International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
 Madhu M S 1 , Dr. Chandrakala V 2 , Praveen K B 3
Madhu M S 1 , Dr. Chandrakala V 2 , Praveen K B 3
1
M.Tech Student[DCN]Department of Electronics and Telecommunication, Dr. Ambedkar Institute of Technology, KARNATAKA, INDIA ***
Abstract Mobile ad hoc networks (MANETs) only have individual sidekicks and lack an edge. This article demonstrates rigorous convention directing testing for MANET.ThetestbedrunningontheLinuxplatformisshown on mobile PCs. For outline, advancement speed, and the number of hops that affect steering judgment, various limitationsareexcavated.Onceagain,twoperformancesare chosen to be coordinated for the testbed evaluation. The maindisplayisreferredtoasBABELandisacomputation forcoordinatingpartitionvectors.Theenhancedinterface state directing convention (OLSR), which is regarded as a visionarycontrollingshow,isthealternative.Amulti bounce downloadofarchiveswithdistinctsizeswastheapplication scenario.Thegoalistoanalyzerwhatdifferentbobssignify forholdbackandexchangespeed.Theproblemsshowthat OLSR performs better in terms of the outcome. Babel, however,haslesserdeferralandishastywithconjunction.
Key Words: MANET, wireless communication, Routing Protocols, transmission delay and packet delivery ratio, energyconsumption
Thedynamicpenetrationofremoteconnections(3)Mobile orremoteadhocnetworkisacutting edgetechnologythat enhancesthetendenciestodeveloppositivestrikesorsolid organization.Doesnotcountondesign(2).Thehitsincluded in this mobile network or remote ad hoc network are not resolvedinanyway;Instead,theystrikefreelyandextend theconnectiontoanearbydeviceviaaremotewithoutthe need for a centralized entity to keep them pointed in the rightdirection.Becauseitismoving,itbeatsgraduallyand quickly(9).Becauseofitsoutstandingfeatures,mobilead hoc networks create many routing challenges because strikesintheadhocnetworkoccupyaportionofthehosts and switches needed to conquer all data (2). Therefore, routingcalculationplaysanimportantroleinMANETRebar design.(3)TheseintriguingfeaturesmakeMANETpopular inawidevarietyofmissions,includingmilitarygovernance, marinescience,clinicalfields,attractivedepartments,area regulationandrecovery missions.Aspartofthe research, philosophieswereappliedtotraditionalnetworkssuchas
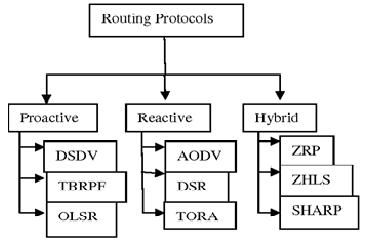
Table Drive, On Demand, Situation Centric, Progressive, SenselessandMultipath(1)usingcomprehensivedatafor traditionalmethodssuchasB(12).Inordertoimprovethe
organization'sexistence,itisnecessarytolessenorchange thewaythatportableadhocnetworksaremanagedsince thedrawbacksincludelowpowerinclination.tosimplifythe process of transmission while maintaining calmness. Finalizingthesteeringsetupthatgeneratesaportablehello correspondence that is occasionally communicated along withtheknocksspeedtodecreasetrafficandoutpouringin the organization (5), the directing hybridizing two or differentstyleswerealsoused(13),(14),and(15)inrisking a more available framework, to limit start to finish confinementandthememoryandpowerusage.Asampleof the steering options for the MANET are shown in fig. 1 below.
Every single style examined up until this point used methodstoenhanceorganizationallifebyreducingenergy consumption and reducing restrictions while looking into thequickestpossiblemeansofinformationtransmission,but theyall failedtogather informationonhowto maintain a constantmeansofcommunication.
Therefore, the suggested framework makes use of the type of machine education, the supporting learning for portability vaticination of knocks corresponding to the objectivetakingadvantageoftheknocksfromthedatathat could support in laying out the most constrained course alongsidethesteadyway.
Thedecentralization,tonaloperation,andotherintriguing features of the MANET attract effective attacks within the organization.Overthepasttenyears,avarietyofsecurity measureshavebeenintroducedtorepelattacksandmitigate
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
their by products. A wide range of these methods appear underthehighestsecuritystandardsonMANETs,builtona cryptographic approach. A complex framework of functionality was approved in 1999 for the use of limited ciphersforcertificationprocessingonspecificallydesignated networks. Some of the strikes carried out the work of the serversintheproposedframework,butmostofthestrikes stole the chief part. In addition, SAODV Comprehensive UnderstandingofAODV (4)wasintroduced.Theproposed system uses computerized hash chains and signatures for cryptographic security on designated networks. Several cryptographicsystemshavebeensetuponcentralauthority to push tools for verification reasons (5) (6) (7). (8) However,someotherapproaches,suchasthetrustmodelof the PGP network (9), changed the origin of central management (10). As a result, the authentication process involvesaseriesoftoolsstoredatitsends.Inthesestyles, therealgroupisreadytostoretheirtools.Inwriting,itwas noted that the ciphers introduced critical limitations in communicationandthatapre linkbetweenthehitsmustbe maintained, which is not achieved in casual meetings. Therefore, experimenters have used a wide range of hybridizationdesignstoimprovethesecurityoftheMANET. StrikesonMANETsaresubjecttoavarietyofattacks,suchas dynamicandopenattacks.Forexample,someexamplesof commonattacksarePower Challenging,Man in the Middle, Flooding, Mocking, Pantomime, Dark Opening, Opening ScoringAttacks,etc.Fineinterceptdetectionframeworksare usedintheliteraturetodescribeawidevarietyofattacks.
In short, various cryptographic tools have been used in thepasttohighlightthesecurityfeaturesoftheMANET,but overthepast10yearstherehasbeenachangeinthewaywe view networks as new developments such as machine learning, deep learning, and artificial intelligence. and hereditary calculations became a key decision. Experimenters on MANETs risk practical, security enhanced results. This study provides recent developmentsthathaveproveneffectiveinproviding safety outcomes. Included in the Excellent Safety GuidelinesbasedonMachinePerfection,aswellasthe detection, prevention, adoption and mitigation of penetratingstrikes.
Sendingemailsandsigningcontracts,forexample,wouldbe impossiblewithoutadequatesecuritymeasuresinplace.
Whencreatingsensitivesoftware,it'scrucialtokeepinmind theorganization'sfundamentalsecuritypillars.
Apredictionmodelmaybebuiltutilizingmanufacturing data for certain attack scenarios and evaluated with the remainderofthetestdatausingAIapproaches.Thequality ofthelearningmodelisscrutinizedinlightoftheprecision withwhichnewattackdesignsmaybedetected.Thehubson
theMANETaremorevulnerabletovarioustypesofattacks suchasfloods,DoSattacks,darkopenings,wormholes,dim openings,etc.duetothecompany'sopenenvironment.Hubs on the MANET also display multi echo correspondence, meaning that the source hub transmits packets to several intermediatehubsbeforesendingthemtothetargethub.All communication depends on the cooperation of the interlocutor. To prevent packets being diverted to any malicious or malicious hubs within the company, it is importanttodeterminethereliabilityofthehubsaspartof security efforts. To improve security in the organization, several confidence assessment approaches have been proposedintheliterature.TheclassmatesshowninFigure1 can be used to separate security devices on MANETs. In addition, ML plays an important role in improving the securityofmanyspeciallydesignednetworks.InMANETs, different ML computations can be used to isolate interruptions and clear attack strategies. To improve the security features in the company, many intellectual frameworksareotherwrittenproposals.Thefollowingthree obvious securityareasarediscussedinMANETusingML basedapproaches:
2. Related works:
HuaLiang,YanhHongShangetal.,[24]proposedtostudythe DTNroutingprotocolforavehicle specificnetworkbasedon machineliteracy.MANETincorporatestheVehicle Mounted Tone ArrangingNetworkintothisarchitecture.Itisbetween good correspondence equipment and off road vehicle. It serves as the hub for all street vehicles and offers multi horsepowerremotecontrolsandtheabilitytoexchangedata withothervehicles.
AccordingtoDr.M.Duraipandian's [25]proposed routing methodbasedonreinforcementalgorithm byestablishing theshortestpathforthemobileadhocnetworksevaluating theparameterslikethroughput,packetdeliveryratioetc.,
Rober a Sowah et al.,[12] presented intrusion detection systems using +e ANN classifier algorithm for network variedtrafficconditionsandmobilitypatternsin multiple attacks which offers a productive and less expensive to performMITMattacks.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
Bykeepinganeyeonalldatapertainingtothatparticular
parcel, we are sustaining USOR in this module. Since the parcel in this module is linked by a recognized stoner's agreement,othergroupscannottelltheinformationabout thatbundleapart.
The steering is a crucial component of a flexible ad hoc network, therefore the suggested system makes use of supportingadvancingtoroutepackagesfromthesourceto the target. When the lead includes the assurance of the detainment derived from the knocks readily available alongside the efficient transmissions of each bunch, the supportinglearningselectstheknocksbasedontheupsides ofthedirect.Themosteffectivetransmissionisdefinedinto a group using the k implies bunching, which is not completelyfixedwithminimalrestriction.Basedonitsprice, the appropriate gathering is selected from the range of availablegatherings.Thebestgroupselectionisfollowedby choosing the nearby hitch for the coming leap, the group with the closest distance to the goal is selected to be the approachingbounce,andcondition(5)providesthemethod usedingroupselection.
As a result, the group is referred to as a direct, and the group'sworthisdeterminedonthecostsoftheknocks.The quickestapproachisthenestablishedbyselectingkicksthat areasclosetothegoalaspossible.Thesetwocriteriaassess theworthofthegroups basedonthe quantityofeffective transmission (succtrans) and the confinement of the transmission.(6)and(7)(delaytrans).
Delaytrans=As*(ret=(v*MINvalue). 1
However,arithmetichelpsustoidentifythefastestwayto loserelevanceasstrikesarefarfromtheirintendedlocation. Therefore,intheproposedcourse,supportwillalsobeused toassesstheconditionsofgroupflexibilitytodisassemble theblows.
This module has a fake to authorize USOR while safeguardingallinformationincludedintheexpressbundle. Inthismodule,onlyapprovedaddictsareallowedtopossess thebundle;attractiveknockscannotvouchforitscontents.
To further ensure safe communication, we added a sophisticated hand architecture to this. We can use cryptosystemdesigntocreateadvancedsigns.Forasupport wisemeaningfulcryptosystem,therearefourcyclesthatare clearandessential.
a) Decrypting an encrypted communication reveals the preciseoriginalinformation
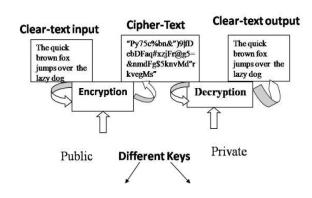
D(E(M))=M 2
b)ReversingtheprocessstillreturnsM: E(D(M))=M 3
c)EandDaresimpletocompute.
d) YoucannotjustdeduceDfromEsinceE'sopennessdoes notyieldD'sconcealment.
Supposee,dandnarepositiveintegerswhereeandnserve astheencryptionkeyanddandnasthedecryptionkeyand n=pq.
To get C, for reading the code cycle, we now monitor the similaritybyincreasingthenthpowerscale.TogetMagain, wealsotranslateCbyincreasingthepowerfactordthn.We officiallygetthesecodinganddecodingequationsforEand D.
C=E(M)=Me mod(N) 4
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
1. Source communicates course demand (RREQ) to the capitalsofitsneighboringcountriesandlocatesthecourseto thing.
2. Capitals truly examine their instructing table, and if no course is present, they reassign RREQ correspondence to theirneighbors
3. The process is repeated until the request reaches the object and the object responds to the source in a direct manner.
4.Eventually,thesourcewilldeterminewhichsectionsofthe proposed path are closest to them and forward channel request(CREQ)communicationtothecapitalsandrequests thattheirareadealswith.
5.Capitalcitiesreactwithchannel reply(CREP)messages andprovideinformationabouttheirregionalbearingstothe source.
6.Sourcediscoversthetraveltime(RTT)requiredtogetthe CREP, and whenever it is determined that RTT is more obvious than actual respect, it attests to the entry's proximity.
7. When the chosen association length is more than the actuallength,wormholecapitalsareidentified.Byandlarge, sourcefiguresinterfacelengthofassociationsexistinginthe way.
8. Source educates all other meccas to refrain from communicatingwithrelatedwormholecapitals.
Position Aware Services: Six Automatic Call Moving, Position Sub Par Turn Companion, Report Position UnambiguousOrganizations.
To demonstrate its feasibility and the short path that has beenestablished,theproposedframeworkwastestedusing the Enterprise Test System II device. The proposed framework, which will form a stable path for a flexible temporarygrid,isestimatedtohave100to500strokes,100 joules of first force, 100 seconds of breeding season and 2500 * 400 square meters of recreational space. The proposedframeworkiscomparabletoprevious modelsof the thin film method, which is more limited for ad hoc networks (11) and shortens the life expectancy of the shorthand calculation method based on the firefly (9) to increasethelifeexpectancyandtransportlife,basedonthe firefly (9) to demonstrate the increased viability of the suggestedfoundationforeffectivemail.
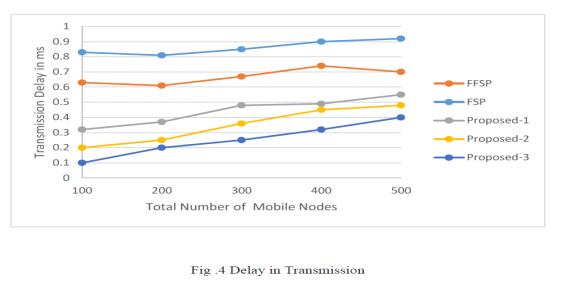
Theproposedapproachandtheothertwomethods,vague shortcutdeterminationfortemporarymobilenetworksand the firefly algorithm for finding short paths for mobile networks,willbeevaluatedbasedontheabovesimulation resultfortransmissiondelay.
The built method is stable and due to some failures and diversionduetorouteinstability,theproposedtechnology showsthatithaslessdelaythanthecurrentone.
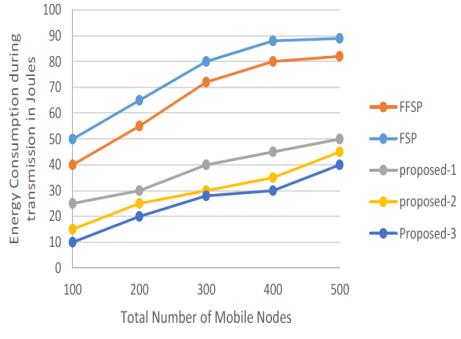
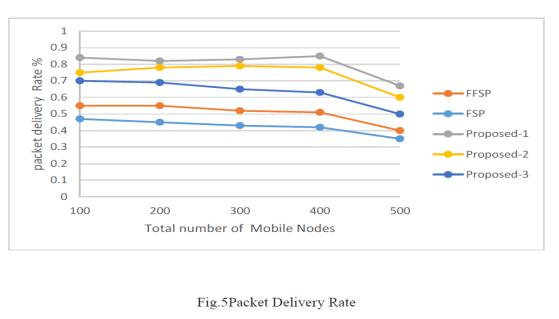
Thesimulationresultsaboveillustratetherateofpackets sent using the suggested strategy and the conventional method.Usingreinforcementlearningtobuildaconsistent shortrouteresultsina35%improvementinpacketdelivery. whichhastheeffectofcomparingtheproposedmethodto theopacity(FSP)basedshortcutand28%methodcompared tothestandard.
Thesimulation'sfindingsonhowmuchenergyisusedbythe suggested approach and the standard method as they transmitpacketsfromsourcetodestination.Theproposed
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
methoddemonstratestohaveasignificantamountofenergy savingsduetostableconnection established, avoidingthe circumstances of the rerouting protocol and links failure, even though all three methods have a limited energy consumptionduetotheestablishmentoftheshortestpath fromthesourcetothedestination.Thesimulation'sfindings onhowmuchenergyisusedbythesuggestedapproachand thestandardmethodastheytransmitpacketsfromsourceto destination. Due to the establishment of the shortest path fromthesourcetothedestination,allthreeapproacheshave arestrictedenergyusage.theproposedsolutionavoidsthe circumstances of the rerouting protocol and connections failure and demonstrates a significant amount of energy savingsthankstothestableconnectionformed.
ThisstudyprovidesanhonestevaluationofMANETrouting protocols for data dissemination and optimal guidance. Examines the OLSR and Babel separation guidelines for output, execution and stability. On MANET PCs, these two preemptiveheuristicconventionsarefrequentlyused.Our evaluation and research is based on testing with different hubportabilitysettingsandtrafficvolumes.Providedclear 10 axisresultsbyimplementingouruniquesetuprouting conventionwithvariableportabilityandtrafficloads.Babel is considered to be the least resource in terms of using resourcessuchasmemoryandhandling.
Additionally, the Routing Update component specifies howtoupdatechassischangesbysendingcontroltrafficas carryingroutingifalinkisfoundwithremotesystemsthat arelarge scaleormulti echorouting.Insuchcases,theOLSR isconsideredsuperiortotheBabel,andthisarisesbecause theOLSRhasitsentirecyclicaltemporalroleindirectingthe sending and updating of structural elements, as Babel considersupdatingthecourseonacase by casebasis.Due toBabel'sactions,OLSRcouldnotbecomparedtoBabelin termsofjoiningstrengthorcouplingcapacity.However,the substantialcostoftheroutingagreementmakesthisbabel reproduce an extra cycle and does not properly control traffic.
[1]GoyalNandGabaA,“Anewapproachoflocationaided routingprotocolusingminimumbandwidthinmobileadhoc network”, published in International Journal of Computer TechnologyandApplications,pp.653 656,vol4,ISSN:2229 6093,2013.
[2] Popli R, Garg K and Batra S “SECHAM: Secure and efficient cluster head selection algorithm for MANET”, proceedings in IEEE International Conference on Computing for Sustainable Global Development,pp.1776 1779,volume 2,2016.
[3] Kamboj P and Goyal N “Survey of various keys management techniques in MANET”, published in InternationalJournalofEmergingResearchinManagement andTechnology, ISSN: 2278 9359,Volume 4,pp176 178, 2015
[4] Zapata M G and Asokan N “Securing ad hoc routing protocolsWiSE”, Proceedings in ACM workshop on Wireless security,pp.1 10,2002.
[5] Capkun S, Buttya L and Hubaux J P “Self Organized Public Key Management for Mobile Ad Hoc Networks”, publishedinIEEETransactionsonMobileComputing,pp.365 455,vol.2,2003.
[6]HamzaFandVigilaSMC,“ReviewofMachineLearning Based Intrusion Detection Techniques for MANETs”, ProceedingsininternationalconferenceinComputingand NetworkSustainability,pp.367 374,2019.
[7]Bose S,BharathimuruganSand Kannan “AMulti layer intergradedanomalyintrusiondetectionformobileadhoc networks”, Proceedings in IEEE International Conference on SignalProcessingCommunicationsandNetworking,pp.360 365,vol.11,2007.
[8] Cabrera J.B.D,Gutirrez C, and Mehra R.K, “Ensemble methods for anomaly detection and distributed intrusion detectioninmobileadhocnetworks”,InformationFusion9 ,issue1,pp.96 119,vol.9,2008.
[9] Moradi Z, Teshnehlab M and Rahmani, “A Implementationofneuralnetworksforintrusiondetection in MANET”, Proceedings in International Conference on EmergingTrendsinElectricalandComputerTechnology,Vol. 5,pp.625 724,2011.
[10]LalliMandPalanisamyV“Anovelintrusiondetection modelformobilead hocnetworksusingCP KNN”, published in International Journal of Computer Networks and Communications,Vol3,Issue4,ISSN:2319 1953,(Impact Factor:0.654)2014.
[11] Sebopelo R, Isong B and Gasela N “Identification of Compromised Nodes in MANETs using Machine Learning Technique”, published in International Journal of Computer Network and Information Security,Vol.1,pp.1 10,2019.
[12]SowahRA,Ofori AmanfoKB,MillsGAandKoumadiK M,“Detectionandpreventionofman in the middlespoofing attacksinMANETsusingpredictivetechniquesinArtificial NeuralNetworks(ANN)”, published in Journal of Computer Networks and Communications, vol, https://doi.org/10.1155/2019/4683982pp1 15,2019.
[13]Goyal N,SandhuJ K, Verma L, “CDMA BasedSecurity Against Wormhole Attack in Underwater Wireless Sensor Networks”, published in Advances in Communication and
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
Computational Technology Lecture Notes in Electrical Engineering, , pp829 835,2021.
[14] Patel M, Sharma S and Sharan D, “Detection and prevention of flooding attack using SVM”, Proceedings in International Conference on Communication Systems and Network Technologies, pp.533 537,2013.
[15]WenchaoLi,PingYi,YueWu,LiPanandJianhuaLi,“A NewIntrusionDetectionSystemBasedonKNNClassification AlgorithminWirelessSensorNetwork”, publishedinJournal of Electrical and Computer Engineering,pp1 8,2014.
[16]PatelNJandJhaveriR H,“Detectingpacketdropping misbehavingnodesusingsupportvectormachine(SVM)in MANET”, published in International Journal of Computer Applications, vol.122,pp1 7,2015.
[17]ElwahshH,GamalM,SalamaAAandHenawyIM,“A novel approach for classifying MANETs attacks with a neutrosophicintelligentsystembasedongeneticalgorithm”, published in International journal of Security and Communication Networks,pp1 10,vol.3,2018.
[18] Shams E A and Rizaner A, “A novel support vector machine basedintrusiondetectionsystemformobileadhoc networks”, published in International Journal in Wireless Networks,vol.24pp.1821 1829,2018.
[19]SumaR,PremasudhaBGandRaviRV,Anovelmachine learning basedattackerdetectionsystemtosecurelocation aidedroutinginMANETs, publishedinInternationalJournal of Networking and Virtual Organisations,pp.17 41,vol.22, 2020.
[20] Damiani E, Vimercati S.D.C.D, “Samarati P A wowa based aggregation technique on trust values connected to metadata”, published in Electron Notes Theory Computer Science,pp.131 142,2006.
[21] Jinarajadasa G, Rupasinghe L and Murray I,“A reinforcementlearningapproachtoenhancethetrustlevel of MANETs”, proceedings in National information Technology,pp.1 7,2018.
[22] Jinarajadasa G M and Liyanage S R, “A trust based advanced machine learning approach for mobile ad hoc networksecurity”, proceedingsinInternationalConferenceon Advances in Computing and Technology, pp.1 7,2019.
[23]PopliR,JunejaV,GargKandGuptaDV,“FuzzyBased TrustEvaluationModelforEnhancingSecurityinMANETs” published in International Journal of Engineering and Advanced Technology,vol8,pp.506 510,2019.
[24]HuaLiang,YanhHongShangetalStudyonDTNRouting Protocol of Vehicle Ad Hoc Network Based on Machine Learning Volume2021, https://doi.org/10.1155/2021/7965093
[25] Dr. M. Duraipandian's performance evaluation of routingalgorithmforMANETbasedonthemachinelearning techniqueJournaloftrendsinComputerScienceandSmart technology,vol01,pp24 35,2019.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal
