International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056


International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

1Student, Dept. of Information Technology and Engineering, Goa College of Engineering, Farmagudi, Goa, India
2 Assistant Professor, Dept. of Information Technology and Engineering, Goa College of Engineering, Farmagudi, Goa, India ***
Abstract – MaliciousSoftware,also,knownasMalware,can pose serious cybersecurity threats. This can have significant consequences not only for individuals and organisations but, also, for the nation at large. The meteoric surge in malware types and its magnitude dampens the efficacy of traditional techniques, that usefeatureextractionandcomparison,for the detection of cyber threats, thus rendering the identification of malware extremely difficult.Malwaredetectionchallengesare intensified by the sizeable increase in the intricacies, in the type and structure, in recent years, including instructions, settings, source code, binary files, and others. The increased intricacies encourage misjudgement. This study adopts Convolutional Neural Networks (CNN) and Blockchain to enhance the security of cyber networks by increasing the efficiency and accuracy of malware detection under largeand numerous types of malware. The experimentoffersthatCNNis extremely effective with sourcecodeandbinarycode detection and, it can recognize malware that is embedded into benign code, making malware impossible to hide. This research suggests a viable solution for network administrators to identify malware at the very start in the complex network environment, so as to enable information technology personnel to engage in timely protective actions and prepare for potential additional cyberattacks.
Key Words: Malware,Blockchain,CNN,Binarycode,Benign, Malign
Intheworldwhere‘information’isoneofthemostprized assets,asignificantthreatisposedtoitbytheever evolving and sophisticated malwares (Sewak, Sahay, & Rathore, 2018). The malware is an industry with ulterior profit motives, although it was initially created for fun (Statista, 2022). The identified malware, as per AV Test, greatly increasedfrom182.90millionintheyear2013to1332.56 million in 2022 (AV TEST). The malware file type and structure also grew in complexity with the increase in volumeaswellasvarietyofmalware.Themalicioussource filescontainsourcecodefiles,binaryfiles,shellscriptfiles, perl script files, make files and read me files, along with several hierarchical directories. There are many types of malwares such as Adware, Rootkit, Virus, Ransomware, Backdoor, Worm and Trojan (Gandotra, Bansal, & Sofat,
2014).Hybridmalwaresareembeddedincyber attacksto compromisethesecurityoftheinformationsystem.Awide varietyoftechniquesareproposedfordetectionofmalwares (Sewak,Sahay,&Rathore,2018).
A wide variety of techniques were employed by the researchersandindustriesfordetectionofmalwares.This includes heuristic based methods and signature based methods(Nawroozi&SaravanaGuru,2020).Thesignature basedmethod,consideredthesimplestmethodofdetection, considersandcomparesthetrafficnetworkormalwarefor possibleattackswithknownsignature.Antivirussoftwares have been used for many years for identification of a particulartypeofvirus.
Theauthorsofmalwaretrytododgetheantiviruswiththe use of metamorphic and polymorphic malware to bypass virus signatures (Nawroozi & SaravanaGuru, 2020). However, this method is not free of drawbacks. Its inefficiencyindetectionofunknownmalwaresandsecurity threats compel the antivirus vendors to rely on heuristic methods,whichisbasedonrulesdeterminedbytheexperts. It relies on static and dynamic methods of analysis. The heuristicmethodforexaminingthemalwarebeforewriting thesignatureisrequiredtoanalysewhetheritisbasedon thebehaviourorbytestingthecodeinasafeenvironment. The methods employed in the analysis of the malware is basedontwomethods,namely,StaticanalysisandDynamic analysis. Static analysis refers to analysing the malware without its execution, whereas Dynamic analysis analyses the behaviour of a malware program while running or operatingonacontrolledenvironmentlikeavirtualmachine or a sandbox. During Static analysis, the pattern will be detected, like opcodes or byte sequence, string signature, byte sequence n gram or opcodes n grams, etc. Under Dynamic analysis, the behaviour of malware will be observed by utilising tools such as Wireshark, Process Explorer,andCaptureBAT,etc.tomonitorthefunction,the networkandtheflowofdata.Althoughthisanalysisismore effective, it is both time and resource consuming as comparedtothestaticanalysis.
Although these methods are able to detect unknown malwares, it produces more amount of false positive than signature basedmethod(Nawroozi&SaravanaGuru,2020). Variousvendorsofantivirus,therefore,useahybridmethod ofanalysiswhichincludesboththemethods(i.e.heuristic
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page29
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
andsignature based)forimprovedrecognitionofunknown malware. Machine learning and Deep learning are the concepts lately being used and implemented for the detection of malware. Therefore, due to the wider applicability of these techniques in this field, much of the successcanbeattributedtoDeeplearningmethodssuchas Convolutional Neural Networks (CNN) (Apruzzese, Colajanni,Ferretti,Guido,&Marchetti,2018).
CNNsconsistoflayersthatarereferredtoasconvolutional layers,poolingandnon linearlayers.Thefirstlayerwhichis aninputlayermovestheinputsamplestoCNN'sfirstblock, thuspassingthedatathroughthenetworktothelastlayeris thekey.ForthesystemstouseArtificialIntelligentsystems correctly and securely, each block must be flawlessly authenticated.TheCNNmodelwillmisstheaccountability foreachblockand,hence,blockchaincanbebeneficial(Gu, etal.,2018).Blockchaintechnologyoffersincreasedsecurity whichcanbeleveragedinsecuringthelocalnetworks(Raje, Vaderia,Wilson,&Panigrahi,2017).
Blockchain can support the safe implementation of AI systemsinthepublicdomainwithitsuniquefunctionslike dataprivacy,transparency,safety,andauthentication.The security element ensures that the network architecture is not manipulated or tampered with. Also, it works on an ArtificialIntelligentsystem.Thedecisionpropertywhichis made by a specific block of an AI model would require validationofotherblocksconnectedtotheblockinconcern. Thisisknownasauthentication(Ye,Li,Adjeroh,&Iyengar, 2017).Blockchainhelpstoachievehigherdetectionaccuracy isreceivedinalimitedtime(Investopedia,2022).
Itispossibletoevadetheattackintheapplicationmethod fordiscoveryandclassificationwiththeproperdeployment of blockchain technology. It is no more possible to manipulateanylayerinCNNduetothealarmbeingraised.It willbesupportedbyfeatureextractionandmatchingusing cryptographyandtransitivehash.Anymodificationinany layerwillraisealarms.Ifanyoperationexecutedataspecific block is malicious, the system can be restored at the previous checkpoint. Moreover, the decentralization attributepromisesthatnotallcontrolsaresituatedwitha singleentity.
Theafore mentionedcharacteristicsareapre requisiteto offerasecuremodeloftheDeepNeuralNetwork(DNN)and making blockchain a suitable candidate for the job of detection of malware. In the study, an effort is made to suggestanarchitecturethatderivethebenefitsofCNNwith blockchaintechnologycharacteristics.Thearchitecturecan detectmalwareattackthatiscarriedoutatthelevelofthe parameterorattheleveloffeatureextraction.Theaddition ofblockchaininCNNcaneffectivelyeliminatenetworklevel attackonCNN.Thetamperingvulnerabilitydoesnotexistif CNNmodelsareusedwithblockchain.
Classification of malware can be referred to the classificationoffilesintomalwareandbenignfiles(Hassen, Carvalho,&Chan,2017).Basedontheexecutionofmalware, themalwaredetectionmethodisseparatedintostaticand dynamicanalysis (Cosma&Joy,2012).Moreover,aHybrid approach,thatusethevariedfeaturesfromboththestatic and dynamic analysis are combined, also, exists (Ahmadi, Ulyanov, Semenov, Trofimov, & Giacinto, 2016). The static analysismethoddirectlyevaluatestheextractedfeatureof binarycodeorsourcecode(Tahan,Rokach,&Shahar,2012).
Techniques based on Deep Learning are gaining popularityforthefeatureextraction.Numerousstudieshave focused and successfully implemented Deep Learning Techniquesviz.DeepNeuralNetworks(Saxe&Berlin,2015), DeepBeliefNetworks(David&Netanyahu,2015),Recurrent NeuralNetworks(Pascanu,Stokes,Sanossian,Marinescu,& Thomas, 2015) and combination of Recurrent and Convolution Neural Networks for supervised learning and classification (Kolosnjaji, Zarras, Webster, & Eckert, Deep learningforclassificationofmalwaresystemcallsequences, 2016).Likewise,DeepBeliefNetworks(DBN),StackedAuto EncodersorAutoEncodersandRNNbasedAuto Encoders (RNN AE) have been used for optimal feature extraction (Wang&Yiu,2016).
Theapplicationofneuralnetworkhasbeeninusesince 1960 in various regions of Machine Learning, namely computervision,handwritingrecognitionandclassification of images. In the year 2012, AlexNet was proposed by Krizhevsky, which championed the ImageNet competition (Singh,2017).ItiscreditedwiththefamegainedbyCNNas thefocusofMachineLearninginacademicfieldandattracted the interest of researchers (Nataraj, Karthikeyan, Jacob, & Manjunath,2011).Itwasabreakthroughinimageandvoice process field. The CNN has much better accuracy than humans, especially in the field of image classification (Schmidhuber,2015).
CNNhasadistinctcalculusprocessinconvolutionallayer, poollayerandfullconnectedlayer(Krizhevsky,Sutskever,& Hinton, 2012) (White, Tufano, Vendome, & Poshyvanyk, 2016)(Huang,Al Dujaili,Hemberg,&O’Reilly,2018).Using thevariousstackmethod,convolutionalneuralnetworkcan beusedfortheconstructionofdifferentstructuresthatcan beappliedindifferentfieldsofresearch(Chen,Wang,Wen, Lai,&Sun,2019).
(Su, Vasconcellos, Prasad, & Sgandurra, 2018) suggested a light weight novel method for detection DDos malware in IoT environment. Frist, they extracted one channelwheregray scaleimageisconvertedfrombinaries then used a light weight convolution neural network to classifyIoTmalwarefamilies.Accordingtotheirexperiment resultstheygaineditis94.0%accuracyfortheclassification oftheDDosmalware.Itshowedsignificantresult.
Inthestudy(Prasse,Machlica,Pevný,Havelka,&Scheffer, 2017)createdamethodthatallowsthemtogathernetwork flowsofbenignapplicationandknownmalwareastraining
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
dataandthentheyappliedamethodfordetectionofmalware which it is based on a neural language method and long short term memory network (LSTM). The approached methodcandetectnewmalware.
The authors (De Paola, Gaglio, Re, & Morana, 2018) proposedanovelmethodbasedonthedeepnetworks.First, theyrunmalwareinthesandboxenvironmentandafterthis theywillconvertthelogfileofsandboxtoalongbinarybit string file. It is fed to a deep neural network with eight layeredthatproduced30valuesintheoutputlayer.These values as signature produced by the DBN which is very successfulfordetectingofmalware.Andtheadvantageofthis algorithmisthatitcanbeusedforthesupervisedmalware classification. In this paper, the proposed method is the cloud basedmalwaredetectionsystem.Thismethodisable to analysis big data which produced on the network. This systemprovidesafastclassificationthatisbasedonthestatic analysisthatuseddeepnetworks.Andwhenthedetection reachesuncertaintyexceedagiventhresholdthenitwilluse dynamic analysis and the result of dynamic analysis is exploited to refine the deep network in the continuous learningloop.Andtheadvantageofthissystemisthatitwill beuptodatethatwilldetectnewmalwareversions.
In the study by (Kolosnjaji, Zarras, Webster, & Eckert , 2016),amethodwasfeaturedandwasimplementedbased ontheCNNandacurrentnetworklayer,whichcameoutto be one of the best for malware image detection. A full convolutionofn gramswascombinedasasequentialmodel inextractionofthemodel.Theaverageaccuracywasfrom 85.6%to89.4%
(Abdelsalam, Krishnan, Huang, & Sandhu, 2018) in their work, they introduced a malware detection approach for virtual machines based on two dimensional convolution neuralnetworksbyutilizedperformancemetrics.Theresult fromthetestingdatasetshowedthattheygainaccuracyof 79% and they also used 3D CNN model to improve the detection performance which used samples over a time windows,andafterapplying3Ddimensiontothe2Dinput matrixtheachievedresultwasabove90%thatisasignificant outputresult
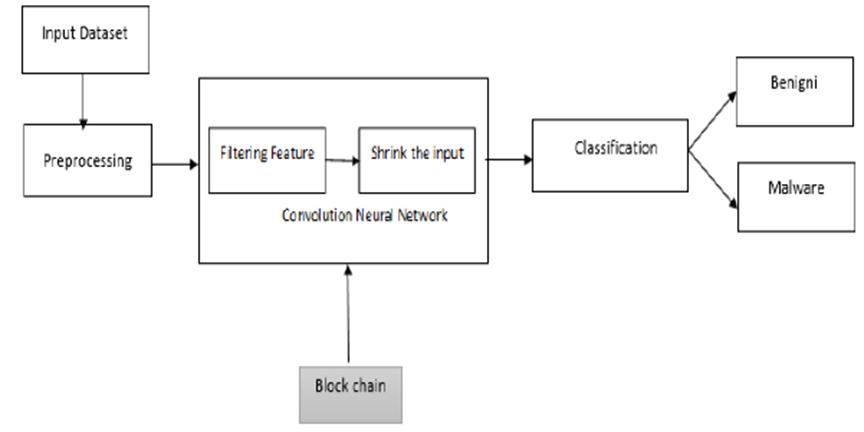
The process of detection and classification of malware basedonSBCalgorithmisdescribedinFig1.Itstartswith theinputdatasetwhichincludesmalignandbenigndatasets. Thedatasetwillpreprocessandlabelasmalwareorbenign. The processed data will be forward as input for the convolution neural network then the algorithm would classify to the mentioned classes. As shown in the above diagram, the vulnerability exists in CNN method during filtering the features and shrinking the input that the attacker can easily modify it and it affects the result of detection.Therefore,theblockchaintechnologyisappliedto avoid it. Each layer of CNN stored in each block and each blockwouldhaveitsownhashvalueandthepervioushash valueofblock.UsingCNNmethodeachgrayscaleimageof
value:
malwarewillanalyzeonebyonebasedonthetrainandtest model.
TheMalimgdataset[6]usedinthisworkconsistsofimage malwarealongwiththebenignimage.Thebinarymalwareis changedtothegrayscaleimageandthereispythonscript which converts binary malware into the grayscale image usingNumpylibrary.Inthiswork,thegrayscaleimagehas useddirectlyasinputtoCNNmodeltotrainthedataandto classifyit.
Fig 1:Processofdetectionandclassificationofmalware
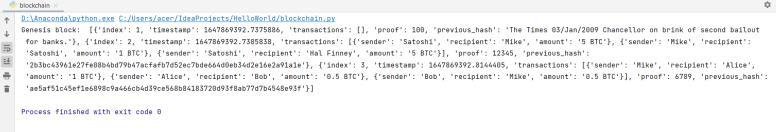
As it is shown in the Fig 2, it is the architecture of designed algorithm which the input phase is explained already in Fig 1. And after preprocessing the dataset into trainandtestdata..Thenextphaseismakeupoftwofold process that it is Blockchian and Convolution Neural Network.Firstly,theblockchainiscreatedandeachlayerof theCNNisstoredasdatainblockchain. EachlayerofCNN wouldhavesamefunctionwithdifferentvaluesandahash value,thenthenextstepisthevalidationofthehashvalue whichwillcheckifitisvalid.Ifitisinvalidtherearesome changesinthesystemthatwouldnotapplyCNNalgorithm anditshowsthemassagewhichisinvalid.Ontheotherhand ifitisvalidtheCNNmethodforanalyzingandclassifyingthe inputisapplied.Theblockchaintechnologyisexplainedin theupcomingcontentwithCNNalgorithmindetail.
Isadistributedmodelwhichstoresthedatabetweenblocks andaccordingtothisprojecteachfunctionofCNNstoredas datainblocks.Thestoreddataisimmutableandpermanent thatcanbeeasilyverified.Theblockchainismostlyusedin crypto currenciesandbasicallybuiltfromblocks;therefore itisnotrelateddirectlytoCNNinprior.Recentlythereare manyresearchesinthispartofdifferentfieldssuchashealth care,smartenergyandgridsthatshowsblockchainhaving goodpotentialandsignificantoutput.
TheblockchainstructuredeterminedinFig3isdescribedas follows[11]:
Data: The stored data in blockchain depends on the application.Inthismodel,thestoreddataineachblockisthe Layer of convolution neural network components such as convolutionandmax poolingfunction.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
Hash: A hash function takes any length of input and generates the output with fixed length and unique. The output would be different if a single value of input is modified and no matter the change is big or small, for instance if someone modified a single character of the convolution neural network layer which is hashed in the block then the modified block would have different hash valuescompletely.Thisincreasedandimprovedthetrustof datasavedin blockchain.
Pervious Hash:thisisthehashvalueofthepreviousblock which is stored in the current block to make sure the validation of block is correct. The same process would continue up to the end of blockchain and each of the pervious hash value will combine with the current hash valueofblock.
Timestamp:Itisusedtorecordthetimeofcreatingofthe block.Thisisamethodtotrackthemodificationorcreation timeoftheblockinasecureway.
The convolutional layer: This layer is the main part of a CNN.Itisextractingthefeaturesfromtheinputimageand sending it to the next level, then the extracted features valueswillmultiplywiththeoriginalpixelvaluesinthefilter part. Here, we used fifth convolution filters of size 32,64,128,64,32andthevectorsizeis5foreachconvolution layer.
Rectified linear unit (ReLU) layer: In this layer, all the negativevalueswillberemovedfromthefilteredimageand willreplaceitwithzero.Itwillbedonetoavoidthevalues formsumminguptozero.Transformedfunctionisactivated only when a node if the input is above a certain quantity, whiletheinputisbelowthezerothenthevaluewillbezero.
Pooling layer: Pooling is a non linear method of down sampling. For implementing the pooling layer there are manynon linearfunctionsliketheminimum,maximumand theaveragebutthemaximumisthemostcommonone.In themaximumpoolingfunctiontheimagewillpartitionintoa groupofnon overlappingrectanglesandthemaximumvalue is the output of each sub region and in this algorithm for reducingthedimensionalityofthedata,thefactorvalueis5.
Fully Connected layer: Theresponsibilityofthislayeristo classifytheimageintoalabelbyusingtheoutputfromthe poolingprocesslayer.Thefilterofshrunkimagewouldput intoasinglelist.Toidentifythemostaccurateweights,the fullyconnectedlayergoesthroughitsownbackpropagation process. To prioritize the most appropriate label, it is according to each neuron weights received. The classificationwillbedoneaccordinglytowardstheendofthe process. The fully connected layer is a classic multi layer resultant in the output layer with a softmax activation functionandafterthisweuseddropoutmethodtoprevent overfitting.
Theprocessflowdiagramandthearchitectureforthestudy isgivenbelow:
1.3
Fig 3:SBCArchitecture
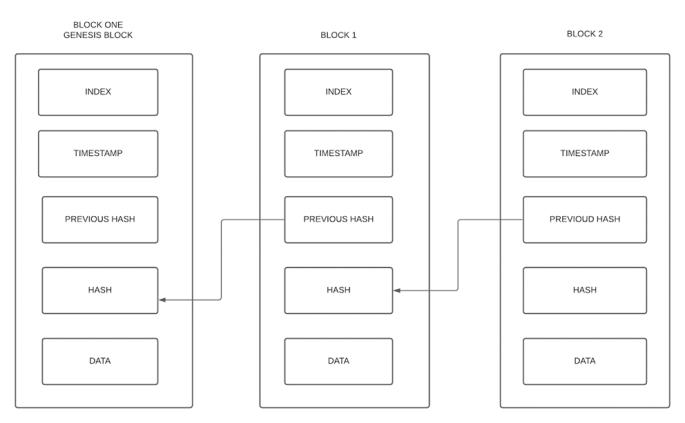
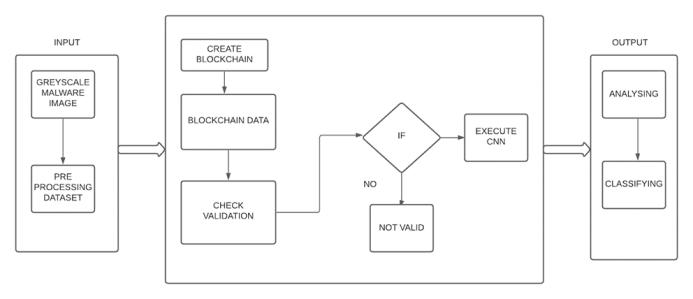
Fig-4:BlockchainArchitecture
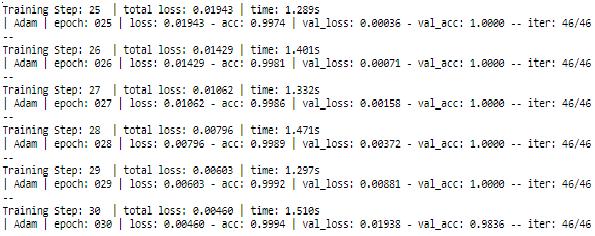
Inthissection,theexperimentresultoftherobustnessand validityofthepurposedalgorithmisdiscussed.Herethe experimentofthisprojectisdeployedinpython3.7.We hadperformed30iterations.Ineverylayer,differentfilter valuesareusedandtherectifiedlinearunit(ReLU)isused asactivationfunction.Thisalgorithmtakeslesstimefor thecalculationprocessoftrainingandtheaccuracyis higher.
Table 1 Accuracy and Loss of SBC Algorithm
Accuracy 0.99 Loss 0.00460
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
Theaccuracyisincreasedineachapproachandthefinal accuracyis0.99asshownintheabovetableandthelossis 0.00460inthelastiteration.
[2] Ahmadi, M., Ulyanov, D., Semenov, S., Trofimov, M., & Giacinto,G.(2016).Novelfeatureextraction,selection and fusion for effective malware family classification. ProceedingsoftheSixthACMConferenceonDataand Application Security and Privacy, CODASPY '16, 183 194.
[3] Apruzzese, G., Colajanni, M., Ferretti, L., Guido , A., & Marchetti, M. (2018). On the effectiveness of machine and deep learning for cyber security. 2018 10th InternationalConferenceonCyberConflict(CyCon),(pp. 371 390).Tallinn.
[4] AV TEST. (n.d.). Malware. Retrieved March 14, 2022, fromhttps://www.av test.org/en/statistics/malware/

[5] Chen,C. M.,Wang,S. H.,Wen,D. W.,Lai,G. H.,&Sun, M. K.(2019).ApplyingConvolutional Neural Network for Malware Detection. 2019 IEEE 10th International Conference on Awareness Science and Technology (iCAST),1 5.
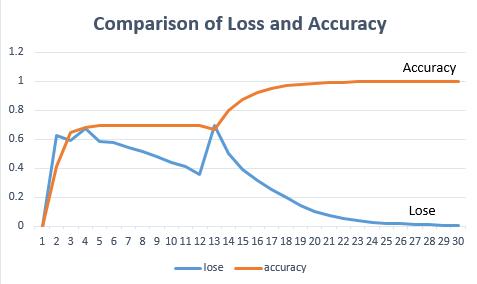
Fig 8 Loss and Accuracy Result Graph Fig 9. Malware and Benign image Result Thefollowingoutputwasobtainedup Fig 8: BlockchainOutput
Thedatasetplaysaverycrucialrolefortheclassification, objectdetectionandsegmentationfortheclassificationof malware. Preprocessing images is a very crucial task in image processing since accurate malware identification is onlyattainablebydetectingbackgroundnoise.
The proposed project makes use of CNN and blockchain technology.
[1] Abdelsalam, M., Krishnan, R., Huang, Y., & Sandhu, R. (2018). Malware Detection in Cloud Infrastructures Using Convolutional Neural Networks. 018 IEEE 11th InternationalConferenceonCloudComputing(CLOUD), (pp.162 169).
[6] Cosma,G.,&Joy,M.(2012).AnApproachtoSource Code Plagiarism Detection and Investigation Using Latent Semantic Analysis. IEEE Transactions on Computers, 61(3),379 394.
[7] David,O.E.,&Netanyahu,N.S.(2015).DeepSign:Deep learning for automatic malware signature generation andclassification.2015InternationalJointConference onNeuralNetworks(IJCNN),1 8.
[8] DePaola,A.,Gaglio,S.,Re,G.L.,&Morana,M.(2018).A hybridsystemformalwaredetectiononbigdata.IEEE INFOCOM 2018 IEEE Conference on Computer Communications Workshops (INFOCOM, (pp. 45 50). Honolulu,HI.
[9] Gandotra, E., Bansal, D., & Sofat, S. (2014, April). MalwareAnalysisandClassification:ASurvey.Journalof InformationSecurity,5(2),56 64.
[10] Gu,J.,Sun,B.,Du,X.,Wang,J.,Zhuang,Y.,&Wa,Z.(2018). Consortium Blockchain Based Malware Detection in MobileDevices.IEEEAccess,6,12118 12128.
[11] Hassen, M., Carvalho, M. M., & Chan, P. K. (2017). Malware classification using static analysis based features. 2017 IEEE Symposium Series on ComputationalIntelligence(SSCI),1 7.
[12] Huang, A., Al Dujaili, A., Hemberg, E., & O’Reilly, U. M. (2018).AdversarialDeepLearningforRobustDetection of Binary Encoded Malware. 2018 IEEE Security and PrivacyWorkshops(SPW),(pp.76 82).
[13] Investopedia. (2022, March 5). Blockchain Explained. Retrieved from https://www.investopedia.com/terms/b/blockchain.as p
[14] Kolosnjaji,B.,Zarras,A.,Webster,G.,&Eckert,C.(2016). DeepLearningforClassificationofMalwareSystemCall Sequences. Australasian Joint Conference on Artificial Intelligence,(pp.137 149).
[15] Kolosnjaji,B.,Zarras,A.,Webster,G.,&Eckert,C.(2016). Deeplearningforclassificationofmalwaresystemcall sequences.AI2016:AdvancesinArtificialIntelligence, 137 149.
[16] Krizhevsky, A., Sutskever, I., & Hinton, G. E. (2012). Imagenetclassificationwithdeepconvolutionalneural networks. Proceedings of Advances in Neural Information Processing Systems (pp. 1106 1114). Cambridge:MITPress.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 07 | July 2022 www.irjet.net p ISSN: 2395 0072
[17] Nataraj,L.,Karthikeyan,S.,Jacob,G.,&Manjunath,B.S. (2011). Malware images: visualization and automatic classification.InternationalSymposiumonVisualization forCyberSecurity(VizSec),1 7.
[18] Nawroozi, S., & SaravanaGuru, R. K. (2020, March). Design of Secure Blockchain Convolution Neural Network Architecture for Detection Malware Attacks. International Journal of Recent Technology and Engineering(IJRTE),8(6),3055 3060.
[19] Pascanu,R.,Stokes,J.W.,Sanossian,H.,Marinescu,M.,& Thomas, A. (2015). Malware classification with recurrent networks. 2015 IEEE International ConferenceonAcoustics,SpeechandSignalProcessing (ICASSP),1916 1920.
[20] Prasse,P.,Machlica,L.,Pevný,T.,Havelka,J.,&Scheffer, T. (2017). Malware Detection by Analysing Network TrafficwithNeuralNetworks.2017IEEESecurityand PrivacyWorkshops(SPW),(pp.205 210).SanJose,CA.
[21] Raje, S., Vaderia, S., Wilson, N., & Panigrahi, R. (2017, November). Decentralised firewall for malware detection.2017InternationalConferenceonAdvances inComputing,CommunicationandControl(ICAC3),(pp. 1 5).
[22] Saxe,J.,&Berlin,K.(2015).Deepneuralnetworkbased malware detection using two dimensional binary programfeatures.201510thInternationalConference onMaliciousandUnwantedSoftware(MALWARE),11 20.
[23] Schmidhuber, J. (2015). Deep learning in neural networks:Anoverview.NeuralNetworks,61,85 117.
[24] Sewak, M., Sahay, S. K., & Rathore, H. (2018, June). ComparisonofDeepLearningandtheClassicalMachine Learning Algorithm for the Malware Detection. 2018 19thIEEE/ACISInternationalConferenceonSoftware Engineering, Artificial Intelligence, Networking and Parallel/DistributedComputing(SNPD),293 296.
[25] Singh, A. (2017). Malware Classification using Image Representation.Department ofComputerScienceand Engineering,IndianInstituteofTechnologyKanpur.
[26] Statista. (2022, February 3). Security software Statistics & Facts. Retrieved March 13, 2022, from https://www.statista.com/topics/2208/security software/
[27] Su, J., Vasconcellos, D. V., Prasad, S., & Sgandurra, D. (2018).LightweightClassificationofIoTMalwareBased on Image Recognition. 2018 IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC),(pp.664 669).Tokyo.
[28] Tahan, G., Rokach, L., & Shahar, Y. (2012). Mal ID: AutomaticMalwareDetectionUsingCommonSegment Analysis and Meta Features. Journal of Machine LearningResearch13,13,949 979.
[29] Wang, X., & Yiu, S. M. (2016). A multi task learning modelformalwareclassificationwithusefulfileaccess patternfromAPIcallsequence.
[30] White, M., Tufano, M., Vendome, C., & Poshyvanyk, D. (2016). Deep learning code fragments for code clone detection. Proceedings of the 31st IEEE/ACM International Conference on Automated Software Engineering,(pp.87 98).Singapore.
[31] Ye,Y.,Li,T.,Adjeroh,D.,&Iyengar,S.S.(2017,June).A survey on malware detection using data mining techniques.ACMComputingSurveys(CSUR),50(3),1 40.
2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal
