International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
PONRADHA N1 , Mrs.R.SAHILA DEVI2, M.E.,
1PG student, Rohini College of Engineering & Technology, Kanyakumari
2Associate Professor, Rohini College of Engineering & Technology, Kanyakumari ***
Distributed denial of service (DDoS) attacks stay testing to mitigate in existing systems, recalling for home associations that include different Internet of Things (IoT) contraptions. DDoS traffic revelation model that includes a supporting systemfordeterminedmodeltreesfordifferentIoTdeviceclasses.Specifically,asubstitutetypeofthemodelwillbemade and applied for each device class, since the qualities of the association traffic from each contraption class could have honest variation(s). As a context oriented examination, we get a handle on how devices in a normal smart home environmentcanbecharacterizedintofourunmistakableclasses(andinournovelsituation,Class1 outstandinglyraised level of traffic consistency, Class 2 raised level of traffic consistency, Class 3 medium level of traffic consistency, and Class 4 low level of traffic consistency). Disclosures from our appraisals show that the precision of our proposed approachissomeplaceinthescopeof99.92%and99.99%forthesefourcontraptionclasses.Witheverythingtakeninto account,weshowthewaythatwecanusecontraptionclassestohelpusevenmoretrulyperceiveDDoStraffic.
Keywords:DDoS,IoT,mitigation,cloudcomputing.
Distributed denial of service (DDoS) assaults have been a bad dream for big business tasks, accessibility, and security. Afterthedevelopmentofcurrentprocessingstandardslikedistributedcomputing,theseassaultssawsignificantchanges inscale,techniques,points,andtargets.The benefitsgaveDistributeddenial ofservice(DDoS)assaultshavebeena bad dreamforbigbusinesstasks,accessibility,andsecurity.Aftertheriseofcurrentregisteringidealmodelslikedistributed computing, these assaults saw significant changes in scale, techniques, points, and targets. The benefits given by distributedcomputingareaccessibletothetwocasualtiesandtheaggressorscharacterizedbydistributedcomputingare accessible to the two casualties and the assailants [1]. A comprehensive solution to DDoS attacks requires covering the globaleffectsoverawideareaofautonomoussystem(AS)domainsontheInternet.Obviously,theglobal scaledefenseis toocostlyforareal lifeimplementation.EventheCyberDefenseTechnologyExperimentalResearch(DETER)testbedcan onlyemulatepartialInternetactivities.Toimplementanefficientdefensesystem,wemustleveragethenetworktopology andusedistributedtrafficmonitoringanddetection.Inreality,webuildaDDoSdefensesystemoveralimitednumberof network domains serviced by the same Internet service provider (ISP). These ISP network domains cover the edge networkswheretheprotectedsystemsarephysicallyconnected [2].AtthebeginningphaseofaDDoSassault,thetraffic changes are challenging to distinguish on the grounds that low traffic variances are not discernible. Observing Internet traffic at the singular stream level is cost restrictive to cover every single imaginable stream. In the mean time, the worldwide traffic in a wide region network is hugely enormous to perform ongoing discovery of organization oddities really. Latest works target countering DDoS assaults by battling the hidden vector, which is generally the utilization of botnets.Abotnetisanenormousorganizationofcompromisedmachines(bots)constrainedbyoneelement(theexpert). The expert can send off synchronized assaults, like DDoS, by sending requests to the bots by means of a Command and Control channel. Tragically, recognizing a botnet is likewise hard, and effective arrangements might expect to partake effectively to the botnet itself [3], which raises significant moral issues, or to initially identify botnet related malevolent exercises (assaults, diseases, and so on), which might defer the relief. Distributed computing is a model that permits organizations to send venture applications that, if appropriately planned, can scale their figuring assets on request. OrganizationscaneithersendtheirownapplicationsonInfrastructureasaService(IaaS)orPlatformasaService(PaaS) arrangements,ortheycanpurchasepreparedto involveapplicationsthatutilizationtheSoftwareasaService(SaaS)[4] model.whichraisessignificantmoralissues,ortoinitiallyidentifybotnet relatedmalevolentexercises(assaults,diseases, and so on), which might defer the relief. Distributed computing is a model that permits organizations to send venture applicationsthat,ifappropriatelyplanned,canscaletheirfiguringassetsonrequest.Organizationscaneithersendtheir ownapplicationsonInfrastructureasaService(IaaS)orPlatformasaService(PaaS)arrangements,ortheycanpurchase preparedto involveapplicationsthatutilizationtheSoftwareasaService(SaaS)[4]model.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
A key element that has prompted the early reception of public distributed computing is the utility estimating model, whichoverseestheexpenseofregisteringassetsconsumed.Likepublicutilities,forexample,gasandpower,cloudbuyers just compensation for the assets (stockpiling, transfer speed, and PC hours) they consume and for the time they utilize such assets. As per the terms of arrangement of the cloud specialist co op (CSP), cloud buyers are liable for all computational expenses caused in their rented process conditions, whether or not the assets were consumed sincerely. NormalusecasesfororganizationsthathavetakenonopendistributedcomputingincorporatesiteandWebapplication facilitating and web based business. Like any Internet confronting presence, these cloud based administrations are helplessagainstcirculatedrefusalof administration(DDoS)assaults.Suchgoesafterarenotable,andtherelateddangers have been well informed. Here, we investigate a more unobtrusive assault on Web based administrations facilitated in the cloud. Given the pay more only as costs arise estimating, cloud facilitated Web administrations are defenseless againstassaultsthatlooktotakeadvantageofthismodel.Anaggressor(for instance,abotnet)canplayoutafalseasset utilization (FRC) assault by consuming the metered transmission capacity of Web based administrations, expanding the cloud shopper's monetary burden[5]. Distributed computing is at present perhaps the most advertised data innovation region and has become one of the quickest developing sections in IT industry. Because of the adaptability, pay per use, flexibility, versatility, and different characteristics guaranteed by this worldview, it acquired the interest of huge associations and corporates for facilitating their administrations onto the cloud. Nonetheless, the capacity to answer securitydangersandoccasionsisrecordedasoneofthemainpressingconcernsofworryindistributedcomputing.
Distributed computing permits us to increase our servers and to serve an enormous number of solicitations for a help. Thepresentationofassetrichdistributedcomputingstages,whereadoptersarechargedinviewoftheutilizationofthe cloud'sassets,referredtoas"pay as you use"orutilityregistering,haschangedtheDistributedDenialofService(DDoS) chasedownissueinthecloudtoamonetaryone.Thisnewkindofassaultfocusesonthecloudadopter'sfinancialassets, and is alluded to as Economic Denial of Sustainability (EDoS) assault [6]. All in all, the assault is making the cloud unreasonablebyblurringthecloudchargingsystemtochargethecloudclient'sbillfortheassault'sexercises.Anotable strategy taken by EDoS assaults is to remotely control zombies to easily (with low rate to try not to set off security cautions)floodadesignatedcloudadministrationbyundesiredsolicitations.Becauseofsuchundesiredsolicitations,and inlightofthecloudversatilitythought,thehelpuse will be increasedtofulfill theon requestdemands.Furthermore,in view of the "pay per use" idea, a cloud adopter's bill will be charged for those undesired solicitations, prompting administration withdrawal or liquidation. What makes this more shocking is that it is incredibly hard to specifically channel the vindictive traffic without influencing the help overall. This likewise implies that any proposed moderating methodshouldbeexceptionallywise;anyotherway,theactualprocedurecouldbeusedbytheaggressorsasawellspring ofEDoSassault.
Inthispaper,spreadouta mathematical model inview ofqueueingspeculationto formalizeandtakeapartthelow rate DDoS attack circumstance in compartment based cloud climate. Considering the results of these examinations, we raise the characteristics and deficiencies of the compartment based cloud climate in defeating the low rate DDoS attack andproposeastrongDDoShelpframeworkconsentingtothecomponentsofcompartmentbasedcloudclimate.
We research the probability that involving the new features in compartment based cloud climate defeats the low rate DDoSattack.weraisethecharacteristicsanddeficienciestodirectlow rateDDoSattackintheholderbasedcloudclimate. We spread out a mathematical model considering queueing speculation to formalize the low rate DDoS attack circumstanceinholderbasedcloudclimateandanalyzetherestrictionofholderbasedcloudclimateindefeatingagainst low rate DDoS attack. Coordinated by this model, we propose an exceptional balance part to improve and organize the resourcedisseminationandtheamountofholdersforeasingthelow rateDDoSattack.
Aman bakshi et al.[7] lways creating cloud idea, issues are emerging from this "brilliant arrangement" in the endeavor field. Keeping interlopers from going after the cloud foundation is the main sensible thing the staff, the board and organizers can predict. Notwithstanding organization size or volume and extent of the cloud, this paper makes sense of howmoveITvirtualizationsystemcouldbeutilizedinansweringarefusalofadministrationassault.Inthewakeofgetting a terribly unusual spike in inbound rush hour gridlock, designated applications could be quickly moved to virtual machines facilitated in another serverfarm.Wanchun Dou etal.[8] proposed Solidlytalking,the technique issent bytwo periods, i.e., non assault period and assault period. All the more uncommonly, genuine parcels are gathered in the non assault period, for removing trait matches to create an ostensible profile. With the ostensible profile, the CBF strategy is advanced by working out the score of a specific parcel in the assault period, to decide if to dispose of it or not. Finally, broadrecreationsareledtoassesstheplausibilityoftheCBFtechnique.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
Wanchun Dou et al.[9] proposed Appropriated Denial of Service assault (DDoS), particularly HTTP, XML or REST based DDoS assaults might be extremely hazardous and may give exceptionally destructive impacts to accessibility of administrationsandallpurchasersmightgetimpactedsimultaneously.Anotherexplanationisthatonthegroundsthatthe distributed computing clients cause their solicitation in XML and afterward to send this solicitation utilizing HTTP conventionandfabricatetheirframeworkcommunicatewithRESTconvention(likeAmazonEC2orMicrosoftAzure)thus XMLassaultmorehelpless.SothecompromisecomingfromconveyedRESTassaults aremoreandsimpletocarryoutby the aggressor, however to security master undeniably challenging to determine. Mohd Nazri Ismail et al.[10] proposed anothermodel torecognizeflooding basedDoSassaultincloudclimatehasbeenrecommendedcomprising threestages. (1) The first stage is to display the typical traffic design for pattern profiling and (2) the subsequent stage is the interruptionidentificationcyclesand(3)atlastanticipationstage.
Wanchun Dou et al.[11] proposed Hadoop Map Reduce and Spark to accelerate information handling by isolating and handlinginformationstreamssimultaneously.Withacertifiableinformationalcollection,wedirectedtruetrialstoassess theviabilityofourcreatednetworkobservinganddangerrecognition framework asfarasorganizationchecking,danger discovery,andframeworkexecution.Ourexperimentalinformationshowsthattheproposedframeworkcanproductively screen network exercises, track down strange ways of behaving, and identify network dangers to safeguard basic foundationframeworks.MassimoFiccoetal.[12]proposedastrategytoorchestratestealthyattackpatterns,whichexhibit aslowly increasing intensitytrenddesignedtoinflictthemaximumfinancialcosttothecloud customer,whilerespecting thejobsizeandtheservicearrivalrateimposedbythedetectionmechanisms.
OswaldoOlivoetal.[13]proposed thatTorpedocansuccess fullydetectsecond orderDoSvulnerabilitiesinwidelyused webapplicationswritteninPHP.Once ourtooldiscoversa vulnerability,italsoperformssymbolicexecutionto generate candidate attack vectors. Gaurav Somani et al.[14] proposed a clever moderation system, DARAC, which pursues auto scaling choices by precisely separating between genuine solicitations and aggressor traffic. Aggressor traffic is distinguishedanddroppedinviewofhumanconductexaminationbaseddiscovery.Welikewisecontendthatthegreater partofthearrangementsinthewriting,don'tgivealotofconsiderationtothehelpqualitytogenuinesolicitationsduring anassault.
GauravSomanietal.[15]proposedtheisolatedenvironmentisanothervirtual machinethatissimilartotheoriginalone. Atthemeantime, execution oftheoperatingsystemandtaggedapplicationkeepscontinuouslybothinnewenvironment and original one. Siqin Zhao et al.[16] proposed a novel resource containment approach to enforce the victim’s resource limits. Our real time experimental evaluations show that the proposed approach results in reduction in the attack reporting time and victim service downtime by providing isolated and timely resources to ensure availability of other criticalservices.
youhuizili etal.[17]proposed PINE,aperformance isolationoptimizationsolutionincontainer environments,whichcan adaptively allocate the storage resource for each service according to their performance behaviors through dynamical resource management and I/O concurrency configuration. Ping Du et al.[18] proposed a cloud based attack defense systemcalledCLAD,whichisrunningoncloudinfrastructuresasanetworkservicetoprotectWebservers.GauravSomani et al.[19] proposed DDoS attacks on cloud services, where having the same attack features, two different services show completelydifferentconsequences,duetothedifference
in the resource utilization per request. Manoj Singh Gaur et al.[20] proposed a novel resource containment approach to enforce the victim’s resource limits. Operating System (OS) level “internal collateral damage”, in which the other critical servicesarealsoaffected.
To solve the above problems, we developed dynamic DDoS mitigation mechanism to defeat the low rate DDoS attack in container based cloud environment. The article is organized as follows: section 1 presents introduction and related works. Section 2 discusses the proposed method DDoS attack in container based cloud environment. Section 3 discussestheexperimentsandresults,andsection4describestheconclusionoftheresearchwork.
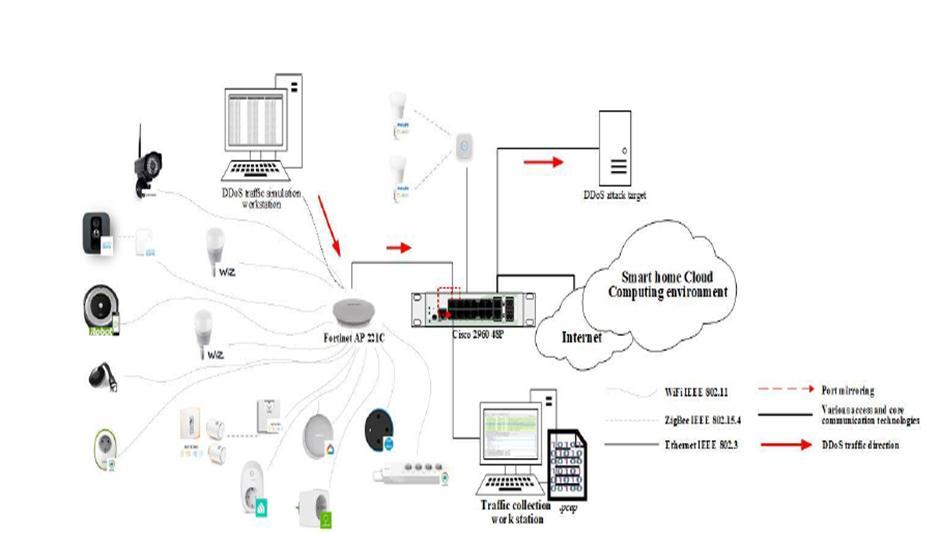
Inthiswork,environmentconsistsof41assortedSHIoTgadgets,andthesupportingcorrespondenceframework and programming equipment stage are likewise arrangement to empower traffic assortment that can be utilized to prepareDDoSidentificationmodels.Notwithstandingtheessentialinformationgatheredinthisexamination,welikewise utilized optional information, including a bigger number of different SHIoT gadgets (i.e., more noteworthy gadget heterogeneity).TheFortinet AP221Cremotepassageway,theCisco2960Catalyst48PoE(PoweroverEthernet)switch,
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
theHPPavilliondm1,andMicrosoftHP1010.0.17134form17134workstationshavebeensetuptocatchtrafficutilizing port reflecting, x64 processor engineering, AMD E 350, 1600MHz two centers, 4 GB RAM) with Wireshark programming device variant 2.6.3 introduced. The switch's actual correspondence ports (FA0/1 and FA0/3) to which the remote passageway and IoT center point for the Phillips Hue gadget are associated are designed for port reflecting. These ports aresetupassources,whichguaranteesthatalltraffictoandfromthemisreflected(planned)totheobjectivecontactport (FA0/2).Atrafficassortmentworkstationisassociatedwiththisport.WithanauthentictrafficprofileofaSHIoTgadget,it isvitaltohaveadatasetthatincorporateDDoStraffic.Thesetwosetsstructurethereasonforfosteringapowerfulmodel foridentifyingnetworktrafficinconsistencies,forexample,DDoStrafficcreatedbySHIoTgadgets.
SHIoT is a dynamic and inescapable climate, where new client IoT devices with different functionalities are persistently familiarwiththemarket.ToencourageaDDoStrafficdisclosuremodelconsideringasoflateportrayedSHIoTcontraption classes, it is essential to describe a certifiable traffic profile of each and every device class. In the improvement of any irregularityrecognizableproofmodelconsideringcontrolledAIprocedures,itisvitaltohavealotofdatathatwilladdress certifiabletrafficandalotofdatathatwilladdressnonsensicaltraffic.
The SHIoT contraption classes described by the investigation enable the ID of the class relationship of the device considering the traffic stream made by the contraption. This moreover engages the development of a bona fide traffic profileconsideringthewaythateachtrafficstreamallotedtooneofthefourdescribedclassesbytherequestmodelends up being fundamental for a set that tends to a genuine traffic profile of a comparable class. To cultivate a model for perceiving(nonsensical)DDoSnetwork traffic,theLogistic Model Trees(LMT)procedure wasused.Forthe executionof themethodologyanddatatakingcareof,weusedtheWEKAprogrammingdevice,aswellasinstructiveassortmentsthat address profiles of common traffic coming about in light of the SHIoT contraption gathering model and educational assortments of misguided DDoS traffic. Also similarly as with any AI model new development, the goal is to use those independent components whose change greatestly influences changing the dependent part. Moreover basic to diminish those components can incite model tendency. Thusly, moreover with the improvement of the SHIoT device portrayal model, independent components z1 to z7 address traffic stream identifiers and contain information on the source and objectiveIPaddresses,showsused,andtrafficstreamagetimewipedoutfromthefundamentaldatasets.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
MadebythecreatedmodelofabsurdDDoStrafficareaoccursintwophases.Theessentialstageisafundamentalforlater distinguishing proof of DDoS traffic in the ensuing stage and remembers the portrayal of SHIoT contraptions for perspectiveonmadetrafficstream.Themulti classgatheringmodelresultsshowthewaythattheSHIoTcontraptioncan bedescribedintooneoffourpredefinedclassesconcerningthetrafficstreamsitmakeswithanaccuracyof99.79%.The lowerleveloftrafficconsistencyisachievedbythecontraption'sstrategyformovement,similartoaraisedlevelofclient association, playback of sound/video content, and the like.This achieves a more incredible LMT model that can't be summarizedtotherootcenterpoint,yetitincludes11centersor6terminalcenterpoints.Anessentialbackslidemodelis portrayedoneachpieceofthedecisiontreepolishingoffwiththeterminalcenterpoint.Intheongoingcase,thissuggests that the LMT model contains an amount of five growing concentrations and six vital backslide models. A LMT model containing a decision tree and related vital backslide models with picked relevant independent features and related coefficients.Theworkingruleofthemademodel foracknowledgmentof nonsensical DDoSnetwork traffic.Madebythe mademodelofnonsensicalDDoStrafficareaoccursintwophases.Thechiefstageisafundamentalforlaterrevelationof DDoStrafficintheensuingstageandrememberstherequestforSHIoTcontraptionsforlightofdeliveredtrafficstream.
Due to the qualities of low rate DDoS assault, the harmless and the noxious solicitations have comparable ways of behavinginrushhourgridlock.Subsequently,weassume theorganizationtrafficissteadyandconsistentwhether under nonattack situations or assault situations. Furthermore, as a general rule, the solicitations couldn't be in every way malignant demands enduring an onslaught scenarios. suppose the appearance pace of solicitations to the microservice followsthePoissondispersionundernonattacksituations.
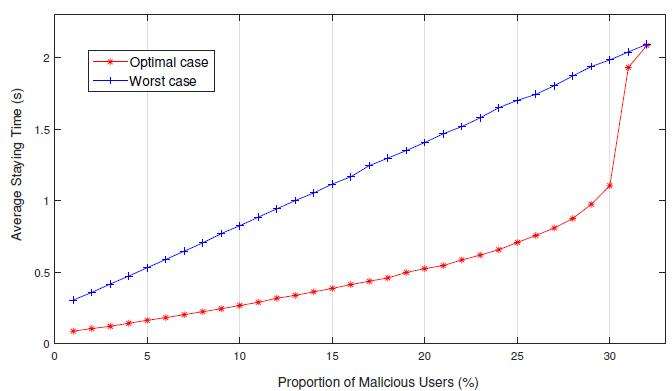
Tounknownrequests,theremainderofassetswillbeallocatedtotheminthewakeofmeetingtheprerequisiteof whitelistdemands.What'smore,weendeavortomakethenormalremainingtimeofobscuresolicitationsadequateunder the situation that the extent of malevolent solicitations as high as could really be expected. To accomplish this objective, weleadaninvestigationoftherelationshipbetweenthequantityofcompartmentsandnormalremaining timeofrequest under various assault qualities To examine the accuracy and viability of the relief component, we lead a set of reenactment examinations to gauge the normal remaining season of solicitations after DDoS alleviation instrument improvingundervariousassaultqualities.What'smore,asthecorrelationbunch,weruntherecreationexploresdifferent avenues regarding something similar designs to acquire the remaining season of solicitations in the most pessimistic scenariowithoutimprovement.Ineachtrial,wedirectmultipletimesreenactmentsandafterwardtakethenormal asthe end product.ThesubtletiesoftheexaminationresultsaredisplayedinFig.2
Fig.2:Averagewaitingtimeofunknownusersinscenarioswithadifferentnumberofcontainersanddifferent attackstrengths.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
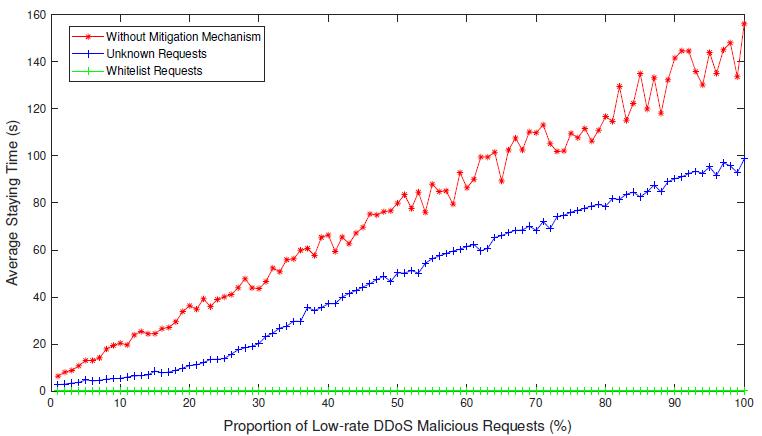
Now and again, the low rate DDoS attack isn't shipped off independently besides, mixes in with the flood based DDoS attack.Tosurveythepracticalityofourmitigationframeworkintheseconfoundedcircumstances,weimpersonateaflood basedDDoSattack andadditintothepastattack caseswhichina mannerofspeakingcontainthelow rateDDoSattack. Specifically, the ordinary attack speed of the flood based DDoS attack is 5,000 requesting each second, which is the on numerous occasions occupations than the regular case. Additionally, the evaluation results are shown in Fig. 3. The alleviation component, the QoS of whitelist solicitations can in any case be kept up with in the typical level under the combinationDDoSassaults.Likewise,withtheassaultstrengthofthelow rateDDoSassaultexpanding,theQoSofobscure solicitationshasalevelofprogresscontrastedwiththecaseswithoutourDDoSmoderationinstrument.However,theQoS oftheunknownrequestsisstillfarawayfromtheacceptablelevel,becausethemicroserviceonlyhaslimitedresourcesto facethemassiveDDoSrequests.Inordertomaximizetheeffectivenessofourmitigationmechanism,combiningitwiththe traffic filtering mechanism will have greater capacity to defeat the DDoS attacks in these complex scenarios. In this case, thetrafficfilteringmechanismisacomplementforourmitigation mechanismtofilterthemaliciousrequestsfromflood basedDDoSattack.
Fig.3:AveragewaitingtimeofrequestsincomplexDDoSscenarioswithorwithouttheDDoSmitigationmechanism.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
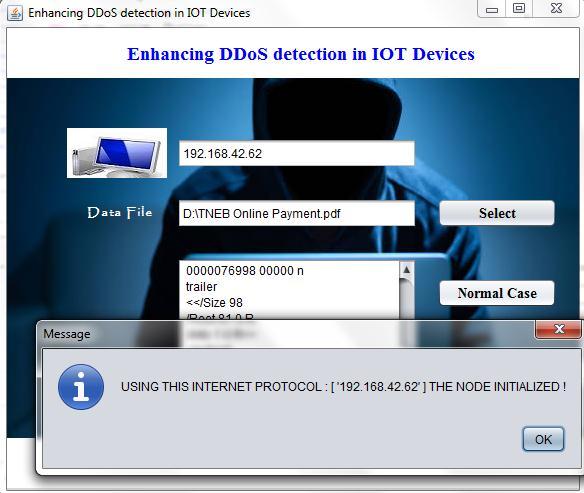
Fig4.Sendfileusingnormalcase
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072

The DDoS recognizable proof model presented in this paper diverges from the all around average organization traffic peculiarity acknowledgment draws near. Earlier methodologies are by and large established on making a real traffic profilethatissupposedtoapplytoeachandeveryterminaldevice.Suchaphilosophyiscognizantinconditionscontaining normal devices whose traffic makes characteristics that are smart of the action of the presented applications on the contraptionsandhowtheclientsusesuchcontraptions.Thusly,DDoSdisclosureapproachesconsideringindividualdevice characteristics require re learning or even redevelopment of the fundamental model for each new contraption that appears accessible. Such a procedure is unquestionably convoluted and deficiently nonexclusive in an obviously baffling anddynamicIoTclimate.
[1] G. Somani, M. S. Gaur, D. Sanghi, M. Conti, M. Rajarajan, and R. Buyya, “Combating DDoS attacks in the cloud: Requirements,trends,andfuturedirections,”IEEECloudComputing,vol.4,no.1,pp.22 32,2017.
[2] Y. Chen, K. Hwang, and W. S. Ku, “Collaborative detection of DDoS attacks over multiple network domains,” IEEE TransactionsonParallelandDistributedSystems,vol.18,no.12,pp.1649 1662,2007.
[3] J. Franc¸ois, I. Aib, and R. Boutaba, “Firecol: a collaborative protection network for the detection of flooding ddos attacks,”IEEE/ACMTransactionsonNetworking,vol.20,no.6,pp.1828 1841,2012.
[4]M.Villamizar,O.Garc´es,L.Ochoa,H.Castro,L.Salamanca, M.Verano,R.Casallas,S.Gil,C.Valencia,A.Zambranoetal., “Costcomparisonofrunningwebapplicationsinthecloudusingmonolithic,microservice,andawslambdaarchitectures,” ServiceOrientedComputingandApplications,vol.11,no.2,pp.233 247,2017.
[5] J. Idziorek, M. F. Tannian, and D. Jacobson, “The insecurity of cloud utility models,” IT Professional, vol. 15, no. 2, pp. 22 27,2013.
[6] M. H. Sqalli, F. Al Haidari, and K. Salah, “Edos shield a two steps mitigation technique against edos attacks in cloud computing,”inProceedingsofthe4thInternationalConferenceonUtilityandCloudComputing,2011,pp.49 56.
[7]A.BakshiandY.B.Dujodwala,“Securingcloudfromddosattacksusingintrusiondetectionsysteminvirtualmachine,” inProceedingsofthe2ndInternationalConferenceonCommunicationSoftwareandNetworks,2010,pp.260 264.
[8] W. Dou, Q. Chen, and J. Chen, “A confidence based filtering method for ddos attack defense in cloud environment,” FutureGenerationComputerSystems,vol.29,no.7,pp.1838 1850,2013.
[9]T.Karnwal,S.Thandapanii,andG.Aghila,“AFilterTreeApproach toProtectCloudComputingagainstXML DDoSand HTTPDDoSAttack,”inProceedingsofthe2012InternationalSymposiumonIntelligentInformatics,2012,pp.459 469.
[10] M. N. Ismail, A. Aborujilah, S. Musa, and A. Shahzad, “Detecting flooding based DoS attack in cloud computing environment using covariance matrix approach,” in Proceedings of the 7th international conference on ubiquitous informationmanagementandcommunication,2013,pp.36:1 36:6.
[11]Z.Chen,G.Xu,V.Mahalingam,L.Ge,J.H.Nguyen,W.Yu,andC.Lu,“Acloudcomputingbasednetworkmonitoringand threatdetectionsystemforcriticalinfrastructures,”BigDataResearch,vol.3,pp.10 23,2016.
[12]M.FiccoandM.Rak,“Stealthydenialofservicestrategyincloud computing,”IEEETransactionsonCloudComputing, vol.3,no.1,pp.80 94,2015.
[13] O. Olivo, I. Dillig, and C. Lin, “Detecting and exploiting second order denial of service vulnerabilities in web applications,” in Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, 2015, pp. 616 628.
[14] G. Somani, A. Johri, M. Taneja, U. Pyne, M. S. Gaur, and D. Sanghi, “DARAC: DDoS Mitigation Using DDoS Aware ResourceAllocationinCloud,”inProceedingsofthe11thInternationalConferenceonInformationSystemsSecurity,2015, pp.263 282.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072

[15]Y.Gilad,A.Herzberg,M.Sudkovitch,andM.Goberman,“CDNon Demand:AnaffordableDDoSDefenseviaUntrusted Clouds,”inProceedingsofthe23rdAnnualNetworkandDistributedSystemSecuritySymposium,2016.
[16] G. Somani, M. S. Gaur, D. Sanghi, M. Conti, and M. Rajarajan, “DDoS victim service containment to minimize the internalcollateraldamagesincloudcomputing,”Computers&ElectricalEngineering,vol.59,pp.165 179,2017.
[17]Y.Li,J.Zhang,C.Jiang,J.Wan,andZ.Ren,“PINE:optimizingperformanceisolationincontainerenvironments,”IEEE Access,vol.7,pp.30410 30422,2019.
[18] P. Du and A. Nakao, “DDoS defense as a network service,” in Proceedings of the 10th Network Operations and ManagementSymposium,2010,pp.894 897.
[19] G. Somani, M. S. Gaur, D. Sanghi, M. Conti, and R. Buyya, “Service resizing for quick DDoS mitigation in cloud computingenvironment,”AnnalesdesT´el´ecommunications,vol.72,no.5 6,pp.237 252,2017.
[20]G.Somani,M.S.Gaur,D.Sanghi,M.Conti,andM.Rajarajan,“DDoSvictimservicecontainmenttominimizetheinternal collateraldamagesincloudcomputing,”Computers&ElectricalEngineering,vol.59,pp.165 179,2017.
[21] Y. Xiang, K. Li, and W. Zhou, “Low Rate DDoS Attacks Detection and Traceback by Using New Information Metrics,” IEEETransactionsonInformationForensicsandSecurity,vol.6,no.2,pp.426 437,2011.
[22] J. Luo, X. Yang, J. Wang, J. Xu, J. Sun, and K. Long, “On a mathematical model for low rate shrew DDoS.” IEEE TransactionsonInformationForensicsandSecurity,vol.9,no.7,pp.1069 1083,2014.
[23]J.Burnim,S.Juvekar,andK.Sen,“WISE:Automatedtestgeneration forworst casecomplexity,”inProceedingsofthe 31stInternationalConferenceonSoftwareEngineering,2009,pp.463 473.
[24]B.Tak,C.Isci,S.S.Duri,N.Bila,S.Nadgowda,andJ.Doran,“Understandingsecurityimplicationsofusingcontainersin thecloud,”inProceedingsofthe2017USENIXAnnualTechnicalConference,2017,pp.313 319.
[25] C. Raiciu, S. Barr´e, C. Pluntke, A. Greenhalgh, D. Wischik, and M. Handley, “Improving datacenter performance and robustness with multipath TCP,” in Proceedings of the 2011 ACM SIGCOMM Conference on Applications, Technologies, Architectures,andProtocolsforComputerCommunications,2011,pp.266 277.