International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
1,2,3,4,5Department of computer Engineering, Agnel Institute of Technology and Design, Assagao, Goa 6,7Assistant Professor, Department of computer Engineering, Agnel Institute of Technology and Design, Assagao, Goa ***
Abstract The use of many cards’ transaction in various places like shopping, restaurants, lodges and online transaction in regarding booking hotels, movies, flights and train tickets etc., are on a rise each second. Hence the problem of people carrying payment card & cash along with themselves and keep the cards/cash secure to use it all the time; chances of being victim of theft. As in present work, biometric facial recognition transactions are used everywhere. Use of One Time Password (OTP) to secure the transaction further helps us in avoiding need of memorizing different passwords. Face recognition transaction systems are safe and secure with ease. It’s known for its reliability and more efficient compared to other payment technics. A general idea of an online transaction system using facial recognition is suggested. The technique chosen for facial identification are Local Binary Pattern Histogram (LBPH) andHAAR CASCADE.
Key Words: OTP, LBPH, HAAR CASCADE(Misra & Dev, October 2020) In recent years, the security has become a vital and rigorous service to secure possessionsandprovidedataprivacy.Henceexistneedfor more reliable security system that has to be developed in order to avoid loss due to identity theft. Paving the way too many researchers to invent new answers for improvising security systems, especially in human identification. The conventional method of transaction is unreliable since it can be copied / manipulated and even stolen. Apart from these, conventional security methods like keys and payment cards can be lost or misplaced. Thus, a more simple and effective transaction system needs to be developed to avoid greater loss. Biometric based method is implemented for transaction, as a higher degree for security. (Mutteneni, Kasireddy, & Achanta, ISSN: 2277 3878, Volume 8 Issue 6, March 2020) Human faceisunique,itcannotbemanipulatedbyanymeans.The techniques used with facial recognition are very efficient thanother.Thefaceisaprimaryfocusinourlifethatplays a vital role in connecting identity and even emotions, System that recognize and identify face can be applied to various applications that include online transactions, security systems and criminal identification. Face recognition and detection is difficult as these algorithms
are stiff and complicated. Main difference between recognitionanddetectionisthat,infacedetectionweneed to determine whether the face is present in the image, whereas in face recognition we need to input face from already existing database. In the present work we have used facial recognition technology for the online transaction,transactionsinretailshopsandmallsetc.
2.1 Face Net (2015 IEEE): A Unified Embedding for Face Recognition and Clustering.
(Schroff, Kalenichenko, & Philbin, 2015) In this paper, presented system is called Face Net. Face Net learns how to directly map facial images to a packed Euclidean area. The space between the generated vectors giving us similarity between the faces. The created space is also used for different tasks such as facial recognition, verification and clustering with help of techniques with Face Net embedding as feature vectors. We broaden this concepttopracticesecureonlinetransactions.
2.2 An Efficient Scheme for Face Detection based on contours and feature skin recognition
(Heshmat, Moheb & Abd Elhafiez, & Elaw, 2015/12/01) This work is founded on skin color, contour drawing and attribute extraction to obtain an effective and simple way to detect human faces in pictures. The attributes under consideration include mouth, eyes and nose. The results arewithgreataccuracy,speedandsimpleprocess.
(Jetsiktat, Panthuwadeethorn, & Phimoltares, November 2015) A credit card transaction system which integrates facial recognition and detection technology using Haar Casecade algorithms is developed. The training dataset includes the extracted attributes from the pictures and is saved in administrator database, which helps in authentication. We use CNN instead to increase efficiency andreducecomplexityofsystem.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
Technology and Engineering, recognition of currency notes is one of the serious problems faced by visually Challenged. So, a system with almost 99.07% accuracy level According to their project, bank notes with different wasdeveloped.
(Suciu & Emami, 2012) From “Facial Recognition using OpenCV”paperdeductionismadeonhowtotraindataset that contains user images stored in them. In training the firststepistomakesurethesizeofalltheimagesissame. As the images are only stored in grey scale for this algorithm to work, the LBPH operation is executed which creates boundaries ofvarious objects presentin image by comparing the light and intense dark contrast in the grey image. The light contrasts in the image are used by computercreatingvirtuallinesonpictureandusingwhich comparison parameters along with already saved basic linestructuresthecomputerisabletodetecttheobjectsin picture and if programmed can be used specially to mark outfacesinthepicture.
Today’s technology is moving towards biometrics. Researchers are doing research regularly on ‘bioinformatics and biometric’ to incorporate these latest technics with other system. The main reason for popularity of biometric is that, each individual has their own biological footprint that is unique and hence cannot be duplicated. Systems are created to make biometric enabled system robust. Loopholes in this system are recognizedandworkisdonetoremovesaidshortcoming. We have tried to build such a system in which the computerusingopticalvisioncanrecognizethefaceofthe person correctly in real time and can help in facilitating cashlesstransactioninthisproject.
Project has been developed to facilitate ease of transactions. OpenCV module in Python programming language are being used. We have created a database of face images of user and the details of user’s account and registered phone number, trained it using algorithm and Haarcascadeclassifierandrecognizeafacefromrealtime picture input using ada boost algorithm. For transaction process once the machine identifies the user, an OTP is sentonregisteredSIMcardforsecuretransaction.
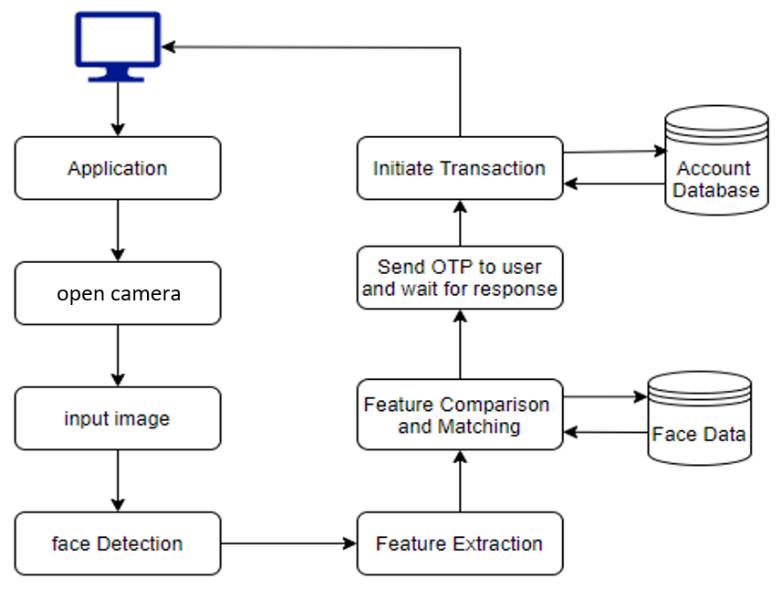
Theprocedureisasfollows:
1.Atfirstimageofthepersonwhowantstodopaymentis captured.Dynamicimageiscaptured.
2.After capturing the image it must be converted into greyscalesothateverydetailisbeingcaptured.Afunction CVTColor()isbeenused.
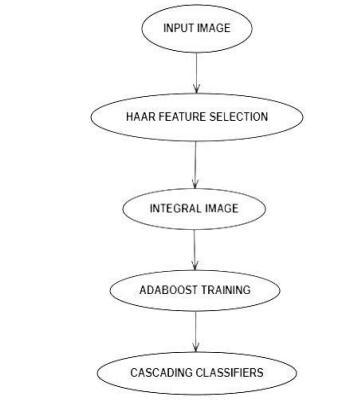
3.For the converted greyscale image, Haar Cascade Algorithm is been applied to detect the face and extract integral features. The techniques used for detection and extractionare:
“Haarfeatures”extraction
IntegralImages
AdaBoost:toimproveclassifieraccuracy
Cascadeofclassifiers
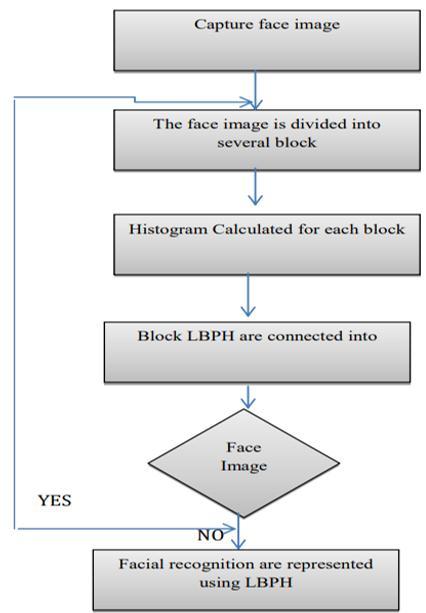
4.DivisionofimageintoblockstakesplacetoapplyLBPH algorithm. The histograms calculated is combined into singlehistogramforfurtherprocess.
5.Evaluating the histogram, the face image is processed andfaceisrecognized.
6.Iftheprocessedimagematches,OTPisgeneratedandis senttotheuser.
7.Uponverification,transactioniscarriedout.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
(L & Raga, Vol.6, Issue.5, pp.06 10, October (2018)) The Viola Jones object detection framework is initial step to provide competitive object detection rates in real time. It can be trained to detect a various of object classes, it is motivated by problem of face detection. This algorithm is implemented in OpenCV as cvHaarDetectObjects(). Other algorithms regularize a gallery of facial pictures and compress face data, keeping only the useful data in image recognition. Identification is done by facial attribute extraction or by examine relative positioning, sizes and shapes of Eyes, Cheekbones etc. These attributes are then used to find pictures with matching features. A probe is latercomparedwithfacialdata.
From cvtColor, we have used the function to convert RGB to Grayscale. Transformations such as elimination or addition of the alpha channel are to be carried out within the RGB space. RGB colour to grayscale conversion is done using RGB [A] to Grey: {Y←0.3 R+0.59G+0.11B}. Grey=cv2.cvtColor(img,cv2.COLOR_BGR2GRY)
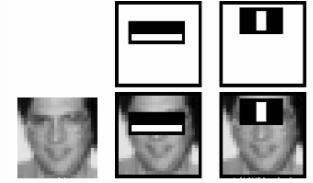
Haar attribute or Haar like attribute are those used to group generic objects. These are the main attribute for
facial detection using which system analyses whether a picture has a face or not. The picture is segmented by reducing down the area of interest. The attribute is a single value that is computed by the subtraction of pixels underthe whiteand black regions.Thisdata issavedin a file known as haar cascade which is normally an XML format file. Amorework is required to train the classifier systemandproducethecascadefile.Giveninthediagram below:
An Integral image lets you analyse aggregates of image sub regions. These aggregates are needed in various applications, like analysing HAAR wavelets. These are normally applied in face recognition and other alike algorithms. Suppose a picture is x pixels width and y pixels height. Then integral of this picture is x+1 pixels widthandy+1pixelsheight.Thefirstcolumnandrowof the integral picture is zeros. Any other pixel shall have the sum of all the pixels before them as the value assignedtothem.
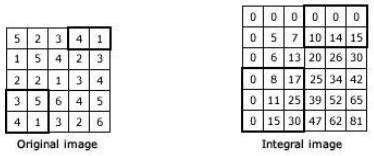
Now, you can find sum as: (Bottom right + top left top right bottom left). So, for the box with 3,5,4,1, analysis is done as: (30+0 17 0 = 13). For box with 4,1, will be (0+15 10 0 = 5). Hence, we aggregate in rectangular regionscanbeanalysed.
In Adaptive Boosting a.k.a. Ada Boost, over 180,000 attributeresultsina24X24panel.Notallattributeisused to identify a face. To select the unique attribute out of all available ones, a machine learning algorithm called Ada boost is adapted. The core construct used here is the
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
identification of the best attributes essential for recognizing a face. It is performed by building of a strong classifier which is a linearly combined group of weak classifiers.Asaresult,adrasticreductionofattributefrom 180,000to6000isseen.
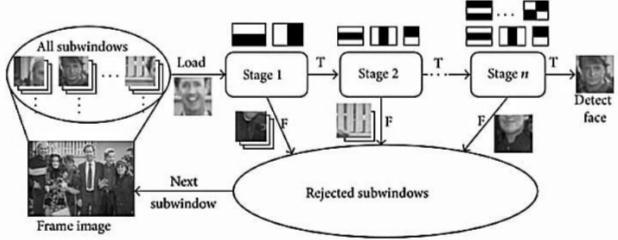
Cascade of classifiers helps to increase speed of haar cascade algorithm. The cascade classifier has of many stageswhereeachstageconsistsofastrongclassifier.This ishelpful to endthe need of applyingall the attributes on the window at once. Instead, it groups the attribute into different mini windows and at every stage, the classifier decideswhethertheminiwindowisafaceornot.Ifaface is not detected, the mini window and its attributes are discarded. However, if a face is identified, the mini windowmovespasttheclassifierandthencarriesontothe next stage where the second round of attributes are applied.Theprocesscanbeseeninthediagrambelow.
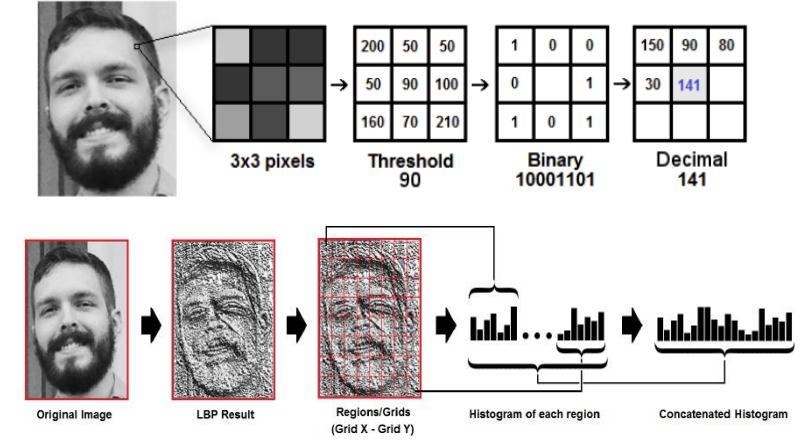
(Rani & Kamboj, Volume: 04 Issue: 08 | Aug 2017) Local BinaryPattern(LBP)isasimple,effectivetextureoperator labellingpixelsofa picturebythresholding neighborhood ofeachpixelandconsideringresultasnumberinbinary.It is grey scale image processing technique. Since the capturedimageiscolored,firstweconvertittogreyscale withformula x= 0.3R + 0.59G + 0.11B.
Using LBP combined by histograms we correspond the facialpictureswithadatavector.
(L&Raga,Vol.6,Issue.5,pp.06 10,October(2018))
1. Divide the picture into cells (e.g., 8x8 pixels for every cell).
2. For every pixel in a cell keeping centre pixel value an indicator, analyse the pixel to each of its eight neighbours (all direction including diagonal) Applying theLBPoperation:
3. When the centre pixel's value is more compared to neighbour’s value, assign "1”, or else “0". This gives an eight digit binary number (converted to decimal) Verificationorauthenticationofafacialpicture
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
4. Compute the histogram, for each cell, of the frequency of each "number" occurring (i.e., each combination of which pixels are smaller and which are greater than thecentre)
5. Compute Euclidean distance to find match in system if itexists.
Access controls exist to prevent unauthorized access. Companiesmakessurethatunauthorizedaccessisdenied andalsoauthorizedusersareunabletomakeunnecessary changes. The controls exist in a various form, from Identification Badges and passwords to access authenticationprotocolsandsecuritystandards.
While making transaction, customer ID is retrieved using facialrecognition
Adatabaseisessentialcomponentsformanyapplications, used for saving a series of data in a single set. In other words, it is a group/package of information that is put in order so that it can be easily accessed, manage, and update.
First, we register the user as customer or merchant and assignuniqueidentitytoeachwithhelpofdatabase.

Uponsuccessfulmatch,totalamountisenteredandOTPis sent to linked mobile number to that customer and based on balance in account, transaction may be completed or failed.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
[4]Kharat, D., Kajawe, P., Kopnar, S., Jinabade, N., & Wagh, J. (Vol. 8, Issue 11, November 2019). Face Recognition Using Local Binary Pattern. International Journal of Innovative Research in Science Engineering and Technology, 10659 10662.
[5]L, S. S., & Raga, S. (Vol.6, Issue.5, pp.06 10, October (2018)). Real Time Face Recognition of Human Faces by using LBPH and Viola Jones Algorithm. International Scientific Research Organization for Science, Engineering andTechnology,6 10.
[6]Misra,A.,&Dev,R.K.(October2020).Securedpayment system using face recognition technique. TH INTERNATIONAL CONFERENCE ON THE SCIENCE AND ENGINEERING OF MATERIALS:ICoSEM2019. ResearchGate.
[7]Mutteneni, Y., Kasireddy, S., & Achanta, A. (ISSN: 2277 3878, Volume 8 Issue 6, March 2020). A Robust Hybrid BiometricFaceRecognitionPaymentSystem. International Journal of Recent Technology and Engineering (IJRTE), 5586 5591.
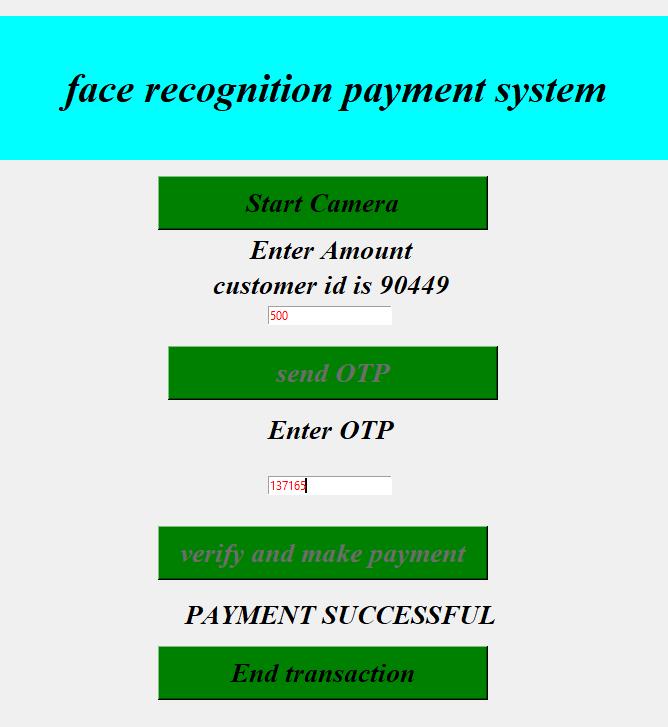
7.Conclusion
Fig 10: Transaction Process
We have implemented transaction processing system using facial recognition with help of Haar Cascade and LBPH algorithms. Use of OTP further secures the process of user authentication. The whole system is user friendly and works efficiently with very little error if any. More featurescanbeincludedinfuture
We would acknowledge the help provided to us by our college professors and staff to complete this project successfully
[1]Baratam,A.,Gudla,S.,B.,R.,&A.,V.(Volume8,Issue5 May 2020). ATTENDANCE SYSTEM BASED ON FACE RECOGNITION USING LBPH. INTERNATIONAL JOURNAL OF CREATIVE RESEARCH THOUGHTS IJCRT (IJCRT.ORG), 1267 1277.
[2] Heshmat, M., Moheb & Abd Elhafiez, W., & Elaw, S. (2015/12/01). An efficient scheme for face detection based oncontours and feature skin recognition. IEEE.
[3]Jetsiktat, ,., Panthuwadeethorn, S., & Phimoltares, S. (November2015). Enhancing user authentication of online credit card payment using face image comparison with MPEG7 edge histogram descriptor. Okinawa,Japan:IEEE.
[8]Rani, K., & Kamboj, S. (Volume: 04 Issue: 08 | Aug 2017). FACE RECOGNITION TECHNIQUE USING ICA AND LBPH. International Research Journal of Engineering and Technology (IRJET),104 108.
[9]Schroff, F., Kalenichenko, D., & Philbin, J. (2015). FaceNet: A unified embedding for face recognition and clustering. IEEE Conference on Computer Vision and PatternRecognition (pp.815 823).Boston,MA,USA:IEEE.
[10]Suciu,V.,&Emami,S.(2012).FacialRecognitionusing OpenCV. Journal of Mobile, Embedded and Distributed Systems.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal
