International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
2
1,2Reserach Student, Department of Computer Science and Engineering 1,2Sanjay Ghodawat University, Kolhapur, Maharashtra, India. ***
Abstract PrivateandpublichybridcloudsareaConcept thatisfrequentlydebatedinthecurrenttimes.Becausemost datamustbemaintainedon premisehardwareandcannot bemigratedtoanypubliccloud,thehybridsolutionisthe only method for major corporations and governmental institutions to participate in cloud computing innovation. Eveniftherearenolegallimitsinsidethehybridsituations, businesses are concerned about information leakage or otherconstraintsthatmaydevelopwhentheydonothave control over their data. The use of outplacement infrastructure,aboutwhichtheusershouldnotbother,orof services in the areas of machine learning, business intelligence,streamanalytics,andotherSaaSfeatures,onthe other hand, is highly tempting. From a cost savings perspective,migratingtocloudsolutionsisaveryattractive idea. However, some cloud service functionalities that cannotbecombinedwithlocal,on premiseserversprovidea challenge for public cloud solutions. Recent studies have tendedtoconcentratesolelyonthetopicofprivateorpublic clouds.
This study is concerned with security in hybrid clouds. It exploresnumeroussecuritymeasuresandchallengeswithin the context of IaaS and SaaS, as well as various authentication and security concepts and security related difficulties.
Key Words: Hybrid Cloud, Cloud Security, Security Challenges,ThreatsinCloudToday,94percentoffirmsutilizesomesortofcloud,with 58percentadoptingahybridcloudarchitecture.Theterm "hybrid cloud" refers to an IT infrastructure that includes somelevelofworkloadmigration,andmanagementacross twoormoreconnectedbutindependentenvironments,such as physical servers, virtualized, private cloud, and public cloud. We can execute applications in any of the interconnectedenvironments,transferitacrossthem,and use resources from those environments interchangeably usingahybridcloudarchitecture.
Although implementing IaaS through a hybrid architecture allows a flexible, on demand method for meeting organizational computing needs, there are still severaldifficultiesthatneedtoberesolved.Securityisthe main barrier to IaaS adoption in the company. Due to the
division of resources into different clouds, software complexity and configuration increase as an organization migratesitsresourcestohybridclouds.Inadditiontothis complexity, there are multiple security concerns, such as controlling the communication link between the two sites when delivering IT infrastructure from the cloud to businesses, creating firewall rules that only permit authorizedtrafficfromthecloud,andincompatiblenetwork policies.Securityisamajorconcernnomatterwhereyouare in your hybrid cloud journey. In fact, 81 percent of businessesidentifycloudsecurityasathreat.Hybridcloud security vulnerabilities often manifest as loss of resource monitoringandcontrol,whichmightincludeunauthorized usage of the public cloud, a lack of resource visibility, insufficientchangecontrol,poorconfigurationmanagement, andineffectiveaccesscontrols.Theseholescanbeexploited byunauthorizedindividualstohaveaccesstoconfidential informationandcorporateresources.Securitylapsescanbe expensive. A data breach typically costs US$3.92 million, withlostrevenueaccountingfor36.2%ofthisexpense.
Therestofthepaperisorganizedasfollows.InSection2, we provide an overview on the different service models beingusedandcloudarchitectureswhichcanbedeployed accordingtotheenterpriserequirements.Section3presents the challenges involved while deploying hybrid cloud architecture for enterprise needs, Section 4 describes the solutionswhichhelpinenterprisestooperateefficientlyand securely in hybrid environment. Section 5 discusses on differences in the mentioned solutions. We conclude and givefutureworkinSection5andSection4respectively.
Thehybridcloudisonesystemthatcombinesdifferentcloud environments,typicallyprivateandpublic.Ahybridcloudis usually supported by software that helps manage and automate workloads, allowing them to operate seamlessly across on premise and public cloud environments. The concept of hybrid cloud is closely related to multi cloud, which is the combination of two or more public clouds operatedbydifferentvendors.Thearchitectureofahybrid cloudtypicallyincludesanInfrastructure as a Service(IaaS) platform.ThemainIaaSplatformsareAmazonWebServices (AWS),MicrosoftAzureandGoogleCloudplatform.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
Currently,therearemoreservicemodelsavailablethanthe four fundamental ones that helped establish cloud computing.Organizationscontinuetodevelopnewconcepts thatmaybeofferedasa service.However,NIST [National Institute of Standards and Technology] states that the followingarethefundamentalfour(withoutSECaaS)
• SaaS SoftwareasaService ApplicationLayer
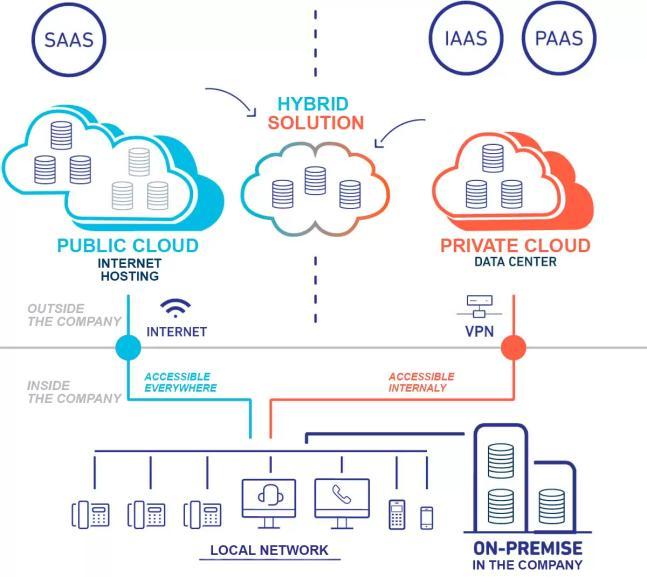
• IaaS InfrastructureasaService HardwareLayer
• PaaS PlatformasaService MiddlewareLayer
• DaaS DataasaService,orDatabaseasaService
• SECaaS SecurityasaService
It is necessary to discuss the fundamental cloud service deployment capabilities of each architecture right away. Fourfundamentaltypesofcloudcomputingaredefinedby NIST[NationalInstituteofStandardsandTechnology]:
1. Public Cloudinfrastructureisownedbyaservice provideranditsentireadministration.
2. Private Infrastructureisownedbyacompanyor hostedbyaprovider,butitisalwaysdevelopedand Managedbythecustomerorthirdparties.
3. Community Cloud infrastructure is shared by several companies / organizations and it is managedbyoneofthecompaniesorathirdparty.
4. Hybrid This model is the interconnection of previousmodels,combinesthem,butalsocreatesa customentity
Beyondthetechnicalaspectsthatareinvolved,itrequiresan in depth understanding of security, governance, and end user requirements. Following are a few essential considerationsforsuccessfulhybridcloudmanagement.
Figure1[HybridCloudArchitecture]
Source:https://www.padok.fr/
Security and governance We need to prepare securityforyourhybridcloudfromthebeginning with today's DevSecOps attitude. Utilize solutions likeIdentityandAccessManagement(IaM)tobuild uniformsecurityinterfacesacrossenvironmentsas youdeterminethesecurityneedsforon premises andcloudenvironments.Verifythatperformanceis notimpactedbysecurityneedslikeencryption
Workload inventory learn about the workloads thatwillbeusedinthehybridcloudandhowthey willmakeuseofbothon premisesandpubliccloud resources. Understand the importance of apps to users, anticipated loads, data needs, integrations, networking, and everything else that can affect availability or performance by mapping out the applications.
Service level agreements (SLA) Due to the high sensitivity of hybrid clouds to performance, SLAs areacrucialcomponentofplanning.Toeasilyfulfil userperformanceexpectations,buildpublic private interfaces,datatransferpipelines,andlatencies.To achievehighavailabilityandbeabletomeetuptime needs, use public and private cloud resources effectively.
Visibility across multiple cloud environments
Usingdashboardsorinterfacesforeveryindividual cloudenvironmentmaygetcomplexratherquick. Utilize a device or technology that can gather information from both private and public cloud systemsandpresentitallonasinglepieceofglass. Management will be lot simpler if everything is visible in one location and there is a consistent systemformeasurementsandreporting.
The majority of corporate apps available today are multi tiered and frequently comprise several different parts. Businessesmaydeploytheirappspartiallyon premisesand partiallyinthecloudduetohybridarchitecture.Sincedatais often the backbone of businesses, it is crucial to manage access permissions and safeguard it. Any data security breach will not be tolerated, hence several methods have beendevelopedtosafeguardsuchdataandinformation.In additiontothis,businessesmustadheretoanumberoflaws to ensure data governance. Enterprises will lose some
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

controlovertheirowndatasetbyputtingthedataintothe cloud.Toensurethesecurityoftheirdata,theymustrelyon theserviceproviders.
management capabilities and employing technologies like IDS/IPStodetectharmfultraffic.
The Distributed Denial of Service (DDoS), one of the most dangerous kind of cyber attack, is a crucial problem that oftenoriginatesfromseveralsourcestotargetasingleplace. These assaults often provide a high risk factor since they haveseveralorigins,makingitdifficulttoidentifyanddetect them.
Maintaining a stringent monitoring system that can track inputandoutflowisnecessarytodealwiththis.Inaperfect world,thissystemwouldbescalable,quick,andcapableof defendingagainstmulti vectorassaults.
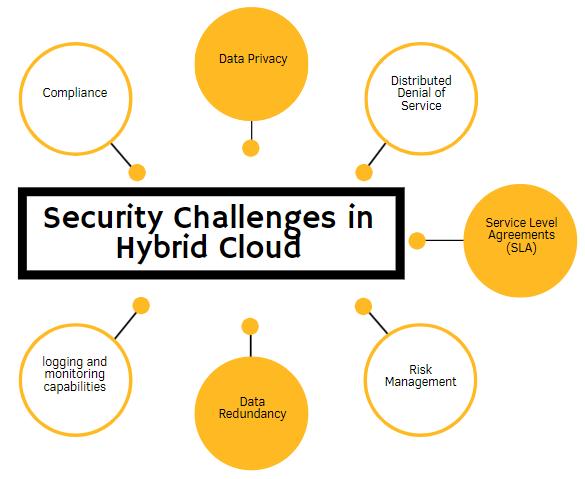
Datatravelsbetweenhighlysecureprivatecloudnetworks and less secure public cloud networks in a hybrid cloud computing approach. This frequently puts data and compliance at risk. Additionally, the introduction of data securitystandardslikeGDPRhasraisedawarenessoflegal andcompliancerequirements.Therefore,companiesmust goaboveandbeyondtoguaranteethatcomplianceneedsare satisfied. Make that the data transmission mechanism complies with legal requirements and that the public and privatecloudnetworksbothcomplywithindustrystandards likeGDPR.
Thisisanothersignificantsecurityissuethatahybridcloud approachmayencounter.Datatransferbetweenpublicand private clouds must be flexible when using hybrid clouds. Your data may be vulnerable to hacker assaults in these circumstances, violating the organization's data privacy policies.
During security breach incidents, measures like endpoint verificationprotocol,astrongVPN,andastrongencryption policymayencryptandsafeguardyourdata.
To safeguard the organization's secrets from possible dangers, appropriate risk management and preventative safety measures must be implemented in light of the vulnerabilitiesandthreats.Thismayentailmaintainingalog monitoringsystemwithcutting edgefirewallandsecurity
In IaaS, there is a requirement to investigate the solution thataidsinofferingsafetransferofITinfrastructureservices from cloud to corporate internal network since the cloud gives the whole computing and storage capability as a service to the companies and end users. Encryption and providing safe transmission are crucial techniques for defendingbusinessdatafromintruders.
SinceAmazondevelopedthissolution,itisconsideredthat thepubliccloudusedisAmazonWebServices.Organizations mayuseAmazonVirtualPrivateCloud(VPC)tobuildtheir own virtual cloud inside of Amazon Public Cloud, hosting their IT infrastructure within a specified subnet. A VPN connection is provided by VPC between business IT infrastructureandthebusinessvirtualcloud(presentinside public cloud). To prevent data eavesdropping and manipulation,theVPNconnectionuseIPsectunnelmode.All security measures put in place for organizations may be extendedtovirtualclouds.Itisevidentfromfigure3thatthe businesshasbuiltitsownvirtualcloudcalledVPCinsidean Amazonpubliccloud.AVPNconnectionismadebetweena corporatenetworkandtheAmazonpubliccloudthroughthe internet with the assistance of the VPN gateway and the customergateway.
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page152
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
need to worry about altering the network, changing the securityandaccessconfigurations.
Enterprisecustomersshouldbeabletoaccessdataasifthey were using local workstations in order to give them a smoothcommunicationexperiencewhenusingthecloud. To increasecommunicationspeed,WideAreaNetwork(WAN) performanceoptimizationiscrucial.
Figure3[AmazonVPC]
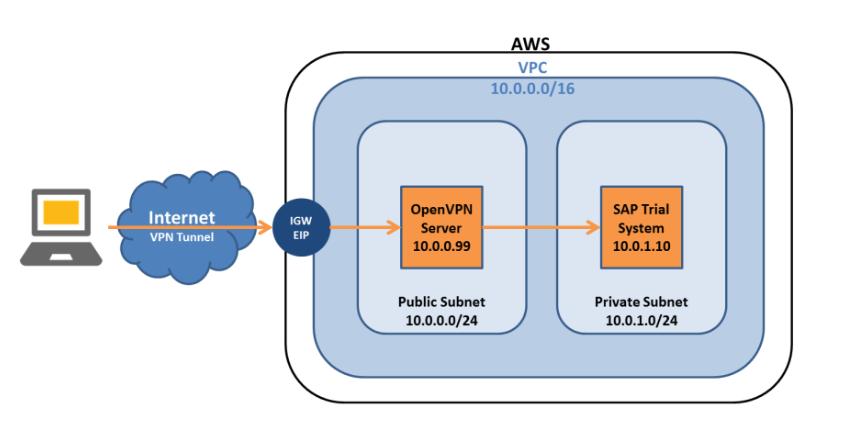
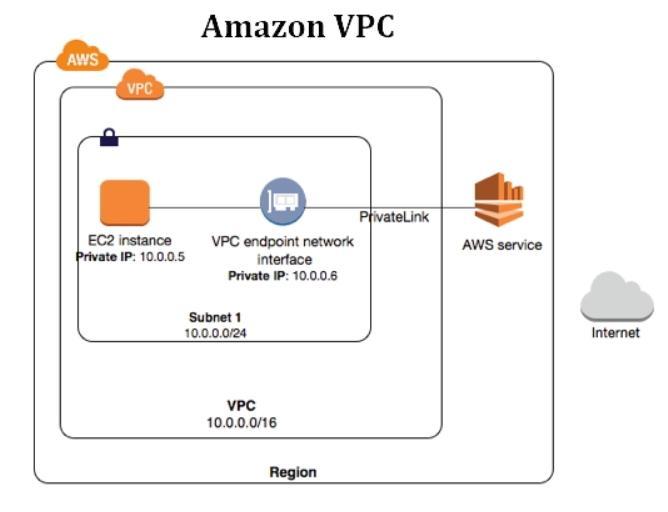
Source:https://www.testpreptraining.com/
This open source VPN technology enables networks to exchangedata securely.The data inthiscaseis encrypted using an OpenSSL based system. For the flow of data BetweencompanyITinfrastructureandthecloud,OpenVPN creates a secure tunnel. OpenSSH is the protocol used to encrypttunnelcommunication.OpenVPNusestheSSL/TLS protocol to offer a secure network. Before establishing a secure connection, it supports a variety of authentication methods,includingcertificateverification,smartcardusage, username/passwordauthentication,firewallaccesscontrol settings,andmore.
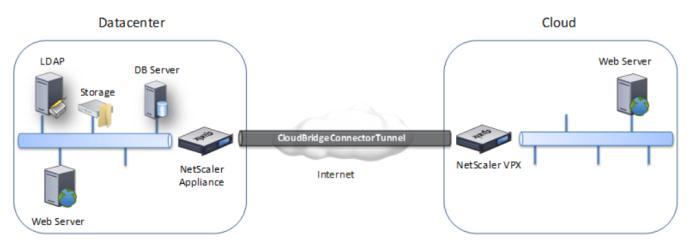
Figure5[OpenCitrixinCloudArchitecture]
Source:https://docs.citrix.com/
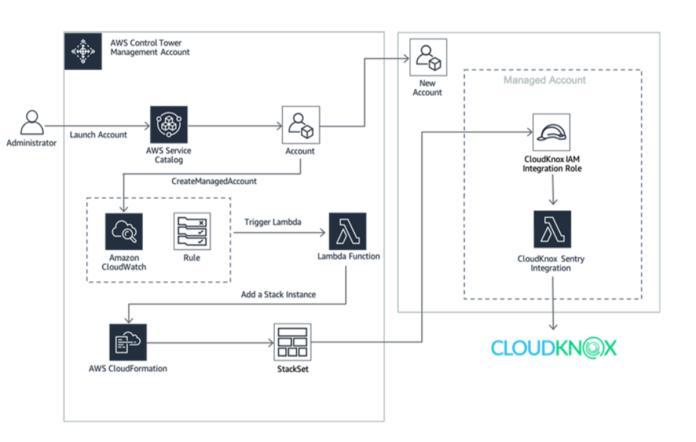
CloudKnoxisanidentityandaccesscontrolssupplierthat protects the hybrid cloud with its own activity based authorization architecture. It also serves as a rights managementplatform,allowingyoutoseeprivilegecreep, high risk roles, and unusual activities in real time. CloudKnoxisdesignedspecificallyforhybridsettings,andit works with all major public clouds as well as virtual machines.
Figure4[OpenVPNinCloudArchitecture]
Source:https://blogs.sap.com/
Between enterprises and public clouds, cloud bridge solutions offer transparent networks and seamless connection.Theyneedtoactasasingleintegratednetwork and be securely connected in order to deliver a seamless hybridcloud.Theenterprise'sdemilitarizedzone(DMZ)is safelyandopenlyextendedintothecloudusingOpenCloud Bridge.Sincethecloudbridgesolutionmakesthebusiness andcloudlookasunifiednetwork,organizationsnolonger
Figure6[CloudKnoxinAWSCloudArchitecture]
Source:https://aws.amazon.com/
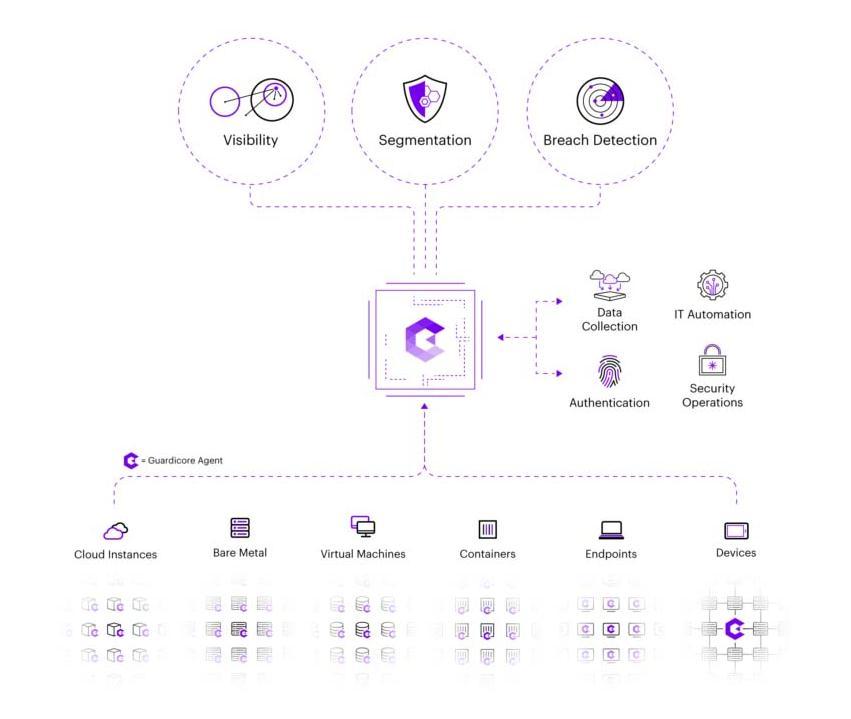
GuardicoreCentra'ssoftware onlydesignenablesadvanced networksegmentation.Thissecurityplatformisasmarter alternative to classic firewalls, allowing you to view, segment, and secure your assets across physical data centres, public clouds, and hybrid cloud environments. Guradicoreisapowerfulpolicyenginethatmapsyourwhole
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

ITenvironmentandmakessuggestionsbasedontheasset classification.Guardicorerunsonartificialintelligence.
[4] Hybrid Cloud Management https://cloudian.com/guides/hybrid it/hybrid cloud management/
[5] HYBRIDCLOUDARCHITECTUREDESIGN,DEPLOYMENT AND ANALYSIS
https://era.library.ualberta.ca/items/b66ad826 fcc9 427e bf8c b1b4eb3e165e/view/edb88087 2804 43c1 a987 1ceaa362ebf2/Soliven.pdf
[6] Extending your existing datacenter to the cloud. Technicalreport.https://docs.citrix.com/en us/citrix adc/current release/system/cloudbridge connector introduction.html
Figure7[GuardicoreCentrainAWSCloudArchitecture] Source:https://www.guardicore.com/cyber security platform/
To avail advantage of the features offered by cloud computing models, the majority of business IT companies intend to implement cloud models in their regular IT operations. Enterprises are free to select from the many cloud deployment and resource options. The hybrid approachismadetofittheneedsofthebusiness,enabling themtoplacesomedatainthelocalnetworkandsomeinthe cloud. However, there are various outside concerns that could endanger the sensitive company data. Many businesses have developed solutions, some of which are detailed here, such as building a secure tunnel between a companyandthecloud,encryptingthedataandstoringit there,andsettingupafirewallusingsimpleACLrules.
[1] https://www.redhat.com/rhdc/managed files/cl hybrid cloud security ebook f18867 202002 en.pdf
[2] Security Risks in Hybrid Cloud https://www.veritis.com/blog/hybrid cloud model 6 security risks and ways to overcome/
[3] Security Challenges in Hybrid Cloud
https://www.csoonline.com/article/3638780/5 top hybrid cloud security challenges.html
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal