International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072

International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
Sangmesh Melinmani
Assistant Professor , Depatrment of Electronics and Communication Engineering
Dayananda Sagar College Of Engineering Bangalore,INDIA
DepartmentofElectronicsand CommunicationEngineering
Dayananda Sagar College Of Engineering Bangalore,INDIA
Venkatesh.K
DepartmentofElectronicsand CommunicationEngineering Dayananda Sagar College Of Engineering Bangalore,INDIA
Prakash V
DepartmentofElectronicsand CommunicationEngineering Dayananda Sagar College Of Engineering Bangalore,INDIA
***
Abstract In this world of universal electronics, transmitting private data via a computer network necessitates a high level of security. For clouds, networks, and individuals, researchers are also looking for the most secure and complicated cryptographic methods. Cryptography is the process of converting data or information from one form to another in cryptography, and it is a very efficient and effective technique of securing data. RSA Algorithm will allow for securing the communication when third parties are present. As there is an increased publicsecurityawarenessahugedemandisessentialforany effective surveillance system, it has grown significantly, with the goal of lowering crime rates and serving numerous objectives. However, several developed monitoring systems contain flaws that limit their uses. This project mostly consists of a design and a robot powered by a Raspberry Pi 3B+ with a DC motor, AVR board, Bluetooth, and a Raspberry Pi camera are all used to send live data over a virtual network and update collected photos for encryption and decryption. With the help of communication there is huge advantage for any multimedia systems, medical purposesaswellasinmilitary basedimagingsystemsalluse image encryption. This project covers a wide range of electronic and computer science topics, including cryptography and network security, Python programming, wirelesssensors,andtheInternetofThings.
DepartmentofElectronicsand CommunicationEngineering Dayananda Sagar College Of Engineering Bangalore,INDIA
Cryptography, RSA Algorithm, Encryption, Decryption, AVR board, IOT
Information has been one of our most valuable possessions since the birth of civilisation. The ability (or
inability) of our species to maintain secrets and hide informationhaswipedoutpolitical parties,turnedthetide of wars and toppled entire regimes. Every day banks, payment processors and their clients exchange sensitive financial information. Whether you realise it or not, all of these records must be saved in a huge database at some time. Cryptography, or the art and science of encrypting sensitive data, was traditionally exclusive to government, academics, and the military. These are more important in our daily lives. Digital signatures and authentication are critical applications. This would be a major issue without cryptography a significant issue If any of these documents werestoredorcommunicatedwithoutencryption,hackers wouldhavefreereign,andyourbankaccountwouldswiftly deplete. Banks, on the other hand, are aware of this and have gone through a lengthy procedure to implement advancedencryptiontechnologiestokeepyourinformation safe from hackers and food on your table. Visual cryptographyisakindof cryptographictechniquewhichis mainly applicable for encrypting visual information like images as well as used in text etc by which the decrypted information appears in the form of an visual image. Visual cryptography is employed in the real of data concealment and authentication in cybercrime. At its most basic level, cryptography consists of two steps: encryption and decryption. A cypher is used in the encryption process. Turn plaintext into ciphertext to encrypt it. On the other side,decryptionusesthesamecyphertoconvertciphertext to plaintext. Cryptography hascome to pervadeall aspects ofordinarylifeasaresultofrecenttechnicaldevelopments. Everything from your smartphone to your banking relies largely oncryptographytokeep yourinformationsafeand your livelihood secure, and we employ the Mutual Authentication procedure to satisfy all Cryptography
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

services, such as Access Control, Confidentiality, Integrity, and Authentication. We can keep the data more securely thisway.BecauseweutilisetheRSAalgorithmtosecurethe data(pictures),anyotherindividualonthenetworkwillbe unabletoaccessthedata.Thegoalofthisprojectistoimply a new method of disguising an image by utilising the capabilities of the RSA algorithm in cryptography. RSA(Rivest Shamir Adleman) isasymmetric cryptography algorithm which focus to work on the basis of two different keys one is called as Public Keyand other is calledas PrivateKey.Herethe PublicKeyisknowntoall theuseswhowantstousethe encryptionandPrivatekey is the key which is kept private so that presence of private and public key enables a successful encryption and decryption Nowadays RSA has been still used in a range of many web browsers for secure information purpose ,email for secure mail transfer, VPNs, chat and other communication sources. RSA has been used often to make a strong and secure connections in between VPN clientsaswellas VPNservers
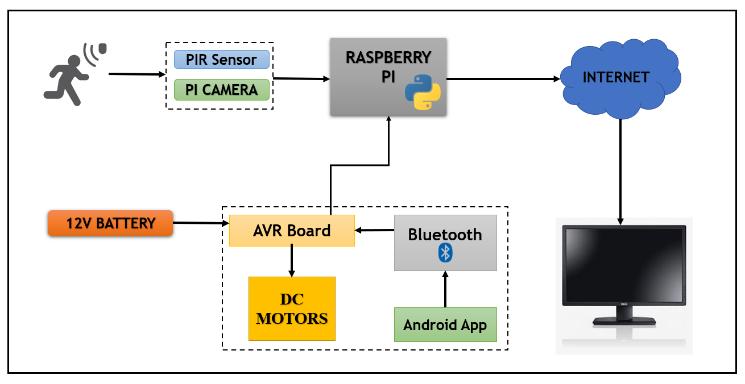
We will utilise the Raspberry Pi 3B+ as the main hardware in this project and the model will be equipped with an Pi camera sensor for monitoring purposes. DC motors have been employed for movement, which are embedded with the AVR board and relays. Relay are used for smooth robot movement. To prevent damage to the power source for the dc motor, an AVR is employed. This movement is controlled by a free app called “Serial Bluetooth Terminal”that can be downloaded from the Google Play Store. The AVR is connected to the HC 05 so thattheandroidphoneandtherobotmaycommunicate..It isoneofthestrategiesformotivatingworkerstocomplete tasksefficientlyandeffectivelyinordertoachievecommon goals. It is required for improved performance. The key reason for choosing this project is because Providing protection to personal materials, messages, or digital photos has grown difficult due to recent improvements in crypto analysis. Crypto analysis can quickly expose the existence of data, information, or any other medium. As a resultofbeingexposedtosuchissues,wedecidedtowork on this project, which involves the entire process of transferring an image from one location to another. where the user can access the info anytime they need it without fearofbeinghacked.
It is a project whose main focus was on building a kind of spying robot which can be utilized for manoeuvring and monitoring in treacherous environment. This robotic system includes aRaspberryPiwhichhasbeen interfaced with a DC motors for locomotion purpose, GPS module for tracking the location of the robot, Pi camera for image capturingindarknights,andIRThermalcamerasensorfor monitoring heat objectsTo control the motion of the robotic system it can be done with the help of a web
Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072 © 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page 2274
application through by utilizing a Wi fi connectivity. This robotic system is programmed in order to stream all the importantlivedatathroughavirtualnetworkand keepon updating all the captured images and additionally adding up with the time stamp and the location at certain instances to the cloud. It can successfully transmit all the capturedreal timevideosandpicturesthroughthethermal vision .It can also be utilized in war zones and extremely dangerousplaces,thisalsocanbeusedinobservingallthe targeted disaster affectedregions whicharenotadequate overbeyondhumanreach[1]
Thisprojectmainlyfocusedonthesuccessful transmission ofalltheprivatestatisticsoverthecomputernetwork.But it needs a huge protection and providing data protection against all the mischievous third party attacks .To tackle these problem cryptographic algorithms are a boon .There are many algorithms but specially RSA has a set of rules basedalgorithmswhichcanwidelybeenusedinPublicKey infrastructure implementations. A several prosecutions havebeenmadetomaketheuseofalltheneededfourkeys for more quicker and more efficient than the real encryption and decryption techniques It enables the implementation of the necessary operation with the continuous subtraction operation instead of division operation.[2]
The main target for a successful communication is secure and reliable exchange of data that occurs in between the devices is crucial and the information should be maintained over the storage devices ,routing devices as well as the communication which occurs over the cloud. Cryptographic techniques are mainly used to give the security for the transmission of all the crucial data and make sure that the user’s privacy is given by storing and transmitting all the private data in a particular format. Using encryption we can only intend user possessing the key can access the information. Homomorphic Encryption (HE) isa advantageous techniques whichhasbeenutilized inthepastyears.HEiseitherseeninitsslowtransmission ability or fast key capacity of the decryption .The HE CRT RSA, utilizes many multiple keys for efficient communicationalongwiththehighsecurityHE CRT RSAis observed to be 3 4% faster than the classical Rivest Shamir Adleman(RSA).[3]
RSA (Revist,Shamir,Adleman) algorithm is an asymmertic key cryptosystem, which can be found mostly used in the confirming all the fragile data, particularly when a person hassentsomedata overahighly problematic framework, such as the Internet. RSA was basically origanted by thse scientistsR.Rivest,AdiShamir,andLeonardAdlemanofthe Technology Institute of Massachusetts in 1977. Since it consist of two keys the public and private key the public key can be issued to anyone ,but since privacy of the sent data is essentail and to protect the private key it is not
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
shared.Thetwoindividualsusersandtheprivatekeyswill encrypt the message based on set rule of rule based algorihms encryption happens where as the opposite key from the other end of user is used to decrypt message is used to unscramble it. This attribute is one of the reasons why RSA has become the most frequently used upside down estimate: it offers a technique to ensure the protection, decency, validity and non reputability of products such as electronic trades and data collection. Various protocols like SSH, Open PGP, S/MIME, and SSL/TLS rely upon RSA for encryption and progressed mark limits. Programs are an obvious model that needs to establish a guaranteed relationship over an insecure environmentsuchastheInternetorconfirmamechanized imprint, similarly used to programming rationales. RSA signature checks quite possibly the most consistently achievedactivitiesininformation
1) We select any two prime numbers (basically large primenumbers)sothatitcanprovidemoresecurity.
2)Obtainthevalueofnusing(n=pq).
3)FindoutEuler’stotientfunction[φ(n)=(p−1)(q−1)].
4)Choose any random integer for ’e’ in the range 1 < e < φ(n) suchthatgcd(φ(n),e)=1.
5)Calculate‘d’using [d=1mod(φ(n)]
5) The public key is {e, n} and the private key {d, n} are successfullyobtained.
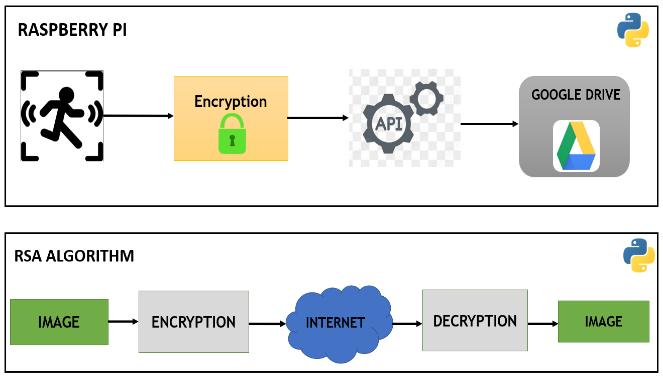
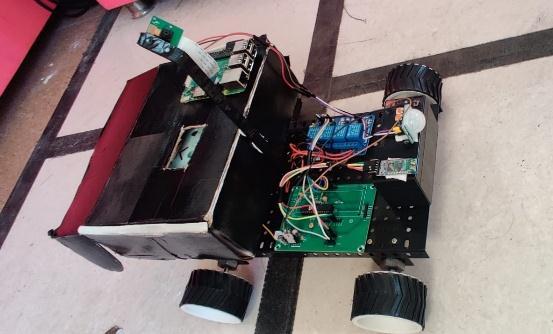
AlltheprincipalandusefulpartsofCryptoBotare referenced in the block graph above. It tends to be extensively isolated into 2 principal parts, the locomotion partandImageCapturingpart.Forthemovementofrobot, the modified AVR Board is utilized. This AVR Board comprises of Atmega 48, Relays and Voltage Regulator. The 12V Battery is associated with AVR board. The DC MotorsareassociatedwithsamesourcebymeansofRelay, while Raspberry Pi and Atmega 48 requires 5V Power Supply. This is given with the assistance of Voltage Regulator. The Bluetooth Chip (HC 05) is additionally associated with Atmega 48. The programming of Atmega 48isdoneinEmbeddedCtosuchanextentthat, the total movementofrobotcanbecontrolledfromanAndroidApp through Bluetooth. This program is dumped into Atmega 48andtherobotispreparedtomove.
Substitutealltheneededvaluesintheformula.
Computesthecipher:C=M^emod(n).
The ciphertext is obtained and can be given to the recipient.
To compute back the plaintext, use the formula M = C^dmod(n)
If both public and private keys are correct the encryptedanddecryptedinformationwillbesame
The Second part is Image Capturing. Here RaspberryPIassumesa significantpart.ThePIR Sensoris utilized for Motion Detection. When it identifies the movementofanylivingobjects(likeHumanBeings),itsets offthePICameratocatchpictures.Thecaughtpicturesare examined, encoded and transferred into Google Drive through an API. The encoded picture is put away in the web and just approved client can see this picture. The approvedUsercanutilizeDecryptorprogramtodownload anddecodethepictures.TheprogramutilizesGoogleDrive API to lay out Connection and download pictures from
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page 2275
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
server. The downloaded pictures are then decoded and displayedtoUser.
At the point when PIR Sensor recognizes the movement,thePICameraiscatchesthepictureandstores itinSDCard.Thepictureispresentlytakenandencrypted utilizing RSAAlgorithm.At first the picturecaught is gone through an encrypter. The Encryption Algorithm utilizes 4096bitsPublicKeytoencodethepicture.alongsideOAEP (Optimal Asymmetric Encryption Padding). The encrypted pictureisthen transferred toGoogle drive. WeuseGoogle Drive API to lay out secure association with Google Drive and transfer every one of the encrypted pictures. The encrypted pictures can be downloaded on the approved client's machine and decrypted in like manner utilizing DecryptorProgram.
TheRaspberry Pi3Model B+isthe important part of the project as it is used to connect Pi camera and PIRsensortocontroltheimagecaptureandtorunthe encryptionscript.
It is a general purpose switch with a high current whichcanbeusedasaswitchtocontrolthedcmotors forlocomotionpurpose.
Mainly used in a wide range of applications, such astoysandvehiclesetccarswhichhasa30rpmwhich isembeddedwiththerelay
ThebatteryusedisLeadAcidBatteryandsupplies 12 volts which is mainly used by the DC motor as it requiredahighvoltageusedtomovementoftherobot. Andare rechargeableinnature.
Itis enabling asmoothconnectivity betweeneach andeverycomponent
Pi Camera module of 5MP isused to take pictures as well as a high definition video and has been connectedwiththeRaspberryPiBoard
Passive infrared (PIR) sensor are most often used inmotiondetectionpurposewitharangeof10meters andoperatedat5V.
It is used to manually control the locomotion of robot with a frequency of 2.45GHz and range is up to 10meters.
AVR isa microcontroller of the ATMEL family, uses at mega 48 microcontroller for controlling the locomotionandBluetooth
Theencryptionanddecryptionscriptiswrittenin python and loaded in raspberry pi and also to control thePicamerawithPIRsensor
The AT mega 48 chip is programmed with embeddedCtocontroltherobot.
Itisa crosscompilerusedtocodeembeddedCto ATmega48.
D.
Raspbian OS is an open source computer operating system which is loaded to raspberry pi board.
Itismainlyusedasastagebytheusertoviewthe decryptedoriginalimage.
IthasmainlythetwoHardwaresystem: i)AVRBoard
ii)Raspberrypi
TheAVR boardismountedwith ATmega48IC chip, which has a voltage regulator which helps to regulate the voltage to 5V .Since we are using 12V battery mainly for the movement of the robot we require 12V hence to regulateitfor5Vthevoltageregulatorhelpstoprovide5V toAVRboard whichisconnectedtoBluetoothHC 05.
There are four DC motors where the each side of 2 parallel motors are shorted together and given to relay outputpinandVCCtonopin andGNDtoμcpinwithinthe relay.theportsaredeclared andgiventok1tok4asi1to i4intherelayfromAVR board TheHC 05moduleisused
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page 2276
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
for communicating with the bot using android application called as “ Serial Bluetooth Terminal ” which is freely available in the Playstore. These components are connected by wires and are placed upon a metallic insulatedchassisframeandthechassisisconnectedwithL clamp on all the sides to connect dc motor with movable wheels.
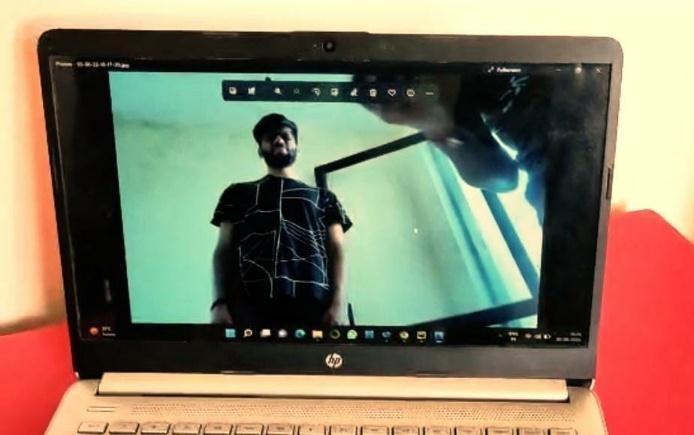
The Raspberry Pi is embedded with the sensors like PIR sensor as motion detector and Pi camera to capture the image We can observe that whenever any person is standing in front of the robot , it can easily detect the person with the help of PIR sensor ,as a result it triggers the Pi camera to capture the image .Once the image is captured it starts to encrypt using public key and if the private key is utilized by authorized person then he can usethattodecrypttheimageandcanviewitinthelaptop
Inthesoftwareimplantation,theAVRisprogrammed with Embedded C programming using code vision .The projectfileiscreatedbyselectingATmega48andsetclock to 4 MG Hz in the configure project and by importing the USART protocol, port pins for necessary components and ADC pins selection and the program is written for the locomotion by assigning condition to the port pins and creating necessary function to the direction. After the program is saved as a hex file and dumped to the AVR boardusingAVRstudioapplication.
For the Raspberry Pi 3B+, the Raspberry Pi OS is loaded in to it .The necessary condition for image capturing from Pi camera and motion detection using PIR sensor is written along with the code for encryption and decryption using RSA algorithm is written and later it is loaded to the raspberry pi board. Once when an motion is detected and image is captured the image gets encrypted using public key which is available to all .If any person without private key tries to decrypt the image he cannot view the it .The image can be viewed by the user using google drive API where he should use the private key Since the private key is available only with authorized person, he can view it in Google API by which any tamperingcanbeprevented.
Indicates the entire crypto vison bot where the robot is beenembeddedwithallthe hardwareaswellassoftware connectionsasmentionedabove.
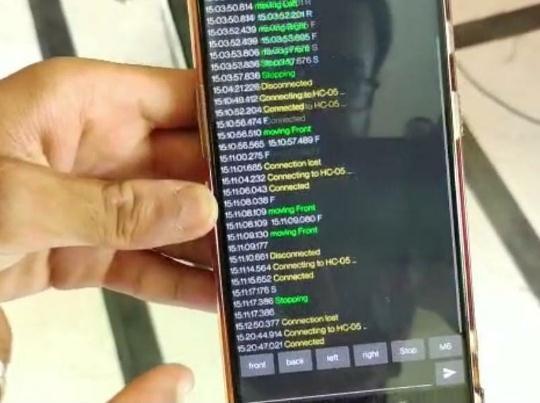
Itshowstheconnectivityaswellasthemovement of the robot in the specified directions using the HC 05 bluetoothinconnectionwiththeSerialBluetoothTerminal AppdownloadedfromPlaystore
The image captured by the Pi camera is been encrypted using RSA encryption algorithm such that encryptedimageisnotintheformattobeviewed
Fig6:Decryptedimage
International Research Journal of Engineering and Technology (IRJET) e ISSN: 2395 0056

Volume: 09 Issue: 06 | Jun 2022 www.irjet.net p ISSN: 2395 0072
The authorized person who has the private key can decrypttheimageandcanviewtheimagecapturedbythe Picamera
Cost Efficient Connecting these elements to form a triangle clearly defines costs benefits, resources benefits,andcosts resources
NoDataInfiltration Bythehelpofstrongencryption technique,noonecanmodifytheoriginalinformation
MoreSecure WeareusingRSAsecurealgorithmfor informationsafety
Authentication Sensitiveinformationcanbeaccessed onlybytheauthorisedperson
MilitaryPurpose Ourrobotishighlyrecommendedfor Military security for the Border surveillance, Spying, patrollingthissinglerobotavoidstheriskofsoldiers
CyberSafetyandsecurity duetotheexcessiveleakage of the crucial and sensitive information form in the securityareaourbotsprovidesbetterauthenticity
Private investigation This bots can be used for any kind of investigations in the areas like where human can'tvisitandcollectclues
Image basedautomatic inspectionand analysis In our Robot we are using Pi camera to capture image so by using this technique we can inspect and analyses presentconditionsofthearea
Government department for enhancing security and safetyingovernmentoranycivicspots
The proposed framework is endeavouring a cost-effective and feasible project in which the speed of the on RSA algorithm by providing the security for the data by using the two keys those are Public key and the Private key. which is fast efficient and secure wireless communication system.BytheuseofPicameraithasabilitytocapturethe imageandencryptusingRSAalgorithm.Thiswilldefinitely enabletherobotWirelessmanualcontrolviawebapp,live streamingofimagesUsedmanuallyforcivilianandmilitary applicationsthroughtheFirebaseplatform.
This kind of robots are more effective where human surveillance is hazardous. Mainly our Crypto bot can be easilycontrolbytheAndroidapplicationfromtheOperator so, the movement of the robot is traceable . Our Robot provide integrity, confidentiality and authenticity from the unauthoriseduse
[1] Aarthi V, Vishal R, Nagarajan K.K “Smart Spying robot with IR Thermal Vision,” 2021 7th International Conference on Advanced Computing and CommunicationSystems(ICACCS)
[2] K Pavani, P. Sri Ramya “ Enhancing Public Key Cryptography using RSA ,RSA CRT and N Prime RSA with Multiple Keys ”, 2021 3rd International Conference on Intelligent Communication TechnologiesandVirtualMobileNetworks(ICICV)
[3] Rabia Abid, Celestine Iwendi, Abdul Rehman Javed, Muhammed Rizwan , Zunera Jalil, Joseph Henry Anajwmba , Cresantus Biamba “An Optimised homomorphic CRT RSA algorithm for secure and effective communication “, Springer , 2021