International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072
1 Associate Professor, Dept. of Computer Science and Engineering, vellore institute of techonology, vellore , Tamil nadu.
2,3,4,5Btech student, CSE , vellore institute of techonology, vellore , Tamil nadu. ***
Abstract - In this examination, the close to home result of the watcher was broke down while they watch the film before genuine delivery is, during its review. Generally Functional Magnetic Resonance Imaging gadget was utilized to survey human cerebrum movement however ended up being Non attainable and expensive, so EEG sensors were utilized to screen and record the working of the mind of workers for additional examination. We proposed a model to utilize the gathered information through EEG sensors were broke down utilizing counterfeit brain network which was utilized to find high and low of various mind waves planning to the feelings portrayed in each scene of the film. A crossover Recurrent Neural Network (RNN) Extreme Learning Machine (ELM) structure for wrongdoing area of interest order is proposed. The RNN removedthevitalelementsfromtheinformationandtookin the example utilizing Long Short-Term Memory (LSTM) design. ELM was applied toward the finish of the layers for our characterization issue. The dataset under study was assessed by the proposed mixture RNNELM which didn't utilize the backpropagation procedure. Execution measures, for example, exactness, accuracy and review were determined to approve our proposed model. Our proposed model brought about giving help to film producers who could concentrate on the beat of crowd before the genuine deliveryandcouldconsolidatechanges ifessential.
Key Words: RNN,ELM,LSTM,AccuracyCriminology studies focuses on identifying patterns in crime and also in predicting the occurrence of crime. Crimeisknowntohavepatternsspatiallyatvariouslevels of aggregation. Crime is either planned or opportunistic and does not happen at random [1]. The study about the awareness space of potential offenders can lead to identification of various patterns that can help in preventing the occurrence of the crime. Two main questionsthataretobeansweredare:howtopreventthe occurrence of crime and where the crime will possibly occur.Studiesrevealthatifwewanttoanticipatewherea crime will happen, then we need to look into the location where that crime has already occurred. This theory is calledasrepeat-victimizationornear-repeatvictimization. Crimessuchasresidentialburglary,theft,chain-snatching, etc.fallunderthecategoryofrepeat-crimeswhichleadsto
repeat-victimization [2]. In these types of crimes, we can see an underlying pattern or a unique signature, understandingwhichcanhelpinreducingthecrime.Some of the reasons for this type of crimes can be: the vulnerable location, lack of infrastructure like improper street lights, chaotic lifestyles in the location such as highly crowded area, etc. Repeat victimizations can be determined by using probability distribution functions to findoutthetimeintervalbetweentheoffences.Eachtime a crime occurs, the repeat victimization can also be modelled as a series of events with changing likelihood values. Lately, researchers show significant interest in analysisofcrimehotspotsbyexploitingthespaceandtime of occurrence of crime known as the spatio-temporal analysis. In most of the hotspot analysis available in literatures, space and time are treated as two separate entities.Thisincreasesthechanceofmissingoutonsome of the important statistics pertaining to crime analysis. Exploring the spatio-temporal signatures, the regularities present in the repeat-crimes can be studied comprehensively [3]. Information examination in medication has for long been the region of analysts, yet clinical information are coming to past the simply quantitative to take more complicated structures, for example, for example, printed data in EHR, pictures in numerous modalities, all alone or blended in with differentsortsofsigns,ordiagramsdepictingbiochemical pathwaysorbiomarkerconnections[4].Pastthemoreold stylefactualmethodologies,man-madeconsciousness(AI) and, more specifically, AI (ML) are drawing in much interest for the examination of clinical information, regardless of whether ostensibly with a moderately low effect yet on clinical practice. It was at that point a question of scholastic conversation very nearly quite a while back [5]). This portrayal is generally important to enormous IT organizations however accurately mirrors the ebb and flow cycle. Regardless, this implies that AI frameworks and items are arriving at the general public overall,and,hence,thatculturalissuesconnectedwiththe utilization of AI overall and ML specifically ought not be disregardedanymoreandsurelynotinthemedicationand medicalcarespaces.
Once more, any utilization of AI and ML in real clinical practice will undoubtedly create conversation about its
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page1091

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072
legitimate limits and suggestions. A relevant model is the new execution. This order commands a right to clarification of all choices made via "computerized or misleadingly shrewd algorithmic frameworks" [6]. As per The right is to clarification suggests that the "information regulator" lawfully will undoubtedly furnish mentioning residents with "significant data about the rationale in question, as well as the importance and the imagined outcomesofsuchhandlingfortheinformationsubject"[7]. The ramifications ofGDPR for the utilization ofAIandML in medication and medical services are not too hard to even consider appreciating. Any AI-or ML-based clinical choice emotionally supportive network whose reason it is to help the clinical specialists in their dynamic will be unequivocally giving a (semi)automated choice on a person.Theinformationregulatorforthissituationwillbe theclinicalmaster(fromattendantstoexperts[8])andthe establishment this master has a place with. A clinical master or any medical care framework representative utilizing these innovations should have the option to decipher how they arrived at explicit choices and should have the option to clear up those choices for any human impacted by them. It is idea to predict crime using mobile data and demographic data. While the previous research works focused on using historical background knowledge orprofilingtheoffenders,theauthorssuggestedtheuseof aggregated and anonymized human behavioral data. Since the usage of mobile phones has been increased over the last few decades, using the mobile data becomes a great source for tracing human behavioral data. The core idea proposed in the research works were as follows. 1. PredictingcrimehotspotsinEuropeanmetropolisbyusing the aggregated and anonymized mobile data combined withdemographics.2.Comprehensiveanalysisofproposed model used in predicting the crime occurrence and comparison with stateof-art methods. 3. Finally, discussionsonpracticalandtheoreticalimplicationsofthis proposedmethodwerediscussed.Spatiotemporalanalysis helps to identify a place to be either crime free or crime specific in nature based on the location and time. Both location and time are considered parallel because for example, a place can be a hotspot at early morning, whereas the same place can be a crime-free area in the evenings.Wecanalsoidentifyeachoftheplaceasawarm spot or hot spot or cold spot based on identifying the necessary regions in the given time interval. If a place is identified as a warm spot, the probable prediction of occurrenceoftherepeatcrimeoccurringthereishigheras compared to place that is identified as a cold spot. When comparing between a warm and hotspot we also identify that the crime rate at one spot that is warm may increase into a hotspot thereby increasing the rate of repeat crime orevenslideontoacoldspotduetopolicingactivitiesand other security parameters depending upon the geographic intensitiesprevalentinthatspot[9,10].
ELM is arising to be perhaps of the most conspicuous technique in AI. It was first figured out as a solitary layer feed forward brain organizations. The secret hub boundaries in ELM are haphazardly created proceeding acquire the preparation information [10]. The ELM which was utilized essentially in light of the lesser preparation mistake and preferred speculation execution over the Backpropagation calculation is present. A typical neural networkisgenerallyslowbecauseofthegradientdescent based algorithms which are used to prepare the brain organizations and boundaries are iteratively tuned by the calculations. Least preparation mistake, least standard of loads and quicker preparing process makes the ELM models more believable. The ELM was proposed to have random training weights and random biases. This was because of the fact that traditional neural networks require parameter tuning that created dependencies on theparameterswhichmakesitslow.ELMsweredesigned not to use backpropagation algorithm due to several reasons. Few of the reasons were if the learning rate in a backpropagation algorithm was very small, the algorithm convergedveryslowly.Ifthelearningratewasverylarge, thenthealgorithmcompletelydiverged[11].Aninsightto ELM was proposed [12] which answered two major questions. Without tuning the neurons, weights and biases, is it possible to obtain a good performance? Is there a unified framework available for feed forward neural networks and feature space selection? This researchworkfocusedonprovidinginsightstohowELMs can deal with irregular neurons, arbitrary highlights and pieces. It was demonstrated that ELMs will more often than not beat SVM utilizing similar bits. In ref. [13] investigated the application of adaptive ELMs for time series prediction. This work comprised of testing the adaptively of ensemble models on a non-stationary time series problem. A common assumption when handling time series problems is that the data generated by underlying process is stationary and identically distributed.However,inmostofthepracticalapplications, it is not the case. ELMs with varying complexity were generated and trained on the data. The individual ELMs were combined to form the ensembles. Two experiments were conducted with this adaptive ELMs one for stationary time series and another one for a nonstationary time series. In both the methods, the results that were achieved were comparable with the other best methods that existed. It is presented a method by which ELM can be used for missing value imputations. Gaussian Mixture model was developed which was designed to handle the missing values whereas ELM was used to devise multipleimputation strategyinordertoobtainthe final estimates. The ultimate aim for implementing any machine learning algorithm is the accurate prediction or forecast of the future values. But there are chances that the available data might contain missing values. The first
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072
step should be to clean the missing values which can be done by imputing the missing values with statistical measures of central tendency such as mean, median or mode whichever is applicable [14]. The approach proposedinthismethod,however,madeuseofGMMona dataset that had missing values. New datasets were generated using the GMM deployed in the previous step and then ELMs were built on each of the generated dataset. Finally, all ELMs were combined to provide the finalestimate.FewadjustmentsweregiventotheGMMsin order to tackle the missing values. Multiple imputations caused an increase in the overall computational time. However,atrade-offwasobtainedbydeployingELMsince theysubstantiallyreducethetrainingtime[15].
Crime occurrences are well planned based on the environmental factors such as improper infrastructure such as poor street lighting, deserted streets, etc. Recent studies suggested that crime hotspots are the tools that provide strong insights on exposing the areas that are vulnerable to crime occurrence. Erstwhile research established that the crimes cluster over space and time (Johnson et al. 2007). But how the crimes vary concurrently has not been studied comprehensively. In this proposed work, both the space and time are taken concurrently and the pattern of crime is studied. Creating ahotspotforthecrimeregionscanleadtoacognizancefor the police. Spatio temporal analysis can also help the police in increasing the patrol in certain areas where crimes can be determined to occur at a specific time periodorcanremovethepatrolfromfewareaswhichare not vulnerable at specific instances of time. From the Philadelphia's crime data, top 15 locations where the repeatcrimesaremorearefilteredandagraphisplotted. We depict our crossover engineering of RNN-ELM model. ELM is a solitary layer feed forward (FF) brain network which can be seen in Fig. 1. The ELM incorporates an information layer, a secret layer with 'n' neurons and a result layer. For N unmistakable perceptions of (xi,yi), where xiare the nin theinfolayerandyiaretheninthe resultlayers,thetypicalELMcanbecharacterizedas:
The loads and predisposition are arbitrarily created for theELM.AconventionaltypeofEqu.(1)canbecomposed asdisplayedinEqu.(2)
(2)
With the arbitrarily relegated values to the weight vector wi and predisposition bi, the result vector H is resolved utilizingEqu.(3).
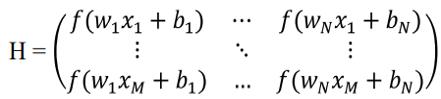
(1)
Wherej=1,2...N, wiaddressestheloads related with input n and the ith stowed away n, Bi are the loads interfacing theithstowedawayneuronsandtheresultlayer,bi'sare theinclinationvector
Start Given a preparation set (xi, yi), an enactment capability f and number of stowed away hubs N Step 1: Randomlydoleoutinputloadswiandpredispositionsbi,I [1,N];Step2:CalculatethesecretlayeryieldlatticeHStep 3:CalculateyieldweightgridB=H'YEndELMisgenerally utilized in relapse and characterization issues. In our utilization case, ELM is utilized for multiclass characterization. Our half and half engineering includes RecurrentNeuralNetworkwithLSTMwhichcanextricate pertinent highlights, store and recollect the transitional outcomes and ELM can be utilized for arranging the wrongdoing.
Thepointofthisexaminationworkistousetheupsidesof utilizingRNNandELM.Theinformationthatisutilizedfor this debate is philosophers wrongdoing information. We appointed the three gatherings of bunches as areas of interest, cold spots and warm spots. Areas of interest are the locales wherein there are extremely horror rate, cold spotsarethosedistrictswhereinthecrimepercentagehas diminished because of expanded policing exercises and
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072
warmspotsarethosedistrictswherethecrimepercentage is expanding, neglecting to screen these areas could lead themtobecomeareasofinterest.Rehashviolationscanbe displayed as a period series information since they are consecutive, i.e., there is high chance of a wrongdoing happeninginthedistrictwhereithadbeforehappened(in ongoingpast).
Accuracy Precision Recall
RNNwithBP 97.34% 91.82% 83%
RNNwithELM 97.89% 95.78% 91.26%
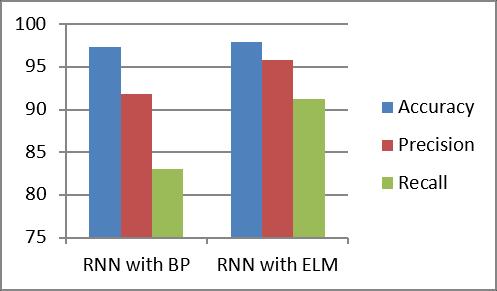
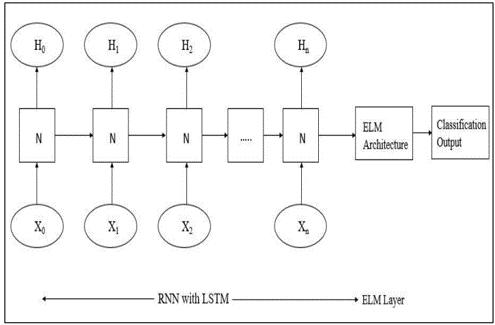
Fig.2:RNNELMHybridarchitecture
This sort of information requires an engineering which can store earlier data. For this prerequisite, RNN are the well suited design as they have LSTM which can store earlier data and give that to the progressive layers. Generally, a backpropagation system would be utilized, which feeds back the result to the information layer again to expand the precision. Our half and half design is displayed in the Fig. 2 underneath. We propose to involve ELM design in a various leveled manner in the wake of applying RNN for grouping issue and give a similar examination on how our RNN-ELM mixture and conventional RNN with BP observe for the information netherstudy.
We trained the model using Keras library by specifying adamoptimizer.Backpropagationalgorithmisbydefaulta part of Keras implementation of RNN. Cross entropy is used as the loss function and the metrics used is accuracy with 100 epochs. An epoch is the number of input objects for which one iteration of training occur. Different combinations of epochs were given such as 50,100 and 150. 100 epochs yielded the best accuracy of all others. Execution measures, for example, exactness, accuracy and reviewaredeterminedforthetestdataset.Fortheinferior piece of our investigation, we hold the prepared RNN model and the component determination. Rather than applying the BP, we employ the ELM at this crossroads to anticipate the evaluate for the test dataset. We compute a similarpresentationmeasureslikeexactness,accuracyand review. The Table 1 represents the exhibition evaluate for ourdataset.
One of the main reasons for this result is that the type of crimedataissequential.WiththeseoutputsfromRNN,we can decide that if the area at a given time is a warm spot, more policing activities are to be provided so that wecan try to reduce the number of repeat crimes occurring in thatarea.Similarly,iftheareaatagiventimeisahotspot, suitable measures are to be taken to reduce the criminal activity.
ThepointofthisworkistousetheRNN-ELMengineering and to dissect the impact of this half breed technique on the presentation measures. The wrongdoing characterization is an extremely difficult undertaking and area of interest investigation has previously become one of the fascinating examination subjects among specialists across the globe. RNN with LSTM network gives the element extraction and furthermore supports arrangement. Nonetheless, we present the ELM engineering eventually to add one more layer of arrangement. Though not much change in accuracy, eliminates much of false positives as well as false negatives which showed an increase in the precision and recall value. Although the traditional hotspot analysis cannotberuledoutcompletely,theanalysiscarriedoutin this study uses both the space and time factor concurrently which gives a more efficient solution to the crimetrends.Theinclusionsofdeeplearningmethodsadd to the robustness of the system as the results that are predicted are more accurate and precise. The results of thisanalysisprovideaprogressivesteptounderstandthe effectofresidentialburglaries.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 09 Issue: 08 | Aug 2022 www.irjet.net p-ISSN: 2395-0072
1. Chen, M., Mao, S., & Liu, Y. (2014). Big data: A survey. Mobile networks and applications, 19(2), 171-209.
2. BacciuD,LisboaPJ,MartínJD,StoeanR,VellidoA: Bioinformatics and medicine in the era of deep learning; in Proceedings of the European Symposium on Artificial Neural Networks, ComputationalIntelligence andMachineLearning (ESANN). Bruges, Belgium, i6doc.com, 2018, pp 345–354.
3. Flach, P. and Kull, M., 2015. Precision-recall-gain curves: PR analysis done right. In Advances in neural information processing systems (pp. 838846).
4. Cabitza F, Rasoini R, Gensini GF: Unintended consequences of machine learning in medicine. JAMA2017;318:517–518.
5. Chen, Y.L, Tang.K, Shen R.J and Hu, Y.H 2005. Market Basket Analysis in a multiple store environment.DecisionSupportSystems,40(2).Pp 339-354.
6. VellidoA,Martín-GuerreroJD,LisboaPJG:Making machine learning models interpretable; in: Proceedings of the European Symposium on Artificial Neural Networks, Computational IntelligenceandMachineLearning(ESANN2012). Bruges,Belgium,i6doc.com,2012,pp163–172.
7. Mamoshina P, Vieira A, Putin E, Zhavoronkov A: Applicationsof deeplearningin biomedicine.Mol Pharm2016;13:1445–1454.
8. Fernández-Alemán JL, Señor IC, Lozoya PÁO, Toval A: Security and privacy in electronic health records: a systematic literature review. J Biomed Inform2013;46:541–562.
9. Zhang,Y,Wang,Y,Zhou,G,Jin,J,Wang,B,Wang,X & Cichocki, A 2018, ‘Multi-kernel extreme learning machine for EEG classification in braincomputer interfaces’ Expert Systems with Applications,vol.96,pp.302-310.
10. Wu, Z & Wang, H 2016, ‘Super-resolution reconstruction of SAR image based on non-local means denoising combined with BP neural network’,arXivpreprintarXiv:1612.04755.
11. M. Bkassiny, Y. Li, and S. K. Jayaweera, “A survey on machine learning techniques in cognitive
radios,” IEEE Communications Surveys & Tutorials,vol.15,no.3,pp.1136–1159,Oct.2012.
12. S. Marsland, Machine learning: an algorithmic perspective.CRCpress,2015.
13. P. Harrington, “Machine Learning in action”, Manning Publications Co., Shelter Island, New York,2012.
14. Tayal,DK,Jain,A,Arora, S, Agarwal,S,Gupta,T & Tyagi, N 2015, ‘Crime detection and criminal identification in India using data mining technique’, AI & society, vol. 30, no. 1, pp. 117127.
15. Sovilj, D, Eirola, E, Miche, Y, Björk, KM, Nian, R, Akusok, A & Lendasse, A 2016, ‘Extremelearning machine for missing data using multiple imputations’ Neurocomputing, vol. 174, pp. 220231.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page1095
