International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072
,
Abstract: In order to create a chronological single source of truth for the data, a blockchain is a database that stores encrypted chunks of data before chaining them together. Instead of being copied or moved, digital assets are distributed, resulting in an immutable record of the asset. Due to the asset's decentralised nature, the public has complete real time access and transparency. The public ledger and built in security features of blockchain make it a top solution for practically every industry. Thus, in this paper we try to implement blockchain system to select an IDE Subject (INTER DEPARTMENT ELECTIVE) which makes sure that the data isn’t tampered through external source and the information is stored securely and is transparent to the college authorities and students.
Keywords Block chain, Database, Encrypted, Digital assets, Data Storage, Security, Immutable, Transparency, IDE(Inter department elective)
Blockchain [1] is a constantly growing set of data with certain records in it called blocks, it is a particularly encouraging and progressive innovation since it lessens risk, gets rid of extortion and acquires straight forwardness.Theyaresecuredandlinkedtogetherusing cryptographic methods. Here we developed a program that simulates a real time block chain technology blockchain for choice of IDE (INTER DEPARTMENT ELECTIVE), which ensure that the chosen IDE (INTER DEPARTMENT ELECTIVE) can't be changed by any outside source and it is likewise straightforward to people in general. A block of data it consists of data of students such as the name, the college seat number and the subject selected .The Blocks containing these data arethen encrypted [1] ,it’s a way when normal readable textisconvertedintounreadabletextsothatitcannotbe accessed and changed, the encryption works in such a waythatifanywordorspacingorcapsischangedinthe original text the encryption text gets changed .The encryptiontextisirreversiblesotheoriginaltextcannot beretrieved.Theentireprojectisboundbyusingpython andflaskframeworkthathelpsustohostthewebsite,to make entries these entries are then passed on to the databases these databases are distributed in nature whichisthecoreconceptof blockchain.Anychangesin any one of the database the data in other databases will
notbechangedunlessthethirdpersonchangesthedata inallthedatabasethatmakeupmorethan51%.
A blockchain [2] is an very advanced technology for safety and security of data. Every time a certain theexchangeisdoneon thenetwork, a record ofthisexchange is added tothe registration ofeach member. Every exchange on the blockchain is represented by a square in the chain, and each time an exchangetakesplace,arecordof thatexchangeisadded to the record of every member. Ethereum the second biggest blockchain execution after bitcoin. Ethereum disperses a money called ether, yet additionally considersthecapacityandactivityofPCcode,takinginto account brilliant agreements. Starting around 2008 square chain has been seeing persistent development in allfields.
There are several distinct financial advantages of blockchain development [3]. The producers begin by utilising,forinstance,abankandalloftheresourcesthat are essentially squandered given that they handle and addressall transactionsthemselves. With theuseof this new record, the bank would be able to maintain safer recordsthatarelesslikelytobetamperedwithandgain a more accurate understanding of prospective opportunities.
For security purpose, Tranquillini examines recent concerns withthe prosperityandadequacyof European financialbusinesssectorsandgovernmentcontrol[7].In light of everything, he avoids a particular end and resolves that execution of such development would be inconvenient, most ideal situation, and that it will not happenassoonaspossible.
Infoodsecurity,researchersfromMontanaschoolfigure out a couple of creating examples to address the need andpotentialforblockchainprogressesforfoodsecurity [7].Themajorquestioninthisissueisrecognizabilityof food things, from their sources, on all through their dissemination frameworks, and on to their last client. This could assist with hindering blackmail and deflect
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072
or on the other hand if nothing else address issues of foodborneailment.
In Product Traceability, Tranquillini examines recent concerns withthe prosperityandadequacyof European financial business sectors and government control [8] His article serves more as a source for his insightful considerations on the capacity of the utilization of such advancement to the protections business. In light of everything, he avoids a particular end and resolves that execution of such development would be inconvenient, most ideal situation, and that it will not happen at whateverpointassoonaspossible.
Proposed a system that uses the blockchain core basics suchasdistributeddatabase, immutable,BetterSecurity by storing data in encrypted format with the encryption ofthepreviousblock[5].
Here the main approach was to create a distributed database, the creation of distributed database was done my initialize multiple database instances in various systems that was connected with our main program, an exactcopyofthedatafromourprogramissenttoallthe databases, the main data base used here is the MySQL databasethatstoresdatainarelationaltable,andacopy of a data is also sent to cloud database Firebase for addedsecurity.
Here the front end iscontrolledby the flask Framework to host the website on the person server which is a raspberrypi4
Back end is programmed with python that handles all therequestsandtheAPIcallstoallthesoftwareandalso theencryptionofthedata. TheencryptionmethodusedhereisSHA256.
The distributed database is created by using multiple cloud server instances and local machine to host the database.
For the local machine database MySQL database the community version is used. Here the data is stored as records and in a table format The data stored here will be the Student name, student college seat number, the subject selection. These data will not only be stored in onedatabasebutindifferentMySQLinstancerunningin the different local host. In this project we had three MySQL instances running. Thus there were three copies ofthesamedataatthreedifferentlocation.
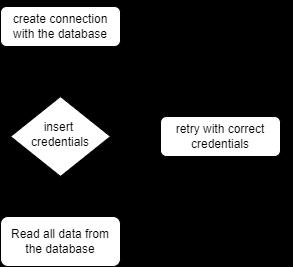
Aspythonwasusedtocommunicatewiththedatabases. Theconnectionwasmade:
Fig 1: Flowchart for credentials
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072
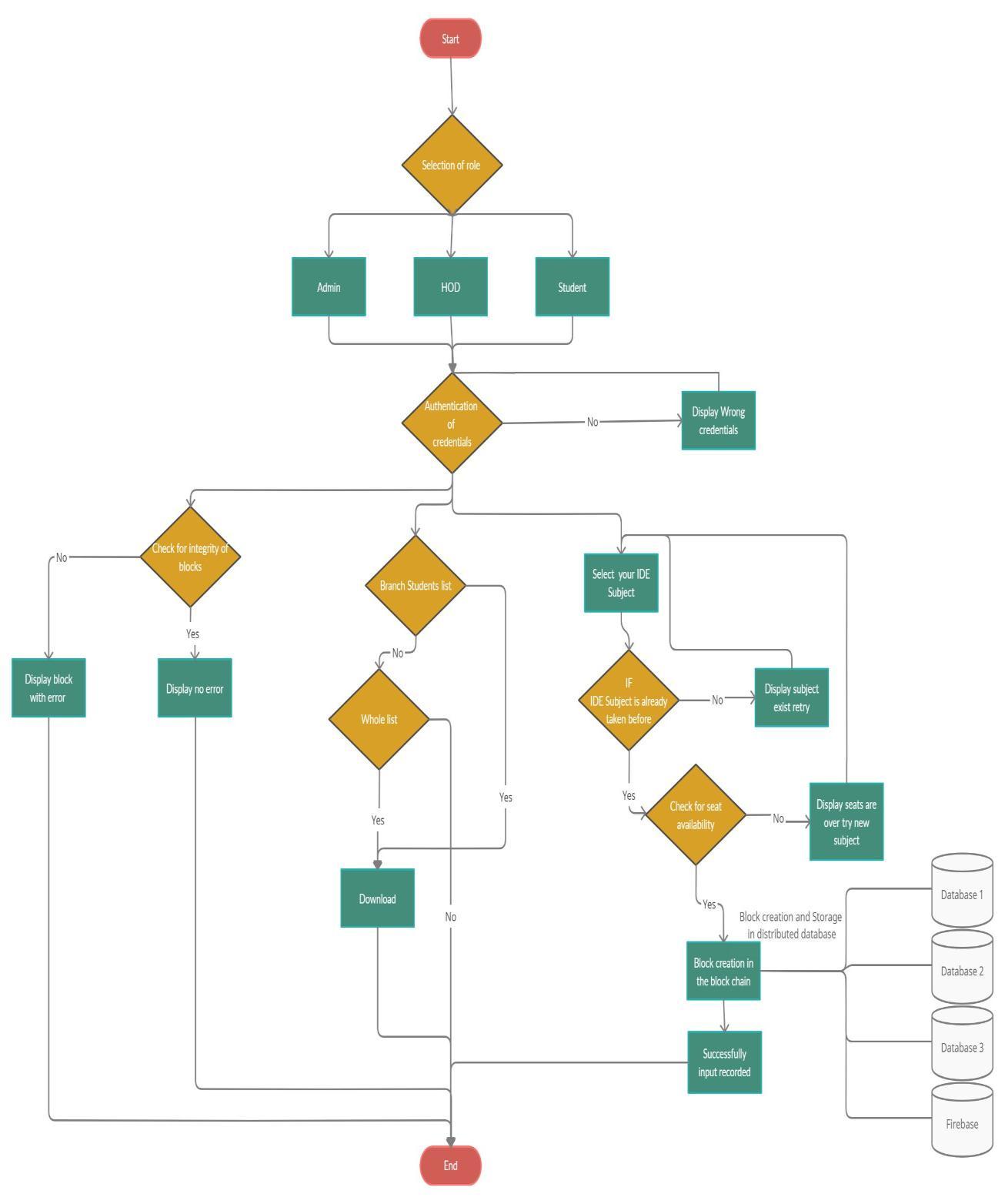
The data wassentor written intothedatabase mypre defining the SQL query with variables that would be enteredbytheStudent
ForthedatabaseinstanceinthecloudFireBase Realtime Databasewasused, The FirebaseRealtimeDatabaseis a database stored in the cloud. Every connected client receivesreal timesynchronisationofdatasavedasJSON. todevelopcross platformapplications.
The Firebase Realtime Database enables safe access to the database from client side code, enabling you to create robust, collaborative apps. The end user has a responsive experience because to local data persistence andreal timeeventsthatcontinuetohappenevenwhile thesystemisoffline.Thelocal dataisupdatedwhenthe deviceregainsconnectivitywiththedistantupdatesthat tookplacewhiletheclientwasoffline.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072
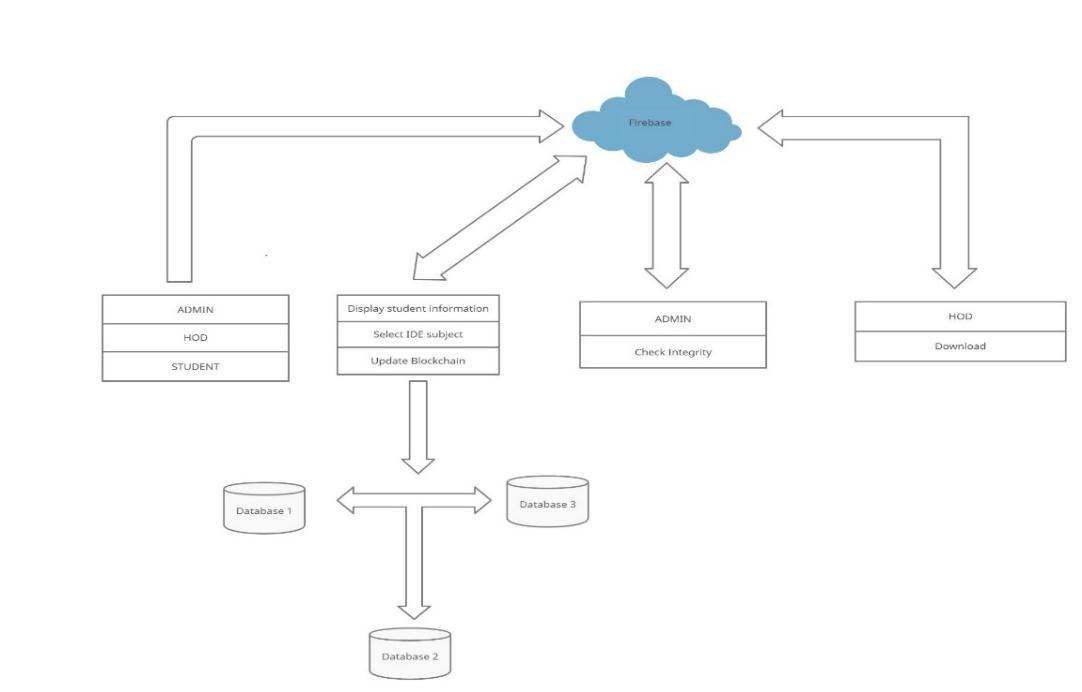
Thus totally four duplicate copies were getting saved in four different location which eliminated the centralized structuredatabase.
Each copy the same data with the same capitalization andtheencryptionmethod.
OurwebsitewasdevelopedusingHTML,CSSthatisused for the user/student to interact. It consists of the basic loginpageforthedifferentauthoritiesofthecollegeand the student authentication. the information provided in the front end is then feed into the backend python programtocreatetheblockandalsofeedtheblockdata inthedatabase
The entire project is bound by the python code. It helps in sending and receiving data and also the check the integrityoftheblocks,foranychangeindata.
The code takes in the values of the student and the encrypted value of the previous block and forms a dictionary whichisa JSON typeformatand encryptsthe datausingSHA256algorithm.
When a block is created the data of the block is encrypted and then the encrypted text is then stored in theblock.
When the next new block is created it consists the encryption text of the previous block and the data of its blockitencryptsthedatawiththeencryptiontextofthe previousblock
Whenanewblockiscreateditcheckstheintegrityofthe other blocks like if any data has been changed and reportsthechangeindata.
The integrity check is done by taking the human readable data and the entire data is encrypted and checkedwiththeencryptedtextinsidetheblockthathas the encryption of the block thus this two must match to showthattheblockisnottampered.Forthenextblockit takes the data of the previous block and the data of the currentblockandencryptsthedataandthenchecksthe encryptiontextwiththatstoredinsidetheblock.
Hashing the process to convert normal plain text to non readable text which cannot be reversible it is similar to encryption but in encryption the text can be reversed withakeyhereinhashingitcannotbereversed
Thus when storing data we use hasing so when an unauthorized person gets access to the code he cannot reverse the string. even a slight change in the plain text will create an exponetial change in the hashed texted we use the sha256 algorithm to hash the entire block.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page 1239
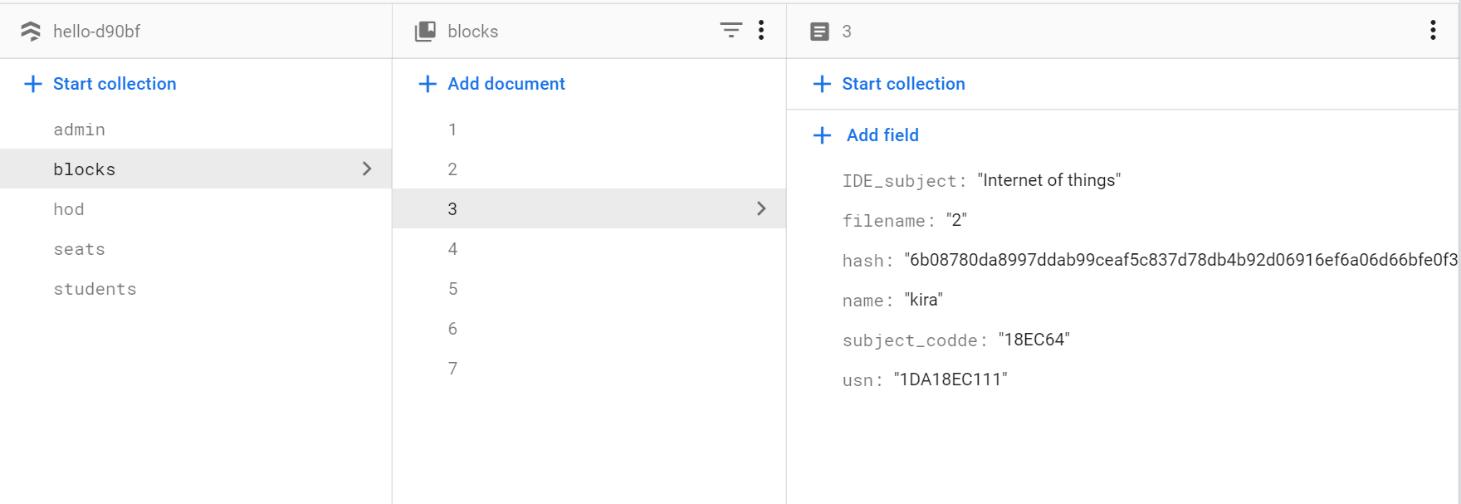
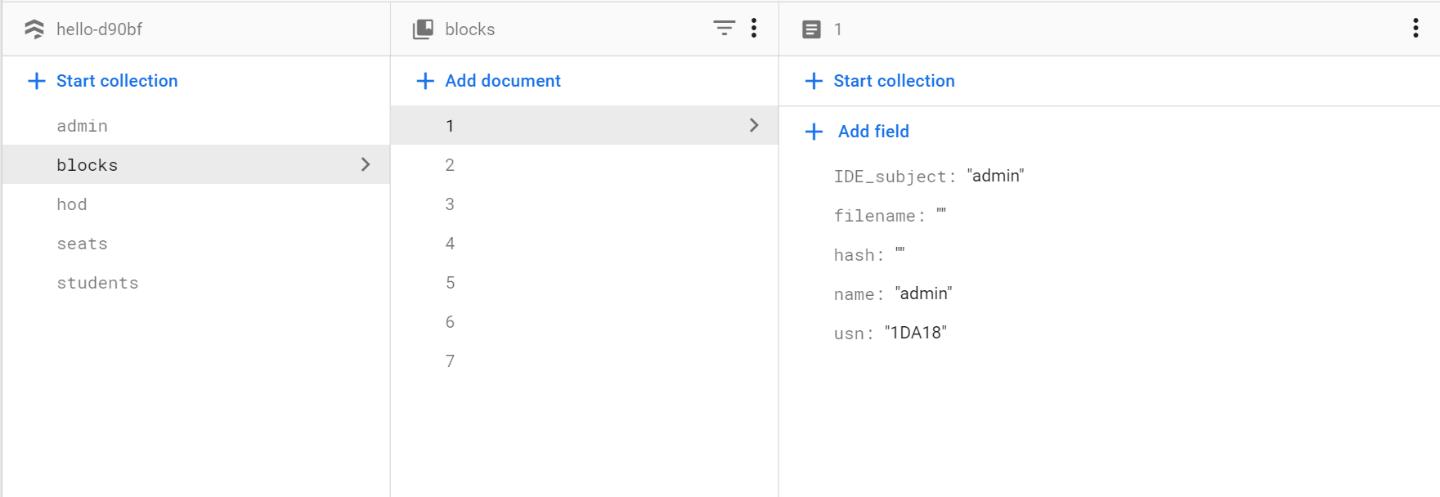
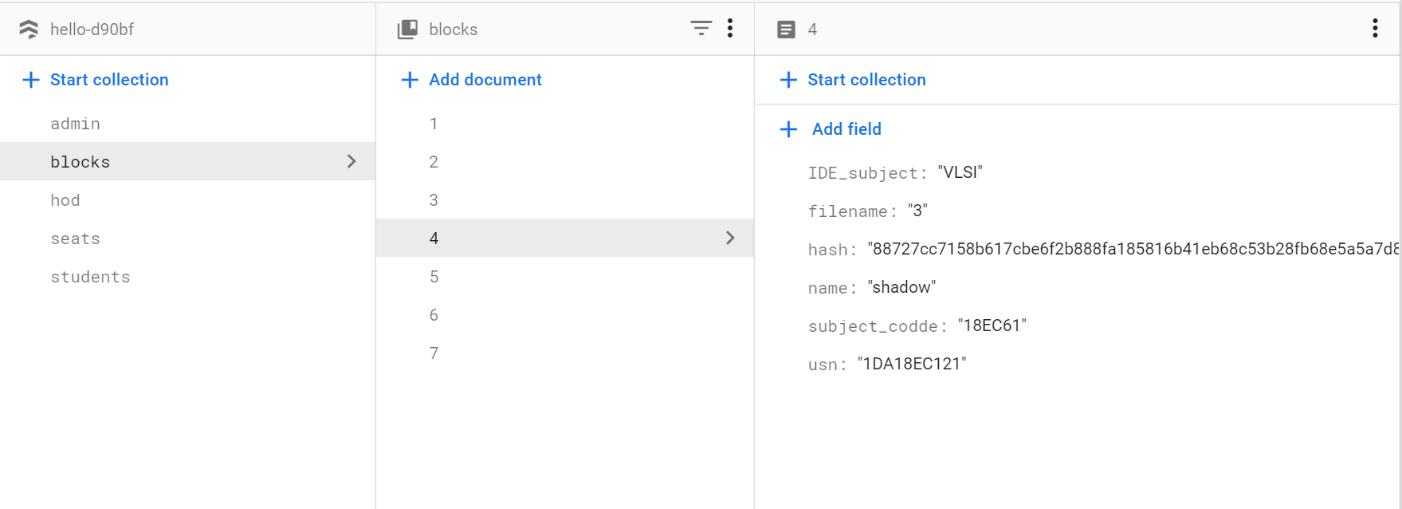
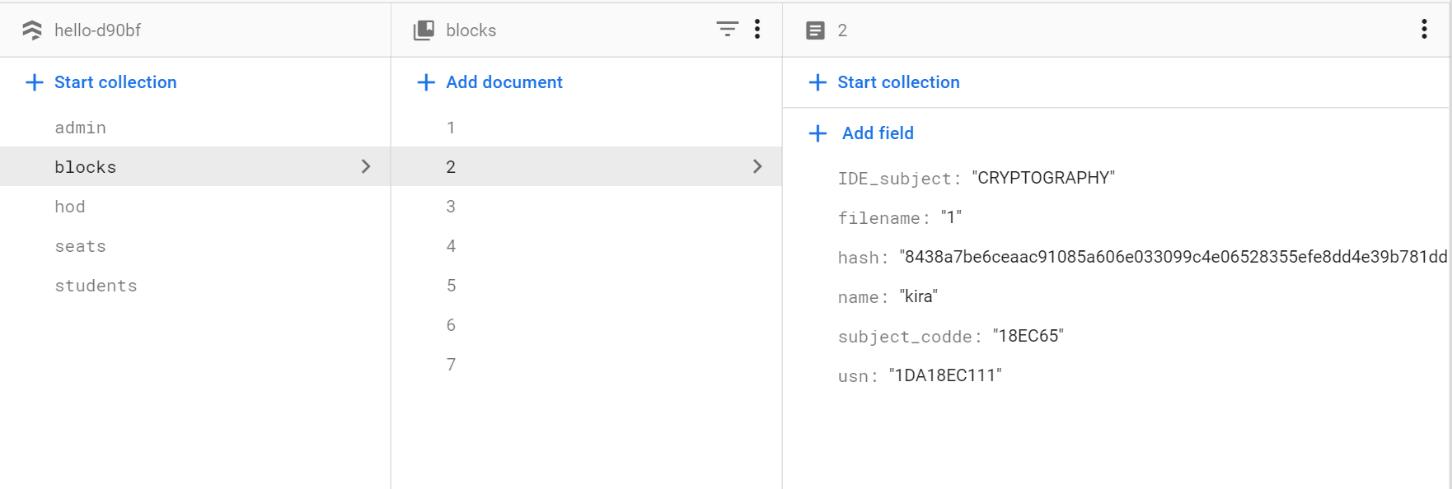
Fig 4 : Block creation
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p-ISSN: 2395-0072
Result:
The developed safe and secure database of student ledger showed promising results by using the blockchain technology. Since the existing way of recording the student academic detail of the number of subjects taken by the student and the difficulty in segregating the repeated subjects, the blockchain technology will eliminate the entire difficulty since it uses the technology of hashing which enables the portal to give students a different subject apart from the subjectsalreadyfinished.
There are 3 different types of logins namely hod login studentloginandtheadminlogin
Thestudentloginisonlyforthestudentswheretheywill have to login with their respective email ids and passwordwhichwilltakethemtotheirhomepagewhich displaysthenameofthestudentsemesterofthestudent andtheuniversityseatnumberofthestudentandallthe subjects the student has already studied in the previous semester and the option to select the available subjects. Uponselectingthesubject,anewblockwillbegenerated connectingtothehashofthepreviousblockandrecords the data in the decentralized database which is now permanentandcannotbealtered.
The hod login is primarily to monitor the student’s history of the subjects taken and to assign the teachers for a particular class from the student’s response to a specified course. The hod (head of the department) will be given the privileges to check how many have opted foreachindividualsubjectorcourse.
The hods are given a login id and password with which they can login to the document and download the requireddocuments
The admin section is to control, monitor and maintain the entire process without anyone facing issues regarding the selection process and to keep track of the entire process of subject selection. The admin will have the complete control on the entire network and can resolvetheissuesfacedbythestudentsortheprofessors ortheheadofthedepartments.
[1] Zheng, Z., Xie, S., Dai, H., Chen, X., & Wang, H. (2017). An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. 2017 IEEE International Congress on Big Data (BigDataCongress).
[2] Ahram, T., Sargolzaei, A., Sargolzaei, S., Daniels, J., & Amaba, B. (2017). Blockchain technology
innovations. 2017 IEEE Technology & Engineering Management Conference (TEMSCON)
[3] SK,V.,RS,Y.,Prashanth,Y.,N,Y.,&M,N.(2020). E Voting Systems using Blockchain: An Exploratory Literature Survey. 2020 Second International Conference on Inventive Research inComputingApplications(ICIRCA).
[4] Hjalmarsson, F. P., Hreioarsson, G. K., Hamdaqa, M., & Hjalmtysson, G. (2018). Blockchain Based E Voting System. 2018 IEEE 11th International ConferenceonCloudComputing(CLOUD).
[5] Sachchidanand Singh IBM Software Lab Pune, India 411 057. Nirmala Singh Tech Mahindra Pune,India 411057.
[6] D Sathya1 , S Nithyaroopa2 , D Jagadeesan3 , I Jeena Jacob4 1 Assistant Professor II, Dept. of CSE, Kumaraguru College of Technology, Coimbatore 2 Assistant Professor, Dept. of CSE, Kumaraguru College of Technology, Coimbatore 3 Assistant Professor, Department of Management Studies, Rathinam College of Arts and Science, Coimbatore 4Associate Professor, Department of CSE, GITAM School of Technology,GITAMUniversity,Bengaluru.
[7] Ahmed, S., & Broek, N. t. (2017). Food supply: Blockchain could boost food security.(brief article).Nature,550(7674).
[8] Lu, Q., & Xu, X. (2017). Adaptable blockchain based systems: A case study for product traceability.IEEESoftware.
[9] Cocco, L., Pinna, A., & Marchesi, M. (2017). Banking on blockchain: Costs savings thanks to theblockchaintechnology.FutureInternet.