International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072
SPECTRUM SHARING FOR 6G COMMUNICATION
Gangadurai.E 1 , Mohan Raj.G 2 , Pranesh .P.Srinivas3 , Duraichandiran.R4, Yuvarajan.S5
1Assistant Professor, Department of ECE, Velammal Engineering College, Chennai, Tamil Nadu 2,3,4,5 UG Student, Department of ECE, Velammal Engineering College, Chennai, Tamil Nadu ***
Abstract Ad hoc networks are temporary wireless networks that do not have a fixed infrastructure, also known as unstructured networks. Ad hoc networks are more vulnerable to attacks than wired networks due to some inconsistencies similar to those of the wireless media involved and the lack of centralized collaboration. The wormhole attack is the most severe of all other attacks. In this attack, aBushwalker captures packets atone location in the network and sends them over coverage to two other bushwalkers at a remote location using various methods such as: This gap between the two conspirators is virtual and is called a wormhole. A wormhole attack is possible when no host is involved in the bushwalker and all communications offer authenticity and confidentiality. The dynamic packet information can still be modified using colored methods. to change the outcome of a wormhole attack. Therefore, there is a needto develop secure means of detecting and reforesting wormholes to provide stronger protection in certain scripts such as battlegrounds that require a large amount of secure information. With this issue in mind, the proposed plan was drawn up. This paper discussestheproposedworkshoponwormholeattacksalong with available countermeasures in wireless ad hoc networks
1. INTRODUCTION
Ad hoc wireless networks are an excellent option for urgent operations, short term networks and vehicle communications.Themainsecuritychallengesin wireless adhocnetworksarethelackofcentralcontrolandthefact thateachnodehastoforwardpacketstootherbarriers.To avoidthis,adhocnetworksmustdealwithoutsidedamage and include internal hits (a node performing internal attacks includes nodes that allow non public information tobeintentionallyexposedtounauthorizedhits).Itcanact as a risk.) broadcasters participating in ad hoc networks, insecure operational areas, lack of infrastructure, lack of
centralauthority,lackoffederation,limitedresourcegaps, completely changing network topologies, resource limitations AND the lack of a clear line of defense has characteristics , makes them vulnerable. For a variety of security attacks. There are two types of videlicate attacks, non resistance and active attacks. In a non destructive attack, the attacker disrupts data on the network without altering it, while the proactive attack attempts to alter or destroythedata exchangedonthenetwork.Theseattacks can include wiretapping, communications tampering, or identitytheft.ForaBushwalkertobecapableoflaunching dangerous data attacks, one option is to spread a large number of key adversary barriers across the network and leverage cryptographic keys. A bushwacker can carry out this attack by targeting a specific controlling entity on the network. Some examples of the controls business are topology discovery, distributed positioning, routing, and node monitoring. A particularly severe control attack on wireless network routing functionality, known as a wormhole attack, has been introduced in ad hoc network environments. In a wormhole attack, a malicious node captures and "caps" packets from a location on the network. remotely in another malicious node. Lairs are configured in different ways, e.g. B. packet encapsulation, use of high power transmission or use of direct antennas. This allows tunneled packets to arrive sooner or with fewer hops than packets transmitted on normal multihop routes. That's what gives the impression that these two potholes offer the shortest route through them. A layer of wormholes can be really useful when used to slow down all packets, it puts the bushwalker in a critical position compared to other imperfections in the network that the bushwalker can exploit in a way that increases the speed of the network. can jeopardize safety. In a wormhole attack, two distant regions are directly connected by (malicious) bulges that appear to be neighbors but are actually far apart. A similar wormhole attack results in a wrong path. Therefore, a wormhole attack is one of the mostseriousdamageto an adhoc network asit canharm boththesenderandthereceiverbydroppingormodifying packets.Thisdocumentisstructuredasfollows.Wormhole attack methods, we include the results proposed in the literature as countermeasures to this attack. A final
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page1955
Keywords: Infrastructure less network, Direct Antennas, Wormhole, Stream Control Transmission Protocol (SCTP), AODV Routing Protocol, RSA Algorithm.International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072
proposed approach to silencing the wormhole and conclusion
subroutine. One of the principle worrying conditions in designingmulti pathshippingsubcastprotocolsisreceiver buffer blocking off issues as a result of escheval of order packetadvances.Thereceiverbufferpurchasestheout of order packets and distributes them to the mileage subqueryduetotheadventofalllackingpackets.Pathwar ofwordsinamulti pathreporttransfercanmotiveout of orderpacketstoberoutedviathereceiverbuffer.Asaend result,therecordssenderisthrottled,inflictingthegeneral output ofthe relationship todrop or possibly endupzero in cases. This miracle is seemed because the receiver buffer blocking off trouble. Receiver buffer blocking off is multiplied on Wi Fimultihopnetworksduetothe factthe unreliabilityofthedirectioncreatesuselesscomplexityfor deliverysubroutines.
Fig-1:SystemArchitecture
Oneofthefundamentalassaultsinwi fiadhocnetworksis the RREQ flood assault. In a flood tide assault, a vicious circle fills up all routing tables with its packets and subsequently communique among the supply and the vacationspotisparalyzed.Toguardinoppositiontoflood assault,amitigationschemeisproposedthatmakesuseof timetostayvaluestosignifyanddoawaywiththevicious knots that cataract the community. In the proposed scheme, there may be a restrict of RREQ which is exactly checked after a positive length in order that there may be no flood assault. The proposed scheme is emulated through QualNet and the end result indicates that the scheme prevents flood assault, reduces give up to give up detentionandwillincreaseoutput.
2.EXISTING SYSTEM
The Internet Engineering Assignment Pressure (IETF) defined Sluice Control Transmission Protocol (SCTP) as a today's causal shipping protocol in 2000. SCTP changed intofirstdesignedforpublicswitchedcellphonenetworks; Nevertheless, SCTP's specifically set up cappotential, inclusiveofmulti homing, makesitanappealing desireas a dependable multi course shipping subcast protocol in recordsnetworks.Multi homingisthecappotentialtotest componentpositiveIPaddressestohelp.SCTP CMTisone of the first prophs to include concurrent switch records over separate paths with inside the specific SCTP. SCTP makes use of the identical visitors manipulation mechanismasTCP.SCTPispredicatedattheTransmission Sequence Statistics (TSN) of packets for dependable records delivery; But, in SCTP the multi direction records transfer reasons out of order packet arrival on the receiver and problems with inside the universal overall performance degradation with inside the shipping
Harm:
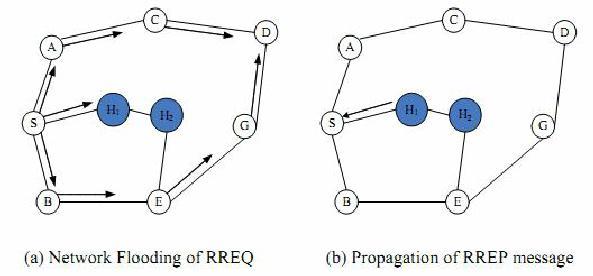
Unpredictabletopology,restrictedbandwidth,lackof records,restrictedsafety.
3.PROPOSED SYSTEM
In order to offer extra sturdy safety in positive scripts togetherwithbattlefield,theremaybeawanttobroadena few stable manner for wormhole discovery and afforestation wherein big scale stable records is required. Soouraimistocreateasturdyandstablemediumtosave you the perishable stuff as a result of a wormhole assault. Theessentialtargetsforthistechniqueare:
• To save you listening • To keep away from packet change • To offer authentication and confidentiality. • To lessen packetoverhead. •Tolessencomputation, the plan includes 4 parts: • Route discovery • Detection of malicious nodes • Secure records transmission • Route maintenance.
The writer makes use of hop rely evaluation in that the gadget first examines the hop rely values of all routes for records transmission. Ultimately we aimlessly transmit packets via stable routes. Using this technique the charge oftheusageofthecoursedirectionviathewormholemay be reduced.In proposed technique we're the usage ofthis hoprelyevaluation,wealsoaretheusageofcryptographic technique to provide stable records transmission. We are the usage of AODV routing protocol on this technique . It defines 3 kinds of dispatches, just like Route Requests (RREQs), Route Replies (RREPs), and Route Crimes (RERRs). These dispatches are reused as proven withinside the influx mapbelow. The gadget makesuse of clever sellers which are linked to all legal bumps and the
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page1956
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072
bumps provoke communique after the clever agent confirms the specified information included. Huh. The clever agent carries mystery records to test the authenticityof the knot. Thisgadget makesuse of RSAset ofrulesto providestablecommunique.Thepacketissplit into wide variety of corridors and those corridors are translatedtheusageofRSAanddecryptedonthereceiver side.
Thegain:
Warm hollow assault is prevented, AODV is a flat routing protocol, it does now no longer require any valuable administrative gadget to address the routing method, AODVprotocolisaloopunfastenedandavoidsthetrouble ofrelytoinfinity.AODVhasaexcessivebandwidthshare.
Theequation:
Assumption 1 Quantum Bit: In the context of classical communique, a binary fee of zero or 1 in keeping with bit is used to symbolize records. On the alternative hand, in quantum communique,a quantum bit,or qubit,includesa superpositionofeachlogicalvaluesontheidenticaltime.
|8i=a0|0i+a1|1i,(1)
wherein |eight represents a dimensional vector, wherein the coefficients a0 and a1 are the complicated numbers, andzeroand1arethe2logicalvalues.
4.METHODOLOGIES
4.1 Module
• Detecting/putting off cooperative black hollow assaults inMANET.
• Analysis of black hollow and grey hollow assault on RPAODVforMANET.
• Destination primarily based totally organization black hollowassaultdetectionforMANET.
• Impact of packet drop assault and determination on the generaloverallperformanceofAODVinMANET.
• Dynamic notion primarily based totally approach for mitigatingblackhollowassaultinMANET.
4.2 Module Description
Detecting/Removing Cooperative Black Hole Attack from MANET:
Thegadgetmaybeusedtolocateshorterandmoresecure routes and take a look at black hollow bumps in MANET through checking if there may be a big distinction among the series wide variety of the supply knot or the intermediateknotthattransferredthe RREPpacketlower back Or now no longer. Usually the primary course solution may be from the vicious knot with the better vacation spot series wide variety, that's saved withinside the RR desk due to the fact the primary course access additionally compares the primary vacation spot series wide variety with the supply knot series wide variety, if there may be an excessive amount of distinction. exists amongthem,whichmeanstheknotistheviciousknot, do awaywiththataccessfromtheRR deskincoherently.
Analysis of black hollow and grey hollow assault on RPAODV fromMANET:
Fig 2: 5GArchitecturevs6GArchitecture
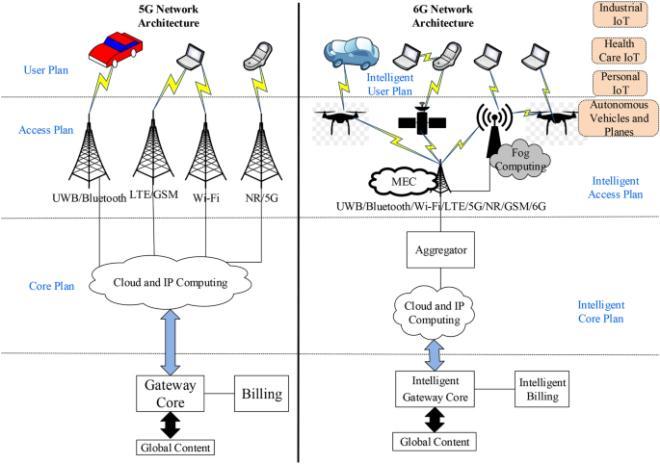
Figure2indicatesacomparativeevaluationamong5Gand 6G architectures. The velocity of 6G is anticipated to be a hundred instances quicker than 5G. 6G will offer a most recordschargeofonethousandGb/s.
Collaborating gives a style to locate chain of vicious knots that drop a bit packet. Instead of moving the full records commercial enterprise in a single go, divide the full commercial enterprise into smaller sized blocks. So that the vicious knot among the transmission of equal blocks may be detected and eliminated through icing the give up to give up checking. The supply knot sends a preamble communique to the vacation spot knot earlier than any blocks are transferred to warn approximately the incoming records block. Business float is covered. At the give up of the transmission, the vacation spot sends an
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page1957
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
acknowledgment through postalude communique containing the Not Known records packet. SourceNot makes use of this records to test whether or not records lossthroughouttransmissionisinsidetolerablelimits.
Destination primarily based totally organization black hollowassault detectionfromMANET:
TodescribeFrowardBumps(NRMDM).Thegadgetadopts the authentic fee of its K hop community and modifications the fee withinside the K hop community. This gadget facilitates to research gestures from one's neighbor flawlessly which facilitates in enhancing the cappotential to decide and accurate oneself from one's neighbor. NRMDM carries for modules. The tester module listensorvideodisplayunitswhilethenodesendsapacket to the incoming node, whether or not it caches the packet withinsidethe incoming node,or whether or not itcaches the packet concurrently. The Character System module consists of NOT ID, Direct Character, Circular Character and Alarm Count and Flag. The direction director module selectsthedirectionfromthesupplytothevacationspot.
Impact of Packet Drop Attacks and Solutions at the Overall Performance ofAODV inMANET:
Destination primarily based totally making plans includes 3phases.
1.Storethe.RREPpacketattheprecedingnode.
2.Checkthetwohopdistanceofthesuspectednode.
3.RejectionofRREPpacketstodiscoversuspiciousnodes.
The not unusualplace neighbor of the previous knot and the suspected knot tests the knot of hop distances for its cappotential to attain the vacation spot. To try this it first shops the RREP packet on the earlier knot and attaches a hop distance to the suspected knot. In this paper, while RREP communique responds to the previous knot, it have to additionally connect a hop distance knot of the answering knot (suspect knot) in any other case the previous knot will reject the RREP communique while no vicious knot is gift withinside the community. That is, the records packet effectively travels among the supply node tothevacationspotnode.
Fig-3: UsecaseDiagram
UsecaseexampleinUnifiedModelingLanguage(UML)isa formofbehavioralexampledescribedandcreatedthrough use case evaluation. Its reason is to provide a graphical evaluate of the capability assigned through a gadget in phrases of actors, their pretensions (represented as use cases), and any dependencies among the ones use cases. The essential reason of a use case example is to reveal which gadget responsibilities are carried out for which actors. The places of actors withinside the gadget may be depicted.
Dynamic notion primarily based totally approach to mitigate blackhollowassaultinMANET:
Presents the agree with version. Then every knot through masking its gesture withinside the community calculates the self belief fee and linkage situation for all its neighboring bumps. This agree with version is likewise includedintotheDSRprotocolthat'snotunusual placeon call for routing protocols utilized in MANET. The safety issues in an ad hoc community are structural and there may be a agree with primarily based totally federation safety. To describe the vicious knot, every knot keeps a union desk. The affiliation desk is used to save the affiliation nation of any knot with its acquaintances. The affiliationdeskincludes areasthatfirstdiscoveritswhole neighboring knot and extrade its affiliation function with thatoftheneighboringknot.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
Fig-4: Classdiagram
Therectangulardrawingisastaticexample.Itrepresentsa static view of an operation. Class illustrations are used now no longer most effective for imaging, describing and putting in place numerous components of a gadget, however additionally for generating an executable regulationofsoftwareprogramoperation.
1:sendingpackets 2:findingattacks
3:interferancecoordination 4:handovertechniques
sender dsdv receiver
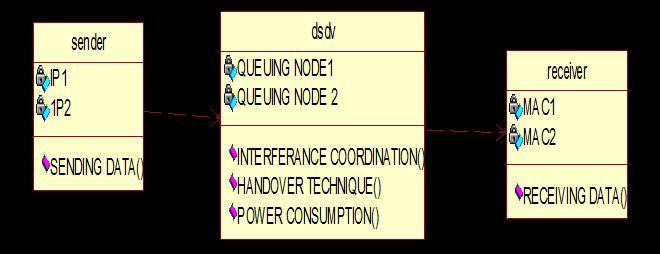
Fig 5: Collaboration diagram
A collaboration diagram, additionally referred to as a communique diagram, is an instance of the connections and relationships among software program items withinside the Unified Modeling Language (UML). These plates may be used to depict the dynamic gesture of a selectedusecaseandtooutlinetheapartofeveryobject.
Fig-6:
Flowdiagram
A records float diagram is a image device used to explicit gadget situations in a graphical form. DFD is likewise referred to as a "bubble map", which pursuits to explain gadget situations and offers with key metamorphoses encounteredingadgetlayout.
Hence DFD may be termed because the place to begin of the layout section which functionally decomposes the specsofthephrasesintothesmallestnationofdetail.
5.RESULTS AND DISCUSSION
5.1 Network Simulation and Simulator
Generally speaking, community simulators try to version actual globalnetworks.Thepinnacleconceptisifagadget may be modeled, the traits of the version also can be modified and matching effects may be anatomized. Since themethodofversionchangeisawholelotlessexpensive than that of complete actual time crime, loads of scripts may be made at low cost (relative to creating modifications to the actual community). The community simulator is constantly there. Still, community simulators
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
arenotperfect.Theycan'tversionalloftheinformationof the community flawlessly. Nevertheless, if modeled well, they may be near sufficient to provide the experimenter a significant expertise ofthecommunitybeneathcheck,and thewaymodificationswillhaveaneffectonitsoperation.
5.2 Simulation and Simulation
In the exploration discipline of laptop and dispatch networks, simulation is a beneficial style due to the fact community gestures may be modeled through computing trade among numerous community factors (they may be communityrealitiestogetherwith routers, bodilylinks, or networks). packet) the usage of first class formulas. They alsocanbeproducedthroughtouchdownsimplyornearly and gambling lower back experimental compliance from therealproductcommunity.Afteracquiringobservational records from simulation tests, community gestures and supported protocols also can be determined and anatomizedinasequenceofofflinechecktrials.Allsortsof environmental traits may be changed in a managed manner to evaluate how the community can tolerate beneath one of a kind parameter combos or one of a kind configuration situations. Another special function of community simulation this is really well worth noting is that simulation packages may be used with loads of operations and offerings to look at give up to give up or different factor to factor overall performance in a community . Network emulation, nevertheless, manner that the community beneath making plans is decomposed to evaluate its overall performance or to estimate the effect of potential modifications, or adaptations. The essential distinction among them is that a community impersonator manner that the identical give up gadget because the laptop may be linked to the emulator and couldfeaturepreciselyasthoughtheyhavebeenlinkedto a actual community. The key factor is that the task of a community impersonator is to emulate the community that connects the give up hosts, however now no longer the give up hosts themselves. Typical community emulation gear encompass NS2 which changed into a famous community simulator that may be used as a restricted capability emulator. In anomaly, a standard communityimpersonatorjustlikeWANsim.
5.3 SIMULATION RESULTS
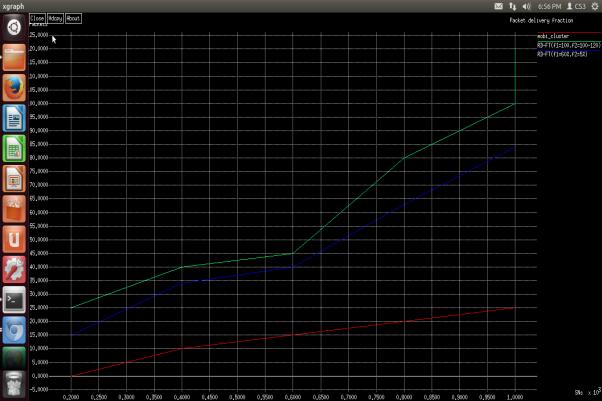
EFFICIENTTHROUGHPUTIDENTIFICATION
Efficient throughput identity differentiate among current andproposedgadget.
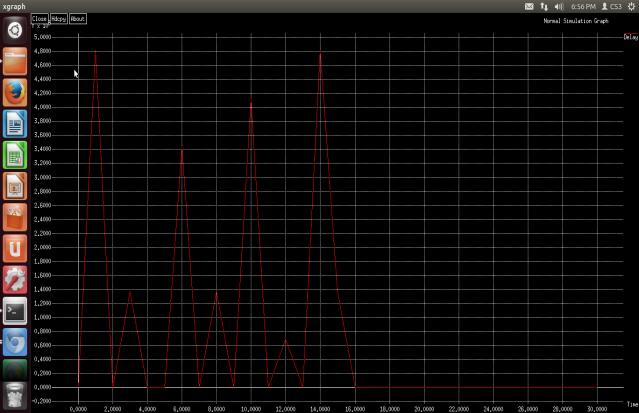
POWER LOSS IDENTIFICATION
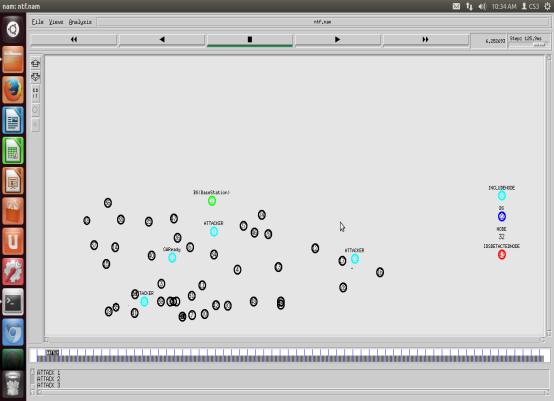
ATTACKER’S FINDING
Thegadgetmaybeusedtolocateshorterandmoresecure routes and take a look at black hollow bumps in MANET through checking if there may be a big distinction among the series wide variety of the supply knot or the
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
intermediateknotthattransferredthe RREPpacketlower back Or now no longer. Usually the primary course solution may be from the vicious knot with the better vacation spot series wide variety, that's saved withinside the RR desk due to the fact the primary course access additionally compares the primary vacation spot series wide variety with the supply knot series wide variety, if there may be an excessive amount of distinction. exists amongthem,whichmeanstheknotistheviciousknot, do awaywiththataccessfromtheRR deskincoherently.
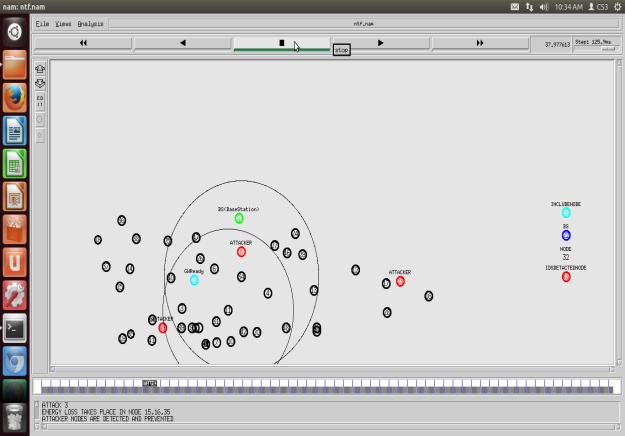
ATTACKER’S NODE IS DETECTED AND PREVENTED
the proposed end result primarily based totally on safety parameters together with packet outflow, reminiscence operationanddynamics.
REFERENCES
[1] J. Yick, B. Mukherjee, and D. Ghoshal, "Wireless Sensor Network Survey," Compute. Net., Vol. 52, no.12,pp.2292 2330,August2008.
[2] I. F. Akyildiz, W. Su, Y. Sankarasubramanium, and E. Cayirci, "A Survey on Sensor Networks," IEEE Commun.Mag.,Vol.40,no.8,pp.102 114,August 2002.
[3] I. Dietrich and F. Dressler, "On the Lifetime of Wireless Sensor Networks," ACM Trans. Censor Net.,Vol.5,no.1,February2009,Art.No.5.
[4] M. Perillo, Z. Cheng, and W. Heinzelmann, "On the problem of unbalanced load distribution in wireless sensor networks," in Proc. IEEE GLOBECOM Workshop Wireless Ad Hoc Sensor Network,December2004,pp.74 79.
Presents the agree with version. Then every knot through masking its gesture withinside the community calculates the self belief fee and linkage situation for all its neighboring bumps. This agree with version is likewise included into the DSR protocol that's not unusualplace on call for routing protocols utilized in MANET. The safety issues in an ad hoc community are structural and there may be a agree with primarily based totally federation safety. To describe the vicious knot, every knot keeps a union desk. The affiliation desk is used to save the affiliation nation of any knot with its acquaintances. The affiliationdeskincludes areasthatfirstdiscoveritswhole neighboring knot and extrade its affiliation function with thatoftheneighboringknot.
6. CONCLUSION
In this layout we've got stated AODV protocol and Black hollow assault in MANET. We have proposed a wonderful end result for a black hollow assault that may be carried out to the AODV protocol. The proposed gadget may be used to locate the vicious knot. Based at the self belief fee of the knot we outline which direction is quality ideal for routingthepacketandtheuntrustedknotmaybefluently eliminatedorignored.Asapieceinprogress,weintendto broaden simulations to dissect the overall performance of
[5] J. Lee and P. Mohapatra, "Analytical Modeling and Mitigation Techniques for the Energy Hole Problem in Sensor Networks," Pervasive Mobile Compute.J.,Vol.3,no.3,pp.233 254,June2007.
[6] X. Woo, G. Chen, and S.K. Das, "Avoiding Energy Holes in Wireless Sensor Networks with Non uniform Node Distribution," IEEE Trans. parallel distribution.Syst.,Vol.19,no.5,pp.710 720,May 2008.
[7] S. Katti, H. Rahul, W. Hu, D. Katabi, M. Maydard, and J. Croft, "XOR in the Air: Practical Wireless Network Coding," IEEE/ACM trans. Net., Vol. 16, no.3,pp.497 510,June2008.
[8] D. Loon, M. Maydard, R. Koeter, and M. Efros, "Further results on coding for reliable communication over packet networks," in Proceedings. International Symposium on Information Theory, 2005 (ISIT 2005), Adelaide, Australia,2005,pp.1848 1852.
[9] R. Koetter and M. M´edard, "An Algebraic Approach to Network Coding," IEEE/ACM Trans. Net.,Vol.11,pp.782 795,October2003.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056 Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072

[10] J. Sundararajan, D. Shah, M. Maydard, M. Mitzenmacher, and J. M. Barros, "Network Coding Meets TCP," in Proc. IEEE Infocomm, Toronto, Canada,April2009,pp.280 288.
[11] J. Of. Sundararajan, S. Jakubzak, M. Maydard, M. Mitzenmacher, and J. M. Barros, "Network Coding Meets TCP: Theory and Implementation," Proceedings of the IEEE, vol. 99, pp. 490 512, March2011.
[12] Barrow, Sebastian & Pasch, Christophe & Bonaventure, Olivier, "Multipath TCP: From Theory to Practice," in Networking 2011, 2011, pp.444 457.
[13] Fisk, Mike and Fang, Wu Chun, "Dynamic Right Sizing in TCP," in http://lib www. Lanal. gov/la pubs/00796247.PDF,2001.
[14] T. Dreibolz, M. Becke, E. Rathgeb, and M. Tucson, "Ontheuseofconcurrentmultipathtransfer over asymmetric paths," Global Telecommunications Conference (Globecom 2010), 2010 IEEE, December2010,pp1 in6.
[15] Ji Qing and L. Zeng, "Logistic Regression in Rare Events Data," Political Analysis, Vol. 9, pp. 137 163,2001.
[16] Mattignon,L.andLaurent,G.J.andLeFort Piat,N., "Improving reinforcement learning speed for robot control," Intelligent Robots and Systems, 2006 IEEE/RSJ International Conference on, pp. 3172 3177,2006.
[17] Y.Yuan,Z.Zhang,J.Lee,J.Shi,J.Zhou,G.Fang,and E. Dutkiewicz, "Extension of SCTP to Concurrent Multi Path Transfer with Parallel Substreams," 2010 IEEE Wireless Communications and NetworkingConference,April2010,pp.1 6.
[18] P. Natarajan, N. Akise, PD. Amer, JR. Iyengar, and R. Stewart, Networking 2008 Ad hoc and Censored Networks, Wireless Networks, Next Generation Internet: 7th International IFIP TC6 Networking Conference Singapore, May 5 9, 2008 Proceedings. Berlin, Heidelberg: Springer Berlin Heidelberg, 2008, ch. Concurrent Multipath TransferUsingSCTPMultihoming:Introductionto PotentiallyFailedDestinationState,pp.727 734.
[19] B. Horan, Practical Raspberry Pi, 1st ed.Berkley, CA, USA: Apres, 2013. [online]. Available: http://daz pi.com/ebooks/
[20] J. Sundararajan, D. Shah, M. Maydard, and P. Sadeghi, "Feedback Based Online Network Coding,"November2011.
[21] J. Sundararajan, D. Shah, and M. Maydard, "Online Network Coding for Optimal Throughput and Delay The Three Receiver Case," Information Theory and its Applications, 2008. ISITA 2008. International Symposium, December 2008 , pp. 1 6.
[22] J. Barros, R. Costa, D. Munaretto, and J. Widmer, "Effective Delay Control in Online Network Coding," in INFOCOM 2009, IEEE, April 2009, pp. 208 216.
[23] H. Balakrishnan, V. Padmanabhan, S. Seshan, and R. Katz, "Comparison of Mechanisms for ImprovingTCPPerformanceoverWirelessLinks," OnNetworking,IEEE/ACMTransactions,1997.
