International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
1UG Student, RV College of Engineering, Bengaluru, Karnataka, India
2Professor, Dept of Information Science and Engineering, RV College of Engineering, Bengaluru, Karnataka, India ***
Abstract Smart contracts have been developed and employedinbothpermissionedandpermissionlessblockchains recently,mainlytoenforceagreementsamongpartieswithout the need for intermediaries. This achievement is the result of blockchain immutability which guarantees that no party can altertheconditionsofanalreadydeployedcontract.However, immutability also makes patching or updating contracts impossible even when incorrectness, unfairness, or security flawsarespottedinthem.Sofar,researchersinacademiaand industryhavedevelopedtwomainmethods,datasegregation and proxy storage, with six patterns to make deployed contracts upgradable. However, until now, there has been no comprehensive framework that can simultaneously offer upgradability,securityresilience,andscalabilityfeatures.For example,noneoftheexistingsolutionshaveimplementedany security mechanism that can resist attacks such as the DAO one. Through extensive analysis and implementation of all these patterns, and taking state of the art attacks on the Ethereum network into consideration, we review framework, “Comprehensive Data Proxy pattern” which uses data segregation on the top of proxy pattern, that can completely defend against any types of Reentrancy attacks. Additionally, this solution mitigates the scalability issue of the proxy pattern. Our experiments show that the framework can address these two issues with negligible impact on performance.
Key Words: Blockchain, Smart Contract, Ethereum, Distributed platform, DAO
Duetotheimmutabilityofblockchains,smartcontracts[26] arereplacingregularcontractssincetheycandoawaywith middlemen. This immutable quality guarantees that deployed contracts are not changed by any participating parties, fostering confidence between them. With the exceptionofBitcoin[12],manyblockchainshavebeenbuilt to accommodate smart contracts. Smart contracts are written in languages like Go Lang [1] and Solidity [19] on someplatforms,suchasEthereum[7].Oncedeployed,they can be executed by the parties concerned at specific addresseswithintheEthereumnetwork[17].
Anyone can access any address or smart contract on a permissionless blockchain like Ethereum and start its executionifthenecessarycriteriaaresatisfied.Inactuality, anyone can create and use contract. Making sure that the deployedsmartcontractsareaccurate,equitable,andsecure
is crucial [11]. Writing fair and error free contracts is far from simple, as shown by the numerous attacks being attemptedagainsttheEthereumplatform[4].Thiskindof securityvulnerabilityrequiresthetargetedsmartcontractto be patched immediately, or attackers exploit it again. However, patching or upgrading a contract is in contrast withtheimmutabilityfeatureofblockchain.Weneedtofind a way to patch or upgrade smart contracts if we aim to develop this new technology and prepare it for mass adoption.
So far, there have been two categories of upgradable patternsdevelopedbyresearcherstoachieveupgradability ontheEthereumplatform.Thetechniqueusedinallthese solutionsistomapthestatesofstoragedata inthe newly deployedcontractstotheoriginalversions.Bydoingso,the statesofdatacanbeupdatedandmanipulatedbythenew contracts without making any changes to the previous versions,somethingwhichwassupposedlyimpossibletodo directlybefore.Forinstance,in[25],theauthorsintroducea datasegregationpattern,whichsuggeststhatacontractis writtenastwoseparate(sub)contracts;adatacontractanda logic contract. In this case, the upgradability is achieved throughupgradingthelogiccontractwithouttouchingthe datainthedatacontract.Inanotherapproach,OpenZeppelin [9]developedanovelmethodthatusesaproxycontractto overtaketheownershipofstorageaddressesofallversions ofagivencontract.Anycalltothetargetcontractwouldbe redirectedtotheproxycontractwhichinturn,willsendall transactions to the same address it controls, and through this,achievestheupgradabilitygoal.Tosumup,mappingthe statesofnewversionofthedeployedcontracttoitsoriginal storageaddressisthekeytoanystate of the artsolution.
While these solutions can bring upgradability to smart contractsintheimmutableenvironmentofblockchain,what ismissinginthemisresiliencetoattacks,whichwasoneof thereasonsbehindtheneedforupdatingthecontractinthe firstplace.Indeed,noneoftheexistingpatternsimplement anycontroltopreventcriticalattacks,suchasReentrancy attacks[16],inEthereum.Forinstance,protectingtheEthers heldbylogiccontractsindatasegregationpatternsisvital, butnoneofsub patternsinthiscategorycanhandleit.Thus, it remains an open question how we can apply a security mechanism to improve updatable contracts resilience to attacks.
In this paper, we first introduce six main state of the art approachesandthencomprehensivelyanalysefourofthem
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
thataddresstheupgradabilityprobleminEthereum.Three oftheseusedatasegregationpattern:basicdatasegregation, satellite data segregation and register pattern [25]. The remaining three methods that employ the proxy pattern approachareInheritedStorageProxy[14],EternalStorage Proxy [13] and Unstructured Storage Proxy [15]. After introducing the six approaches, we deeply examine three kindsofpopularattacksonEthereumwhichwerestudiedin [16],[8]and[21],namely,cross functionReentrancy,typical Reentrancy and DAO attacks. After analysing and implementingtheseattacks,wethenreviewmechanismto enhance the current upgrading approaches in terms of resiliencetosuchattacks.Next,wethoroughlyanalysethe proxy patterns and specifically, we study the function signatures[19]ofsmartcontractsinordertodeterminehow toimprovethescalabilityofthispattern.Wetheyimplement thedesignofmulti contractsproxywithasinglecontractso thatthisimplementationrequiresonlyoneproxyforbetter scalability.
Tothisend,weformulateandimplementthecomprehensive combined model,Comprehensive data proxypattern[3],to fullyachieveupgradabilityaswellassecurityresilienceand scalability.Underthismodel,thedesignsmartcontractsin twolayersasproposedbytypicaldatasegregationpatterns, butwiththedistinctivecharacteristics.First,theyembedone extra authentication and data verification component betweendatalayeranditslogiccontractlayer,toruleout thepossibilityofDAOattacks.Second,weimplementaproxy patternatthedatalayertofullyachieveupgradability.
The first contribution is the analysing of state of the art methods that have been developed to upgrade smart contracts,inwhichweshowsthatwhileproxypatternscan fully achieve upgradability, they raise concerns about memoryhandlingandscalability.Wealsofoundthatnoneof the existing patterns have any security control to defend againsttypicalattacks.Then,wemakeenhancementstoeach pattern based on our evaluation in the previous step. We show that with the enhancement, i.e. Ether Transfer Verification,alltheexistingdatasegregationpatternswould completelythwartwell knownRe entrancyandDAOattacks. The new model of upgradable smart contract, i.e. Comprehensive dataproxy pattern, which can simultaneously provide upgradability and resilience to typicalDAOandRe entrancyattacks.Therestofthepaperis organisedasfollows:InSectionII,weintroducethegeneral backgroundofsmartcontractsandtheproblemsthatjustify theneedforupgradabilityfeature.Discussionontheresults will be presented in Section III. We wrap up the paper in SectionIVwithourconclusionandfurtherwork.
Ifsmartcontractsareimmutable,howcanweupdatethem like conventional software? This is the main research
question.Itiscrucialtounderstandthatanalreadydeployed contractoropcodecannotbechangedinanyway.However, we can upgrade contracts by creating a storage mapping from the new contract to the old one. Several sorts of patternsarenowusedtodealwithcontractupgradeability. Thesixmostcommonupgradablecontractpatternswillbe examined in the remaining paragraphs of this section. Additionally,weseparatethemintotwogroups:proxyand datasegregation.
In this section, we discuss the first upgradable pattern of smartcontract,i.e.DataSegregation.Thecoreideabehind datasegregationistoseparatedatafromthecontractlogic. In this way, a given contract is written in two separate (sub)contracts, a data contract and a logic or business contract.Thelogic
Fig.1.UpgradabilitybyDataSegregation.
contract interacts and manipulates the data in the data contract through some interfaces provided by the data contract(seeFig.1).Bydoingso,itbringstheupgradability to the contract as the logic contract can be upgraded and redeployed,whilethedatacontractwhichholdsallthestates offorthecontractremainsthesameonthechain.However, one disadvantage of this simple pattern is that, the data contractinthiscasedoesnothaveanyupgradablecapacity likeitscounterpart.
There are currently three patterns in this category: basic data segregation, satellite pattern, and register contract pattern.Inthebasicdatasegregationapproach,anoriginal contractissimplyseparatedintotwochildcontracts;adata contract and a logic contract. For instance, an ERC20 [23] standard contract is realised by a data contract which containsthestatessuchasaccountsandbalanceofaccount, andalogiccontractwhichcoversoperationslikemintand transfermethods.Similarly,SatelliteContractalsocontainsa datacontractandsatellitecontractswhichworkssimilarlyto the logic contract mentioned before. What makes this patterndifferentfromthepreviousoneisthat eachofthe satellitecontractsisresponsibleforonefunctionalityonly. Registercontractpatternisadditionallyusedtoupdatethe logic contract address to the data contract. Although this patterncanrefertothelatestcopyofacontract,itcannot importtheexistingdataintothenewversionofthecontract. Therefore,itshouldbeusedwithothertypesofupgradable pattern, such as basic segregation or satellite contract pattern.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
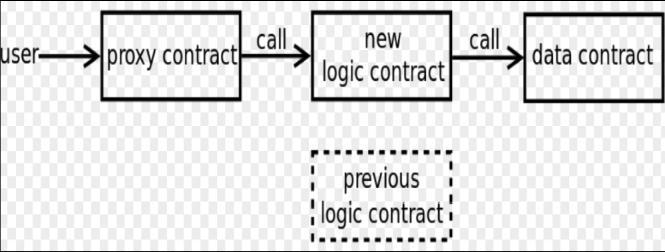
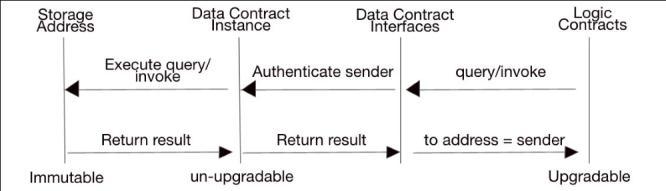
Another upgradable category is about proxy contracts, as Zeppolinos[10]hassuggestedfortheEthereumplatform. There are currently three types of upgradable proxy patterns:InheritedProxyStorage,EternalProxyStorageand Unstructured Proxy Storage. They all share the same foundation that the proxy contract takes control of all the states of contracts by handling every call to them though delegatecalls[6].Bydoingthis,thesender’soriginaladdress is preserved while its call is passed through the proxy contracttotheoriginalstorageaddress,asshowninFig.2.
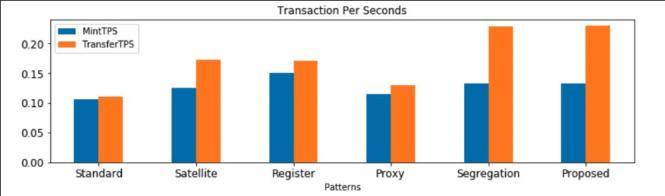
Fig.6.TheTPSperformanceindicator.
used for the deployment, mint and transfer method as wellastheTPSareconsistentwithouranalysesinsection III.Italsoprovedthatthese twoindicatorsofproposed pattern, are not considerable more than these existing methods.
Fig.2.UpgradabilitybyusingtheInheritedStorage.
Asitcanbeseen,allthecallstothecontractarehandledby theproxycontract.Itforwardsallthesecallstotheexecution storageareaofthecontractbyusingdelegatecall.Through this,theproxyisincontrol ofthestorage,andallstatesof the contract, since the delegatecall does not change the senderorigin.Itisalsoworthnoticingthatthereisnoneed forseparationofdataandlogiccontractsinthissolution.The target contract will update itself with its storage being controlledbytheproxycontract,thus,itcanaccessallthe statesofitsoriginalcontract.
In this section, we describe the key results of the experimentregardingtotheperformanceofupgradable patterns,resiliencetoDAOandre entranceattacksand upgradabilitycapacity.
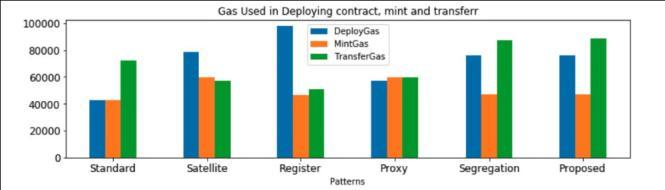
InordertoevaluatethegasusedandTPSforeachpattern, we perform the experiment with two standard transactions;themint(topup)andtransfertransactions. Fig. 5. Gas used for deployment, mint and transfer (gas usedfordeploymentwaspresentedby3 percent ofactual valueforpresentingpurpose
We also measured the gas consumed in the process of deployingsmartcontractsforeachpatternasshownin Fig.5.Asitcanbeseenfromthetheseabovetables,and TPSintable6,theamountofGas
Inordertoevaluatetheresilienceofpatternsagainsttwo common attacks on the Ethereum Public Chain, we launched the attacks on each of them. Out result is consistentwithouranalysis.Withoutaproperprotection mechanism, all patterns are vulnerable to DAO and Reentrancyattacks.Onthecontrary,theproposedpattern completelyblockstheseattackseventhoughtheabove mentionedvulnerabilitiesexistinthelogiccontract.Inthe otherwords,DATandanytypesofReentrancyattacksare eliminated by the use of data segregation technique introduced.
Aswestatedbefore,noneofthedatasegregationpatterns can provide full upgradability, since only the logic contract of this category is upgradable while its counterpart(thedatacontract)isnot.Ontheotherhand, allthethreeproxypatternsaswellasthepatternhavethe capacityforcompleteupgradability.Inthecaseofproxy patterns, the target contact can be upgraded freely regardlessoftheproxycontract.Thepatternalsoachieves thiswithbothlogiccontractanddatacontract,plusmulti proxycontractcapacity.
In this paper, we analysed the need for upgradability in smartcontracts,state of the artupgradablepatterns,then we thoroughly analysed those patterns to show the main differences,alsothelimitations.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

[1] Golang documentation. [Online]. Available: https://golang.org/doc/
[2] N.Atzei,M.Bartoletti,andT.Cimoli,“Asurveyofattacks onethereumsmartcontractssok,”in Proceedingsofthe 6th International Conference on Principles of Security andTrust Volume10204.NewYork,NY,USA:Springer Verlag New York, Inc., 2017, pp. 164 186. [Online]. Available:https://doi.org/10.1007/978 3662544556 8
[3] C.Bui.(2019,May)Upgradablesmartcontractpatterns. [Online]. Available: https://github.com/SWlabs/dao attacks
[4] Consensys, “Known attacks,” May 2016. [Online]. Available:https://consensys.github.io/smart contract best practices/knownattacks/
[5] P. Daian. (2016, Jun) Analysis of the dao exploit. [Online]. Available: http://hackingdistributed.com/2016/06/18/analysis of the dao exploit/
[6] Ethereum, “Ethereum virtual machine opcodes,” Sep 2018. [Online]. Available: https://ethervm.io/#CALLDATALOAD
[7] “What is ethereum,” July 2019. [Online]. Available: http://www.ethdocs.org/en/latest/introduction/what is ethereum.html
[8] S. Kalra, S. Goel, M. Dhawan, and S. Sharma, “Zeus: Analyzingsafetyofsmartcontracts,”012018.
[9] Z. Labs, “Upgradeability using eternal storage,” April 2018.[Online]. Available: https://github.com/zeppelinos/labs/blob/master/upgr adeabilityusingeternalstorage/contracts/Proxy.sol
[10] “Upgradeability using eternal storage,” April 2018.[Online]. Available: https://github.com/zeppelinos/labs/tree/master/upgr adeabilityusingeternalstorage
[11]L. Luu, D. H. Chu, H. Olickel, P. Saxena, and A. Hobor, “Makingsmartcontractssmarter,”in Proceedingsofthe 2016 ACM SIGSAC Conference on Computer and Communications Security, ser. CCS ’16. New York, NY, USA: ACM, 2016, pp. 254 269. [Online]. Available: http://doi.acm.org/10.1145/2976749.2978309
[12]S. Nakamoto, “Bitcoin: A peer to peer electronic cash system,” Dec 2008, accessed: 2015 07 01. [Online]. Available:https://bitcoin.org/bitcoin.pdf
[13]OpenZeppelin. (2018, April) Upgradeability using eternal storage. [Online]. Available: https://github.com/OpenZeppelin/ openzeppelin labs/tree/ff479995ed90c4dbb5e32294fa95b16a22bb9 9c8/upgradeabilityusingeternalstorage
[14]Upgradeability using inherited storage. [Online]. Available: https://github.com/OpenZeppelin/openzeppelin labs/tree/ ff479995ed90c4dbb5e32294fa95b16a22bb99c8/upgra deability usinginheritedstorage
[15]Upgradeability using unstructured storage. [Online]. Available: https://github.com/OpenZeppelin/openzeppelin labs/tree/ff479995ed90c4dbb5e32294fa95b16a22bb9 9c8/upgradeabilityusingunstructuredstorage
[16]M. Rodler, W. Li, G. Karame, and L. Davi, “Sereum: Protectingexistingsmartcontractsagainstre entrancy attacks,”in Proceedings of the
Network and Distributed System Security Symposium (NDSS’19),2019.
[17]F. Schar, “Decentralized finance: On blockchain and smartcontract ¨basedfinancialmarkets,”032020.
[18]D. Siegel. (2016, June) Understanding the dao attack. [Online]. Available: https://www.coindesk.com/understanding dao hack journalists
[19]Solidity. (2019, Mar) Solidity assembly. [Online]. Available: https://solidity.readthedocs.io/en/v0.5.5/assembly.ht ml
[20]Solidity assembly. [Online]. Available: https://solidity.readthedocs.io/en/v0.5.3/assembly.ht ml
[21]P. Tsankov, A. Dan, D. Drachsler Cohen, A. Gervais, F. Bunzli,¨ and M. Vechev, “Securify: Practical security analysisofsmartcontracts,”in Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, ser. CCS ’18. New York, NY, USA:ACM,2018,pp.67 82.[Online].Available: http://doi.acm.org/10.1145/3243734.3243780
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page2605
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
[22]D. Wesley. (2017, Oct) Reentrancy attack on a smart contract. [Online]. Available: https://medium.com/JusDev1988/Reentrancy attack on a smart contract 677eae1300f2
[23]E. Wiki, “Erc20 token standard,” Dec 2018. [Online]. Available: https://theethereum.wiki/w/index.php/ERC20 Token Standard
[24]M. Wohrer and U. Zdun, “Smart contracts: security patterns in the ethereum ecosystem and solidity,” in 2018 International Workshop on Blockchain Oriented Software Engineering (IWBOSE),March2018,pp.2 8.
[25]M. Wohrer and U. Zdun, “Design patterns for smart contractsinthe¨ethereumecosystem,”2018.
[26]G.Wood,“Ethereum:Asecuredecentralisedgeneralised transaction ledger eip 150 revision (759dccd 2017 08 07),”2017,accessed:201801 03.[Online].Available: https://ethereum.github.io/yellowpaper/paper.pdf
[27]X. Xu, I. Weber, M. Staples, L. Zhu, J. Bosch,L. Bass,C. Pautasso, and P. Rimba, “A taxonomy of blockchain based systems for architecture design,” in 2017 IEEE International Conference on Software Architecture (ICSA),April2017,pp.243 252.
[28]X.Xu,C.Pautasso,L.Zhu,Q.Lu,andI.Weber,“Apattern collectionforblockchain basedapplications,”072018.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal
