International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
1PG Student, VLSI & Embedded Systems, Dept. of ECE, B.N.M Institute of Technology, Bangalore, India 2Professor and Head, Dept. of ECE, B.N.M Institute of Technology, Bangalore, India 3Assistant Professor, Dept. of ECE, B.N.M Institute of Technology, Bangalore, India ***
Abstract An invisible digital watermarking is a process where an image or a video is embeddedwithsomeinformation in the form of a text or an image called as watermark which is not visible to human eye. In this paper, two invisible digital watermarking techniques based on Discrete Cosine Transforms (DCT) and Discrete Wavelet Transforms (DWT) are implemented in MATLAB and are compared for its robustness using correlation coefficient parameter. The measure of this parameter is doneafterperformingalltypesof attacks and degradation on the images. The end results show that invisible image watermarking based on DWT is more robust to all sort of attacks and degradation as compared to DCT.
Key Words: Digital Invisible Watermarking, Discrete Wavelet Transform (DWT), Discrete Cosine Transform (DCT), Robustness, Co efficient Correlation, MATLAB.
Duetothewideexpansionofinternetoveryears,availability ofdataondigitalplatformhasincreasedveryrapidly.Oneof themajorproblemistoprotectthemultimediainformation availableandsoastherightfulowneroftheinformationare concernedabouttheirworkbeingillegallyduplicated.Soin ordertomaintainthebalanceofmultimediabeingavailable and also being protected of illegal use, out of many approaches digital watermarking is the one which has gainedalotofinterestintheindustry.
Themainideaofrobustnessofimagesinwatermarkingisto embedthewatermarkwithintheoriginalimagewhichisnot visible for human eye and also protects the images from imageprocessingattacksanddegradations.Inotherwords, themajoraimistodevelopanimagevisibleexactlyassame as the original image, but still allows identification of the hiddenwatermarkwhencomparedwiththekeygivenbythe ownerwhenevernecessary.
This paper is divided into six sections: section 1 gives the introductionofthepaper,section2dealswiththebasicson digitalwatermarking,section3talksaboutimplementation of the whole watermarking process, section 4 talks about implementation of DCT method, section 5 gives an idea aboutimplementationofDWTmethod,section6describes
theresultsoftheworkdoneandsection7istheconclusion oftheworkdone.
The rapid increase in the usage of digital multimedia applicationshascreatedagreatnecessitytogivencopyright protectiontothosedata.Generallywatermarkingisatypeof markerwhichisembeddedinadigitalimagewhichisusedto identifytheownershipoftheimage.Digitalwatermarkingare oftwotypes.1.Spatialdomainmethodwhere,inanimage space,achangeinthepositionofXdirection,willprojectsthe change of position in space.2. Transform domain method, wheretheimageistransformedintofrequencydomainusing differenttransformationsandthenwatermarkingisdone.
A watermark indeed can be described as a unique identificationcodevisibleorinvisiblewhichisembeddedinto the image permanently. Watermarks are of four different types.1.Visiblewatermark:watermarksarevisibleonthe image.2.Invisiblewatermark:watermarksarehiddeninthe imageandnotvisiblebynakedeyes.3.Publicwatermarks: Not so secure watermarks that can be understood and anyone can modify using certain algorithms. 4. Fragile watermark: watermarks that can be destroyed by manipulatingthedata.
Digital Watermarking has three phases in its life cycle. 1. Embed:hereadigitalimageisembeddedwithawatermark image. 2. Attack: Once the original image is changed, it is more prone to threats and this is known as attack to the system. 3. Protection: it is the detection of the watermark fromanoisewhichmighthavealteredtheoriginalimage.
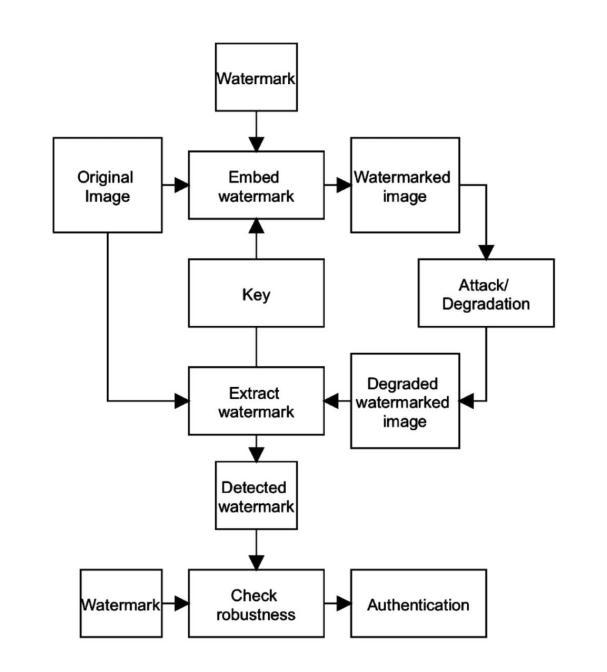
Consideringthelifecycleofthewatermarkingprocess,Fig 1 showstheflowofthewatermarkingprocessimplementedin this work. The original which has to be marked must be a grayscaleimage,butincaseifacolorimageisselected,itis convertedintoagrayscaleimagebeforeproceedingfurther.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
TheDCTpermitstobreaktheimageintobandsofdifferent frequency, which makes it much easy to embed the watermarkintothemiddlefrequencybandsoftheimageas showninfigure4.Thesemiddlebandsareselectedasthey don’trepresentthemostimportantvisualpartoftheimages.

The original image used here is an X ray ofa human hand withdimensionsof512x512pixelsasshowninFig 2.The watermarkimageusedhereisabinaryimageofsize64x64 pixelsasshowninFig 3.Whenembeddingandextractingthe watermark,theuserisaskedtoenteracryptographickeyas a password. The two transform domain methods used for digitalinvisiblewatermarkingareDCTandDWT.
Fig 4: 8x8Coefficientstobemodified

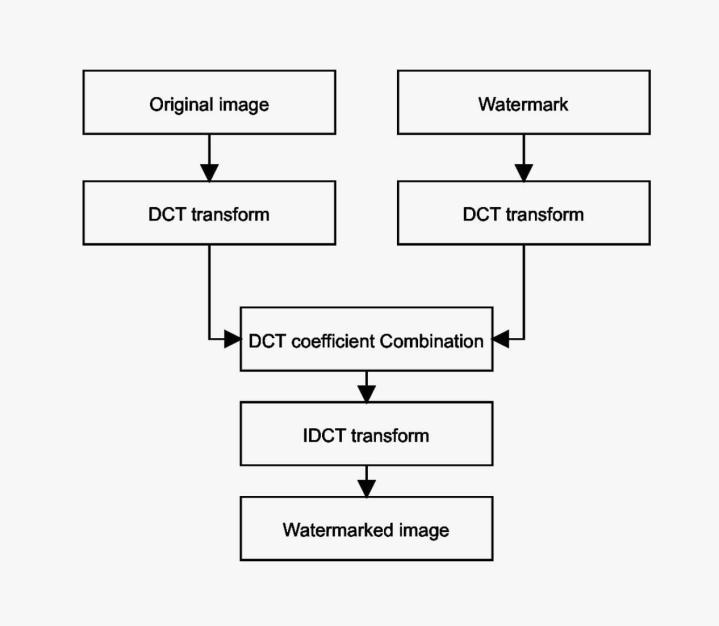
Figure5showstheembeddingflowchartforDCT.Hereone pixeloftheimageishiddeninevery8x8blockofimageby performing2 DDCT.Thenthecoefficientscombinationfor DCTaremodifiedandinverseDCTisperformedtoobtain thewatermarkedimage.

Figure6showstheextractingflowchartforDCT.HereDCT coefficientsofthecorrespondingblocksofanoriginalimage aresubtractedfromtheDCTcoefficientsofthewatermarked imageblock.Ifthesumofdifferencesbetweenthesetwoare
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

greaterthan0,thevalueofthebitdetectedisconsidered1 else0.
diagonalandverticaldetailsandmodifiedatlevels2and3to embedthewatermark.Laterwhichaninverse3levelDWT decomposition is performed to obtain the watermarked image.
Fig 6: ExtractingFlowchart
DWTisawavelettransformmethodwherethewaveletsare sampled discretely. The wavelet transform methods gives the frequency and spatial description of an image. DWT dividestheimageintolowandhighfrequencyparts,where higher frequency parts contain information of edge componentsoftheimage,whilethelowerfrequencyparts areagainsplitintohigherandlowerfrequencybands.The higher frequency bands are most widely used for digital invisiblewatermarkingastheyarelessvisibletohumaneye whenedgesarechanged.
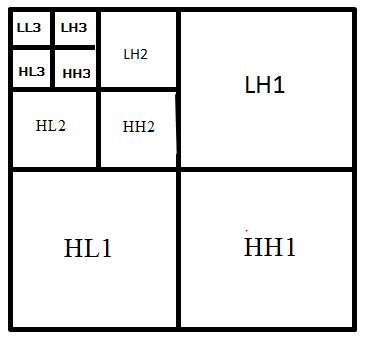
The3leveldecompositionofDWTisasshowninFig 7.
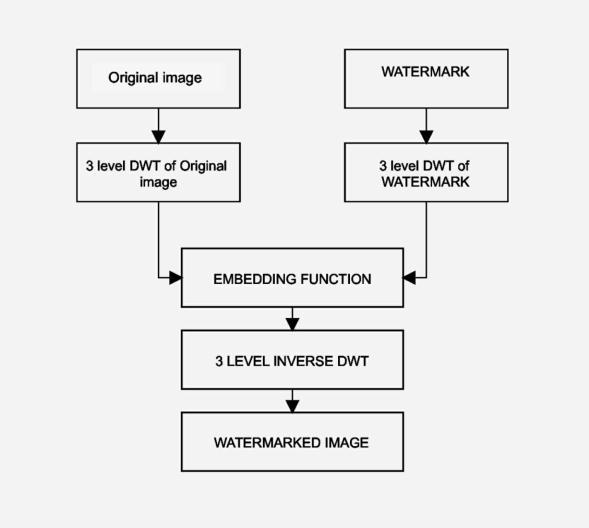
Fig 8 shows the embedding flowchart for DWT. After performing 3 level decomposition on both original and watermark images, the coefficients of the horizontal,
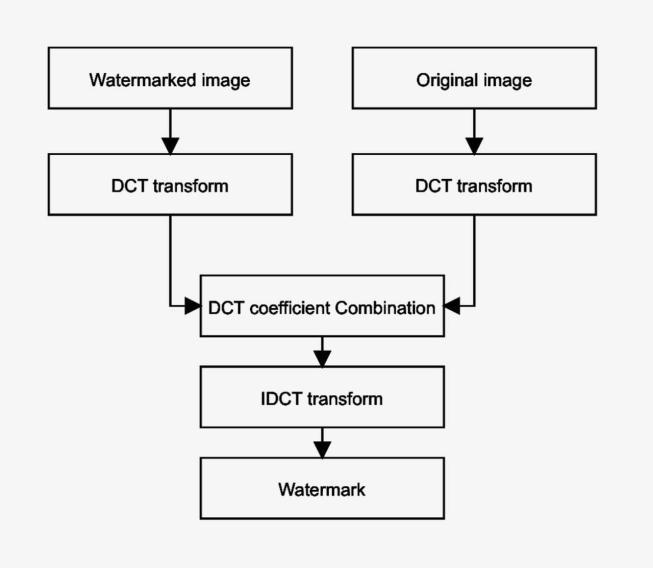
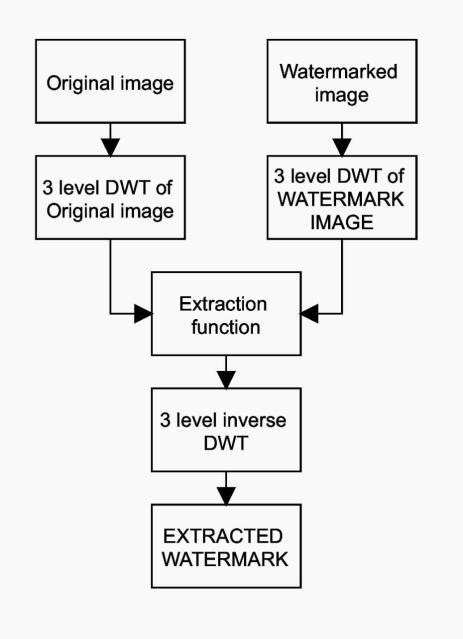
Fig -8: EmbeddingFlowchart
Fig 9showstheextractingflowchartforDWT.Here,DWT coefficients of levels 2 and 3 of the original image are subtractedfromeveryDWTcoefficientoflevels2and3of the watermarked image. The differences are added and if their sum’s differences is greater than 0, the value of the detectedbitisconsideredtobe1,else0
Fig 9: ExtractingFlowchart
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
In this work, both the watermarking methods use the original non marked image for the detection of the watermarkthusmakingthesystemaprivateinvisibledigital watermarking system. Also in this paper, the correlation coefficient which is the similarity measure between the originalwatermarkandextractedwatermarkiscalculated using MATLAB function “corr2”. As this correlation coefficientapproachescloseto1,itisdeterminedthatboth theoriginalandextractedwatermarksarealmostmatching.
Totestthequalityofthedetectedwatermarkwhichiscalled the robustness of the watermarking system, there are a series of attacks performed: JPEG compression, cropping, contrastmodification,brightnessmodification,filteringand addingnoise.Aftereveryattack,a watermark isextracted and is compared with the original watermark using correlationcoefficient.
Whenthewatermarkedimagesarenotpronetoanyattacks, the DCT and DWT techniques yield a good correlation coefficientvalueasshowninTable 1.
Table -1: Correlationcoefficientoforiginalanddetected watermarkwithoutattacks
DCT DWT 0.987946 1
TheJPEGcompressionattacksareperformedfor10qualities andthecorrelationcoefficientvaluesareaslistedinTable 2.ItshowsthatthevaluesincaseoftheDWTmethodsare higher than 0.5 which is up to 20% of JPEG compression quality.HenceDWTmethodismorerobust.
Table 2:Correlationcoefficientoforiginalanddetected watermarkafterJPEGCompressionattack
Quality DCT DWT 10 0.163426 0.318756 20 0.295148 0.587610 30 0.332688 0.610387 40 0.387562 0.725036 50 0.421597 0.836497 60 0.503624 0.803412 70 0.586931 0.901479 80 0.690752 0.966587 90 0.706981 0.975905 100 0.996308 1
Brightness implies the indication of more gray level in an image.Thisattackisdoneover10differentlevelsandthe correlationcoefficientvalues areaslistedinTable 3.Itis observedthatonamajorityDCTmethodismorerobustthan DWT.
Table -3: Correlationcoefficientoforiginalanddetected watermarkafterbrightnessattack
Level DCT DWT
0.1 0.962381 1 0.1 0.967857 0.994860 0.2 0.93785 0.971269 0.2 0.882490 0.921475 0.3 0.819575 0.849625 0.3 0.726942 0.612589 0.4 0.652369 0.603470 0.4 0.606777 0.325871 0.5 0.456297 0.409787 0.5 0.425778 0.214085
Contrastistheratioofminimumandmaximumvaluesofthe graylevelintheimages.Whilehistogramisthedistribution of the gray level over the image. Correlation coefficient valuesfororiginalanddetectedwatermarkwithhistogram equalization contrast attack is listed in Table 4. It isseen thatbothmethodsshowapproximatelysamevaluesforthis attack.
Table 4:Correlationcoefficientoforiginalanddetected watermarkaftercontrastattack
Level DCT DWT
0.5 0.152364 0.251268 0.6 0.180369 0.278569 0.7 0.236187 0.284156 0.9 0.279641 0.281456 1.1 0.286147 0.278945 1.4 0.291025 0.271025 1.5 0.296947 0.276301 1.6 0.300156 0.269785 1.7 0.314789 0.268941 1.8 0.297510 0.087456
International Research Journal of Engineering and Technology (IRJET)

e ISSN: 2395 0056
Croppingisalteringtheimagebyremovingsomepartofit, whiletheremovedpartarepaddedwith0s.Differentlevels ofcroppingisdoneandtheircorrelationcoefficientvalues are listed below in Table 5. It is seen that both methods perform well even after half of the pixels are replaced by zeros.
Table -5: Correlationcoefficientoforiginalanddetected watermarkaftercroppingattack
Level DCT DWT
1.1 0.164259 0.065148
1.2 0.275630 0.154783
1.4 0.469512 0.289641
1.6 0.584102 0.423271
1.8 0.650326 0.539245
2 0.720159 0.674715
4 0.926314 0.970364
8 0.985201 0.983014
16 0.980236 0.995214
Imagefilteringisperformedbyconvolutionofimageandthe impulseresponseofthefilter.Averaging(LFfiltering)and Sharpening(HFfiltering)arealsoperformedontheimage andtheirvaluesarelistedinTable 6.Itisconcludedthaton amajoritybasisDWTismorerobustthanDCTasitdoesn’t tolerateaveraging.
Table 6: Correlationcoefficientoforiginalanddetected watermarkafterfilteringattack
Type DCT DWT
Average 0.186485 0.465120
Gaussian 0.762014 0.920365
Laplace 0.624596 0.892145
Log 0.542360 0.810265
Median 0.317526 0.69785
Unsharp 0.564523 0.804526
Noiseisanunwantedpixelthatdoesn’tbelongtotheoriginal picture.Gaussiannoise,impulsenoise(Salt&pepper)which is characterized by pixels that deviate from their surroundings,and Speckle noise, whichis a multiplicative noise are the different types of noise attacks that are performedonthewatermark.TheirvaluesarelistedinTable 7. It is seen that DWT is more robust except for salt & peppernoiseattacks,wherethesituationisunresolved.
Table 7: Correlationcoefficientoforiginalanddetected watermarkafternoiseattack
Type DCT DWT
Gaussian 0.275630 0.569085
Salt & Pepper 0.542697 0.510697 Speckle 0.302689 0.536478
Inthispaper,twodifferenttypesofinvisibledigitalimage watermarkingmethodsusingDCTandDWTtechniquesare implemented.TheirRobustnessiscomparedafterdifferent typesofattacksanddegradation.Thecorrelationcoefficient whichisthesimilaritymeasureoftheoriginalandextracted watermarkaretakenasameasureforRobustness.
Considering the obtained results, it is concluded that invisible digital image watermarking based on DWT technique is more robust than the image watermarking basedonDCTtechnique.
[1] Cox, IJ, Miller, ML & Bloom, JA 2002, "Digital Watermarking", Morgan Kaufmann Publisher, San Francisco,CA,USA2002
[2] Christine I. Podilchuk, Edward J. Delp, ―"Digital watermarking:Algorithmsandapplication",IEEESignal processingMagazine,July2001.
[3] Sumedh P. Ingale, Dr.C.A.Dhote,"A Survey Of Digital WatermarkingTechniques"
[4] Vinita Gupta,Mr.Atul Barve ,"A Review on Image WatermarkingandItsTechniques"
[5] ManpreetKaur,SonikaJindal,SunnyBehal,"ASTUDYOF DIGITALIMAGEWATERMARKING"
[6] Lalit Kumar Saini, Vishal Shrivastava " A Survey of DigitalWatermarkingTechniquesanditsApplications"
[7] G.RoslineNesaKumari,B.VijayaKumar,L.Sumalatha, and Dr V. V. Krishna," Secure and Robust Digital Watermarking on Grey Level Images", International JournalofAdvancedScienceandTechnology,2009
[8] Baisa L. Gunjal, R.R. Manthalkar, "An overview of transform domain robust digital image watermarking algorithms",JournalofEmergingTrendsinComputing andInformationSciences,2010
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

[9] W. Hong and M. Hang, "Robust Digital Watermarking SchemeforCopyRightProtection,"IEEETrans.Signal Process,2006.
[10] D.S. Bormane, Pallavi Patil, “DWT Based Invisible Watermarking Technique for Digital Images”, International Journal of Engineering and Advanced Technology (IJEAT) , April 2013, ISSN: 2249 8958, Volume 2,Issue 4
[11] DeepshikhaChopra,PreetiGupta,GaurSanjayB.C.,Anil Gupta,“LsbBasedDigitalImageWatermarkingForGray Scale Image” IOSR Journal of Computer Engineering (IOSRJCE)
[12] Qing Liu,Jun Ying(2012),”Grayscale Image Digital WatermarkingTechnologyBasedonWaveletAnalysis”
[13] Mohamed Sathik, SS Sujatha, “A novel DWT based InvisibleWatermarkingTechniqueforDigitalImages”, InternationalArabJournalofe Technology,Jan2,Vol.2, No.3
[14] Li Sukang, Mei Jiansheng, and Tan Xiaomei, “Digital Watermarking Algorithm Based On DCT and DWT”, Proceedings of the 2009 International Symposium on WebInformationSystemsandApplications(WISA’09), China,May22 24,2009,pp.104 107
[15] Ikpyo Hong, Intaek Kim, Seung So0 Han, “A Blind Watermarking Technique Using Wavelet Transform”, ISIE2001,Pusan,KOREA,07803 70~9 2/01,IEEE
[16] PravinM.Pithiya,H.L.Desai,“DCTBasedDigitalImage Watermarking, Dewatermarking & Authentication”, International Journal of Latest Trends in Engineering andTechnology(IJLTET),Issue3May2013,Vol.2
[17] Shahin Shaikh, Manjusha Deshmukh, “Digital Image WatermarkingInDCTDomain,InternationalJournalof Emerging Technology and Advanced Engineering, Volume3,Issue4,April2013
[18] Sharma, Janki Ballabh et al. “Comparison of Bit Error Rate Performance Measure of Robust Watermarking Scheme Based On Self Fractional Fourier Functions , Empirical Mode Decomposition and Cyclic Encoding.” (2013).
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |