International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
Piyush Somani1, Poornima Kulkarni2
1Student, Department of Information Science and Engineering, RV College of Engineering, Bangalore, India 2 Assistant Professor, Department of Information Science Engineering, RV College of Engineering, Bangalore, India ***
Abstract Vulnerability Management is a pervasive problem in the development ofany codebase. In the basic termsconceivable,acybervulnerabilityisanyinaccuracy, shortcoming, or defect in an information system, internal controlsystems,orsystemprocessesofanorganisation.It mightbereferredtoasanimperfectionordeficiencyinthe architecture of the code base which produces application malfunctions. Accordingly, it is important to implement a robust vulnerability management measure to avoid widespreadassaultsoreventomitigatethedamageinflicted byacyberattack.Inthiswork,aVulnerabilitiesManagement System(VMS)solutionisproposed.
Key Words: Software vulnerabilities, vulnerability management, vulnerability database, and vulnerability management system
Presently, firmware which governs an electronic device's operation are incorporated through every electrical appliance. Those application programs, developed by variousengineerswithsucha smallerpercentageofcode, might well be enormously complicated and yet are later showninacomprehensivetechnologyprogramorproject. Almost majority of cases, application software errors are causedfromlingeringproblemsorvulnerabilitiesinsidethe code that can generate unforeseen consequences. The computerprogramisvulnerabletotheimpact ofthisflaw insidetheprogramminglanguage.Softwarevulnerabilities thereforearediscoveredinapplicationsoftwareorsoftware platforms that also have unresolved issues, flaws, or vulnerabilities. Eventually, such program vulnerability provides a good example of the a point of entry into a softwareplatform,whichcancausesignificantharmtothe system,thatbothcomputerhostingthesoftwareaswellas thedeviceassociatedtowardstheinfectedsystem
Notwithstanding in all security protocols, as even more individuals are browsing the network, vulnerabilities are indeedbeingidentifiedatanacceleratingrate.Sourcecode abnormalities,inconsistencies,andflawscandevelopinjust about any device that seems to have programming functionalities;consequently,detectionmechanismsshould emerge both for attempting to resolve and mitigating softwarevulnerabilities.thatboththecomputerhostingthe softwareaswellasthedeviceassociatedwiththeinfected system.
Notwithstanding in all security protocols, as even more individuals are browsing the network, vulnerabilities are indeedbeingidentifiedatanacceleratingrate.Sourcecode abnormalities,inconsistencies,andflawscandevelopinjust about any device that seems to have programming functionalities;consequently,detectionmechanismsshould emerge both for attempting to resolve and mitigating softwarevulnerabilities.
A hacker continually aims to break into the a system and acquirecredentialsthatwouldgivethemaccesstosensitive data or resources. A cyberattack potentially lead to significant financial destruction, damage to someone's character,includinglossofirreplaceableinformation.Ifthis programmingstructureissubjectedtopenetrationtesters, thensusceptibilityareasmustbedetected.
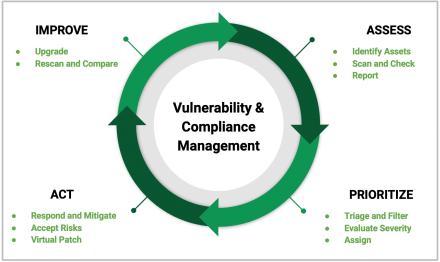
Figure 1 depicts a brief overview of vulnerability managementhastobeimplemented.
This section focuses on research which has already been conducted.Theexistingworkwillserveasafoundationfor something like the construction of a new vulnerable managementsystemfeaturingadvancedbenefits.
Theauthorin[1]providesanovelvulnerabilitymanagement solution, known as the Software Vulnerability Integrated ManagementSystem(SV IMS),hasindeedbeenintroduced by that of the authors in this study. That program can operatesecurityscreeningtoidentifyprogramweaknesses, aswellastheoutcomesofthesekindsoftestscouldbeseen on a different platform. Furthermore, it specifies the Popularly Known Scoring Scheme , a worldwide ratings systemthatevaluatesthegravityofbugs.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
Theauthorin[2]describesSpringBootwhichisajava based frameworkforbuildingwebandenterpriseapplicationsand how it provides the flexibility for service oriented architecture(SOA).Asaresult,thispapersuggeststhatthe SOA based REST API using Spring Boot Framework has definiteadvantagesoverotherspring basedframeworks.
The author in [3] highlights the necessity of accurate and comprehensiveinformationbeingprovidedinbugreports intended to assist inside the quicker response of errors. Nevertheless,followingmultiplecyclesofinteractionamong correspondents and programmers, relevant information frequently trickles to developers. Inefficient debugging methods are partially to blame for the prolonged informationsharing.Byrecommendingfourmainroutesfor improvements, it tackles the issues with bug tracking systems.Italsoexhibitsaproof of conceptinteractivebug tracking system that asks users for pertinent information and identifies files that need to be updated in order to remedythefault.
In [4] this research study, the author discusses Common Vulnerability Exposure (CVE) and Common Security Vulnerabilities Languages, two global, community based effortsinvolvingbusiness,thepublicsector,andresearch. Although OVAL seeks to provide enough methods for comprehensive vulnerability analysis as well as result in standardizedreportinginformationsecuritystandardsfor networks,CVEdeterminesthebestmethodforgenerating vulnerability notifications increasingly appropriate to differentorganisations.
Theauthorsin[5]describethetoolsforprojectmanagement and issues/bugs tracking that are becoming useful for governing the development process of Open Source software. Such tools simplify the communications process amongdevelopersandensurethescalabilityofaproject.The more information developers are able to exchange, the clearer are the goals, and the higher is the number of developerskeenonjoiningandactivelycollaboratingona project.
The author [6] established a method that made use of a learningalgorithmanddepthofknowledge.Throughusing this, the cyber risk management identifies, assesses, and negates the problem automatically. Challenges, security risks, reputational harm, and Economic loss all are minimizedbytheproposedapproach.
Theauthorin[7]providesinformationinordertoidentify the vulnerabilities for injection attacks, the author of this research has created an automated vulnerability scanner. The webpage is continuously analysed by this system for Cross siterequestandSqlinjectionattacks.TheNationwide Vulnerable Database, or Dynamic model, is also another componentoftheproposedsystem.
Theauthorin[8]providesdatabybuildingavulnerability database,theauthorofthisresearchstudyhasdevelopeda newtechniqueforcreatingandmanagingvulnerabilities.A newNationalVulnerabilityDataset(NDV)platformmaybe used by different companies in this proposed study.A recentlyfoundbugcouldalsoberegisteredinsidetheNeeds torequestdatabasewhilestillbeingreferredto.
In[9]theSCADAsystem'svulnerabilityisevaluatedtousea paradigm that this researcher has developed in risk assessments.Threelevelsareengagedinthis:Technology, Circumstances, and gateways. The systems with such a gatewayandcredentialpatternsservesasafoundationfor this architecture. Overall impact of the operation is also analysed using the proposed framework, and countermeasuresforstrengtheningcomputersecurityare developed.
The author in [10] implies implementing a risk database managementsystem. Theuseof security devicescould be extended upon and using this online system. The architectureoftheweaknessesinformationandindeedthe technique for generating the problems information are presentedinthisresearch.
The objective of the vulnerabilities control system is to identify and evaluate any application software problems. Themorphologicalinspectionandstaticanalysisareusedto conductthisassessment.Everyweaknessdiscoveredwillbe reviewed,maintainedintheVMSdatabase,andtestedifany software application is tested utilising the planned VMS technology.Ifindeedtheidentifiedexposureisaproduct,it canberegisteredintheVMSrepositoryafteralreadybeing evaluated either by various agencies. Comparable to the Appeared As early Points System, the Risk Monitoring Systemwouldnotonlydiscovertheweaknessbutitwillalso assessorrankitsintensity.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
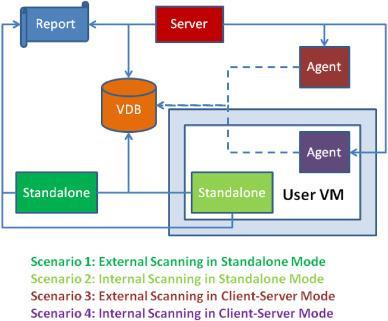
Abugscanner,aprocesscontrolplatform,andadatastorage comprisethreemainpartsofthevulnerabilitymanagement system.Abugscannerwillhaveanuniqueinterfaceitisonly for and has a variety of functional characteristics. Any memberofaproduct'ssecurityteamcanusethisinterfaceto advisethescannerhereabouthowtocontinuewiththenext step.Thecomputationalsystemwillanalysethecomputer user'scodeandbinaries.Automaticallyselectedprocedures wouldbeusedtoconductthisevaluation.Anyweaknesses identified during the technology manufacturer's testing phasewouldberecordedinthedatabase.Figure2depicts theuseofthescanner.Allpreviouslyunknownweaknesses wouldberecordedintherepository.
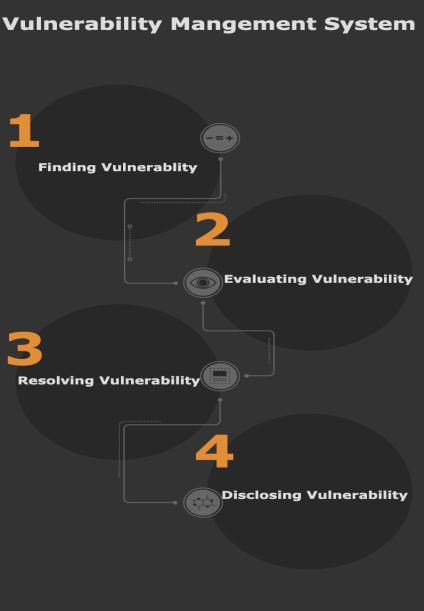
Data processing is categorized into 4 main phases, comprisingfindingvulnerabilities,evaluatingvulnerabilities, resolving vulnerabilities, and disclosing vulnerabilities, throughoutordertoincreasetheeffectivenessofscanning. Figure3depictsthefourphasesofthedataprocessing.
will be evaluated in this phase, as well as the high transformationwouldberatedorassessed.Theorganization needs to determine how and where to highlight the identifiedissuesthatusetheseexposureratings.
It's essential to address risks after grading issues and prioritising many who were identified. The computer programmer of a tested application would be available seeingtheweaknessesidentifiedduringthisprocedure.
Afterthat,theprogrammerhasthreealternativesregarding addressingtheissue:rectification,abatement,andadoption.
Thespeedandagilityofdetectingandpreventingcomputer productswillincreasewithusingriskmanagementsystems.
Throughoutthisoperation,astatementknownasasoftware agency's scan test will indeed be created. A visual representationusingseveralvariables,includingsuchrisk scoring,etc.,wouldbeaccessiblewiththeVMSsystem.Every user also may raise a ticket at this point to accelerate the sharingofthecomprehensivestudyordata
Thecompletedetailsinthefirstvulnerabilityreport,oras soonaspossible,aidprogrammersinresolvingtheissuefast. Thisworkaimsatenhancingvulnerabilityscanningsystems withtheintentofcreatingvulnerabilityreportsincreasingly comprehensive. Researchers are particularly consisting of fourwaystoenhancevulnerabilityscanningsystems.
The detection of risk is the most pivotal point in a Vulnerability Management system. The flaws in the evaluatedsoftwarepackagewouldbedisclosedasaresultof this process. Any open ports and functions that really are existentinthesoftwareprogrammewouldbescannedand recognizedduringthisprocess.Thatinformationwouldbe utilizedtojustprovidesummaries,statistics,aswellasother attributes.
Thecomputeralgorithmwillhavetoevaluatealltherisks once they've been identified and properly handled. Furthermore, overall intensity of the identified weakness
Vulnerability scanning processor architectures' characteristics are augmented with equipment based enhancements.Thosethatcanhelpalleviatethehardshipof knowledgestorageanddistribution.Vulnerabilityscanning processes, for instance, can be designed to automatically pinpointthepertinentautomaticallysendaswellasaddthis to an user query. Besides that, having provided stages to produceoffspringcanindeedbedonebymachinesthrough usingacquisitiontechniquesormeta;actualbehaviourcould beeasilyprovedbystandardisingscreengrab;andpossible solutionscanindeedbeautomaticallygenerated.Everyone of the case studies above are intended to assist inside the collection of information required by dev’s to identify vulnerabilities.
The material becoming supplied by the reporters is the immediatepriorityoftheseimprovements.Technologieslike Cedilla,thatprovidereal timeassessmentonthevalueof theevidenceprovidedandwhatcanbeaddedtomaximize
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
value, can be implemented into vulnerability systems. Reportersmaybeencouragedaboveandbeyondandcollect more data if indeed the system gives helpful recommendations.Technologiescouldbefurthermodified toperformoutassessmentmethods,includingsuchverifying that supplied modifications are acceptable as well as the reportedstacktracingisaccurateandconsistent
Technique centric enhancements to vulnerability managementsystemsconcentrateoncoordinatingadware efforts. Selecting whichever worker will fix a bug, for example, could be mechanized to accelerate the process. Additional instances involve giving users an advance approximationofthatwhentheirissuewouldberesolvedor create and encourage of something like the advancement achievedoneventlogs(sothatreportsareknowledgeableof thewaysofrespondingtotheirefforts).
Reporters and programmers are both included in this. Reporterscanunderstandwhattodotogetmaterialorwhat to provide. Engineers also can benefit from similar requirements on what characteristics to expect in reports andusethisinformationtoresolvebugs.
Some of the proposed benefits of the Vulnerability Managementsystemsareenvisionedasfollows:
Softwarethathassecurityweaknessesgivehackersaway intothecomputernetwork.Findingthesevulnerabilitiesis essential for protecting all assets and corporate data. Following that, these problems are rated for severity and givenapriority.TheevaluatedreportaidsinfixingITasset weaknesses and shielding them from cyber attacks that mightexposethenetworktosecurityrisks.Furthermore,IT security professionals are able to locate vulnerabilities remotelywithoutbeingpresentphysicallyinthecomputer environment.Theycanmanagehigh riskproblemswiththe leastamountofITresourcesthankstoit.Figure4depictsthe increaseinsecurityofdata.
ITsecurityprofessionalsmayremedythemostseriousIT securityconcernsimmediatelyanddealwiththelesserones afterwards with the review of the vulnerability list. The uncertaintyduringtheclean upprocessiseliminatedifthe effectofthepotentialdangerstothebusinessisidentified. Additionally, organisations may remotely automate and managevulnerabilities.Asaconsequence,itsavestimeand improvesoperationalefficiencybylesseningtheburdenof owningandmaintaininghardwareandsoftwareupgrades.A thorough vulnerability management solution significantly reducestheworkrequiredbythesecurityteam.Toreduce the likelihood of cyberattacks and improve the security posture,limitedITresourceswillbeneeded.
No matter what kind of digital marketing strategy your business is involved in, overcrowding will always be an obstacle to success. Competing against a large marketing budgetnolongerhastoplayafactorintheabilitytoachieve success. It is a very good marketing platform related to marketingandanyonecandoit!Paidadsquicklyshutdown smallbusinessesthatcompaniescanafford.
The visibility of the security teams would suffer if the vulnerability reports are manually compiled across hundreds of assets. It is challenging to display the vulnerability data from one scan to another using conventionalmethodologies.Consequently,itisimperative tohaveacompletevulnerabilitymanagementsystemwith an operational dashboard. It provides a security flaw's severity rating, charts, solutions recommendations, and creates personalised reports, all of which assist in establishingastrongcasefornewsecurityactivities.
An IT team may then secure their computer environment withbetter informedsecuritydecisions.Additionally,they maybegintheremedyprocessimmediatelyfollowingeach report.Ithelpsteamsoperatemoreefficiently,lessensteam fatigue,andtakestheguessworkoutofthings.
The research introduced the Vulnerability Management System (VMS), which will identify and report a software product'svulnerabilities.Wewillresearchthecurrentthreat detectionmodelandevaluateitseffectivenessandspeedof detection.Afterwards,we'lltrytocreateamodelthatmodels outcomes greater rapidly, correctly, and efficiently. The improvised model also will determine the severity of an impact a weakness will have on the system, helping in prioritisingvulnerabilities.
4.
Existing vulnerability management systems do not adequately extract all of the necessary information by
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
designers.Usersbelievevulnerabilityscanningtechnologies mustbeupgradedtoefficientlyobtaindatabecausewithout it,developerscaneasilyfixerrors.Thestudypostulatesfive mainareasforimprovement.Itmaybepreferabletomakea series of changes from some of these categories, problem trackingsystemsmayalsowanttospecialise,givingawide variety of choices. In comparison to existing scenarios, wheretheyallofferthesamefunctionality,thiswouldbea welcomeimprovement.Researchersalsodefinedanonline systemofcollectingdatafromreportsandutilisingthattool todeterminetheerror'ssourceasanexampleofthekindof enhancements wesupport. Researchersrana preliminary analysiswhereintheresearchersmimickedadynamicbug monitoringsysteminordertodemonstratetheusefulnessof thatkindofproposal.Inordertoobtainrelevantdataabout the defect immediately on and recommend prospective documents that need to be fixed, the system prompts the usersituationallyquestions.Thisonewilldefinitelyspeed thevulnerabilityprocess.Inside,wewilldevelopfromthe dynamicsystem'scurrentprototypestoacompletesystem which can manage a range of information gathering, as is commonlyseenintherealworld..
[1] Madalina Aldea, Daniel Georgica, Victor Croitoru, “Software Vulnerabilities Integrated Management System”, 2020 13th International Conference on Communications(COMM),IEEE,2020:pp.97 102,doi: 10.1109/COMM48946.2020.9141970
[2] K. Guntupally, R. Devarakonda and K. Kehoe, "Spring Boot based REST API to Improve Data Quality Report Generation for Big Scientific Data: ARM Data Centre Example," 2018 IEEE International Conference on Big Data(BigData),2018
[3] GeonLyangKim,JinTaeOh,DongISeo,JeongNyeoKim, “The Design of Vulnerability Management System”, International Research Journal of Engineering and Technology(IRJET)e ISSN:2395 0056Volume:08Issue: 11|Nov2021www.irjet.netp ISSN:2395 0072©2021, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 CertifiedJournal|Page28IJCSNSInternationalJournalof Computer Science and Network Security, VOL.13 No.4, April2013:pp.19 24

[4]ManojKumar,ArunSharma,“Anintegratedframework for software vulnerability detection, analysis and mitigation: an autonomic system”, Indian Academy of Sciences Sadhana Vol. 42, No. 9, September 2017, pp. 1481 1493,doi:10.1007/s12046 017 0696 7
[5] Chee Wooi Ten, Chen Ching Liu, Govindarasu Manimaran,“VulnerabilityAssessmentofCybersecurity for SCADA Systems”, IEEE Transactions on Power Systems,Vol.23,no.4,November2008,pp.1836 1846, doi:10.1109/TPWRS.2008.2002298.ff
[6]Y.Jin,Z.LinandH.Lin,"TheResearchofSearchEngine BasedonSemanticWeb,"2020InternationalSymposium on Intelligent Information Technology Application Workshops, 2020, pp. 360 363, doi: 10.1109/IITA.Workshops.2020.193.
[7] Armold; Hyla, Rowe, “Automatically Building an Information SecurityVulnerabilityDatabase”,2006IEEE InformationAssuranceWorkshop”,21 23June2006,pp. 376 377,doi:10.1109/IAW.2006.1652119
[8]AndreyFedorchenko, Igor Kotenko, Andrey Chechulin, “Design of Integrated Vulnerabilities Database for Computer Networks Security Analysis”, 2015 23rd Euromicro International Conference on Parallel, Distributed,andNetwork BasedProcessing,4 6March 2015,pp.559 566,doi:10.1109/PDP.2015.38
[9]M.RajaramandS.L.S.Vadivu,"WebcachinginSemantic Web based multiple search engines," 2010 IEEE InternationalConferenceonComputationalIntelligence and Computing Research, 2019, pp. 1 7, doi: 10.1109/ICCIC.2019.5705850.
[10] Ching Huang Lin, Chih Hao Chen, Chi Sung Laih, “A StudyandImplementationofVulnerabilityAssessment andMisconfigurationDetection”,2008IEEEAsia Pacific Services Computing Conference, 9 12 Dec. 2008, pp. 1252 1257,doi:10.1109/APSCC.2008.212
[11] Jan Min Chen, Chia Lun Wu, “An automated vulnerability scanner for injection attack based on injection point”, 2010 International Computer Symposium(ICS2010),16 18Dec.2010,pp.113 118, doi: 10.1109/COMPSYM.2010.5685537 Computational IntelligenceandComputingResearch,2020,pp.1 7,doi: 10.1109/ICCIC.2020.5705850.
[12] W. Xiaoyin, Z. Lu, X. Tao, J. Anvik and J. Sun, "An approachtodetectingduplicatebugreportsusingnatural language and execution information", Proceedings of International Conference on Software Engineering,2019
[13]R.DevarakondaandK.Kehoe,"SpringBootbasedREST APItoImproveDataQualityReportGenerationforBig Scientific Data: ARM Data Center Example," 2018 IEEE InternationalConferenceonBigData(BigData),2018
[14]QingL,BoyuZ,JinhuaW,QinQianL.Research“onkey technology of network security situation awareness of private cloud in enterprises”, IEEE 3rd International ConferenceonCloudComputing andBigData Analysis (ICCCBDA),2019
[15]KumarR,Kumar P.“Special issueon recenttrends in artificial intelligence techniques for fault tolerance, reliabilityandavailabilityin mission critical networks. RecentAdvComputSciCommun”.20205.
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page2501