International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p-ISSN: 2395-0072

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p-ISSN: 2395-0072
Sreejesh N. G.1, Sabina M. A.2
1P G Scholar, Department of Computer Science and Engineering, Rajiv Gandhi Institute of Technology, Kottayam, Kerala, India
2Assistant Professor, Department of Computer Science and Engineering, Rajiv Gandhi Institute of Technology, Kottayam, Kerala, India
Abstract - The word Software Defined Networks (SDN) came into limelight only a few years ago.Butithasbecomethe backbone for various popular network technologies such as data centers, cloudstorage,mobilecommunication,Internetof Things and even in small business environments, thankstothe flexibility, programmability, scalability and centralized coordination that brings to the entire network. Even though the introduction of SDN brought easiness in network management, it is susceptible to all the attacks that may happen in the traditional network. One suchcommonattackis saturation attack, means saturating the network resources using malformed packets. In happens in two forms; Denial of Service attacks and Distributed Denial of Service attacks. Many proposals have been brought since the evolution of SDN to detect and mitigate these attacks. This survey brings an overview of some of such proposals, their effectiveness and possible comparisons.
Key Words: Software Defined Networking, saturation attacks,DoS,DDoS,IoT,controlplane,dataplane,OpenFlow, northboundandsouthboundinterfaces.
Theevolutionofnetworkhasgonethroughdifferentphases beforereachingthefullyconnectedworld.The traditional networking scenario uses routers as the backbone of the network paradigm. Apart from it, gateways and switches make their specific roles wisely. Transfer a packet of data from a source to destination needs proper end to end connectivityandthroughthisconnection,physicalorlogical, packetsaretravelled.Thistransferneedsproperroutingand forwarding. The traditional network does this task in a fantastic manner with the help of different protocols and addressing schemes. The problem arises when some functionalities of the intermediate network need to be changed. This brings a tedious thing because; most of the functionalitiesarefixedintothenetworkdevices.Changing thefunctionalityrequirechangingthewholeorpartofthe networkdevices.Thiscausesheadachebothpracticallyand economically. Here comes the role of Software Defined Networking(SDN).
Anetwork devicecanhavea data planetoforwardthe incomingpackets,acontrolplanetomanageandcontrolthe
internalprocessingofthedevice,suchascreatingtherouting table, executing specific algorithms etc, and anapplication planetoaccessthedeviceeitherformonitoringthedevice, managing the control plane by the administrators or executing business specific applications. In the traditional network components such as routers and switches, the controlplaneandthedataplaneareinacombinedform.If the network does not need any change, this form is good method. But as the network technology advances more functionalityandchangesneedtobeincorporated.Hencethe controlplanemustbeseparatedfromthedataplane,asitis thecontrolplanewhichneedsreformationeverytime.
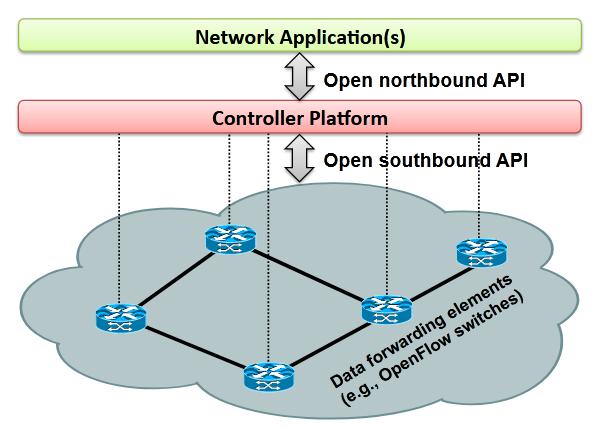
TheSDNtechnologyseparatesthecontrolplanefromthe data plane [1][10][14]. The data plane devices are simply forwardingdevices.Thecontrolplaneismostlyapowerful systemtowhichthedataplanedevicesareconnecteddirectly or indirectly.Thissystemiscalledthe SDN controller.The controlplanefunctionalitiesareprogrammedintotheSDN controller.ThisiswhytheSDNisaidtobeaprogrammable network.Onemajordutyofthecontrolleristoinstructthe forwarding device what to do with the incoming packets. Sincethemostcommonactionisforwardingthepackets,this device can be considered as a special type of switch. The application plane (otherwise called management plane) mostlyliesonthecontrolleritself,oritmaybeinasystem directlyaccessibletothecontroller.Theapplicationsareused tomonitorthenetworkanditsvariousparameters,business specificfunctionalitiesorasadministrativeaccesspathtothe controller.ThearchitectureofSDNisshowninFig.1[14].
The interface between the data plane and the control plane is called the southbound interface. The forwarding devices communicate with the controller through this interface. The packets that flow through this interface are generallypacket inmessages,packet outmessagesandflow modificationmessages.Theinteractionneedtofollowsome protocolsforeffectivecommunication.Theprotocolusedin the southbound interface is the OpenFlow protocol [2][3]. TheOpenFlowfollowsaneventbasedwayofcommunication. TheswitchesthatfollowtheOpenFlowprotocolarecalled OpenFlowSwitches,whichformsthedataplaneoftheSDN architecture.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
The interface between the control plane and the application plane is called the northbound interface. The protocol in this interface varies with the APIs used in the interface, and hence there is no specific protocol in this interface.
neednotbesenttothecontroller,savingthebandwidthin between.
TheSDNcontrollerrunscodeforhandlingthepacket in messages and other event messages. Examples of such controller code/softwares are RYU [4], POX [5], NOX [6], Floodlight[7]etc.Mostofthecontrollersoftwaresareopen innaturesothatdevelopersarefreetomodifyitoraddmore functionalitiesasdesired.
The features that highlights the SDN from traditional network comprises of its ability to program the network withoutchanginganyoftheforwardingdevice.Anypolicies orfunctionalitiesthatneedtobeaddedorchangedcanbe done in the controller through programs, which will take effect in the whole network. This will save huge effort in changing the network infrastructure to implement the change. Another feature is the fine grained access control basesonthepoliciesassignedbytheSDNcontroller.Thisis highlyusefulinIoTbasedenvironmentsastheydonothave in built access control mechanisms in their light weight devices[11][12].
ThecorecomponentintheOpenFlowswitchistheflow table. Itisa hugetable containingtwo major fields;match field and corresponding action field. The match table can contain parameter that can be checked with the incoming packets. If any match occurs, the corresponding action is taken.Somecommonactionsare;forwardingthepackettoa specified port, drop the packet, etc. The flows will have priorities so that the matches with higher priorities are checked first. If no match is there, it is calleda table miss. Then the default action is taken, which is to forward the packettothecontroller,encapsulatingitinamessagecalled packet in message. On getting he packet in message, the controller unwraps itand decides whatisto be done with thatpacket.Thepacketisthensentbacktotheswitchputting it into a packet out message, along with an action for this packet. The controller may then send a flow rule to that switchspecifyingthematchandactionforthesimilarpackets thatmaycomeinthefuturesothatwhenthepacketcomes later to theswitch,it will create a table hitand thepacket
The major feature and at the same time the most prominentvulnerabilityoftheSDNisitscentralizedcontrol. This weakness is used by the attackers to act upon the controller to perish the entire network. Most attacks in traditional network is applicable to SDN too [8][9][10]. Saturation attack is the major SDN aimed attack. Here the major areas of SDN aimed attacks are the switch, the link between the controller and the switch, and the controller itself.Exhaustingtheresourcesinallthethreewillresultin denial of services to the hosts connected to the network. Hence it is a type of Denial of Service (DoS) attack. It is possibleforattackerstocreateabotnetbyincludingmore zombiesystemsintotheattackscenarioandhencethiscan leadtoDistributedDoS(DDoS)attack.
Ina(D)DoSattack,theattackercreatesspoofedpackets andfloodthemintotheswitch.Thesewillbequeuedupat the switch causing a lot of table miss and thereby lot of packet in message to the controller. Hence, the switch resourceswillgetexhaustedandthelinkbetweentheswitch andthecontrollerfilledwithuselesspacket inmessages.The controllerontheotherhandwillunwrapeachofthis,tryto findactionforitwhichwillgoinvain.Itwilltelltheswitchto flood these packets and create useless entries in the flow table. Thus the controller CPU time and memory also get wasted.Thepacketswhosufferarethebenignpacketswhich cannotreachtheswitchorthecontrollerandtheservicefor itsuserisdenied.
AsDoSattackscanhappeninanynetworks,soisinSDN. Herethedifferenceisthattheattackscanbehost aimedor SDN aimed. The host aimed attacks are possible in all networksindependentofwhetheritislegacy[14]orSDN based[8][9][10].
TCPconnectionsareheavierthanotherconnectionless protocols as there are different handshakes and table managementsasfarasanormalhostisconsidered.MostTCP attacksuseSYNflagstoexhausttheTCPconnectiontablesof thetarget.Tosolvethistypeofattack,thecontrollercanact asaproxybymanagingatableofactiveTCPstatesasseenin Avant Guard[16].Thustheflowscanbeclassifiedintothose which complete the handshake and those which do not.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
Basedonthis,itcancreateflowrulestomanagetheflows whichdonotcompletetheTCPhandshakes.
ApartfromTCP,otherprotocolscanalsocreateattacks especiallyUDPandICMP.Alltheattackswillcauseadisaster tothenetworksandneedtobedetectedwiththecombined actionoftheswitchandthecontroller.NEODdescribesthis scenarioandaremedy[17].Butthismustnotincreasethe CPUloadofthecontrollerandtheswitch.
Sometimesthenetworkoperatingsystem(NOS)itselfcan becreatedwithprimaryfocus topreventattacksthatmay happentothecontrollerbycompartmentalizingthenetwork applications so that the services would work in side sandboxes and does not cause much problems to the network.Rosemary[18]isdesignedwithsuchaview.Hence itispossibletosaythattheOSisapplication centricrather thanflow centric.
Oneofthecommonmethodsistofirstdetectthepresence ofanyattackandmitigateitbymeansofdifferentalgorithms. This detection and mitigation strategy is used by many researchersintheirownmethodssuchasFloodGuard[19], SGuard [20], Flokeeper [22], SDNGuard [24] and FloodDefender[25].Wheneveranattackstarts,theswitches willbegettingoverwhelmed.Toovercomesuchsituation,the generalideasareeithertodivertthepacketstosomewhere else, say neighbor switches [25] without losing the inport information,ortostorethepacketstemporarilyinacachefor laterprocessing[19][20][24].Butusingtheadditionalcache forpacketstorageispracticallyverydifficult.Alsoitneeds extracosttoaddtheadditionalhardwarecache.Classifying thepacketsintobenignandillegalisanothertediousthing. DifferentclassifiersareusedforthissuchasSVM[25],Self Organizing Maps [20], etc. In small networks, this will not takemuchtime,butwhenthenetworkgrowbiggerinsize, therealtimeclassificationmustnottakemuchtimeasitmay cause severe packet transfer delay. Another method of finding the attack is theanomaly detectionin the network [23]. Maddu et. al. uses a probabilistic model for such classification[24].
Whenthenumberofspoofedpacketsincreasesatswitch, thiswill increasethenumberofpacket inmessagestothe controller.Thustheswitch controllerlinkwillgetbusierand thisthismayleadtolinksaturation.Hencebymonitoringthe link bandwidth, it is possible to detect the presence of floodingattheswitchandtherebypredicttheattack[21]. Thepredictionwillnotbecrispasthenetworkbehaviourcan bechangedatanytime.Thusonlyafuzzymodelisfeasiblein predictingthefuturebandwidthutilizationandtherebythe chanceofattack.
Most of the alleviation methods are focused on the controller. Recently experiments are being happened to providesomesortofintelligencetotheopenflow switches too,sothattheycandomorethanjustforwardingthepacket
basedontheflowtable.SuchaninitiationistheDataPlane DevelopmentKit(DPDK)thatconsistsoflibrariesinstalledin theswitchtoacceleratepacketprocessingandforefficient computing.BasedontheDPDKtheattackdetectioncanbe madefasterbyprocessingeachpacketinaveryspeedyway. Newer methods such as DPDK based DDoS Detection frameworks[26]arebasedonsuchpacketprocessing.With thistheattackdetectionhappensatthedataplaneitselfand mitigationatthecontrolplane.
One of the difficult attacks to mitigate is the Low Rate attack,whichoccursasspikesatrandomintervaloftime.To identifysuchattacksdifferentmethodsneedtobecombined and collaborated. Tang et. al. has introduced a model for classificationbasedonperformanceandfeaturesofthetraffic [27].Itcombinesbothmachinelearningandflowfrequency analysis.
A comparison of some of the previous proposals are shownintable1.
Proposal Protocols Additional Hardware Controller
AvantGuard[16] TCP No POX
FloodGuard[19] All Yes POX
SGuard[20] All Yes NOX
BWManager[21] All No Floodlight
DAISY[23] All No RYU
SDNGuard[24] All Yes POX
FloodDefender [25] All No RYU
The SDN can be introducedas the backbone of the IoT network,sothatthecontrollerwillgetanentireviewonthe wholeIoTtopology[28][29].Thesensordatapacketscanbe inspectedbythecontrollerandknowthecompleteattributes ofthepackets.ThisenablesthecontrollertomanagetheIoT networkinafinerlevel.
IoT architecture also is not escaped from DoS attacks. Withspoofedfloodandjunkvaluepackets,thesinkdevices may get overwhelmed and the valuable sensor packets cannot reach the sink, causing DoS situation. As SDN can
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
handle the devices and packet flow in a granular way, differentproposalshavebeenintroducedbyimplementing SDNintoIoTenvironment.Somearejusttofinetunethedata flowandsomelightlyapproachesthesecurityaspectsalso. CommonattacksthatmayhappentoanIoTnetworkinclude malwareinjection,DDoSattacks,spoofing/masqueradingand man in the middleattack[12].Asindatacentersandclouds, DoSandDDoSattacksintheIoTenvironmentmayleadto failureofcollectingsensordataandtherebyhinderingthe intendedservicestoberunatthepropertime.Theattacks mayhappenfrominsideoroutsidetheIoTnetwork.Thiscan becontrolledbylimitingtheaccesstoauthenticateddevices onlyandcontrollingtheaccessofnetworkservicesinapre definedmanner.ThisispossibleusingSDN.
Z. Qin et. al. [31] proposed MINA which uses the programmability and flow control feature of the SDN. It focuses on Network Services and scheduling flows. The networkservicesareprovidedasprogrammablefeaturesand SDN'sinherentflowtablemechanismisusedforscheduling flows. This resists the illegal flows in the network and therebyreducingthechanceofDoSattacks.But,thereisno mentioningaboutwhichdeviceshastoaccessthenetwork andwhichservicesareallowedforthem.IoTPotandIoTBox [30]aresomesortofhoneypotandsandboxingmethodsto traptheattackerandtherebystoppingitfromgeneratinga DoSattack.Anentropybasedmethodin[32]findsanomalyin thepacketflowbyconstantlymonitoringthedataflowand therebydetectsandmitigatestheillegalpackets.Onlarger IoTnetworksofheterogeneousdevices,clustersofdevices canbeformed,whicharemanagedbyoneSDNcontrollerfor eachclusterandalltheclustercontrollerscanbecoordinated byamastercontroller[33].Heretheclustercontrollerswill classifytheabnormalflowsusinganomalydetectionthrough SupportVectorMachine(SVM)andwillreporttothemaster controller.Themasterwilldecidetheactions/flowrulesto manageandcontroltheflowsinthenetwork.KrishnanP et. al. [34]proposedalooselycoupledintegrationschemeand tightly coupled integration scheme. In the former, the controller apps take care ofthe attacks whereas the latter does the detection through the switch and its security controller.
Toimplementandtesttheproposals,settingupahardware environment is very costly. Hence the researchers use an emulatortoolcalled“Mininet”[35][36][37]forcreatingthe wiredandwirelesssetup.Itishighlyscalableandpowerful sothatitcancreatevirtualhostsandOpenVirtualSwitches. The hosts are provided with terminals to access its functionality and the switches are as powerful as the real ones. With specific tools such as Scapy [38][39][40] and hping[41],benignandspoofedtrafficcanbecreatedinside thenetwork.Performanceofthesystemssuchasbandwidth and throughput can be measured using iperf [42] like
utilities.Thecontrollercanbefromalistofchoicessuchas RYU,POX,NOX,Floodlightetc.
ThispaperprovidesabriefoverviewofDoSattacksinSDN and some mitigation measures proposed for various contextssuchasdatawarehousesandIoTenvironments.As thecontrolleristhekeyelementinSDN,anyattemptwhich causes hindrance to the controller or the link to the controller will decrease the functionality of the network, sometimesdestroyingtheentirecommunication.Itcanbe seenthatthemeasuresagainstDoSattacksarewellsuited for DDoS attacks too. The measures reveal that the attack mitigation is possible through speculative and efficient management of resources and prompt and accurate classification of illegal packets from benign ones. Furthermore,thispaperbringsthemethodologyusedinthe preventive measures, the features they used and the limitationstheybear.Eachnewmethodtriestoovercome thegapfoundinthepreviousones.Overall,aresearchercan usethissummarytowellprepareforfindingnewmethods to detect and mitigate DoS and DDoS attacks in more effectiveways.
[1] Kirkpatrick, Keith. “Software defined networking.” Communications of the ACM 56.9 (2013): 16 19. M. Young, The Technical Writer’s Handbook. Mill Valley, CA:UniversityScience,1989.
[2] N.McKeownetal.,“OpenFlow:Enablinginnovationin campusnet works,”ACMSIG COMMComput.Commun. Rev.,vol.38,no.2,pp.69 74,Mar.2008.
[3] OpenFlow Switch Specification [online] https://opennetworking.org/wpcontent/uploads/2014 /10/openflow switch v1.3.5.pdf
[4] RYUSDNFramework[online]https://ryu sdn.org/
[5] Kaur, Sukhveer, Japinder Singh, and Navtej Singh Ghumman. “Network programmability using POX controller.” ICCCS International conference on communication, computing & systems, IEEE. Vol. 138. sn,2014.
[6] Gude,Natasha,etal.“NOX:towardsanoperatingsystem fornetworks.”ACMSIGCOMMcomputercommunication review38.3(2008):105 110.
[7] Floodlight Controller [online] https://floodlight.atlassian.net/wiki/spaces/floodlightc ontroller/overview
[8] Chica, Juan Camilo Correa, Jenny Cuatindioy Imbachi, and Juan Felipe Botero Vega. “Security in SDN: A
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
comprehensive survey.” Journal of Network and ComputerApplications159(2020):102595.
[9] Ahmad, Ijaz, et al. “Security in software defined networks:Asurvey.”IEEECommunicationsSurveys& Tutorials17.4(2015):2317 2346.
[10] Benzekki,Kamal,AbdeslamElFergougui,andAbdelbaki ElbelrhitiElalaoui.“Software definednetworking(SDN): asurvey.”Securityandcommunicationnetworks9.18 (2016):5803 5833.
[11] Flauzac,Olivier, etal.“SDN basedarchitecture forIoT and improvement of the security.” 2015 IEEE 29th international conference on advanced information networkingandapplicationsworkshops.IEEE,2015.
[12] Karmakar,KallolKrishna,etal.“SDN enabledsecureIoT architecture.” IEEE Internet of Things Journal 8.8 (2020):6549 6564.
[13] Das¸, Resul, Abubakar Karabade, and Gurkan Tuna. “Common network attack types and defense mechanisms.” 2015 23nd signal processing and communications applications conference (siu). IEEE, 2015.
[14] Kreutz, Diego, et al. “Software defined networking: A comprehensivesurvey.”ProceedingsoftheIEEE103.1 (2014):14 76.
[15] Abdullaziz,OsamahIbrahiem,Li ChunWang,andYu Jia Chen. “HiAuth: Hidden authentication for protecting software defined networks.” IEEE Transactions on Network and Service Management 16.2 (2019): 618 631.
[16] S.Shin,V.Yegneswaran,P.Porras,andG.Gu,“AVANT GUARD:Scalableandvigilantswitchflowmanagement in software defined networks,” in Proc. ACM SIGSAC Conf. Comput. Commun. Secur. (CCS), 2013, pp. 413 424.
[17] S.Song,S.Hong,X.Guan,B. Y.Choi,andC.Choi,“NEOD: Network embedded on line disaster management framework forsoftwaredefined networking,” in Proc. IFIP/IEEE Int. Symp. Integr. Netw. Manage. (IM), May 2013,pp.492 498.
[18] Shin, Seungwon, YongjooSong,TaekyungLee, Sangho Lee, Jaewoong Chung, Phillip Porras, Vinod Yegneswaran,JiseongNoh,andBrentByunghoonKang. “Rosemary: A robust, secure, and high performance networkoperatingsystem.”InProceedingsofthe2014 ACM SIGSAC conference on computer and communicationssecurity,pp.78 89.2014.
[19] H. Wang, L. Xu, and G. Gu, “FloodGuard: A DoS attack preventionextensioninsoftware definednetworks,”in Proc.45thAnnu.IEEE/IFIPInt.Conf.DependableSyst. Netw.,Jun.2015,pp.239 250.
[20] Wang,Tao,andHongchangChen.“SGuard:Alightweight SDN safeguard architecture for DoS attacks.” China Communications14,no.6(2017):113 125.
[21] Wang,Tao,Zehua Guo,HongchangChen,andWei Liu. “BWManager: Mitigating denial of service attacks in software defined networks through bandwidth prediction.”IEEETransactionsonNetworkandService Management15,no.4(2018):1235 1248.
[22] S.Gao,Z.Li,B.Xiao,andG.Wei,“Securitythreatsinthe dataplaneofsoftware definednetworks,”IEEENetw., vol.32,no.4,pp.108 113,Jul.2018.
[23] Imran,Muhammad,MuhammadHanifDurad,Farrukh AslamKhan,andHaiderAbbas.“DAISY:Adetectionand mitigation system against denial of service attacks in software definednetworks.”IEEESystemsJournal14, no.2(2019):1933 1944.
[24] Maddu,JeevanSurya,SomanathTripathy,andSanjeet Kumar Nayak. “SDNGuard: An Extension in Software DefinedNetworktoDefendDoSAttack.”In2019IEEE Region 10 Symposium (TENSYMP), pp. 44 49. IEEE, 2019.
[25] Gao, Shang, Zhe Peng, Bin Xiao, Aiqun Hu, Yubo Song, andKuiRen.“DetectionandMitigationofDoSAttacksin Software Defined Networks.” IEEE/ACM Transactions onNetworking28,no.3(2020):1419 1433.
[26] Varghese, Josy Elsa, and Balachandra Muniyal. “An Efficient IDS Framework for DDoS Attacks in SDN Environment.”IEEEAccess9(2021):69680 69699.
[27] Tang,Dan,etal.“PerformanceandFeatures:Mitigating theLow RateTCP TargetedDoSAttackviaSDN.”IEEE Journal on Selected Areas in Communications 40.1 (2021):428 444.
[28] Tayyaba,SahrishKhan,etal.“Softwaredefinednetwork (sdn) based internet of things (iot) a road ahead.” Proceedings of the international conference on future networksanddistributedsystems.2017.
[29] Flauzac,Olivier, etal.“SDN basedarchitecture forIoT and improvement of the security.” 2015 IEEE 29th international conference on advanced information networkingandapplicationsworkshops.IEEE,2015.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
[30] Pa,YinMinnPa,etal.“IoTPOT:AnalysingtheRiseofIoT Compromises.” 9th USENIX Workshop on Offensive Technologies(WOOT15).2015.
[31] Qin, Zhijing, et al. “A software defined networking architecture for the internet of things.” 2014 IEEE network operations and management symposium (NOMS).IEEE,2014.
[32] Galeano Brajones,Jesus,etal.“Detectionandmitigation of dos and ddos attacks in iot based stateful sdn: An experimentalapproach.”Sensors20.3(2020):816.
[33] Bhunia,SumanSankar,andMohanGurusamy.“Dynamic attackdetectionandmitigationinIoTusingSDN.”2017 27th International telecommunication networks and applicationsconference(ITNAC).IEEE,2017.
[34] Krishnan,Prabhakar,JishaS.Najeem,andKrishnashree Achuthan.“SDNframeworkforsecuringIoTnetworks.” International Conference on Ubiquitous Communications and Network Computing. Springer, Cham,2017.
[35] Mininet Walkthrough [online] http://mininet.org/walkthrough/
[36] DeOliveira,RogerioLeaoSantos,etal.“Usingmininet for emulation and prototyping software defined networks.” 2014 IEEE Colombian conference on communicationsandcomputing(COLCOM).Ieee,2014.
[37] Fontes, Ramon R., et al. “Mininet WiFi: Emulating software defined wireless networks.” 2015 11th International Conference on Network and Service Management(CNSM).IEEE,2015.
[38] Rohith, R., Minal Moharir, and G. Shobha. “SCAPY A powerful interactive packet manipulation program.” 2018 international conference on networking, embeddedandwirelesssystems(ICNEWS).IEEE,2018.
[39] Biondi,Philippe.“Scapy:explorethenetwithneweyes.” Technical report, Technical report, EADS Corporate ResearchCenter(2005).
[40] Scapy[online]https://scapy.net/
[41] hping3[online]https://linux.die.net/man/8/hping3
[42] iperf[online]https://iperf.fr/iperf doc.php


Sreejesh N. G. is a P. G. Scholar of ComputerScienceandEngineering at Rajiv Gandhi Institute of Technology, Kottayam, Kerala, India.HehascompletedhisB.Tech in Computer Science and Engineering. His areas of interest includeComputer Networks,SDN andNetworkSecurity.
Sabina M. A. is an Assistant Professor in the Department of ComputerScienceandEngineering at Rajiv Gandhi Institute of Technology, Kottayam, Kerala, India. She has completed her M.Tech in Computer Science and Engineering.Shehasmorethan5 years of experience as Lecturer and her areas of interest include ComputerNetworksandMachine Learning.