International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
Student, Dept. of Information Science and Engineering, RV College of Engineering, Bangalore, Karnataka, India Associate Professor, Dept. of Information Science and Engineering, RV College of Engineering, Bangalore, Karnataka, India ***
Abstract Today's development is mostly done using a microservice architecture. As part of the microservices architecture, applications are built from a number of small modular services. In 2014, Google, Netflix and Twitter implementedMicroserviceArchitecture(MSA),whichruns as separate processes and communicates with each other in different ways. Since then, these companies have widely decoupled and implemented Microservice Architecture. With this design, an application's services are broken down, distributedindependently,andthenrun.Inthisstudy,welook at how Java microservices can be developed, as well as how OAuth2 and the Spring Security Framework can be used to secure microservice APIs that are built on top of the Spring Framework.
Key Words: SpringBoot, Microservice Architecture (MSA), Software Architecture, OAuth2, Proof of Concept (POC), and Spring framework.
AlthoughRESTfulendpointswithasinglefunctionalityare howmicroservicesarefrequentlycharacterized,there are numerous different ways for developers to build these services.Themicroservicearchitecturalstylewascreatedas a result of the architectural design of Service Oriented ArchitectureandDomain DrivenDesign,withasignificant focusonDevOpstechniques.Ithasattractedalotofinterest from academics as a trustworthy and scalable solution to constructcloudservices,andithasalsobeenwidelyadopted bycompanieswithmillionsofclients,likeNetflixorAmazon.
Inanutshell,themicroservicearchitectureencouragesthe division of the programme into services as an unique software architecture. According to the conventional monolithic method of software architecture, each deploymentrequiresthebundleofthefullapplicationstack. Thisideahasnumerousdisadvantagesfortheapplication, including rigid scalability, significant resource costs and refactoring effort, and challenges with DevOps amongst scatteredteams.BycreatingaProofofConcept(POC)ofan MSA application utilizing the Spring Framework, Spring Security,andOAuth2,andperformingsecuritytestingover thePOC,thisresearchaimstoclosetheknowledgegapon MSAandAPIsecurity
RESTful endpoint based applications operating independentlyandactingasservicesforacertain systemcharacteristic.
CreationofheadlessserviceslikeAWSLambda,also referredtoasFunctionasaService(FaaS).
Services that use messaging or events to communicate,suchasclusteredVert.xvertices(the JavaReactiveframework),areknownasmessaging orevent basedservices.
Itcanbedifficulttothinkaboutthetechnologyroadmap whileswitchingfromsuchamonolithictosomethinglikea microservices architecture because there are so many concepts,problems,andtechnologicaloptions.Peoplecould therefore overthink the issue and overdevelop theanswer when developing a new application under a microservice architecture.Themostcompletecoverageformicroservices librariesisprovidedbytheSpringframework,whichispart oftheJavaecosystem.
AvarietyoflibrariesarelistedwithusecasesinTable 1.
Table 1: LibrarieswithUseCases
Library Usecases Tools Illustration
Discoveringand RegisteringServices Manage configurations ina distributed andsafe manner
Implementation Management Using registered servicenames tolocate servicenodes
SpringCloud Configuration, Consultation, andVault
SpringCloud NetflixEureka, Consul
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
Monitoringfor Systems,JVMs,and APIs
Performance degradation, riskand crashanalysis
APIGateway servingasa pointofentry andmanaging issueswith security,URL name,etc.
Security Securesocket layer authenticity usinga passwordand adigest, OAUTH,and JWT,andsocial login integrations
NewRelic, SpringBoot Adminand Datadog
Zuul,Nginx, cloud provided API gateways
SpringSecurity forSpring
There is a very robust community that can offer answerstomanypotentialissues.
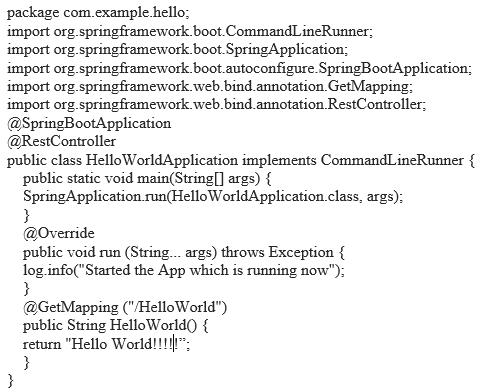
Examine the base class for our usage cases and the Hello World application example. This class will serve as the foundationforoursamplewebapplication.Ifyouwantto change or modify anything, you can use a property file, a Metadatafile,orJava basedconfiguration.
Define the Application class first. The Spring Boot application'sstartingpointandRESTfulendpointareboth providedbythisshortsingleclass.
ClassofApplicationshowninFig 1below.
A new breed of Java frameworks allows you to swiftly packageanentirewebservicewiththeembeddedcontainer of your choice in an auto running JAR file. It was revolutionarytoswitchfromabig,heftyJ2EEcontainertoa smaller, lighter version. There will be a few frameworks accessible,suchasSpark,Dropwizard,andSpringBoot.We willinvestigateaSpringBootsample.TheSpringframework hasbeenusedtobuildJavaapplicationsformorethanten yearsandisthedefactoindustrystandard.
One important factor in Java's success in enterprise development is the Spring Framework. Almost all of the widely used libraries and frameworks for Java web development are supported by this framework. We can swiftlydevelopself runningmicroserviceswithSpringBoot in a matter of minutes. In the past, developing boilerplate code for an application's sole purpose of wiring Spring infrastructurecomponentsrequiredasignificantamountof development effort. The majority of the routine stuff has alreadybeensetupforus.
ListedherearesomeofSpringBoot'shighlights: Thingsmayberapidlysetupandgoing.
Overridingconfiguration,libraries,andframeworks isincrediblyflexible.
Factor
Anordertoeliminatetheneedformanualprojectsetupin thebeginning,theSpringFrameworkcommunityoffersan additionalfacility.Youcangetarapid,ready to launchinitial configuration witha listofall theSpringdependencieson thehttp://www.start.spring.iowebsite.
By default, Spring Boot loads the settings from class path filescalledapplication.propertiesorapplication.yml.Inthis manner,Javawillfinallybeusedtodevelopthemicroservice.
So we have created the microservices necessary to apply securityinordertomakesecureapplications.
Therefore,inordertobuildsafeapps,wehavedesignedthe microservices that are required to apply security. Applicationsexchangeinformationwithoneanotheracross theInternetandnetworkcommunicationprotocols,hence this architectural design strongly relies on APIs (API). A microservice application's Api must be appropriately securedasaresultinordertoprotecttheapplicationaswell
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
as its resources against risks associated with API invocations.
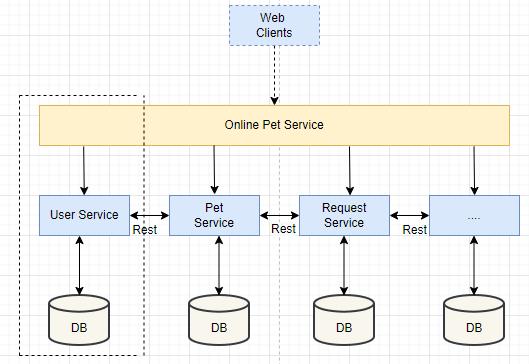
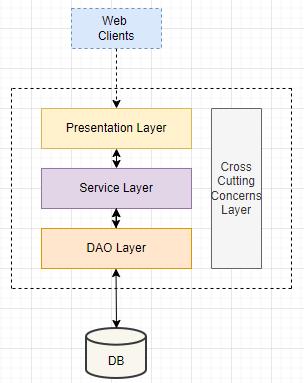
Microservice architecture (MSA) is the term for the application architecture that divides an application into a number of narrowly focused, single responsibilities, portable,andindependentlyevolvingservices.Thetypical monolithic software architecture, in contrast, deploys the completeapplicationwithallofitsservicesinsidejustone applicationserver.BecauseRESTisalightweightprotocol, this research employs it for the API development and experiment. MSA simply divides the application logic into numerous smaller components; it does not make a programmeanysimpler.Scalabilityandhighavailabilityare two benefits of decomposition, but it also results in a significantly highly complex network linkage between components,especiallywhenevertheapplicationismadeup of an excess amount of services. A comparison of the monolithicandmicroservicearchitecturesisshowninFig 2 andFig 3.
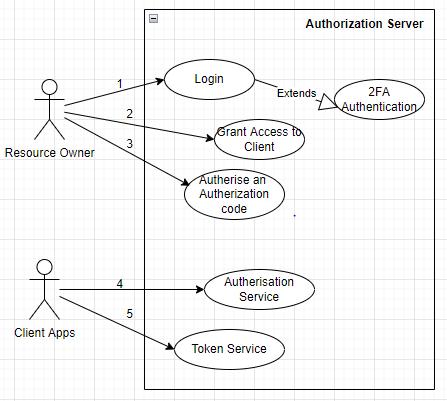
The POC is created in order to respond to the inquiry. Additionally,itmusttodemonstratehowMSAcanbeusedin actualbusinesssituations.Inordertoreplytotheenquiry, thePOCisestablished.Additionally,itmustshowhowMSA canbeappliedinreal worldbusinessscenarios.Thismakes aPOCforsuchjustaninventorymanagementsoftwarean appropriate experimental application. OAuth2 is used for backendservicesthatdon'tneedawebapplicationbrowser anduserinteractiontechniquesinadditionaltotheonline application,asseeninFig 4.ThePOCmustbeconstructedin a specific fashion in order to perform security checks for both of these technology types. Additionally, OAuth 2.0 should be investigated in the experiment for both authenticationandauthorizationneeds.Keycharacteristics and actors are suggested in the following subsections in accordancewiththeexperimentalneeds.
The Identity Provider in the OAuth2 process is the AuthorizationServer.Thedesignprovidesthefundamental use scenarios for the Authorization Server, as shown in Figure 4. The following two actors communicate with the AuthorizationServer:
OwneroftheresourceintheOAuth2workflow.
The client app is the client application which has identifiedwiththeauthorisationserver.
International Research Journal of Engineering and Technology (IRJET)

e ISSN: 2395 0056
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
Thebuilt inAuthorizationServerConfigureAdapterof the Spring Security Framework is improved by OAuth configuration and now includes an implementation for OAuth2 authorisation support. It offers the following key features:
OAuthDataSource:searchesthedatabaseforclient informationduringtheauthorizationprocedure.
TokenStore: The Java Database Connectivity (JDBC)approachisusedtoaccesstheaccesstokens keptinthedatabaseaswell.
ApprovalStore:UsingJDBCtechnology,usersmay accessapprovaldatathatiskeptinadatabase.
Usescenariosforanresourceserverinclude:
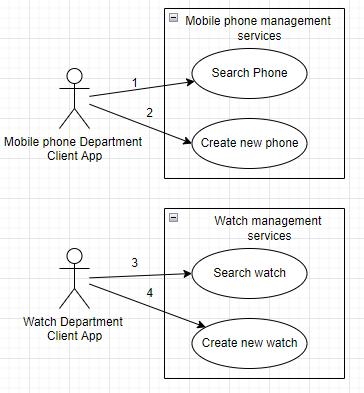
TherearetwomicroservicesputintoplacebythePOCto manage the watch and mobile phone, respectively. The microservicesreplacetheRPsintheOAuthpipeline.Figure5 displaystheusecasesfortheresourceserver.
AuthorizationCodeServices:Authorizationcodes are saved in a database, just like in the ApprovalStore.
ConfiguretheClientDetailsServicebydefiningeach unique client and their properties with configure(ClientDetailsServiceConfigurerclients). void Use the configure(AuthorizationServerEndpointsConfigurer endpoints) command to set up the Authorization Server access points, including a token storage, authenticatingcodeservice,tokencustomizations, userapprovals,andgranttypes.
Justnow,welookedatthestandardstartingpoint.Duetothe factthatitoffersthemostcomprehensivesolutionsforthe diverse needs of any corporate system, the most of the examplesweexaminefromhereonoutwillutilisetheSpring Framework. Using Spring Boot, we may split a larger microserviceintosmallerones.Microservicesinteractwithin the MSA application with one another using service API endpoints. An API endpoint is a location in which the servicescanconnectandreceivetheresourcestheyneedto performtheirduties.TheAPIendpoint,whichservesasthe interface through which data is transferred between services,iscrucialinensuringtheproperoperationofthe systems and services that interact with it. As a result, API endpoint security is among the most crucial security componentsinanMSAapplications.Theresearcherhopesto expandonthisworkinthefuturetoincludethesecurityof allAPIimplementations,aswellasthesecurityofadditional applicationlayerslikethebusinesslayerandthedataaccess layer. As a result, suggest an API security solution that is morecompletefortheJava basedmicroserviceapplication.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
[1] Y.Gong,F.Gu,K.ChenandF.Wang,"TheArchitectureof Micro services and the Separation of Frond end and Back end Applied in a Campus Information System," 2020 IEEE International Conference on Advances in Electrical Engineering and Computer Applications( AEECA),2020,pp.321 324
[2] R. Pereira, P. Simão, J. Cunha and J. Saraiva, "jStanley: PlacingaGreenThumbonJavaCollections,"201833rd IEEE/ACM International Conference on Automated SoftwareEngineering(ASE),2018,pp.856 859
[3] Y.GanandC.Delimitrou,"TheArchitecturalImplications of Cloud Microservices," IEEE Computer Architecture Letters,vol.17,no.2,July Dec.2018,pp.155 158
[4] Hatma Suryotrisongko, Dedy Puji Jayanto, Aris Tjahyanto, “Design and Development of Backend Application for Public Complaint Systems Using MicroserviceSpringBoot”,ProcediaComputerScience, vol.124,2017,pp.736 743
[5] Y. Jayawardana, R. Fernando, G. Jayawardena, D. WeerasooriyaandI.Perera,"AFullStackMicroservices Framework with Business Modelling," 2018 18th International Conference on Advances in ICT for EmergingRegions(ICTer),2018,pp.
[6] Hatma Suryotrisongko, Dedy Puji Jayanto, Aris Tjahyanto, “Design and Development of Backend Application for Public Complaint Systems Using Microservice Spring Boot”, 4th Information Systems International Conference 2017, ISICO 2017, 6 8 November2017,Bali,Indonesia
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal
