International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
1MTech student at R V College of Engineering, Bengaluru, Karnataka
2Professor and Associate Dean (PG CSE) at R V College of Engineering, Bengaluru, Karnataka ***
Abstract - Nowadays, Near Field Communication (NFC) market is no more a monopoly. Competition is highamongthe companies with regard to products they manufacture and their features for consumer attraction. Mutualauthentication between NFC reader and tag ensures safe communication between them. This paper proposes an accessory authentication model that guarantees that counterparts of a product are of same company. AES 128 bits algorithm is used in two different modes, that is AES ECB and AES CBC for mutual authentication. AES CBC mode is stronger in terms of security when compared to AES ECB mode.
Key Words: AES, Brand protection, Mutual authentication,NFC,Security.
NFC technology was developed in the year 2004 by Philips Electronics and Sony. It is a short range, wireless technology with operating area within 10 centimeters, operatingfrequency13.56MHzanddatatransmissionrate used here is of 106 kbps. The objective of the paper is to develop an accessory authentication model for an NFC enabledproduct.Thisensuresthatreplaceablepartofthe product(NFCtag)andthefixedpart(activeNFCreader)are pairedcounterpartsandareofthesamecompany.Withthis end usercangethighqualityproduct.Thiskindofproduct positively impacts manufacturing and authenticating companies, thereby ensuring brand protection. Some examples are authentication in motorized tooth brush, wherebrushhandlehasNFCreaderandthebrushheadhas NFCtaginit.Inhighendblenders,thebaseunitwillhave NFCreaderandthejar/containerwillhaveNFCtag.[12]To achievethis,firstlycommunicationisestablishedamongthe NFC reader and the tag. Then three pass AES (Advanced Encryption Standard) algorithm is run, before actual data transferhappens.AES 128isasymmetricblockcipher,that uses one shared secret key for both encryption and decryption. Choice for mode of AES is provided. User can choose authentication to happen either in AES ECB (Electronic Code Book) or in AES CBC (Cipher Block Chaining)mode,dependingontheirrequirement.
In [1], authors have used the fact that NFC has an operatingmodecalledreadorwrite.Thishasthepropertyof
one directional transfer of data only. However, they have triedtobringinabi directionalmodelthatishalfduplexin nature.MainadvantageofthisoperatingmodeofNFCisthat, it allows different data formats and very low protocol overhead. But one main challenge is regarding the reader collisionproblem,completingtransactionsinasecureway, withinatimeframe.FingerprintandKerberosaretwofactor authenticationused.
In [2],a smart bandage with wireless temperatureand strainsensor,withpassiveNFCtagisdesigned.Anandroid applicationcalledSenseAblewasbuilt,todisplaythebody temperatureandothersensorreadings.Chestexpansionand contractionofaCovid 19patientwasrightlymonitoredby thissmartbandage.
In[3],itprovesthatMITMattackscanbedoneduringNFC communication,whenusingapassivecard.Thismethodof attackmimicsrealimplementationofEMVprotocolenabling devices, used for payments. Paper demonstrates how a contactless payment system can be compromised by an attacker,byusingamaliciousMITMcard.
In [4], study is done on reading range of implanted sensors,basedonNFCIntegratedcircuit(IC)byusingaNFC enabledsmartphone.Challengesnotedwerelowcoupling betweenloopsofvarioussizesandlimitedqualityimposed bybandwidthcommunication.Resultsshowthatsystemwith three coils performs better at longer distance than 2 coil system.
In[5],aschemetobuildanewpublictransportpayment method with different technologies likeNFC, Bluetooth, IC cardisintegrated.Advantageisthat,passengerscanchoose thepaymentmethodthatsuitsthem,intermsofdiscounton ticket fare. This solves the problem that the payment platforms are not unified and that passengers have many applications on their mobile, which causes inconvenience whiletravelling.
In[6],amodelforvehiclenetworkoperatorsusingNFCis proposed. Tourists generally will not use local mobile operator’s services, as they stay for short time and the roamingchargesarealsohigh.Asasolution,themodelwhich allowslessmobiletrafficcostfortouristandhasincreased transaction security is proposed. Here the user’s mobile traffic is routed to the network of vehicle rental service
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
provider.Thissimplifiesthetourismforatouristandsecurity ofuser’spersonaldata.
In [7], author starts the paper by discussing general aspects of NFC and its comparison with RFID technology. LightisthrownondifferentISOstandardsNFCcomplieswith andNFCoperatingmodes.TheyprovethatNFCisvulnerable tosecurityattacks,whichcanleakuser’simportantdata.This can have negative impact on organization adopting NFC technologyanditsapplications.Differentattacksarelisted andascientificmethodtoincreasesecurityisalsoproposed.
In[8],extendedversionofdifferentattacksinNFCareais briefed.FocusonDoSanddatacorruptionswasgivenasit wasnotedfromstudyingriskassessmentmodels,thesetwo attacksweremostcommonlywitnessed.Theywerestudied by Analytical Hierarchy Process (AHP). A solution was proposedwhichwasatouchandgoapplicationcalledMIDAS. It is concluded that AES and ECC (Elliptic Curve Cryptography)arebestknownalgorithmstobuildasecure channelandtoavoiddatacorruption.
In [9], Authors propose an application of NFC in the IoT domain.TextileindustryisfarbehindintermsofIoT.Hence, toenhancethetextilebusiness,asystemcalled‘Interactive clothes’isdesigned.EveryclothhasanNFCchipwithunique number embedded in it. An application to scan the NFC is developed,whichgivesaURLtothedatabase.Thissystem modernises manufacturing, managing, selling and buying goods.
In[10],authorprovesthattagsusedinNFCsystemare limitedintermsofchipsizeandpowerconsumption.These limitationsmakeitdifficulttointegratestrongcryptographic securityontothetags.Authorsuggeststhatthereisneedto implementsecurealgorithmthatissecureagainstattacklike Side Channel Analysis (SCA). As a case study, a tag with cryptographicalgorithms(AESandECDSA)implementedis taken.
Fewoftheresearchgapsobservedareasfollows:
1. NFCisashort rangecommunicationtechnology,and hence believed that security risks are low as the interaction is within close proximity. But security vulnerabilities do exist and few attacks are only discovered.
2. NFCismostlyusedintheareaofaccesscontroland paymentmethod.Otherapplicationslikefiletransfer andinIoTcanberesearchedmore.
3. The economic performance of NFC developments canbeevaluatedandimpactsofNFCtechnologieson companies,organizationsandbusinessmodelscan beexplored.
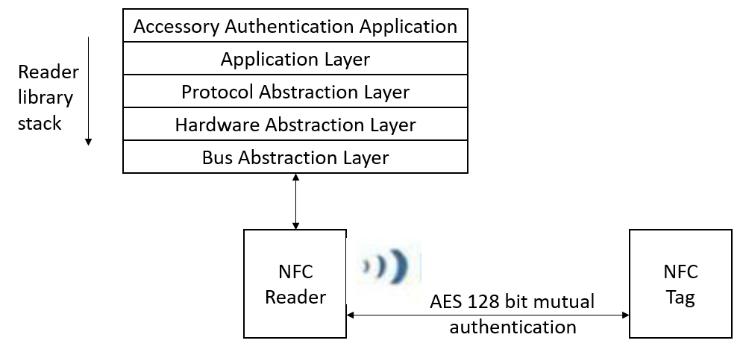
Project design gives an outline of project development process. It helps to identify the modules and the tools required to implement them. Figure 1 shows the system architecturewhichincludesauserapplicationbuiltonNFC reader library for authentication process [11]. The reader librarystackhasfourlayers.Applicationlayeristhetoplayer, whichimplementsthecommandstoworkwithcontactless technologies.ProtocolabstractionlayerhasfunctionsforNFC card activation. The hardware specific elements of reader implementedinthehardwareabstractionlayer.Italsohelps execute native commands of the chip. The lowest bus abstractionlayer,implementsthecommunicationbetween thereaderandtag.Bothreaderandtaghaveakeystore,from whichtheydecideuponasecretkeyforauthentication.
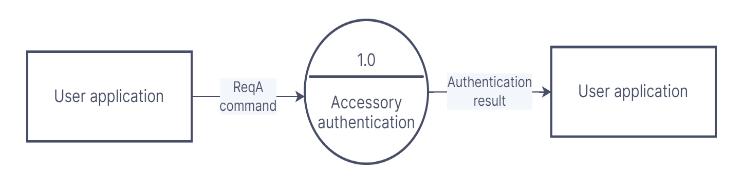
Dataflowdiagramshelptounderstandthesystembetter as it brings in modularity. Figure 2 shows DFD Level 0. Authentication procedure starts when user application makes reader to pass ReqA (Request A) command to the detected cards. Authentication result is decisive, if counterparts are authenticated then communication betweenthemstarts,elseaborts.
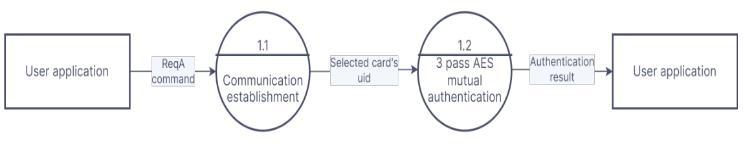
DFDLevel1infigure3showsthetwomodulesinvolved in accessory authentication. First is communication establishmemtbetweenreaderandtag,whichisachievedby usingavailablecommandsetoftags.Ifmorethanonecardis presentinproximity,collisionresolutionisdonebystandard anticollisionprocedureandonecardisselected.Thenthree passAESalgorithmisusedformutualauthentication.
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
themselvestoother,theaccessoryauthenticationprocedure is aborted. User can choose either AES ECB mode for authenticationorAES CBCmode.Ifdatabeingencipheredby each party is not sensitive, ECB is best option as it is fast. However, if security of data is prime concern, then CBC is preferredbecauseofitscomplexity.Figure5showspictorial representationofauthenticationprocedurediscussedabove.
Figure 3: DFDLevel1
NFCreaderwill emitradiowavesina periodic manner andchecksifanycardispresentinitsproximity.Ifnocardis detected,readercontinuestheloopuntilacardisdetected.If more than one card is detected, anticollision procedure resolvestheconflictandchoosesonecardascounterpartfor reader. After card selection and activation, authentication procedure happens. If reader and tag successfully authenticatetoeachother,asampletextiswrittenintothe card and then read back to check data integrity. Figure 4 showsentiremethodologyadoptedintheformofflowchart.
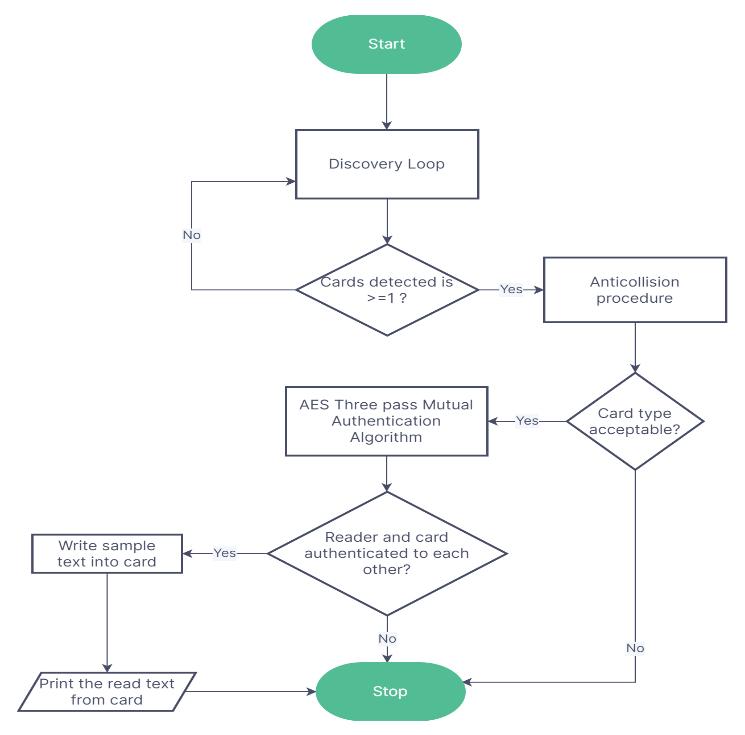
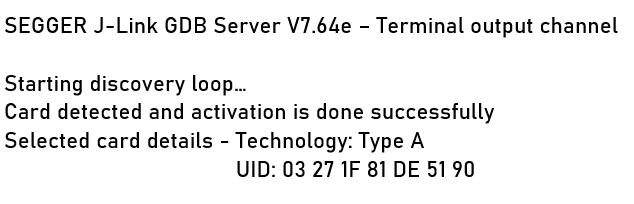
Anticollision procedure selects a tag based on its uid (unique identification number) which is followed by card activation. The console display is as shown in figure 6. Technologyofthedetectedcardisdisplayedalongwithits uid.
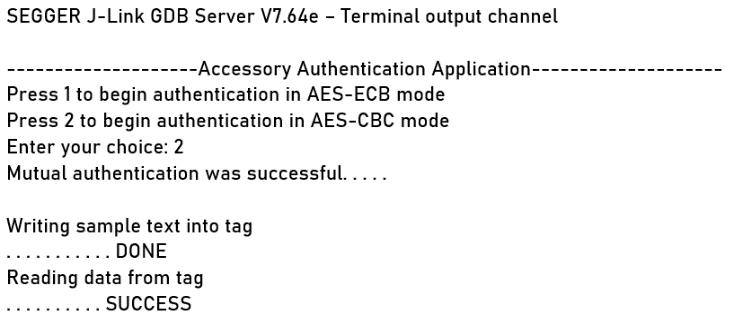
Card activation is followed by choice entry by user for mode selection. The output after running accessory authenticationinAES CBCmodeisshowninfigure7.Both readerandtaghaveauthenticatedtoeachother.Sampletext waswrittenintotagandreadsuccessfullywithoutanyerror.

AES three pass mutual authentication is a procedure which uses key of length 128 bits [12]. In the first pass of algorithm,NFCreaderencryptsitsdata(RndX)withagreed secretkey(K)andsendstheciphertoNFCtag.Inreturn,tag respondsbysendingthedeciphereddata.Insecondpass,tag encryptsitsdata(RndY)andsendstheciphergeneratedto reader.Readerdeciphersandsendstheresponseback.Third passincludeseachpartyverifyingifdatareceivedissameas whattheyhadgeneratedoriginally.Thatisreaderchecksif tag had sent RndX correctly, and tag checks if reader’s response had RndY. If any one party fails to authenticate
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

AES ECBmodeissimpleandfastapproach.Drawbackis thatduplicatedatainplaintextwillbereflectedinthecipher text. Hence, it is not recommended in the areas where securityisapriority.Whereas,AES CBCmodewillencrypt everyoccurrenceofsameplaintextintodifferentciphertext. ButitisslowandcomplexcomparedtoECBmode.YetCBCis stronger in terms of security and is preferred for authentication.
AsurveyshowsthatNFCmarketislikelytoraisefrom 18billionUSDin2020to34.9billionUSDby2025.Themain use cases are in mobile commerce and usage of wearable technology. This paper serves the need for accessory authentication by AES algorithm, to ensure that genuine partsofsamecompanyareused.Thisenhancesconsumer experience, convenience and ensures product safety. If productrequiresmoresecureformofauthentication,ECCis suggestedfrompublickeycryptographicalgorithms.Here, userapplicationjustchecksreadandwriteontothetagafter successful authentication. This feature can be enhanced according to user needs. Example in case of NFC enabled product like motorized toothbrush, authentication can be followedbytappingmobilephonetotagcandisplayURLto webpage that keeps track of oral health and brush head replacementdate.
[1] M.S.Chishti,C.T.KingandA.Banerjee,“ExploringHalf Duplex Communication of NFC Read/Write Mode for Secure Multi Factor Authentication”, 2021 in IEEE Access, vol. 9, pp. 6344 6357, doi: 10.1109/ACCESS.2020.3048711.
[2] P.Escobedo,M.Bhattacharjee,F.Nikbakhtnasrabadiand R. Dahiya, “Smart Bandage With Wireless Strain and TemperatureSensorsandBatterylessNFCTag”,2021,in IEEEInternetofThingsJournal,vol.8,no.6,pp.5093 5100,15March,doi:10.1109/JIOT.2020.3048282.
[3] S. Akter, S. Chellappan, T. Chakraborty, T. A. Khan, A. RahmanandA.B.M.AlimAlIslam,“Man in the Middle Attack on Contactless Payment over NFC Communications:Design,Implementation,Experiments and Detection”, 2021, in IEEE Transactions on Dependable and Secure Computing, vol. 18, no. 6, pp. 3012 3023, 1 Nov Dec, doi: 10.1109/TDSC.2020.3030213.
[4] A.Lazaro,M.Boada,R.VillarinoandD.Girbau,“Studyon the Reading of Energy Harvested Implanted NFC Tags UsingMobile Phones”, 2020in IEEE Access, vol. 8, pp. 2200 2221,doi:10.1109/ACCESS.2019.2962570.
[5] C. Shuran and Y. Xiaoling, “A New Public Transport PaymentMethodBasedonNFCandQRCode”,2020IEEE
5th International Conference on Intelligent Transportation Engineering (ICITE), pp. 240 244, doi: 10.1109/ICITE50838.2020.9231356.
[6] V.OliinykandO.Rubel,“ImprovingSafetyandEaseof UseinAutomaticElectricVehicleRentalSystems”,2020 IEEE15thInternationalConferenceonAdvancedTrends inRadioelectronics,TelecommunicationsandComputer Engineering (TCSET), pp. 800 803, doi: 10.1109/TCSET49122.2020.235545.
[7] A. Albattah, Y. Alghofaili and S. Elkhediri, “NFC Technology: Assessment Effective of Security towards ProtectingNFCDevices&Services”,2020International ConferenceonComputingandInformationTechnology (ICCIT 1441), 2020, pp. 1 5, doi: 10.1109/ICCIT 144147971.2020.9213758.
[8] M.M.Singh,K.A.A.K.AdzmanandR.Hassan,“NearField Communication (NFC) Technology Security Vulnerabilities and Countermeasures”,2018, InternationalJournalofEngineering&Technology,vol.7, no.4.31,pp.298 305.
[9] Kishore Kumar Reddy N. G. and Rajeshwari K., “InteractiveclothesbasedonIOTusingNFCandMobile Application”, 2017 IEEE 7th Annual Computing and Communication Workshop and Conference (CCWC), 2017,pp.1 4,doi:10.1109/CCWC.2017.7868339
[10] KorakT,“Evaluationofasecurity enabledNFCTagwith AESandECDSA”,2011,Master’sthesis,Institute
forappliedInformationProcessingandCommunications (IAIK),Austria.
[11] NFCReaderLibrary: https://community.nxp.com/pwmxy87654/attachme nts/pwmxy87654/nfc/707/1/UM10802_NXP NFC Reader Library v3.010 API.pdf
[12] Mutualauthenticationprocedure: https://community.nxp.com/pwmxy87654/attachme nts/pwmxy87654/tech days/179/1/AMF SMC T3036.pdf
Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal |
Sukrutha C Basappa, is a MTech student at Department of Computer Science and Engineering, R V College ofEngineering,Bengaluru,Karnataka, India.(sukruthacb.scn20@rvce.edu.in)

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056
Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
Dr. Nagaraja G S, is working as Professor and Associate Dean (PG CSE) at Department of Computer Science and Engineering, R V College ofEngineering,Bengaluru,Karnataka, India (nagarajags@rvce.edu.in)

2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal
