International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072
ABSTRACT: Searchable encryptionallowsyou touploadan encrypteddocument toa remote, honestandsuspiciousserver andquerythisdataontheserverwithoutfirstdecryptingthedocument.Withtheadventofcloudcomputing,dataownersare encouraged to move advanced data management systemsfrom on premises locationsto commercial publiccloudsto reduce flexibilityandcosts.However,forprivacyreasons,sensitivedata mustbeencryptedpriortooutsourcing,and thetraditional useofdatabasedonplaintextkeywordsearcheshasbeendiscontinued.Therefore,itisimportanttoimplementanencrypted clouddataretrievalservice.Giventhelargenumberofdataconsumersanddocumentsinthecloud,itisimportantthatsearch services support multiple keyword queries and result similarity rankings to meet the needs of effective data retrieval. This paperproposesa securemulti keywordsearchfor encryptedclouddata basedonthequalityandeaseofuseofsendingand storingclouddata.WealsousedtheTripleDES(DataEncryptionStandard)algorithmforencryptionanddecryptionkeysfora secure authentication process. The encryption process uses different key sizes. Our analysis shows that the proposed approach is safe against attacks by adaptively selected keywords. This solution is very efficient, can be applied to real cloud storagesystems,andalsospeedsupencryptionanddecryption.
Keyword: CloudComputing,DataEncryptionStandard,MultikeywordSearchableencryptionallowsyoutoqueryencrypteddatainthecloudwithoutdecryptingit.However,becausethe relationships between variables are fundamentally different, most SE solutions focus on SQL queries and cannot be easily appliedtospatialdata.Toenablethequeryserviceforencryptedspatialdata,wehavetraditionallyusedaspace fillingcurve toconverttheoriginalpositionofthePOItoaone dimensionalindexvalue.Aspace fillingcurveisacurvethatintersectsall partitions of a closed space without intersecting itself. In this way, each curve is a curve that intersects each partition of a closedspace withoutintersecting itself.Inthis method, eachpoint inmultidimensional spaceis mapped to one dimensional space as a value. The standard Hilbert curve (SHC), a sort of space filling curve, is employed as a building block in many schemes for spatial data processing, which can protect the confidentiality of outsourced geographical data and enable successfulspatialenquiries.Userscanusethetransformation keyandtheoriginalgeographicquerytocreateaquerytokento retrieveencryptedspatialdata.
As a result, fine grained validation feature approval is supported. That is, only users whose validation structure matches the allowed area can validate the query results. Cloud storage is a computer data storage system that stores digital data ina logical pool calledthe"cloud.".Physical storageisoftendistributedacross multipleservers(sometimesindifferent locations), and the physical environment is typically owned and managed by the hosting company. Enterprises only have to payforthe storagetheyuse.
Thisusuallycorrespondstotheaveragemonthlyusage.I'mnotsayingthatcloudstorageischeaper.Rather,itcosts anongoingcostratherthananinitialcost.Spatialdatabasesareusedtostoreandquerydatathatrepresentsobjectsspecified in geometric space. Most spatial databases support the representation of simple geometric objects such as points, lines, and polygons.Resistsunilateralaccessinsideandoutsidethecloud.Sensitivedatasuchasemail,personal health records, photo albums, and taxrecords may need to be encrypted by thedata owner before being offloaded to the commercial public cloud. However, with traditional plaintext keyword search based data usage services, only users whose validation structure matches the allowed area need to validate the query results. Cloud storage is a computer data storage system that stores digital data in a logical pool called the "cloud." Physical storage is often distributed across multiple servers (sometimes in differentlocations),andthephysicalenvironmentistypicallyownedandmanagedbythehostingcompany.Enterprises only
International Research Journal
Engineering
Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072
havetopayforthestoragetheyuse.Thisusuallycorrespondstotheaveragemonthlyusage.I'mnotsayingthat cloudstorage ischeaper.
Rather, it costs an ongoing cost rather than an initial cost. Spatial databases are used to store and query data that representsobjectsspecifiedingeometricspace.Mostspatialdatabasessupporttherepresentationofsimplegeometricobjects suchaspoints,lines,andpolygons.Tocounterunilateralaccesstosensitivedatainsideandoutsidethecloud.Emails,personal healthrecords,photoalbums,taxdocuments,etc.mayneedtobe encryptedbythe data ownerbeforebeingoffloadedtothe commercialpubliccloud.However,thisremovesthetraditionaldatausageservicebasedonplaintextkeywordsearch.
ThecloudcomputingservicemodelsareSoftwareasaService(SaaS),PlatformasaService(PaaS)andInfrastructure as a Service (IaaS). The Software as a Service model provides pre built applications with the required software, operating system,hardware,andnetwork.PaaSprovidesoperatingsystems,hardware,andnetworks,andcustomersinstallordevelop theirownsoftwareandapplications.TheIaaSmodelprovidesonlyhardwareandnetworks.Customersinstallordeveloptheir ownoperatingsystems,software,andapplications.
Cloud services are typically delivered via a private cloud, community cloud, public cloud, or hybrid cloud. Services provided by the public cloud are generally provided over the Internet and are owned and operated by cloud providers. Examplesincludepublicservicessuchasonlinephotostorageservices,emailservices,andsocial networkingsites.However, enterpriseservicescanalsobeprovidedinthepubliccloud.
In a private cloud, the cloud infrastructure is dedicated to a particular organization and is managed by the organizationorathirdparty.Inthecommunitycloud,servicesaresharedbymultipleorganizationsandareonlyavailableto thosegroups.Infrastructuremaybeownedandoperatedbyyourorganizationorcloudserviceprovider.Hybridcloudsarea combinationofdifferentmethodsofresourcepooling(forexample,acombinationofpublicandcommunityclouds).
Cloudservicesare popular because theycan reduce the costandcomplexityof owningand operatingcomputersand networks.Cloud usersdon'thavetoinvestinITinfrastructureorbuyhardwareor softwarelicenses,reducing upfrontcosts, improving return on investment, rapid deployment, customization, flexible use, and new innovations. The solutions you can takeadvantageofnewinnovations.
Inaddition,cloudprovidersthatspecializeinspecificareas(suchasemail)canofferadvancedservicesthatmaynot beavailableordevelopedbyasingleorganization.Otherbenefitsforusersarescalability,reliability,andefficiency.
Scalabilitymeansthatcloud computingoffersunlimitedprocessingpowerandstoragecapacity.Thecloudisreliable in that you can access your applications and documents from anywhere in the world over the Internet. Cloud computing is oftenseenasefficientbecauseitallowsenterprisestofreeupresourcesandfocusoninnovationandproductdevelopment.
Another potential advantage is that your personal information can be better protected in the cloud. In particular, cloud computing can incorporate privacy protection into technology from the beginning and improve efforts to use better securitymechanisms.CloudcomputingenablesmoreflexibleITprocurementandexpansion,andmaybeabletoadjuststeps basedondataconfidentiality.Widespreaduseofthecloudcanalsopromoteopen standardsforcloudcomputingthatspecify basicdatasecuritycharacteristicscommontodifferentservicesandproviders.Cloudcomputingcanalsoenableabetteraudit trail.Moreover,theinformationinthecloudisnoteasilylost.
C.Guo,R.Zhuang,Y.Jie,K.Choo, andX. Tang [1] Secure range search of encrypteddatafromIoTdevices.Inparticular,use homomorphic, order maintaining encryption (OPE) to encrypt data published by the data owner. Then create a data index usingak dtree(KDtree).Theseschemesaredesignedtoensuretheprivacyofthedatasetwithoutsacrificingtheefficiencyof
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072
keyword searches on the (encrypted) dataset. Demonstrate that our scheme can preserve both data and query privacy and evaluateitsperformancetodemonstratethis.
Y. Wang, Q. Wu, B. Qin, W. Shi, R. Deng, and J. Hu [2] Cloud storage systems provide distributed clients with simplified file storageandsharingservices.Toaddressintegrity,controllableoutsourcing, and origin auditing concerns onX. Yao, R. Zhang, Y. Zhang, and Y.Lin
[3] Social data outsourcing is a new paradigm for effective and efficient access to social data. In such systems, a third party socialdataprovider(SDP)purchasesthecompletesocialdatasetfromanonlinesocialnetwork(OSN)operatorandresellsitto dataconsumers.Adataconsumerisanindividualororganizationthatneedscompletesocialdata.Meetscertaincriteria.SDP isnot completelyreliableandreturnsfalsequeryresultstodataconsumersbyaddingfakedata ordeleting/modifyingtrue data in favor of companies wishing to pay. This white paper begins an investigation into the outsourcing of verifiable social data.Thisstudyallowsdatauserstoverifythe authenticity of the social data returned by theoutsourcedfiles,theypropose anidentity baseddataoutsourcing(IBDO)schemeequippedwithSDP.
Y. Zhang, C. Xu, X. Liang, H. Li, Y. Mu, desirable features advantageous over existing proposals in securing outsourced data. First, the IBDO scheme allows users to allow a dedicated proxy to upload data to a cloud storage server on their behalf. For example,acompanycanallowsomeemployeestouploadfilestotheircloudaccountinacontrolledway.
and X. Zhang [4] Cloud storage services allow users to offload data to cloud servers and save on local data storage costs. However,unlikeusinglocal storage devices,usersdo notphysicallymanagethedata stored on cloudservers.Therefore, the data integrity of the offloaded data is an issue. Many public validation schemes have been proposed to allow third party auditorstoverifytheintegrityofauser'sdata.Theseschemesmake theunrealisticassumptionthattheverifierhassufficient computationalpowertosupporttheverifier'sexpensiveverificationcosts,communications,andcomputationalefficiency.
K.Yang,Q.Han,H.Li,K.Zheng,Z.Su,andX.Shen[5]Controllingaccesstolargeamountsofbigdatacanbeadaunting task, especially if big data is stored in the cloud. Ciphertext policy attribute based encryption (CPABE) allows end users to encrypt data based on the access policy defined for some attributes of the data consumer, and only data consumers whose attributesmeettheaccesspolicyencryptthedata.Itisapromisingencryptiontechnologythatenablesyoutomakeit.Decode. CPABE addstheaccesspolicytotheciphertextincleartextformat.Thismayrevealpersonalinformationabouttheenduser. Theexistingmethodonlypartiallyhidestheattributevalueintheaccesspolicy,buttheattributenameisnotyetprotected.
J.Li,R.Ma,andH.Guan [6] Cloudstorageprovidesconvenient,large scale, andscalable storage at a low cost, but privacy is amajorconcernthatpreventsusersfromtrustingandstoringfilesinthecloud.Onewaytoimproveprivacyfrom the data owner's point of view is to encrypt the file before it is offloaded to the cloud and decrypt it after it is downloaded. However, data encryption is a significant overhead for mobile devices, and the data acquisition process requires complex communicationbetweenthedataconsumerandthecloud.Normallywithlimitedbandwidthcapacityandlimited batterylife, these issues introduce heavy overhead to computing and communication as well as a higher power consumption for mobile deviceusers,whichmakestheencryptedsearchovermobilecloudverychallenging.
H.Tian,Y.Chen,C. C.Chang,H. Jiang, Y.Huang,Y.Chen,andJ.Liu[7]Cloudstorageisanincreasinglypopularapplicationofcloudcomputingthatcanprovideon demanddataoutsourcingservicestobothorganizationsandindividuals.However,usersmaynot completelytrusttheircloud serviceprovider(CSP)becauseitisdifficulttodetermineiftheCSPmeetstheirlegalexpectationsfordatasecurityTherefore, it is very important to develop efficient verification methods to increase the trust of data owners in cloud storage. This whitepaperintroducesanewpublicauditschemeforsecurecloudstoragebasedondynamichashtables(DHT).Thisisanew 2D data structure that resides in the Third Parity Auditor (TPA) to map data property information records. In contrast to existing work, the proposed scheme migrates allowed information from CSP to TPA, thereby significantly reducing computationalcostsandcommunicationoverhead.
Sun,S.Yu,W.Lou,Y.T.Hou,andH. Li
[8] Searching with encrypted data is a very important technique in cloud computing, and pre outsourcing encryption is the basic solution for protecting user data in untrusted cloud server environments. Many secure search schemes have a single
International Research Journal of Engineering
Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072
contributorscenariowhereapagingrecordorasecuresearchableindexofrecordsisencryptedandisusuallymanagedbya single owner based on symmetric encryption. I'm in focus. In this paper, they attention on a distinctive but extra difficult situationinwhichtheoutsourceddatasetmaybecontributedfromacouple of proprietors and are searchable with theaidof using a couple of users, i.e., multi consumer multi contributor case. Inspired byattribute based encryption (ABE), the first attribute based keyword search scheme with efficient user revocation (ABKSUR) that enables scalable, fine grained (ie, file level)searchauthentication.Introduce.Ourschemeallowsmultipleownerstoindependentlyencryptdataandoffloadittoa cloudserver.
M. Talha, I. Kamel, and Z. A. Aghbari [9] Database outsourcing is a not unusualplace cloud computing paradigm that permits facts proprietors to take benefit of its on call for garage and computational resources. The main challenge is to maintaintheconfidentialityofthedatatountrustedparties.B.Cloudserviceprovider.Providesreal timequeryresultsrelated to authenticated users. Existing approaches have the problem of compromising data confidentiality or increasing the cost of communicationbetweentheserverandtheuser.Tosolvethisproblem,theyhavedualspatialdataconversionandencryption where the encrypted query is fully executed by the service provider of the encrypted database and the encrypted result is returnedtotheuser.Weproposeacryptographicscheme.
Y. Miao, J. Ma, X. Liu, J. Weng, H. Li, and H. Li [10] Fog computing is an extension ofcloud computing that offloads sensitive encrypted data to multiple fog nodes at the edge of the Internet of Things (IoT) to reduce latency and network congestion. However, existing ciphertext recovery schemes rarely focus on fog computing environments, and most of them still impose heavy computational and memory overhead on resource constrained end users. This paper first introduces the Lightweight FineGrained Ciphertexts Search (LFGS) system to fog computing by extending CiphertextPolicy AttributeBased Encryption(CPABE)andSearchableEncryption(SE)technologies.Thismakesitpossibletoachievefine tunedaccesscontrol andkeywordsearchatthesametime.LFGScanoffloadsomeofthecomputationalandstorageoverheadtoend user selected fog nodes. In addition, the basic LFGS system has been improved to support conjunction keyword searches and attribute updatestopreventirrelevantsearchresultsandunauthorizedaccess.Formal security analysis shows that the LFGSsystem can withstand ChosenKeyword Attack(CKA)andChosenPlaintextAttack(CPA),andsimulationsusingreal worlddatasets maketheLFGSsystemreallyefficientandfeasible.Itshowsthat.
Multi Keyword Ontology A set of rigorous privacy requirements to define and solve the difficult problem of protectingprivacywithkeywordmappingandencryptedclouddata(MROS)searches,andtoachievesuchasecureclouddata sharing system. To develop. Choose anefficient concept of coordinate matching from multiple multi keyword semantics. We present the Secured Multikeyword Search (SMS) problem over encrypted cloud data (ECD) and build a set of privacy standardsforsuchasafeclouddatautilizationsystem.
We firstpropose a basicSecured multikeyword ranking ontologykeyword mapping andsearchtechnique basedon safeinnerproductcomputation,whichwesubsequentlydeveloptofulfillvariousprivacyneeds.Rankingresultsshowthefirst ksearchresults.Inaddition,weproposeanalertsystemthatgeneratesalertswhenunauthorizeduserstrytoaccessdatafrom thecloud.Notificationsaregeneratedintheformofemailsandmessages.
CloudSetup
CryptographyCloudStorage
VectorModel
CloudSetupThismodulesetsupthedataownerandcloudserver.Therefore,thedataownertransfersthedatatothe cloud server. When users offload private data to the cloud, cloud service providers can control and monitor the data, protectingcommunicationbetweenusersandthecloud. CRYPTOGRAPHY
Encrypted cloud storage In this module, data is uploaded to storage and search services. You cannot fully trust the cloudservertoprotectyourdatabecausethedatamaycontainsensitiveinformation.Forthisreason,outsourcedfilesmustbe
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
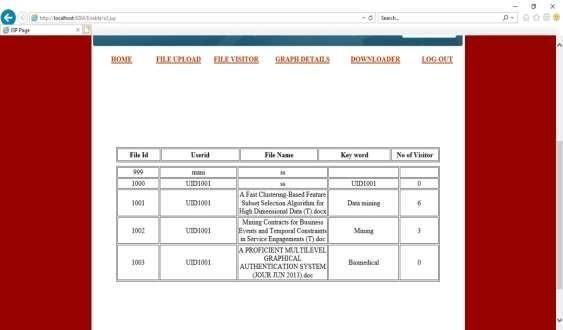

encrypted.locatedonpremise(i.e.,inthecustomersregionofcontrol).Specifically,thismeansthataccesstocustomerdatais underitscontrolandisonlygrantedtotrustedparties.
VectormodelThismodelusesasetofsearchablesymmetricencryptionschemesthatallowthesearchforciphertext. In the former case, the files are sorted by the number of keywords found, which affects the accuracy of the search. A vector spacemodel,orconceptualvectormodel, isanalgebraicmodelforrepresentingatextdocument(andgenerallyanyobject)as avectorofidentifiers(suchastheconceptofanindex).Itisusedforinformationfiltering,informationretrieval,indexing,and relevanceranking
HomeMappingistheprocessofusingtheInternettoview,analyze,orshareavisualrepresentationofgeospatial datainamapformat.ImproveservicebyidentifyingtherootcauseofITinfrastructureproblemsand changes. Servicemappingusestraffic basedactionstocreateservicemapsforamoreintegratedinfrastructure.
WebSearchisadedicatedcomputerserverthatsearchesforinformationontheWeb.Userquerysearchresults are oftenreturnedasalist.Thesehitsconsistofwebpages,images,andotherfiletypes.
Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page514
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072
Searchableencryptionisamechanismthatenablessecureretrievalofencrypteddataonremoteservers.Thistaskis the first to discover and solve the problem of searching encrypted cloud data in one term, providing a set of privacy constraints. To better capture the similarities between search terms and outsourced documents, we have determined an efficientprincipleof "coordinatedcoordination".i.eAsmanymatchesaspossiblebetweendifferentmulti keywordsemantics. Addresses the difficulty of multi meaning words without losing confidentiality. First, it provides a basic strategy for secure multi keyword search based on secure dot product computing. This has been significantly enhanced to meet the privacy requirementsofthetwothreatmodels.CompareDES,RSA,andplannedTripleDES.Theproposedapproachshowsthatthere isasignificantdifferenceinthetimerequiredfortheencryptionanddecryptionprocess.Athoroughinvestigationandhands ontestingofthevariousmethodsofguaranteeingprivacyandefficiencywillbeprovided.
[1] C. Guo, R. Zhuang, Y. Jie, K. Choo, andX.Tang,“Securerangesearchoverencrypteduncertainiotoutsourceddata,”IEEE InternetofThingsJournal,vol.6,no.2,pp.1520 1529,2018.
[2] Y. Wang, Q. Wu, B. Qin, W. Shi, R. Deng, and J. Hu, “Identitybased data outsourcing with comprehensive auditing in clouds,” IEEETransactions on Information Forensics andSecurity,vol.12,no.4,pp.940 952,2017.
[3] X. Yao, R. Zhang, Y. Zhang, and Y. Lin, “Verifiable social data outsourcing,” in Proc. of IEEE Conference on Computer Communications,Atlanta,USA,May2017,pp.1 9.
[4] Y.Zhang,C.Xu,X.Liang,H.Li,Y.Mu,andX.Zhang,“Efficientpublicverificationofdataintegrityforcloudstoragesystems from indistinguishabilityobfuscation,”IEEETransactionsonInformationForensics andSecurity,vol.12,no.3,pp.676 688,2017.
[5] K. Yang, Q. Han, H. Li, K. Zheng, Z. Su, and X. Shen, “An efficient and fine grained big data access control scheme with privacypreservingpolicy,”IEEEInternetofThingsJournal,vol.4,no.2,pp.563 571,2017.
[6] H. Tian, Y. Chen, C. C. Chang, H. Jiang,Y.Huang,Y.Chen,andJ.Liu,“Dynamic hash tablebasedpublicauditingforsecure cloudstorage,”IEEETransactionsonServicesComputing,vol.10,no.5,pp.701 714,2017.
[7] W. Sun, S. Yu, W. Lou, Y. T. Hou, and H. Li, “Protecting your right: Verifiable attribute based keyword search with fine grained owner enforced search authorization in the cloud,” IEEE Transactions on Parallel and Distributed Systems, vol. 27,no.4,pp.1187 1198,2016.
[8] B.Ananthi, S.V.Priyadharshini, andM.Ramesh “Security Multikeyword Search over encrypted cloud data based on quality andusability,”IEEEInternetofThingsJournal,vol.6,no.2,pp.1520 1529,2018.