International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN: 2395 0072
Siva ramu1 , Surya2 , Vikraman3 , Sivasakthi4
1N.Siva ramu, Dept. of Information Technology, AAMEC, Tamilnadu, India
2M.Surya,Dept.of Information Technology, AAMEC, Tamilnadu, India
3R.Vikraman,Dept.of Information Technology, AAMEC, Tamilnadu, India
4Mrs.V.Sivasakthi, Asst .Prof., Dept. of Information Technology, AAMEC, Tamilnadu, India ***
Abstract - Safety, and security are major concerns in the modern day. People and organizations can employ security mechanisms to safeguard their property be it home or company. Present security systems involve the utilization of assorted sensors for cameras for video surveillance. This project aims at providing one such idea to make sure the protection and security of one's property. this technique performs face recognition as an authentication procedure when an unknown face is detected by a snapshot of the unknown face. during this paper, we propose to supply a sensibleCCTVclosed circuittelevisionwithintrusiondetection using the LBPH algorithm and structural similarity index measure. By the utilization of intrusion detection, CCTV camerasnotonlyrecordthereal timevideosandalsoprocess the video at the time of recording to search out the unwanted persons arriving within our surveillance area.
Key Words: Computer vision, authentication, intrusion detection, LBPH, SSIM , surveillance area.
The development of technology associated with the processing using a computer is already growing rapidly, whereas image processing is using digital technology. As technology advances, graphic images are fully utilized to marketthewelfareofmankind.togetherwiththeeventof creativity,theimagecannotbeseparatedfromdigitalimage processing. Most of the CCTV footage is employed for bufferingpurposes.Ifanyissues/eventsoccurCCTVFootage isusedtodeterminethecriminal.CCTVswillonlycapture the events/incidents but don't seem to be capable of recognizingacriminal.Nowalmostaltogetherplaces,CCTVs areused.they'reonlyusedforcapturinglivevideooccurring underitspremises.Inmostcases,anindividualisdeployed to watch the video streaming. And in another case, video capturedbyCCTVsisrecordedandit'llbecheckedgiventhat anyincidenthadoccurred.
There was a time when surveillance techniques were utilizedonlyinshoppingcentersandmalls.Nowadays,you cannoticetheelectriccircuittelevisionsinalmostanyplace youvisit,fromtinylowstorestohomesandholyplaces.Asa
result, they guarantee greater security at fraction of the price.
Inourbusylives,wedonothavemuchtimetoobserveand tostayawatchoneverything.Fromeveryfamily,mostofthe membersareworking,ormaybeinmallsandhospitalsso observing each and each space isn't possible. It’s the 21st centuryandwemustthinksmartlytoformourlifebetter, easier,andmoresecure,soratherthansittingwithoutdelay placeforanextendedwhynotcarrytheprotectioninour pocket.
LBPHmay bea face recognitionalgorithm it'saccustomed recognizethefaceofsomeone.it'sknownforitsperformance andthewayitcanrecognizethefaceofsomeonefromboth the front face and side face. Before starting the intuition behindtheLBPHalgorithm,let'sfirstunderstandatouchbit aboutthefundamentalsofImagesandpixelstograsphow images are represented before we start the content about face recognition. So let’s start understanding images and pixels.
It is an apperception based model that considers image degradationasaperceivedchangeinstructuralinformation, whilealsoincorporatingimportantperceptualphenomena, includingbothluminancemaskingandcontrastmasking.The difference with other techniques like MSE is that these approachesestimateabsoluteerrors.Itisthethoughtthatthe pixelshavestronginterdependenciesespeciallyaftertheyare close.Thesedependenciescarryimportantinformationabout the structure of objects within the display. Luminance masking could be a phenomenon whereby an may be less visibleinbrightregions,whilecontrastmaskingcouldbea phenomenon whereby distortions lessen visibility where there'samajoractivity.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN: 2395 0072
3.1 Hybrid algorithm formulti people counting and tracking for smart surveillance, Mahwish Pervaiz, Ahmad Jalal, Kibum Kim,2021.
Inpeopleverification,wehaveappliedahybridapproachof skin detection and body parts detection to intensify the accuracy level and reduce the error rate. During skin detection,themaskoftheoriginalimagehasbeencreated andappliedtotheobjectdetectedtoconvertthemintoan RGB image. This RGB image is further converted to the YCbCrdomainandpixelvaluesareusedtodetectskinpixels ineachobject.Forpartdetection;thehead,hands,andfeet ofeachsilhouetteareextracted,thedistancebetweenthese partsisidentified,andaccustomedtoverifytheobjectasa human.Peoplecountingareimplementedusingthecentroid ofeachsilhouettethat'sextractedateachframeandmoving objects are identified among consecutive frames. In body tracking, centroid and jacquard similarity are accustomed trackpeople'smovementsbetweenframes.
3.2
Algorithm forIntelligent Traffic television,Chethan Kumar B, Punitha R, Mohana,2020.
Deep convolutional neural networks (DNNs) are used to detect objects within the regions. In the proposed implementation,theCNNalgorithmisusedtopredictclass labels and detect objects Methodology of implementation, consistsofdataCollection:Thechosendatasetisavehicle detectiondatasetforurbanroads.itisimportantbecausethe qualityandquantityofdatawilldirectlydeterminehowwell thetrainedmodelwillbehaveundervariousenvironmental conditions.
3.4 an internet of Things Based Smart Surveillance and Monitoring System using Arduino, Aditya, Mukul Sharma, Subhash Chand Gupta,2018.
The latest and most effective technology used against robbery and theft is video surveillance and a monitoring system. But the worth of installation and maintenance of thesesystemsbecomesimpossibleforsomepeopletoafford. ArduinoMega2560couldalsobeamicrocontrollerboard thathasthepotentialtobecomeacamerasystemwhenits mini modulecalledArducamgetsattachedthereto.instead ofimplementingvariouscomplexalgorithms,areplacement andeffectivemethodologyhasbeendevelopedformotion detectionwhichistousePyroelectricinfrared(PIR)sensors. Whenever the motion is detected by the PIR sensor, WhenevermotionisdetectedbyPIRsensor,itcapturesthe image with the help of an attached Arducam and sends a pushmessagetoAndroidusingtheFirebaseAPI.
3.5 IoT Based Smart Surveillance Security System using Raspberry Pi, Neha Patil,Shrikant Ambatkar, and Sandeep Kakde,2017.
3.3 Multi Person
in Smart television system for Crowd Counting and Normal/Abnormal Events Detection, Ahsan Shehzad, Kibum Kim,2019.
Inthispaper,wedevelopedacurrentrobustsmarttelevision to trace multiple people's overcrowding counting and normal/ abnormal event detection scenarios via a monocular camera. An accurate people detection and verification model is utilized to detect people. These detectedpeoplearefurtherprocessedtocomebackupwith headtemplates.Templatematchingusingnormalizedcross correlation with the assistance of the Jaccard similarity measure is utilized to trace and count the people. Finally, detectedpeopleareaccustomedgenerateGaussianclusters toresearchthegangforabnormaleventdetections.
The purpose of the paper is to define a safekeeping alert device spending little handling power by the Internet of thingswhichassiststoobserverplusalertswhengestures insteadmotionarethereandthensendsimagestoacloud server.Besides,internetofthingscentereduseisoftenused continuously to look at the action further and acquire a warningwhengesturesasanalternateindicationarethere. theimagesareshownstraighttoacloudattendant,whenthe cloudattendantisn'taccessibleatthattimetherecordsare putinstoragenearbyonaRaspberryPi.AMasterCardsize RaspberryPiwiththeadvantageofOpenSourceComputer Vision (Open CV) software knobs the image processing, control algorithms used for the attentiveness then shows takenimagestoconcernedpersonemailbytheutilizationof Wi Fimodule.Thesystemusesanordinarywebcam.
StructuralSimilarityIndexMetric(SSIM)formonitoringThis feature is employed to seek out what's the thing which is stolenfromtheframewhichisvisibletothewebcam.This meansItconstantlymonitorstheframesandcheckswhich objectorthingfromtheframehasbeenbumpedoffbythe thief. This uses Structural Similarity to seek out the differences between the two frames. the 2 frames are captured first when noise wasn't happening and second whenthenoisestoppedhappeningwithintheframe.SSIMis employed as a metric to live the similarity between two given images.Asthissystemhasbeenaroundsince2004, lotsoffabricexistsexplainingtheideabehindSSIMbutonly a few resources pass into the main points, that too
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN: 2395 0072
specificallyforagradient basedimplementationasSSIMis commonlyusedasalossfunction.
SSIMextracts3keyfeaturesfromanimage:
• Luminance
• Contrast
• Structure
Thecomparisonbetweenthe2imagesisperformedonthe thepremiseofthose3features.Thissystemcalculatesthe Structural SimilarityIndex between2 givenimages which couldbeavaluebetween 1and+1.aworthof+1indicates thatthetwogivenimagesareverysimilaroridenticalwhile the worth of 1 indicates the two given images are very different. Often these values are adjusted to be within the range[0,1],wheretheextremesholdtheidenticalmeaning.
Luminance: Itismeasuredbyaveragingoverallthepixel values.
Luckily,duetotheimagepackageinpython,we shouldn’t replicateallthesemathematicalcalculationsinpythonsince theimagehaspre builtafeaturethatdoesallofthosetasks for us by just calling its in built function. We just must enclosetwoimages/frameswhichwe'vecapturedearlier,so wejustfeedtheminanditgivesusoutthemaskedimage withthescore.
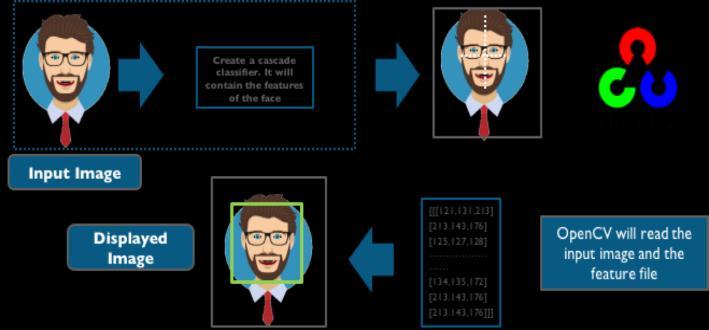
ThisisdonethroughHaarcascadeclassifierswhich areagainbuilt inintheOpenCVmoduleofpython.
Itsdenotedbyμ(Mu)andalsotheformulaisgivenbelow.
Cascade classifier working with haar like features, is a specialcaseensemblelearningcalledboosting.Ittypically reliesonAdaboostclassifiersCascadeclassifiersaretrained onafewhundredsampleimagesthatcontaintheobjectwe wanttodetectandotherimagesthatdonotcontainthose images.
Therearesomecommonfeatures: adarkeyeareacomparedtouppercheeks. a bright nose bridge region compared to theeyes. somespecificlocationsoftheeyes,mouth, andnose.
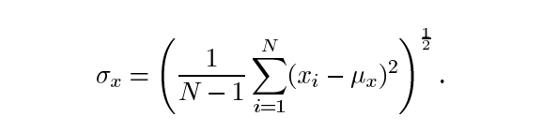
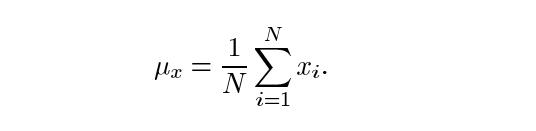

Structure: The structural comparison is completed by employingaconsolidatedformula(morethereonlater)but inessence,wedividethesignalingwithitsvariancesothat theresulthasunitvariancewhichallowsforamorerobust comparison.
Thefeatureextractionprocesswilllooklikethisfeatureare similartothisconvolutionkernelwhichisusedtodetectthe presenceofthefeatureinthegivenimage.Fordoingallthe stuffintheOpenCVmoduleinpythonlanguagehasabuilt in function called cascade classifier which we have used to detectfacesinthisframe.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN: 2395 0072
Thisfeatureisusedtofindthenoisesintheframeswellthis issomethingyouwouldfindinmostoftheCCTVsbutinthis module,we’llseehowitworks.Talkinginasimplewayall the frames are continuously analyzed and checked for noises.Noisecheckedintheconsecutiveframes.Wesimply makeacompletedistinctionbetweentwoframes,inthisway thedistinctionbetweenthetwoimagesisanalyzed,andthe edges(boundariesofmotionaredetermined)andifthere arenoboundariesthennomotion,andifthereareanythere ismotion.
Neighbors: the number of sample points to make the circularlocalbinarypattern.detainmind:themoresample points you include, the upper the computational cost. it's usuallysettoeight.
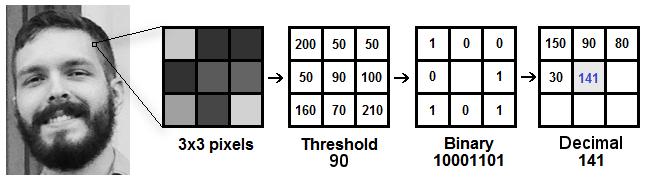
Grid X:thenumberofcellswithinthehorizontaldirection. The more cells, the finer the grid, the upper the dimensionalityoftheresultingfeaturevector.it'susuallyset toeight.
Grid Y:thenumberofcellswithintheverticaldirection.The more cells, the finer the grid, and the upper the dimensionalityoftheresultingfeaturevector.Itisusually settoeight.ThefirststepincalculatingLBPHistocreatean intermediateimagethatbestdescribestheinitialimage,by highlightingthefacialcharacteristics.Todoso,thealgorithm uses an idea of a window, supported by the parameters radiusandneighbors.Thisisshownperfectlyviatheabove image.
Asyouwouldknowallimagesarejustinteger/floatvalues of pixels which tell the brightness of pixel and similarly everypixelhasvaluesofbrightness.
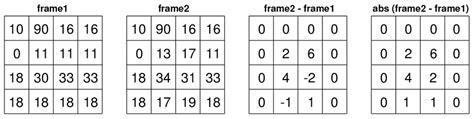
Sowearesimplymakingacompletedifferencebecausethe negativemakesnosense.
Sonowwe'vedetectedfaceswithintheframeandthiscanbe the time to spot them and check if it's within the dataset whichwasaccustomedtotrainingourLBPHmodel.
TheLBPHuses4parameters:
Radius: the radius is employed to make the circular local binarypatternandrepresentstheradiusaroundthecentral pixel.it'susuallysetto1.
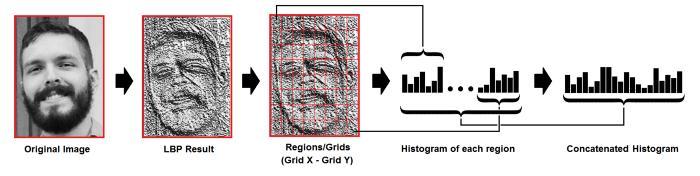
Extracting the Histograms: Now, using the image generated within the last step, we can use the Grid X and GridYparametersto divide theimageinto multiplegrids. Andonbalance,themodelistrained,andlateron,whenwe would like to create predictions the identical steps are appliedtothemak,e,anditshistogramsarecomparedwith thealreadytrainedmodelinsuchawaythisfeatureworks.
Intheend,weconcludethateachpersonwantstobeinan exceedinglybetterandsecureworld,thispaperhascovered theadvantagesanddownsidesofeachpaperthathasbeen publishedtothispoint.Toproducebettersecurityandsafety newsystemwasimplementedusingLBPHandSSIMandalso which are cost effective and form better further research goes on Below are future workouts on this project, like [1]Creating Portable CCTV [2]Adding in built night vision capability[3]Deadlyweapondetection[4]Accidentdetection [5]FireDetection.
[1] A hybrid algorithm for multi people counting and tracking for smart surveillance, Mahwish Pervaiz, AhmadJalal,KibumKim,2021
[2] PerformanceAnalysisofObjectDetectionAlgorithmfor IntelligentTrafficSurveillanceSystem,ChethanKumar B, PunithaR,Mohana,2020.
[3] Multi PersonTrackinginSmartSurveillanceSystemfor Crowd Counting and Normal/Abnormal Events Detection, AhsanShehzad, KibumKim,2019
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | June 2022 www.irjet.net p ISSN: 2395 0072
[4] Multi PersonTrackinginSmartSurveillanceSystemfor Crowd Counting and Normal/Abnormal Events Detection, AhsanShehzad, KibumKim,2019.
[5] IoT Based Smart Surveillance Security System using Raspberry Pi, N Neha Patil, Shrikant Ambatka,r and SandeepKakde,2017.
[6] Smart Video Security Surveillance with Mobile Remote Control by Tasleem Mandrupkar Manisha KumariRupaliMane(2014).

[7] VideoMonitoringandMotionDetectionSystembased on arm Linux platform and HTTP protocol with SMS capabilityNavaJeevanRaju,O.andPraveen,P.(2014)
SivaramuN
B.TechInformationTechnology
Anjalai Ammal Mahalingam EngineeringCollege,Tamilnadu India.

SuryaM
B.TechInformationTechnology
Anjalai Ammal Mahalingam EngineeringCollege,Tamilnadu India.