International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
1 , Abhijith G
2 , Adhokshaja N R3 , Ajay Chinnaswamy4 , Aravinda Kumar R V5
R1HOD, Department of ECE, Global Academy of Technology, Bangalore, India 2345Student, ECE, Global Academy of Technology, Bangalore, India ***
Abstract Elections are important in our democratic society because they let the people decide who will lead their government. In a democracy like India, voting is an essential way for residents to exercise their right to vote. Voters frequently use polling places to cast their ballots. Electronic voting machines are being used to cast ballots more frequently as technology develops. This study proposes a novel methodology with a very secure mechanism. IoT, biometrics, and Aadhar make up its main parts. With biometric fingerprint and face recognition for security and IOT for accurate results, Aadhar ID is a unique card for each individual. The proposed system features secure voting, automatic vote counting, and a highly secure data handling technique.
Key Words: Face recognition, fingerprint recognition, EVM, LBPH, Aadhar ID, IoT, Haarcascade.
Indiahasaparliamentarysystemwithadivisionofpower between the federal government and the states, as per its constitution.Electionsinthiscountryhaveabigimpacton how the government is run. A candidate for president is chosen using this procedure. The Constitution's requirementsledtothecreationofIndia'sfederal agency, theElectionCommission,whichisinchargeofsupervising andmanagingall electionsinthenation. Thisagencyis in responsibility of making sure that elections are free, fair, andunbiased. There are5 typesof electionsconducted in India 1. MembersoftheParliamentinLokSabhaandRajya Sabha
the public because picking a candidate for office is important. Asa result,theEVMneedsto be builtwiththe utmost security and safety. Voting systems, ballots, punch cards, electronic voting, blockchain there are many technologies. Network security, microcontrollers, GSM modules, and i voting are all utilised. However, there are still many issues with EVM in use today. So this study describes a biometric face and fingerprint recognition protected EVM technology employing a special card with IoT. Voters cannot repeat their votes since biometric face and fingerprint recognition are important for identifying individuals.AadharistheuniqueIDnumberforeveryone
5. By election is held when a seat holder of a particular constituent dies, resigns, or is disqualified.
This paper examines safe voting practises and how biometrics could enhance elections. The accuracy of the electronic voting system's results has earned the trust of
Fig 1: DataforusingEVMpast20years.
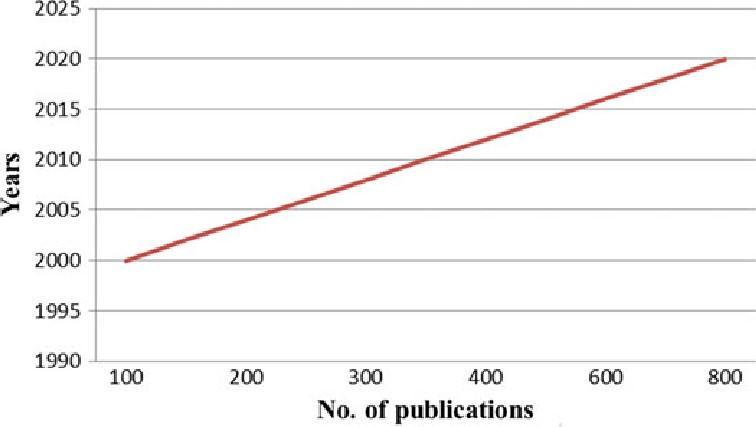
DataforusingthetechnologyinEVMfromthelast20years in the research community were increasing as shown in Fig.1
[1]S.Kumar,S.Singh,J.Kumar,Livedetectionoffaceusing machine learning with the multi feature method. Face identification and detection are crucial areas of study in digital image processing (DIP). These algorithms employ two basic strategies: holistic feature recognition, in which the image data is evaluated as a whole without isolating variouspartsofaface,andlocalfeaturedetectionbasedon the geometric model of the human face. Finding human faces independent of their pose, orientation, or imaging situationisthemainissueinfeature basedfacialdetection.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
[2]B. Shahzad, J.Crowcroft,Trustworthy electronic voting using adjusted blockchain technology. People must maintain their confidence in the vote and the voting process because public faith in democracies is rising. The votingsystemoriginatedasameansofassistingcitizensin electing their representatives, who subsequently form the governments, as a result of growing confidence in democratic institutions. The fundamental functionality of this system is to enable electronic voting, which necessitates aspects like privacy, security, anonymity, and verifiability. To address these problems, the underlying technology must be chosen carefully. It has been determined that Blockchain technology effectively addresses each of these issues. Blockchain technology correctedflawsinthewayelectionsareconductednowby making the voting process transparent and easy to use, preventing fraudulent voting, bolstering data protection, andverifyingtheresultsoftheelection.
[3]R.Rezwan,A.Rahman,Biometricallysecuredelectronic votingmachine.Inthisproject,anewvotingsystembased onanelectronicvotingmachineisproposedinlightofthe drawbacks of the prior voting system (EVM). The voters' fingerprints will be used to provide biometric security, which is another element of this system. Voting systems should be simple to authenticate and verify, have a high accuracyrate,andbeveryreliable.Additionally,thesystem must be original and cost effective. An enhanced voting mechanism is created that makes use of an Aadhaar card, althoughitiscomplicatedandonline.Theonlinemethodis never completely risk free. According to this material, the suggested approach will use a fingerprint scanner to identifyeachvoterbasedontheirfingerprint Itcandetect if someone is a registered voter or not and it will deny if someonetriestocastasecondvote.
[4] Himanshu, G.N. Pandey, Online voting system for India basedonAADHAARID.Thispapermakesthefirstproposal for an online voting system for the elections in India. The suggested methodology offers higher security because the voter'shigh securitypasswordisverifiedbeforethevoteis recorded in the Election Commission of India's primary database. The model's added feature allows the voter to verifythattherightcandidateorpartyreceivedtheirvote. Inthissystem,avoterhastheoptiontocastaballotfroma placeotherthantheonedesignatedforthemorfromtheir favourite site. The counting of the votes will be done automatically under the proposed approach, saving a significant amount of time and allowing the Election CommissionerofIndiatodeclaretheresultsquickly.
[5] S. Anandaraj, R. Anish, P.V. Devakumar, Secured electronic voting machine using biometric. The project suggests and puts into practise a quick and secure techniqueforcollectingvotesusingbiometrics.Technology has changed so much, and as a result, voting has seen several developments. The improvisations reduce the amount of time needed to announce the outcome while
boostingthemodel'sflexibility,security,dependability,and scalability.Thegovernmentdatabasealreadycontainedthe fingerprint module. Therefore, our initiative offers the greatest way to prevent fraudulent votes. The computer was connected to the electronic voting machine. The computer has a complete database list of everyonewho is eligible to vote. The corresponding person's identify was removedforeachpoll.Falsevotingis thereforeprevented. There is a touch screen, so it is user friendly. A printer is alsousedtoprovideaconfirmationsheetforthevoterwho pollstheauthenticatedvote.
[6] Srikrishna Swetha, S. Kumar, A study on smart electronics voting machine using face recognition and Aadhar verification with IoT. It is an electronic voting machine even though the voting machine is a mechanical device that is most frequently created by an electronic material. A very secure voting procedure using face recognition technology is proposed. It was created with a variety of goals in mind, including long term use, security needs, high voting efficiency and accuracy, among many more. The majority of voters might find this to be useful. Another name for this electronic device is e voting. It also covers the use of some of the other network kinds, includingprivatecomputernetworkuseandmobilephone usage.
[7] R.P. Jacobi, F. Trindade, J.P.A. deCarvalho, R. Cantanhede, JPEG decoding in an electronic voting machine, in IEEE 13th Symposium on Integrated Circuits and Systems Design (2000).The Joint Photograph Experts Group established JPEG as a standard for image compression [4, IO]. Due to its lossy nature, which causes data to be wasted during the compression and decompression processes, JPEG performs better with natural photos. The lack of visual information is partially made up for in natural imagery. the visual content. Image informationisnotlostwhenusingotherJPEGformats.The EVM uses the lossy JPEG standard, where the amount of information lost is determined by the compression factor. Images with high compression ratios are subpar. Almost flawlessphotosareproducedbysmallcompressratios,but littlememoryissaved.
[8]S.Lavanya,Trustedsecureelectronicvotingmachine.In this paper, a secure study of electronic voting machines is analyzed. The electronic device is susceptible to some major threats, according to an analysis. For instance, maliciouscodeonamachinemaystealvotescovertlyifan attacker gained physical access to it or its removable memory card for even a little period of time. Additionally, during regular election activities, a hacker could produce harmful code that spreads silently and automatically from machine to machine. With little to no chance of detection, malicious software operating on a single voting machine canstealvotes.Thiselectronicdeviceiscapableoffiguring out the theft attack. Whoever has directaccess toa voting machine or a memory card that will afterwards be loaded
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

into a machine. In practice, poll workers and others often haveunsupervisedaccesstothemachines.
[9] M. Karim, S. Khan, An electronic voting system with biometrics is being proposed. The Bangladesh Election Commission (EC) still conducts elections using a manual system in this contemporary era of technology. In this work, we have created an automated biometric voting system with a user friendly interface and a built in database system that contains data on every voter. At the conclusion of the voting process, votes will automatically be counted, and the outcome will be generated centrally more quickly. As a result, the suggested system will enhance the management of Bangladesh's elections by ending fraud and corruption, assuring security, openness, fairness, and correctness, and maintaining backup voting processrecords.
The literature review revealed some significant technical issues with the voting procedure. The voting procedure cannotbeaccuratelyandsecurelycountedbyhand.
Thevotingprocesssuffersgreatlywhenvotesaremissed. In the 2019 elections in India, approximately 21 billion individualsdidnotcasta ballot,andonlya selectfewhad the opportunity to cast two votes in some locations. This occurred as a result of incorrect voter information being registered and a lack of valid identification. Out of the 3,16,671entriesinthevoterslist,theElectionCommission wasonlyable todetect38,586double entries, ithas been reported to the Kerala high court. One of the main issues withtheIndianelectoralprocessispluralvoting.
• The primary goals of this initiative are to eliminate manual vote counting, stop votes from going uncounted, andstopvotersfromusingmultipleballots.
•Ensuringthatavoterisverifiedindetailbeforecastinga ballot.
• Preventunauthorizedaccesstothevotingprocess.
•Theentirevotingprocessshouldbedigitalizedtoreduce corruption.
The two steps of the suggested approach are the registrationofvoterinformationandthevotingprocedure, as depicted in Fig. 4. The Raspberry Pi3B+, a visual desktop sharing system of PI, along with a fingerprint reader,webcam,votingbuttons,adisplay,andaconnecting cable, make up the hardware components. Python version 3.5 and (SSH) Secure shell were the software components
employed. We presented a novel methodology for voting registration, biometric voting, counting issues, and result declaration based on the literature review mentioned above.Intheproposedmethodology,a webcamwithgood quality is used to build a real time face detector and achieve better accuracy. Monitor/screen is used for enteringAadharnumbers,facerecognition,andidentifying the authorized & unauthorized voters with automatic countingofvotes.WehaveusedtheLBPHalgorithmforthe training of images and testing of images. The hardware consists of monitor, voting buttons, connecting cable and wires, and a webcam. VNC viewer works by connectingto the server with an IP address using a username and password.
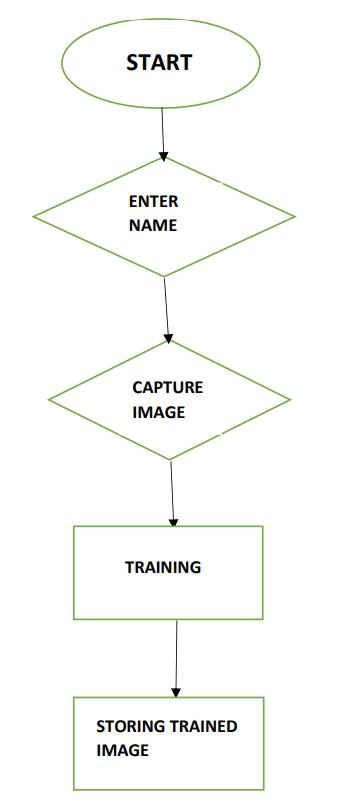
Algorithm(Fig.2)
Step1 EnterIDnumber
Step2 Capturingimagesoftheface Step3 Capturedsuccessfully
Step4 ImagesarestoredwithIDsinhaarcascadepath.
Step5 Successfullytrained Step6 Registrationcompleted
Fig 2:Faceregistrationflowchart
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
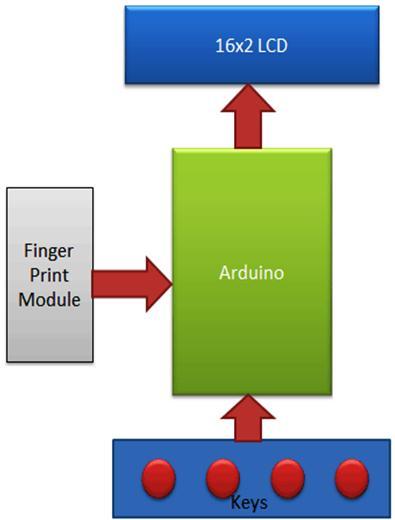
In our project, we've employed a Fingerprint Sensor Module (R307) to collect thumb or fingerprint impressions for system input. In this case, the enrol/back, delete/OK, up, and down buttons are all push buttons. There are two features on every key. New finger imprints areenteredintothesystemandthebackfunctionusingthe enrolkey.Toenrolafreshfinger,theusermustfirstpress the enrol key. The LCD will then ask for the ID orlocation where the user want to store the fingerprint output. The usercannowpresstheenrolkeyoncemoretoturnaround iftheydecidetheydonotwanttomoveonatthismoment (this time enrol key behave as the Back key).This means enrollkeyhasbothenrollmentandbackfunctions.DEL/OK keyalsohasthesamedoublefunctionwhenauserenrolls a new finger then he/she need to select finger ID or Location by using another two key namely UP/MATCH AND DOWN/MATCH (which also has a double function) now user needs to press DEL/OK key (this time this key behaves like OK) to proceed with selected ID or Location. UP/DOWN keys also support the Fingerprint match function.
With the use of a push button or key, the user must enrol a finger. The user must first press the ENROLL key before the LCD prompts them to enter thelocationandID where the finger will be saved. Thus, using the UP/DOWN keys, the user must now enter the ID (Location). After choosingLocation/ID,theusermustpresstheOKkey(DEL key). The LCD will now prompt you to place your finger over the fingerprint reader. The user must now place his finger on the fingerprint reader. The LCD will prompt you to take your finger out of the fingerprint module before asking you to put it back in. The user must now place his finger over the fingerprint reader once more.Now user needs to put his finger again over the fingerprint module. Now fingerprint module takes an image and converts it
into templates and stores it by selected ID into the fingerprintmodule'smemory.
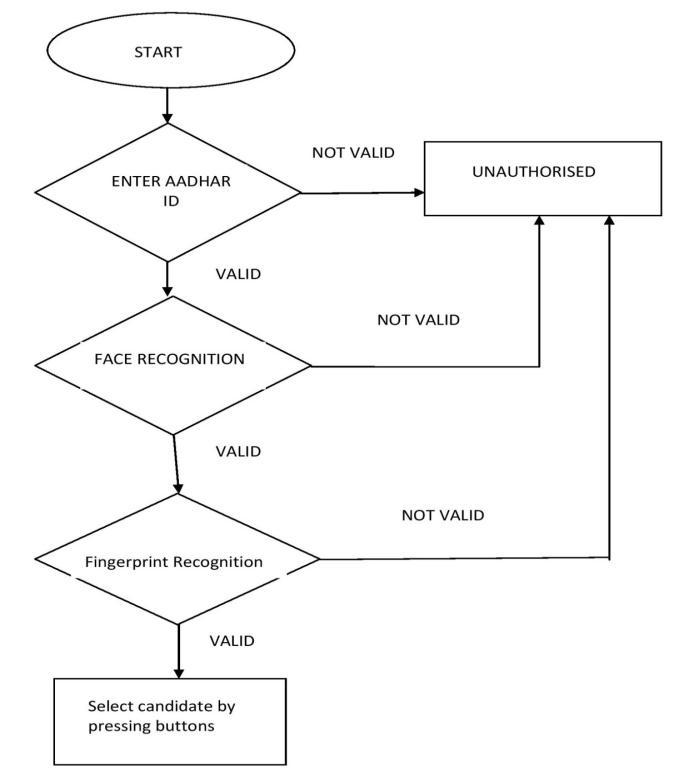
Algorithm(Fig.4)
First,enteryourAadharnumber.
Step2:Showingwhetheranythingisapprovedornot.
Step3:Ifpermitted,openthewebcamrightaway.
Step4:Livefacecaptureandrecognition.
Step 5: Display approved or unauthorized using live data andtrainedimages.
Step6:Ifthevoterisapproved,thefingerprintrecognition processwillbegin;else,thevotewillnotbecounted.
Step 7: If permitted, voting is completed after choosing a button.
Step8:Resultsdisplay.
Fig 4: Votingprocessflowchart.
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072

Fig 5: LCDresults.

The above figure Fig.5 shows that the voting process is started,bydisplayingontheLCDas"VOTINGMACHINEBY FINGERPRINT".
Fig -6: LCDresults.
The above figure Fig.6 explains that a voter is an "AUTHORIZED PERSON" to cast a vote. A person has considered an authorized voter only if his Aadhar id is valid,hisfaceisrecognizedandhisfingerprintismatched.
The below figure Fig.7 explains that a voter to "PLACE A VOTE". This is displayed after face recognition and fingerprint recognition are valid. We have added three different parties Party1, Party2, and Party3. A voter can placeavotebypressingthepushbuttons.
Fig 7: LCDresults.



Fig.8 shows the final resultin LCD as"VOTESUBMITTED" afteravotercasthisvoteforanyoneoftheparties.
Fig -8: LCDresults.
Fig.9 shows that a voter’s face is recognized and he is an authorizedpersontovote.
Fig 9: Authorizedface.
Elections in our nation are still not conducted in a very secure manner to ensure fair voting. This suggested approach can include face recognition, better registration procedures, automatic vote counting, storage and transmission of results, and result declaration. Therefore, by doing this, we can prevent double voting, inaccurate registration,andfakebiometricsforbetterelectionsanda betternation.
[1] S. Kumar, S. Singh, J. Kumar, “Live detection of face using machine learning with multi feature method” , in Wireless Personal Communication Springer Journal (SCI) Published https://doi.org/10.1007/s11277 018 5913 0

[2] B. Shahzad, J. Crowcroft, “Trustworthy electronic voting using adjusted blockchain technology”. IEEE Access 7,24477 24488(2019).
[3] R. Rezwan, A. Rahman, “Biometrically secured electronic voting machine”, in IEEE Region 10HumanitarianTechnologyConference(2017).
[4] Himanshu, G.N. Pandey, “Online voting system for India based on AADHAAR ID”, in 11th International Conference on ICT and Knowledge Engineering (ICT&KE)(2013).
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
[5] S. Anandaraj, R. Anish, P.V. Devakumar, “Secured electronic voting machine using biometric”, in IEEE International Conference on Innovations in Information,EmbeddedandCommunicationSystems (ICIIECS)(2015).
[6] K. Srikrishna Swetha, S. Kumar, “A study on smart electronicsvotingmachineusingfacerecognitionand Aadhar verification with IoT”, in 7th International Conference on Innovations in Electronics & Communication Engineering (ICIECE 2018), vol. 65,(Springer,2018).
[7] R.P. Jacobi, F. Trindade, J.P.A. de Carvalho, R. Cantanhede, “JPEG decoding in an electronic voting machine”, in IEEE 13th Symposium on Integrated CircuitsandSystemsDesign(2000).
[8] S. Lavanya, “Trusted secure electronic voting machine”, in International Conference on Nanoscience,Engineering,andTechnology(2011).
[9] D. Karima, Pr. T. Victor, Dr. R. Faycal. “An improved electronic voting machine using a microcontroller and a smart card”, in 9th International Design and TestSymposium(IEEE,2014).
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal
