International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN:2395 0072
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN:2395 0072
Sonali Ankolikar1, Samiksha Agrawal2, Rupal Mohanty3
1Student, School of Electronics and Communications Engineering, Dr. Vishwanath Karad MIT World Peace University, Pune 411038, Maharashtra, India
2Student, School of Electronics and Communications Engineering, Dr. Vishwanath Karad MIT World Peace University, Pune 411038, Maharashtra, India
3Student, School of Computer Science and Engineering, Dr. Vishwanath Karad MIT World Peace University, Pune 411038, Maharashtra, India ***
Abstract In today’s world, we are constantly surrounded by the exploitation of image manipulation techniques and the circulation of forged images on the internet. With this, the need for regulation methods and image forgery detection techniques has risen and it is evident that to understand different detection methods. In this paper, we review the various methods by which images can be manipulated and provide a comparative analysis of the different techniques to detect image forgery in a comprehensive manner with respect to all the literature available from the past decade. This comparison has been done to understand which methods prove fruitful under respective circumstances and to ensure that future implementations in this area of research are able to create an independent model which will successfully identify the forgeryinanimagewithouthumanintervention.
governments and institutions across the world. The main architecture of these image manipulation techniques is basedonGAN GenerativeAdversarialNetwork.Thereare majorly 2 digital forensics methods that are largely followed in the industry. The first method includes methods that attempt to understand the image by performing a ballistic analysis of it and creating an understandingofwhatkindofdevicewasused/notused to capture it. The second method consists of the method forexposingtracesoftamperingorsemanticmanipulation bycalculatingtheinconsistenciesinnaturalimageforgery techniques.
Types of manipulation can be generally classified into 3 categories:
Words: Forgery, detection, image manipulation, human intervention, image forensics
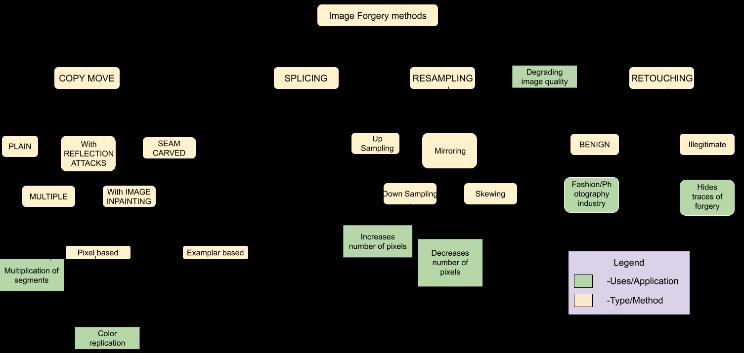
Image manipulation is the application of using various techniques for altering images in order to create a deception. The modern world around generating diverse art has created a huge deposit of fake, doctored images. Digital image forensics has been developed in order to provide tools for blind investigations. It originally stems from the existing domains of research falling under the umbrella of image forensics. Moreover, it exploits the properties of image processing and analysis tools to understand the processing of the data and recovery of informationfromtheimages.Thisunderscoresourefforts to understand which image detection techniques are effective,accurate,andprovidequickresults.Webelieveit is key to restoring the integrity of images that are not generatedbytakenfromtheirauthenticsources
As the act of faking images is not new to the modern ‘generation’ (cultural reference Generation Z), deep fakes and image manipulation techniques continue to display powerful abilities to generate visual and audio content with the help of artificial intelligence and machine learning despite the curbing measures implemented by
Throughoutthedomain,thereareanimmensenumber of methodologiesweobserved.Doctoringanimagecanhave alastingeffectontheimageandthesubject.Itcancreatea falseidentityandgeneratefalsebeautystandards.Studies suggest that one in every 5 images is doctored or manipulated. This raises the concern for the need for
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN:2395 0072
detection of manipulation because the data generated or images generated in today’s world are the heritage of the coming generations. Thefirstmethodology addressed isa CNN universal forgery detection method. It consists of a pre trained model and is an active method of detection used. It does not require human interaction to create the detector.
The term "convolutional neural network" indicates that the network employs a mathematical operation called convolution. Convolutional networks are a specialized type of neural network that uses convolution in place of generalmatrixmultiplicationinatleastoneoftheirlayers. CNNs are regularized versions of multilayer perceptrons. Multilayer perceptrons usually mean fully connected networks,thatis,eachneuroninonelayerisconnectedto all neurons in the next layer. The "full connectivity" of thesenetworksmakesthempronetooverfittingdata.
Typical ways of regularization or preventing overfitting, include: penalizing parameters during training (such as weight decay) or trimming connectivity (skipped connections, dropout, etc.) CNN's take a different approach towards regularization: they take advantage of the hierarchical pattern in data and assemble patterns of increasing complexity using smaller and simpler patterns embossed in their filters. Therefore, on a scale of connectivity and complexity, CNNs are on the lower extremity. CNNs use relatively little pre processing compared to other image classification algorithms. This means that the network learns to optimize the filters (or kernels) through automated learning, whereas in traditionalalgorithmsthesefiltersarehand engineered.
This independence from prior knowledge and human intervention in feature extraction is a significant advantage. Convolutional networks may include local and/orglobalpoolinglayersandtraditionalconvolutional ones. Pooling layers reduce the dimensions of data by combiningtheoutputsofneuronclustersatonelayerinto a single neuron in the next layer. Local pooling combines smallclusters,andtilingsizessuchas2x2arecommonly used.Global pooling actson all theneuronsof the feature map. Fully connected layers connect every neuron in one layer to every neuron in another layer. It is the same as a traditional multi layer perceptron neural network (MLP). The flattened matrix goes through a fully connected layer to classify the images. One more dependency observed wasthataCNNwithmorekernelsyieldsbetterresults,the useofmorekernelsrequiresmoretimefortraining.
Table 1: Comparisonofmethodswithrespectto
Inthis literature, theyhave workedon restrained CNNandused alearnable manipulation feature extractorto createa unified feature representatio nofvarious contentfrom theimage data.
Moreover,it explainshow acoarseto simulatea fineforensic processinthe realworld
1.Achieves manipulation techniques classification and manipulated region segmentation simultaneously
2Asingle stream learnable manipulation feature extractor.
3. Anattention regional proposal network(RPN A)
4
Title Description Technique/Me thod Accurac y Citat ion Constrained R CNN:A General Image Manipulation Detection model,Chao Yang, HuizhouLi, FangtingLin, BinJiang, HaoZhao
Automated image splicing detection usingdeep CNN learned features, Souradip Nath,Ruchira Naskar
Inthispaper, wepropose anautomated imagesplicing detection schemeusing deepCNN learned featuresand ANN based classifier.The proposed approach involvestwo mainsteps: (A)feature engineering and(B) classification
Ablindimage splicing detection technique usingadeep convolutional residual network architectureas abackbone, followedbya fullyconnected classifier network,that classifies between authenticand splicedimages.
96% 11
ADeep Learning based Methodfor Image Splicing Detection, KunjBihari Meenaand VipinTyagi 2021J.Phys.: Conf.Ser. 1714012038
Thispaper explainsthe implementati onofadeep learning basedmethod todetect imagesplicing intheimages. Theinput imageis preprocessed usinga technique called ‘Noiseprint’to getthenoise residualby suppressing theimage content.
The architectureof theproposed method consistsof3 mainsteps:
1.Obtaining noiseresidual mapusingthe Noiseprint
2.Extracting featuresusing ResNet 50
3.Feature classification usingsupport vectormachine
97.24% 12
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN:2395 0072
Second,the popular ResNet 50 networkis usedasa feature extractor K.M.Hosny, A.M.Mortda, M.M.Fouda, andN.A. Lashin,An EfficientCNN Modelto DetectCopy MoveImage Forgery
Copymove forgery detection usinga methodofa CNNbased modelfor imageforgery detection.
AdeepCMF methodalong withCNN.A feature extraction layerconsists of3 convolution layersfollowed byamax poolinglayer andafull connection layeratthe ends.
JPEGCompressionwithoutCNNtechniques: Learning RichFeatures forImage Manipulation Detection, Zhou,Peng& Han,Xintong &Morariu, Vlad&Davis, Larry
This literature explainsa fasterR CNN networkand trainedmodel todetectthe tampered regionsina doctored imageendto end.
RGBstream extracts featurefrom theRGBimage inputtofind tampering artifactslike strongcontrast difference, unnatural tampered boundaries, etc.stream2 Tendsto leveragethe noisefeatures extractedfrom a steganalysis richmodel filterlayerto discoverthe noise inconsistency
100% 44
DoubleJPEG compression forensics basedona convolutional neural network, Wang,Qing, andRong Zhang
Inthis literature,it aimsat performing preprocessing onDCT coefficients and histograms whichare further extractedas inputand sentthrough aCNNforthe featurestobe learned.Later itsjobisto distinguish thedouble JPEG compression forgeriesand
Usestwo convolution allayers, kernelsize to3 × 1, Using different feature dimenions 71%to 79.4%; Using different trainingset sizes 50% to79.1%; Uses different numbersof kernels 71.6%to 79.6%;
93% 6
Rao,Yuan, andJiangqun Ni."Self supervised domain adaptation forforgery localization ofJPEG compressed images."
achieve localisations.
70%to 80% 7
Passive Image Forgery Detection Based onthe Demosaicing Algorithm andJPEG Compression Vega, Esteban Alejandro Armas; Fernandez, Edgar Gonzalez; Orozco,Ana Lucila Sandoval; Villalba,Luis JavierGarcia
BoLiu,Chi ManPun, Xiao Chen Yuan,"Digital Image Forgery Detection UsingJPEG Featuresand LocalNoise Discrepancie s",
This literature proposesa self supervised domain adaptation networkand a compression approximatio nnetworkis proposedfor JPEG resistant imageforgery localization.
Thispaper proposesa digitalimage authenticatio nmethod basedonthe quadratic meanerrorof colorfilter array interpolation pattern estimated fromthe analyzed image.
Containsa backbone network.
41
Makesuseof Errorlevel analysisalong withthecolor filteranalysis tofigureout the interpolation patternofthe colorfilter.
73.30% 42
Carriesout imageforgery detectionby usinga blockwise specialized descriptor andthena forehand imagequality assessment procedureis implemented.
TransformTechniques:
Blockartificial gridsfollowed bymapping afterwhichthe feature generationfor 8x8blocksare generated. Noisefeature extractionis latercarried outusingSLIC segmentation.
Variabl efrom 80%to 100% w.r.t the JPEG compre ssion ratio.
43
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN:2395 0072
Researchon Copy Move Image Forgery Detection Using Featuresof Discrete Polar Complex Exponential Transform, YanfenGan& JunliuZhong
Image splicing detection basedon Markov featuresin QDCT domain, CeLia,Qiang Mab,Limei Xiaob,Ming Lib,Aihua Zhang
Itcoversan unused strategy basedonthe Polar exponential changewhich isproposedin orderto address variousissues oftheimage features.
Theproposed approachin thisliterature isthatthe modelis basedon Markov featuresof theimageand theirvaluesin theQDCT domainare introduced andobserved.
Templateis formulated suchthat1 pixelpassedat atime, lexicographic isusedfor invariance features,judge, detectand locateto forgeryregion oftheimage
Applying 8×8 blockQDCTon theoriginal imagepixel arrayandthe corresponding QDCT coefficient arrayis obtained. Secondly, roundingthe QDCT coefficientsto integerand taking theabsolute value. Thirdly, calculatethe horizontal, vertical,main diagonal,and minordiagonal intra block difference2 D arrays.
65% 8
Histogram Model ,Zhu,Nan, JungeShen, andXiaotong Niu.2019.
DCT(Discrete Cosine Transform) coefficients mixture histogram model.
2.By eliminatingthe quantization noise, 3.Resortto thesplitnoise filtering algorithm 4.100 uncompressed imageswith size1024× 1024
93% 9
DCT domain Deep Convolutiona lNeural Networksfor MultipleJPEG Compression Classification , VinayVerma, Nikita Agarwal,and NitinKhanna
This literature focusesonthe processof differentiatin gbetween imagesbased onthe numberof compressions thefeatures oftheimage have undergoneby extracting histogram based featuresand thenfeeds themintoa CNN.
CNN architectures suchas AlexNet, VGGNet, GoogLeNet, andResNet withafilterof size 3×1(kernel size),the networkhas four convolutional layersfollowed bythree fully connected layers
86% 10
Hegazi,Aya; Taha,Ahmed; Selim,Mazen M.(2019).An improved copy move forgery detection basedon density based clustering and guaranteed outlier removal.
Hayat, Khizar;Qazi, Tanzeela (2017). Forgery detectionin digital imagesvia discrete waveletand discrete cosine transforms.
Inthispaper, akeypoint basedcopy moveforgery detectionis proposed.The proposed methodwhich isbasedon density based clusteringand Guaranteed Outlier Removal algorithm.
Aforgery detection methodwhich worksonthe transform domains technique relyingon DCTandDWT for copy/move forgery
5.Treated doubleand singleJPEG compressed pixelsas positiveand negative samples, respectively
Inthispaper, themodel implements CLAHEfor preprocessing andimage feature extraction usingSIFTand thenmoveson tomatchsuing densitybased clustering.
100% 17
Reducesthe featuresusing DWTandthen worksby applyingDCT ontheblocks (reduced featuresofthe image).These arefurther lexicographical lyreducedand correlated.
73.62% 19
DoubleJPEG Compression Detection Basedon Noise Free DCT Coefficients Mixture
Thispaper talkedabout animproved doubleJPEG compression detection methodbased onnoise free
1.Method basedon noise freeDCT coefficients mixture histogram model
Varying betwee n50to 100%
13
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN:2395 0072
Mahmood, Toqeer; Mehmood, Zahid;Shah, Mohsin;Saba, Tanzila (2018).A robust techniquefor copy move forgery detectionand localization indigital imagesvia stationary waveletand discrete cosine transform.
Gani, Gulnawaz; Qadir,Fasel (2020).A robustcopy moveforgery detection technique basedon discrete cosine transform andcellular automata.
This literature proposesthe robust technique usingCMF detectionand localisationin digital images.
Thistechnique is implemented usingaSWT basedon featureswhich isusedfor exposing forgeriesinthe images
Varying case wise
20
Image Manipulation Detection using Convolutional Neural Network,Kim, D. H&Lee,H. Y.
Usesmodified imagesgenerated usingmedianfilter processing, GaussianFiltering, andblurring, Additivewhite Gaussiannoise additionwith imageresizing.
Itcanbe appliedforthe detectionof more manipulation techniquesifa bettermodel isestablished inlater studies.In addition,it willbe possibleto applyitto various multimediaas wellasimage infurther research
[2]
Arobust methodfor detecting copymove forgeryunder different forgery attacksusing DCTand cellular automata
ItusesDCTto extract featuresfrom eachblock thenthe Cellular Automatais employedto construct featurevectors basedonthe sign informationof theDCT coefficients. Thenthe featurevectors arematched usingthekd treebased nearest neighbor searching methodtofind theduplicated areasinthe image.
Varies case wise but maintai nsits accurac y betwee n70% to90%
21
Developingan Image Manipulation Detection Algorithm BasedonEdge Detectionand FasterR CNN, XiaoyanWei, YirongWu, Fangmin Dong, Jun Zhang&Shuifa Sun
Constrained R CNN:A General Image Manipulation Detection model,Chao Yang,Huizhou Li,Fangting Lin,BinJiang, HaoZhao
Insteadofusinga max pooling approach,the Bilinear interpolation methodisusedto obtaintheRoI region.Aregional ProposalNetwork isusedtolocate theforgery locations.
Cancapture manipulationclues directlyfromdata withoutany handcrafted component.
Multiple featuresof tampered imagescould befusedto findmore tampering cluesand improve image manipulation detection performance.
Limitedto manipulation classification and localization.
[3]
Table 2: Comparisonofmethodswithrespectto correspondingAdvantagesandFutureScope
Title Advantages FutureScope Citation No.
ADeep Learning ApproachTo Universal Image Manipulation Detection UsingANew Convolutional Layer, Belhassen Bayar, MatthewC. Stamm
Usesadeep learningmodel, improved accuracy, introducedanew convolutionlayer, reductionin overfittingofthe model.
Time complexity increases,and thelengthy process
Automated imagesplicing detection usingdeep CNN learned featuresand ANN based classifier, SouradipNath &Ruchira Naskar
Withthe experimental results,itis demonstratedthat theperformanceof theproposed modelissuperior tothatofthestate oftheart.
[1]
ADeep Learning basedMethod forImage Splicing Detection, KunjBihari Meenaand VipinTyagi 2021J.Phys.: Conf.Ser. 1714012038
Theusageofthe noseprinting methodenables themodelto highlightthe tamperedpartsof theimagewith muchhigher accuracy.
Thismodel canonly detect whetheran imageis splicedornot butdoesnot involvethe localizationof slicedregions withinsuchan image.Inreal lifecases,this isofutmost importance.
Itdoesn’ttell usany information aboutthe splicedregion andavoids headinginto theanalytics oftheimage.
[4]
[11]
[12]
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN:2395 0072
K.M.Hosny,A. M.Mortda,M. M.Fouda,and N.A.Lashin, AnEfficient CNNModelto DetectCopy MoveImage Forgery
Obtainsan accuracyof100% andisquickand accurate.
Thismodel needstobe trained first andthen tested.
[44]
PassiveImage Forgery Detection Based onthe Demosaicing Algorithmand JPEG Compression Vega,Esteban Alejandro Armas; Fernandez, Edgar Gonzalez; Orozco,Ana Lucila Sandoval; Villalba,Luis JavierGarcia
Sincetheproposed modeldoesn’tjust considerfeatures, ithasabetter chanceat localisationofthe partoftheimage thathasbeen forgedbecauseit cancomparethe contentsofthe originalimage fromthe manipulatedparts.
Themodel successfully worksonlyfor imageswith dimensionsof 700x700 pixelsor greater.Hence moreworkfor theproposed methodtobe abletowork onthesmaller imagesisyet tobedone.
[42]
Fusionoffeatures fromthetwo streamsthrougha bilinearpooling layertofurther incorporatespatial co occurrenceof thesetwo modalities
JPEGCompressionwithoutCNNtechniques: LearningRich Featuresfor Image Manipulation Detection, Zhou,Peng& Han,Xintong &Morariu, Vlad&Davis, Larry
Canbeinfused inamuch bettermanner withbetter JPEG compression techniques.
[6]
BoLiu,Chi ManPun, Xiao Chen Yuan,"Digital ImageForgery Detection UsingJPEG Featuresand LocalNoise Discrepancies"
DoubleJPEG compression forensics basedona convolutional neural network, Wang,Qing, andRong Zhang
Achieves localization automaticallyand hasabetter performanceonly oncertainQF valueswhichstill haven’tbeen automated.
The computational complexityof theCNNis considerably high,thus generatinga trade off betweenthe localization accuracycap abilityandthe computational effortrequired
Performsbetterin caseswherejpeg imagesare compressedwith unknownQFs, therefore,giving theproposed methodasuperior generalization ability.
TheQFfactors consideredin the compression ofJPEGsare extremeand maynotbe applicablefor regularreal worldcases.
[7] Rao,Yuan,and JiangqunNi. "Self supervised domain adaptationfor forgery localizationof JPEG compressed images."
[41]
Imagesplicing detection basedon Markov featuresinthe QDCTdomain, CeLia,Qiang Mab,Limei Xiaob,Ming Lib,andAihua Zhang
Hasasimulation basedapproach henceisableto simulateand counterareal splicingattackdue toits implementation usingafactorthat calculatesthe coefficientusing theimageequality. Itishighly applicableto highlycompressed andhigh quality images.
Reducesrounding errorsofthe transformfromthe Polarcoordinate systemtothe Cartesian coordinatesystem, anew transformation methodis presentedand discussedindetail atthesametime.
Worksbetteron thedatasetused thanothermodels withtheblind detectionmodelon colorimages.
Itsaccuracyis dependenton theJPEG compression ratio.
Reliesheavily oncomplex algorithms hencethetime neededisalot. Lexicographic sortingdoes noteasethe complexity butrather increasesit.
[8]
[43] TransformTechniques: Researchon Copy Move ImageForgery Detection Using Featuresof DiscretePolar Complex Exponential Transform, YanfenGan& JunliuZhong
Doesnot possess theoretical valuebutis moreinclined toward practical value.
[9]
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN:2395 0072
DCT domain Deep Convolutional Neural Networksfor MultipleJPEG Compression Classification, VinayVerma, Nikita Agarwal,and NitinKhanna
DoubleJPEG Compression Detection Basedon Noise Free DCT Coefficients Mixture Histogram Model ,Zhu,Nan, JungeShen, andXiaotong Niu.2019.
1.Itdirectly utilizesJPEG bitstreamand reducesany additionaleffectof performingDCTon thedatafedtothe CNN, outperformingthe existingsystemfor multipleJPEG compression classifications
SinceforeachDCT frequency,a posterior probabilityis obtainedby solvingtheDCT coefficients mixturehistogram withasimplified modelitensuresa muchsmarter model.
Limitationof theproposed methodisthe requirement ofthesame compression chainsin trainingand testingdata.
[10]
The quantization noiseis neededtobe improved uponasitmay resultinfalse detectionof false tampered regions.
[13]
Hegazi,Aya; Taha,Ahmed; Selim,Mazen M.(2019).An improved copy move forgery detection basedon density based clusteringand guaranteed outlier removal.
Hayat,Khizar; Qazi,Tanzeela (2017). Forgery detectionin digitalimages viadiscrete waveletand discrete cosine transforms.
Themethod implementedgives acollective accuracyof95.83 %sincetheSIFTis activelyableto robustlydetectthe forgeryinjpg compressionand featuretransform methods.
Thechoiceof numberof blockswill hamperthe accuracyand performance ofthemodel andaffectthe SIFT
[17]
Themask multiplication basedmethodwith themelangeofthe DCTandDWT methodswere crucialincreating alessfalse detectionrate.It possessesviability forbothsplicing andcopymove forgerymethods
May underperform inthecaseof occlusion.
[19]
Mahmood, Toqeer; Mehmood, Zahid;Shah, Mohsin;Saba, Tanzila (2018).A robust techniquefor copy move forgery detectionand localizationin digitalimages viastationary waveletand discrete cosine transform.
Implementationpf SWT,DCT,and CMFDtechniques makesitmore robustandmakes representationof featuresmore diverse.
Post processing operations make detectionof CMF challenging.
Effectiveunder robustmethods andcandetectin presenceofnoise andcombined attacks.
Possesses unattractive time complexity.
[21]
[20] Gani, Gulnawaz; Qadir,Fasel (2020).A robustcopy moveforgery detection technique basedon discrete cosine transformand cellular automata.
Thevastgapsinimagemanipulationdetectiontechniques start with the continuously evolving methods of artificial intelligence and machine learning techniques to improve the quality of manipulated images and content. When it comes to identifying one unique reliable and accurate method for all possible images, many of the detection techniquesfallshortofdatasetsavailability.
Even though all the highly specific methods are robust, one cannot deny the need for the presence of human intervention. This posesa gapin research. Byconsidering the multiple features of the image (which is normally in RGB)songwithitsnoisefeatures,theRGB Ngeneratesthe correct classification for different tampering techniques which makes it genuinely robust. This method is largely applicable across various image manipulation techniques. However, in cases of JPEG compression, it is still to be accurately developed. Although many suggest using deep learning models as an approach to apply a generalized solutiontothedetectiontechniquesitfailstocomeacross in terms of the power of giving a good performance in several applications. At times of innocent manipulations i.e., those carried out by error of machine or quality deterioration(examples unintendedblurring/reductionin the files quality/compression etc.), method specific models can sometimes identify it as a manipulation. Such casesmustbeconsideredinthedatasetsinsteadofhaving
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN:2395 0072
them identified. Ultimately, copyrighting proves most essentialinprovidingproofofsuccessfuldetectionoffake imagesaswell.Withthecopyright,originalimagescan be recognized and safely stored from manipulation regardlessofwhohasaccesstoit
Challenges in image manipulation detection techniques include:
ProcessingofVideoincludesmanysecurityissues (Watermarking, Encryption, and Steganography) usingthedifferentcompressiontechniques.
Videotransmissionoverrealwirelesschannels.
Image enhancements based on Fusion techniques which is a very hot topic, especially for medical purposes.
research in the future, it could be possible to implement suchamodel.
[1] Bayar, Belhassen, and Matthew C. Stamm. "A deep learning approach to universal image manipulation detectionusinganewconvolutionallayer."InProceedings of the 4th ACM workshop on information hiding and multimediasecurity,pp.5 10.2016.
[2] Kim, Dong Hyun, and Hae Yeoun Lee. "Image manipulation detection using convolutional neural network." International Journal of Applied Engineering Research12,no.21(2017):11640 11646.
Deep learning and its wide applications in Signal processing.
The Application of the Advanced Optimization techniques for solving the multi variable problems in several digital signal processing problems.
Throughout the kinds of literature reviewed and studied, many challenges were observed over the span of all the varioustechniquesandproposedmethods.Incaseswhere thefeatureswerebeingdetectedandscrutinizedusingthe transformation techniques, although they were highly robust and powerful, they were seen to be susceptible to factors like additive white noise, the combination of attacks, time complexities, and precision. The dimensionality reduction based methods tend to ignore the crucial data which results in a lack of robust results and accuracy in cases of geometric transformations. This madeitdifficulttoidentifyhowmanyfeaturesareexactly enough for transformation based techniques since even though the accommodation of multiple features will increase the accuracy of the results of the model it will result in an unattractive time complexity which is not desirableformostofthetimeincaseofforensics.Texture based detection methods, since they function block wise, tendtoalsobesensitivetothescalingoperations,rotation operations,andjpegcompressions.
Despite the rise in technologies to detect the forgery of media, it has become terribly difficult to differentiate between real and fake images even with the intervention of humans. Thus the symbiotic relationship between humansandA.I.arevastforapplicationinthefieldoflaw enforcement and forensics. Through this review, we conducted comparative research on how successful a certain method would bein order tosee what would bea more robust and accurate approach to any image regardless of the image manipulation method. With more
[3] Wei, Xiaoyan, Yirong Wu, Fangmin Dong, Jun Zhang, and Shuifa Sun. "Developing an image manipulation detection algorithm based on edge detection and faster r CNN."Symmetry11,no.10(2019):1223.
[4] Yang, Chao, Huizhou Li, Fangting Lin, Bin Jiang, and Hao Zhao. "Constrained R CNN: A general image manipulation detection model." In 2020 IEEE InternationalConferenceonMultimediaandExpo(ICME), pp.1 6.IEEE,2020.
[5]Yang,Chao,ZhiyuWang,HuaweiShen,HuizhouLi,and Bin Jiang. "Multi Modality Image Manipulation Detection." In2021IEEEInternationalConferenceonMultimediaand Expo(ICME),pp.1 6.IEEE,2021.
[6] Zhou, Peng, Xintong Han, Vlad I. Morariu, and Larry S. Davis. "Learning rich features for image manipulation detection." In Proceedings of the IEEE conference on computer vision and pattern recognition, pp. 1053 1061. 2018.
[7] Wang, Qing, and Rong Zhang. "Double JPEG compression forensics based on a convolutional neural network."EURASIPJournal onInformationSecurity2016, no.1(2016):1 12.
[8] Gan,Yanfen,andJunliuZhong."Researchoncopy move image forgery detection using features of discrete polar complex exponential transform." International Journal of Bifurcation and Chaos 25, no. 14 (2015): 1540018.
[9] Li, Ce, Qiang Ma, Limei Xiao, Ming Li, and Aihua Zhang. "Image splicing detection based on Markov features in QDCT domain." Neurocomputing 228 (2017): 29 36.
[10] Verma, Vinay, Nikita Agarwal, and Nitin Khanna. "DCT domain deep convolutional neural networks for multiple JPEG compression classification." Signal Processing:ImageCommunication67(2018):22 33.
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page 2472

International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056 Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN:2395 0072
[11] Nath, S., Naskar, R. Automated image splicing detection using deep CNN learned features and ANN basedclassifier.SIViP15,1601 1608(2021).
[12]KunjBihariMeenaandVipinTyagi2021J.Phys.:Conf. Ser.1714012038
[12] Zhu, Nan, Junge Shen, and Xiaotong Niu. 2019. "DoubleJPEGCompressionDetectionBasedonNoise Free DCTCoefficientsMixtureHistogramModel"Symmetry11, no.9:1119.https://doi.org/10.3390/sym11091119
[14] Birajdar GK, Mankar VH. Digital image forgery detection using passive techniques: A survey. Digital investigation.2013Oct1;10(3):226 45.
[15] M. Ali Qureshi and M. Deriche, "A review on copy move image forgery detection techniques," 2014 IEEE 11thInternationalMulti ConferenceonSystems,Signals& Devices (SSD14), 2014, pp. 1 5, doi: 10.1109/SSD.2014.6808907.
[16] Qureshi, Muhammad Ali; Deriche, Mohamed (2015). A bibliography of pixel based blind image forgery detection techniques. Signal Processing: Image Communication, 39(), 46 74. doi:10.1016/j.image.2015.08.008
[17] Hegazi, Aya; Taha, Ahmed; Selim, Mazen M. (2019). An improved copy move forgery detection based on density based clustering and guaranteed outlier removal. Journal of King Saud University Computer and Information Sciences, (), S1319157819304707 doi:10.1016/j.jksuci.2019.07.007
[18] Deshpande, Pradyumna, and Prashasti Kanikar. "Pixel based digital image forgery detection techniques." International Journal of Engineering Research and Applications(IJERA)2,no.3(2012):539 543.
[19] Hayat, Khizar; Qazi, Tanzeela (2017). Forgery detection in digital images via discrete wavelet and discrete cosine transforms. Computers & Electrical Engineering, (), S0045790617305785 doi:10.1016/j.compeleceng.2017.03.013
[20] Mahmood,Toqeer,ZahidMehmood,MohsinShah, and Tanzila Saba. "A robust technique for copy move forgery detection and localization in digital images via stationarywaveletanddiscretecosinetransform."Journal of Visual Communication and Image Representation 53 (2018):202 214.
[21] Gani, Gulnawaz; Qadir, Fasel (2020). A robust copy move forgery detection technique based on discrete cosine transform and cellular automata. Journal of Information Security and Applications, 54(), 102510 doi:10.1016/j.jisa.2020.102510
[22] Kaushik, Rajeev, Rakesh Kumar Bajaj, and Jimson Mathew. "On image forgery detection using two dimensional discrete cosine transform and statistical moments." Procedia Computer Science 70 (2015): 130 136.
[23] Moghaddasi, Zahra, Hamid A. Jalab, and Rafidah Md Noor. "Image splicing forgery detection based on low dimensional singular value decomposition of discrete cosine transform coefficients." Neural Computing and Applications31,no.11(2019):7867 7877.
[24] Ojeniyi,JosephA.,BolajiO.Adedayo,IdrisIsmaila, and Shafi’I. Muhammad Abdulhamid. "Hybridized technique for copy move forgery detection using discrete cosine transform and speeded up robust feature techniques."(2018).
[25] Kumar, Sunil, Jagannath Desai, and Shaktidev Mukherjee. "A fast DCT based method for copy move forgery detection." In 2013 IEEE Second International ConferenceonImageInformationProcessing(ICIIP 2013), pp.649 654.IEEE,2013.
[26] Alkawaz, Mohammed Hazim, Ghazali Sulong, TanzilaSaba,andAmjadRehman."Detectionofcopy move imageforgerybasedondiscretecosinetransform."Neural ComputingandApplications30,no.1(2018):183 192.
[27] Armas Vega, Esteban Alejandro, Edgar González Fernández, Ana Lucila Sandoval Orozco, and Luis Javier García Villalba. "Copy move forgery detection technique based on discrete cosine transform blocks features." Neural Computing and Applications 33, no. 10 (2021): 4713 4727.
[28] Reddy, V., K. Vaghdevi, and Dr Kolli. "DIGITAL IMAGE FORGERY DETECTION USING SUPER PIXEL SEGMENTATION AND HYBRID FEATURE POINT MAPPING." European Journal of Molecular & Clinical Medicine8,no.2(2021):1485 1500.
[29] Chen, Haipeng, Xiwen Yang, and Yingda Lyu. "Copy move forgery detection based on keypoint clustering and similar neighborhood search algorithm." IEEEAccess8(2020):36863 36875.
[30] Li, Weihai, and Nenghai Yu. "Rotation robust detection of copy move forgery." In 2010 IEEE International Conference on Image Processing, pp. 2113 2116.IEEE,2010.
[31] Soni, Badal, Pradip K. Das, and Dalton Meitei Thounaojam."CMFD:adetailedreviewofblockbasedand keyfeaturebasedtechniquesinimagecopy‐moveforgery detection." IET Image Processing 12, no. 2 (2018): 167 178.
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page 2473

[32] Silva, Ewerton, Tiago Carvalho, Anselmo Ferreira, and Anderson Rocha. "Going deeper into copy move forgerydetection:Exploringimagetelltalesviamulti scale analysis and voting processes." Journal of Visual CommunicationandImage Representation29(2015): 16 32.
[33] Hsu, Chih Chung, Tzu Yi Hung, Chia Wen Lin, and Chiou TingHsu."Videoforgerydetectionusingcorrelation of noise residue." In 2008 IEEE 10th workshop on multimediasignalprocessing,pp.170 174.IEEE,2008
[34] Bo, Xu, Wang Junwen, Liu Guangjie, and Dai Yuewei. "Image copy move forgery detection based on SURF." In 2010 International Conference on Multimedia Information Networking and Security, pp. 889 892. IEEE, 2010.
[35] Wu, Yue, Wael Abd Almageed, and Prem Natarajan."Busternet:Detectingcopy moveimageforgery with source/target localization." In Proceedings of the Europeanconferenceoncomputervision(ECCV),pp.168 184.2018.
[36] Zheng,Lilei,YingZhang,andVrizlynnLLThing."A surveyonimagetamperinganditsdetectioninreal world photos." Journal of Visual Communication and Image Representation58(2019):380 399.
[37] Hashmi, Mohammad Farukh, Vijay Anand, and Avinas G. Keskar. "Copy move image forgery detection using an efficient and robust method combining un decimated wavelet transform and scale invariant feature transform."AasriProcedia9(2014):84 91.
[38] Wu, Yue, Wael Abd Almageed, and Prem Natarajan. "Deep matching and validation network: An end to end solution to constrained image splicing localization and detection." In Proceedings of the 25th ACM international conference on Multimedia, pp. 1480 1502.2017.
[39] Zhang, Qingbo, Wei Lu, and Jian Weng. "Joint image splicing detection in dct and contourlet transform domain." Journal of Visual Communication and Image Representation40(2016):449 458.
[40] Rao, Yuan, and Jiangqun Ni. "Self supervised domain adaptation for forgery localization of JPEG compressed images." In Proceedings of the IEEE/CVF International Conference on Computer Vision, pp. 15034 15043.2021.
[41] Vega, Esteban Alejandro Armas, Edgar González Fernández, Ana Lucila Sandoval Orozco, and Luis Javier García Villalba."Passiveimageforgerydetection based on the demosaicing algorithm and JPEG compression." IEEE Access8(2020):11815 11823.
[42] Bo Liu, Chi Man Pun, Xiao Chen Yuan, "Digital Image Forgery Detection Using JPEG Features and Local Noise Discrepancies", The Scientific World Journal, vol. 2014, Article ID 230425, 12 pages, 2014. https://doi.org/10.1155/2014/230425
[43] Hosny, Khalid M., Akram M. Mortda, Mostafa M. Fouda, and Nabil A. Lashin. "An Efficient CNN Model to DetectCopy MoveImageForgery."IEEEAccess10(2022): 48622 48632.
International Research Journal of Engineering and Technology (IRJET) e ISSN:2395 0056 Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN:2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page 2474
