity, availability of companyinformation.
The main objective of this proposed work is to enhance cybersecurity by using blockchain technology As we all knowcybersecurityisitself a verysecurednetwork, but at some instances it is not so efficient as any organisationsoranyonecantamperthedataifequipped withtheknowledge.Asresultthedatawillbeinathreat, but by introducing blockchain in it we overcome this issue
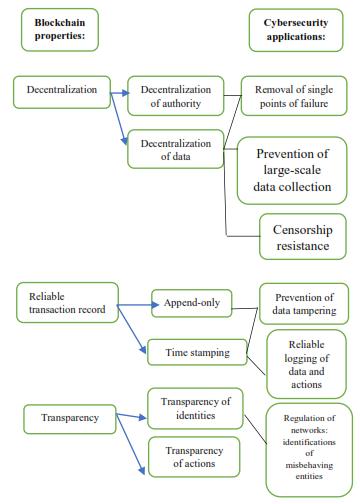
Thegoalofblockchainisto permit digital information, to be recorded and distributed, however not altered. During this manner, a blockchain is that the foundation of immutable ledgers, or records of transactions that can’t be altered, deleted or destroyed. Here we minimize the chance to a bigger extent. We also can’t ignore the point that it is decentralized service i.e. nobody should apprehend or trust anyone else. Every user within the network features a copy of actual same datawithinthevarietyofdistributedledger.Iftheuser’s ledger is altered or corrupted in any manner, it’ll be rejected by the bulk of the users within the network. In particular every block within the chain needs a security key,ifanybodytriedtocounterthat,theinformationcan become invalid for the trespasser and can’t operate any more. So, this method ensures most security of the information and prevents any variety of malpractice. This can facilitate the security agencies that’s serves for thenation.
Thisresearch will be qualitativeanalysistoevaluate the applicability of Blockchain technology in today’s cybersecurity industry. The paper will focus on two aspects of all the highlighted papers, to begin with will
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN:2395-0072
look at the latest implementations of the evolving Blockchain technology in cybersecurity. Second, it’ll check out the strategies available for deploying Blockchaincybersecuritysolutions.The maintakeaways from the research findings will be used to form a discussion on how Blockchain can afford security in today’sITuserenvironments.
Availability: In recent times, cyberattacks trying to impacttechnologyservices availablenesssquare onthe surge with DDoS (Distributed Denial-of-Service) being theforemostcommon types of attacks. However, in blockchain-based systems, DDoS attacks square measure expensive as the assaulter makes an attempt to overpower the network with an excellent variety of tiny transactions. Blockchains haven’t any single purposeof failure that decreasesthe possibilities ofIPbased DDoS attacks disrupting the traditional operation. Information remains accessible through numerous nodes and so full copies of the ledger are often accessed the least bit times. The mixture of multiple nodes and distributed operation makes the platformsandsystemsresilient.
IoT security: As farmuch IoT thinksabout, Blockchain technology stands out due to its ability to unravel measurability, reliability and privacy problems. It allows coordination between devices, furthermore as chase of immeasurable connected devices and process transactions. This is a decentralized approach in which cryptographic algorithms square measure enforced so client information getpleasurefrom biggerprivacy.It’s associate degree approach that eradicates faults and offers a resilient scheme. With the increasing application of AI and IoT, the protection of information and systems from hackers has forever been a serious concern. Usage of Blockchain for improved security by victimization device-to-device encryption to secure communication, key management techniques, and authentication is a potential use case to keep up cybersecuritywithintheIoTsystem.
Decentralized storage of crucial data: The blockchain-based decentralized storage system splits users’ files into varied tiny chunks of information, mentionedas“blocks”.Itthenencrypts everyblockwith
Likewise,allinformationgetsdistributedandholdonat decentralizedlocations.Ifinterlopersdecidetohackinto theselocations,theyhitencryptedblocksofinformation. What’smore,theywillonlybeabletoobtainachunkof information,nottheentirefile.This,insum,ishowever blockchain-baseddecentralizedstoragesystemsensure datasecurity. auniquehashorwithpublic-privatekeysanddistributes the blocks across multiple computers or “nodes”. This method of distributing information across the network ofnodeiscalled‘sharding’
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN:2395-0072
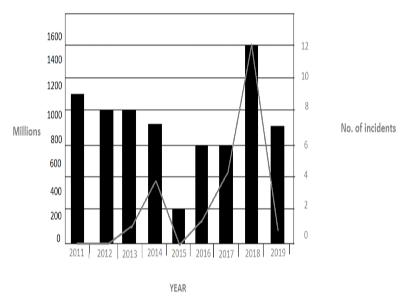
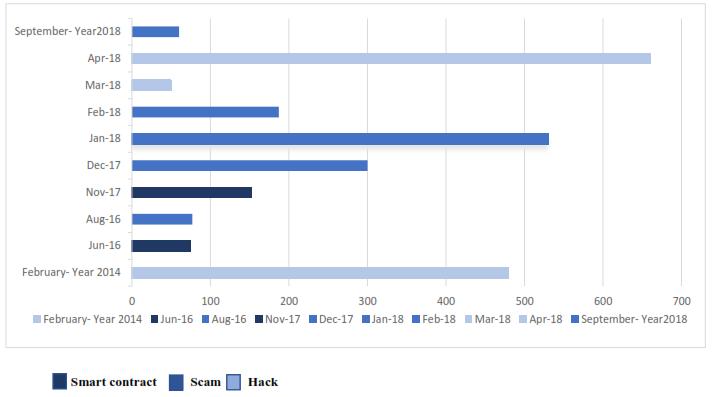
Network: Around 65 real world cybersecurity incidents haveoccurredroundtheglobeamid2011and2019.The incidentshaveadverselyaffectedtheBlockchainsystem. We calculatethe impact based on price ofthe costcoins at the time the attacks were discovered. However, these reports were discovered. However, these reports may differ a little from reality since the lack real life circumstances. We broadly divide the incidents as –hacks, scams and smart contract flow. The highest lose relates to hacking followed by scams and the contract flows. Figure-1, shows that the number of incidentsreducedasthepriceofBTCfell.Butassoonas thepricesoaredup,sodidthenumberofattacks.
Fig-3. Blockchain incidents 2011-2019.
International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN:2395-0072
Fig-4. Top10mostaffectedblockchainincidents.
For better understanding of the working of this proposed system, we can divide the whole procedure in two parts- firstly, the working of blockchain technology andsecondly,howthecybersecuritysystemworks.
So, in the first section weare going to discuss about the process of the blockchain technology. Blockchain is system of recording information in a way that makes it difficult or impossible to change, hack or cheat the system. A blockchain is basically a digital ledger of transactionsthat’sduplicatedanddistributedacross the complete network of computer systems on the blockchain.Eachblockinthechaincontainsanumberof transactions,andeverytimeanewtransactionoccurson the blockchain, a record of that transaction is added to every user’s ledger. The decentralized information managed by multiple users is known as Distributed Ledger Technology. Now, within the second part we are goingtodiscussregardingthecybersecurityandtheway it works. It’s sub-categorized in 3 points- analysis, implementation and support.
Analysis- It includes an intensive analysis of infrastructure, necessities and effective cyber threat scenario. Solid reasons for and against solutions. Joint realization of proof of construct, trial and take a look at surroundings
Implementation- Licensing support, consulting and deployments with the expertise from thousands of difficult IT security projects. Know how across industriesandcompanysizesandahighlevelofroutine.
Support- Troubleshooting, support and 24/7 instant facilitate with qualified contact persons. Certified power concerning product moreover as data concerning individual- environments. Enhancements, reviews and potentialanalyses.
In the paper 1: Cybersecurity through Blockchain technology: A Review. In October 2019, this paper was published by Alex. R. Mathew It was published in International Journal of Engineering and Advanced Technology (IJEAT). This paper looked at several use cases of Blockchain in the cybersecurity industry as envisioned by 30 researchers. It found that most researchers are concentrating on the adoption of Blockchain to protect IoT (Internet of Things) devices, networks,anddata.
In the paper 2: Blockchain for Cybersecurity and Privacy: Architectures, Challenges, and Applications: A Review. In July 2020, this paper was published by MaleheYassine, MamounAlajab, ImedRomdhani.It was publishedinTheInternalAuditandITAudit. Thispaper
International Research Journal of Engineering and Technology (IRJET)

e-ISSN:2395-0056
Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN:2395-0072
looked at Blockchain has moved beyond hype to realworldimplementationinabroadrangeofindustries(eg, finance, supply chain management, and Internet of Things) and applications (eg, cybersecurity and digital forensics),partlyevidencedbyitsevolutionoverthelast decadeorso.
This book focuses on the applications of blockchain in cybersecurity,privacy,anddigitalforensics,fordifferent industry sectors such as Internet of Things and healthcare.
In the paper 3: A systematic literature review of blockchain cyber security, in June 2020, this paper was published by Paul J. Taylor, Tooska Dargahi, Ali Dehghantanha, Reza M. Parizi, Kim-Kwang Raymond Choo This research has identified available recent research on how blockchain solutions can contribute to cyber security problems. The initial keyword searches forthisresearchandcurrentmediareports
highlight blockchain as a standalone technology that brings with it an exorbitant array of possible solutions forfinance,logistics,health,cybersecurity.
This research has focused solely on cyber security. Undoubtedly, there are worthy applications for blockchain; however, a decentralized, trustless system cannot by itself solve all problems one may uncover in thefieldofcybersecurity.
Blockchain technology continues to evolve and notice additional use cases within the modern times. One in every of the viable areas where it’s been studied and applied is cybersecurity. The Blockchain infrastructure makes it extremely sensible in addressing the present security challenges in areas like as IoT devices, and information in transmission and storage. Alongside this, alternativemajorareaunitsasofBlockchainsecurityare networks and information. As ascertained within the discussion, the Blockchain technology is be want to secure IoT devices through additional reliable authentication and information transfer mechanisms. This will forestall hackers from breaching into these devices which frequently ship with poor security configurations.
In future, for obvious reasons, Blockchain technology’s scope lies within the field of Cybersecurity. Though the Blockchain ledger is open and distributed, the information is secured and verified. Theencryptionis finished through cryptography to eliminate vulnerabilities like as unauthorized information tampering bolstered the existing efforts to enhance securityandtodetermaliciousactors.
1. Swan,Melanie.Blockchain:Blueprintforanew economy."O'ReillyMedia,Inc.",2015.
2. Crosby, Michael, et al. "Blockchain technology: Beyond bitcoin." Applied Innovation 2.6-10 (2016): pp.71.
3. Iansiti, Marco, and Karim R. Lakhani. "The truth aboutblockchain."HarvardBusinessReview 95.1 (2017):pp.118-127.
4. CachinC.Architectureofthehyperledgerblockchain fabric. InWorkshop on distributed cryptocurrencies andconsensusledgers2016,310(1),pp.4.
5. Coindesk: Bitcoin venture capital funding, www.coindesk.com/bitcoin-venture-capital, 17 July 2019.
6. CoinMarketCap: Cryptocurrency market capitalizations Coinmarketcap, https://coinmarketcap.com/,17July2019.
7. Chowdhury, M.J.M., Colman, A., Kabir, M.A., Han, J., Sarda, P.: Blockchain as a notarization service for data sharing with personal data store. In: TrustCom/BigDataSE2018,IEEE(2018)1330–1335.
8. V. Buterin, A Next-Generation Smart Contract and Decentralized Application Platform, Etherum, 2014[Online].
9. T.Salman,M.Zolanvari,A.Erbad,R.Jain,M.Samaka, Securityservicesusingblockchains:astateoftheart survey, in: IEEE Communications Surveys & Tutorials,2018.
10. S. Nakamoto, Bitcoin: a peer-to-peer electronic cash system,2008.